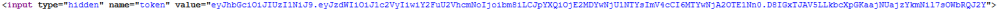-
Posts
18785 -
Joined
-
Last visited
-
Days Won
738
Everything posted by Nytro
-
Engleza e importanta daca vrei o cariera in IT. Aveti aici un tutorial "basic" (adica de baza), pentru incepatori: https://9gag.com/gag/a9ngZ7j
-
https://arhiblog.ro/actioneaza-vaccinurile-covid/ PS: Articolul respectiv nu va fi citit de prea multa lume. Si oricand am incerca, nu vom reusi. Oamenii sunt prosti. Adica pula mea, Youtube Trending: https://www.youtube.com/feed/trending Cam asta se cauta pe o platforma in care puteti gasi filmulete despre virusuri, vaccinuri sau chiar cum functioneaza o bomba nucleara. E mai usor de inteles Jador sau Tzanca Uraganul.
-
Din cate citisem, vaccinurile din prezent functioneaza si in privinta mutatiei de la nurci. Dar cu trecerea timpului vor fi probabil mutatii care vor "bypassa" vaccinul. Desi cu noua tehnologie de producere (acel ARN mesager), cred ca se va gasi destul de rapid unul nou. Asa cum se intampla la gripa. De aceea vaccinurile antigripale "moderne" sunt tetravalente - adica acopera 4 tulpini ale virusului gripal.
-
Noi nu o sa facem niciodata escrow. Nu avem de ce. Fiecare, fie ca vreau sa vanda, fie ca vrea sa cumpere, ca pe OLX, isi asuma responsabilitatea. Noi cerem un minim de 50 de posturi tocmai pentru a stabili un minim nivel de incredere, de a vedea cam "ce poate" un user inainte de a face afaceri cu el. Dar in final, e decizia fiecaruia.
-

Metoda prin care au fost golite conturile vedetelor din România.
Nytro replied to KtLN's topic in Stiri securitate
De obicei fac inginerie sociala pe cei de la support de la operatorul GSM, dar e probabil mai simplu asa, ca cei de la support sunt trainuiti pentru astfel de lucruri. -
2020-12-05 09:00:00 UTC — 2020-12-07 09:00:00 UTC DefCamp Capture The Flag ( D-CTF) is the most shattering and rebellious security CTF competition in the Central Eastern Europe. Here, the most skilled hackers & IT geeks put their knowledge to the test and compete with the best CFT teams from all over the world to get in the shortlist of best top 10, and later on win the overall D-CTF competition or, die trying. DefCamp Capture the Flag is organised since 2011 with over 10,000 players joined since then in annual multi-staged event for anyone. There is one important rule though – hack before being hacked! Event Summary Format: Jeopardy Play format: Team only Genres: Crypto, Pwning, Reversing, Web, Miscellaneous … Language: English Access: Open / Free for everyone Difficulty: Entry Level - Easy - Medium - Hard - Insane Website: D-CTF Detalii: https://dctf2020.cyberedu.ro/
-
adragos e un tip foarte bun la CTF-uri. Din cate am inteles, in timpul CTF-ului nostru se mai desfasura un altul, iar unii au mers la acela. Ceva international. Da, suntem romani
-
Nu se poate din punct de vedere fizic. Exista tehnologii de incarcare "wireless", in general de la distante mici, prin inductie, dar exista si dispozitive care se pot incarca de la undele electromagnetice din camp (e.g. radio). Se poate, tehnologia exista si se foloseste pentru senzori LowPower, dar acea incarcare e EXTREM de mica. Fie telefonul nu arata corect cata baterie are (cel mai probabil), fie (desi cred ca e cam mult) acel APK, daca avea privilegiile necesare, putea schimba in orice procent incarcarea bateriei (doar afisare, nu avea cum sa o incarce).
-
Am adaugat pe site si link-urile catre Youtube si slide-urile prezentarilor: https://rstcon.com/prezentari/
-
Ba, din 2001 ni se baga in organism microchip-uri sub pretextul ca sunt FERMENTI ACTTIVI si asta se face LA VEDERE, cum le place masonilor! Uitati aici, se spune CLAR ca acestia sunt introdusi in ORGANISM. @shitshow sper ca faci caterinca.
-
A, cred ca am auzit si eu, dar sincer, nu am idee de unde vine Cred ca marile interese au vazut parerile impotriva lor pe aici si e un fel de amenintare.
-
M-am gadit ca ar fi mai practic sa puteti gasi toate prezentarile intr-un singur loc. Playlist Youtube: https://www.youtube.com/playlist?list=PLTaLvwriPW8y9lcJRXy1UdQLfGDbkkBjD Lista prezentărilor RSTCon: 10:00 – 11:00 – RST – Trecut, prezent și viitor Ionuț Popescu (Nytro) – UiPath Romanian Security Team este o comunitate care a luat viață în 2006 și care azi ne aduce împreună. Ce este RST? Ce s-a întamplat în acești 14 ani? De ce merită mai multă atenție? Ce este în prezent această comunitate? Și mai ales, ce viitor are? În această prezentare voi răspunde acestor întrebări și vă voi explica punctul meu de vedere, atât ca persoană cât și ca administrator al comunității. 11:00 – 12:00 – Real World Bitsquatting Attack Ionuț Cernica – iccguard Acest studiu practic se referă la exploatarea comportamentului browserelor moderne în legătură cu încărcarea URL-urilor externe. În research-ul meu studiez problema cu acest comportament al browserelor moderne în combinație cu problema “bit flipping” pentru a demonstra un nou tip de atac într-o manieră legală. 12:00 – 13:00 – Pauza 13:00 – 14:00 – Approaching OT Pentesting from an IT perspective Cosmin Radu – Atos O scurta incursiune în cum se desfășoară un pentest într-un mediu OT (Operational Technology – fabrici, nave maritime, sisteme SCADA, sisteme de control pentru furnizat utilități). Care sunt riscurile și challenge-urile când testezi într-un mediu cu 0 downtime fizic, cu TCP/IP stacks proprietare și nu neaparat bine implementate. Care sunt diferențele dintre recomandările de mitigare dintre mediul IT și OT? 14:00 – 15:00 – How to find and exploit data conversion vulnerabilities in web apps Șerban Bejan – SecureWorks Exportarea datelor în diverse formate (PDF, documente OXML, imagini etc.) este omniprezentă pe web. Voi prezenta cum se poate injecta cod pentru a se ajunge la LFI, SSRF sau execuția de cod JavaScript arbitrar când există funcționalități de conversie. Veți vedea totul în legătură cu pașii necesari pentru a identifica și exploata injecțiile în exporturi și diverse trucuri și sfaturi practice. 15:00 – 16:00 – Introducere în exploituri publice Andrei Barbu – SecureWorks În această prezentare voi acoperi pe scurt ce este o vulnerabilitate, ce este un exploit și voi vorbi despre exploituri publice. Prezentarea va avea și live demo în care voi folosi o versiune outdated de Ubuntu pe care mă voi loga cu un guest account, voi descărca un local exploit pe care-l voi compila și apoi îl voi executa pentru a obține root. 16:00 – 17:00 – Security Evaluation of WordPress Backup Plugins Ionuț Cernica – iccguard Protejarea aplicațiilor web e o sarcină importantă pentru orice companie. WordPress este CMS-ul preferat de către companii. În această prezentare vom discuta de ce WordPress e o aplicație web importantă și necesitatea securizării acesteia. Un alt aspect analizat va fi în legătură cu securitatea plugin-urilor folosite pentru backup create pentru WordPress din punctul de vedere al leak-urilor de date sensibile, un număr de module vulnerabile, cauze ale vulnerabilităților, greșeli comune și impactul acestor vulnerabilități. Bazat pe un plan experimental vom observa potențialul distructiv al acestor plugin-uri de backup pe baza celor mai relevante website-uri din topul primelor 10 milioane de website-uri. 17:00 – 18:00 – Web pentesting – Sfaturi utile Ionuț Popescu – UiPath Cu toții știm ce este un XSS și cum să îl găsim, cel puțin în cazurile mai simple. Dar un penetration test trebuie să acopere mult mai mult de atât. Atenția la detalii este cea care rezultă în “finding-uri”. În această prezentare nu voi veni cu lucruri ieșite din comun dar voi trece printr-o listă de sfaturi utile atunci când faceți un pentest. Lista nu este nici pe departe completă, dar sper să vă ajute. 18:00 – 18:20 – Incheiere Ionuț Popescu – UiPath Ceremonia de încheiere a conferinței și prezentarea rezultatelor concursului CTF (Capture the Flag). Alte informatii legate de conferinta: https://rstcon.com/
- 1 reply
-
- 1
-

-
De fapt uite cum sta treaba, pentru cei conspirationisti care considera ca se vrea reducerea populatiei: acele persoane cu INTERESE MARI la mijloc publica aceste articole FALSE cum ar fi: 1. Covid nu exista, este o farsa 2. Covid nu este periculos 3. Vaccinurile au chip-uri ... Exact pentru ca oamenii sa creada ca acest Covid nu exista sau ca vaccinurile nu sunt bune, SPECIAL pentru ca lumea sa nu se protejeze de Covid, sa moara si sa scada populatia. Tocmai v-am pus pe masa o teorie a conspiratiei la adresa unei teorii a conspiratie. Conspiraception!
-
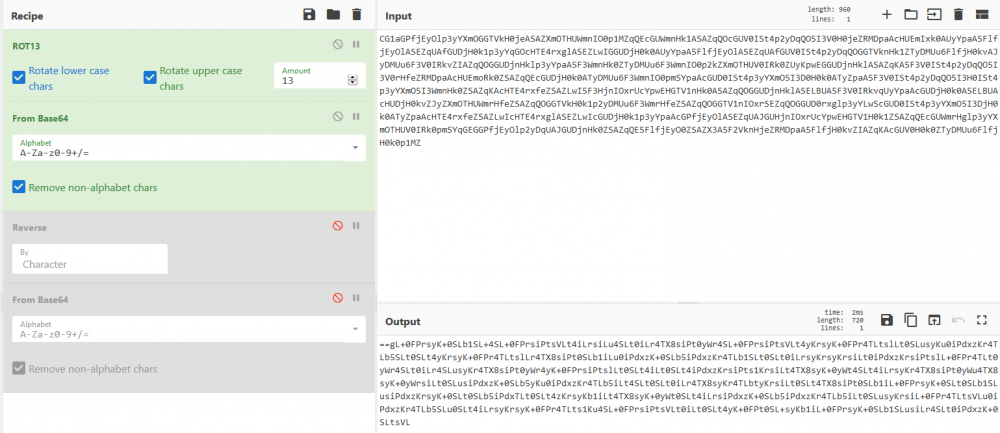
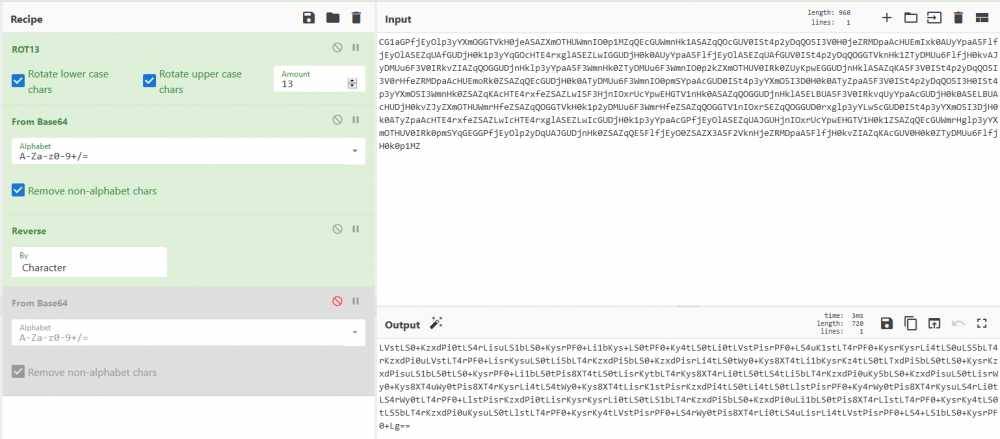
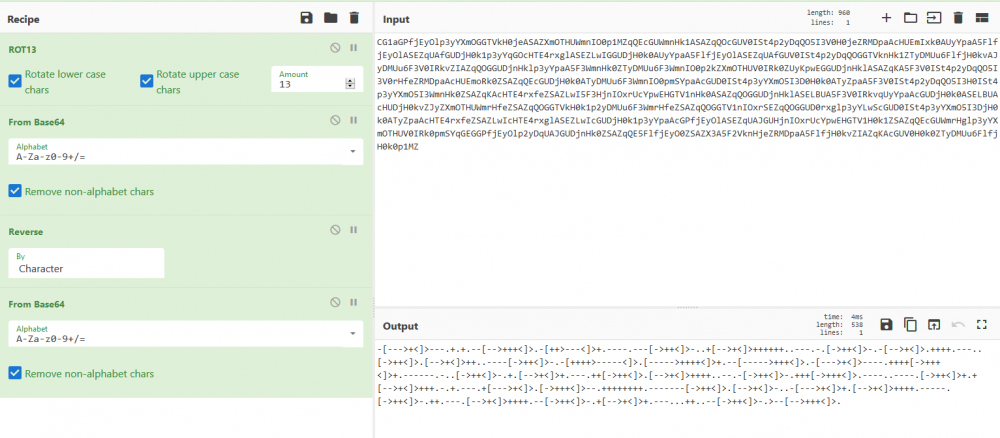
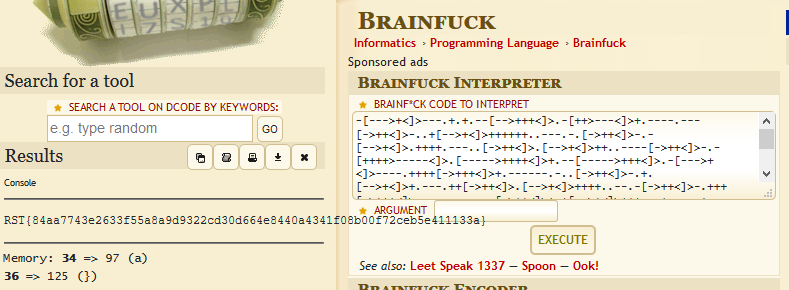
Mesajul de pe retea - II Autor: 0x435446 Summary Asemanator cu Mesajul de pe retea – I, am primit un mesaj encodat. Proof of Solving Pentru inceput am incercat sa trec mesajul prin base32, base58, base62 si base64, dar fara succes. De aici m-am gandit sa fac acelasi lucru, dar facut un rev() peste textul initial; tot nimic. Am mai stat putin sa ma gandesc si am incercat caesar peste text, iar la ROT 13 am reusit sa scot un text in clar, folosind base32 peste. Textul avea un padding la inceput, deci am dedus ca este scris de la dreapta la stanga. Am facut un rev() pe el si arata a text encodat cu base64. L-am decodificat si mi-a dat de brainfuck (literalmente ) ). Am luat codul, l-am bagat intr-un interpretor de brainfuck si am scos flag-ul.
-
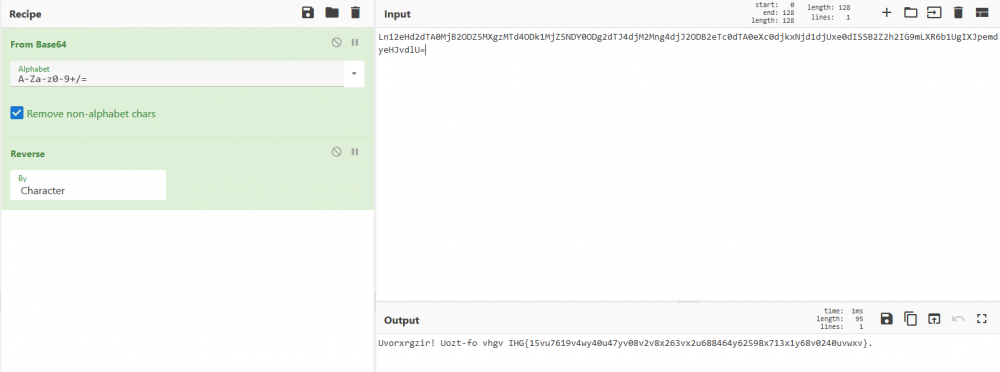
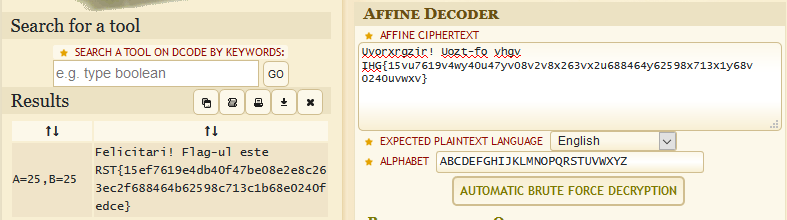
Mesajul de pe retea - I Autor: 0x435446 Summary Am primit un mesaj codificat. Proof of Solving De cand am vazut padding-ul de la base64 am incercat sa vad daca as putea decodifica mesajul cu aceasta metoda. Dupa decodificare am primit in mesaj ce parea scris de la dreapta la stanga, asa ca am facut un rev() pe el si a iesit cam asa: Uvorxrgzir! Uozt-fo vhgv IHG{15vu7619v4wy40u47yv08v2v8x263vx2u688464y62598x713x1y68v0240uvwxv}. De aici am incercat diferite metode de criptare pe care se paote face usor bruteforce si am gasit ca este criptat folosind affine.
-
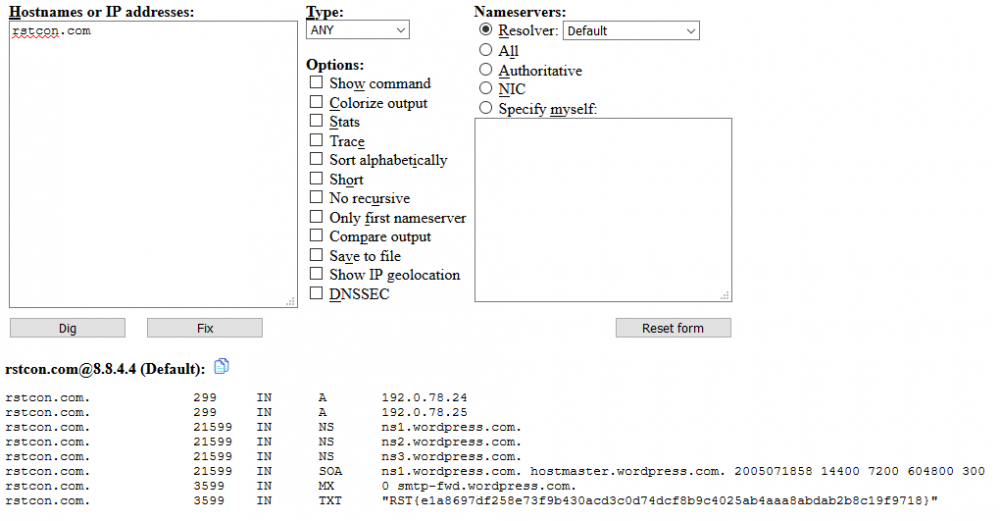
Interviul Autor: 0x435446 Summary DNS Records Proof of Solving Cand am citit prima data descrierea challenge-ului, am crezut ca trebuie sa caut recursiv prin toate paginile de pe rstcon.com si flag-ul se va gasi pe undeva printr-un comentariu, dar aparent nu era asa. Dupa ce m-am gandit putin am incercat sa verific DNS Records. Am intrat pe https://www.digwebinterface.com, am pus site-ul in textbox, am dat pe ANY Records si am gasit flag-ul in cele TXT.
-
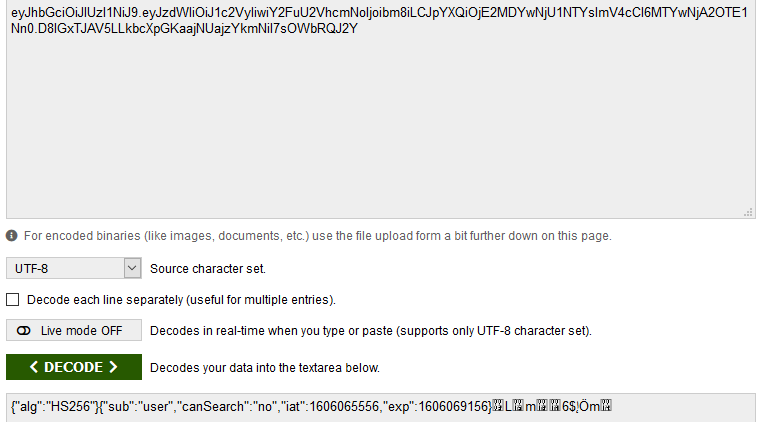
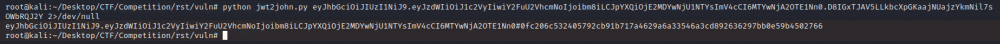
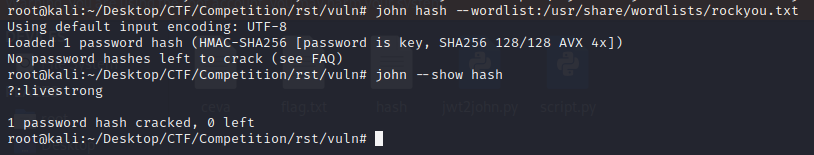
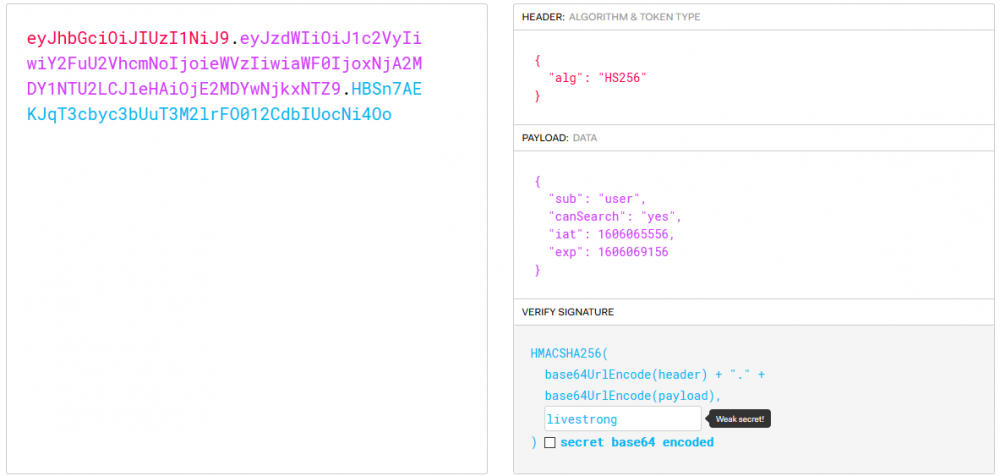
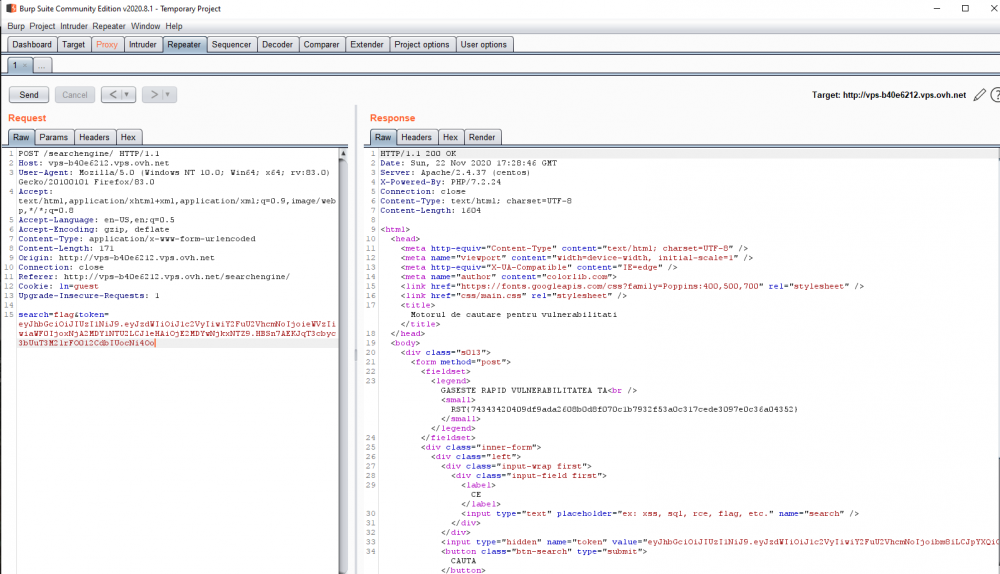
Motorul de cautare pentru vulnerabilitati Autor: 0x435446 Summary Folosirea unui token jwt vulnerabil din cauza secretului. Proof of Solving Prima data am incercat pe acel search-bar de pe prima pagina cateva tipuri de atac, pentru a verifica daca site-ul este vulnerabil. De aici am cautat sa verific daca este ceva in cookie-uri sau robots.txt, dar tot nimc, insa am gasit un token pus pe hidden in sursa paginii. L-am luat, l-am decodificat base64 ca sa pot vedea continutul si am vazut asta: De aici am luat token-ul, i-am scos hash-ul cu jwt2john si i-am facut bruteforce la secret cu john. Acum am mai avut doar de craftat un token care sa aiba setat “canSearch” pe “yes”. M-am folosit de jwt.io pentru asta. Dupa ce l-am craftat am interceptat un request catre site in care am pus “flag” in search-bar, am inlocuit token-ul cu cel generat si am scos flag-ul.
-
Premiul pentru cel mai bun write-up a fost castigat de catre 0x435446, felicitari! Mai jos vom posta write-up-uri.
-
Conferinta: Eveniment Linkedin: 170 de participanti Eveniment Facebook: 68 de participanti Zoom participanti inregistrati: 204 Zoom participanti unici: 186 (fara speakers) Zoom participanti maxim online: 95 (fara speakers) Zoom medie participanti: 70-75 (intre 90+ si 50+) CTF: 15 challenges 80 users registered 45 teams registered 32 right submissions 137 wrong submissions Multumim tuturor celor care au participat, au contribuit sau au transmis mai departe despre eveniment si ne revedem anul viitor! Mie mi se pare ca a iesit bine pentru o prima editie.
-
- 3
-

-

-
├── Crypto │ ├── Mesajul de pe retea - I (50) @Dragos │ ├── Mesajul de pe retea - II (482) @Dragos │ ├── Mesajul de pe retea - III (500) | └── Mesajul de pe retea - IV (500) @Dragos ├── Forensics | └── Hacking Google (500) @Nytro ├── Misc │ ├── Interviul (428) @Dragos │ ├── Ceainicul (496) @Dragos | └── Liftul (500) @Dragos ├── Pwn | └── Animalul preferat (496) @Nytro ├── Reversing | └── The Encryptor (500) @Nytro └── Web ├── Motorul de cautare pentru vulnerabilitati (428) @Dragos ├── Platforma Intranet (496) @Dragos ├── Aresty File Uploader (500) @Dragos ├── Casa Pariurilor (500) @dancezar └── Pingster (500) @nytr0gen Vor mai fi disponibile aproximativ doua saptamani. Ulterior, daca si colegii care au facut challenge-urile sunt de acord, le putem publica atat sursele cat si rezolvarile. Platforma CTF: https://ctf.rstcon.com/
-
- 2
-

-
Cu toții știm ce este un XSS și cum să îl găsim, cel puțin în cazurile mai simple. Dar un penetration test trebuie să acopere mult mai mult de atât. Atenția la detalii este cea care rezultă în “finding-uri”. În această prezentare nu voi veni cu lucruri ieșite din comun dar voi trece printr-o listă de sfaturi utile atunci când faceți un pentest. Lista nu este nici pe departe completă, dar sper să vă ajute. Ionuț Popescu (Nytro) – UiPath Ionuț Popescu este unul dintre administratorii forumului RST. Lucrează la UiPath ca Penetration Tester și este pasionat de tot ce înseamnă securitate IT.
-
- 2
-