-
Posts
1259 -
Joined
-
Last visited
-
Days Won
87
Everything posted by gigiRoman
-
Eu am avut probleme cu enel, care imi "pierduse" niste documente cu caracter personal (copie ci, copie contract casa samd). Desi le dadusem unui agent enel, cand ii tot sunam sa clarific ma puneau sa retrimit. De fiecare data imi comunica robotul ca telefonul este inregistrat. Dupa ce 7 operatori s-au facut ca ploua, am facut plangere la autoritatea care se ocupa cu datele cu caracter personal, le-am dat ora si minutul apelului. In 2 zile m-a sunat enel, cerandu-si scuze ca au ratacit actele si mi-au mai spus ca nu au salvat inregistrarile apelurilor, sac. Din ce stiu, pentru a inregistra apeluri trebuie sa fii operator de date cu caracter personal. 1.trebuie sa fii defapt de acord ca ei sa stocheze inregistrarea telefonica. 2.iti cer ceva care nu e atat de periculos de scurs ca cnpul. Cum ar fi data nasterii sau mail sau adresa. O alta problema mai veche e ca banca (raiff...) vindea datele catre firme de asigurari si m-am trezit sunat de defuncta alico sa imi prezinte o asigurare de viata/sanatate/accident fara sa fiu informat de banca in prealabil ca vor impartasi datele mele personale cu terti. (Aceasta intamplare a fost cu ceva timp inainte de gdpr).
-
Si-a pus leo ca e zodia leu 😄😄😄😄 Si cyber ca e in saibar speis. Cred.
-

cum sa citești sms-urile altcuiva in timp real?
gigiRoman replied to EMA-sms's topic in Cosul de gunoi
La vdf nu, doar ora data si numarul destinatarului/expeditorului. Mai mult decat suficient.- 5 replies
-
- spyphone smsspy
- ss7
-
(and 4 more)
Tagged with:
-

cum sa citești sms-urile altcuiva in timp real?
gigiRoman replied to EMA-sms's topic in Cosul de gunoi
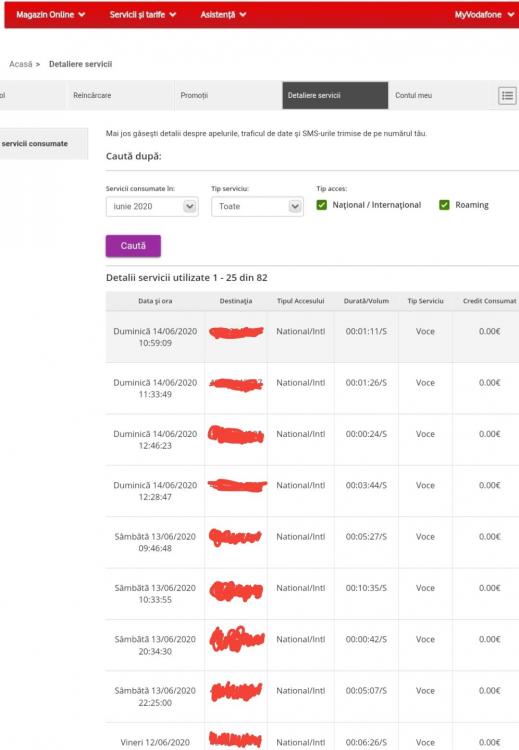
Dc e vdf poti verifica nr catre care se initiaza apeluri se trimite sms. Trebuie sa te loghezi in cont. https://www.vodafone.ro/vfrointegration/appmanager/vfroportal/cartela?_nfpb=true&_windowLabel=OCS_DetaliereServicii&_urlType=action&wlpOCS_DetaliereServicii_action=search&_pageLabel=OCS_Detaliere_Servicii_Page Trebuie sa citesti si sa fii de acord si sa respecti termenii si conditiile:- 5 replies
-
- 1
-

-
- spyphone smsspy
- ss7
-
(and 4 more)
Tagged with:
-
Aici e un forum de baieti discreti pe umarul carora poti plange. @aismen iti poate trimite un cod de introducere.
- 5 replies
-
- 5
-

-
- hacking program l
- tracking sms
- (and 7 more)
-

Introducing Winbindex - the Windows Binaries Index
gigiRoman replied to Kev's topic in Tutoriale in engleza
Nu stiam de pymultitor 🙂 Bun articolul! -
Uite o piesa care nu mai exista pe net: Foarte buna: UNU_-_Robo_Baiat_Bun.zip
-
Interesat.
-
Pentru proiect de licenta si cu ce a zis Nytro poti incerca : Sursa: https://1lib.eu/book/3361903/d45ab9 descriere: Gray Hat 😄 Creating and Automating Security Tools Brandon Perry Learn to use C#'s powerful set of core libraries to automate tedious yet important tasks like performing vulnerability scans, malware analysis, and incident response. With some help from Mono, you can write your own practical security tools that will run on Windows, Mac, Linux, and even mobile devices. Following a crash course in C# and some of its advanced features, you'll learn how to: Write fuzzers that use the HTTP and XML libraries to scan for SQL and XSS injection Generate shellcode in Metasploit to create cross-platform and cross-architecture payloads Automate Nessus, OpenVAS, and sqlmap to scan for vulnerabilities and exploit SQL injections Write a .NET decompiler for Mac and Linux Parse and read offline registry hives to dump system information Automate the security tools Arachni and Metasploit using their MSGPACK RPCs Streamline and simplify your work day with Gray Hat C# and C#'s extensive repertoire of powerful tools and libraries.
-
De ce nu iti pui un proxy sa vezi ce date trimite la server? Poate le manipulezi prin intermediul proxyului. Nu vreti sa vedem ce e in gameguard?
-

Intrebare in legatura cu RAT si drepturile de administrator
gigiRoman replied to grandson's topic in Discutii incepatori
Cred ca se referea la user mode si kernel mode nu la admin rights. -
Fa o sesizare la anpc. Simplu. Nu ai nimic de pierdut.
-

Windows 10 gets DNS over HTTPS support, how to test
gigiRoman replied to Nytro's topic in Stiri securitate
Netripper e doar sniffer, nu? -

Windows 10 gets DNS over HTTPS support, how to test
gigiRoman replied to Nytro's topic in Stiri securitate
Smecherie cu pktmon.exe Since October 2018 Update, Windows 10 comes with a “Packet Monitor” tool called pktmon.exe. With the upcoming release of the Windows 10 May 2020 Update, Microsoft will update the pktmon tool to allow real-time visualization of monitored packets. -
Titus felix furtuna? Licenta sau master sau proiect licenta?
- 6 replies
-
- java
- programare
-
(and 3 more)
Tagged with:
-

Huawei a incercat sa compromita nucleu Linux cu un patch
gigiRoman replied to Nytro's topic in Stiri securitate
Huawei denies involvement in buggy Linux kernel patch proposal. Era doar un pull request. https://www.google.com/amp/s/www.zdnet.com/google-amp/article/huawei-denies-involvement-in-buggy-linux-kernel-patch-proposal/ -
Parca in rootkits and bootkits descriau ca foloseau canale de twiter, telegram sau generatoare de domenii. Daca malwareul nu gasea domeniul respectiv apela generatorul offline si stia unde sa mearga. Mai erau si malwareurile care foloseau pastebin. La youtube nu m-am gandit niciodata, dar pe langa faptul ca este mai repede de dezvoltat partea de infrastructura (se folosesc de youtube) ii ajuta si faptul ca pe multe pc-uri traficul catre youtube e permis.
-
@raduc cu cine faci curs/seminar? https://www.google.com/search?q=proiect+java+ase&oq=proiect+java+ase&aqs=chrome..69i57j0.3197j0j7&client=ms-android-samsung-gn-rev1&sourceid=chrome-mobile&ie=UTF-8
- 6 replies
-
- java
- programare
-
(and 3 more)
Tagged with:
-
The American state of Delaware has been allowed to develop such types of offshore structures since 1965. Sorin Ovidiu Vântu Born: November 23, 1955 (age 64 years), Bucharest Aproape se juca cu puta in tarana vantu cand faceau aia manevre. 😄😄😄
-
Nu platesc taxe. Cica statul delaware din sua e recunoscut ca offshore. https://www.google.com/search?q=delaware+offshore&oq=delaware+off&aqs=chrome.3.69i57j0l3.5481j0j7&client=ms-android-samsung-gn-rev1&sourceid=chrome-mobile&ie=UTF-8
-
Sursa: https://github.com/enkomio/shed/blob/master/README.md Shed is an application that allow to inspect the .NET runtime of a program in order to extract useful information. It can be used to inspect malicious applications in order to have a first general overview of which information are stored once that the malware is executed. Shed is able to: Inject a .NET Assembly in a remote process (both managed and un-managed) Extract all objects stored in the managed heap Print strings stored in memory Save the snapshot of the heap in a JSON format for post-processing Dump all modules that are loaded in memory Download Source code Download binary Using Shed Shed is a command line tool. To display all available options run: shed.exe --help Inspecting an already running application In order to inspect an already running process you have to pass the pid to Shed. Example: Shed.exe --pid 2356 Inspecting a binary In order to inspect a binary, Shed needs to execute it and to attach to it in order to inspect the runtime. Example: Shed.exe --exe malware.exe You can also specify the amount of time (in milliseconds) to wait before to suspend the process. This will allow the program to have the time to initialize its properties. Example: Shed.exe --timeout 2000 --exe malware.exe Injecting an Assembly in a remote process With Shed is possible to inject a .NET Assembly in a remote process thanks to the ManagedInjector Library. In order to do so, it is necessary to specify the pid of the process and the exe to inject. Once that the Assembly is injected is possible to activate it by invoking a specific method. The rules to identify the method are inherithed by the ManagedInjector project and are the following: You must specify the full method name to invoke (eg. this.is.my.namespace.class.method) You can inject an executable that defines an EntryPoint method to execute (like a Console project) You can define a method with the following signatue: <public|private> static void Inject() For example, to inject the Assembly InjectedAssembly into the process with pid 1234, you have the run Shed with the following command: shed.exe --pid 1234 --exe InjectedAssembly.dll --inject With the --method option you can specify a method, from InjectedAssembly.exe to invoke. Find below an example of execution: Dumping options By default Shed dump both the heap and the modules. If you want only one of that specify the --dump-heap option to dump only the objects in the heap or the --dump-modules to dump only the modules. Dumping the heap can produce a lot of information which are not strictly useful for the analysis. You can filter it by using two files: blacklist.txt this file contains the type names prefix that must not be logged whitelist.txt this file contains the type names prefix that must be logged even if blacklisted For example, if you want to filter all the System.IO namespace but you are interested in logging System.IO.MemoryStream, you can add the first value to blacklist.txt and the second one to whitelist.txt. Examples In the Examples folder you will find three different projects that you can use in order to test Shed. Example: Shed.exe --exe ..\Examples\ConfigurationSample\ConfigurationSample.exe When the analysis is completed, Shed will print where you can find the result, as shown below: [+] Result saved to C:\Shed\Result\7800 Build Shed If you have installed Visual Studio, just run the build.bat batch file, it will create a zip file inside the build folder. License information Copyright (C) 2017 Antonio Parata - @s4tan License: GNU General Public License, version 2 or later; see LICENSE included in this archive for details.
-
- 4
-

-