Leaderboard
Popular Content
Showing content with the highest reputation since 07/06/18 in all areas
-
Am dezvoltat o aplicatie pentru hackeri, dar nu o pot publica deoarece ar afecta tot Internetul... ./nytro --exploit https://nasa.gov Hacking in progres... Got access to admin panel: admin : WeWereNotReallyOnTheMoon@Fake Got root! ssh root@nasa.gov... root@nasa.gov:/ ./nytro --hack-facebook https://facebook.com/profile/MarkZukuBergu Hacking in progress... Got account password: IAmZaBossOfZaMoney2020 ./nytro --hack-my-firend Gigel Hacking in progress... Finding home address: Str. Tuicii, Nr. 2, Casa 3 Finding naked pictures... Holy shit, you don't want to see them... Este foarte periculoasa. Desi unii nu o sa creada, este mai pericoloasa chiar si decat Coailii v10.18 points
-
Daca il intrebi, iti va spune sigur ca si-a inceput viata de antreprenor facand iteme de CS:GO care le-a vandut si profitul l-a investit pe Forex. Acolo a folosit un bot bazat pe o retea neuronala si a facut multi bani. Majoritatea ii tine in conturi off-shore dar mai da si el de mila ceva statului Roman sa nu bata la ochi. La muiere, ca sa nu-i faca scandal, i-a setat o retea de dropshipping cu margele si i-o angajat niste content writers de incredere. Are asa de multi bani incat o trebuit sa isi alcatuiasca o metoda bazata pe sirul lui Fibonacci ca sa se descurce la tinut evidenta hartiilor de 200 lei. Are si un front, ca sa nu bata la ochi, un cabinet stomatologic unde ca sa nu plateasca o contabila a facut 4 ani de facultate, mai ales ca a fost pasionat si de metode de criptografie. P.S. - omul defapt era aelius. Are pula mare si e gigolo - face bani de pe cougars16 points
-
Salutare la toti de mult nu am mai intrat pe forum si am fost activ dar acum am un pic de timp :) si m-am gandit sa mai postez si eu ceva. O zi buna va doresc. Buffer Overflow Attack in PDF ShapingUp. https://youtu.be/7wxQmmHjrLc14 points
-
Salut, Lucrez la o platforma de CTI marca RST. Caut oameni care doresc sa se implice activ in aceasta latura a securitatii si sa populeze platforma intr-un mod cat mai eficient. Voi oferi suport atat cat imi permite timpul. Nu sunt bani in joc, dar e o ocazie destul de buna de a invata si a aprofunda acest domeniu. Vom face o multime de chestii interesante. Cu o astfel de experienta ai sanse foarte mari in a printe un job pe partea de Security. Toti cei care sunt interesati de acest subiect si vor sa participe sa scrie aici sau sa-mi trimita un PM. Voi crea un server de discord pt asta si vom discuta mai multe in chat. Infrastructura o platesc eu. Targetul final este de a ajuta cat mai multi oameni sa se dezvolte pe partea asta si de ce nu sa devenim o sursa de incredere pentru companii sau organizatii romanesti in principal. Pentru cei care vor sa se implice activ va astept aici: https://discord.gg/3fjHp6U Chestii facute pana acum: 1. Am ridicat urmatoarele platforme: MISP, TheHive, Cortex Chestii care sunt pe short list: 1. Populat platforma MISP cu ceva evente sample pentru a putea intelege mecanismul acesteia 2. Testat anumiti analyzers din Cortex 3. Create 1-2 cazuri in Hive pentru a ne familiariza cu conceptul de Security Operations Center 4. Email catre cateva surse de threat intel pentru a ne oferi suport in acest proiect, nu cu produsurile finale ale lor dar cu ceva beta Daca stiti ceva surse de threat intel care au trial version sau sunt dispusi sa ne sustina in acest proiect let me know. Am sa postez in acest topic evolutia13 points
-
Echipa de security de la UiPath are 3 pentesteri. Toti sunt membri RST cu vechime. Daca inca sunt persoane care considera ca RST e o adunatura de copii, acesta e doar un exemplu. Multi au pornit de aici. Nu toti mai sunt activi, dar noi, cativa, vom fi mereu aici. RST nu moare!13 points
-
Putin whistle-blowing...share, comment & distribute Vad ca inaptii tac ca "porcul in papusoi" despre treaba asta asa ca postez aici: se pare ca au fost hackuiti si tac in privinta asta. Am aplicatia eBay pe telefon si Sambata dimineata (aproximativ ora 8.30) primesc o notificare de la app ca produsul meu s-a vandut. Nu aveam nimic postat de vanzare si nu folosisem pana atunci eBay-ul de vreo 1-2 luni. A trebuit sa astept pana la 9am sa vorbesc cu cineva de la support si tipa cica "da, stim ca sunt ceva hackeri care fac chestia asta insa se pare a fi automata". A verificat adresa de IP de unde s-a postat produsul si era de Hong Kong. Ce-i mai nasol e ca sunt foarte discreti in treburile astea - nu am primit nici o notificare referitor la schimbarea parolei, ca a fost postat un item nou, ca am vandut ceva nimic - de obicei primesc toate astea prin mail. Daca nu aveam aplicatia pe telefon nu aflam poate nimic, poate doar cand era prea tarziu. Si tipa de la eBay support cica "da, stim ca fac chestia asta, dar nu stim inca cum o fac, se pare a fi un bot care face tranzactii multe si marunte", etc. And the English version - eBay have been hacked and they seem to be keeping quiet about it. I have the eBay app on my phone and on Saturday morning (approx 8.30am) I get a notification from the app that my item has been sold. I did not have any item on sale and have not been using eBay for the past 1-2 months. I had to wait until 9am to ring their support and they were like "yeah, we know there's some hackers who are doing this, seems to be automated". And they checked the IP address from where the listing was made and it was from Hong Kong. But what's more worrying is the stealth with which they've done this - I had no notification of my account changing password, had no notification that an item has been posted for sale, etc. If I wouldn't have had the app on my phone, I would have probably not found about it until too late. And the lady on eBay support on the phone was like "yeah, we know about this, but we don't know how they're doing it, seems to be some bot as they're doing loads of small value transactions", etc.13 points
-
Daca aveti nevoie sa schimbati domeniul pentru un wordpress sau sa schimbati protocolul (din http in https), trebuie sa actualizati toate link-urile prezente in baza de date, atat de la posturi cat si cele de la optiuni. Operatiunea este foarte simpla si aveti nevoie doar de acces MySQL. Puteti utiliza atat CLI cat si phpMyAdmin. Exemplu: update wp_options set option_value = replace(option_value, 'http://rstforums.com', 'https://rstforums.com') WHERE option_name = 'home' OR option_name = 'siteurl'; update wp_posts set guid = replace(guid, 'http://rstforums.com', 'https://rstforums.com'); update wp_posts set post_content = replace(post_content, 'http://rstforums.com', 'https://rstforums.com'); update wp_postmeta set meta_value = replace(meta_value, 'http://rstforums.com', 'https://rstforums.com'); Note: - In exemplul de mai sus domeniul vechi este rstforums.com pe http iar domeniul nou este rstforums.com pe https. - Exemplul este valabil si daca schimbati numele de domeniu, nu doar protocolul - Nu se adauga slash-ul de final dupa numele domeniului. - 'wp_' din numele tabelelor reprezinta prefixul. Este posibil sa aveti wordpress instalat cu alt prefix. In fisierul de configuratie "wp-config.php" puteti vedea prefixul la "$table_prefix" sau direct in mysql.13 points
-
O vulnerabilitate pe care am descoperit-o in https://www.xoom.com/. Aplicatia este detinuta de cei de la PayPal. Este o problema mai veche. Recompensa: 5,300$12 points
-
Topicul asta are legatura mai putina cu IT-ul, este de fapt o experienta avuta cu o individa din romania (e scris intentionat cu litere mici). Poate va ajuta in viitoarele voastre colaborari sau cand va ganditi sa faceti afaceri cu romani, in special aia uscati de foame. Presa, deontologia si afacerile din tara lui Papura Voda. In perioada august 2019 - aprilie 2020 am scris o serie de articole intr-un site de stiri. Majoritatea din ele, au fost articole lungi, bine documentate si scrise intr-o maniera profesionala. Cand am incheiat colaborarea, proprietarul site-ului a sters efectiv utilizatorul sub care am publicat materialele si le-a atribuit pe un nume generic de autor. Oare cat de mare e nivelul de retard incat sa-ti atribui munca altora si sa te doara in fund de tot? Probabil asa si-a facut si lucrarea de licenta, furand de la altii. Si asta nu e tot. In august 2019, am fost contactat de acelasi proprietar de site, sau sa-i spunem de domeniu, pentru ca avea un site facut care efectiv nu mergea. A stat online mai mult de un an, in care nu a castigat mai mult de 300 de euro adunati. Mi-a propus un parteneriat in care sa fie 50/50, eu sa ma ocup de tot ce inseamna parte tehnica, de la constructie site, elemente grafice, seo pana la hosting, iar el sa se ocupe de articole. Site-ul vechi a ajuns sters, am luat totul de la capat si in timp foarte scurt, am facut complet un site functional si bine pus la punct. In scurt timp au fost aduse doua persoane care sa scrie continut, apoi inca una ... si inca una. Traficul a crescut rapid, la fel si veniturile obtinute din publicitate. Din banii castigati din publicitate, erau platiti oamenii care scriau materialele pe site, iar restul, erau impartiti in mod egal, iar eu din partea mea suportam cheltuielile de infrastructura. In urma cu o saptamana (la inceputul lunii), a inceput sa vorbeasca pe un ton nu tocmai potrivit pentru un om care se crede intelectual, superior si foloseste semnaturi pompoase cand comunica pe email. Ne-am certat, sau mai bine spus s-a certat singur. Am sunat sa vorbesc si zbiera la telefon in timp ce eu vorbeam usor, dupa care i-am inchis telefonul in nas, neputand avea un dialog civilizat. Au urmat un schimb de email-uri cu diverse tehnici tiganesti prin care mi se reprosa ca am instalat un wordpress amarat si de fapt nu am facut nimic pentru site, ca tot succesul i se datoreaza. Mi-a spus ca vrea sa isi ia site-ul (toata platforma) si sa-l mute in alta parte, ca nu mai e de acord sa fim parteneri. Nedorind sa ma cert, i-am oferit acces total la platforma, dupa care a luat legatura cu oarece gigei low cost pentru intretinerea site-ului si pentru hosting, apoi au venit alte replici dure pe email. Replici care sunau cam asa: - Sa ofer ajutor gigeilor low cost, ca nu se descurca - Sa las orgoliile, ca sigur am facut ceva prin site si de asta nu reusesc gigeii sa-i puna online cateva module - Ca stie el cu ce ma ocup de fapt si ca pot avea probleme (lol) - Ca nu stiu sa configurez servere (desi fac asta de mai bine de 20 de ani). Oare unde erau impiedicatii astia cand luam distributiile de linux de la universitatea tehnica din Finlanda si le puneam pe ftp-ul public de la roedu network, sa ajut comunitatile sa se dezvolte, sa contribuim la un internet mai bun si sa avem acces la informatie. Asa e cand te incurci cu tot felul de ratati, fara bun simt, care toata viata lor nu au realizat ceva, in afara de certuri si scandaluri ieftine cu diverse persoane. Sfat: cand vedeti in strada un rahat, sub nicio forma nu va opriti sa calcati pe el, sau sa-l luati la palme. Intr-un final se va usca si il va matura ploaia. Fruntea sus si mergem mai departe. Daca aveti curiozitatea despre cine vorbesc: O cheama Anca Andrei iar site-ul este voxbiz.ro.12 points
-
XSS Reflected - api.office.com = 500$. XSS Reflected - [*].live.com = 1.200$ recompensa. Aceasta problema necesita interactiunea utilizatorului.12 points
-
Pentru ca de multe ori am cerut ajutorul aici si de prea putine ori l-am oferit inapoi, va pun la dispozitie toate cartile mele de Cisco. Doar Cisco am ca asa mananc painea zilnica. https://we.tl/t-m69KrEzFGx https://we.tl/t-HrRwcciXqn De asemenea, pentru cine merita am toate cursurile de la INE (CCNA, CCNP & CCIE), atat R&S cat si Security, CBTNuggets, GNS3WorkBench, Pearson IT Certifications, Packt, RouteHUB si IpExperts, care se gasesc foarte greu astazi, pentru ca IpExperts a fost inchis. Cine stie, cunoaste. Ca sa va incadrati la culoarea rosie nu trebuie sa fi cerut invitatii FileList si sa fiti vechi. Toate cursurile video sunt platite si downlodate, asa ca e dreptul meu sa aleg cui le dau. PS: De ceva timp am inceput sa-mi blestem zilele cu CCIE-ul si as avea mare nevoie de cursurile celor de la IpExperts. Cum ei nu mai sunt pe piata, iar eu am doar CCNP de la ei, nu prea am de unde sa le mai iau. Cine le are si crede ca le merit, multumesc.11 points
-
Blog: https://msrc.microsoft.com/blog/2023/08/congratulations-to-the-msrc-2023-most-valuable-security-researchers/ Leaderboard (2023 MVR): https://msrc.microsoft.com/leaderboard Mai sunt doua persoane pe lista si sunt membrii RST: @Zatarra @adiivascu. V-am salutat:11 points
-
Salut. Am gasit doua vulnerabilitati XSS in aplicatiile detinute de cei de la Microsoft. Una este in Outlook, iar a doua intr-o alta aplicatie folosita si cunoscuta de multi... nu pot da detalii momentan deoarece nu a fost rezolvata nici una pana acum... Cel putin, nu am primit duplicat pe rapoartele trimise. 🙂 1. XSS reflected (without user interaction) - [*].live.com: 2. XSS reflected (user interaction required) - Outlook: Am observat ca si domeniile acestea sunt vulnerabile: office365.com si live.com.11 points
-
11 points
-
Cei cu probleme sa ma contacteze. Am in familie epidemilog si pe boli infectioase... (printre singurii pe tara) caz de .... pt oameni pe aici. Nu e de bani. Nici nu se pune problema. https://www.doctorbun.ro/doctor-marinela-tranca_35581.html nr de tel pe privat se cere doar la cazuri confirmate in familie.. fara chestii aiurea cu intrebari. // se dau doar sfaturi de la specialist in cazuri confirmate/izolare. Lasati mesaj pe webmaster@nationalisti.ro cu nr de tel cei cu probleme.11 points
-
Ba, urmaresc forumu asta din umbra de ceva timp, nu am mai postat. Dar cat puteti ba sa fiti de terminati? Oare prostia asta a voastra nu are limite? Ce baza de date ba, ca aia era cu persoane de prin anii 90'. 80% din cei care sunt in baza aia de date au murit. Numa invitatii filelist, coduri, dork-uri si baze de date visati. Sa faceti ceva pentru viitoru vostru n-ati face. Ai aici oameni care sunt guru in Linux, care stiu Python si alte lucruri utile si voi cereti baze de date.11 points
-
1- Web Application Penetration Testing eXtreme (eWPTX ) ---------------------------------------------------- 03. Website_cloning.mp4 03. From_An_XSS_To_A_SQL_Injection.mp4 03. Keylogging.mp4 09. Advanced XXE Exploitation.MP4 07. Advanced_SecondOrder_SQL_Injection_Exploitation.mp4 05. Advanced_XSRF_Exploitation_part_i.mp4 06. Advanced_XSRF_Exploitation_part_ii.mp4 09. Advanced_Xpath_Exploitation.mp4 WAPTx sec 9.pdf WAPTx sec 8.pdf WAPTx sec 2.pdf WAPTx sec 3.pdf WAPTx sec 5.pdf WAPTx sec 6.pdf WAPTx sec 4.pdf WAPTx sec 7.pdf WAPTx sec 1.pdf 2- Penetration Testing Professional (ePTPv3) 3- Web Application Penetration Testing (eWAPT v2) ---------------------------------------------------- Penetration Testing Process Introduction Information Gathering Cross Site Scripting SQL Injection Authentication and Authorization Session Security HTML5 File and Resources Attacks Other Attacks Web Services XPath https://mega.nz/#!484ByQRa!N7-wnQ3t5pMCavOvzh8-xMiMKSD2RARozRM99v17-8I Pass: P8@Hu%vbg_&{}/2)p+4T Sursa:10 points
-
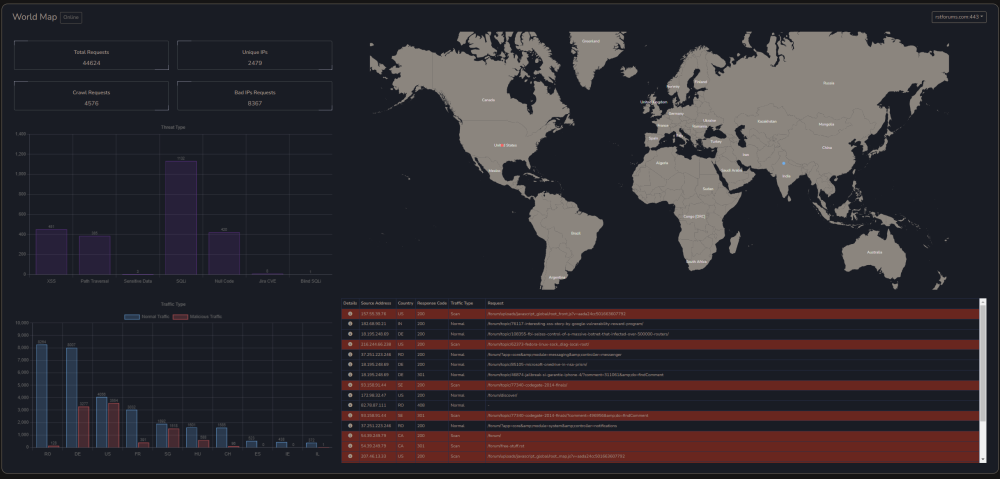
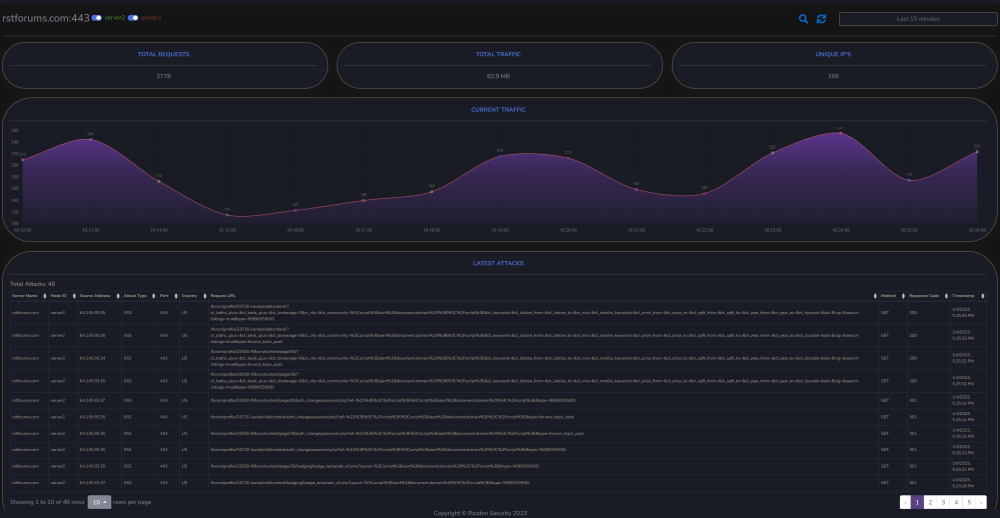
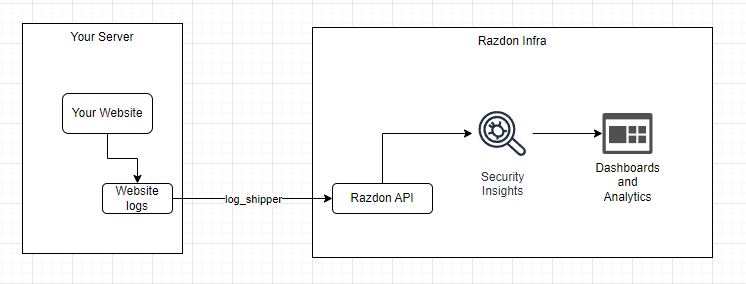
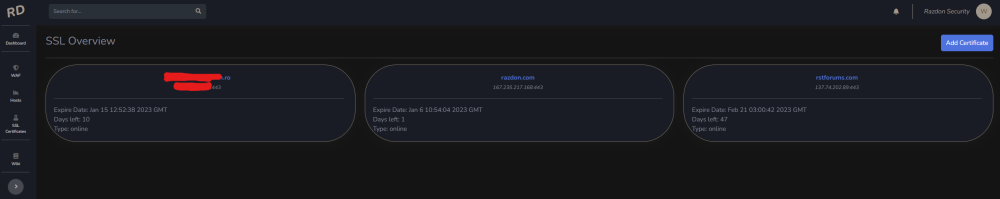
Salut a todos, Am un proiect pe partea de CyberSecurity, la care lucrez de ceva timp impreuna cu un fost coleg de munca si pe care as vrea sa vi-l prezit si voua cu speranta in a veni si a-l testa. Am fost si la Defcamp unde am avut un stand (multumim @Andrei cu aceasta ocazie) si am rulat un program de BugBounty (care inca e valid - cine gaseste un bug valid il raporteaza si in functie de severitate vom premia cu vouchere Emag) Pe scurt, este vorba de https://razdon.com , un website care va ofera posibilitatea de a "onboardui" si a veda traficul vostru LIVE cu un extra context de securitate la fiecare request. Aceasta parte de live este prezentata sub forma unui dashboard unde poti vedea harta lumii si toate request-urile venind spre locatia serverului tau. Aveti un screenshot atasat mai jos: Dupa cum vedeti proiectul a fost dezvoltat pe RST si aici puteti vedea un window de aproximativ 8 ore cu toate statisticiile legate de RST in aceste 8 ore + traficul live, bineinteles. Pe langa partea de dashboard live, care necesita interactiune minima (practic este doar selectia site-ului in scop - in cazul in care aveti mai multe), avem si partea de analiza de trafic. In partea de analiza de trafic ai optiunea de a cauta in toate request-urile pe o anumita perioada de timp dupa ceva anume (ex. toate requesturile cu status code 4XX or 3XX). In partea de analiza este prezenta si un scurt istoric al atacurilor recente (cu tot cu tipul lor) Puteti vedea o bucata din acesta pagina mai jos: Un alt meniu destul de interesat este cel cu partea de certificate SSL, unde va puteti verifica data de expirare a certificatului (iar pe viitor vom implementa si sistem de alerte - atat la certificate cat si la atacuri). Un screenshot cu partea de certificate mai jos: Putem implementa si partea de WAF, dar momentan avem 0 focus in aceasta directie. Foarte curand vom face release si la un beta pe partea de artificial intelligence / machine learning, cu ajutorul carora vom maximiza eficienta detectarii atacurilor. Acestea fiind spuse, daca cineva este interesat de un asemenea produs, inregistrariile sunt deschise si puteti urma pasii necesari pentru a viziona traficul. Pentru a evita intrebariile de tipul cum faceti asta, va informez de pe acum ca singurul lucru care e necesar pentru aceste actiun sunt logurile de apache, respectiv nginx cu traficul website-ului. Momentan preluam aceste loguri cu un binar scris in GO (pentru eficienta) dar voi pune si varianta (raw) cea de a trimite catre API-ul nostru log-urile fara a rula un binar (safety reasons). O mica schema pentru a intelege mai bine cum sta treaba aveti jos. Mersi si o seara faina! P.S. In caz ca vrea sa ne cumpere careva cu vreo 2-3 mil de euro sa-mi dea un MP, dupaia e mai scump.10 points
-
Salut forum, as vrea sa adaugam niste linkuri de la Mega cu orice cursuri SANS (sau altele) pe care le mai gasiti pe net. O sa incep eu. Pentester Academy Abusing SQL Server Trusts in a Windows domain: https://mega.nz/#F!jjpmASIS!VTc_8DjGuExZBDv4E8-SwA SANS 642: https://mega.nz/#F!enwXQSib!uzuCIvly6E9t8cx8J1pN2Q!miAVhDKZ https://mega.nz/#F!enwXQSib!uzuCIvly6E9t8cx8J1pN2Q SANS SEC560 - 2017: https://mega.nz/#F!tO4TQbga!OvStyzKmOta6MEcZmesP7w SANS 555: https://mega.nz/#F!7KZw2AhR!hE-yr2rrxjRxpHgpt8pRGg SANS 760 vm: https://mega.nz/#!3QpCkDQA!qP24XpGeNGZ3_5EBaUULm2F23jyVbYuwP_0JDk097ts Pentester Academy cursuri: https://mega.nz/#F!2zZXwTzI!4wVK8DOAD-Dj8vsccvoKPg https://mega.nz/#F!CewXwASZ!SrQJtaL0MM9f8CqbvcqZGg Luati si adaugati cat sunt calde!10 points
-
Scuzati-ma ca intervin, dar am si eu o mica precizare de facut. Baieti, cum puteti sa discutati despre 5G sau COVID sau teorii ale conspiratiei cu Bill Gates si pula mea cand voi nu aveti teorii minime despre cum functioneaza o retea, despre cum functioneaza un virus in organism sau despre bani? Nu mai rezist sa vad atatia prosti care isi dau cu parerea. Ba nene, esti programator? Vorbeste frate de 0 si 1, vorbeste de clase si ce plm mai e prin programare. Lasati virusii ca mai sunt copii pe aici care vad ce debitati voi si uite asa se naste inca o generatie de retardati. E de bun simt, DE BUN SIMT, sa nu iti dai cu parerea despre ceva ce nu stii. Stiu ca e palpitant, e wow sa pari interesant, dar daca voi habar n-aveti sa treceti strada, cum discutati de virusi? Da, este foarte bine sa va informati, sa nu fiti niste oi. Si eu fac asta. Si eu cred ca acest virus nu provine de la un liliac(wtf) dar totusi, nu am destule informatii. De ce sa debitez pe aici prostii? A aparut prostia aia cu 5G. Mi-am luat o carte despre cum functioneaza undele radio doar pentru ca voiam sa vad daca e ceva adevarat. Nu am inteles subiectu, cu toate ca am citit aproape 500 de pagini, nu imi dau cu parerea. E chiar asa greu sa fiti rezonabili? Sa nu mai zic ca unii dintre voi sunteti atat de idioti, atat de batuti in cap incat voi credeti asa: Bill Gates ala a facut un virus care o sa omoare milioane de oameni pe planeta si a vorbit despre treaba asta acu X ani. Sincer acum, chiar sunt calm dar cum puteti sa fiti asa de idioti? Adica gen eu sunt Bill Gates si o sa dau o bomba nucleara sa omor rusii ca nu imi plac mie rusii. Si ce fac? Vorbesc despre asta cu cativa ani inainte? Vreti sa fiti vectori de opinie? Citit carti frate. Nu mai ctiti pe Facebook si pe stirismechere.ro sau ce fantoma de site-uri mai exista. Citit frate carti. Despre virusi. Si veti afla de exemplu ca noi suntem virusii pe aceasta planeta. Si ca virusii de exemplu sunt primele forme de particule ce au supravietuit in celule parazitare. Nu mai fiti ignoranti si nu mai inaintati forme de informare dubioase. Noi astia cu putin creier stim sa va delimitam si sa va bagam in cutia penibilului dar mai sunt altii care va cred si uite asa, din cauza unora ca voi, primesc eu mesaje pe whatsapp de imi vine sa arunc telefonu pe geam.10 points
-
When hunting for security issues, the pursuit for uncharted assets and obscure endpoints often ends up taking the focus away from obvious, but still critical, functionality. If you approach a target like you are the first person to ever perform a security assessment on it, and check everything thoroughly, I believe you are bound to find something new — especially if the code you are testing has been in continuous development for a while. This is the story of a high-severity bug affecting what is probably one of PayPal’s most visited pages: the login form. Initial discovery While exploring PayPal’s main authentication flow, I noticed a javascript file containing what appeared to be a CSRF token and a session ID: This immediately drew my attention, because providing any kind of session data inside a valid javascript file usually allows it to be retrieved by attackers. In what is known as a cross-site script inclusion (XSSI) attack, a malicious web page can use an HTML <script> tag to import a script cross-origin, enabling it to gain access to any data contained within the file. Sure enough, a quick test confirmed the XSSI vulnerability and, although a javascript obfuscator was used to randomize variable names on each request, the interesting tokens were still placed in fairly predictable locations, making it possible to retrieve them with just a bit of extra work. However, a secret is only as good as the damage you can do with it. I immediately set out to find out what exactly _csrf and _sessionID were and if they could actually be used in a real attack. Digging further After countless attempts to replace regular CSRF tokens inside authenticated requests on PayPal’s platform with the value of _csrf, I came to the conclusion that a classic cross-site request forgery attack was not possible using this specific token. Similarly, a victim’s _sessionID was unfortunately not enough to impersonate them on PayPal’s site. Next, I went back to the vulnerable script and followed the tokens to find what they were actually used for. This led to a deep dive into one of PayPal’s main protection mechanisms used to prevent brute force attacks, the security challenge. While this functionality is used in many places, I will be focusing on the main login form. The idea is pretty simple: After a few failed login attempts, you are required to solve a reCAPTCHA challenge before you can try again. The implementation, however, may raise some eyebrows. Upon detecting a possible brute-force attempt, the response to the next authentication attempt is a page containing nothing but a Google captcha. If the captcha is solved by the user, an HTTP POST request to /auth/validatecaptcha is initiated. The familiar _csrf and _sessionID are present in the request body, as well as two other values, which we will get to a bit later. The response to the captcha validation request is meant to re-introduce the user into the authentication flow. To this end, it contains a self-submitting form with all the data provided in the user’s latest login request, including their email and plain text password. I realized that, with the correct timing and some user interaction, knowing all the tokens used in this request was enough to get the victim’s PayPal credentials. In a real-life attack scenario, the only user interaction needed would have been a single visit to an attacker-controlled web page. So I went back and tried to figure out what the missing parameters were. This was easier than expected: The value of jse was not validated at all. recaptcha was the token provided by Google upon solving a reCAPTCHA challenge. It was not tied to a specific session, so any valid token— for example, from an automated solving service — would be accepted. Exploitation Putting all this together, I created a proof of concept that demonstrated the whole process, except for integrating a captcha solving service. First, the proof of concept would exploit the initial XSSI vulnerability to get a set of tokens which were valid in the victim’s session. It would then launch a few authentication requests with random credentials from the victim’s browser, simulating a brute force attempt, which would trigger the security challenge flow. Once the victim logged in to PayPal using the same browser, the cached random credentials would be replaced by the user’s own email and password. The last step was obtaining a fresh reCAPTCHA token, after which the plain text credentials would be retrieved from the /auth/validatecaptcha endpoint and displayed on the page. The final page shown by my proof of concept code contained your email and password I later found that the same vulnerable process was also used on some unauthenticated checkout pages, allowing plain text credit card data to be leaked using the same technique. Disclosure The proof of concept, along with all relevant information, was submitted to PayPal’s bug bounty program on the 18th of November 2019, and was validated by HackerOne 18 days later. Following a quick acknowledgement by the PayPal team and a few additional questions, I was awarded a $15,300 bounty on the 10th of December. The reward amount corresponds with the bug’s 8.0 (High) CVSS score, which is the same score that I had initially suggested when submitting the report. A patch was applied around 24 hours later, meaning that the bug was fixed only five days after PayPal became aware of it — quite an impressive turnaround time. Fix and prevention advice The /auth/validatecaptcha endpoint now requires an additional CSRF token, which cannot be leaked using cross-site script inclusion. While this properly fixes the vulnerability, I believe that the whole thing could have been prevented when designing the system by following one of the oldest and most important pieces of infosec advice: Never store passwords in plain text. By the way, I am looking to do security assessments and bug bounty program management work. I have experience in security testing, vulnerability triage, as well as a background in software development. Does this sound of interest to you? You can get in touch via alex@ethicalhack.ro. Source https://medium.com/@alex.birsan/the-bug-that-exposed-your-paypal-password-539fc2896da910 points
-
10 points
-
9 points
-
Am blocat anumite clase de IP-uri pentru acces. Va las pe voi sa va dati seama care.9 points
-
Eu am dezvoltat un bruteforcer cuantic care ruleaza pe blockchain si foloseste artificial intelligence ca sa obtina acces la servere de pe glob. E privat. Din fericire nu trebuie compilat, e scris in PHP.9 points
-
Unde ai fost pe afara si cat? Aveti preturi mult mai mari decat in Germania sau Elvetia. In special in catunul de Bucuresti sau in Cluj. Oricum, toti vorbiti de bani. - De liniste nu spune nimeni ceva - De asigurare sociala sau de sanatate nu spune nimeni - De infrastructura la fel. Nu aveti strazi, nu aveti autostrazi, e totul facut in batjocura - De taxele extrem de mari nu spune nimeni nimic (nu alea din statistici, cele reale) - De preturile exorbitante nu mai spune nimeni nimic. Inclusiv alimentele sunt mult mai scumpe decat in tarile din vest. Chiriile au preturi ca in Germania si conditii de romania. In special in saracia aia de bucuresti (cel mai jegos oras vazut vreodata in europa). Ca sa nu spun de Cluj. Preturi de Geneva si conditii de inchisori rusesti. Continuati sa visati ca romania o sa ajunga vreodata o tara civilizata. Te futi in ea de tara si in parastasul ei. Voi va rezumati la IT. Rezumati-va la cineva care serveste la o terasa, care e paznic, care e vanzator. Adica din ce e formata marea pulime, nu faceti statistici pe elite si grupuri privilegiate.9 points
-
Salut, in urma unei discutii la bere cu niste baieti de pe forum am pornit ideea ca o conferinta online a comunitatii ar putea fi utila pentru toata lumea si ar fi realizabila fara un efort prea mare (e.g. locatie, sponsori etc.). Asadar, undeva anul acesta, probabil prin noimbrie (data o putem decide impreuna) am vrea sa facem o conferinta online in limba romana. 1. Va fi online 2. Vor fi prezentari (45-50 min, pauza 10-15 min), probabil pe parcursul unei zile 3. Va fi un CTF, vom incerca sa il facem cat mai diversificat 4. Participarea va fi gratuita 5. Nu oferim bani sau altceva celor care prezinta sau ne ajuta dar putem iesi (in functie de cum evolueaza lucrurile cu Covid) la bere Am vrea sa stim in primul rand cam cate persoane ar fi interesate de participare si ce idei si sugestii ati avea. Ulterior vom deschide un call for papers pentru a gasi prezentari si ne vom apuca de treaba. Din punctul meu de vedere e o singura problema: ce platforma sa folosim pentru conferinta? Cum sa se desfasoare? Deci, ce parere aveti?9 points
-
STAGIU DE VOLUNTARIAT / PRACTICĂ LA CERT-RO Directorul General al CERT-RO Dan Cîmpean caută un număr de patru (4) voluntari pe perioada: 21 Iulie 2020 - 15 Septembrie 2020 , care sunt interesați să trăiască timp de două (2) luni experiența profesională a unui Director din Centrul Național de Răspuns la Incidente de Securitate Cibernetică. Condiții de participare: · Student(ă) sau absolvent(ă) de studii superioare · Cunoștințe de limba engleză nivel cel puțin mediu · Interesat(ă) de a activa, lucra și învăța în una din instituțiile de vârf ale Guvernului României · Un (1) student și o (1) studentă din București, ce vor activa la CERT-RO · Un (1) student și o (1) studentă din județe, ce vor activa online · Disponibilitate de a activa in medie 2 ore pe zi, flexibil. Selecția se va face de către Departamentul HR al CERT-RO pe baza CV-urilor primite. CV-ul trebuie trimis la adresa de mail HR@CERT.RO până la data de 17 iulie 2020, 23:59.9 points
-
Salut, Cisco ofera niste cursuri de Cybersecurity si de Python free. Mai sunt si altele dar pentru mine neinteresante. Personal il fac acum pe cel de la Python care este oferit de Python Institute si este chiar ok. Interfata ok, explicatii ok, exemple ok, teste ok. https://www.cisco.com/c/m/en_sg/partners/cisco-networking-academy/index.html Mai sus gasiti lista cu aceste cursuri. Primiti si o certificare la final (pe care va sftauiesc sa o folositi pe post de hartie igienica si sa nu mai dati iama la Mega Image ca azi n-am mai gasit nimic). Bafta! PS: Pentru cei care se pregatesc sa imi spuna ca sunt niste certificari de cacat. Nu conteaza certificarea ci ce stiti voi. Dar certificarea va ajuta sa treceti de HR, adica de acele domnisoare care stiu cum se aplica oja pe unghii mai mult decat diferenta dintre CCENT si CCIE, ca tot m-am lovit de problema asta curand.9 points
-
9 points
-
Salutare Guys, Cum se mai intampla sa te plictisesti in concediu, am facut azi, un script in python cu care poti descarca melodii de pe Tidal (https://tidal.com). Tidal este un serviciu de streaming online asemanator Spotify, doar ca are o calitate net superioara: HI-FI - 44.1 kHz/16 bit flac si mp4 si Master - 96 kHz/24 bit (MQA) - flac . Daca ai niste scule decente (fie ca e vorba de casti sau un sistem) e must have! Povestea a inceput de la nevoia de a descarca niste melodii pentru a le asculta offline, si cum nu am gasit nimic functional, am decis sa scriu eu aceasta aplicatie. Si m-am gandit sa impartasesc cu voi! Dependinte (e posibil sa imi fi scapat cateva): pip install tidalapi Unidecode ffmpeg - trebuie sa fie in system path Testand jucaria am gasit un bug in tidalapi: in cazul in care o melodie nu are relese date, va crapa, este un caz extrem de rar, si se intampla inspecial la unele melodii vechi. Daca iti place doar muzica noua si foarte comerciala cu siguranta nu ai neaparat nevoie de acest fix. # fix in tidalapi: # edit __init__.py # from line 224 # change: # if 'releaseDate' in json_obj: # try: # kwargs['release_date'] = datetime.datetime(*map(int, json_obj['releaseDate'].split('-'))) # except ValueError: # pass # return Album(**kwargs) # with: # if 'releaseDate' in json_obj: # if json_obj['releaseDate'] is None: # json_obj['releaseDate'] = '2008-10-14' # try: # kwargs['release_date'] = datetime.datetime(*map(int, json_obj['releaseDate'].split('-'))) # except ValueError: # pass # return Album(**kwargs) Salvati codul intr-un fisier .py, si rulati-l. Apropo, caile catre fisierele salvate/creerea de directoare este hardcodata in format *nix, deci nu va asteptati sa va mearga pe windoza fara mici finisaje. Este scris si testat in Python 2,7 (defaultul la macOS Majave) dar am cautat sa il tin compatibil si cu Python 3.x (sper ca mi-a iesit). # -*- coding: utf-8 -*- # RST Tidal MP4 Downloader by Cheater v1.0 (https://rstforums.com) # All tracks will be download in PCM (MPEG AAC Audio coded, MP4A) at 44100 Hz/16 bits, 320 kbps and stored in MP4 container # requirements: # pip install tidalapi Unidecode # ffmpeg # tidalapi has a bug, so if some album/playlist contains one song with no date, it will exit, this is very rare, however, there is some workaround. # fix in tidalapi: # edit __init__.py # from line 224 # change: # if 'releaseDate' in json_obj: # try: # kwargs['release_date'] = datetime.datetime(*map(int, json_obj['releaseDate'].split('-'))) # except ValueError: # pass # return Album(**kwargs) # with: # if 'releaseDate' in json_obj: # if json_obj['releaseDate'] is None: # json_obj['releaseDate'] = '2008-10-14' # try: # kwargs['release_date'] = datetime.datetime(*map(int, json_obj['releaseDate'].split('-'))) # except ValueError: # pass # return Album(**kwargs) import tidalapi import os import subprocess import errno import shlex from aigpy.cmdHelper import myinput from subprocess import Popen, PIPE, STDOUT from random import randint from time import sleep import unidecode # compatibility workaround for py27/py3 try: from subprocess import DEVNULL # py3k except ImportError: import os DEVNULL = open(os.devnull, 'wb') # fill this with your tidal user and pass tidalUser = '' tidalPass = '' cwd = os.getcwd() config = tidalapi.Config() # using HIGH quality in order to get mp4's unencrypted url instead of enctyped flac config.quality = 'HIGH' session = tidalapi.Session(config) session.login(tidalUser, tidalPass) def getTidalTrackUrl(track_id): try: url = session.get_media_url(track_id) return url except: # in case we need to retry we add a random sleep, in order to worckaround bot detection sleep(randint(1,10)) print('Tidal responds with 401. Retrying track url discovery for track id: ' + str(track_id)) generatePlaylistTrackUrl(track_id) def downloadAlbum(): while True: print("----------------ALBUM------------------") sID = myinput("Enter AlbumID(Enter '0' go back) :") if sID == '0': return tracks = session.get_album_tracks(album_id=sID) queue = [] for track in tracks: trackNo = str(tracks.index(track) + 1) # don't try to download unavailable track, it will fail if track.available is False: continue # replace utf-8 diacritics with ascii equivalent, and cleanup " and ' from album/artist/track name trackName = unidecode.unidecode(track.name).replace('"', '').replace("'", "") artistName = unidecode.unidecode(track.artist.name).replace('"', '').replace("'", "") albumName = unidecode.unidecode(track.album.name).replace('"', '').replace("'", "") print('Adding to queue: ' + artistName + ' - ' + albumName + ' - ' + trackNo + '.' + trackName) # create dw directory and subdirs if it not exits if not os.path.exists(cwd + '/tidalDownloaded/' + albumName): os.makedirs(cwd + '/tidalDownloaded/' + albumName) cmd = 'ffmpeg -y -i "rtmp://' + getTidalTrackUrl(track.id) + '" -acodec copy "' + cwd + '/tidalDownloaded/' + albumName + '/' + trackNo + '.' + artistName + ' - ' + trackName + '.mp4"' queue.append(cmd) print('All track has been added to queue successfully. Download begins....') processes = [] for cmd in queue: p = subprocess.Popen(shlex.split(cmd), shell=False, universal_newlines=True, stdout=DEVNULL, stderr=subprocess.STDOUT) processes.append(p) print('All tracks download is in progress. Please wait....') # wait for all started ffmpeg processes to be finished for p in processes: if p.wait() != 0: print("There was an error") print("Finished. All tracks has been download successfully!") return True def downloadPlaylist(): while True: print("----------------PlayList------------------") sID = myinput("Enter PlayList(Enter '0' go back) :") if sID == '0': return playlist = session.get_playlist(playlist_id=sID) tracks = session.get_playlist_tracks(playlist_id=sID) queue = [] for track in tracks: trackNo = str(tracks.index(track) + 1) # don't try to download unavailable track, it will fail if track.available is False: continue # replace utf-8 diacritics with ascii equivalent, and cleanup " and ' from playlist/artist/track name playlistName = unidecode.unidecode(playlist.name).replace('"', '').replace("'", "") trackName = unidecode.unidecode(track.name).replace('"', '').replace("'", "") artistName = unidecode.unidecode(track.artist.name).replace('"', '').replace("'", "") print('Adding to queue: ' + playlistName + ' - ' + trackNo + '.' + artistName + ' - ' + trackName) # create dw directory and subdirs if it not exits if not os.path.exists(cwd + '/tidalDownloaded/' + playlistName): os.makedirs(cwd + '/tidalDownloaded/' + playlistName) cmd = 'ffmpeg -y -i "rtmp://' + getTidalTrackUrl(track.id) + '" -acodec copy "' + cwd + '/tidalDownloaded/' + playlistName + '/' + trackNo + '.' + artistName + ' - ' + trackName + '.mp4"' queue.append(cmd) print('All track has been added to queue successfully. Download begins....') processes = [] for cmd in queue: p = subprocess.Popen(shlex.split(cmd), shell=False, universal_newlines=True, stdout=DEVNULL, stderr=subprocess.STDOUT) processes.append(p) print('All tracks download is in progress. Please wait....') # wait for all started ffmpeg processes to be finished for p in processes: if p.wait() != 0: print("There was an error") print("Finished. All tracks has been download successfully!") return True while True: print(" RST Tidal MP4 Downloader by Cheater v1.0 (https://rstforums.com)") print("=====================Choice=========================") print(" Enter '0' : Exit") print(" Enter '1' : Download Album.") print(" Enter '2' : Download PlayList.") print("====================================================") print("All tracks will be download in PCM (MPEG AAC Audio coded, MP4A) at 44100 Hz/16 bits, 320 kbps and stored in MP4 container") choice = myinput("Choice:") if choice == '0': quit() elif choice == '1': downloadAlbum() elif choice == '2': downloadPlaylist() Ce stie sa faca? 1. Poti descarca un album 2. Poti descarca un playlist 3. Adauga melodiile intr-o coada, si le descarca simultan pentru a scurta timpul de asteptare semnificativ. Daca aveti intrebari sau nu va descurcati puteti scrie aici, si va voi ajuta in limita timpului disponibil (adica sper sa nu fie nevoie :))) ). PS: Fiti blanzi cu code review, sunt programator si python nu este specialitatea mea, este al 2-lea script scris in python si prima interactiune am avut-o in decembrie. PS2: Distractie si La multi ani! PS3: Feel free to improve it! Later: Am gasit un tool functional de download scris de altcineva (daca il gaseam mai repede probabil ca nu il mai scriam eu pe asta, deci nu e neaparat bine): https://github.com/redsudo/RedSea acest tool spre deosebire de ce am scris eu, stie de si decripteze flacurile, astfel poate descarca inclusiv MQA de 92k / 24bit (cea mai intalta calitate disponibila pe tidal), si flac 44.1k / 16bit cu un bitrate de 1.411 kbps. Decriptarea nu e rocket sience, dar cu siguranta a fost nevoie de un reverse engineering serios pentru aflarea algoritmului si key de criptare (AES cu key binara, tinuta in base64 in cod).9 points
-
9 points
-
Salut si Hristos a înviat! In ultimele luni am lucrat la un proiect de hosting in România care are ca scop crearea unui nod independent fata de restul datacentrelor din tara, unde noi avem control asupra tuturor aspectelor, de la locație, net, IP-uri, echipamente, servere, routere, switch-uri, UPS-uri, redundanta electrica, răcire si tot ce tine de livrarea unui serviciu la standardele cu care suntem cu toții obișnuiți. Ne puteți vizita site-ul la adresa: https://cloudforest.ro/ Momentan, oferim doua servicii: - Servere private virtuale cloud - Am creat propriul cloud Openstack din infrastructura pe care o avem, interconectata cu porturi de 10Gbps. Avem cam cele mai folosite si recente imagini cloud, configurare automata cu cloud-init, root deblocat și parola generata. Adminisrarea se face web din contul de client cu toate optiunile de care aveti nevoie, consola, chei SSH, rebuild, firewall privat si multe altele. In plus, aveti si un snapshot gratuit pentru fiecare VPS. - Gazduire Servere Jocuri cu panou Pterodactyl, IP dedicat, fara limite de slots si acces nelimitat la procesor. - Gazduire web - clasica, panou de control Virtualmin & certificat ssl automat. Doar schimbati ns-urile domeniului in ns1.cloudforest.ro si ns2.cloudforest.ro - Gazduire web gratuita - la fel de performanta precum gazduirea web normala, insa limitata la 1 domeniu, 1 baza de date si 1 GB stocare Puteți citi mai multe detalii asupra serverelor noastre si întreaga infrastructura aici: Infrastructura Noastra Cat despre politica de utilizare, nu permitem folosirea abuziva a resurselor si a lățimii de banda, si, evident, toleranta este 0 pentru orice fel de activitate ilegala printre care si nu ne limitam la: malware spreading, scanning, botnet hosting, spam, abuzare port 25, orice fel de blackhat usage. Nu avem nicio problema sa raportam/colaboram cu autoritatile.8 points
-
Un sfat prietenesc: Ar trebui sa lasi prostiile pentru ca risti sa-ti futi viitorul. Cand esti conectat la un router, acolo apare adresa MAC + hostname iar in log-uri apar autentificarile esuate. Risti sa fii dat afara din scoala si sa ai si probleme doar pentru ca te joci unde nu trebuie. Pe bune, chiar nu se merita. Joaca-te acasa la tine, in LAN. Fa-ti cateva VM-uri pe virtualbox si iti testezi ce vrei tu. Poti invata multe in timp, inclusiv sa nu alegi cai gresite Ai trei postari aici si toate merg på calea strâmba8 points
-
After a deep security research by Cysource research team led by Shai Alfasi & Marlon Fabiano da Silva, we found a way to execute commands remotely within VirusTotal platform and gain access to its various scans capabilities. About virustotal: The virustotal.com application has more than 70 antivirus scanners that scan files and URLs sent by users. The original idea of the exploration was to use the CVE-2021-22204 so that these scanners would execute the payload as soon as the exiftool was executed. Technical part: The first step was uploading a djvu file to the page https://www.virustotal.com/gui/ with the payload: Virustotal.com analyzed my file and none of the antiviruses detected the payload added to the file's metadata. According to the documentation at the link: https://support.virustotal.com/hc/en-us/articles/115002126889-How-it-works , virustotal.com uses several scans. The application sent our file with the payload to several hosts to perform the scan. On virustotal hosts, at the time that exiftool is executed, according to CVE-2021-22204 inform, instead of exiftool detecting the metadata of the file it executes our payload. Handing us a reverse shell on our machine. After that we noticed that it’s not just a Google-controlled environment, but environments related to internal scanners and partners that assist in the virustotal project. In the tests it was possible to gain access to more than 50 internal hosts with high privileges. Hosts identified within the internal network: The interesting part is every time we uploaded a file with a new hash containing a new payload, virustotal forwarded the payload to other hosts. So, not just we had a RCE, but also it was forwarded by Google's servers to Google's internal network, it customers and partners. Various types of services were found within the networks, such as: mysql, Kubernetes, oracle database, http and https applications, metrics applications, SSH, etc. Due to this unauthorized access, it was possible to obtain sensitive and critical information such as: Kubernetes tokens and certificates, service settings info, source codes, Logs, etc. We reported all the findings to Google that fixed this issue quickly. Disclosure Process: Report received by GoogleVRP - 04.30.2021 GoogleVRP trigged the report - 05.19.2021 GoogleVRP accepted the report as a valid report - 21.05.2021 GoogleVRP closed the report - 04.06.2021 Virustotal was no longer vulnerable - 13.01.2022 GoogleVRP allowed publishing - 15.01.2022 Source: https://www.cysrc.com/blog/virus-total-blog8 points
-
Cum n-am mai deschis un topic aici de multi ani, si am terminat serialele, si n-am somn, m-am gandit sa impartasesc cu voi optimizarile ce le folosesc pentru a imbunatati timpul de raspuns si viteza internetului. Este vorba de setari si configurari ce se aplica routerului, si este necesar ca routerul sa va permita conectarea prin ssh ca root pentru a le aplica. Eu folosesc https://www.synology.com/en-us/products/RT2600ac dar sunt convins ca ca sunt si alti producatori ce au routere cu linux destul de accesibil pentru a implementa optimizarile. Stiu nu e AX, luna viitoare scot cei de la Synology unul AX. Oricum tutorialul se aplica la fel si la AX si AC. Cand apare wifi 6e in Romania, poate fac o continuare. La routerele Synology parola setata la userul Admin, este parola de root. Valorile ce le gasiti in continuare au fost optimizate pentru o viteza maxima permisa de isp de 940Mbps, dar pana la 2.5Gbps nu ar trebui sa fie necesare modificari semnificative. De asemenea puteti aplica aceste setari si pe servere linux vor aduca imbunatatiri semnificative fata de default. 1. /etc/rc.local Este posibil sa nu functioneze configurarile exact asa cum le prezint eu aici pe routerul vostru, de aceeea inainte de a le scrie in fisiere pentru a deveni persistente, faceti setarile la run-time, si adaptatiile daca este necesar, sau omitetile daca nu se aplica la voi (nu aveti binarele respective/variabilele de kernel, ajustati caila catre ele) 2. /etc/sysctl.conf Ca sa aplicati configurarile fara reboot folositi sysctl -p, sau sysctl -w nume_variabila=valoare. Indepartati variabilele daca primiti eroare, unele pot sa lipseasca din versiunea de kernel pe care o aveti. 3. Wifi Alegem canalul: Primul pas este scanarea de spectru, sunt multe aplicatii pentru asta, scopul este sa identificati canalul cel mai putin folosit pe 2.4/5Ghz sau daca este folosit retelele ce emit pe acel canal sa aiba o putere cat mai mica. - pe 2.4Ghz sunt 3 canale ce nu se suprapun (non overlapping channels), 1, 6 si 11, ideal este sa alegem unul dintre acestea. Daca toate sunt libere, alegeti 11. - pe 5Ghz, cautam sa ne ferim de canalele cu DFS obligatoriu, astfel ne orientam catre benziile U-NII-1 si U-NII-3, daca avem noroc sa locuim in US/Canada (sau routerul crede asta), as recomanda canalul 161. Dar cum locuim in Romania si e 5000 lei amenda daca setezi alta tara si mergi pe un canal aiurea (in ideea in care avem vreo UM in apropiere, bruiem ceva, ei fac sesizare la ANCOM si ne bate ANCOM la usa, putin probabil), iar routerul nu ne lasa sa folosim 161 pe Romania, m-as uita la 40-44, daca este liber. Daca ai un router capabil, si intamplator locuiesti in Australia, routerul iti va permite 4W puterea in U-NII-3, cea mai mare din lume acceptata pe wifi, dar majoritatea routerelor suporta ±1W maxim. Channel width: Marimea canalului este importanta, cu cat este mai mare, cu atat incap mai multe date, deci avem viteza mai mare. - pe 2.4Ghz, eu merg pe width de 40Mhz - pe 5Ghz, routerul meu stie sa mearga pe un width de 80+80 Mhz, practic foloseste 2 canale, am ales un canal din U-NII-1 si unul U-NII-3 (cand locuiam in US), ambele cu un width de 80Mhz, bine si deviceurile din caza trebuie sa stie 80+80 Mhz, sau 160Mhz, cel mai probabil suporta doar 80Mhz, ceea ce e good enough oricum. Alte setari: DTIM 4 - mai mic scade viteza si timpul de raspuns, si se consuma mai multa baterie, mai mare e opusul, optimul este 4. Dar puteti face A/B testing si vedeti ce vi se potriveste mai bine. Multicast translation - on AMPDU - on EXTENDED NSS - on U-APSD - off MU-MIMO - on, ideal 4x4, dar si 2x2 ar trebui sa fie suficient. PMF support - off, apare un overhead ciudat si pare buggy, daca la voi se comporta la fel si on si off, e o idee buna sa ii dati on. La fel si WPA 3. IGMP Snooping - on Orice setare de power saving, off! Downgrade usb 3.0 device to reduce interference to 2.4 Ghz signal - on Allow auto-switch to DFS channels - off WPS - off (security) Daca routerul suporta guest, si nu folositi reteaua in mod curent, opriti guest. La criptarea retelei alegeti AES, pentru ca e hw accelerated. Alegeti pe 2.4Ghz N only, si 5Ghz AC/AX only, ca sa va asigurati ca fortati device-urile sa folosesca cele mai rapide protocoale de wifi, daca sunt device ce nu functioneza corect reveniti la o setare mai permisiva. Daca routerul suporta 802.11v aka Smart Connect, puteti, si recomand, sa folositi acelasi nume si la 2.4Ghz si la 5Ghz si routerul va negocia protocolul cel mai bun suportat de device, tinand cont si de calitatea semnalului pentru a avea cea mai buna acoperire si un plus de simplitate. + Folositi un doh dns, daca suporta routerul, sau macar un cloudflare dns, are datacenter si la otopeni si peers locale - https://1.1.1.1/dns/ . Firewall: Mtu probing se foloseste de icmp (ping), pentru a identifica valoarea optima, astfel este important sa acceptati icmp pe ipv4 si ipv6. Blocati orice port ce nu are ce cauta in afara, eu de exemplu, prefer sa folosesc un port non-default pentru vpn server, din care mai apoi sa am access la interfata routerului si alte chestii. Locatia fizica: Recomand sa identificati locul de unde, din pozitia routerului puteti vedea usile la toate camerele (sau cat mai multe), un hol, sa va asigurati ca nu sunt obstacole (pereti mai ales de beton, frigider, etc..) in jurul routerului, este ideal sa fie situat la o inaltime de 2m, prins pe perete (preferabil), daca folositi wifi cu precadere dintr-o anumita camera cautati o pozitie cat mai aproape de camera care sa respecte cele de mai sus. Daca pui routerul sub pat, de sub pat o sa ai putere maxima :))). Este adevarat ca semnalul ocoleste/trece prin obstacole doar ca fiecare obstacol scade semnificativ puterea, daca punem routerul pe jos, in mod automat va intalni semnificativ mai multe obstacole, si daca prin dreptul lui trec persoane, o sa apara spike-uri, nu ne dorim asta, de aceea inaltimea de 2m este optima. Performante obtinute: Inainte de a face aceste optimizari aveam 300-400 mbps, cu spike-uri mari. Dupa, am 650-666 pe orice device Apple mai nou de 2019 (testat cu: iPhone X, 12, MacBook Pro 16'' M1 pro/M1 max), si 800-900 Mbps pe deviceuri Apple 2017-2019 (chiar 2014) (testat cu: MacBook Pro 16'' 2014, 2019, Intel-based), au pus placi de retea mai slabe pe 5Ghz cu 2/mimo in loc de 3 cum era pana in 2019 pe device recente, probabil ca sa faca o economie de baterie/de cost de productie, naiba stie. https://support.apple.com/ro-ro/guide/deployment/dep2ac3e3b51/web Cert este ca routerul duce mai mult decat deviceurile ce le folosesc. Daca routerul este capabil AX la 2 mimo atat pe partea de router cat si de client estimez o viteza de 750-800Mbps, ceea ce e destul de bine. Update, screenshoot facut din qbittorrent, de pe un MBP M1 Pro, pe WIFI: Sper sa va fie de folos! Have fun! PS: daca am facut vreo greseala, o sa o corectez zilele urmatoare, am inceput sa scriu la 23 si e 038 points
-
Consumati curent, poluati si ucideti balenele si ursii polari. Huooo, pacatosilor 🤣8 points
-
N-ai aflat inca secretul hackerilor independenti si plini de bani? Link.8 points
-
8 points
-
Nu va asteptati la prea multe de la asa ceva, aici e cam tot ce face; https://github.com/zigoo0/webpwn3r/blob/master/vulnz.py Mai exact trimite cateva request-uri sa verifice cateva lucruri simple. Eu am un tool privat: ./nytro --hack ISS Hacking in progress... Getting satellite communication working... Scanning ISS... Found open ports: 69, 1337 Sending 5G payload to COVID-19 port... Hacking complete! Getting root... Got root! Dar va dati seama ca nu il pot publica...8 points
-
"-m conntrack --ctstate NEW" Deci ala trimite pachete si tu le arunci pe conntrack. E ca si cum ar da tiganii cu pietre dupa tine si tu ai sta sa le numeri8 points
-
După ce faceți muncă pe 2 lei, mai luați și țeapă. Bravo, așa meritați.8 points
-
8 points
-
8 points
-
Iar mizeria asta ma oamenilor? - https://rstforums.com/forum/topic/109240-carti-alex-david/ - https://rstforums.com/forum/topic/107863-ghid-cum-sa-ti-recastigi-iubita-de-alex-david/ - https://rstforums.com/forum/topic/102896-carti-de-la-alex-david/ - https://rstforums.com/forum/topic/95847-caut-carte-de-alex-david/ - https://rstforums.com/forum/topic/81112-are-cineva-cartea-cum-să-vorbeşti-cu-o-femeie-alex-david/ - https://rstforums.com/forum/topic/92201-cerere-carti-sarut-o-si-stai-drept/ - https://rstforums.com/forum/topic/89336-cerere-carte-cum-sa-vorbesti-cu-o-femeie/ Daca te uiti pe google si cauti "Alex David carte site:rstforums.com" te ingrozesti. E simplu, vorbesti frumos. DON'T BE A DICK. Si sa-i dai limbi! :))))))8 points
-
8 points