-
Posts
27 -
Joined
-
Last visited
-
Days Won
4
Posts posted by dannybest
-
-
BoomER | An Open Source Post-Exploitation Tool To Exploit Local Vulnerabilities
BoomER is an open source framework, developed in Python. The tool is focused on post-exploitation, with a main objective, the detection and exploitation of local vulnerabilities, as well as the collection of information from a system, such as the installed applications they have.
The framework allows the extension by third parties, through the development of modules, for it the developers must follow certain guidelines, among which the following stand out:
• Type of inheritance
• Methods or functions to be implemented
• Required or new parameters
• Module name
• Location of the module within the framework
We wanted to give the tool a relationship with Metasploit, as it is the reference framework for pentesters, so from BoomER it is possible to open sessions in Metasploit.
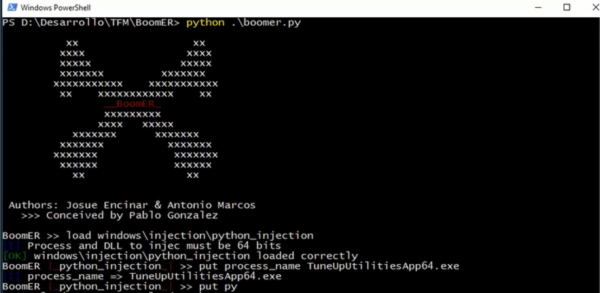
To use BoomER, you should use command line, it is very similar to the tools that currently exist for the detection and exploitation of vulnerabilities, which helps to reduce the learning curve.
An example for DLL injection:
Our own meterpreter (based on Metasploit):
Example Videos
Metasploit + BoomER - Linux Privilege Escalation
Python script + DLL Injection with BoomER
BoomER - macOS Privilege Escalation
-
 1
1
-
-
mai bine pune mana si invata

-
 1
1
-
-
Facebook Launches Pysa – Instagram Security Tool – As Open Source
Pyre is a performant type checker for Python compliant with PEP 484. Pyre can analyze codebases with millions of lines of code incrementally – providing instantaneous feedback to developers as they write code.
Pyre ships with Pysa, a security focused static analysis tool we've built on top of Pyre that reasons about data flows in Python applications. Please refer to our documentation to get started with our security analysis.
Requirements
To get started, you need Python 3.6 or later and watchman working on your system. On MacOS you can get everything with homebrew:
$ brew install python3 watchman
On Ubuntu, Mint, or Debian; use
apt-get:$ sudo apt-get install python3 python3-pip watchman
We tested Pyre on Ubuntu 16.04 LTS, CentOS 7, as well as OSX 10.11 and later.
Setting up a Project
We start by creating an empty project directory and setting up a virtual environment:
$ mkdir my_project && cd my_project $ python3 -m venv ~/.venvs/venv $ source ~/.venvs/venv/bin/activate (venv) $ pip install pyre-check
Next, we teach Pyre about our new project:
(venv) $ pyre init
This command will set up a configuration for Pyre (
.pyre_configuration) as well as watchman (.watchmanconfig) in your project's directory. Accept the defaults for now – you can change them later if necessary.Running Pyre
We are now ready to run Pyre:
(venv) $ echo "i: int = 'string'" > test.py (venv) $ pyre ƛ Found 1 type error! test.py:1:0 Incompatible variable type [9]: i is declared to have type `int` but is used as type `str`.
This first invocation will start a daemon listening for filesystem changes – type checking your project incrementally as you make edits to the code. You will notice that subsequent invocations of
pyrewill be faster than the first one.For more detailed documentation, see https://pyre-check.org.
Join the Pyre community
See CONTRIBUTING.md for how to help out.
License
Pyre is licensed under the MIT license.
-
 1
1
-
-
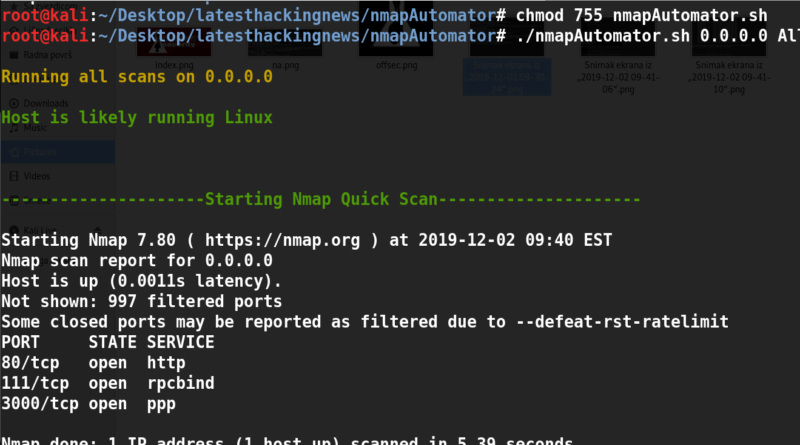
Nmap Automator – a tool I used during OSCP for simple recon Attribution
nmapAutomator
A script that you can run in the background!
Summary
I have created this script as I was preparing for my OSCP exam.
The main goal for this script is to automate all of the process of recon/enumeration that is run every time, and instead focus our attention on real pen testing.This will ensure two things:
1) Automate nmap scans. 2) Always have some recon running in the background.Once you find the inital ports in around 10 seconds, you then can start manually looking into those ports, and let the rest run in the background with no interaction from your side whatsoever.
Features:
- Quick: Shows all open ports quickly (~15 seconds)
- Basic: Runs Quick Scan, then runs a more thorough scan on found ports (~5 minutes)
- UDP: Runs "Basic" on UDP ports (~5 minutes)
- Full: Runs a full range port scan, then runs a thorough scan on new ports (~5-10 minutes)
- Vulns: Runs CVE scan and nmap Vulns scan on all found ports (~5-15 minutes)
- Recon: Runs "Basic" scan "if not yet run", then suggests recon commands "i.e. gobuster, nikto, smbmap" based on the found ports, then prompts to automatically run them
- All: Runs all the scans consecutively (~20-30 minutes)
I tried to make the script as efficient as possible, so that you would get the results as fast as possible, without duplicating any work.
Feel free to send your pull requests and contributions

Requirements:
Required: Gobuster v3.0 or higher, as it is not backward compatible.
You can update gobuster on kali using:apt-get update apt-get install gobuster --only-upgrade
Other Recon tools used within the script include:
Examples of use:
./nmapAutomator.sh <TARGET-IP> <TYPE> ./nmapAutomator.sh 10.1.1.1 All ./nmapAutomator.sh 10.1.1.1 Basic ./nmapAutomator.sh 10.1.1.1 Recon
If you want to use it anywhere on the system, create a shortcut using:
ln -s /PATH-TO-FOLDER/nmapAutomator.sh /usr/local/bin/TODO features list
pull requests are more than welcome

- Support DNS resolution "use of urls/domains instead of IPs"
- Properly identify url extensions "testing index extensions for code 200"
- Add more port-based automatic recon options
- Add an nmap progress bar
-
 3
3
-
EntynetHackerTools ™ (Ehtools Framework) - Official Link
███████╗██╗ ██╗████████╗ ██╔════╝██║ ██║╚══██╔══╝ █████╗ ███████║ ██║ ██╔══╝ ██╔══██║ ██║ ███████╗██║ ██║ ██║ ╚══════╝╚═╝ ╚═╝ ╚═╝ The Ehtools Framework By Ehtools Team entynetproject.simplesite.com ehtools.proDetails
About ehtools framework
INFO: Wi-Fi tools keep getting more and more accessible to beginners, and the Ehtools Framework is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize. -
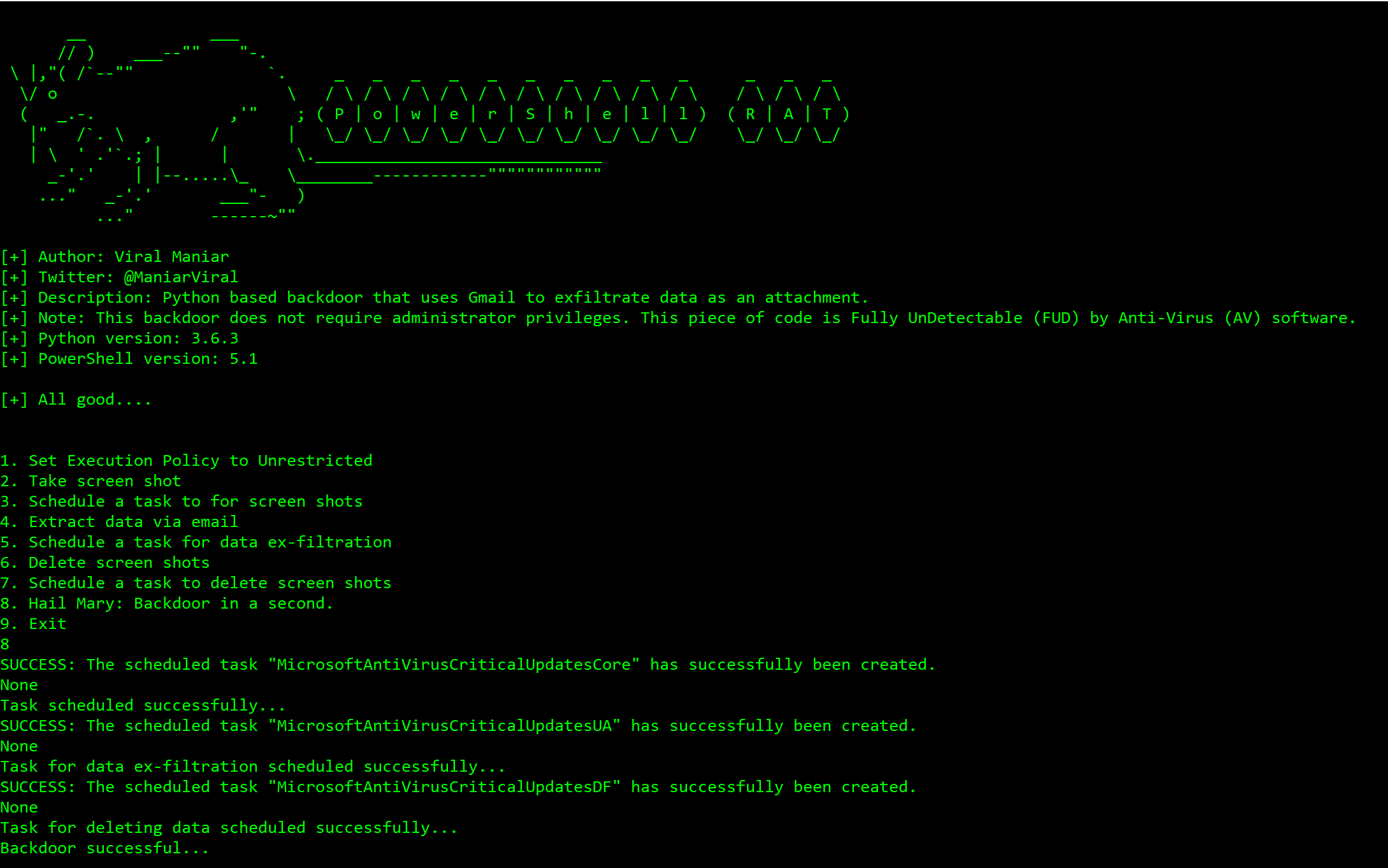
Powershell-RAT - Official Link
Python based backdoor that uses Gmail to exfiltrate data as an e-mail attachment.
This RAT will help someone during red team engagements to backdoor any Windows machines. It tracks the user activity using screen capture and sends the information to an attacker as an e-mail attachment.
Note: This piece of code is Fully UnDetectable (FUD) by Anti-Virus (AV) software.
This project must not be used for illegal purposes or for hacking into system where you do not have permission, it is strictly for educational purposes and for people to experiment with.
Any suggestions or ideas for this tool are welcome - just tweet me on @ManiarViral
RAT Architecture Diagram
Screenshot
On the first run of the
Powershell-RATuser will get options as below:Using
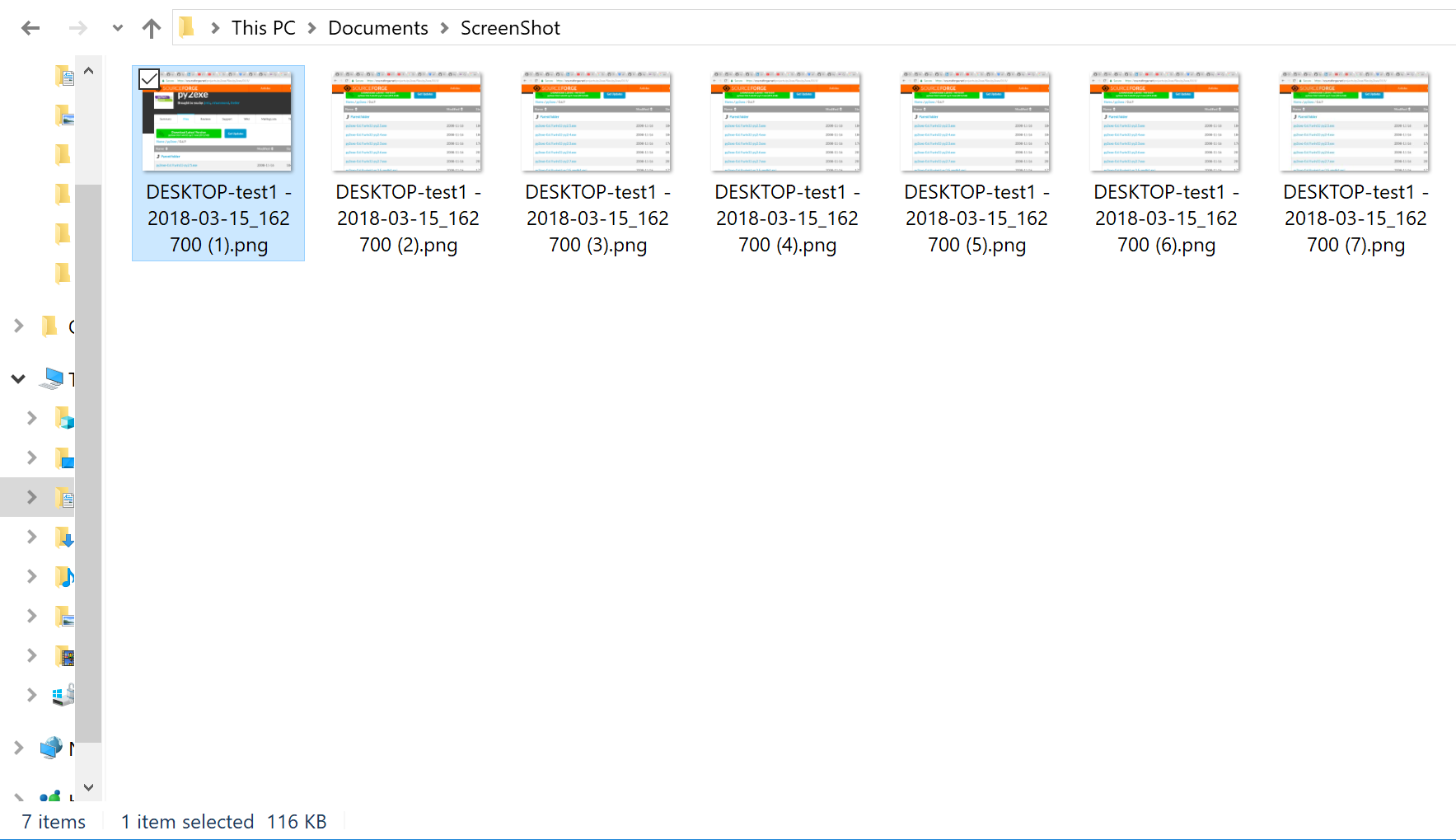
Hail Maryoption to backdoor a Windows machine:Successfully taking screenshots of the user activity:
Data exfiltrated as an email attachment using Gmail:
-
 1
1
-
-
PyRDP - Official Link
PyRDP is a Python 3 Remote Desktop Protocol (RDP) Man-in-the-Middle (MITM) and library.
It features a few tools:
-
RDP Man-in-the-Middle
- Logs credentials used when connecting
- Steals data copied to the clipboard
- Saves a copy of the files transferred over the network
- Saves replays of connections so you can look at them later
- Run console commands or PowerShell payloads automatically on new connections
-
RDP Player:
- See live RDP connections coming from the MITM
- View replays of RDP connections
- Take control of active RDP sessions while hiding your actions
- List the client's mapped drives and download files from them during active sessions
-
RDP Certificate Cloner:
- Create a self-signed X509 certificate with the same fields as an RDP server's certificate
We have used this tool as part of an RDP honeypot which records sessions and saves a copy of the malware dropped on our target machine.
PyRDP was first introduced in a blogpost in which we demonstrated that we can catch a real threat actor in action. In May 2019 a presentation by its authors was given at NorthSec and two demos were performed. The first one covered credential logging, clipboard stealing, client-side file browsing and a session take-over. The second one covered the execution of cmd or powershell payloads when a client successfully authenticates. In August 2019, PyRDP was demo'ed at BlackHat Arsenal (slides).
-
 2
2
-
RDP Man-in-the-Middle
-
AsyncRAT - Official Link
AsyncRAT is a Remote Access Tool (RAT) designed to remotely monitor and control other computers through a secure encrypted connection
Included projects
This project includes the following
- Access terminal for controlling clients
- Configurable client manageable via Terminal
- Log server recording all significant events
Features Include:
- Client screen viewer & recorder
- Client Antivirus & Integrity manager
- Client SFTP access including upload & download
- Client & Server chat window
- Client Dynamic DNS & Multi-Server support (Configurable)
- Client Password Recovery
- Client JIT compiler
- Client Keylogger
- Client Anti Analysis (Configurable)
- Server Controlled updates
- Client Antimalware Start-up
- Server Config Editor
- Server multiport receiver (Configurable)
- Server thumbnails
- Server binary builder (Configurable)
- Server obfuscator (Configurable)
- And much more!
-
24 minutes ago, Lokko said:
Bro, this link is to SpyNote in mega, check this issue, please!
Tksmy bad, I updated the link
-
// solved
-
Deep Exploit - Official Link
Fully automatic penetration test tool using Deep Reinforcement Learning.
Presentation
- February 17th,2018: SECCON YOROZU 2018
- August 9th,2018: Black Hat USA 2018 Arsenal
- August 10th,2018: DEF CON 26! AI Village
- October 24th,2018: CSS2018
- November 3rd,2018: AV TOKYO 2018 Hive
- December 6th,2018: Black Hat EURO 2018 Arsenal
Cooperation
Demonstration
See the demo page.
Documentation (Installation, Usage)
See the project's wiki for installation, usage and changelog.
Overview
DeepExploit is fully automated penetration test tool linked with Metasploit.
DeepExploit identifies the status of all opened ports on the target server and executes the exploit at pinpoint using Machine Learning. It's key features are following.
-
Efficiently execute exploit.
DeepExploit can execute exploits at pinpoint (minimum 1 attempt) using Machine Learning. -
Deep penetration.
If DeepExploit succeeds the exploit to the target server, it further executes the exploit to other internal servers. -
Self-learning.
DeepExploit can learn how to exploitation by itself (uses Reinforcement Learning).
It is not necessary for humans to prepare learning data. -
Learning time is very fast.
Generally, reinforcement learning takes a lot of time.
So, DeepExploit uses distributed learning by multi agents.
We adopted an advanced machine learning model called A3C. -
Powerful intelligence gathering
To gather the information of software operated on the target server is very important for successful the exploitation. DeepExploit can identify product name and version using following methods.- Port scanning
- Machine Learning (Analyze HTTP responses gathered by Web crawling)
- Contents exploration
Abilities of "Deep Exploit".
Current DeepExploit's version is a beta.
But, it can fully automatically execute following actions:- Intelligence gathering.
- Threat modeling.
- Vulnerability analysis.
- Exploitation.
- Post-Exploitation.
- Reporting.
Your benefits.
By using our DeepExploit, you will benefit from the following.
For pentester:
(a) They can greatly improve the test efficiency.
(b) The more pentester uses DeepExploit, DeepExploit learns how to method of exploitation using machine learning. As a result, accuracy of test can be improve.For Information Security Officer:
(c) They can quickly identify vulnerabilities of own servers. As a result, prevent that attackers attack to your servers using vulnerabilities, and protect your reputation by avoiding the negative media coverage after breach.Since attack methods to servers are evolving day by day, there is no guarantee that yesterday's security countermeasures are safety today. It is necessary to quickly find vulnerabilities and take countermeasures. Our DeepExploit will contribute greatly to keep your safety.
-
 4
4
-
Introduction
Maltrail is a malicious traffic detection system, utilizing publicly available (black)lists containing malicious and/or generally suspicious trails, along with static trails compiled from various AV reports and custom user defined lists, where trail can be anything from domain name (e.g.
zvpprsensinaix.comfor Banjori malware), URL (e.g.hXXp://109.162.38.120/harsh02.exefor known malicious executable), IP address (e.g.185.130.5.231for known attacker) or HTTP User-Agent header value (e.g.sqlmapfor automatic SQL injection and database takeover tool). Also, it uses (optional) advanced heuristic mechanisms that can help in discovery of unknown threats (e.g. new malware).-
 1
1
-
-

ManaTI Project - Official Link
Machine Learning for Threat Intuitive Analysis
The goal of the ManaTI project is to develop machine learning techniques to assist an intuitive threat analyst to speed the discovery of new security problems. The machine learning will contribute to the analysis by finding new relationships and inferences. The project will include the development of a web interface for the analyst to interact with the data and the machine learning output.
This project is partially supported by Cisco Systems. For more information about the project please go to Stratosphere Lab page
-
 2
2
-
-
Emagnet is a very powerful tool for it's purpose wich is to capture email addresses and passwords from leaked databases uploaded on pastebin. It's almost impossible to find leaked passwords when they are out of list on pastebin.com. Either they have been deleted by pastebin's techs or the uploads is just one in the crowd. To be honest it's easier to find a needle in a haystack then find outdated uploads on pastebin with the data we want to collect.
Demo - How it works
Left side is how you see it - Right side is what actually happening in the background
Of course everything getting stored to log dir (Filtered email addresses)
-
 1
1
-
-
DOWNLOAD (ATENTIE, POATE FI VAZUT CA SI VIRUS)
Saefko (SAS) is the first known multi-protocol remote administration tool that targets multiple operating systems. In this example the author created a modular-style botnet that connects with the remote system initially via HTTP. Using this HTTP connection the client can send commands, or establish an IRC connection with the remote machine. The IRC servers will switch every 21 minutes for extra-security, on top of the messages being encrypted. You can use IRC or HTTP to establish a TCP connection in which you can call on much more features.
-
 1
1
-
-
AVETI GRIJA, PE VIRUSTOTAL ESTE GASIT CA SI VIRUS (redirect catre VirusTotal) !!! de testat pe virtual machine.
Spy Note is a free advanced Remote Administration Tool targeted for Android systems. It’s server is written in Java, and the client controller is written in Visual Basic .NET. After installation on an Android device, Spy Note will automatically remove it’s on-screen icon from the victim’s device.
Spy Note’s essence is a kind of Trojan generator with some quite attractive features. It was popular in the deep web when first released, since being leaked it has become more popular.
As a tool designed for remotely monitoring and controlling Android system/device. When comparing to competitor software (such as: OmniRAT, DroidJack, Dendroid), SpyNote will always come out on top. While there are simply a lot options and better stability across all Android versions..
As the version upgrades, the features of Spy Note become increasingly powerful, and bring more serious harm to victims. Although Spy Note now seems to have no large-scale use by hackers around the world, today anyone can download it for free.
-
 1
1
-
-
airgeddon - Official Link
This is a multi-use bash script for Linux systems to audit wireless networks.
-
 1
1
-
-
-
 2
2
-
-
Invisi-Shell - Official Link
Hide your powershell script in plain sight! Invisi-Shell bypasses all of Powershell security features (ScriptBlock logging, Module logging, Transcription, AMSI) by hooking .Net assemblies. The hook is performed via CLR Profiler API.
Work In Progress
This is still a preliminary version intended as a POC. The code works only on x64 processes and tested against Powershell V5.1.
Usage
- Copy the compiled InvisiShellProfiler.dll from /x64/Release/ folder with the two batch files from the root directory (RunWithPathAsAdmin.bat & RunWithRegistryNonAdmin.bat) to the same folder.
- Run either of the batch files (depends if you have local admin privelledges or not)
- Powershell console will run. Exit the powershell using the exit command (DON'T CLOSE THE WINDOW) to allow the batch file to perform proper cleanup.
-
 1
1
-
What is a CMS?
A content management system (CMS) manages the creation and modification of digital content. It typically supports multiple users in a collaborative environment. Some noteable examples are: WordPress, Joomla, Drupal etc.
Functions Of CMSeek:
- Basic CMS Detection of over 170 CMS
- Drupal version detection
-
Advanced Wordpress Scans
- Detects Version
- User Enumeration
- Plugins Enumeration
- Theme Enumeration
- Detects Users (3 Detection Methods)
- Looks for Version Vulnerabilities and much more!
-
Advanced Joomla Scans
- Version detection
- Backup files finder
- Admin page finder
- Core vulnerability detection
- Directory listing check
- Config leak detection
- Various other checks
-
Modular bruteforce system
- Use pre made bruteforce modules or create your own and integrate with it
-
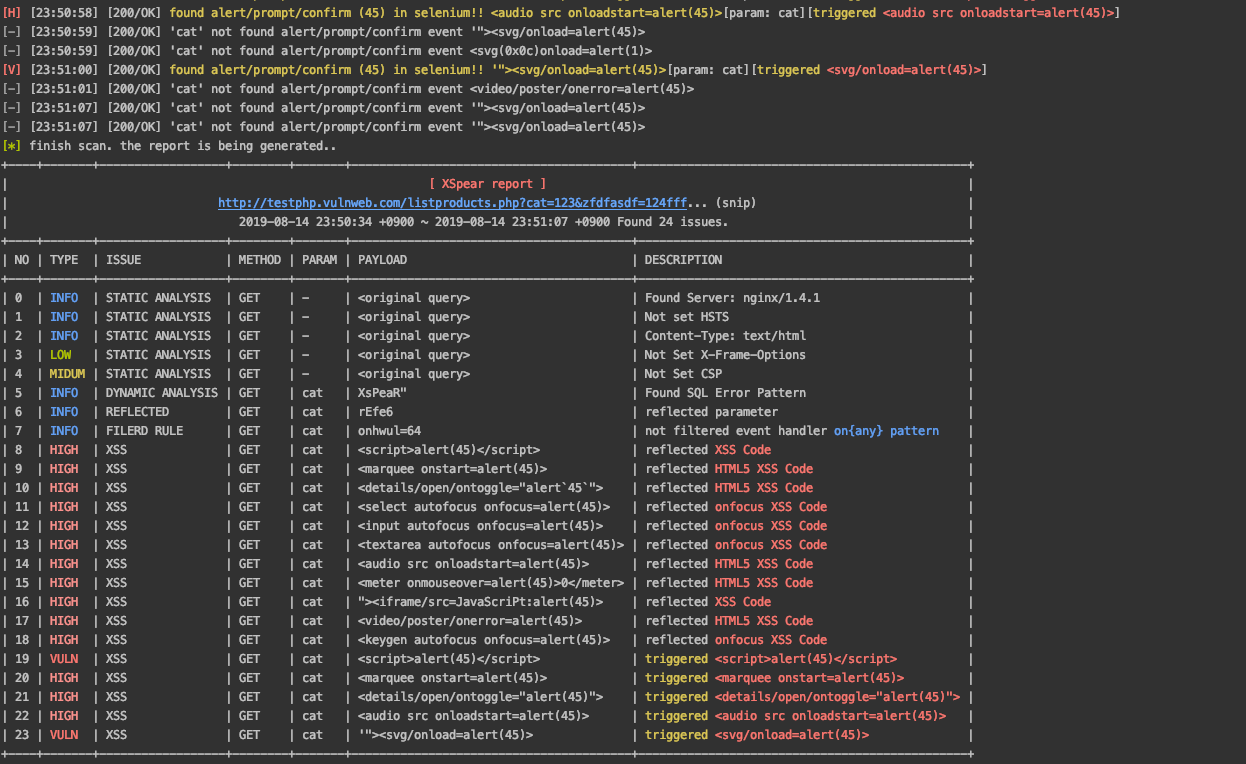
XSpear - Official Link
Key features
- Pattern matching based XSS scanning
-
Detect
alertconfirmpromptevent on headless browser (with Selenium) -
Testing request/response for XSS protection bypass and reflected params
- Reflected Params
-
Filtered test
event handlerHTML tagSpecial CharUseful code
- Testing Blind XSS (with XSS Hunter , ezXSS, HBXSS, Etc all url base blind test...)
-
Dynamic/Static Analysis
- Find SQL Error pattern
-
Analysis Security headers(
CSPHSTSX-frame-options,XSS-protectionetc.. ) - Analysis Other headers..(Server version, Content-Type, etc...)
- Scanning from Raw file(Burp suite, ZAP Request)
- XSpear running on ruby code(with Gem library)
-
Show
table base cli-reportandfiltered rule,testing raw query(url) - Testing at selected parameters
-
Support output format
clijson- cli: summary, filtered rule(params), Raw Query
- Support Verbose level (quit / nomal / raw data)
- Support custom callback code to any test various attack vectors
ScreenShot
-
Just now, Nytro said:
Nu stiu despre aceasta versiune, insa in trecut au existat astfel de keygen-uri pentru Burp infectate. Eu recomand sa dati 300 de EURO pe aplicatie, pentru ca merita.
Si da si nu
 in idea ca esti incepator ca mine, te poti juca cu asta crack-uit. Cand esti mai "doxa" si probabil castigi si din asta, merita cumparat.
in idea ca esti incepator ca mine, te poti juca cu asta crack-uit. Cand esti mai "doxa" si probabil castigi si din asta, merita cumparat.
-
Salut baieti, sunt nou in comunitatea asta de security, momentan invat web pentest si am sa incerc sa vin in ajutor cu fel si fel de tool-uri pe care le gasesc si le si folosesc. Momentan am venit cu Burp Suite Pro.
Burp Suite Pro 2.0.06 beta Loader & Keygen
(works for all Burp Suite Pro versions up to 2.0.11 included!!)
Burp Suite is the leading software for web security testing. Thousands of organizations use Burp Suite to find security exposures before it’s too late. By using cutting-edge scanning technology, you can identify the very latest vulnerabilities. Our researchers frequently uncover brand new vulnerability classes that Burp is the first to report.
What is Burp Suite you ask? Burp Suite is a Java based Web Penetration Testing framework. It has become an industry standard suite of tools used by information security professionals. Burp Suite helps you identify vulnerabilities and verify attack vectors that are affecting web applications. Because of its popularity and breadth as well as depth of features, we have created this useful page as a collection of Burp Suite knowledge and information.
In its simplest form, Burp Suite can be classified as an Interception Proxy. While browsing their target application, a penetration tester can configure their internet browser to route traffic through the Burp Suite proxy server. Burp Suite then acts as a (sort of) Man In The Middle by capturing and analyzing each request to and from the target web application so that they can be analyzed. Penetration testers can pause, manipulate and replay individual HTTP requests in order to analyze potential parameters or injection points. Injection points can be specified for manual as well as automated fuzzing attacks to discover potentially unintended application behaviors, crashes and error messages.
Works only with Java 8. beacuse from version 9 and up xbootclasspath argument has been disabled.
Proof
BurpKeygen.jar Virustotal scan:
burpsuite_pro_v2.0.06beta.jar Virustotal scan:















RSTCon #1 - Discutii initiale
in RSTCon
Posted
eu