-
Posts
18740 -
Joined
-
Last visited
-
Days Won
711
Posts posted by Nytro
-
-
Salut, intrebarea suna ciudat dar are sens.
Tastatura sau alte device-uri vin cu propriul microcontroller care ruleaza cod. In principiu nu se poate face nimic, dar teoretic, daca ar fi un dispozitiv indeajuns de avansat si ar avea o procedura de update de firmare s-ar putea ajunge la asa ceva. Daca ar avea, de asemenea, ar trebui sa verifice integritatea firmware-ului la care se face update/upgrade pe baza unei semnaturi digitale.
Se cunoaste faptul ca in sistemele de operare moderne (datorita arhitecturii procesoarelor) exista o separare de privilegii la nivel de "ring" unde ring0 = Kernel mode, sistemul de operare care are acces la toate resursele iar ring3 = usermode care e mult mai limitat. Dar se poate vede si altfel aceasta problema daca intram mai in adancime in problema:
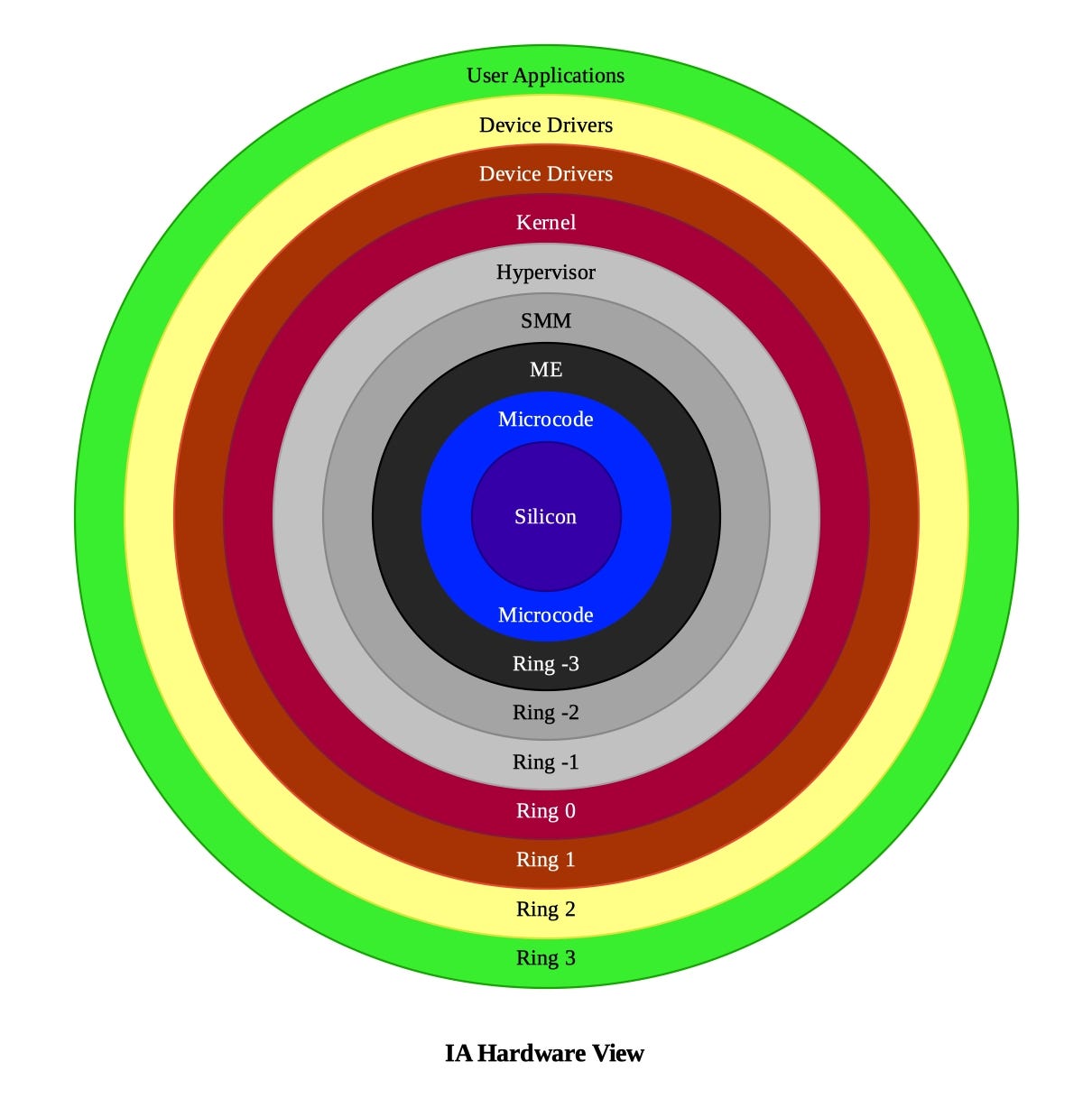
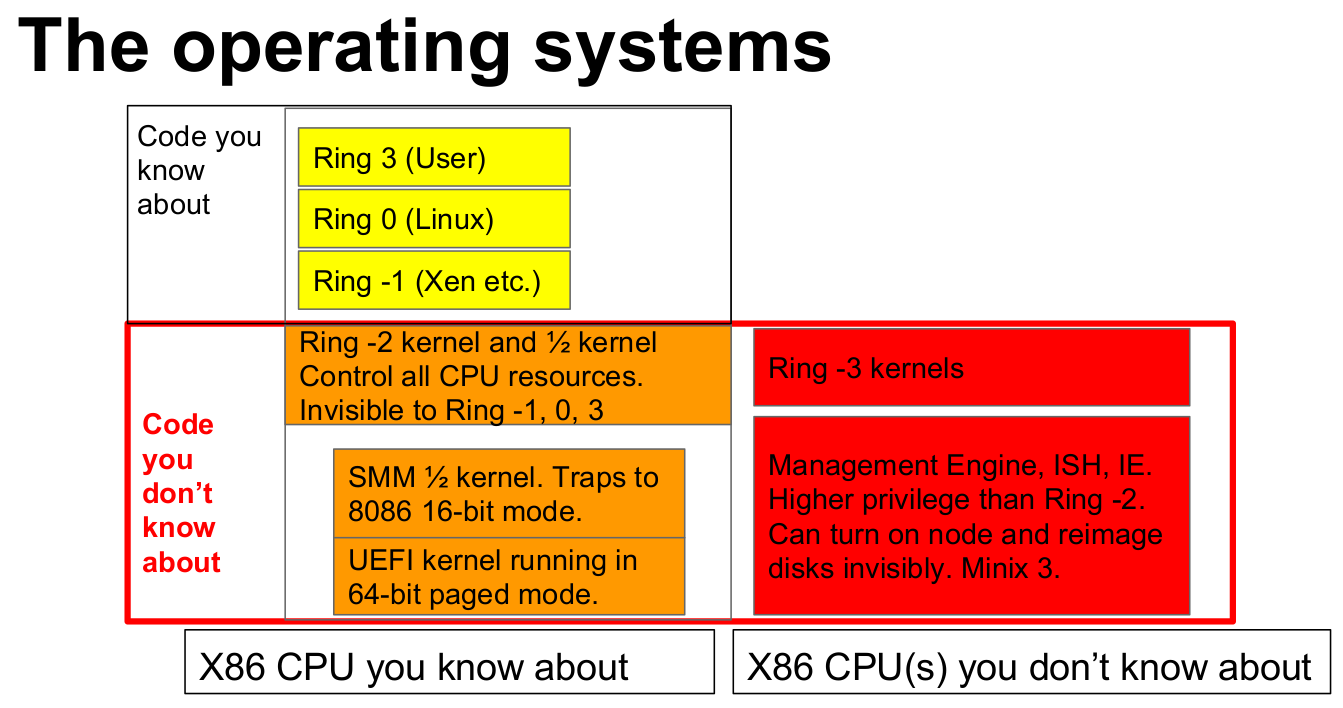
Cu alte cuvinte, exista de exemplu chiar si in procesor in firmware care permite executia codului assembler (in machine code) pe care il cunoastem. Se poate face update la el asa cum s-a intamplat cand au aparut vulnerabilitati in procesoare gen Specter sau Meltdown cand pentru fix a fost necesar update de microcode (firmware de procesor).
Exact acelasi lucru se poate intampla si cu alte device-uri. De exemplu placi video. Sau BIOS. Sau mai stiu eu ce.
Si ca sa rezum problema, daca un device e indeajuns de avansat incat sa aiba (doar ca exemplu) functionalitati gen firmware update, in teorie (si in practica daca e vulnerabil la asa ceva si nu verifica aceste firmware updates) se poate infecta si cand ajunge pe un alt device sa fie in continuare infectat. De asemenea, un antivirus de exemplu nu are ce sa faca.
PS: Asta nu inseamna ca acel device infectat va putea lua controlul asupra calculatorului la care e conectat ulterior. Sistemul de operare prin functionalitati gen Plug & Play si standarde gen PCI Express, USB sau altele, permit doar un numar de actiuni si nu sa faca ceea ce doresc. Acel device infectat va fi limitat la device-ul in sine, nu s-ar putea existinde la alte device-uri sau la sistemul de operare (decat desigur, daca exista probleme de securitate in OS).
Sper ca ajuta.
-
 5
5
-
-
Am fost sunat de catre cineva de la compania de telecomunicatii si am patit acest lucru, dar asta se intampla de fiecare data, indiferent ca e vorba de un serviciu, o banca si mai stiu eu ce.
Mi se par doua lucruri idioate:
1. Ma pune sa fiu de acord ca apelul sa fie inregistrat cand eu sunt cel apelat
2. Imi cere o data personala (sigur, nu CNP, lucruri mai marunte gen data nasterii) dar nu mi se pare normal sa le dau unei persoane la intamplare care ma suna
Eu de obicei ii intreb si pe ei daca sunt de acord ca apelul sa fie inregistrat (desi nu fac asta) si sa imi confirme ca sunt de la serviciul respectiv si ca au anumite date despre mine. Uneori a mers. Problema e urmatoarea: majoritatea inchid (si se mai si supara pe mine
 ) si e posibil sa nu aflu lucruri utile. Am patit asta la banca, dar am avut noroc ca am primit si SMS.
) si e posibil sa nu aflu lucruri utile. Am patit asta la banca, dar am avut noroc ca am primit si SMS.
Voi ce parere aveti despre asta? Sunt prea paranoic? Voi ce faceti?
Cum e din punct de vedere legal? Pe de-o parte inteleg ca imi protejeaza datele personale, pe de alta parte nu prea.
-
 1
1
-
 2
2
-
-
Nu prea avem cum sa te ajutam noi, fiecare platforma web imensa, ca Facebook, are proceduri proprii pentru astfel de situatii.
Daca nu merge ceva (e.g. nu primesti SMS) va trebui probabil sa iei legatura cu cineva de la Support sa te ajute.
-
Probabil cineva de la Support, angajati care by design au acces la productie.
Poate lumea o sa ia mai in serios acum acel "insider threat" pe care toti il considera o porcarie...
-
Hackers Convinced Twitter Employee to Help Them Hijack Accounts
After a wave of account takeovers, screenshots of an internal Twitter user administration tool are being shared in the hacking underground.By Joseph CoxJuly 16, 2020, 2:14aIMAGE: CHRIS RATCLIFFE/BLOOMBERG VIA GETTY IMAGESA Twitter insider was responsible for a wave of high profile account takeovers on Wednesday, according to leaked screenshots obtained by Motherboard and two sources who took over accounts.
On Wednesday, a spike of high profile accounts including those of Joe Biden, Elon Musk, Bill Gates, Barack Obama, Uber, and Apple tweeted cryptocurrency scams in an apparent hack.
"We used a rep that literally done all the work for us," one of the sources told Motherboard. The second source added they paid the Twitter insider. Motherboard granted the sources anonymity to speak candidly about a security incident. A Twitter spokesperson told Motherboard that the company is still investigating whether the employee hijacked the accounts themselves or gave hackers access to the tool.
The accounts were taken over using an internal tool at Twitter, according to the sources, as well as screenshots of the tool obtained by Motherboard. One of the screenshots shows the panel and the account of Binance; Binance is one of the accounts that hackers took over today. According to screenshots seen by Motherboard, at least some of the accounts appear to have been compromised by changing the email address associated with them using the tool.
In all, four sources close to or inside the underground hacking community provided Motherboard with screenshots of the user tool. Two sources said the Twitter panel was also used to change ownership of some so-called OG accounts—accounts that have a handle consisting of only one or two characters—as well as facilitating the tweeting of the cryptocurrency scams from the high profile accounts.
Twitter has been deleting some screenshots of the panel and has suspended users who have tweeted them, claiming that the tweets violate its rules.
Do you know anything else about these account hijackings, or insider data abuse at other companies? We'd love to hear from you. Using a non-work phone or computer, you can contact Joseph Cox securely on Signal on +44 20 8133 5190, Wickr on josephcox, OTR chat on jfcox@jabber.ccc.de, or email joseph.cox@vice.com.
The panel is a stark example of the issue of insider data access at tech companies. Whereas in other cases hackers have bribed workers to leverage tools over individual users, in this case the access has led to takeovers of some of the biggest accounts on the social media platform and tweeted bitcoin related scams in an effort to generate income.
The screenshots show details about the target user's account, such as whether it has been suspended, is permanently suspended, or has protected status.
One of the screenshots is a Twitter user posting images of the panel themselves. At the time of writing that account has been suspended.
ONE OF THE SCREENSHOTS OF THE PANEL. ADDITIONAL REDACTIONS BY MOTHERBOARD.
Data breach monitoring and prevention service Under The Breach obtained a similar screenshot and tweeted it as the worker hijacked several accounts. The person in control of the Under The Breach account told Motherboard Twitter then removed the tweet with the screenshot and suspended them for 12 hours. A message replacing the tweet now says it violated the Twitter rules.
A SCREENSHOT SHOWING THE PANEL'S ACCESS TO BINANCE, ONE OF THE HACKED ACCOUNTS. IMAGE: MOTHERBOARD.
A Twitter spokesperson told Motherboard in an email that, "As per our rules, we're taking action on any private, personal information shared in Tweets."
After the publication of this piece, Twitter said in a tweet that "We detected what we believe to be a coordinated social engineering attack by people who successfully targeted some of our employees with access to internal systems and tools."
Other hijacked accounts include Mike Bloomberg, and cryptocurrency platforms Coinbase and Gemini. The accounts falsely announced they had partnered up with an organization called CryptoForHealth which claims it was going to provide people with bitcoin as long as they sent some to an address first.
Shortly after the spike of takeovers, Twitter itself tweeted that users may be unable to reset their passwords or tweet while the company addresses the issue.
Within an hour of the breach, Republican Sen. Josh Hawley wrote a letter to Twitter CEO Jack Dorsey asking for more information about the hack, including how the hack occurred, how many users were compromised, and whether the hack affected President Trump's account. Hawley said "please reach out immediately to the Department of Justice and the Federal Bureau of Investigation and take any necessary measures to secure the site before this breach expands."
In 2017, a Twitter worker briefly deleted President Donald Trump's account before it was quickly reinstated.
Two former Twitter employees previously abused their access to spy on users for the Saudi regime, according to the Justice Department.
All tech companies face the issue of malicious insiders. Motherboard has previously revealed how Facebook employees used their privilege access to user data to stalk women; how Snapchat workers had a tool called Snaplion that provides information on users; and how MySpace employees abused a tool called "Overlord" to spy on users during the site's hayday.
Update: This piece has been updated to include a response from Twitter and more information from a SIM swapping source.
-
 1
1
-
-
Several High-Profile Accounts Hacked in the Biggest Twitter Hack of All Time
July 15, 2020Ravie LakshmananSocial media platform Twitter, earlier today on Wednesday, was on fire after it suffered one of the biggest cyberattacks in its history.
A number of high-profile Twitter accounts, including those of US presidential candidate Joe Biden, Amazon CEO Jeff Bezos, Bill Gates, Elon Musk, Uber, and Apple, were breached simultaneously in what's a far-reaching hacking campaign carried out to promote a cryptocurrency scam.
The broadly targeted hack posted similar worded messages urging millions of followers to send money to a specific bitcoin wallet address in return for larger payback.
"Everyone is asking me to give back, and now is the time," a tweet from Mr Gates' account said. "You send $1,000, I send you back $2,000."
Twitter termed the security incident as a "coordinated social engineering attack" against its employees who access its internal tools.
As of writing, the scammers behind the operation have amassed nearly $120,000 in bitcoins, suggesting that unsuspecting users have indeed fallen for the fraudulent scheme.
"We detected what we believe to be a coordinated social engineering attack by people who successfully targeted some of our employees with access to internal systems and tools," the company said in a series of tweets.
"Internally, we've taken significant steps to limit access to internal systems and tools while our investigation is ongoing."
It's not immediately clear who was behind the attack, or the attackers could have had access to direct messages sent to or from the affected accounts.
The attack appears to have been initially directed against cryptocurrency-focused accounts, such as Bitcoin, Ripple, CoinDesk, Gemini, Coinbase and Binance, all of which were hacked with the same message:
"We have partnered with CryptoForHealth and are giving back 5000 BTC to the community," followed by a link to a phishing website that has since been taken down.
Following the tweets, the accounts for Apple, Uber, Mike Bloomberg, and Tesla and SpaceX CEO Elon Musk all posted tweets soliciting bitcoins using the exact same Bitcoin address as the one included on the CryptoForHealth website.
Although the tweets from the compromised accounts have been deleted, Twitter took the extraordinary step of temporarily stopping many verified accounts marked with blue ticks from tweeting altogether.
Account hijacks on Twitter have happened before, but this is the first time it's happened at such an unprecedented scale on the social network, leading to speculations that hackers grabbed control of a Twitter employee's administrative access to "take over a prominent account and tweet on their behalf" without knowing their passwords or two-factor authentication codes.
Security researchers also found that the attackers had not only taken over the victims' accounts, but also changed the email address associated with the account to make it harder for the real user to regain access.
Last year, Twitter chief executive Jack Dorsey's account was hacked in a SIM swapping attack, allowing an unauthorized third-party to post tweets via text messages from the phone number. Following the incident, Twitter discontinued the feature to send tweets via SMS earlier this year in most countries.
Given the widespread scope of the campaign, the damage could have been far more catastrophic. But the motive of the adversaries seems to all but indicate this was a quick money-making scam.
"The accounts appear to have been compromised in order to perpetuate cryptocurrency fraud," the FBI's San Francisco field office said in a statement. "We advise the public not to fall victim to this scam by sending cryptocurrency or money in relation to this incident."Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post. -
-
Dar, dar... 9gag e sursa mea de informatii


-
Singurla solutie pentru energie electrica nelimitata (care si functioneaza ca am testat si folosesc asta de ani de zile) e asta:
-
 2
2
-
 3
3
-
-
Te inseala, divertezi, problem solved. Nu vad cu ce ajuta sa citesti mesajele. Ca sa vezi cu cine? Ce mai conteaza?
Ar fi mai simplu sa ii dai de baut si iti zice el. Poate il si stresezi putin.
-
 2
2
-
-
Nu se transfera nimic automat. Ce poate sa faca e sa scaneze de porturi si sa gaseasca vreun serviciu vulnerabil, asa sa se "multiplice". Ceea ce e putin probabil.
Acel RAT a ajuns la tine pentru ca probabil ai descarcat cine stie ce mizerie infectata.
De unde stii ca ai RAT daca nu e detectabil? Instaleaza un antivirus adevarat, Kaspersky sau Bitdefender si scaneaza. Daca gasesc ceva, il sterg. Daca nu, nu il ai. Nu vine NSA sa lucreze ani de zile la bypassuri de AV pentru un RAT care sa ajunga la oameni random.
-
 1
1
-
-
E vorba de simt civic. Daca vezi o fata ca ia bataie pe strada, ii iei apararea. Nu e chiar exemplu ideal dar principiul e acelasi.
La fel si aici: oamenii sunt dobitoci, dar nu ar trebui lasati sa moara. La urma urmei e nevoie si de astfel de persoane pentru societate.
Suntem egal in drepturi. Atat. Cursul vietii noastre depinde de capacitatea noastra de adaptare la conditiile si mediul in care traim. Unde inteligenta are un rol important.
-
Capt. Darwin vine sa va explice: doar cei puternici supravietuiesc. Inteligenta este necesara pentru supravietuire iar cei care urmaresc si accepta sfaturi de la astfel de persoane isi merita soarta.
-
A tricky URL spoofing bug that I reported two years ago to Mozilla and it is still working: https://spoof.lbherrera.me (reproducible only on Firefox).
Sursa: https://twitter.com/lbherrera_/status/1280617786088329220
-
 1
1
-
-
Eu consider ca votul electronic poate fi facut in siguranta. Sigur, centralizat. Cum e si acum, doar ca mai sigur si mai eficient. Baza: chestia aia care se prescurteaza "crypto" (si nu, nu e vorba de "crypto monede" ci de criptografie).
Ce de acum nu e tocmai ideal. Cel putin acum X ani taica-meo vedea saci de voturi aruncati prin padure. Putem face totul mai bine. Si asta e doar una dintre probleme.
PS: Exista si un mare dezavantaj: nu vom putea scrie "Muie PSD" pe buletinul de vot

-
 1
1
-
-
Securitatea sistemelor de vot electronic
Votul electronic este o propunere încă din anii 1960, gândită inițial pentru a diminua posibilitatea fraudării unui proces electoral, iar apoi, datorită creșterii accesului la Internet, și pentru a crește numărul cetățenilor cu drept de vot care participă la alegeri, respectiv pentru a permite cetățenilor din Diaspora unei țări, sau cetățenilor ce nu se pot deplasa la secții, să își exprime votul. Totuși, implementarea unui sistem de exprimare a votului pe internet pare să fie o provocare peste măsura capacității tehnologiei actuale. Scopul inițial, numărarea manuală a voturilor, un proces minuțios și vulnerabil, rămâne un candidat ideal pentru procesul de digitalizare.

Technology Officer
Articol complet: https://civiclabs.ro/ro/byproducts/securitatea-sistemelor-de-vot-electronic
-
 1
1
-
-
404 Not found
-
Live:
Guess who's back! After a rather long pause, Security Espresso's Meetups are back, in an online format! We're sure that you miss the gatherings and the beers, but rest assured it's all going to happen anyway!
Our first virtual meetup will happen online and will be streamed to YouTube. Make sure to join our Telegram group if you didn't already so you can ask any questions you might have for the speakers: https://t.me/secespresso
Without further ado, here are the speakers for Security Espresso Meet-up 0x23:
19:00 → 19:45
☠️ Principles of heap-based exploits on Windows 7 & 10 x32
📣 Stefan Nicula - Senior Threat Researcher @ Avira Protection Labs, Twitter: @stefan_niculaA successful userland heap memory corruption exploit on Windows requires a good grasp on the mechanisms behind the Heap Manager. The talk aims to tackle Windows Heap Manager internals such as Backend vs Frontend Allocators, VirtualAlloc, heap memory layout, Windows 10 vs Windows 7 Heap Manager differences and Windows Heap Integrity protection. We will also explore heap exploit principles for Use-after-free and Double Free exploits like primitives, allocators, precise heap spraying, stack pivot and ROP chaining.
In a future part 2 of the presentation, we will dive into more advanced techniques related to memory information leak, type confusion, abusing vtable pointers and Windows ATP protection bypasses.
19:45 → 20:00
⏸ Break20:00 → 20:45
🕶 Opsec guide for the security enthusiast
📣 Dan Demeter - Security Researcher @ GReAT, Twitter: @_xdanx
📣 Marco Preuss - Director @ GReAT, Europe, Twitter: @marco_preussAs more and more metadata is passively collected at a large scale, one might question the boundaries set by governments in regards to privacy and personal life. We believe privacy is a fundamental human right and, by using the right tools, it can still be achieved.
During this beginner’s opsec guide we will present techniques and tools to protect your digital communications, as well as your equipment.Some covered topics:
- Corporate communication crisis management
- Encryption and secure communication
- Physical device security
- Network activity monitoring
- Travelling to foreign countries20:45 → ∞
🍻 Virtual beer on Discord! Attendance policy: BYOD (bring your own drink).
🔗 Join us: https://discord.gg/7kCdJp8-
 2
2
-
-
Extensii ciudate de browser, click-uri pw cine stie ce site-uri, cu sau voia ta, iframe-uri de pe cine stie ce site-uri (desi nu cred ca ajung la visited) sai drag and drop la cine stie ce sau chiar Allow notifications... Nu stiu, pot fi multe cauze. Clear cache, history si tot ce e acolo, sters extensii si cam atat. Sau cine stie ce Adware de Mac, daca e Mac sau Linux nu inseamna ca nu poate lua Covid. Adica "virusi", doar ca necesita ceva interactiuni ca cele de mai sus sau gen instalare aplicatii ciudate.
-
Am trecut noi peste Sality, Confiqer... Trecem si peste Covid.
-
 4
4
-
-
Nu conteaza, facem conferinta online apoi mergem la bere la gramada - maxim 4 la masa sau cat o mai fi. Si acolo ne batem joc de Gogoasa

-
 1
1
-
 2
2
-
-
-
 1
1
-
 2
2
-
-
Bine ai revenit!
-
 1
1
-
-
Cineva a bagat un cablu de retea intr-un port gresit si a iesit un broadcast storm? (glumesc, nu am idee ce-or fi facut ) https://www.youtube.com/watch?v=se-pVwapTic
PS: La primul loc de munca si eu am facut asta si am stat ceva timp cateva persoane sa aflam ce se intampla

-
 1
1
-





VPN firm that claims zero logs policy leaks 20 million user logs
in Stiri securitate
Posted
VPN firm that claims zero logs policy leaks 20 million user logs
on July 16th, 2020
The VPN company in the discussion is a Hong Kong-based UFO VPN owned by Dreamfii HK Limited.
Perhaps, the most ironic moments in the cybersecurity world occur when those who promise to protect your online privacy cannot guard their own turf. We’ve seen this happen from time to time with security firms getting hacked themselves.
Another similar case has emerged recently when the database of a Hong Kong-based VPN provider called UFO VPN was exposed with more than 20 million users logs.
Discovered by researchers from Comparitech on July 1st, 2020; the exposure occurred due to the database hosted on an Elasticsearch cluster being left without any password.
See: PureVPN claimed it does not keep logs, yet it provided user logs to the FBI
Worth 894 GB, the data allegedly included plaintext passwords, IP addresses, timestamps of user connections, session tokens, information of the device, and OS being used along with geographical information in the form of tags.
The implications of this are pretty dangerous in that not only user accounts are at risk of being taken over by malicious actors but users can also be tracked online.
Furthermore, using the session tokens, any encrypted data that someone gains access to could also be decrypted rendering the entire concept of encryption useless in this scenario.
This, as Comparitech has rightly pointed out, goes against the service provider’s privacy policy and the promises of a zero log policy it has communicated to its users:
See: Israeli firm buys Private Internet Access (PIA) VPN raising privacy concerns
The incident was reported to UFO VPN and the database was secured yesterday on 15 July. The company, on the other hand, claims that due to the certain employee being changed because of the Coronavirus, the issue could not be identified earlier stating the following:
This though of course if what the company seems to be saying to mitigate the damage to its reputation with the facts clearly suggesting otherwise. For the future, hence, it remains to see if the firm improves its security practices and how many users jump ship. Users of the provider are suggested to immediately change their account passwords as they may be at risk.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.
Sursa; https://www.hackread.com/vpn-firm-zero-logs-policy-leaks-20-million-user-logs/