-
Posts
3206 -
Joined
-
Days Won
87
Posts posted by Fi8sVrs
-
-
Cum gratis, daca omul ofera premii, si cazino renumit.. spor la treaba baietii
-
 1
1
-
-
Nu il mai foloseste nimeni, va spun sigur, am acces la mail, numai face up aruba
-
1 hour ago, wHoIS said:
Sa inteleg ca nu am pus solutia corecta?
Tu ce solutie ai ?
Inurl din pacate nu am pe ce lucra mometan, sau insite:
Edit, il gasesc oricum
Edit2: hahaha ne transmite sarbatori fericite
Edit3: pe 1 si 8 sunt ale lor cu ghioceii vietii, pe cand iesim la baut?
-
Toti comentatori, postati solutia, numai faceti troll
-
Gasiti ultimele 3 caractere ce lipsesc din url si primiti,, tricouri, sepci, etc:
https://youtu.be/cZ4QYk3N ???
Succes
Edit (era sa uit) rezolvarea prin pm
Solvers:
.wHoIS
.
...
-
 1
1
-
-
E clean bro, doar yandex il gaseste
-
Produse pt bebelusi, biberoane etc...
Edit, si in spot-uri sunt utilizate
-
12 minutes ago, aismen said:
Eu nu sunt asa de prost. Sa ma iei de boase.
Stiu man, era pamflet
Edit// ideea este, nu arunca nimeni in aer cum vor ei, cheile le detin numai capitanii
-
27 minutes ago, ARUBA said:
Nu am acuzat pe nimeni. Un abonament costa 70 de ron pe luna, iar conditiile de calatorie sunt mult, mult mai bune decat in alte tari civilizate unde costurile sunt mult mai mari.
Sunt pt teste post hunting
On:trimite-mi pm cu screenshot, please, pare cunoscut
-
CVE-2018-10933 libssh authentication bypass, a vulnerable Docker container that listens on port 2222 for exploitation. A basic proof-of-concept libssh patch included in the container to bypass auth. To login use the default "myuser" / "mypassword" from libssh. A patch is applied to a copy of libssh in the Docker container which injects a SSH2_MSG_USERAUTH_SUCCESS packet during any authentication (keyboard-interactive / pubkey / gss-api etc.) attempt and sets the client side state to proceed. The included server has been patched from example code to allow exploitation to succeed.
./build.sh ./run.sh ssh -l myuser -p 2222 localhost
A patched exploit-libssh-0.8.3 and vulnerable sshd are available in the container for testing purposes. The "ssh-client" will successfully bypass authentication but is unable to spawn a shell against the default example server due to additional authentication checks in the server code.
[root@305b48cb932e ]# cd /root/exploit-libssh-0.8.3/build/examples [root@305b48cb932e examples]# ./ssh-client -l root 127.0.0.1 The server is unknown. Do you trust the host key (yes/no)? SHA256:Mg6j2yHWMsRe56ABhAYjLIJK9yD2N3lGQAl3EfGqP7w yes This new key will be written on disk for further usage. do you agree ? yes Requesting shell : Channel request shell failed [root@305b48cb932e examples]#
-
NOTE:
This tool has been re-written to run on Kali (2018.1)
DEPENDENCIES:apt-get install qt4-dev-tools
TODO:Add a updater for the tool.
Add a WPS tab + support for WPS cracking (Reaver / Bully, or support for both)
Consider renaming the project?
Change deprecated "iwconfig" with the use of "iw"
Consider adding "hashcat" GPU cracking option.
WPA handshake capture is slow, considering enhancement to it. wifite2 got a VERY FAST handshake capturing method, consider using that code.
Fix new graphics.
LAUNCH:
To launch the program use: $ python gerix.py
Enjoy!
NOTE: For copy and paste in xterm windows you can use the shortcuts CTRL-INS and SHIFT-INS. In alternative, you can select the text with the mouse, and use the third button of the mouse to paste it. On a laptop you can emulate the third button pressing the first and the second button together.
Source:
https://github.com/kimocoder/gerix-wifi-cracker/blob/master/README.md
-
 1
1
-
-
1 hour ago, ARUBA said:
Postezi in gunoaie gunoierule, acum am observat, nu mai face up (post hunting)
13h de atunci, sunt obosit de la conf
-
E analog si digital, asta e aismen sigur, bashed
-
WPML, a module that allows running fully multilingual websites with WordPress, making it easy to translate WordPress pages, posts, tags, categories and themes was recently hacked by an unhappy employee. According to this page: https://wpml.org/home/about-us/, WPML is running on more than 600 000 websites. There are almost 1 million compromised accounts on the WPML website.
Below you can see a message that was sent to all WPML clients in 20 January 2019.
Quote
,
We’re very sorry to report that our website got hacked. The evidence that we have points to an ex-employee who planted a backdoor before leaving the company.
That attacker did the following:
Copied the names and emails of our clients
Sent a mass email on our behalf
Defaced our purchase page and added a fake blog post
We’re very sorry that we allowed this to happen. We’ll take a lot more precaution when others leave the company in the future. Of course, some of our employees have access to sensitive material and we trust them to use it wisely.
Is there an exploit in WPML plugin?
The attacker did not modify the code in WPML plugins. We double checked right now and we can confirm that the ZIP files that you are downloading from us were not tampered with.
Was payment information compromised?
No. We don’t store payment information on our server. We use PayPal and Stripe for payment processing and they store the payment details. When you buy from us, we don’t ever see your credit card number.
Is my WPML account compromised?
Possibly. The attacker gained access to all client names and emails and may be able to login to your account. This will allow the attacker to pose as you on wpml.org.
Please log-in and change your password.
What’s WPML team doing about this hack?
We’re rebuilding the server from scratch, resetting all passwords and locking down everything. Since the intruder had access to the server, we can’t tell what other holes there are, so we’re building the site from scratch. This will take us until tomorrow morning.
We’ll write again once our site is secured again. Again, we’re very sorry for having lost your name and email to this intruder. Besides fixing the site, we’ll also take legal action.
– Amirrecommend that everyone who has accounts on WPML.com should change urgently his / her password. At this moment the wordpress wpml plugins are not affected by this hack, but your account data from WPML is compromised. If you are using the same password on other websites we recommend to set a different password there too. Make sure to update all your WordPress plugins in order to prevent upcoming plugin hacks.
Via
http://www.hackingnews.com/breaking-news/wpml-org-website-was-hacked-what-you-need-to-know/
-
-
 1
1
-
-
8 hours ago, aismen said:
Uite un total pe ce am cheltuit eu:
RPi3 - 163 lei
Carcasa SNES - 125 lei (include și transport din SUA)
Încărcător - 20 lei
Ventilator - 5 lei
Controller XBOX Wireless - 180 lei
Cablu HDMI - 30 lei
Card SD SDHC Class 10 16GB - 60 lei parcă
Total: 583 lei. Se poate să fi cheltuit și mai mult. Ideea este că dacă vrei să faci această investiție ar trebui chiar să îți placă.
Sunt kituri la 38, $40 canadieni, depinde..
//am gasit kit pi3 b+ la $80 ca, depinde ce xauti
-
 1
1
-
-
VC4CL is an implementation of the OpenCL 1.2 standard for the VideoCore IV GPU (found in all Raspberry Pi models).
The implementation consists of:
The VC4CL OpenCL runtime library, running on the host CPU to compile, run and interact with OpenCL kernels.
The VC4C compiler, converting OpenCL kernels into machine code. This compiler also provides an implementation of the OpenCL built-in functions.
The VC4CLStdLib, the platform-specific implementation of the OpenCL C standard library, is linked in with the kernel by VC4CSource: https://github.com/doe300/VC4CL/blob/master/Readme.md
-
 1
1
-
-
https://www.instructables.com/id/20-Portable-Raspberry-Pi-Game-Console/
Pentru Raspberry ieftin, filtreaza pret crescator
-
 1
1
-
-
-
In most organisations using Active Directory and Exchange, Exchange servers have such high privileges that being an Administrator on an Exchange server is enough to escalate to Domain Admin. Recently I came across a blog from the ZDI, in which they detail a way to let Exchange authenticate to attackers using NTLM over HTTP. This can be combined with an NTLM relay attack to escalate from any user with a mailbox to Domain Admin in probably 90% of the organisations I’ve seen that use Exchange. This attack is possible by default and while no patches are available at the point of writing, there are mitigations that can be applied to prevent this privilege escalation. This blog details the attack, some of the more technical details and mitigations, as well as releasing a proof-of-concept tool for this attack which I’ve dubbed “PrivExchange”.
Read more s-ar incadra la tutoriale, cautati sursa dupa titlu, ceva cu .io
Edit: https://dirkjanm.io/abusing-exchange-one-api-call-away-from-domain-admin/
-
 1
1
-
 1
1
-
-
I love you ❤️
-
 1
1
-
-
This tool was created during our research at Checkpoint Software Technologies on Whatsapp Protocol.
Here is the link to our blog post: https://research.checkpoint.com/fakesapp-a-vulnerability-in-whatsapp/
The Extension:
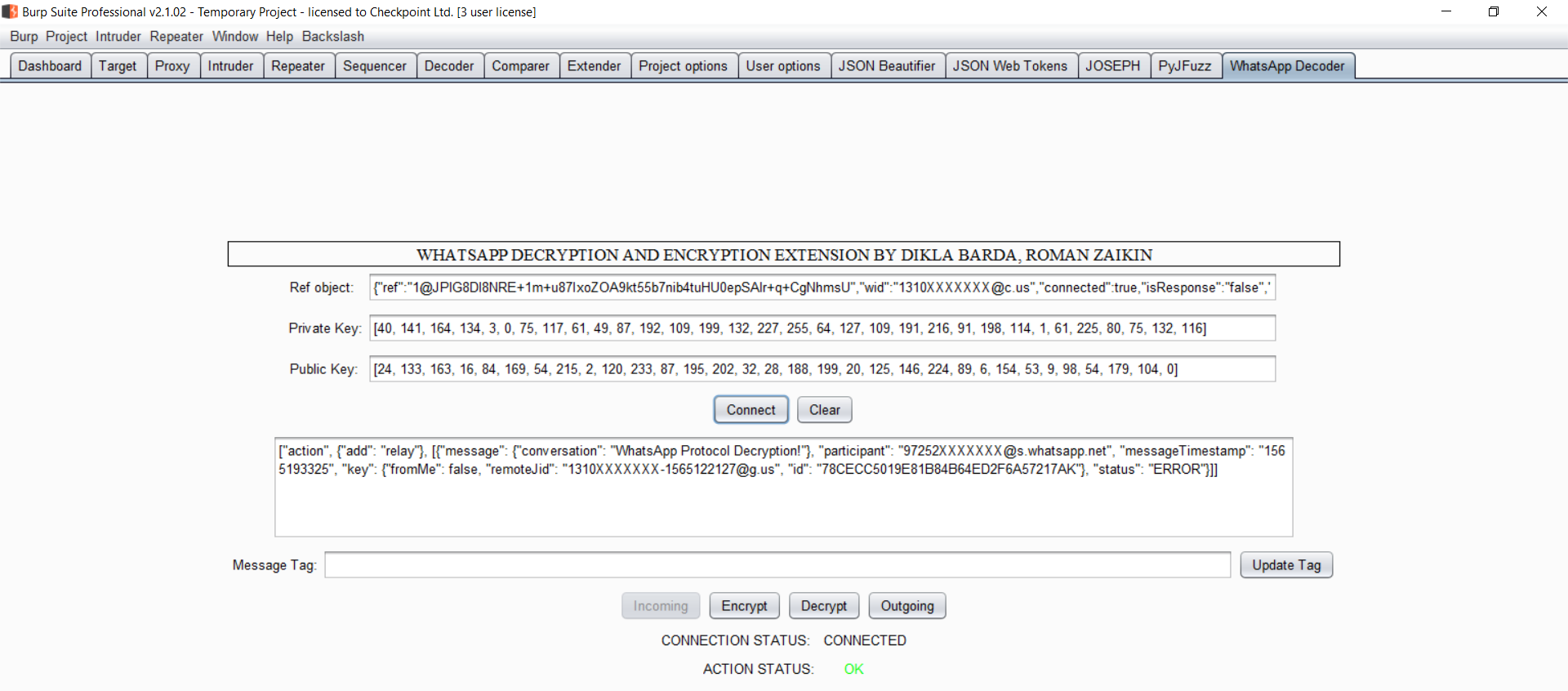
Source: https://github.com/romanzaikin/BurpExtension-WhatsApp-Decryption-CheckPoint
-
 2
2
-
-
2014 tc
-
 1
1
-
-
16 minutes ago, ARUBA said:
@Bissy121 Scrie IMEI-ul aici, poate ma ajuta si pe mine OKQL sa-mi gasesc laptop-ul.
Ajuta-te singur
-
 1
1
-





Fun stuff
in Discutii non-IT
Posted
Sa tot ai asa prof
https://m.facebook.com/story.php?story_fbid=1739838822809785&id=313227042137369