
sado
-
Posts
596 -
Joined
-
Last visited
-
Days Won
1
Posts posted by sado
-
-

Privacy of Internet users is dead somewhere as the Intelligence agencies can watch our every move, hear our every conversation and read our every email and find out anything related to our personal and private life.
Last year, Edward Snowden revealed about the mass surveillance carried out by NSA and other countries intelligence agencies on every citizen of their country.
The US Government has allotted a large share of its 'Black Budget' for secret surveillance programs and to make this happen, NSA has used a number of unethical ways and labelled as legal solutions, harvesting hundreds of millions of Metadata from emails, web activity, chats, social networks, and everything else around the world.
The revelations encouraged Internet users think about their privacy and digital rights, and the time came when different organisations started several campaigns to block mass surveillance and fight back against the U.S. National Security Agency (NSA).
RESET YOUR INTERNET PRIVACY RIGHTS
A wider coalition of more than hundreds of Internet companies and civil liberties, environmental and political organizations is arriving together with a global call to “Reset the Net” that aimed to beat government and corporate surveillance on the web making mass Internet surveillance more difficult for the NSA and other spy agencies and governments.
The campaign is similar to 'The Black-Out Day', the largest online protest in the history of the Internet, successfully carried out by Google, Wikipedia, Wordpress and many other companies to protest two federal bills, the Senate’s Protect IP Act and the House’s Stop Online Piracy Act (SOPA). Thousands of websites went dark over the internet to stop mass surveillance conducted by the government.
But later the US government molded its Foreign Intelligence Surveillance Act in such a way that, now it legally allowed them to monitor Billions of calls in a day and tracking a million of the devices, and this is what we cannot allow them to make happen.
The new campaign is organized by Fight for the Future, which is planning a day to "Reset the Net" by deploying new privacy tools and enhanced security measures on June 5, exactly a year after the first Edward Snowden revelation regarding the NSA’s PRISM program, based on documents the former NSA contractor provided to the media.
The coalition includes Web sites such as Reddit, Boing Boing, Imgur, DuckDuckGo, the Free Software Foundation, CREDO Mobile, along with a number of organizations like the Freedom of the Press Foundation, Demand Progress, the Open Technology Institute, the Libertarian Party.
"The NSA is exploiting weak links in Internet security to spy on the entire world, twisting the Internet we love into something it was never meant to be: a panopticon," they say. "We can't stop targeted attacks, but we *can* stop mass surveillance, by building proven security into the everyday Internet."
HOW TO JOIN
The groups are encouraging developers to add at least one NSA resistant feature to mobile apps and Internet users to use privacy and security tools such as a secure version of HTTP i.e. HTTPS, HTTP Strict Transport Security (HSTS), a Web security policy tool, and Perfect Forward Secrecy (PFS) which is a public key cryptography tool to better secure the communication of Internet users and fail government intelligence agencies’ man-in-the-middle attacks.
“HTTPS, HSTS, and PFS are powerful tools that make mass spying much more difficult,” the groups state. “Until websites use them, we’re sunk: agencies like the NSA can spy on everything. Once they're ubiquitous, mass surveillance is much harder and more precarious—even if you’re the NSA.”
The Government and NSA always defended their mass surveillance program as a part of the legal action, by saying that it is necessary and only carried out to target terrorists and related crimes just to protect the security of the nation.
But we, sitting over here, are not fool to differentiate between the ‘security of the nation’ and ‘security of our privacy’. One has no right to risk other’s security to protect one’s own.
So, will you all, who are reading this article right now, go back and sit relax? You should not. Go and protect your privacy and digital rights, and Join the campaign. We will not remain quiet now. Enough is Enough.
Sursa:http://thehackernews.com
-
e vorba despre o problema de contabilitate, care rezolvata in model matematic da error

-
There is a good news for all Security researchers, Penetration testers and Hackers. The developers of one of the most advance open source operating system for penetration testing, 'KALI Linux' have announced yesterday the release of its latest version of Kali Linux 1.0.7 with some interesting features.
Kali Linux is an open source Debian-based distribution for penetration testing and forensics that is maintained and funded by Offensive Security, a provider of world-class information security training and penetration testing services.
In the beginning of this year, Offensive Security released Kali Linux 1.0.6 with Kernel version 3.12, and also added the Self Destruct feature that allows Kali users to encrypt the full hard disk to make the data inaccessible in an emergency case by entering a secret password at boot time.
This latest Kali Linux 1.0.7 version added some more features to the last version, along with many new penetration testing and hacking tools. The new release includes the most stable and latest kernel i.e. Linux kernel 3.14 with bug fixes, performance improvement and hardware support.
KALI LIVE USB PERSISTENCE ENCRYPTION
The most attractive feature added to the latest Kali Linux release is ‘Live USB persistence encryption’, which allows you to create a bootable Kali Linux with persistent encrypted partition on USB drive, that gives you an option to securely save your changes on the USB drive even after the reboots.
Kali Linux now offers two persistent options in the boot menu, as shown. One is an encrypted USB persistence partition and other one is unencrypted persistence partition.
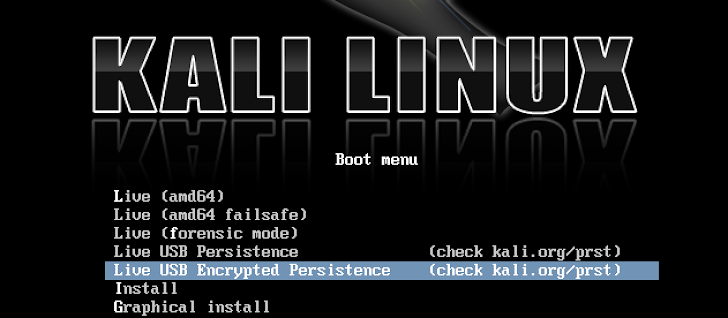
This was one of the most awaiting feature that now allows penetration testers and hackers to keep their data, customized scripts and favorite 3rd party hacking tools organized in the Live Kali Linux on bootable USB Sticks.
UPGRADE KALI LINUX NOW!
If you are already have Kali Installed onto your system, then there is no need to download and reinstall the latest updated version from scratch. Instead, you can use following commands to upgrade to Kali 1.0.7 easily:
apt-get update
apt-get dist-upgrade
# If you've just updated your kernel, then:
rebootThe new release also includes ARM image scripts, and team has promised to provide some additional virtual machine images and custom ARM images in the near future.
sursa: thehackersnews.com
-
Si eu sunt mandru ca sunt roman, o sa va spun si de ce.
Dupa ce am facut o facultate in Romania si gramada de cursuri si specializari diverse, am constatat ca nu imi pot gasi un loc de munca decent care sa-mi aduca satisfactie, asa ca mi-am deschis o firma care dupa mai putin de 2 ani am inchis-o pentru ca mi-am dat seama ca statul imi ia practic 70-80% din venituri iar eu raman cu MULT prea putin din munca mea.
Am plecat prin Franta, am lucrat o scurta perioada de timp si apoi m-am mutat in Germania. Am deschis acolo o firma pe care am ridicat-o la un venit de peste 350.000 euro/anual (de la 0). Facusem in jur de +3000 clienti si ma gandeam sa ma extind, asa ca am mai deschis o firma in UK (filiala a celei din Germania) si am venit in Romania dupa aproape 5 ani cu gandul sa deschid si aici, sa angajez 2-3 studenti, sa inchiriez un spatiu frumos si sa facem o treaba. Plateam la furnizori de internet / servicii diverse din Romania in jur de 15.000 de euro (practic, era o investitie a unei firme Germane in Romania).
Dupa exact 10 luni in care pregatisem toate cele, m-au arestat, au confiscat in mod abuziv toate echipamentele companiei Germane (cu datele clientilor) si s-au pisat pe mine. Deci, vreo 5 ani de munca pierduti, peste 3000 de clienti ramasi cu ochii in soare si inchis cu niste talhari, violatori, spargatori de apartamente si un pedofil.
Great
Chiar sunt mandru ca sunt roman. Mi-a oferit prea multe Romania sa nu fiu mandru.
Am o socoteala de incheiat cu statul Roman apoi o sa pun degetul pe harta sa vad unde pot merge. Chiar si cetatenie de UNGUR daca imi iau, tot o sa fiu multumit ca nu o sa mai am acte in care sa scrie "CETATEAN ROMAN".
Va doresc mult noroc, voua, celor iubitori de patrie.
Dar asta nu inseamna ca tara in sine e devina, ci unele personaje care o conduc. Daca am schimba niste chestii, respectiv mentalitatea unor persoane, cu resursele(umane/naturale) oferite de aceasta tara am ajunge foarte sus.
Ar fi foarte multe de punctat pe aceasta tema..
-
Unul cunoaste site-ul si altul parola
 .
. -
Raspunsul pentru intrebarea de 1k point, este, 'to learn'. O voi folosi pentru a invata practicand.
Pai, ceva care sa mearga pe calitate/performanta/stabilitate/suport/pret
-
Ceva nouati in domeniu?
Cei care sunt in domeniu, ar putea oferii niste informatii despre ce se foloseste acum? pe ce a(s)m putea arunca banii?
-
1
2
http://www.geglobalresearch.com/blog/really-cool-models-of-ice-nucleation
3, ceva awesome gasesc si aici, http://www.arcaspace.com/
-
Yahoo-owned Flickr, one of the biggest online photo management and sharing website in the world was recently impacted by critical web application vulnerabilities, which left website's database and server vulnerable hackers.
Ibrahim Raafat, a security researcher from Egypt has found SQL injection vulnerabilities on Flickr Photo Books, new feature for printing custom photo books through Flickr that was launched 5 months ago.
He claimed to have found two parameters (page_id , items) vulnerable to Blind SQL injectionand one (i.e. order_id) Direct SQL Injection that allowed him to query the Flickr database for its content by the injection of a SQL SELECT statements.
A Successful SQL exploitation could allow an attacker to steal the Database and MYSQL administrator password.
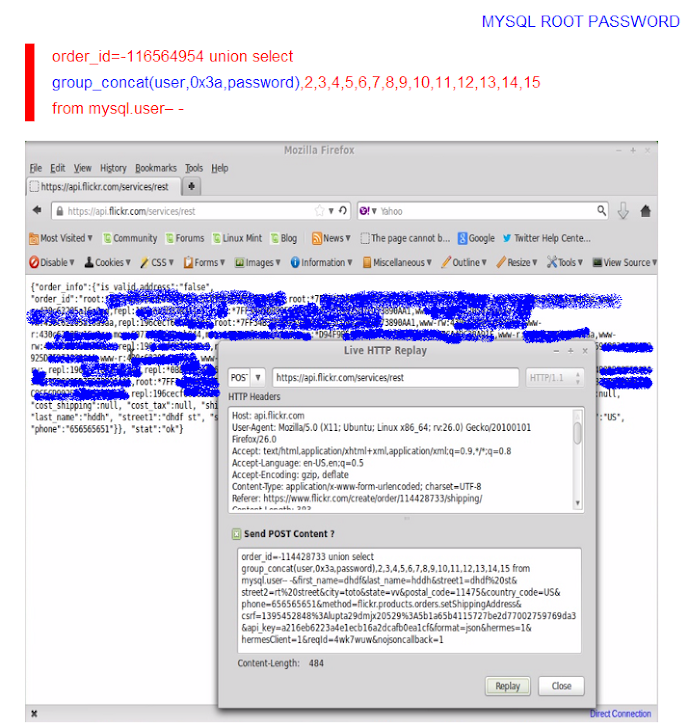
Furthermore, Flickr's SQL injection flaws also facilitate the attacker to exploit remote code execution on the server and using load_file(/etc/passwd) function he was successfully managed to read the content from the sensitive files on the Flickr server, as shown below:
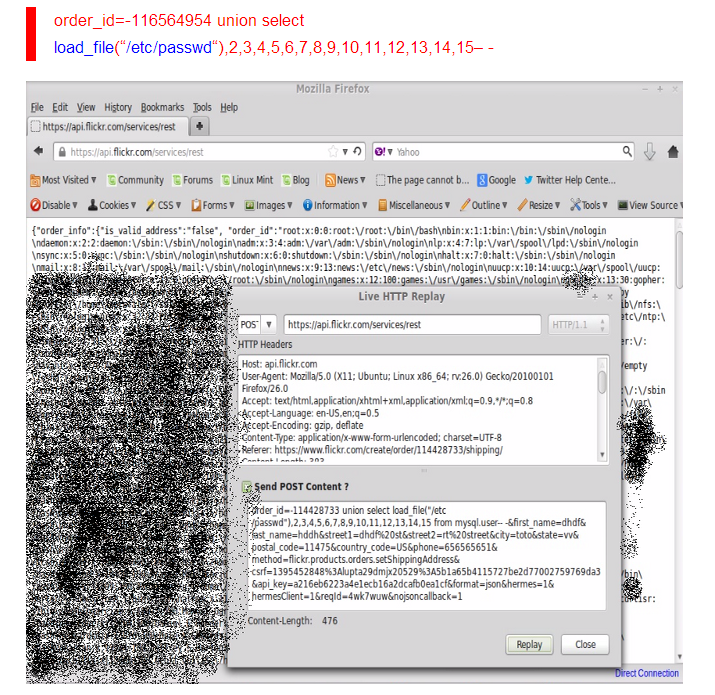
In addition to this, Ibrahim was able to write new files on the server that let him upload a custom 'code execution shell'.
Video Demonstration:
He reported the vulnerability to Yahoo which have been patched.
Update: Yahoo awarded Ibrahim Raafatwith biggest bug bounty payout ever. He received $15,000 for reporting Flickr SQL injection and Remote code execution vulnerability.
-
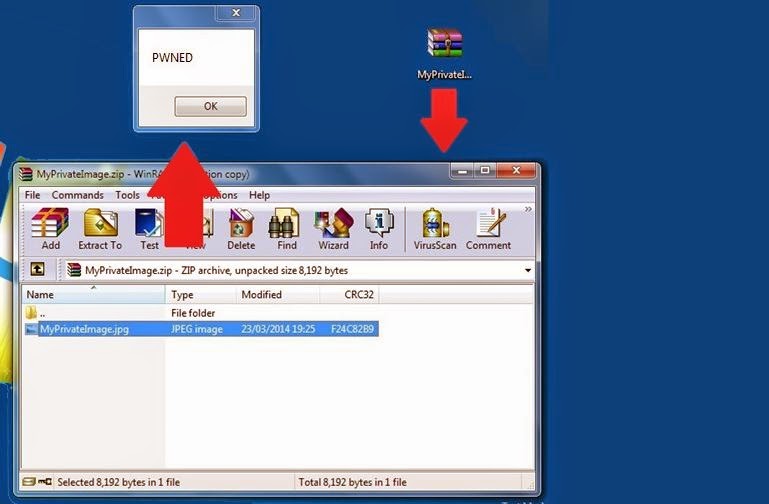
Imagine, You Open a Winrar archive of MP3 files, but what if it will install a malware into your system when you play anyone of them.
WinRAR, a widely used file archiver and data compression utility helps hackers to distribute malicious code. Israeli security researcher Danor Cohen (An7i) discovered the WinRAR file extension spoofing vulnerability.
WinRAR file extension spoofing vulnerability allows hackers to modify the filename and extension inside the traditional file archive, that helps them to hide binary malicious code inside an archive, pretending itself as '.jpg' , '.txt' or any other format.
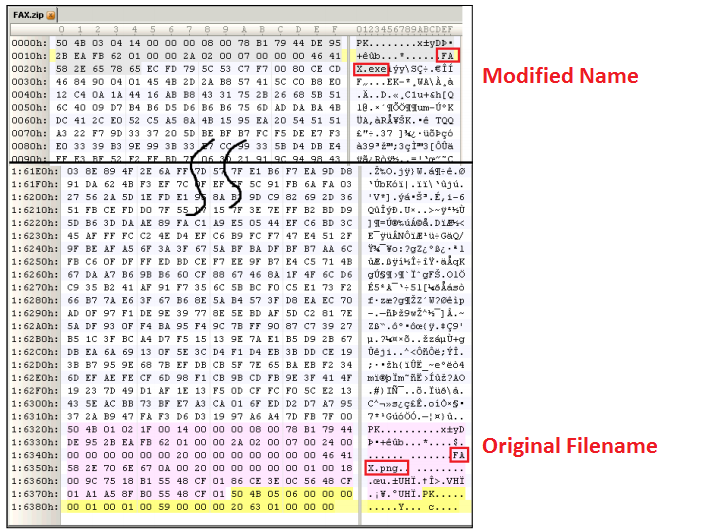
Using a Hex editor tool, he analysed a ZIP file and noticed that winrar tool also adds some custom properties to an archive, including two names - First name is the original filename (FAX.png) and second name is the filename (FAX.png) that will appear at the WINRAR GUI window.
Danor manipulated the second filename and extension to prepare a special ZIP archive, that actually include a malware file "FAX.exe", but displaying itself as "FAX.png" to the user.
Cyber intelligence company, IntelCrawler also published a report, which revealed that cybercriminals specialized in cyber espionage attacks are using this zero-day vulnerability in the wild to target several aerospace corporations, military subcontractors, embassies, as well as Fortune Global 500 companies.
Using this technique, an attacker can drop any malware in very convincing manner to the victim's system. "Using this method the bad actors bypass some specific security measures including e-mail server’s antivirus systems" IntelCrawler said.
Danor successfully exploited winrar version 4.20, and IntelCrawler confirmed that the vulnerability also works on all WinRar versions including v.5.1.
HOW TO CREATE EXPLOITABLE ZIP FILE?
A video demonstration has been prepared by Indian Security Researcher Ajin Abraham, shown below:
"One of the chosen tactics includes malicious fake CV distribution and FOUO (For Official Use Only)-like documents, including fax scanned messages"
Using social engineering techniques, attacker are targeting high profile victims with spear phishing mails, "Most of sent malicious attachments are hidden as graphical files, but password protected in order to avoid antivirus or IDS/IPS detection." IntelCrawler reported.
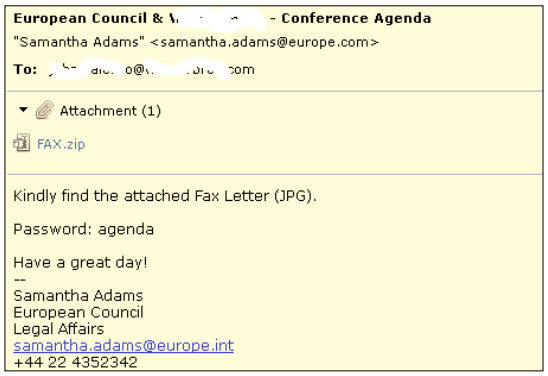
In above example, the Malware archive file was password protected to avoid antivirus detection, used in an ongoing targeted cyber espionage campaign.
Researchers found Zeus-like Trojan as an attachment, which has ability to establish remote administration channel with the infected victim, gather passwords and system information, then send the collected and stolen data to the Command & Control server hosted in Turkey (IP 185.9.159.211, Salay Telekomünikasyon).
Users are advised to use an alternative archiving software and avoid opening archives with passwords even if it has legitimate files.
-
 1
1
-
-
800 Million US based Credit and Debit cards compromised! Really it’s a big number and till now it has not been sized by the cyber security officials but a hacker group claims that they had stolen data on hundreds of millions of U.S. card accounts.
Last week, the hacker group called itself Anonymous Ukraine (Op_Ukraine), said it has seized information pertained to 800 million U.S. credit and debit card accounts, including the cards’ data belong to U.S. President Obama and other political figures. The group says the intention behind this data theft is to harm the U.S. economy.
The messages posted on March 24 shows clearly that they were by anti-American. The first message read, "After the USA showed its true face when she unilaterally decides which of the peoples to live independently and who under the yoke of the Federal Reserve, we decided to show the world who is behind the future collapse of the American banki
ng system. We own all the financial information of the Fed. And even more than you think."
The post was linked with four text files including the data sets of seven million card account that were from all the four card brands, Visa, MasterCard, Discover and American Express. On this, the four card companies didn’t comment until now, AmericanBanker.com reported.
On March 26, Anonymous Ukraine tweeted that it had released account details for five million more credit cards, and the very next day, it posted the details of 20 million more card accounts. Investigators working for Battelle counted a total of 10.2 million card accounts details in these batches.
"I would continue watching posts from the group, and checking their data dumps for validity," says Ernest Hampson, technical director for Battelle's cyber intelligence and counterintelligence group.
"It's really important to keep an eye on your enemy, find out what they're interested in, what their motivation is, what their capabilities are. You have to have somebody out there watching the adversarial groups, watching inside these forums where they gather, and discuss and trade research back and forth, and discover where they're going next before they get there."
The financial data breach has been investigated by two companies, the security provider Risk Based Security and the world’s largest nonprofit research and development organization, Battelle. The companies reported that the records produced as evidence of the breach by the group are incomplete, out of date or are fraudulent.
The investigators were also unable to verify the 800 million accounts that the group claimed to have compromised, including those of the VIPs and political figures.
Till now, the data threat doesn't appear to be as serious as the Target breach that occurred during the last Christmas holidays in which hackers were successfully able to obtain 40 million valid current credit cards’ details.
But, yet the claims and any further releases of information by the hacker group is need to be revised and investigated, because these kind of claims serve as a reminder for the financial firms of the constant vigilance and collaboration.
-
https://rstforums.com/forum/79839-cum-sa-te-ascunzi-eficient.rst
Atata imaginatie au unii, am intreb de ce nu o folosesc intr-un mod constructiv, auzi, robin-hood..
-
Am citit cu atentie comentariile si subiectul pe care se discuta si am iesit la o concluzie destul de idioata.
Acest raportaj a fost facut cam degeaba de un nenea plictisit , haideti sa va argumentez de ce am spus asta.
Fiecare planeta are un camp gravitational , campul gravitational depinde foarte mult si de dimensiunea planetei
Ce sunt meteoritii? Meteoritii sunt sunt niste bucati de fier si roca , care nu au o orbita ci o traiectorie !
Luna este un satelit natural a pamantului citisem la un momendat intr-o carte de astronomie ca luna este formata din bucati din pamant acum miliarde de ani in urma dupa ce pamantul a fost lovit de un meteorit
In prima faza acele bucati din pamant orbitau in juru pamantului sub foma unor inele dar din cauza atractiei gravitationale a soarelui sau indepartat si asa sa creat luna.
Luna orbiteaza in 3 planuri
1) In juru pamantului
2) In jurul propriei axe
3) In jurul soarelui
Daca ne gandim putin mai logic ori ca pui intrebarea "de ce nu pica luna pe pamant" este echivalenta cu intrebarea "De ce nu pica satelitii pe pamant."
Exista un echilibru perfect intre luna / pamant sa spunem ca distantele sunt la limita deoarece luna are tangente cu forta gravitationala a pamantului dar tot odata si pamantul are tanenta cu forta gravitationala a lunii (cel mai concret exemplu sunt marianele flux / reflux) ca sa va fac sa intelegeti mai bine puneti doi magneti nord pe nord si o sa observati ca o sa se respinga dar o sa pastreze mereu aceiasi distanta.
Luna nu se departeaza cu 4cm / an , ca si pamantul traiectoria lunei in jurul pamantului este usor ovata nu perfect rotunda.
haha, interesant ; si de ce ai tu dreptate si el nu?
 ,
, cand discuti un subiect ce tine de o ''stiinta exacta'', trebuie sa aduci argumente reale si dovedite.,
ar fi multe de povestit despre acest subiect..
Sunt sigur ca majoritatea cunosc faptul ca traiectoria luni fata de pamant nu are o forma perfect rotunda. Ideea era ca acea traiectorie isi mareste distanta cu 4 cm/an.
-
Si acum luna se dep?rteaz? de noi cam cu ~ 4cm pe an ?i nu e pe deplin în?eles [1]. Referitor la ce a zis axel mai sus, in general fizica explica doar cum, nu si de ce. Daca nu ma credeti incercati sa va explicati fenomenele din mecanica cuantica

nu cumva universul este intr-o continua expansiune?
-
(Reuters) - A sophisticated piece of spyware has been quietly infecting hundreds of government computers across Europe and the United States in one of the most complex cyber espionage programs uncovered to date.
Several security researchers and Western intelligence officers say they believe the malware, widely known as Turla, is the work of the Russian government and linked to the same software used to launch a massive breach on the U.S. military uncovered in 2008. Those assessments were based on analysis of tactics employed by hackers, along with technical indicators and the victims they targeted.
"It is sophisticated malware that's linked to other Russian exploits, uses encryption and targets western governments. It has Russian paw prints all over it," said Jim Lewis, a former U.S. foreign service officer, now senior fellow at the Center for Strategic and International Studies in Washington.
However, security experts caution that while the case for saying Turla looks Russian may be strong, it is impossible to confirm those suspicions unless Moscow claims responsibility. Developers often use techniques to cloud their identity.
Public talk of the threat surfaced this week after a little known German anti-virus firm, G Data, published a report on the virus, which it called Uroburos. The name is from a string of text in the code that may be a reference to a Greek symbol depicting a serpent eating its own tail.
Experts in state-sponsored cyber attacks say that Russian government-backed hackers are known for being highly disciplined, adept at hiding their tracks, extremely effective at maintaining control of infected networks and more selective in choosing targets than their Chinese counterparts.
"They know that most people don't have either the technical knowledge or the fortitude to win a battle with them. When they recognize that someone is onto them, they just go dormant," said one security expert who has helped victims of state-sponsored hacking operations.
A former Western intelligence official commented: "They can draw on some very high grade programmers and engineers, including the many who work for organized criminal groups, but also function as privateers."
Russia's Federal Security Bureau declined comment as did officials at the Pentagon and U.S. Department of Homeland Security.
On Friday, Britain's BAE Systems Applied Intelligence - the cyber arm of Britain's premier defense contractor - published its own research on the spyware, which it called "snake".
The sheer sophistication of the software, it said, went well beyond that previously encountered - although it did not attribute blame for the attack.
"The threat... really does raise the bar in terms of what potential targets, and the security community in general, have to do to keep ahead of cyber attacks," said Martin Sutherland, managing director of BAE Systems Applied Intelligence.
NATO NATIONS TARGETED
Researchers with established security companies have been monitoring Turla for several years.
Symantec Corp estimates up to 1,000 networks have been infected by Turla and a related virus, Agent.BTZ. It named no victims, saying only that most were government computers.
Hackers use the Turla spyware to establish a hidden foothold in infected networks from which they can search other computers for data, store information that is of interest and eventually transmit it back to their servers.
F-Secure, a Helsinki-based maker of security software, first encountered Turla last year while investigating organizations attacked, according to chief research officer Mikko Hypponen. He also declined to name victims.
"While it seems to be Russian, there is no way to know for sure," said Hypponen.
Security firms that are monitoring the threat have said the operation's sophistication suggests it was likely backed by a nation state and that technical indicators make them believe it is the work of Russian developers.
European governments have long welcomed U.S. help against Kremlin spying, but were infuriated last year to discover the scale of surveillance by America's National Security Agency that stretched also to their own territory.
AGENT.BTZ
Security experts say the stealthy Turla belongs to the same family as one of the most notorious pieces of spyware uncovered to date: Agent.BTZ. It was used in a massive cyber espionage operation on U.S. Central Command that surfaced in 2008 and is one of the most serious U.S. breaches to date. While Washington never formally attributed blame, several U.S. officials have told Reuters they believed it was the work of Russia.
Hypponen said Agent.BTZ was initially found in a military network of a European NATO state in 2008, but gave no details. F-Secure is credited with naming that piece of malware in 2008, though researchers believe it was created already in 2006.
Eric Chien, technical director with Symantec Security Response, described Turla as "the evolution" of Agent.BTZ. "They are a very active development group," Chien said.
Finland said its Foreign Ministry computer systems had been penetrated by an attack last year but would not describe the method or say if it was related to Agent.BTZ and Turla.
Sweden's signals intelligence agency, the National Defense Radio Establishment, said attacks to gain information were "more common than people think", adding that the agency had discovered multiple attacks against authorities, governments and universities, some only detected only after several years
Government sources in the Czech Republic, Estonia, Poland and Romania said Turla had not affected them directly. Other European governments contacted by Reuters declined comment.
CHASING TURLA
Although computer security researchers have been quietly studying Turla for more than two years, public discussions of the threat only began after G Data published its report.
G Data spokesman Eddy Willems said his firm had obtained more than 10 samples of Turla. He declined to name any victims or identify the author of the report, saying the firm was concerned the group behind Turla might attempt to harm him.
Researchers say that the creators of Turla have regularly updated its code, making changes to avoid detection as anti-virus companies detect new strains.
Jaime Blasco, director of AlienVault Labs, said that Turla was more of a "framework" for espionage than simply malware.
The malware is a "root kit" that hides the presence of the spying operation and also creates a hidden, encrypted file system to store stolen data and tools used by the attackers, he said. Those tools include password stealers, tiny programs for gathering information about the system and document stealers.
The operators can download specialized tools onto an infected system, adding any functionality they want by including it in the encrypted file system, Blasco said.
They have used dozens of different "command and control" servers located in countries around the world to control infected systems, according to Symantec, whose researchers have helped identify and shut down some of those systems.
Chien said that in some cases Turla's operators team have responded quickly when one of their servers were taken offline, quickly releasing new versions of the malware that direct infected computers to new command and control servers.
"They have a super active development team," he said.
source: Suspected Russian spyware Turla targets Europe, U.S. | Reuters
-
On February 13, 2014, Air Strato, electrical powered unmanned aerial vehicle performed the first take-off from rough ground. The aircraft performed a short flight at 25 m altitude and then landed.
Air Strato was powered by four electrical engines. Two supplementary engines were added in order to shorten the take-off distance. Other additions ware suspensions installed on main and forward landing gear. The right landing gear suspension was damaged at touch down.
"The aircraft had only 10 percent of the batteries intended for the commercial version so we had to add ballast to simulate take-off weight. We also added two more electrical motors to increase thrust, needed on the rough ground to decrease take-off distance that, combined with the landing gear suspension, provided for a smooth taxi and take-off on rough terrain. It took less than 30 m to lift into the air at maximum thrust. Also we were impressed by the aircraft's rate of climb." - Teodor Diaconu, ARCA flight dynamics engineer.

Air Strato is a high altitude electrical powered unmanned aerial vehicle. It can reach altitudes of above 18 km and has an autonomy of 7 hours on internal batteries and 3 days using solar panels. It can carry a variable payload up to 30 kg consisting of surveillance equipment or other scientific instruments.

sursa: ARCASPACE
-
Cu toate astea, prezenta unei sectiuni gen "show-off"(de acolo a pornit problema cu implicarea rst), prezinta mereu posibilitatea aparitiei problemelor de acest fel. Acolo ar trebui luate masuri intai(daca rst se doreste a nu fi implicat in situatii de genu pe viitor).
-
Ai specificat ca acest canal nu este altau.
Am tras doua concluzii: Esti prost si habar nu ai sa compui un text intr-un topic, ori esti prost si nu sti sa specifici ca textul este scris de persoana X si nu de tine.
Ah, si vezi ca aici e sectiunea de "Bloguri si bloggeri", nu de "youtubisti".
Cat despre tutorial, interesant, am discutat si eu cu tipu' (sper ca nu esti tu)
putea fi pur si simplu un measaj compus de respectivul 'prieten' si 'paste' pe forum..nu te grabi cu concluziile
-
interesant, va dati seama ce ar insemna sa ai o baza de date cu toate incaperile si alte detalii
?
-
"Daca constructorii ar face constructiile in felul in care programatorii concep programe, atunci prima ciocanitoare care ar veni, ar distruge civilizatia."
Definitiile lui Murphy privind sistemele computerizate:
Hardware: Acele parti ale sistemului pe care le poti lovi cu piciorul.
Software: Acele parti ale sistemului care nu functioneaza.
Hard disk: Acea componenta a sistemului care intepeneste in momentul cel mai nepotrivit cu putinta.
Periferica: Acele componente care sunt incompatibile cu sistemul tau.
Imprimanta: Acea componenta a sistemului care se blocheaza cand nu te uiti la ea.
Cablu: Acea parte a sistemului care e prea scurta.
Backup: O operatie care niciodata nu este efectuata la timp.
Restaurare: O precedura care functioneaza perfect pana cand e nevoie de ea.
Memorie: Acea parte a sistemului computerizat care este insuficienta.
Mesaj de eroare: O solicitare de aprobare a distrugerii propriilor tale date.
Fisier: Acea parte a sistemului care nu poate fi gasita.
Procesor: Acea componenta a sistemului computerizat care este depasita tehnologic.
-
ON: Bun venit.
OFF: Ce intelegi tu prin flood? Cum 'flodezi' un server de cs?
-
defapt, nu e al meu site-ul
 . Dar e foarte bine scris si merita citit de cat mai multe persoane.
. Dar e foarte bine scris si merita citit de cat mai multe persoane. -
Acest articol reprezint? o promisiune pe care mi-am f?cut-o în perioada în care eram student, perioad? ce s-a încheiat de pu?in timp. Toate nedrept??ile, abuzurile, erorile ?i abera?iile sistemului de înv???mânt ne afecteaz? direct în intervalul în care facem parte din acest sistem, în calitate de elevi sau studen?i. Odat? încheiat? aceast? perioad?, r?mânem cu diplomele, iar toate neregulile constatate, tr?ite ?i resim?ite organic nu mai reprezint? interes pentru noi ?i ca atare le d?m uitarii. Ne vedem de vie?ile noastre în continuare, pentu c? nu vedem niciun motiv de a lupta pentru o cauz? ce nu ne mai afecteaz?. Acest sindrom se manifest? de la o genera?ie la alta ?i poate, peste un num?r de ani, unii dintre noi ajungem s? facem iar??i parte din acest sistem, de partea cealalt? a baricadei. O baricad? ce nici nu ar trebui s? existe, îns? din p?cate, odat? ajun?i "oameni mari", devenim orbi ?i surzi la problemele cu care se confrunt? copiii. Începem s? ne credem maturi ?i suntem convin?i ca lucrurile stau a?a cum le vedem noi..........
-
 1
1
-
-
Kickbox, kyokushin, kempo unele din cele mai dure.
In ele inveti cu adevarat sa primesti in primul rand.Dezvolti reflexe.Musculatura. singurul dezavantaj e ca ai nevoie de foarte multa ambitie si rezistenta psihica
 . Nu inveti in 2 luni.O sa te obisnuiesti cu durerea in timp. Necesita antrenamente intense si dureroase.
. Nu inveti in 2 luni.O sa te obisnuiesti cu durerea in timp. Necesita antrenamente intense si dureroase.

youtube discurs Putin
in Off-topic
Posted
Urmaream un videoclip pe youtube, respectiv
https://www.youtube.com/watch?v=T4IM-NWZ4zE
, la sfarsitul videoclipului, in loc sa se opreasca, pe un fundal negru, a incepus sa sune vocea lui Putin, era ceva despre un referendum, nu am inteles mare chestie, doar cateva cuvinte care semanau. A tinut undeva la 3-4 minute, dupa care am reincarcat pagina, am pus video-ul la sfarsit dar fara aceleasi rezultat.media atack? propaganda? wtf?