-
Posts
1263 -
Joined
-
Last visited
-
Days Won
7
Posts posted by virusz
-
-
-
-
Web Hack Control Center is a Web Server Vulnerability scanner
Download:
-
rrs is a reverse (connecting) remote shell. Instead of listening for incoming connections it will connect out to a listener (rrs in listen mode). The listener will accept the connection and receive a shell from the remote host. rrs features full pseudo-tty support, full OpenSSL support (high encryption, client/server authentication, choice of cipher suites), Twofish encryption, a simple XOR cipher, plain-text (unencrypted) session, peer-side session monitoring (snooping), daemon option and reconnection features. rrs is Free Software distributed under the MIT License and is known to compile and run under Linux, FreeBSD, NetBSD, OpenBSD and QNX.
HomePage:
http://www.cycom.se/dl/sishell
Download:
-
-
Whoppix is a stand alone penetration testing live cd based on Knoppix. With the latest tools and exploits, it is a must for every penetration tester and security auditor. Whoppix includes Several exploit archives, such as Securityfocus, Packetstorm, SecurityForest and Milw0rm, as well as a wide variety of updated security tools. The new custom kernel also allows for better WIFI support, for tools such as Aireplay.
Licence : GPL
Version : 2.7.1 [stable]
Platforms : Linux
Requirements : Minimum of 128MB RAM, Pentium 1 processor
Size : 700 Mb
Download:
-
Astalavista's Security Toolbox DVD v2.0 is considered to be the largest and most comprehensive Information Security archive.As always we are committed to provide you with a resource for all of your security and hacking interests, in an interactive way! The Information found on the Security Toolbox DVD has been carefully selected, so that you will only browse through quality information and tools.No matter if you are a computer enthusiast, a computer geek, a newbie looking for information on "how to hack", or an ITSecurity professional looking for quality and up to date information for offline use or just for convenience, we are sure that you will be satisfied, even delighted by the DVD!
http://rapidshare.de/files/22963029/astb2.0.part01.rar
[url]http://rapidshare.de/files/22965966/astb2.0.part02.rar[/url]
[url]http://rapidshare.de/files/22968906/astb2.0.part03.rar[/url]
[url]http://rapidshare.de/files/22971825/astb2.0.part04.rar[/url]
[url]http://rapidshare.de/files/22974520/astb2.0.part05.rar[/url]
[url]http://rapidshare.de/files/22977300/astb2.0.part06.rar[/url]
[url]http://rapidshare.de/files/22980233/astb2.0.part07.rar[/url]
[url]http://rapidshare.de/files/22983005/astb2.0.part08.rar[/url]
[url]http://rapidshare.de/files/22985842/astb2.0.part09.rar[/url]
[url]http://rapidshare.de/files/22988432/astb2.0.part10.rar[/url]
[url]http://rapidshare.de/files/22991189/astb2.0.part11.rar[/url]
[url]http://rapidshare.de/files/22993837/astb2.0.part12.rar[/url]
[url]http://rapidshare.de/files/22996059/astb2.0.part13.rar[/url]
[url]http://rapidshare.de/files/22998048/astb2.0.part14.rar[/url]
[url]http://rapidshare.de/files/22999947/astb2.0.part15.rar[/url]
[url]http://rapidshare.de/files/23001613/astb2.0.part16.rar[/url]
[url]http://rapidshare.de/files/23031359/astb2.0.part17.rar[/url]
[url]http://rapidshare.de/files/23033928/astb2.0.part18.rar[/url]
[url]http://rapidshare.de/files/23036563/astb2.0.part19.rar[/url]
[url]http://rapidshare.de/files/23039246/astb2.0.part20.rar[/url]
[url]http://rapidshare.de/files/23042664/astb2.0.part21.rar[/url]
[url]http://rapidshare.de/files/23045279/astb2.0.part22.rar[/url]
[url]http://rapidshare.de/files/23048210/astb2.0.part23.rar[/url]
[url]http://rapidshare.de/files/23051249/astb2.0.part24.rar[/url]
[url]http://rapidshare.de/files/23054164/astb2.0.part25.rar[/url]
[url]http://rapidshare.de/files/23057062/astb2.0.part26.rar[/url]
[url]http://rapidshare.de/files/23059901/astb2.0.part27.rar[/url]
[url]http://rapidshare.de/files/23062926/astb2.0.part28.rar[/url]
[url]http://rapidshare.de/files/23065780/astb2.0.part29.rar[/url]
[url]http://rapidshare.de/files/23068662/astb2.0.part30.rar[/url]
[url]http://rapidshare.de/files/23071370/astb2.0.part31.rar[/url]
[url]http://rapidshare.de/files/23073876/astb2.0.part32.rar[/url]
[url]http://rapidshare.de/files/23076444/astb2.0.part33.rar[/url]
[url]http://rapidshare.de/files/23078753/astb2.0.part34.rar[/url]
[url]http://rapidshare.de/files/23081470/astb2.0.part35.rar[/url]
[url]http://rapidshare.de/files/23083045/astb2.0.part36.rar[/url]
[url]http://rapidshare.de/files/23084586/astb2.0.part37.rar[/url]
[url]http://rapidshare.de/files/23086010/astb2.0.part38.rar[/url]
[url]http://rapidshare.de/files/23087524/astb2.0.part39.rar[/url]
[url]http://rapidshare.de/files/23088971/astb2.0.part40.rar[/url]
[url]http://rapidshare.de/files/23090266/astb2.0.part41.rar[/url]
[url]http://rapidshare.de/files/23090468/astb2.0.part42.rar[/url]have phun!
-
Metasploit took the security world by storm when it was released in 2004. No other new tool even broke into the top 15 of this list, yet Metasploit comes in at #5, ahead of many well-loved tools that have been developed for more than a decade. It is an advanced open-source platform for developing, testing, and using exploit code. The extensible model through which payloads, encoders, no-op generators, and exploits can be integrated has made it possible to use the Metasploit Framework as an outlet for cutting-edge exploitation research. It ships with hundreds of exploits.This makes writing your own exploits easier, and it certainly beats scouring the darkest corners of the Internet for illicit shellcode of dubious quality. Similar professional exploitation tools, such as Core Impact and Canvas already existed for wealthy users on all sides of the ethical spectrum. Metasploit simply brought this capability to the masses.
version 2.6
for windows
http://www.metasploit.com/tools/framework-2.6.exe
for linux and mac and sun
http://www.metasploit.com/images/os/osx.gif
version 3.0
for linux and mc and sun
http://www.metasploit.com/projects/Framework/msf3/download.html?Release=alpha-r3
3nJoy!
-
I dont take Responsability if you get your a*s in jail for using this. use it at your own risk.
The latest version of the Uncapping Kit fromtheoryshare. Learn to uncapyour modem step by step with pictures. NewFeatures include updatedfirmware and eurodocsis support
http://rapidshare.de/files/13189106/Cable_Modem_Uncapping_Kit-www.WebXposed.de.rar.html
password: .webxposed.de -
Cum sa patrunzi intr-un sistem de operare (Windows XP si SP1)
Salut, sa incepem cu inceputul: Treaba "merge" atat in retea cat si in afara retelei in care te afli, dar mai nou providerii de servicii internet au inchis porturile folosite in general la exploatarea sistemelor. Am sa va explic cum faceti "treaba" in retea, tot asa se face si in afara doar ca va trebui sa aveti noro (sa nu fie inchise principalele porturi. ...metode sunt multe, va voi explica o metoda simpla si functionala. Presupun ca ati auzit de "blaster" sau "sasser"
 ,poate v-ati confruntat cu ei, sunt doi virusi care patrund intr-un calculator fara ca voi sa executati ceva sau sa intrati pe o pagina ciudata... Windows XP si Windows XP + Sp1 sunt vulnerabile: Sistemele Windows XP Home, Pro sunt vulnerabile la "blaster" si "sasser", Windows XP Pro + sp1 este vulnerabil doar la "sasser".. Oare ce inseamna "blaster", este numele unui virus care patrunde in calculator cu Windows XP (fara update-uri), el foloseste porturile: 135,139,445,539 , in general 135. Ah.."sasser" este tot un virus asemanator lui "blaster" dar acesta patrunde prin alta matoda si foloseste portul 445. .Cum patrundem intrun calculator care are Windows XP (fara update-uri).
,poate v-ati confruntat cu ei, sunt doi virusi care patrund intr-un calculator fara ca voi sa executati ceva sau sa intrati pe o pagina ciudata... Windows XP si Windows XP + Sp1 sunt vulnerabile: Sistemele Windows XP Home, Pro sunt vulnerabile la "blaster" si "sasser", Windows XP Pro + sp1 este vulnerabil doar la "sasser".. Oare ce inseamna "blaster", este numele unui virus care patrunde in calculator cu Windows XP (fara update-uri), el foloseste porturile: 135,139,445,539 , in general 135. Ah.."sasser" este tot un virus asemanator lui "blaster" dar acesta patrunde prin alta matoda si foloseste portul 445. .Cum patrundem intrun calculator care are Windows XP (fara update-uri). 1.Cautam cu ajutorul unui motor de cautare, "rpc dcom exploit" (sursa o gasim mai usor) compilam sursa (daca nu aveti posibilitatea, cautati mai bine, veti da si de exploitul deja compilat).
2.Cautam tot cu ajutorul unui motor de cautare: a. un scanner de porturi cu care scanam porturile 135,139 etc... sau b. un scanner pentru vulnerabilitatea "rpc dcom" - o varianta simpla.
3.Avem nevoie de un client (pentru conectare la calculatorul "spart" - putty sau NetCat sunt cele mai bune pentru asa ceva. !!!Avem tot ce ne trebuie, sa ii dam drumul: Rulam scannerul pentru vulnerabilitatea "rpc dcom", scriem ip-urile (intreaga clasa) care dorim sa fie scanate, asteptam sa gasim un calculator vulnerabil, sa presupunem ca am gasit unul: 21.242.53.87 Pornim consola (start>run> cmd), ne ducem acolo unde am pus exploitul "rpc dcom" care presupunem ca are numele "dcom.exe",dam comanda: dcom.exe -d 21.242.53.87 -t 1 -r 0100139d -p 135 -l 7315 Dupa ce am dat comanda, daca victima nu are firewall.. ne v-a aparea ceva de genu "c:windowssystem32" de acum nu aveti decat sa ii puneti un troian sau sa va deschideti un port anume.. si sa ii dati comenzi, sa il spionati si alte cele...
metoda veche dar inca functionala
 lolikz
lolikz -
A very quick half-open portscanner with optional multithreaded protocol specific probing tool.
Download:
http://www.bindshell.net/tools/synscan/syn...can-3.1.tar.bz2
-
This program performs reverse DNS lookups for network blocks or an input file. The requests can be performed mulit-threaded.
Usage:
./res <subnet or filename to resolve> <forks>
Download:
http://www.bindshell.net/tools/massresolve/res.c
-
A small utility,for quickly and easily generating lists of IP addresses.
Download:
-
cautatzi UpLink , mie mi-a placut....
-
===========================================
How to autorun a program in Windows:
===========================================
There are many ways .exe,.bat,.vbs,.com, etc programs can autostart
on a target computer.
1. Winstart.bat on older systems - Winstart.bat will start with
windows every
time the computer boots on older machines. Any command prompt
commands can be
used in the batch file.
===================================================================
2. Startup Folder - The startup folder is the most basic way of
getting an
executable to start with windows. This method is easy to detect and
will be
found. If the method is used I would suggest to have it not matter
if it is found
(use your imagination) and/or have an alternative auto startup method
as well.
The default startup folder for windows 9x & ME is found at:
C:windowsstart menuprogramsstartup
Windows 2k, XP, 2003 use :
C:Documents and SettingsAdministratorStart MenuPrograms
(Administrator can be changed to another user name if you know what
it is.)
Any executable files placed in this folder will be automaticaly
executed at
startup.
====================================================================
3. Win.ini & System.ini - The Win.ini & System.ini methods are old
favorites.
Find the files are located in c:windows or c:winnt depending on
the
version of windows and where it is installed.
To use Win.ini to autostart your program first open Win.ini with a
text editor
find [windows] or add it if its not there and then add (making sure
path is
right) load=Whatever.exe and then run=Whatever.exe.
Ex.
[windows]
load=Whatever.exe
run=Whatever.exe
System.ini is very simple too, first open System.ini in notepad and
then find
[boot] in the text and add Shell=Explorer.exe Whatever.exe.
Ex.
[boot]
Shell=Explorer.exe Whatever.exe
======================================================================
4. Registry - Registry is probably the most popular method of auto
starting
trojans, worms and viruses. Most people do not know how to remove
registry entries or how to even find them via regedit.
To make software run automaticaly a string can be added to either of
the
following registry keys:
[HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRunServi
ces]
[HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRunServi
cesOnce]
[HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRun]
[HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRunOnce]
For the above keys all you have to do is add a string with what ever
name you
want and data of what ever path to your exe, such as:
Name | Type | Data
-------------------
Windows Update | REG_SZ | c:windowssystem32Whatever.exe
Another key is:
[HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRunOnceE
x
-
Sending Anonymous Emails
Sometimes it is neccasary to send an email anonymously.
There are several web based utilities that allow this, but each one registers the ip info in the headers which allows tracing. They also
will not allow you to use a proxy and utilize their service. This is for security reasons.
My definition of anonymous includes the email addresses appearing as if they have been sent from whatever address you specify as well
as no accurate record of your IP in the headers of the mail that could be traced back to you.
The method that follows supports my definition of anonymous.
Amazingly, all you need to accomplish this is telnet and a smtp server. Allow me to break it down.
Telnet is a software application that connects one machine to another, allowing you to log on to that other machine as a user.
If you don't have telnet, you can easily download it for free from the web - do a search on "telnet" or "download telnet"in any search
engine.
...and just for the sake of being thorough...
What is SMTP?
SMTP stands for "Simple Mail Transfer Protocol"
Basiclly just a protocol for sending e-mail.
Where do you get a SMTP server?
Heres a few links, but as always be aware that these sites may not be here forever or their content may change. Searching for "SMTP servers"
or "SMTP server list" should produce effective results.
http://www.gr0w.com/help/email_help_smtp_servers.htm
http://www.uic.edu/depts/accc/ecomm/smtpmove/isps.html
http://www.thebestfree.net/free/freesmtp.htm
http://www.registerdirect.co.nz/help/smtp_servers.html
http://www.bu.edu/pcsc/email/remote/smtplist.html
Once you've selected a server, open the command prompt, and type:
telnet xxxxxx.com 25
(obviously replace the x's with the SMTP server you've selected)
now type the following:
--------------------------------
HELO targetsmailserver.com
MAIL FROM: whoever@whatever.com
RCPT TO: target@address.com
DATA
from: whoever@whatever.com
subject: whatever
received: xxx.xxx.xxx.xxx
x-header: xxx.xxx.xxx.xxx
The body of the message goes here
.
----------------------------------------
*Note 1: Remember to end with "." on a line by itself as directed.
*Note 2: Adding x-header and received allows you to alter the IP information found in the headers of the mail, making it untracable and
totally anonymous**
*Note 3: There are ISPs that have port 25 (SMTP) blocked. Be sure your settings and ISP allow connections to port 25. If all else fails,
get the SMTP sever address from your ISP.
Thats all it takes to send a totally anonymous email. Hope you enjoyed.
-
Free SMS Messaging With Nokia
Section 1: The Introduction
----------------------------
Once again here is another tutorial written by your's truly. I was
going to implement this concept into a program, but it came to me
early on that the idea just wasn't going to work. So instead I bring
this information to you in my typical tutorial format. So read, and
enjoy...
Section 2: The Method
----------------------
This method is known to work on the nokia 3210, 5610, and 9110 models.
To perform this trick we will first turn off your phone. Then turn
your phone on and enter your pin. Once you have done this, punch in
the following string...
*#746025625#
If your model works with this trick then you will get a "SIM CLOCK
STOP ALLOWED" message on the screen. That's it, now you can send
sms messages for free. Be warned, this trick sometimes doesn't work
on certain networks so I wouldn't go overboard with this trick until
you receive your first bill. If you get no signs of the sms messaging
you did after performing this trick on your bill then feel free to
chat all you want. Have fun! =)
Section 3: The Conclusion
--------------------------
Well once again I hope you enjoyed reading this as much as I enjoyed
writing this. I'm right now trying to work with programming under the
SymbianOS (for those a bit illiterate in this field, basically,
programming nokia phones) so hopefully you will all see some nokia
apps made by me coming out soon enough. And of course, I have a
couple of tutorial ideas I might pick back up on when I get the chance,
but life has been keeping me busy lately so don't expect any immediate
release of anything. Well anyways, until next time...
-
Making Free Calls With Nokia
Section 1: The Introduction
----------------------------
Tired of wondering if you have gone over your minute limit? Tired of
trying to guess how many minutes you are going to use? Tired of even
paying for the shit? Then this is the tutorial for you. This is a
short and simple tutorial that will teach you, the reader, how to
make free calls on your Nokia cell phone. So let's proceed...
Section 2: So How Do We Do It?
-------------------------------
This technique works on most of the nokia models out today. Meaning
this will work for you as long as you don't have an old fossil sort
of model. So what you will first do is turn on your phone. Then punch
in the code *3001#12345#. This will bring up the NAM programming menu.
From here go down and select the option NAM 1. Once you are in the NAM
1 menu, go down until you see "Emergency Numbers", and enter. You then
go down until you see an empty slot and enter the empty slot. Then
simply punch in the number that you want to call and exit the NAM
programming menu. Now when you dial up the number, the number will be
treated as an emergency call number, which will therefore put the
phone into emergency call mode (which you can exit out of once you are
finished with your call). No number in the emergency call number list
is ever billed to you. There are a couple of other things you can do
from within the NAM programming menu, but that can be saved for another
time, and another tutorial.
Section 3: The Conclusion
--------------------------
Once again I hoped you enjoyed reading this as much as I enjoyed
writing this. This trick for the most part only works on the Nokia
60 series, though I believe may also work for a couple of other models.
Be sure to also note that this trick also doesn't work on all
networks. Therefore, if you indeed do have a compatible model, first
try it with just one or two calls before you start going wild. Then
just wait for the bill, and if nothing shows up about the calls you
made with this trick, then feel free to call away. Anyways, until next
time...
Note: If you have a question or comment and feel the need to reach me
then you can do so at murdermouse@informationleak.net and I will try to get back
with you as soon as possible.
-
zuper nice, trecetzi si p'aici: http://www.kismetwireless.net/download.shtml
-
Sprajax is the first web security scanner developed specifically to scan AJAX web applications for security vulnerabilities. Denim Group, an IT consultancy specializing in web application security, recognized that there were no tools available on the market able to scan AJAX. AJAX allows web-based applications a higher degree of user-interactivity, a feature with growing popularity among developers.
[url]http://www.denimgroup.com/Sprajax/Default.aspx[/url] -
Actually I released this a bit while ago, but I wasn't active here on Igniteds when I released it so I never had the chance to post it here. Anyways, the Anti School Kit (or simply ASK) offers the following...
Guides
------
Hacking Win98: by Halla
How to bypass restrictions to get to the command prompt: by Halla &
Murder Mouse
Thawing Out DeepFreeze: by Murder Mouse
Hacking The School Network: by Murder Mouse
Hijacking The School PA System: by Murder Mouse
Net Send Time Bomb: by Murder Mouse
How to bypass web filters: by Halla
Hacking Windows NT/2K/XP: by Halla
Tools
-----
Silent Web Cgi Shell: description self-explanatory
bindin: identifies which novell users have what permissions
chknull: cracks novell accounts
Deep UnFreezer: unfreezes affected versions of DeepFreeze
FileDate Changer v1.1: description self-explanatory
Haxernet Explorer v2.01: a browser that uses translation services
to browse sites not allowed by the web filtering software.
NetStumbler: scans and reports wireless access points
OnSite: browses the cached network
Pandora: kit full of novell related warez
SharesFinder: uh, finds open shares of course
SMAC: spoofs MAC address
snlist: CLI app that is used for the same purpose that ONSite is
userdump: naturally dumps a list of users on the network
The programs are meant to compliment the guides, and the guides meant to show you how to apply the included tools (in short for some of you who may need to be reminded, don't just jump at the programs, take a little time out of your life to read the tutorials included). Anyways, here is the link, and be sure to tell me what you think (it's like I make a rhyme, everytime)...
Download:
-
This is a full hacked kb905474 hotfix.
Just install this as you would normaly install the hotfix.
reboot when installed.
After reboot no more nag screens and you can update again.
Download:
http://files2.9down.com:8000/crack/kb90547...4_1.5.532.2.rar
-
Warning
=======
This information should only be used to test your own server's security. Do not attempt to "test" a website's security without permission from it's administrator. Hacking is illegal.
Quick Intro
=========
If you're not familiar with dictionary-based password cracking then this tutorial is not for you.
Using dictionaries to crack passwords can be very frustrating – Especially after you've waited over two days for a program to use a 240MB list that doesn't seem to have that password. So what do you do? There's a way to dramatically increase your chances of cracking that password. How? By making your own dictionary. No, I don’t mean creating a list by hand in notepad (Don't worry it's all mostly automated)
Tools needed
===========
PassParse:
http://darknet.org.uk/content/files/passwo...d/passparse.zip
RemDupes:
http://ksoze.deny.de/RemDupes2.exe
Brutus:
http://217.125.24.22/h/brutus.zip
Intellitamper:
http://www.intellitamper.com/download/inte...amper_v2.07.exe
The Steps
=========
1. Alright. What we need to do first is extract all text from the website. Sounds like a huge task but IntelliTamper will make things a little easier for us. Okay let's open IntelliTamper, enter the website, and press the "Start Search" button. What this will do is find all (or most) pages of the site. Once it's finished, save all the pages it found into one directory on your computer (Right-Click > Save).
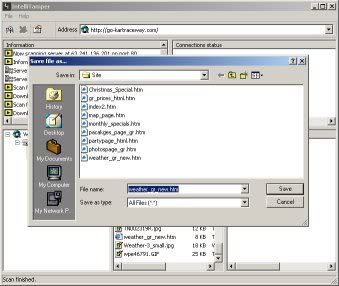
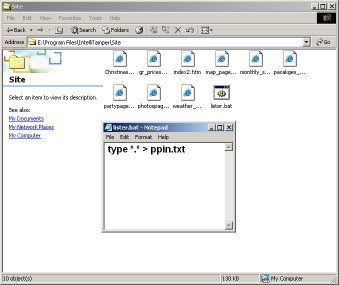
2. Now let's navigate to the directory where we saved the files. Next we're gonna make a simple batch file that will read all the files and send the output to a text file named "ppin.txt". Open Notepad and enter the following:
CODE
type *.* > ppin.txt
and save it as "lister.bat" (without quotations of course). Once you've saved it, run it. Ppin.txt should have been created. (Note the file MUST be name ppin)
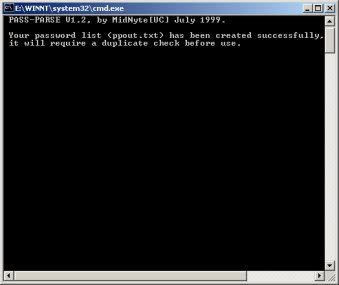
3. Next we're going to create the actual list itself. If you open ppin.txt you'll see that it's just a bunch of html/text. We're gonna use Pass Parse to extract all the words and put in list format. Alright. Copy the file "ppin.txt" and paste it into the same directory as your Pass Parse program. If there’s already a file named ppin then overwrite it. Now launch Pass Parse. The DOS Prompt should have shown for a second or less. Your new password list, "ppout.txt", was just created.
4. Almost finished. If you open your new password list you'll notice that there are many words used more than once. To take care of the problem we'll use RemDupes. This program will remove all duplicated words and sort your list in alphabetical order. So open your copy of RemDupes, click "Add", and navigate to your password file (ppout.txt). Click "Find Dupes" and when that's finished click "Save List". Your list is completely finished.
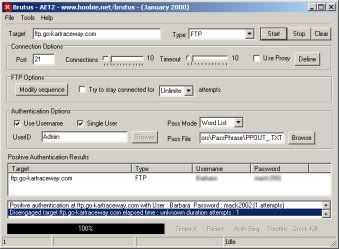
"Positive Authentication with User: Admin Password: inagokart"
-
MAC SPOOFER is a MAC Address Modifying Utility (spoofer) for Windows 2000, XP, and Server 2003 systems, regardless of whether the manufactures allow this option or not. MAC SPOOFER is a MUST-HAVE TOOL for IT, Security, Networking professionals, gamers, and everyone who needs a MAC Addresses Changer.
Key Features
Easy usage and simple configuration, highly intuitive interface makes operation easy for both beginners and power users.
Able to manage up to 16 network interfaces.
In detail, it does not change the hardware built-in MAC-address, but changes software based MAC Address on the Windows NT, 2000, XP and 2003.
Display all available network adpaters.
Works with wireless network adapters.
Low resource required.
Download:



Certified Ethical Hacker Lab 3.0.iso
in Programe hacking
Posted
Certified Ethical Hacker Lab 3.0.iso
Download:
Module 1: Ethics and Legality
What is an Exploit?
The security functionality triangle
The attacker's process
Passive reconnaissance
Active reconnaissance
Types of attacks
Categories of exploits
Goals attackers try to achieve
Ethical hackers and crackers - who are they
Self proclaimed ethical hacking
Hacking for a cause (Hacktivism)
Skills required for ethical hacking
Categories of Ethical Hackers
What do Ethical Hackers do?
Security evaluation plan
Types of Ethical Hacks
Testing Types
Ethical Hacking Report
Cyber Security Enhancement Act of 2002
Computer Crimes
Overview of US Federal Laws
Section 1029
Section 1030
Hacking Punishment
Module 2: Footprinting
What is Footprinting
Steps for gathering information
Whois
http://tucows.com
Hacking Tool: Sam Spade
Analyzing Whois output
NSLookup
Finding the address range of the network
ARIN
Traceroute
Hacking Tool: NeoTrace
Visual Route
Visual Lookout
Hacking Tool: Smart Whois
Hacking Tool: eMailTracking Pro
Hacking Tool: MailTracking.com
Module 3: Scanning
Determining if the system is alive?
Active stack fingerprinting
Passive stack fingerprinting
Hacking Tool: Pinger
Hacking Tool: WS_Ping_Pro
Hacking Tool: Netscan Tools Pro 2000
Hacking Tool: Hping2
Hacking Tool: icmpenum
Detecting Ping sweeps
ICMP Queries
Hacking Tool: netcraft.com
Port Scanning
TCPs 3-way handshake
TCP Scan types
Hacking Tool: IPEye
Hacking Tool: IPSECSCAN
Hacking Tool: nmap
Port Scan countermeasures
Hacking Tool: HTTrack Web Copier
Network Management Tools
SolarWinds Toolset
NeoWatch
War Dialing
Hacking Tool: THC-Scan
Hacking Tool: PhoneSweep War Dialer
Hacking Tool: Queso
Hacking Tool: Cheops
Proxy Servers
Hacking Tool: SocksChain
Surf the web anonymously
TCP/IP through HTTP Tunneling
Hacking Tool: HTTPort
Module 4: Enumeration
What is Enumeration
NetBios Null Sessions
Null Session Countermeasures
NetBIOS Enumeration
Hacking Tool: DumpSec
Hacking Tool: NAT
SNMP Enumertion
SNMPUtil
Hacking Tool: IP Network Browser
SNMP Enumeration Countermeasures
Windows 2000 DNS Zone transfer
Identifying Win2000 Accounts
Hacking Tool: User2SID
Hacking Tool: SID2User
Hacking Tool: Enum
Hacking Tool: UserInfo
Hacking Tool: GetAcct
Active Directory Enumeration
Module 5: System Hacking
Administrator Password Guessing
Performing Automated Password Guessing
Legion
NTInfoScan
Defending Against Password Guessing
Monitoring Event Viewer Logs
VisualLast
Eavesdroppin on Network Password Exchange
Hacking Tool: L0phtCrack
Hacking Tool: KerbCrack
Privilege Escalation
Hacking Tool: GetAdmin
Hacking Tool: hk
Manual Password Cracking Algorithm
Automatic Password Cracking Algorithm
Password Types
Types of Password Attacks
Dictionary Attack
Brute Force Attack
Distributed Brute Force Attack
Password Change Interval
Hybrid Attack
Cracking Windows 2000 Passwords
Retrieving the SAM file
Redirecting SMB Logon to the Attacker
SMB Redirection
Hacking Tool: SMBRelay
Hacking Tool: SMBRelay2
SMBRelay Man-in-the-Middle (MITM)
SMBRelay MITM Countermeasures
Hacking Tool: SMBGrinder
Hacking Tool: SMBDie
Hacking Tool: NBTDeputy
NetBIOS DoS Attack
Hacking Tool: nbname
Hacking Tool: John the Ripper
LanManager Hash
Password Cracking Countermeasures
Keystroke Logger
Hacking Tool: Spector
AntiSpector
Hacking Tool: eBlaster
Hacking Tool: SpyAnywhere
Hacking Tool: IKS Software Logger
Hardware Tool: Hardware Key Logger
Hacking Tool: Rootkit
Planting Rootkit on Windows 2000 Machine
_rootkit_ embedded TCP/IP Stack
Rootkit Countermeasures
MD5 Checksum utility
Tripwire
Covering Tracks
Disabling Auditing
Auditpol
Clearing the Event Log
Hacking Tool: Elslave
Hacking Tool: Winzapper
Hacking Tool: Evidence Eliminator
Hidding Files
NTFS File Streaming
Hacking Tool: makestrm
NTFS Streams Countermeasures
LNS
Steganography
Hacking Tool: ImageHide
Hacking Tool: MP3Stego
Hacking Tool: Snow
Hacking Tool: Camera/Shy
Steganography Detection
StegDetect
Encrypted File System
Hacking Tool: dskprobe
Hacking Tool: EFSView
Buffer Overflows
Creating Buffer Overflow Exploit
Outlook Buffer Overflow
Hacking Tool: Outoutlook
Module 6: Trojans and Backdoors
What is a Trojan Horse?
Overt and Covert
Hacking Tool: QAZ
Hacking Tool: Tini
Hacking Tool: Netcat
Hacking Tool: Donald Dick
Hacking Tool: SubSeven
Hacking Tool: BackOrifice 2000
Back Oriffice Plug-ins
Hacking Tool: NetBus
Wrappers
Hacking Tool: Graffiti
Hacking Tool: Silk Rope 2000
Hacking Tool: EliteWrap
Hacking Tool: IconPlus
Packaging Tool: Mic*ft WordPad
Hacking Tool: Whack a Mole
Trojan Construction Kit
BoSniffer
Hacking Tool: FireKiller 2000
Covert Channels
ICMP Tunneling
Hacking Tool: Loki
Reverse WWW Shell
Backdoor Countermeasures
BO Startup and Registry Entries
NetBus Startup and Registry Keys
Port Monitoring Tools
fPort TCPView
Process Viewer
Inzider - Tracks Processes and Ports
Trojan Maker
Hacking Tool: Hard Disk Killer
Man-in-the-Middle Attack
Hacking Tool: dsniff
System File Verification
TripWire
Module 7: Sniffers
What is a Sniffer?
Hacking Tool: Etheral
Hacking Tool: Snort
Hacking Tool: WinDump
Hacking Tool: EtherPeek
Passive Sniffing
Active Sniffing
Hacking Tool: EtherFlood
How ARP Works?
Hacking Tool: DSniff
Hacking Tool: Macof
Hacking Tool: mailsnarf
Hacking Tool: URLsnarf
Hacking Tool: Webspy
Hacking Tool: Ettercap
Hacking Tool: SMAC
MAC Changer
ARP Spoofing Countermeasures
Hacking Tool: WinDNSSpoof
Hacking Tool: WinSniffer
Network Tool: IRIS
Network Tool: NetInterceptor
SniffDet
Hacking Tool: WinTCPKill
Module 8: Denial of Service
What is Denial of Service Attack?
Types of DoS Attacks
How DoS Work?
What is DDoS?
Hacking Tool: Ping of Death
Hacking Tool: SSPing
Hacking Tool: Land
Hacking Tool: Smurf
Hacking Tool: SYN Flood
Hacking Tool: CPU Hog
Hacking Tool: Win Nuke
Hacking Tool: RPC Locator
Hacking Tool: Jolt2
Hacking Tool: Bubonic
Hacking Tool: Targa
Tools for Running DDoS Attacks
Hacking Tool: Trinoo
Hacking Tool: WinTrinoo
Hacking Tool: TFN
Hacking Tool: TFN2K
Hacking Tool: Stacheldraht
Hacking Tool: Shaft
Hacking Tool: mstream
DDoS Attack Sequence
Preventing DoS Attack
DoS Scanning Tools
Find_ddos
SARA
DDoSPing
RID
Zombie Zapper
Module 9: Social Engineering
What is Social Engineering?
Art of Manipulation
Human Weakness
Common Types of Social Engineering
Human Based Impersonation
Important User
Tech Support
Third Party Authorization
In Person
Dumpster Diving
Shoulder Surfing
Computer Impersonation
Mail Attachments
Popup Window
Website Faking
Reverse Social Engineering
Policies and Procedures
Social Engineering Security Policies
The Importance of Employee Education
Module 10: Session Hijacking
What is Session Hijacking?
Session Hijacking Steps
Spoofing Vs Hijacking
Active Session Hijacking
Passive Session Hijacking
TCP Concepts - 3 way Handshake
Sequence Numbers
Sequence Number Example
Guessing the Sequence Numbers
Hacking Tool: Juggernaut
Hacking Tool: Hunt
Hacking Tool: TTYWatcher
Hacking Tool: IP Watcher
Hacking Tool: T-Sight
Remote TCP Session Reset Utility
Dangers Posed by Session Hijacking
Protection against Session Hijacking
Module 11: Hacking Web Servers
Apache Vulnerability
Attacks against IIS
IIS Components
ISAPI DLL Buffer Overflows
IPP Printer Overflow
msw3prt.dll
Oversized Print Requests
Hacking Tool: Jill32
Hacking Tool: IIS5-Koei
Hacking Tool: IIS5Hack
IPP Buffer Overflow Countermeasures
ISAPI DLL Source Disclosure
ISAPI.DLL Exploit
Defacing Web Pages
IIS Directory Traversal
Unicode
Directory Listing
Clearing IIS Logs
Network Tool: LogAnalyzer
Attack Signature
Creating Internet Explorer (IE) Trojan
Hacking Tool: IISExploit
Hacking Tool: UnicodeUploader.pl
Hacking Tool: cmdasp.asp
Escalating Privilages on IIS
Hacking Tool: IISCrack.dll
Hacking Tool: ispc.exe
Unspecified Executable Path Vulnerability
Hacking Tool: CleanIISLog
File System Traversal Countermeasures
Mic*ft HotFix Problems
UpdateExpert
Cacls utility
Network Tool: Whisker
N-Stealth Scanner
Hacking Tool: WebInspect
Network Tool: Shadow Security Scanner
Module 12: Web Application Vulnerabilities
Documenting the Application Structure
Manually Inspecting Applications
Using Google to Inspect Applications
Directory Structure
Hacking Tool: Instant Source
Java Classes and Applets
Hacking Tool: Jad
HTML Comments and Contents
Hacking Tool: Lynx
Hacking Tool: Wget
Hacking Tool: Black Widow
Hacking Tool: WebSleuth
Cross Side Scripting
Session Hijacking using XSS
Cookie Stealing
Hacking Tool: IEEN
Module 13: Web Based Password Cracking Techniques
Basic Authentication
Message Digest Authentication
NTLM Authentication
Certificate based Authentication
Digital Certificates
Mic*ft Passport Authentication
Forms based Authentication
Creating Fake Certificates
Hacking Tool: WinSSLMiM
Password Guessing
Hacking Tool: WebCracker
Hacking Tool: Brutus
Hacking Tool: ObiWan
Hacking Tool: Munga Bunga
Password dictionary Files
Attack Time
Hacking Tool: Varient
Hacking Tool: PassList
Query Strings
Post data
Hacking Tool: cURL
Stealing Cookies
Hacking Tool: CookieSpy
Hacking Tool: ReadCookies
Hacking Tool: SnadBoy
Module 14: SQL Injection
What is SQL Injection Vulnerability?
SQL Insertion Discovery
Blank sa Password
Simple Input Validation
SQL Injection
OLE DB Errors
1=1
blah' or 1=1
Stealing Credit Card Information
Preventing SQL Injection
Database Specific SQL Injection
Hacking Tool: SQLDict
Hacking Tool: SQLExec
Hacking Tool: SQLbf
Hacking Tool: SQLSmack
Hacking Tool: SQL2.exe
Hacking Tool: Oracle Password Buster
Module 15: Hacking Wireless Networks
802.11 Standards
What is WEP?
Finding WLANs
Cracking WEP keys
Sniffing Trafic
Wireless DoS Attacks
WLAN Scanners
WLAN Sniffers
MAC Sniffing
Access Point Spoofing
Securing Wireless Networks
Hacking Tool: NetTumbler
Hacking Tool: AirSnort
Hacking Tool: AiroPeek
Hacking Tool: WEP Cracker
Hacking Tool: Kismet
WIDZ- Wireless IDS
Module 16: Virus and Worms
Cherobyl
ExploreZip
I Love You
Melissa
Pretty Park
Code Red Worm
W32/Klez
BugBear
W32/Opaserv Worm
Nimda
Code Red
SQL Slammer
How to write your own Virus?
Worm Construction Kit
Module 17: Novell Hacking
Common accounts and passwords
Accessing password files
Password crackers
Netware Hacking Tools
Chknull
NOVELBFH
NWPCRACK
Bindery
BinCrack
SETPWD.NLM
Kock
userdump
Burglar
Getit
Spooflog
Gobbler
Novelffs
Pandora
Module 18: Linux Hacking
Why Linux ?
Linux Basics
Compiling Programs in Linux
Scanning Networks
Mapping Networks
Password Cracking in Linux
Linux Vulnerabilities
SARA
TARA
Sniffing
A Pinger in Disguise
Session Hijacking
Linux Rootkits
Linux Security Countermeasures
IPChains and IPTables
Module 19: IDS, Firewalls and Honeypots
Intrusion Detection System
System Integrity Verifiers
How are Intrusions Detected?
Anomaly Detection
Signature Recognition
How does IDS match Signatures with Incoming Traffic?
Protocol Stack Verification
Application Protocol Verification
What Happens after an IDS Detects an Attack?
IDS Software Vendors
SNORT
Evading IDS (Techniques)
Complex IDS Evasion
Hacking Tool: fragrouter
Hacking Tool: TCPReplay
Hacking Tool: SideStep
Hacking Tool: NIDSbench
Hacking Tool: ADMutate
IDS Detection
Tools to Detect Packet Sniffers
Tools to inject strangely formatted packets onto the wire
Hacking Through Firewalls
Placing Backdoors through Firewalls
Hiding behind Covert Channels
What is a Honeypot?
Honeypots Evasion
Honeypots vendors
Module 20: Buffer Overflows
What is a Buffer Overflow?
Exploitation
Assembly Language Basics
How to Detect Buffer Overflows in a Program?
Skills Required
CPU/OS Dependency
Understanding Stacks
Stack Based Buffer Overflows
Buffer Overflow Technical Implementation
Writing your own Buffer Overflow Exploit in C
Defense against Buffer Overflows
Type Checking Tools for Compiling Programs
StackGuard
Immunix
Module 21: Cryptography
What is PKI?
Digital Certificates
RSA
MD-5
RC-5
SHA
SSL
PGP
SSH
Encryption Cracking Techniques
---
have fun!